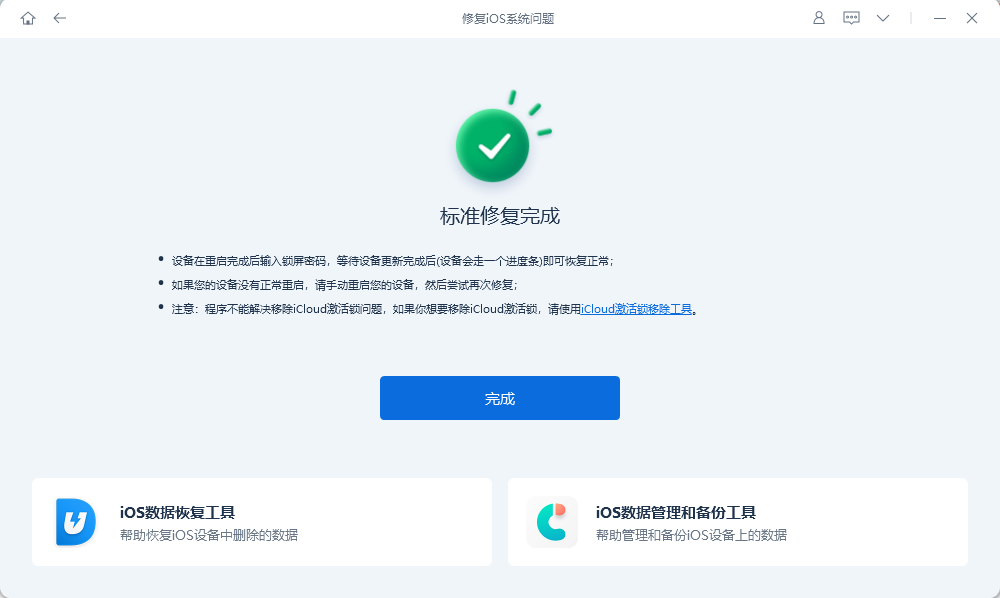
由于之前使用frida已经是2年前了,后来一直没有研究两年以后
首先手机得root才可以,
我使用的是一加9pro, root方法参考一加全能盒子、一加全能工具箱官方网站——大侠阿木 (daxiaamu.com)编辑https://optool.daxiaamu.com/index.php
由于之前使用的是frida 15.1.1在android14上一运行,手机就重启动
所以更新一下,frida到16.1.11
Releases · frida/frida · GitHubClone this repo to build Frida. Contribute to frida/frida development by creating an account on GitHub.![]() https://github.com/frida/frida/releases?page=1
https://github.com/frida/frida/releases?page=1 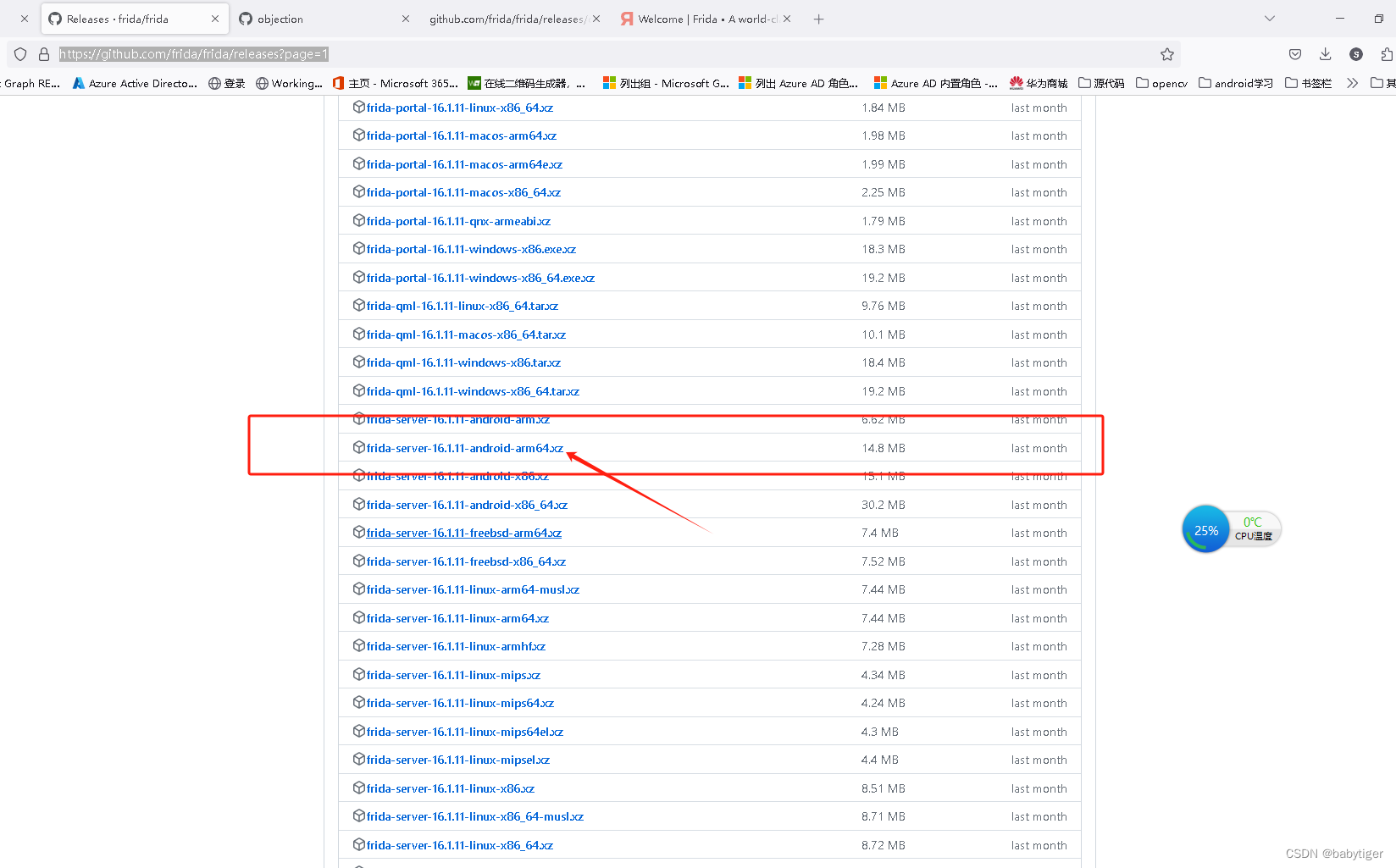
下载后,pc上执行
adb push /data/local/tmp frida-server-16.1.11-android-arm64
然后手机(root后)上执行
chmod 777 /data/local/tmp frida-server-16.1.11-android-arm64
然后在pc上安装调试运行环境,PC上已经有python 3.7,(anaconda)
pip install frida-tools
pip install --upgrade typing_extensions
frida · PyPIDynamic instrumentation toolkit for developers, reverse-engineers, and security researchers![]() https://pypi.org/project/frida/#files
https://pypi.org/project/frida/#files
pip install frida-16.1.11-cp37-abi3-win_amd64.whl
调用代码
// hook_showlog.js
function byteArrayToHexString(byteArray) {
return Array.from(byteArray, byte => ('0' + (byte & 0xFF).toString(16)).slice(-2)).join('');
}
function byteArrayToString(buffer, offset, byteCount) {
var byteArray = Java.array('byte', buffer);
var strContent = "";
for (var i = offset; i < offset + byteCount; i++) {
strContent += String.fromCharCode(byteArray[i]);
}
return strContent;
}
function printStackTrace() {
var Thread = Java.use("java.lang.Thread");
var currentThread = Thread.currentThread();
var stackTrace = currentThread.getStackTrace();
console.log("Current stack trace:");
for (var i = 0; i < stackTrace.length; i++) {
console.log(stackTrace[i].toString());
}
console.log("*************************\n");
console.log("");
console.log("");
}
function hookLog_all() {
var Log = Java.use("android.util.Log");
var pClass = Java.use("com.oplus.backuprestore.common.utils.p");
//Get all methods in pClass
var methods = pClass.class.getDeclaredMethods();
for (var i = 0; i < methods.length; i++) {
var method = methods[i];
// Skip synthetic and bridge methods
if (!method.isSynthetic() && !method.isBridge()) {
// Create hooks for each method
var methodName = method.getName();
var hookMethod = pClass[methodName];
hookMethod.implementation = function() {
var args = [].slice.call(arguments);
console.log(methodName + " arguments:", args);
var result = this[methodName].apply(this, arguments);
return result;
};
}
}
}
function hookBundle() {
// 导入Java类
var Bundle = Java.use("android.os.Bundle");
// 钩取Bundle类的toString()函数
Bundle.toString.implementation = function() {
// 打印堆栈信息
// 调用原始的toString()函数
// 调用原始的toString()函数并获取结果
var result = this.toString();
// 打印结果
console.log("BundletoString() result:", result);
console.log("Bundle.toString() called from:");
var stackTrace = Java.use("android.util.Log").getStackTraceString(Java.use("java.lang.Exception").$new());
console.log(stackTrace);
// 返回结果
return result;
};
}
function hookBase64() {
var base64Class = Java.use('android.util.Base64');
// Intercept the decode method with String parameter
var decodeWithString = base64Class.decode.overload('java.lang.String', 'int');
decodeWithString.implementation = function (str, flags) {
if (str.length < 25600) {
console.log('base64 decode(String) called with str length: ' + str.length + ' str: ' + str + ' flags: ' + flags);
console.log('');
} else {
console.log('decode(String) called with str length: ' + str.length + ', flags: ' + flags);
}
// Call the original method
var result = this.decode(str, flags);
// Convert the result to string
var resultString = String.fromCharCode.apply(null, result);
if (resultString.length < 12