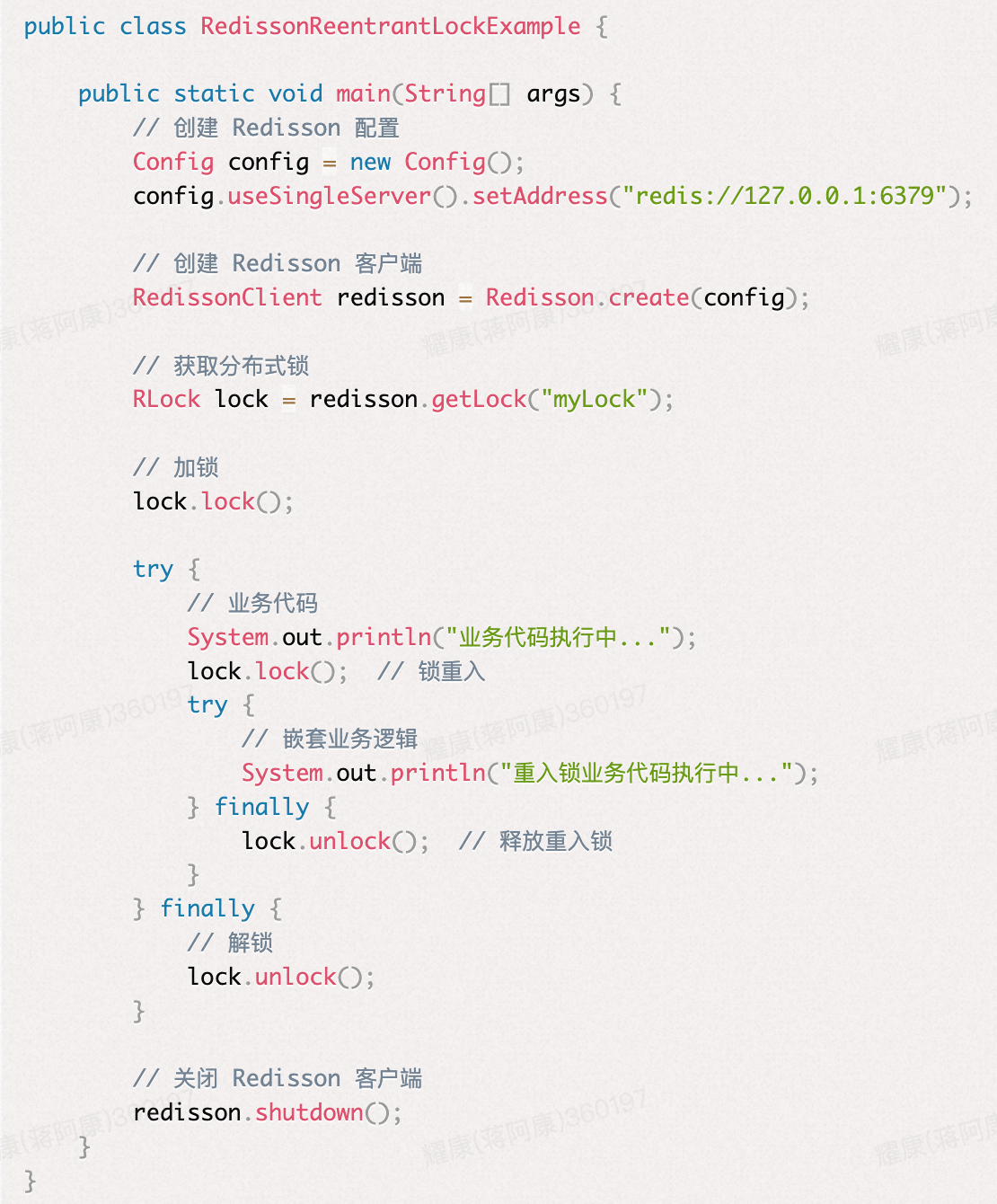
在执行 adb remount 时高版本经常会提示失败

此时就需要对设备的进行解锁操作。记录两个部分,Google解锁和展锐解锁。
目录
一、Google解锁
二、展锐解锁
三、补充跳过按键检测的方案
一、Google解锁
官网介绍的unlock方法如下:锁定/解锁引导加载程序 | Android Open Source Project
简单总结一下需要的步骤如下:
1、进入引导加载程序
adb reboot bootloader
2、解锁引导加载程序(设备处于lock状态,进行unlock)
fastboot flashing unlock3、锁定引导加载程序(设备处于unlock状态,进行lock)
fastboot flashing lock二、展锐解锁
我们使用的是展锐的芯片,根据以上步骤操作会提示未知的命令,如下图:

查阅了相关的 《Android 12.0 Secure Boot使用指南V1.0.pdf》、《Android 14 Secure Boot使用指南V1.0.pdf》 都有介绍详细流程。这里根据自己理解记录下需要的操作。
1、进入引导加载程序
adb reboot bootloader
2、获取当前手机的id
fastboot oem get_identifier_token
3、生成解锁凭证 certificate.bin(ubuntu环境下)
脚本路径为:vendor/sprd/tools/packimage_scripts
秘钥路径为:bsp/tools/secureboot_key/config/rsa4096_vbmeta.pem
vendor/sprd/tools/packimage_scripts$ ./signidentifier_unlockbootloader.sh 上一步获取到的id ../../../../bsp/tools/secureboot_key/config/rsa4096_vbmeta.pem certificate.bin4、PC上执行如下的解锁指令,需要在设备侧按音量下键确认
fastboot flashing unlock_bootloader certificate-b.bin
然后重启设备即可。
5、PC上执行如下的锁定指令
fastboot flashing lock注意:需要使用平台编译生成的 fastboot,编译指令为 make fastboot。生成路径为out/host/windows-x86
三、补充跳过按键检测的方案
bsp/bootloader/lk
diff --git a/app/sprdboot/fastboot.c b/app/sprdboot/fastboot.c
index 7291950a..679bb2b8 100755
--- a/app/sprdboot/fastboot.c
+++ b/app/sprdboot/fastboot.c
@@ -3137,12 +3137,15 @@ void fb_cmd_flashing(const char *arg, void *data, uint64_t sz)
fastboot_okay("Bootloader has been locked!\n");
return;
}
-
+ // lichang 忽略按键选项,直接lock
+ /*@start*/
lcd_printf("\n Warning: lock device may erase user data.\n");
+ lcd_printf("\n Ignore key.\n");
+ /*
lcd_printf(" Press volume down button to confirm that.\n");
lcd_printf(" Press volume up button to cancel.\n");
while(!butt_check) {
- /* continue check till button pressed */
+ *//* continue check till button pressed *//*
key_code = wait_for_keypress();
if (key_code == KEY_VOLUMEDOWN) {
butt_check = true;
@@ -3151,7 +3154,8 @@ void fb_cmd_flashing(const char *arg, void *data, uint64_t sz)
fastboot_okay("Info:user cancel lock bootloader! ");
return;
}
- }
+ }*/
+ /*@end*/
lcd_printf(" Begin to erase user data...\n");
if (0 != common_raw_erase("userdata", 0, 0)) {
debugf("erase userdata failed\n");
@@ -3191,11 +3195,15 @@ void fb_cmd_flashing(const char *arg, void *data, uint64_t sz)
return;
}
+ // lichang 忽略按键选项,直接lock
+ /*@start*/
lcd_printf("\n Warning: lock device may erase user data.\n");
+ lcd_printf("\n Ignore key.\n");
+ /*
lcd_printf(" Press volume down button to confirm that.\n");
lcd_printf(" Press volume up button to cancel.\n");
while(!butt_check) {
- /* continue check till button pressed */
+ *//* continue check till button pressed *//*
key_code = wait_for_keypress();
if (key_code == KEY_VOLUMEDOWN) {
butt_check = true;
@@ -3204,7 +3212,8 @@ void fb_cmd_flashing(const char *arg, void *data, uint64_t sz)
fastboot_okay("Info:user cancel lock bootloader! ");
return;
}
- }
+ }*/
+ /*@end*/
lcd_printf(" Begin to erase user data...\n");
if (0 != common_raw_erase("userdata", 0, 0)) {
debugf("erase userdata failed\n");
@@ -3259,10 +3268,14 @@ void fb_cmd_flashing(const char *arg, void *data, uint64_t sz)
//memset(product_sn_signature, 0, sizeof(product_sn_signature));
lcd_printf("\n Warning: Unlock device may erase user data.\n");
+ //lichang 忽略按键,直接unlock
+ /*@start*/
+ /*
+ lcd_printf(" Ignore key.\n");
lcd_printf(" Press volume down button to confirm that.\n");
lcd_printf(" Press volume up button to cancel.\n");
while(!butt_check) {
- /* continue check till button pressed */
+ *//* continue check till button pressed *//*
key_code = wait_for_keypress();
if (key_code == KEY_VOLUMEDOWN) {
butt_check = true;
@@ -3271,7 +3284,8 @@ void fb_cmd_flashing(const char *arg, void *data, uint64_t sz)
fastboot_okay("Info:user cancel unlock bootloader! ");
return;
}
- }
+ }*/
+ /*@end*/
lcd_printf(" Begin to erase user data...\n");
if (0 != common_raw_erase("userdata", 0, 0)) {
debugf("erase userdata failed\n");