文章目录
- 1.开关机安全控制
- 1.1 GRUB限制
- 1.2 实例:GRUB 菜单设置密码
- 2.终端登录安全控制
- 2.1 限制root只在安全终端登录
- 2.2 禁止普通用户登录
- 3.弱口令检测
- 3.1 Joth the Ripper,JR
- 4.网络端口扫描
- 4.1 nmap命令
1.开关机安全控制
1.1 GRUB限制

限制更改GRUB引导参数
通常情况下在系统开机进入GRUB菜单时,按e键可以查看并修改GRUB引导参数,这对服务器是一个极大的威胁。
可以为GRUB 菜单设置一个密码,只有提供正确的密码才被允许修改引导参数。
1.2 实例:GRUB 菜单设置密码
(1)根据提示设置GRUB菜单的密码;
[root@clr ~]# grub2-mkpasswd-pbkdf2 #根据提示设置GRUB菜单的密码
输入口令:
Reenter password: #此处设置的密码就是登录系统时,输入的密码,用户名和密码正确才可以登录系统,修改GRUB引导参数
PBKDF2 hash of your password is grub.pbkdf2.sha512.10000.2E11090ED7F21187E36302A2F34296AAC411240DE33B9E997A58DF4CE3BF5CA0CF0241882DD1A6B509C6F22BAD6E302DBC77909BF7685614D29D9954B170545E.5903DA571D3EBD55FA35B9D45595C552EA2AE017C11F3C47020CA158FFD4609C3ABCDFF39C000AACC175831EFA2C105462D4E6FC2B2AAF128AEE3CCA2FDD4E7A #加密生成的密码字符串
(2)备份密码字符串、grub.cfg文件以及00_header文件;
[root@clr ~]# vim pass.txt #将密码字符串复制到pass.txt文件中
[root@clr ~]# cat pass.txt
ha512.10000.2E11090ED7F21187E36302A2F34296AAC411240DE33B9E997A58DF4CE3BF5CA0CF0241882DD1A6B509C6F22BAD6E302DBC77909BF7685614D29D9954B170545E.5903DA571D3EBD55FA35B9D45595C552EA2AE017C11F3C47020CA158FFD4609C3ABCDFF39C000AACC175831EFA2C105462D4E6FC2B2AAF128AEE3CCA2FDD4E7A
[root@clr ~]# cd /boot/grub2
[root@clr /boot/grub2]# ls
device.map fonts grub.cfg grubenv i386-pc locale
[root@clr /boot/grub2]# cp grub.cfg grub.cfg,bak #将grub.cfg文件中的内容备份到grub.cfg,bak文件中
[root@clr /boot/grub2]# cd /etc/grub.d/
[root@clr /etc/grub.d]# cp 00_header{,.bak} #将00_header文件中的内容备份到00_header.bak文件中
(3)设置能够修改GRUB菜单的用户名和密码;
[root@clr /etc/grub.d]# vim 00_header
echo else
make_timeout "${GRUB_HIDDEN_TIMEOUT}" "${GRUB_TIMEOUT}"
fi
cat << EOF
set superusers="root" #设置能够修改GRUB菜单的用户名为root
password_pbkdf2 root grub.pbkdf2.sha512.10000.2E11090ED7F21187E36302A2F34296AAC411240DE33B9E997A58DF4CE3BF5CA0CF0241882DD1A6B509C6F22BAD6E302DBC77909BF7685614D29D9954B170545E.5903DA571D3EBD55FA35B9D45595C552EA2AE017C11F3C47020CA158FFD4609C3ABCDFF39C000AACC175831EFA2C105462D4E6FC2B2AAF128AEE3CCA2FDD4E7A #设置并保存经过加密生成的密码
EOF
(4)生成新的grub.cfg文件;
[root@clr /etc/grub.d]# grub2-mkconfig -o /boot/grub2/grub.cfg
Generating grub configuration file ...
Found linux image: /boot/vmlinuz-3.10.0-1160.el7.x86_64
Found initrd image: /boot/initramfs-3.10.0-1160.el7.x86_64.img
Found linux image: /boot/vmlinuz-0-rescue-675c23e85f174b7ca25013149d0b69ad
Found initrd image: /boot/initramfs-0-rescue-675c23e85f174b7ca25013149d0b69ad.img
done

2.终端登录安全控制
2.1 限制root只在安全终端登录
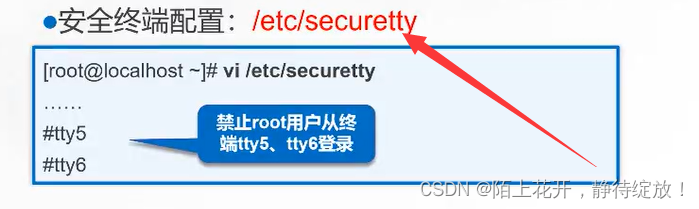
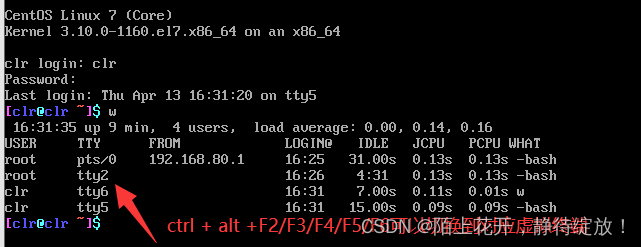
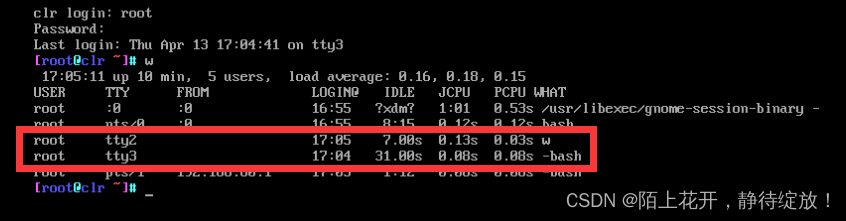
/etc/securetty:保存虚拟终端的配置文件,注释指定虚拟主机,将无法登录到系统;
[root@clr ~]# vim /etc/securetty
console
vc/1
vc/2
vc/3
tty2
tty3
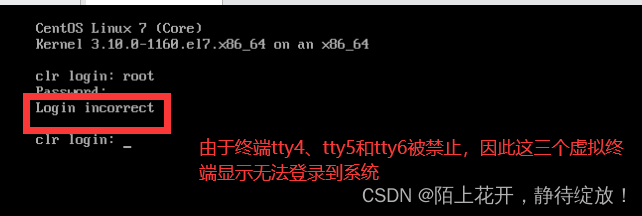
#tty4
#tty5 #限制虚拟终端从tty4,tty5和tty6登录到系统
#tty6
2.2 禁止普通用户登录
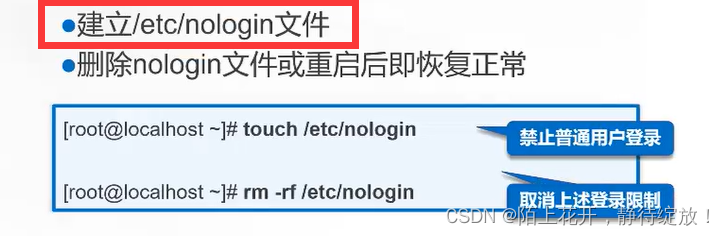
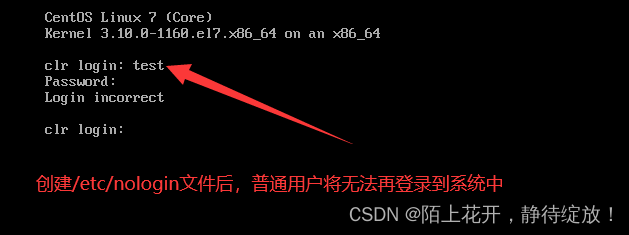
/etc/nologin:创建该文件后,普通用户将无法再登录到系统中;
[root@clr ~]# touch /etc/nologin
[root@clr ~]# rm -f /etc/nologin #删除该文件后,其他普通文件仍然又可以继续登录到系统中
3.弱口令检测
3.1 Joth the Ripper,JR
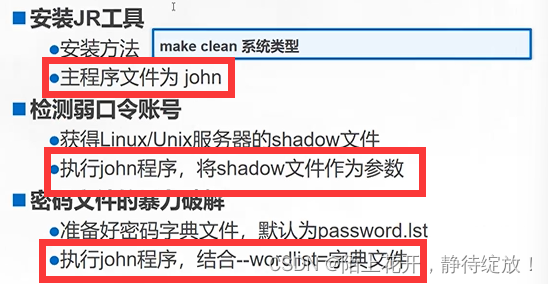
使用JR密码破解工具,进行弱口令检测,步骤如下所示:
(1)解压工具包;
[root@clr ~]# cd /opt/
[root@clr /opt]# rz -E #将john压缩工具包拉入虚拟机中
[root@clr /opt]# ls
john-1.8.0.tar.gz rh
[root@clr /opt]# tar xf john-1.8.0.tar.gz #解压工具包
(2)切换到src子目录;
[root@clr /opt]# ls
john-1.8.0 john-1.8.0.tar.gz rh
[root@clr /opt]# cd john-1.8.0/
[root@clr /opt/john-1.8.0]# ls
doc README run src
[root@clr /opt/john-1.8.0]# cd src/
(3)进行编译安装;
[root@clr /opt/john-1.8.0/src]# make clean linux-x86-64
rm -f ../run/john ../run/unshadow ../run/unafs ../run/unique ../run/john.bin ../run/john.com ../run/unshadow.com ../run/unafs.com
rm -f ../run/unshadow
ln -s john ../run/unshadow
rm -f ../run/unafs
ln -s john ../run/unafs
rm -f ../run/unique
ln -s john ../run/unique
make[1]: 离开目录“/opt/john-1.8.0/src”
(4)准备待破解的密码文件;
[root@clr /opt/john-1.8.0/src]# cd ..
[root@clr /opt/john-1.8.0]# ls
doc README run src
[root@clr /opt/john-1.8.0]# cd run/
[root@clr /opt/john-1.8.0/run]# ls
ascii.chr digits.chr john john.conf lm_ascii.chr mailer makechr password.lst relbench unafs unique unshadow
[root@clr /opt/john-1.8.0/run]# cp /etc/shadow ./shadow.txt #将/etc/shadow下的文件复制到当前目录下的shadow.txt文件中
(5)执行暴力破解;
[root@clr /opt/john-1.8.0/run]# ./john shadow.txt #执行暴力破解密码
Loaded 4 password hashes with 4 different salts (crypt, generic crypt(3) [?/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
abc123 (root)
123456 (clr)
123 (cCLR)
123123 (gzy)
4g 0:00:01:31 100% 2/3 0.04391g/s 134.0p/s 137.2c/s 137.2C/s leslie..boston
Use the "--show" option to display all of the cracked passwords reliably
Session completed
password.lst:该文件保存密码字典;
[root@clr /opt/john-1.8.0/run]# vim password.lst #该文件保存密码字典,只有保存在字典里的密码才能够破解出来,对于字典里没有的密码,将无法破解(字典里的文件越全,破解能力越强)
slip
stivers
test2
test3
tula
unix
user1
xanth
!@#$%^&
1701d
@#$%^&
Qwert
allo
dirk
(6)查看已破解出的账户列表;
[root@clr /opt/john-1.8.0/run]# ./john --show shadow.txt #查看破解出来的相关用户和密码
root:abc123:19460:0:99999:7:::
cCLR:123::0:99999:7:::
clr:123456:19460:0:99999:7:::
gzy:123123:19460:0:99999:7:::
4 password hashes cracked, 0 left
john.pot:破解后的密码信息都保存在该文件中;
[root@clr /opt/john-1.8.0/run]# ls
ascii.chr john john.log lm_ascii.chr makechr password.lst shadow.txt unique
digits.chr john.conf john.pot mailer password,lst relbench unafs unshadow
[root@clr /opt/john-1.8.0/run]# cat john.pot
$6$ZGvwnTF/$5Ss8aBWvsKHJ6gV8rIPFs9/9zBCP8iRdLsYXvWJaHrHiV0OF1nRfyaIdWyJzvEr0korljPXvtsCxuGh6wbrzQ/:abc123
$6$F3B.32tO$WKKGH8gCsZJeDlwZ/6NeZdptN.3s8HN6rrfUee8dQyCoC8U/wP2mc5pmFCjrKbqhu96J15Qk45tlSFF0MT4n./:123456
$6$gy7MYQ5UGcLxJrGX$GgqRkJhqVMt2uvInbArGKjqkYdYtw2GJhqA/Y5mHly6eqzQUiIDjw8q/2t9K42l1TOvW0hRI1QoK/R3V3hJUo0:123
$6$rL7V7J7X$7/zj8kk2A8LfT8AwV.lf7cF8xCY5dMxqFN1yikYrQ4fw3wsrDZR5AZe9iSeIddCyddeP2jt134zhTuWRExXme1:123123
./john --wordlist=[指定字典文件的绝对路径] [需要破解的文件名]:使用指定的字典文件进行破解;
[root@clr /opt/john-1.8.0/run]# ./john --wordlist
Option requires a parameter: "--wordlist"
[root@clr /opt/john-1.8.0/run]# ./john --wordlist=./password.lst shadow.txt #指定当前目录下的password.lst文件作为默认字典,破解指定文件shadow.txt
Loaded 4 password hashes with 4 different salts (crypt, generic crypt(3) [?/64])
No password hashes left to crack (see FAQ)
4.网络端口扫描
4.1 nmap命令
netstat -lntp:以数字形式显示TCP处于监听状态的网络连接及端口信息;
[root@clr /etc/yum.repos.d]# netstat -lntp #以数字形式显示TCP处于监听状态的网络连接及端口信息
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name #进程的PID号和进程名
tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 1308/dnsmasq
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1088/sshd
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1086/cupsd
tcp6 0 0 ::1:25 :::* LISTEN 1357/master
tcp6 0 0 ::1:6010 :::* LISTEN 2403/sshd: root@pts
[root@clr /etc/yum.repos.d]# systemctl start httpd #开启httpd服务
[root@clr /etc/yum.repos.d]# netstat -lntp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 1308/dnsmasq
tcp6 0 0 ::1:6010 :::* LISTEN 2403/sshd: root@pts
tcp6 0 0 :::111 :::* LISTEN 590/rpcbind
tcp6 0 0 :::80 :::* LISTEN 3019/httpd #新开启的httpd服务
netstat -antp:以数字形式显示TCP所有状态下的网络连接及端口信息;
[root@clr /etc/yum.repos.d]# netstat -antp #以数字形式显示TCP所有状态下的网络连接及端口信息
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 1308/dnsmasq
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1088/sshd
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1086/cupsd
tcp6 0 0 ::1:6010 :::* LISTEN 2403/sshd: root@pts
tcp6 0 0 :::111 :::* LISTEN 590/rpcbind
tcp6 0 0 :::80 :::* LISTEN 3019/httpd
ss -antp:以数字形式显示TCP所有状态下的网络连接及端口信息;(效果和netstat命令相同,但执行效率比netstat命令更高)
[root@clr /etc/yum.repos.d]# ss -antp #以数字形式显示TCP所有状态下的网络连接及端口信息
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 5 192.168.122.1:53 *:* users:(("dnsmasq",pid=1308,fd=6))
LISTEN 0 128 *:22 *:* users:(("sshd",pid=1088,fd=3))
LISTEN 0 128 127.0.0.1:631 *:* users:(("cupsd",pid=1086,fd=11))
LISTEN 0 100 127.0.0.1:25 *:* users:(("master",pid=1357,fd=13))
[::]:* users:(("rpcbind",pid=590,fd=11))
LISTEN 0 128 [::]:80 [::]:* users:(("httpd",pid=3024,fd=4),("httpd",pid=3023,fd=4),("httpd",pid=3022,fd=4),("httpd",pid=3021,fd=4),("httpd",pid=3020,fd=4),("httpd",pid=3019,fd=4))
查看指定服务端口是否开启的三种方法;
#方法一:通过查看进程信息,过滤指定服务的端口是否开启;
[root@clr /etc/yum.repos.d]# ps aux | grep httpd #过滤指定服务httpd的端口是否开启
root 3019 0.0 0.1 228320 5168 ? Ss 21:40 0:00 /usr/sbin/httpd -DFOREGROUND
apache 3020 0.0 0.0 230404 3124 ? S 21:40 0:00 /usr/sbin/httpd -DFOREGROUND
apache 3024 0.0 0.0 230404 3124 ? S 21:40 0:00 /usr/sbin/httpd -DFOREGROUND
root 3045 0.0 0.0 112824 980 pts/0 S+ 21:42 0:00 grep --color=auto httpd
#方法二:通过指定服务名进行过滤;
[root@clr /etc/yum.repos.d]# netstat -lntp | grep httpd
tcp6 0 0 :::80 :::* LISTEN 3019/httpd
#方法三:通过指定端口号进行过滤;
[root@clr /etc/yum.repos.d]# netstat -lntp | grep :80
tcp6 0 0 :::80 :::* LISTEN 3019/httpd
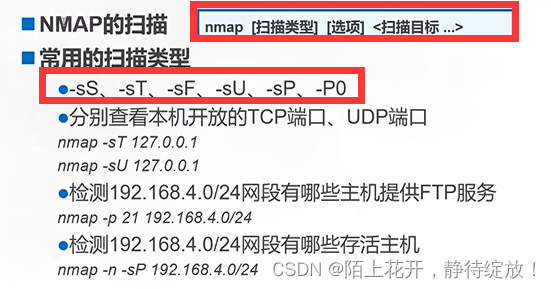
nmap -sT 192.168.80.20:查看指定主机192.168.80.20上开启了那些TCP端口和服务;
[root@clr /etc/yum.repos.d]#nmap -sT 192.168.80.20 #查看指定主机192.168.80.20上开启了那些端口和服务
Starting Nmap 6.40 ( http://nmap.org ) at 2023-04-13 22:02 CST
Nmap scan report for bogon (192.168.80.20)
Host is up (0.0013s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
Nmap done: 1 IP address (1 host up) scanned in 0.17 seconds
Starting Nmap 6.40 ( http://nmap.org ) at 2023-04-13 22:02 CST
Nmap scan report for bogon (192.168.80.20)
Host is up (0.0013s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
nmap -p 80 192.168.80.0/24 :查看指定192.168.80.0网段内有哪些主机开启了80端口;
[root@clr /etc/yum.repos.d]# nmap -p 80 192.168.80.0/24 #查看指定192.168.80.0网段内有哪些主机开启了80端口
Starting Nmap 6.40 ( http://nmap.org ) at 2023-04-13 22:06 CST
Nmap scan report for bogon (192.168.80.1)
Host is up (0.00098s latency).
PORT STATE SERVICE
80/tcp filtered http
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for bogon (192.168.80.2)
Host is up (0.00029s latency).
PORT STATE SERVICE
80/tcp closed http
MAC Address: 00:50:56:FD:CC:46 (VMware)
Nmap scan report for bogon (192.168.80.20)
Host is up (0.00014s latency).
PORT STATE SERVICE
80/tcp open http
Nmap scan report for bogon (192.168.80.151)
Host is up (0.00011s latency).
PORT STATE SERVICE
80/tcp open http
nmap -n -sP 192.168.80.0/24:查看192.168.80.0网段内,有哪些主机存活;
[root@clr /etc/yum.repos.d]# nmap -n -sP 192.168.80.0/24 #查看192.168.80.0网段内,有哪些主机存活
Starting Nmap 6.40 ( http://nmap.org ) at 2023-04-13 22:10 CST
Nmap scan report for 192.168.80.1
Host is up (0.00051s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.80.2
Host is up (0.00044s latency).
MAC Address: 00:50:56:FD:CC:46 (VMware)
Nmap scan report for 192.168.80.30
Host is up (-0.10s latency).
MAC Address: 00:0C:29:E2:4B:FE (VMware)
Nmap scan report for 192.168.80.254
Host is up (-0.10s latency).
MAC Address: 00:50:56:FF:5E:1A (VMware)
Nmap scan report for 192.168.80.20
Host is up.
Nmap scan report for 192.168.80.151
Host is up.
Nmap done: 256 IP addresses (6 hosts up) scanned in 4.73 seconds