文章目录
- 准备部署的yml文件
- Harbor私服配置
- 测试使用效果
- Jenkins远程调用
- 参考文章
准备部署的yml文件
apiVersion: apps/v1
kind: Deployment
metadata:
namespace: test
name: pipeline
labels:
app: pipeline
spec:
replicas: 2
selector:
matchLabels:
app: pipeline
template:
metadata:
labels:
app: pipeline
spec:
containers:
- name: pipeline
image: 192.168.56.112:80/repository/pipeline-test:1.0.0
imagePullPolicy: Always
ports:
- containerPort: 8080
---
apiVersion: v1
kind: Service
metadata:
namespace: test
labels:
app: pipeline
name: pipeline
spec:
selector:
app: pipeline
ports:
- port: 8081
targetPort: 8080
type: NodePort
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
namespace: test
name: pipeline
spec:
ingressClassName: ingress
rules:
- host: batman.pipeline.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: pipeline
port:
number: 8081
Harbor私服配置
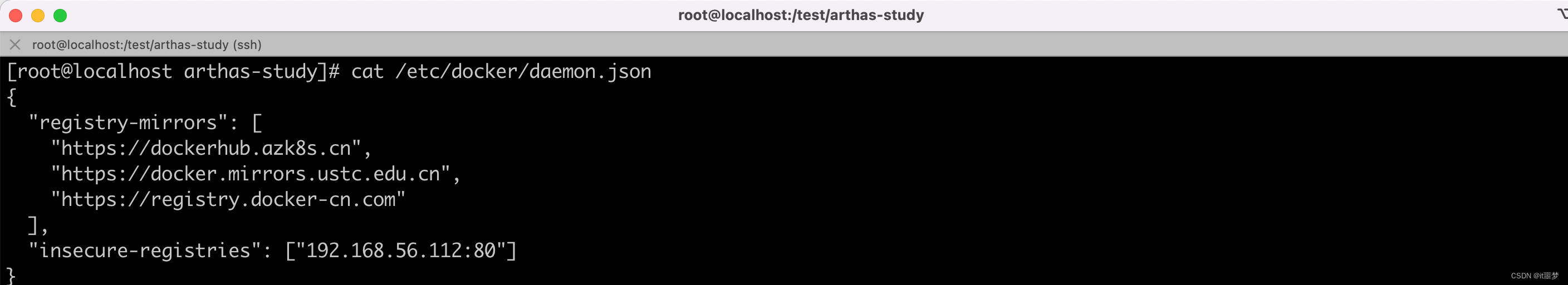
在尝试用kubernetes的yml文件启动pipeline服务时,会出现Kubernetes无法拉取镜像的问题,这里需要在kubernetes所在的Linux中配置Harbor服务信息,并且保证Kubernetes可以拉取Harbor上的镜像
- 设置Master和Worker的私服地址信息
{
"registry-mirrors": [
"https://dockerhub.azk8s.cn",
"https://docker.mirrors.ustc.edu.cn",
"https://registry.docker-cn.com"
],
"insecure-registries": ["192.168.56.112:80"]
}
- 设置免密登陆k8s节点
k8s 111上执行
mkdir /root/.ssh
然后再 jenkins 112中执行如下操作
1、采用dsa加密生成密钥,也可以采用rsa加密
ssh-keygen -t dsa
然后一路回车。
上面将密钥生成在默认路径/root/.ssh下,然后将其内容输出到/root/.ssh/authorized_keys中
cat /root/.ssh/id_dsa.pub >> /root/.ssh/authorized_keys
然后将公钥复制到其他两个需要免密钥登录的k8s 111中
scp /root/.ssh/authorized_keys 192.168.56.111:/root/.ssh/
ssh 192.168.56.111
- 解决拉取私有镜像的权限问题
kubectl create secret docker-registry myharbor \
--docker-server=192.168.56.112:80 \
--docker-username=admin \
--docker-password=Harbor12345 \
--docker-email=943104990@qq.com \
-n test
- pod spec 配置imagePullSecrets
spec:
containers:
- name: pipeline
image: 192.168.56.112:80/repository/pipeline-test:1.0.0
imagePullPolicy: Always
ports:
- containerPort: 8080
imagePullSecrets:
- name: myharbor
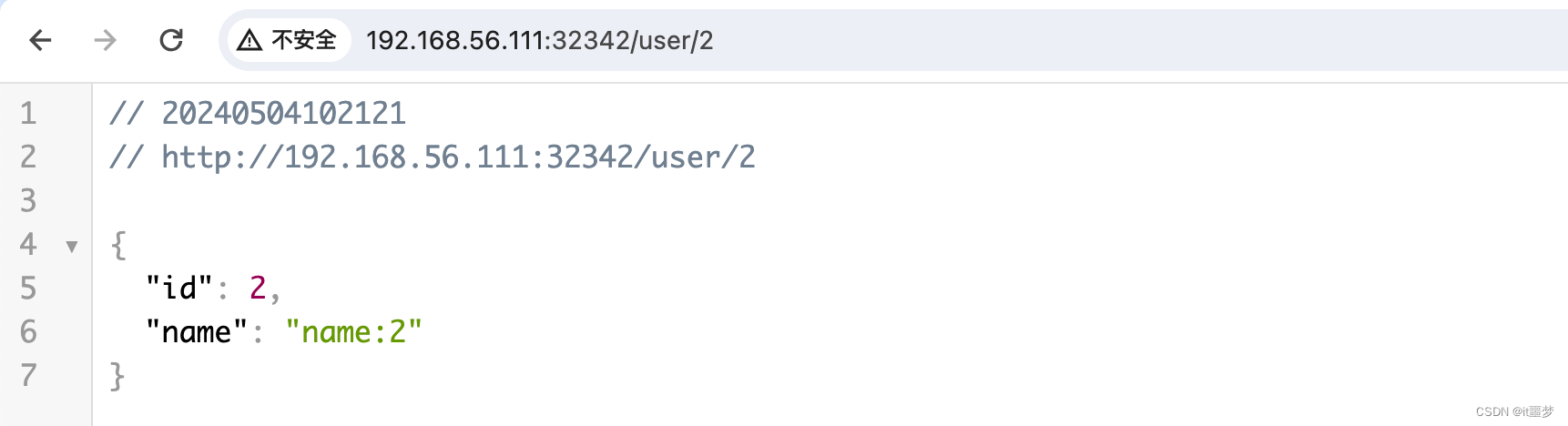
测试使用效果
kubectl apply -f pipeline.yml
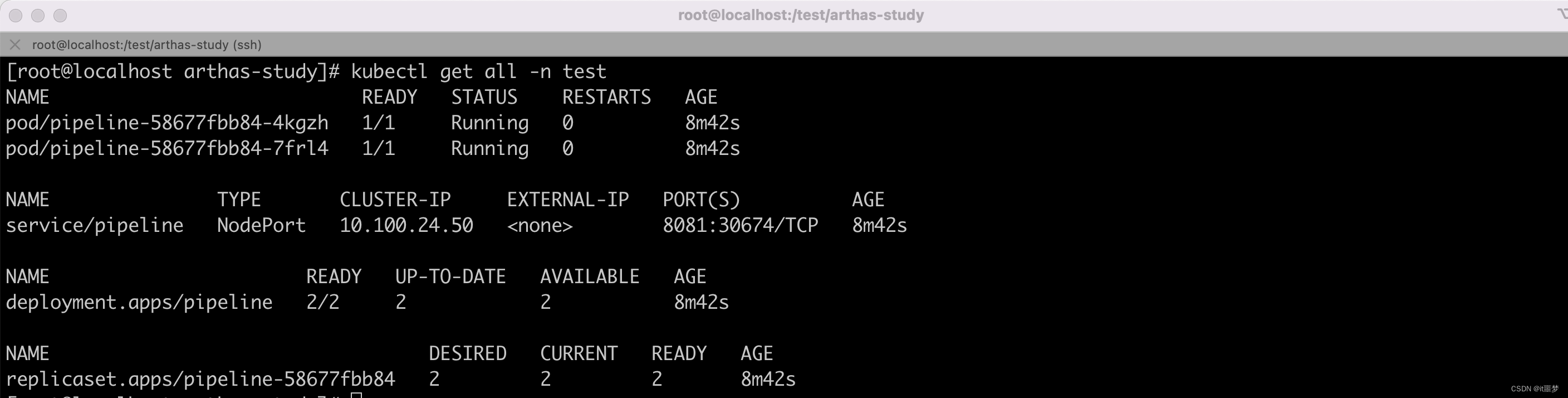
访问 http://192.168.56.111:30674/user/2

Jenkins远程调用
-
将pipeline.yml配置到Gitlab中
-
配置Jenkins的目标服务器,可以将yml文件传输到K8s的Master上
-
设置执行kubectl的脚本到Jenkinsfile
apiVersion: apps/v1
kind: Deployment
metadata:
namespace: test
name: pipeline
labels:
app: pipeline
spec:
replicas: 2
selector:
matchLabels:
app: pipeline
template:
metadata:
labels:
app: pipeline
spec:
containers:
- name: pipeline
image: 192.168.56.112:80/repository/pipeline-test:1.0.0
imagePullPolicy: Always
ports:
- containerPort: 8080
imagePullSecrets:
- name: myharbor
---
apiVersion: v1
kind: Service
metadata:
namespace: test
labels:
app: pipeline
name: pipeline
spec:
selector:
app: pipeline
ports:
- port: 8081
targetPort: 8080
type: NodePort
pipeline {
agent any
environment{
harborHost = '192.168.56.112:80'
harborRepo = 'repository'
harborUser = 'admin'
harborPasswd = 'Harbor12345'
port = 8080
host_port = 8888
}
stages {
stage('拉取Git代码') {
steps {
checkout scmGit(branches: [[name: '${tag}']], extensions: [], userRemoteConfigs: [[credentialsId: 'gitee', url: 'https://gitee.com/qfxcoffee/shield.git']])
}
}
stage('构建代码') {
steps {
sh 'cd arthas-study && /var/jenkins_home/maven/bin/mvn clean package -DskipTests'
}
}
stage('制作自定义镜像并发布Harbor') {
steps {
sh '''cd arthas-study/docker
mv ../target/arthas-study.jar ./arthas-study.jar
docker build -t ${JOB_NAME}:${tag} ./'''
sh '''docker login -u ${harborUser} -p ${harborPasswd} ${harborHost}
docker tag ${JOB_NAME}:${tag} ${harborHost}/${harborRepo}/${JOB_NAME}:${tag}
docker push ${harborHost}/${harborRepo}/${JOB_NAME}:${tag}'''
}
}
// stage('目标服务器拉取镜像并运行') {
// steps {
// sshPublisher(publishers: [sshPublisherDesc(configName: 'testEnv', transfers: [sshTransfer(cleanRemote: false, excludes: '', execCommand: "/usr/bin/deploy.sh $harborHost $harborRepo $JOB_NAME $tag $port $host_port", execTimeout: 120000, flatten: false, makeEmptyDirs: false, noDefaultExcludes: false, patternSeparator: '[, ]+', remoteDirectory: '', remoteDirectorySDF: false, removePrefix: '', sourceFiles: '')], usePromotionTimestamp: false, useWorkspaceInPromotion: false, verbose: false)])
// }
// }
stage('将yml文件传到k8s-master上') {
steps {
sshPublisher(publishers: [sshPublisherDesc(configName: 'k8s', transfers: [sshTransfer(cleanRemote: false, excludes: '', execCommand: '', execTimeout: 120000, flatten: false, makeEmptyDirs: false, noDefaultExcludes: false, patternSeparator: '[, ]+', remoteDirectory: '', remoteDirectorySDF: false, removePrefix: '', sourceFiles: 'arthas-study/pipeline.yml')], usePromotionTimestamp: false, useWorkspaceInPromotion: false, verbose: false)])
}
}
stage('远程执行k8s-master的kubectl命令'){
steps {
// sh 'ssh root@192.168.56.111 kubectl apply -f /test/arthas-study/pipeline.yml'
sshPublisher(publishers: [sshPublisherDesc(configName: 'k8s', transfers: [sshTransfer(cleanRemote: false, excludes: '', execCommand: "kubectl apply -f /test/arthas-study/pipeline.yml", execTimeout: 120000, flatten: false, makeEmptyDirs: false, noDefaultExcludes: false, patternSeparator: '[, ]+', remoteDirectory: '', remoteDirectorySDF: false, removePrefix: '', sourceFiles: '')], usePromotionTimestamp: false, useWorkspaceInPromotion: false, verbose: false)])
}
}
}
}
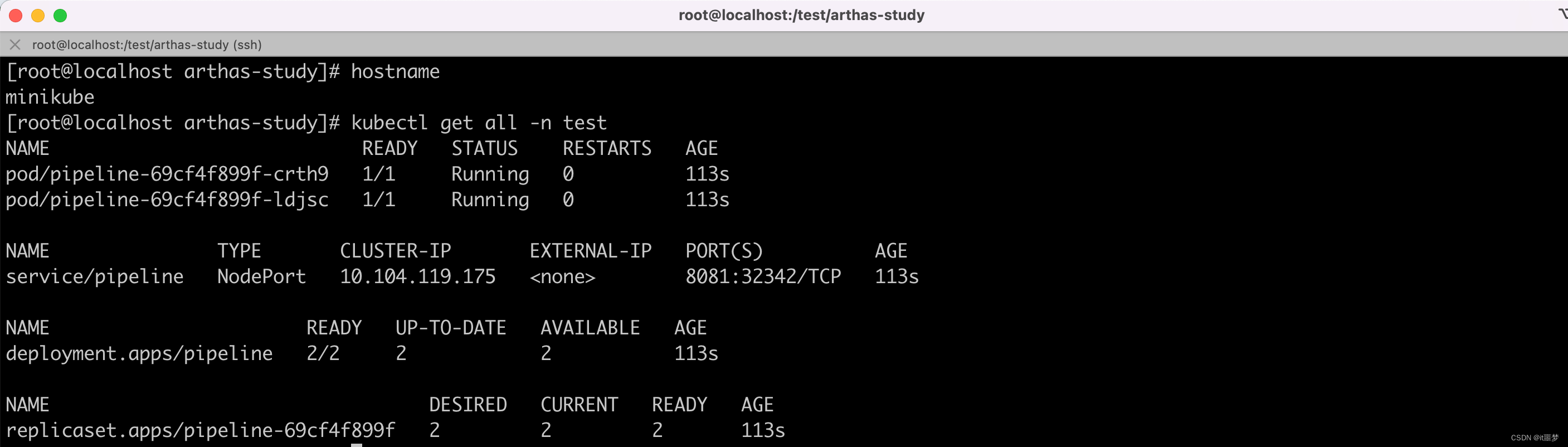
- 查看效果
参考文章
微服务架构学习(二)之CentOS安装minikube