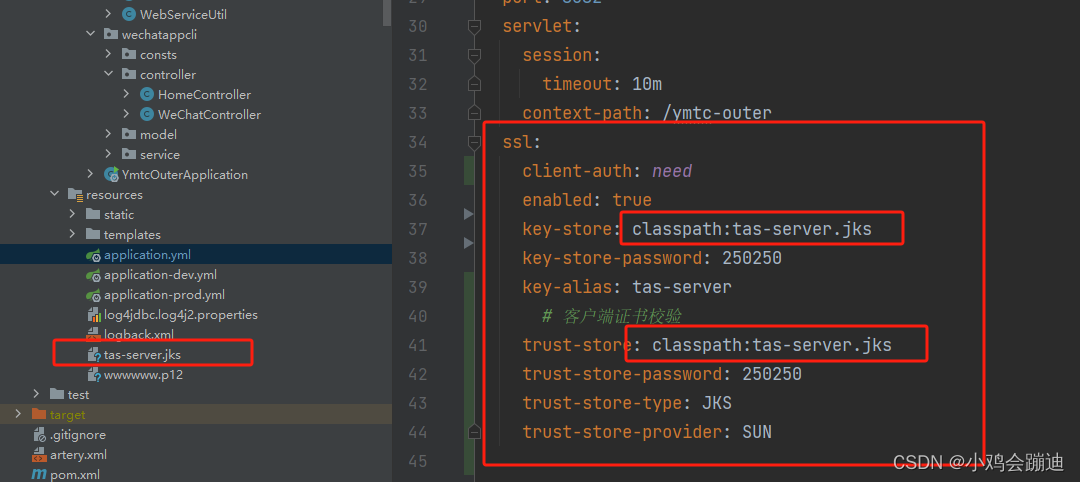
服务器:xxx.xxx.xxx.56
客户端器:xxx.xxx.xxx.94
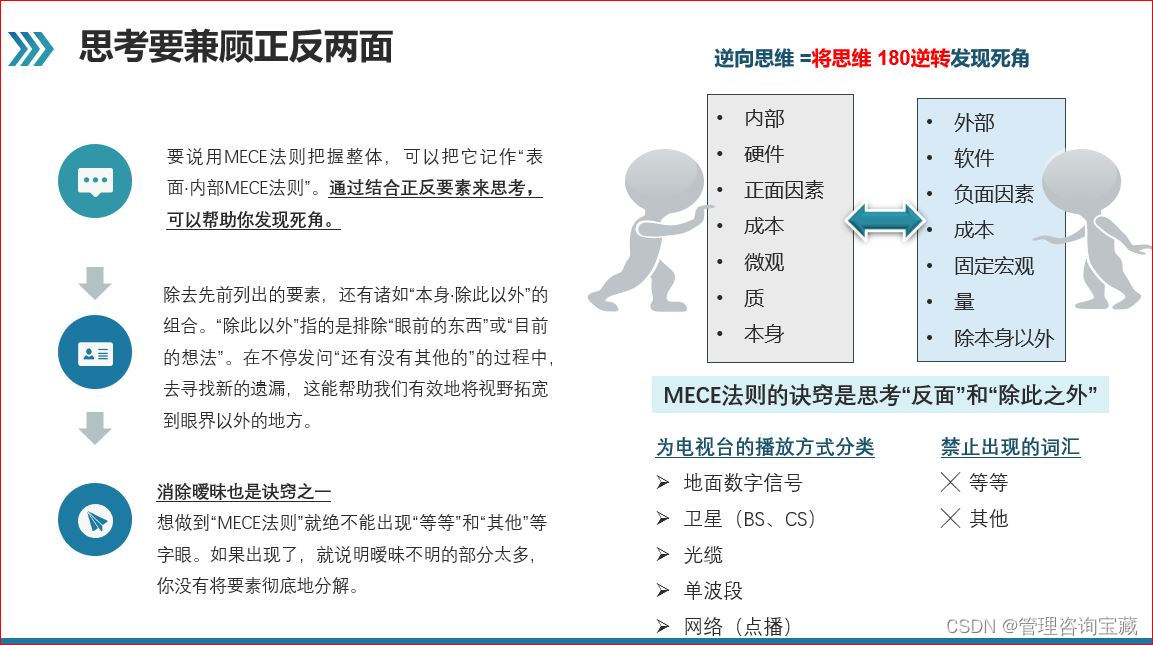
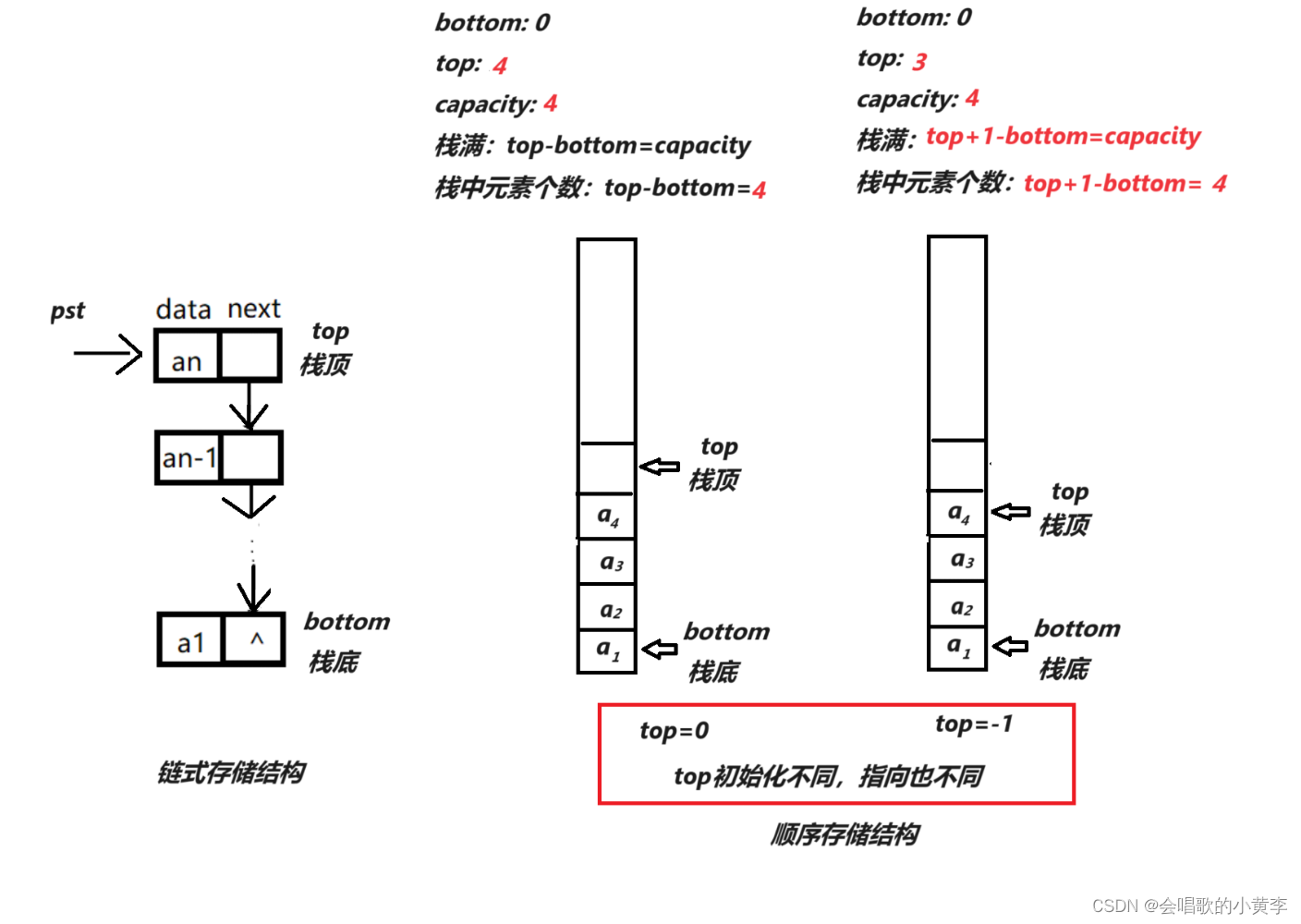
##生成服务器证书和密钥容器
keytool -genkey -alias tas-server -keypass 250250 -keyalg RSA -keysize 2048 -validity 3650 -keystore D:\https证书\tas-server.jks -storepass 250250 -dname "CN=xxx.xxx.xxx.94,OU=Test,O=Test,L=BeiJing,ST=BeiJing,C=CN"
##生成客户端证书和密钥容器
keytool -genkey -alias tas-client -keypass 250250 -keyalg RSA -keysize 2048 -storetype PKCS12 -keypass 250250 -storepass 250250 -keystore D:\https证书\tas-client.jks -dname "CN=xxx.xxx.xxx.94,OU=Test,O=Test,L=BeiJing,ST=BeiJing,C=CN" -ext "SAN=IP:xxx.xxx.xxx.94,IP:xxx.xxx.xxx.56,DNS:ymtc.xx"
##希望56和zsd.com也可以使用这个证书
##服务器信任客户端证书
##由于keytoo1不能直接将PKCS12格式的证书库导入,必须先把客户端证书导出为一个单独的CER文件,使用如下命令:
keytool -export -alias tas-client -file D:\https证书\tas-client.cer -keystore D:\https证书\tas-client.jks -storepass 250250 -keypass 250250
##将该文件导入到服务器的证书库,添加为一个信任证书:
keytool -import -alias tas-client -file D:\https证书\tas-client.cer -keystore D:\https证书\tas-server.jks -storepass 250250 -keypass 250250 -noprompt
##完成之后通过11st命令查看服务器的证书库,可以看到两个证书,一个是服务器证书,一个是受信任的客户端证书:
keytool -list -v -keystore D:\https证书\tas-server.jks -storepass 250250
keytool -importkeystore -srckeystore D:\https证书\tas-client.jks -destkeystore D:\https证书\tas-client.p12 -srcstoretype JKS -deststoretype PKCS12 -srcstorepass 250250 -deststorepass 250250 -srckeypass 250250 -destkeypass 250250 -srcalias tas-client -destalias tas-client -noprompt
pkcs12 -nokeys -in D:\https证书\tas-client.p12 -out D:\https证书\tas-client.pem -password pass:250250
pkcs12 -nocerts -nodes -in D:\https证书\tas-client.p12 -out D:\https证书\tas-client.key -password pass:250250
ng:
1.nginx.conf修改:
worker_processes auto;
error_log logs/error.log;
pid logs/nginx.pid;
events {
worker_connections 1024;
}
http {
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log logs/access.log main;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
server_names_hash_bucket_size 128;
client_header_buffer_size 32k;
large_client_header_buffers 4 32k;
client_max_body_size 500m;
client_body_buffer_size 512k;
# 代理的相关参数设置
proxy_connect_timeout 5;
proxy_read_timeout 60;
proxy_send_timeout 5;
proxy_buffer_size 16k;
proxy_buffers 4 64k;
proxy_busy_buffers_size 128k;
proxy_temp_file_write_size 128k;
# 启用gzip压缩,提高用户访问速度
gzip on;
gzip_min_length 1k;
gzip_buffers 4 16k;
gzip_http_version 1.1;
gzip_comp_level 2;
gzip_types text/plain application/css application/javascript application/x-javascript text/css application/xml text/javascript application/x-httpd-php image/jpeg image/gif image/png;
gzip_vary on;
include mime.types;
default_type application/octet-stream;
include conf.d/*.conf;
}
2.创建文件夹 .key 和pem扔里
新建域名.conf

域名.conf配置:
server {
# 可在监听端口后边 添加 ipv6only=off 参数来禁用 ipv6 支持 从而避免因为IPV6地址设置有误导致 nginx 服务未能正常启动
listen 443 ssl default;
#根据HOST匹配虚拟主机。目前同一个端口只有一个虚
server_name ymtc.xx;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2; #SSL协议
ssl_certificate ssl/tas-client.pem;
ssl_certificate_key ssl/tas-client.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4; #加密算法
ssl_prefer_server_ciphers on;
if ($scheme = http){
return 301 https://$server_name$request_uri;
}
location / {
#需要代理的地址
proxy_pass ip:端口;
#使用upstream才会用到
#proxy_set_header Host $host:$server_port;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header REMOTE-HOST $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_redirect off;
proxy_connect_timeout 300;
proxy_read_timeout 300;
proxy_send_timeout 300;
root html;
index index.html index.htm;
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root html;
}
}3.spring配置