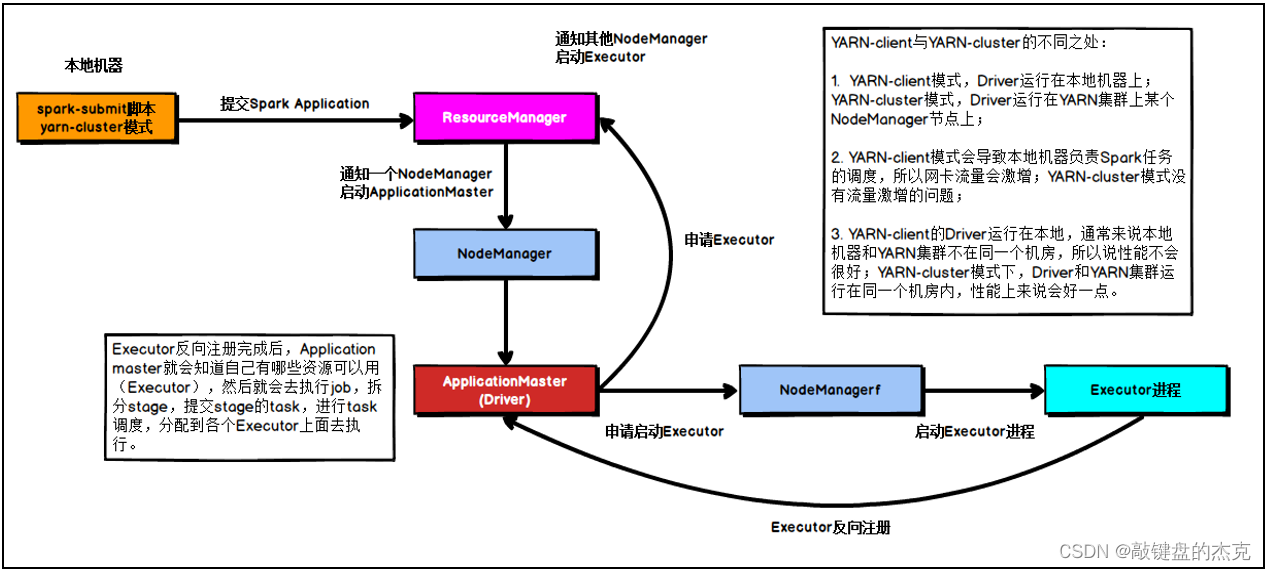
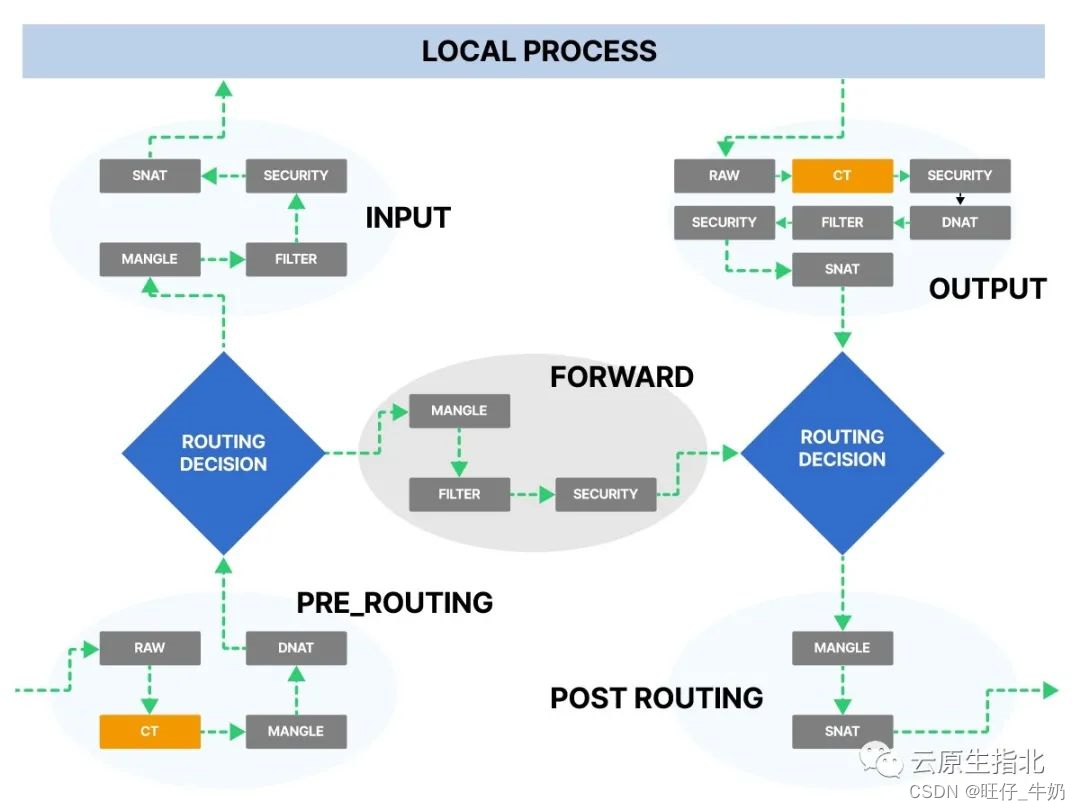
当前实验网络为IPV4模式通过tcpdump抓包,我们可以发现ping localhost的流量最终发送到lo网卡了 通过iptables pkts数据计数我们可知,ping localhost的iptables过滤流程为:应用程序->OUTPUT->POSTROUTING(路由决策到lo网卡)->lo网卡(处理完成后)->PREROUTING(路径决策到本地)->INPUT->应用程序,由此可见我们针对localhost做一些防火墙规则是会生效的 ping 127.0.0.1和ping localhost效果一致,这里不做测试了
[ root@localhost ~]
1 : lo: < LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0 .0.1/8 scope host lo
valid_lft forever preferred_lft forever
2 : ens160: < BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:82:82:e5 brd ff:ff:ff:ff:ff:ff
altname enp2s0
inet 192.168 .0.21/24 brd 192.168 .0.255 scope global noprefixroute ens160
valid_lft forever preferred_lft forever
iptables -t raw -A PREROUTING -p icmp -j ACCEPT
iptables -t raw -A OUTPUT -p icmp -j ACCEPT
iptables -t mangle -A INPUT -p icmp -j ACCEPT
iptables -t mangle -A POSTROUTING -p icmp -j ACCEPT
[ root@localhost ~]
dropped privs to tcpdump
tcpdump: listening on lo, link-type EN10MB ( Ethernet) , snapshot length 262144 bytes
07:24:23.690903 IP6 ( flowlabel 0xe1051, hlim 64 , next-header ICMPv6 ( 58 ) payload length: 64 ) ::1 > ::1: [ icmp6 sum ok] ICMP6, echo request, id 2 , seq 1
07:24:23.690938 IP6 ( flowlabel 0xfcb2c, hlim 64 , next-header ICMPv6 ( 58 ) payload length: 64 ) ::1 > ::1: [ icmp6 sum ok] ICMP6, echo reply, id 2 , seq 1
^C
2 packets captured
4 packets received by filter
0 packets dropped by kernel
[ root@localhost ~]
Chain PREROUTING ( policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2 168 ACCEPT icmp -- * * 0.0 .0.0/0 0.0 .0.0/0
Chain OUTPUT ( policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2 168 ACCEPT icmp -- * * 0.0 .0.0/0 0.0 .0.0/0
[ root@localhost ~]
Chain PREROUTING ( policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT ( policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2 168 ACCEPT icmp -- * * 0.0 .0.0/0 0.0 .0.0/0
Chain FORWARD ( policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT ( policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING ( policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2 168 ACCEPT icmp -- * * 0.0 .0.0/0 0.0 .0.0/0
iptables -t raw -F
iptables -t mangle -F
由于ping本机地址,数据报文最终也被送到lo网卡了,其iptables过滤顺序和ping localhost一致,这里不重复分析了
同上面网络信息
[ root@localhost ~]
ping: socket: Address family not supported by protocol
PING 192.168 .0.21 ( 192.168 .0.21) 56 ( 84 ) bytes of data.
64 bytes from 192.168 .0.21: icmp_seq = 1 ttl = 64 time = 0.090 ms
--- 192.168 .0.21 ping statistics ---
1 packets transmitted, 1 received, 0 % packet loss, time 0ms
rtt min/avg/max/mdev = 0.090 /0.090/0.090/0.000 ms
[ root@localhost ~]
dropped privs to tcpdump
tcpdump: listening on ens160, link-type EN10MB ( Ethernet) , snapshot length 262144 bytes
^C
0 packets captured
0 packets received by filter
0 packets dropped by kernel
[ root@localhost ~]
dropped privs to tcpdump
tcpdump: listening on lo, link-type EN10MB ( Ethernet) , snapshot length 262144 bytes
21 :51:04.409541 IP ( tos 0x0, ttl 64 , id 37837 , offset 0 , flags [ DF] , proto ICMP ( 1 ) , length 84 )
192.168 .0.21 > 192.168 .0.21: ICMP echo request, id 4 , seq 1 , length 64
21 :51:04.409557 IP ( tos 0x0, ttl 64 , id 37838 , offset 0 , flags [ none] , proto ICMP ( 1 ) , length 84 )
192.168 .0.21 > 192.168 .0.21: ICMP echo reply, id 4 , seq 1 , length 64
^C
2 packets captured
4 packets received by filter
0 packets dropped by kernel

![[CoderChef复盘] START86 div4 20230419】](https://img-blog.csdnimg.cn/41bbc5270d064091a2ea16d1bae11ed0.png)