文章目录
Misc
sign in
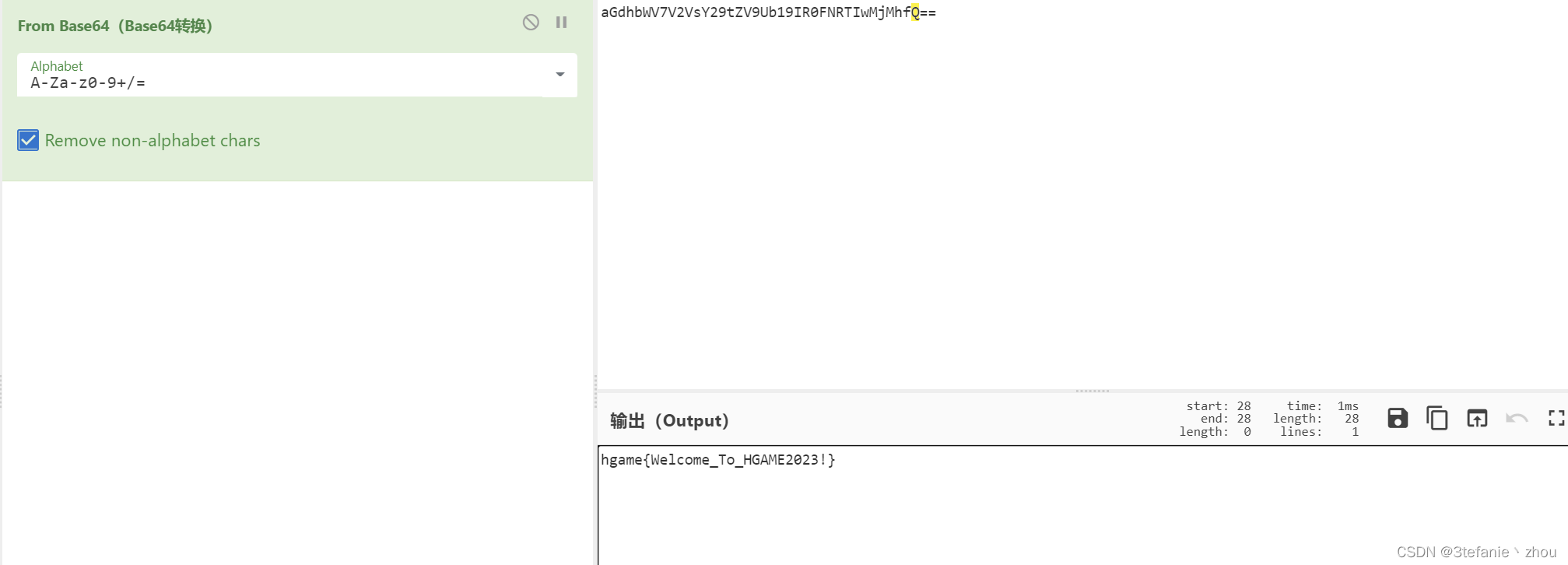
签到题,base64解密即可得到flag
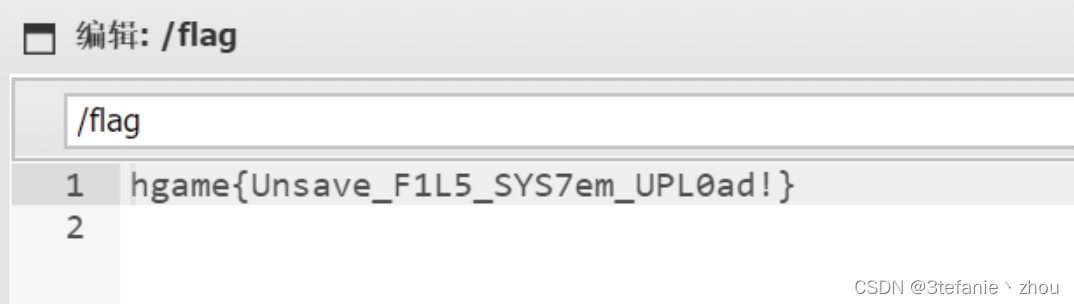
e99p1ant_want_girlfriend
修改图片高度

神秘的海报
查看lsb得到前有一部分flag
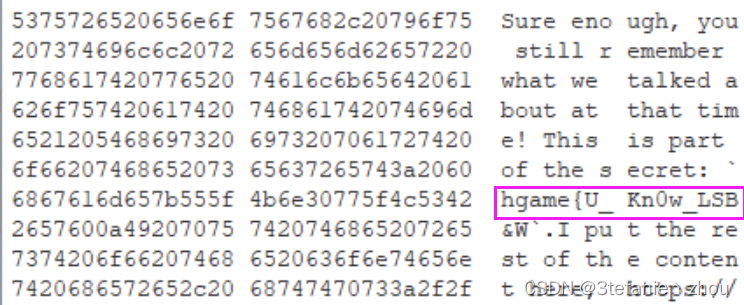
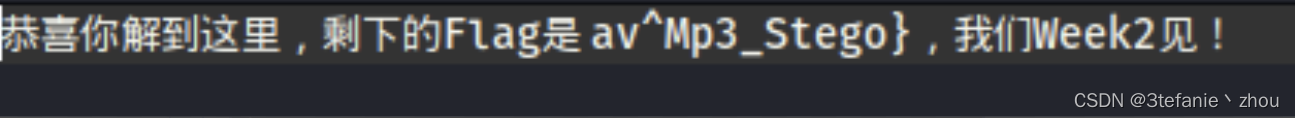
然后steghide 密码123456 得到剩下一部分flag
Where am I
wireshark导出http对象,然后用010删除多余的hex,得到一个rar文件。接下来是rar伪加密,修改rar的第24个字节为00即可正常解压
查看图片信息得到GPS信息
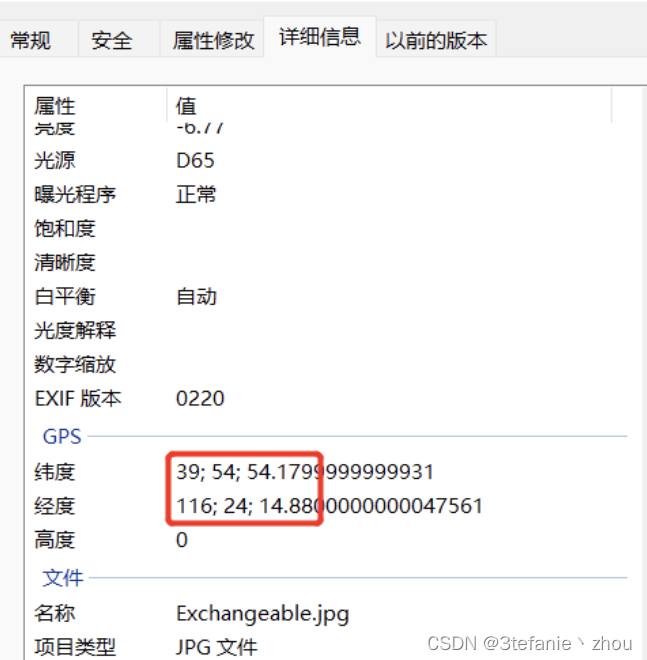
根据题目要求精确到小数点后两位,54.179四舍五入变成54.18
得到flag
hgame{116_24_1488_E_39_54_5418_N}
Web
Classic Childhood Game
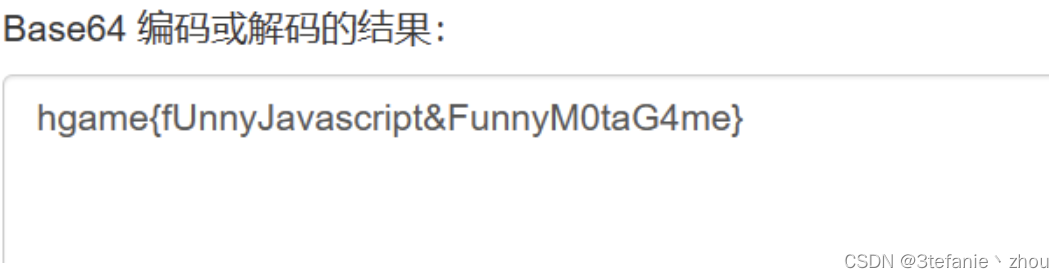
游戏类题目,直接查看js代码,发现一串可疑16进制
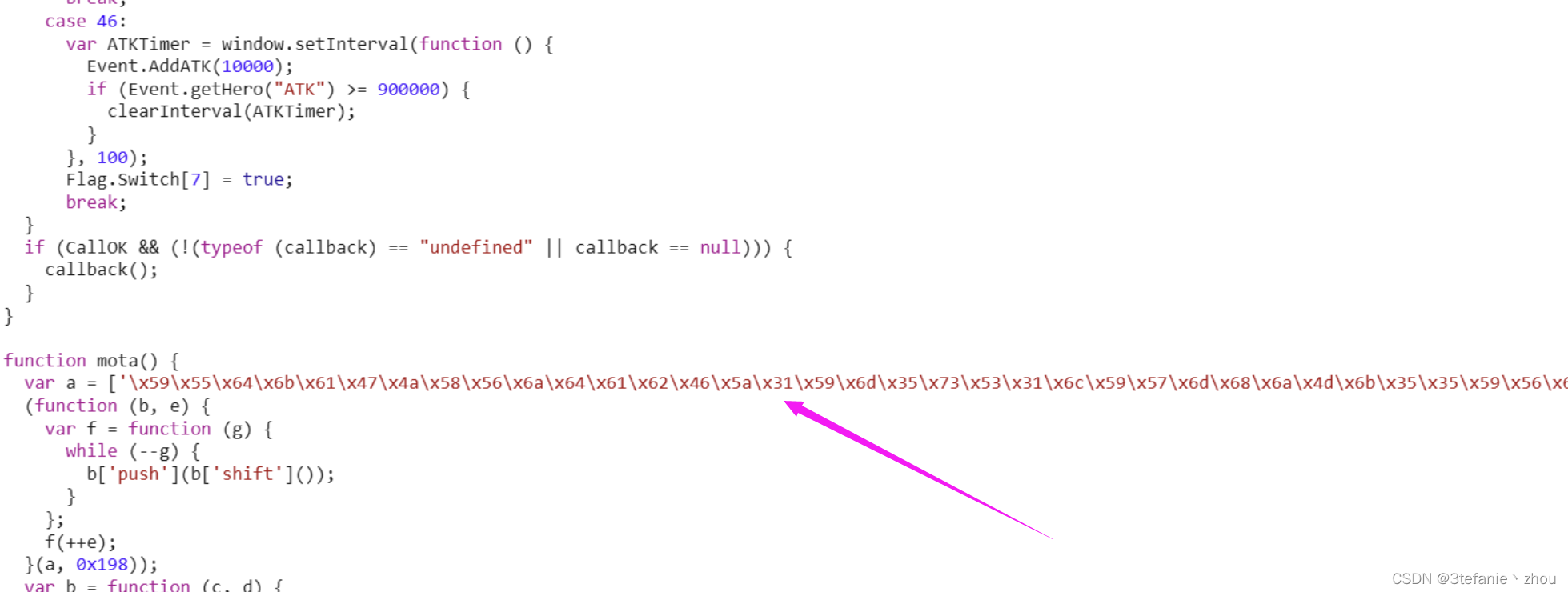
然后16进制转字符串,再连续两次base64解密即可得到flag
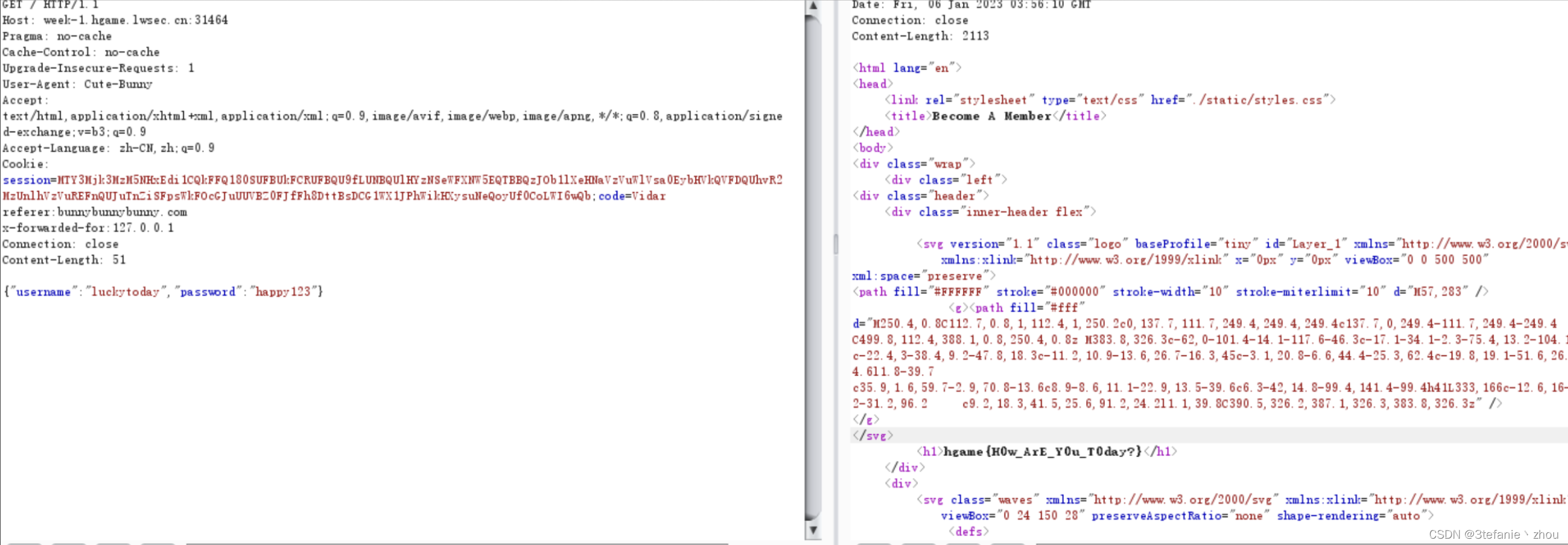
Become A Member
根据题目给的信息依次
修改UA为Cute-Bunny
添加Cookie: code=Vidar
添加Referer: bunnybunnybunny.com
添加X-Forwarded-For: 127.0.0.1
username:luckytoday passsword:happy123(请以json请求方式登陆)
然后发送请求即可得到flag
PS:提交json数据的时候以get方式提交
Guess Who I Am
ctrl u大法发现hint
https://github.com/Potat0000/Vidar-Website/blob/master/src/scripts/config/member.js
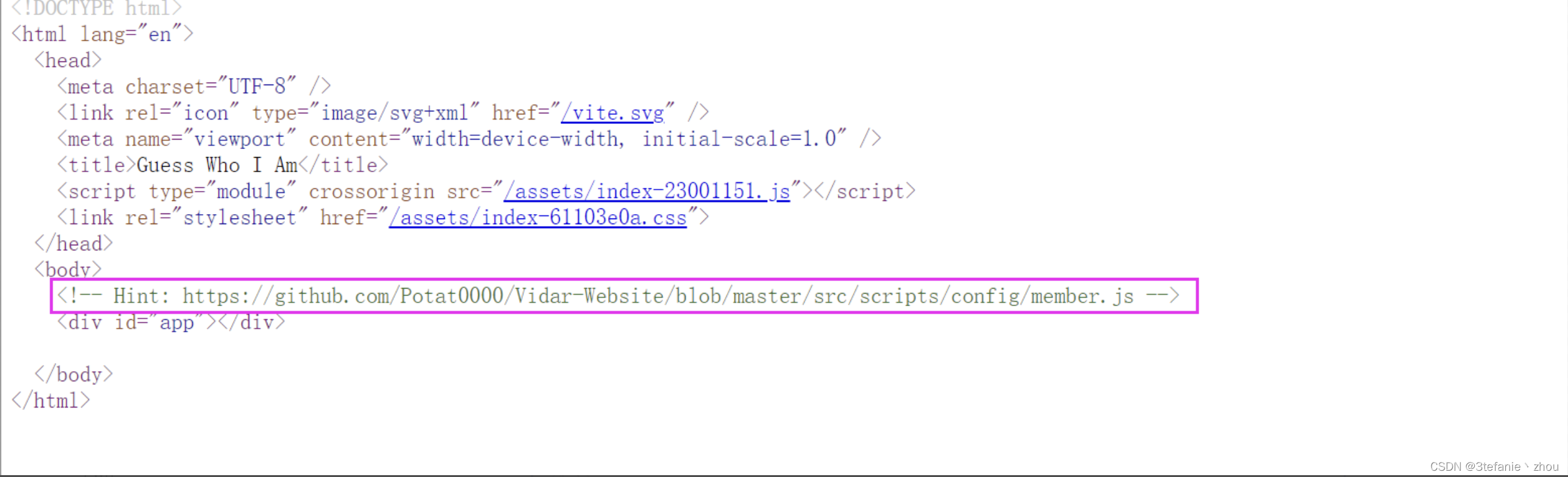
访问站点得到其战队成员信息
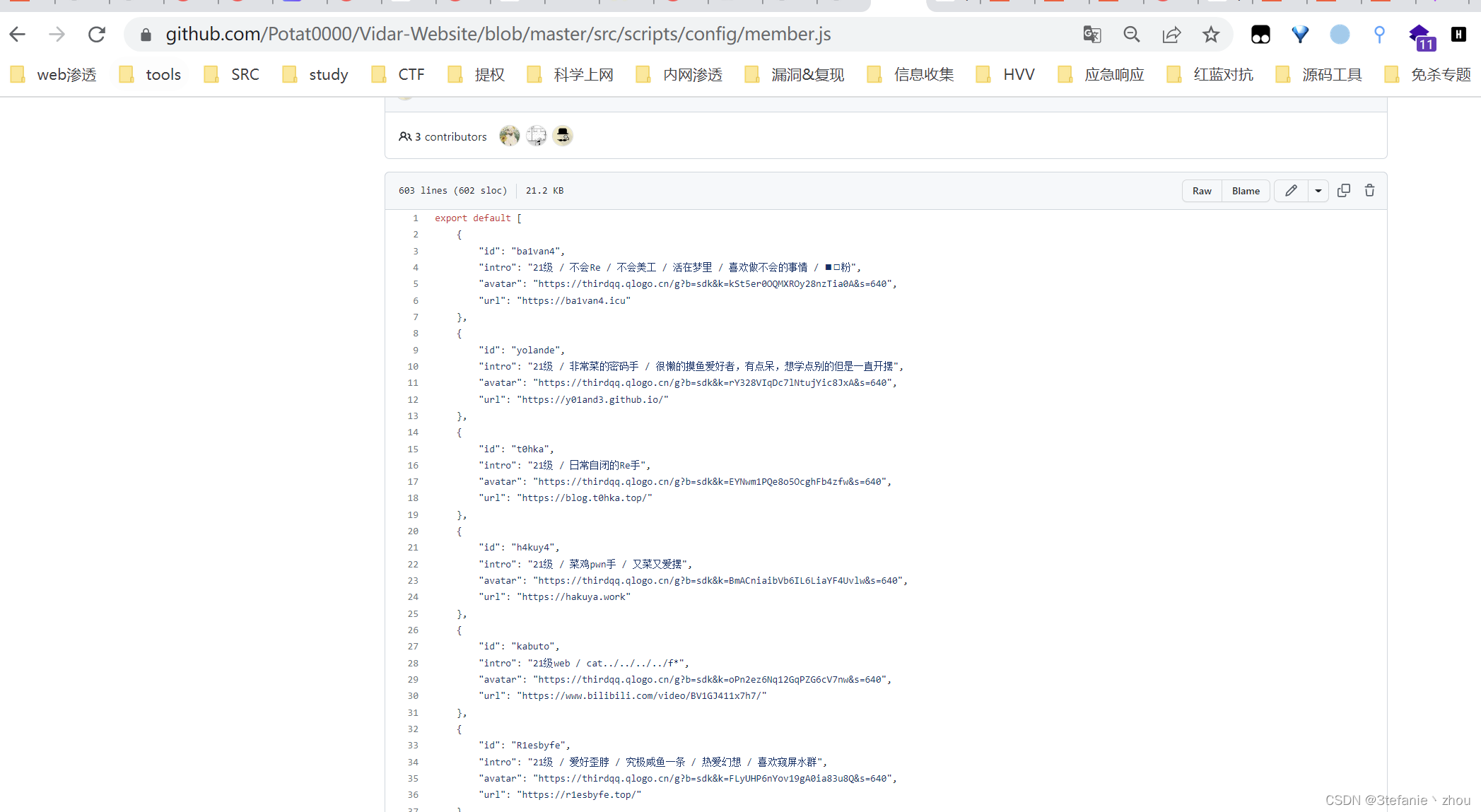
根据题目信息得知,是根据 intro信息找到id信息然后提交,在burp抓包发现三个api
api/getScore
api/getQuestion
api/verifyAnswer
分别用来获取分数、获取intro信息、提交答案,三次请求作为一次完整的过程,且session相同
接下来就是循环一百次获取分数、获取intro信息、根据intro遍历得到id然后提交答案过程
脚本如下:
import requests
answer = [战队成员信息]
s = requests.session()
for i in range(200):
getscore = "http://week-1.hgame.lwsec.cn:32703/api/getScore"
getquestion = 'http://week-1.hgame.lwsec.cn:32703/api/getQuestion'
verifyanswer = "http://week-1.hgame.lwsec.cn:32703/api/verifyAnswer"
r1 = s.get(getscore)
if "hgame" in r1.text:
print(r1.json()["message"])
break
else:
r2 = s.get(getquestion)
data1 = r2.json()
find_id=data1["message"]
for j in answer:
if find_id in j.values():
id = j["id"]
break
data = {"id":id}
r3 = s.post(verifyanswer,data=data)
if "Correct answer!" in r3.text:
print(f"第{i+1}次正确")
Show Me Your Beauty
文件上传大小写绕过
然后蚁🗡连接或者web页面执行命令即可得到flag
Crypto
RSA
直接分解n得到p,q。然后rsa普通解密
import gmpy2
from Crypto.Util.number import *
c = 110674792674017748243232351185896019660434718342001686906527789876264976328686134101972125493938434992787002915562500475480693297360867681000092725583284616353543422388489208114545007138606543678040798651836027433383282177081034151589935024292017207209056829250152219183518400364871109559825679273502274955582
n = 135127138348299757374196447062640858416920350098320099993115949719051354213545596643216739555453946196078110834726375475981791223069451364024181952818056802089567064926510294124594174478123216516600368334763849206942942824711531334239106807454086389211139153023662266125937481669520771879355089997671125020789
p = 11239134987804993586763559028187245057652550219515201768644770733869088185320740938450178816138394844329723311433549899499795775655921261664087997097294813
q = 12022912661420941592569751731802639375088427463430162252113082619617837010913002515450223656942836378041122163833359097910935638423464006252814266959128953
e = 65537
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
m = pow(c,d,n)
flag = long_to_bytes(m)
print(flag)
flag:
hgame{factordb.com_is_strong!}
Be Stream
题目:
from flag import flag
assert type(flag) == bytes
key = [int.from_bytes(b"Be water", 'big'), int.from_bytes(b"my friend", 'big')]
def stream(i):
if i==0:
return key[0]
elif i==1:
return key[1]
else:
return (stream(i-2)*7 + stream(i-1)*4)
enc = b""
for i in range(len(flag)):
water = stream((i//2)**6) % 256
enc += bytes([water ^ flag[i]])
print(enc)
# b'\x1a\x15\x05\t\x17\tu"-\x06lm\x01-\xc7\xcc2\x1eXA\x1c\x15\xb7\xdb\x06\x13\xaf\xa1-\x0b\xd4\x91-\x06\x8b\xd4-\x1e\xab\xaa\x15-\xf0\xed\x1f\x17\x1bY'
通过get_steam()函数计算出water,然后在用water对这个字节进行异或,然后将每一个结果拼接起来就是flag
解题代码:
key = [int.from_bytes(b"Be water", 'big'), int.from_bytes(b"my friend", 'big')]
enc = b'\x1a\x15\x05\t\x17\t\xf5\xa2-\x06\xec\xed\x01-\xc7\xcc2\x1eXA\x1c\x157[\x06\x13/!-\x0b\xd4\x91-\x06\x8b\xd4-\x1e+*\x15-pm\x1f\x17\x1bY'
def get_stream(i):
if i==0:
return key[0]
elif i==1:
return key[1]
else:
return (get_stream(i-2)*7 + get_stream(i-1)*4)
flag = b""
for i in range(len(enc)):
water = get_stream((i//2)**6) % 256
flag += bytes([enc[i] ^ water])
print(flag)
神秘的电话
morse.wav 摩斯转字符串
0223E_PRIIBLY__HONWA_JMGH_FGKCQAOQTMFR
另外还有一串加密信息
5Yeg5Liq5pif5pyf5YmN77yM5oiR5Lus5pS25Yiw5LiA5Liq56We56eY55qE5raI5oGv44CC5L2G5piv6L+Z5Liq5raI5oGv6KKr6YeN6YeN5Yqg5a+G77yM5oiR5Lus5LiN55+l6YGT5a6D55qE55yf5q2j5ZCr5LmJ5piv5LuA5LmI44CC5ZSv5LiA55+l6YGT55qE5L+h5oGv5piv5YWz5LqO5a+G6ZKl55qE77ya4oCc5Y+q5pyJ5YCS552A57+76L+H5Y2B5YWr5bGC55qE56+x56yG5omN6IO95oq16L6+5YyX5qyn56We6K+d55qE57uI54K54oCd44CC
base64解密加密信息
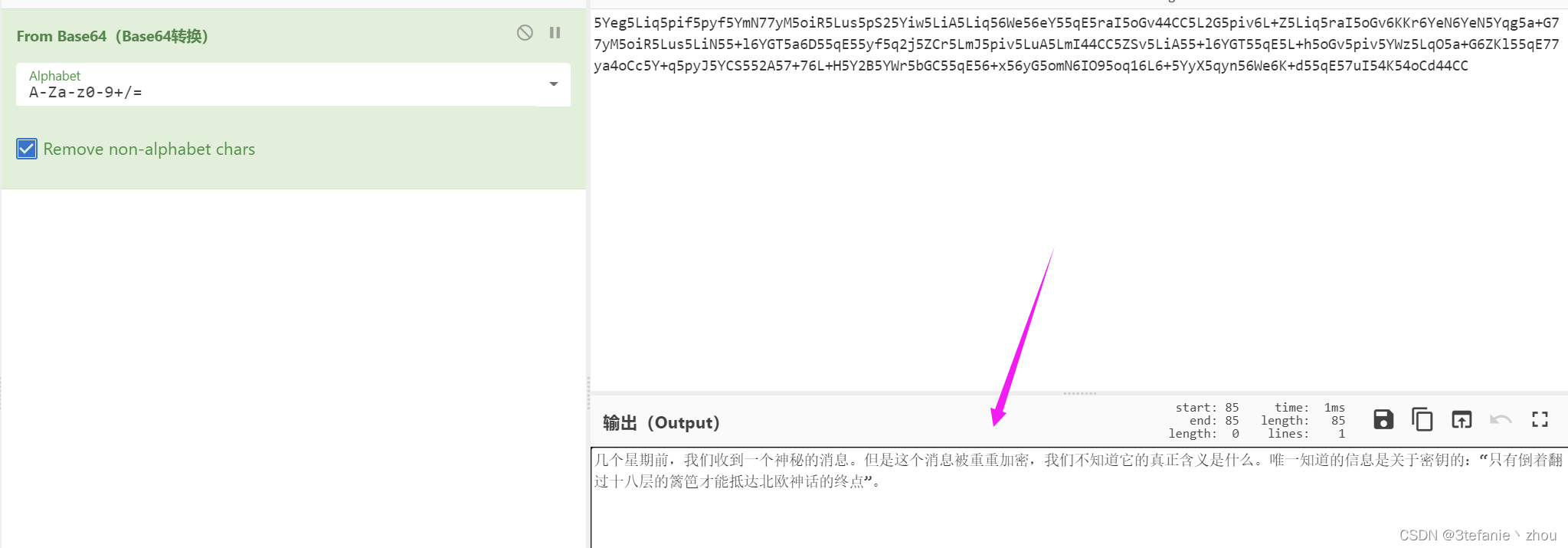
得知hint信息:
几个星期前,我们收到一个神秘的消息。但是这个消息被重重加密,我们不知道它的真正含义是什么。唯一知道的信息是关于密钥的:“只有倒着翻过十八层的篱笆才能抵达北欧神话的终点”。
将morse转成字符串,然后reverse再栅栏18,最后维吉尼亚解密 key:Vidar
PS:找维吉尼亚的Key找了一天,闷了
出题人吃我一拳

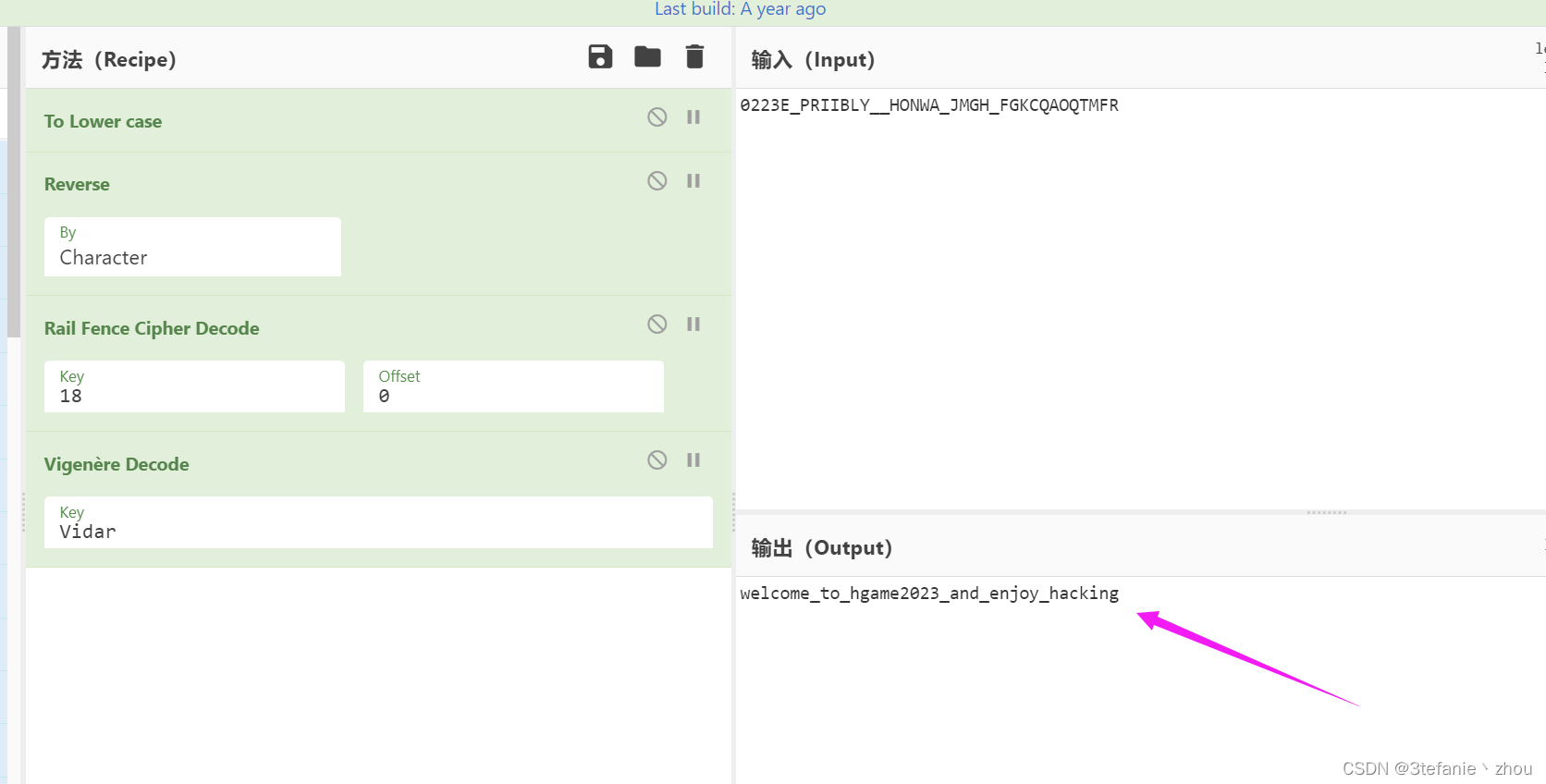
得到flag:
hgame{welcome_to_hgame2023_and_enjoy_hacking}
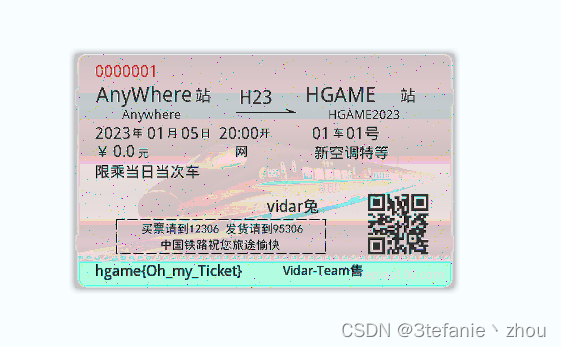
兔兔的车票
题目:
from PIL import Image
from Crypto.Util.number import *
from random import shuffle, randint, getrandbits
flagImg = Image.open('flag.png')
width = flagImg.width
height = flagImg.height
def makeSourceImg():
colors = long_to_bytes(getrandbits(width * height * 24))[::-1]
img = Image.new('RGB', (width, height))
x = 0
for i in range(height):
for j in range(width):
img.putpixel((j, i), (colors[x], colors[x + 1], colors[x + 2]))
x += 3
return img
def xorImg(keyImg, sourceImg):
img = Image.new('RGB', (width, height))
for i in range(height):
for j in range(width):
p1, p2 = keyImg.getpixel((j, i)), sourceImg.getpixel((j, i))
img.putpixel((j, i), tuple([(p1[k] ^ p2[k]) for k in range(3)]))
return img
n1 = makeSourceImg()
n2 = makeSourceImg()
n3 = makeSourceImg()
nonce = [n1, n2, n3]
index = list(range(16))
shuffle(index)
e=0
"""
这里flag.png已经提前被保存在source文件夹下了,文件名也是picture{xx}.png
"""
for i in index:
im = Image.open(f"source/picture{i}.png")
key = nonce[randint(0, 2)]
encImg = xorImg(key, im)
encImg.save(f'pics/enc{e}.png')
e+=1
16张图片,3*5+1,一张flag,剩下的就是三组密钥图片,我们可以提取每张图片的像素然后对比是不是相同,得到大概的加密图片像素分布,最后再还原flag.png。
还原脚本如下
from PIL import Image
width = 379
height = 234
img = Image.new('RGB',(width,height))
data1 = open("flag.txt","r").read()
data2 = open("out.txt","r").read()
data1 = data1.replace(", "," ").replace("(","").replace(")","").replace("[","").replace("]","").split(" ")
data1 = [int(x) for x in data1]
data2 = data2.replace(", "," ").replace("(","").replace(")","").replace("[","").replace("]","").split(" ")
data2 = [int(x) for x in data2]
r = []
g = []
b = []
print(data1)
for i in range(0,len(data1),3):
r.append(data1[i]^data2[i])
g.append(data1[i+1]^data2[i+1])
b.append(data1[i+2]^data2[i+2])
index = 0
for i in range(height):
for j in range(width):
img.putpixel((j, i),(r[index],g[index],b[index]))
index = index + 1
img.save("flag.png")
得到flag.png
Re
test_your_IDA
直接用notepad++打开,搜索 hgame,发现flag
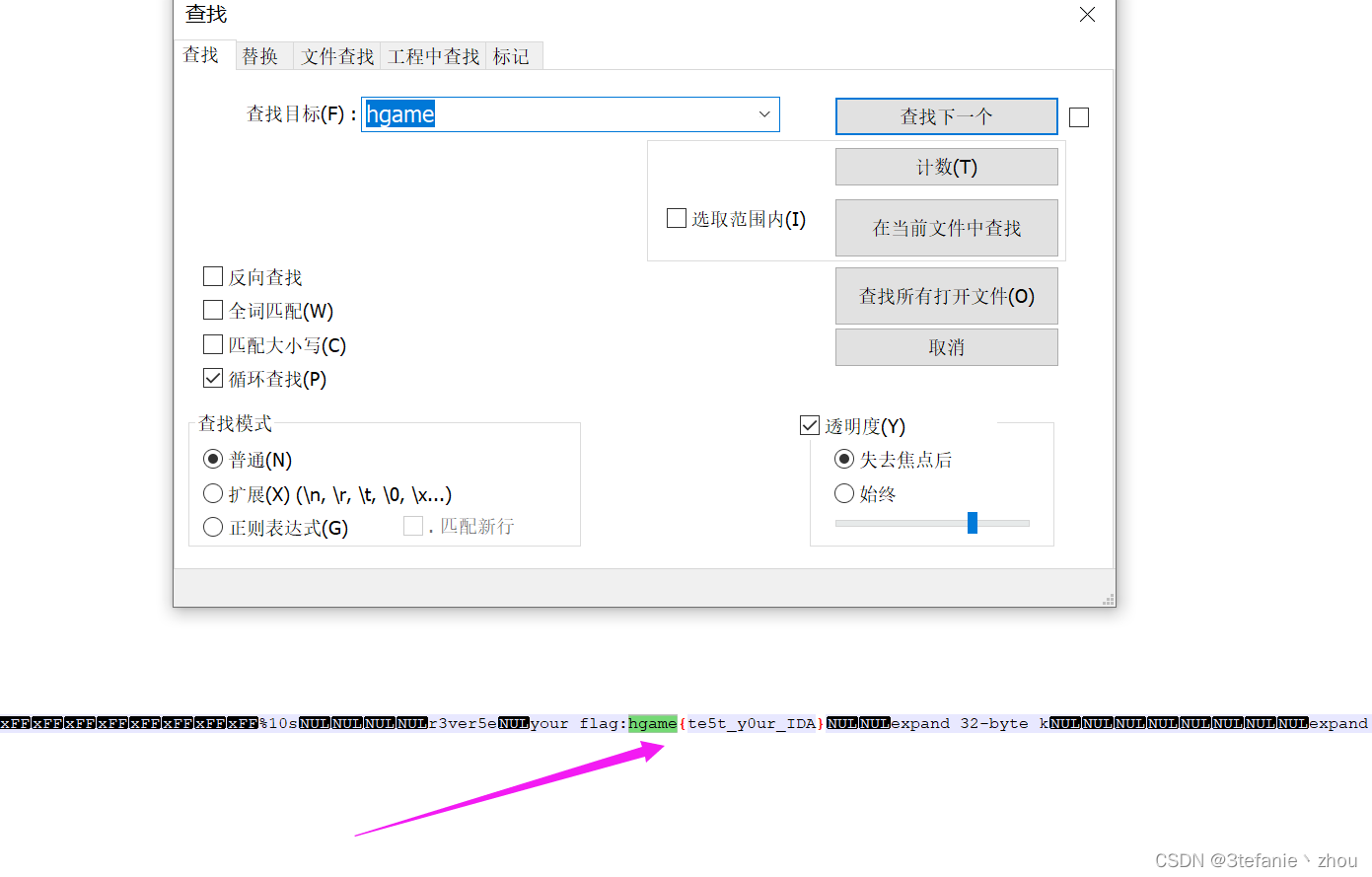
flag:
hgame{te5t_y0ur_IDA}
easyasm
简单分析 一下代码

只是逐位与0x33做异或,ok,那就把密文的每一位与0x33做异或然后拼接起来即可得到flag
enc = [0x5b,0x54,0x52,0x5e,0x56,0x48,0x44,0x56,0x5f,0x50,0x3,0x5e,0x56,0x6c,0x47,0x3,0x6c,0x41,0x56,0x6c,0x44,0x5c,0x41,0x2,0x57,0x12,0x4e]
flag = ''
for i in range(len(enc)):
flag += chr(enc[i]^0x33)
print(flag)
flag:
hgame{welc0me_t0_re_wor1d!}
encode
解题代码:
enc = [dword_403000[100]]
flag = ''
for i in range(50):
flag+=chr((enc[2*i+1]<<4) | enc[2*i])
print(flag)
easyenc
enc = ['''v8''' ]
flag= ''
for i in range(41):
flag += chr(((enc[i]+ 86)^0x32)%128)
print(flag)
a_cup_of_tea
from Crypto.Util.number import *
def decode(v, k):
v0 = v[0]
v1 = v[1]
x = 0x79bde460
delta = 0xabcdef23
k0 = k[0]
k1 = k[1]
k2 = k[2]
k3 = k[3]
for i in range(32):
v1 -= ((v0 + k2) << 4) ^ (v0 + x) ^ ((v0 >> 5) + k3)
v1 = v1 & 0xFFFFFFFF
v0 -= ((v1 << 4) + k0) ^ (v1 + x) ^ ((v1 >> 5) + k1)
v0 = v0 & 0xFFFFFFFF
x -= delta
x = x & 0xFFFFFFFF
v[0] = v0
v[1] = v1
return v
key = [0x12345678, 0x23456789, 0x3456789, 0x45678901]
enc = [[0x2E63829D, 0xC14E400F],[0x9B39BFB9, 0x5A1F8B14],[0x61886DDE, 0x6565C6CF],[0x9F064F64, 0x236A43F6]]
flag = b''
for i in enc:
dec = decode(i, key)
for j in dec:
flag += long_to_bytes(j)[::-1]
print(flag)
Pwn
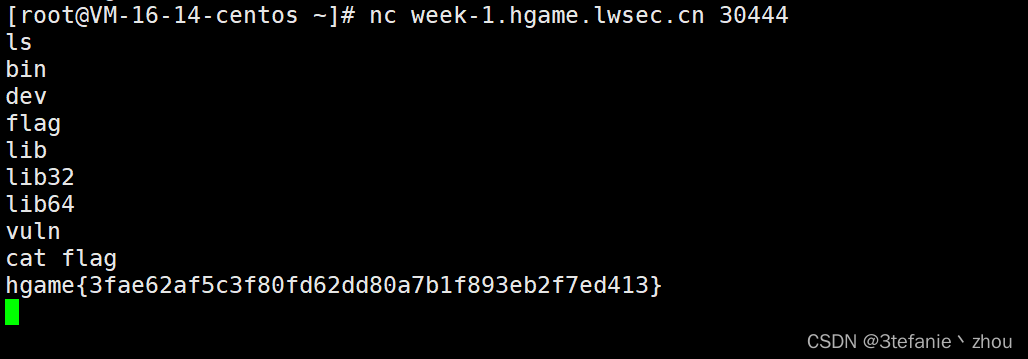
test_nc
直接nc 连接容器获取到一个shell
然后执行命令得到flag
iot
Help the uncle who can’t jump twice
题目直接给了broker 地址
broker:117.50.177.240:1883
根据题目信息
兔兔在车站门口看到一张塑料凳子,上边坐着一个自称V的男人.他希望你能帮他登上他的大号 Vergil 去那边的公告栏上康康Nero手上的YAMATO怎么样了
另一个附件给了一个密码本,应该是爆破Vergil 密码,然后登入上去订阅Nero寻找YAMATO
github上mqtt-pwn项目可以爆破MQTT Broker密码
https://github.com/akamai-threat-research/mqtt-pwn.git
安装以及使用教程:https://zhuanlan.zhihu.com/p/581871896
启动docker 配置username.txt以及 password.txt
执行命令爆破Vergil密码
bruteforce --host host --port port
爆破出Vergil的密码为power
broker连接工具 MQTT.fx -1.71
https://pan.baidu.com/s/1jwA7GUcT8h-rk_kt4CZq1A
提取码:1234
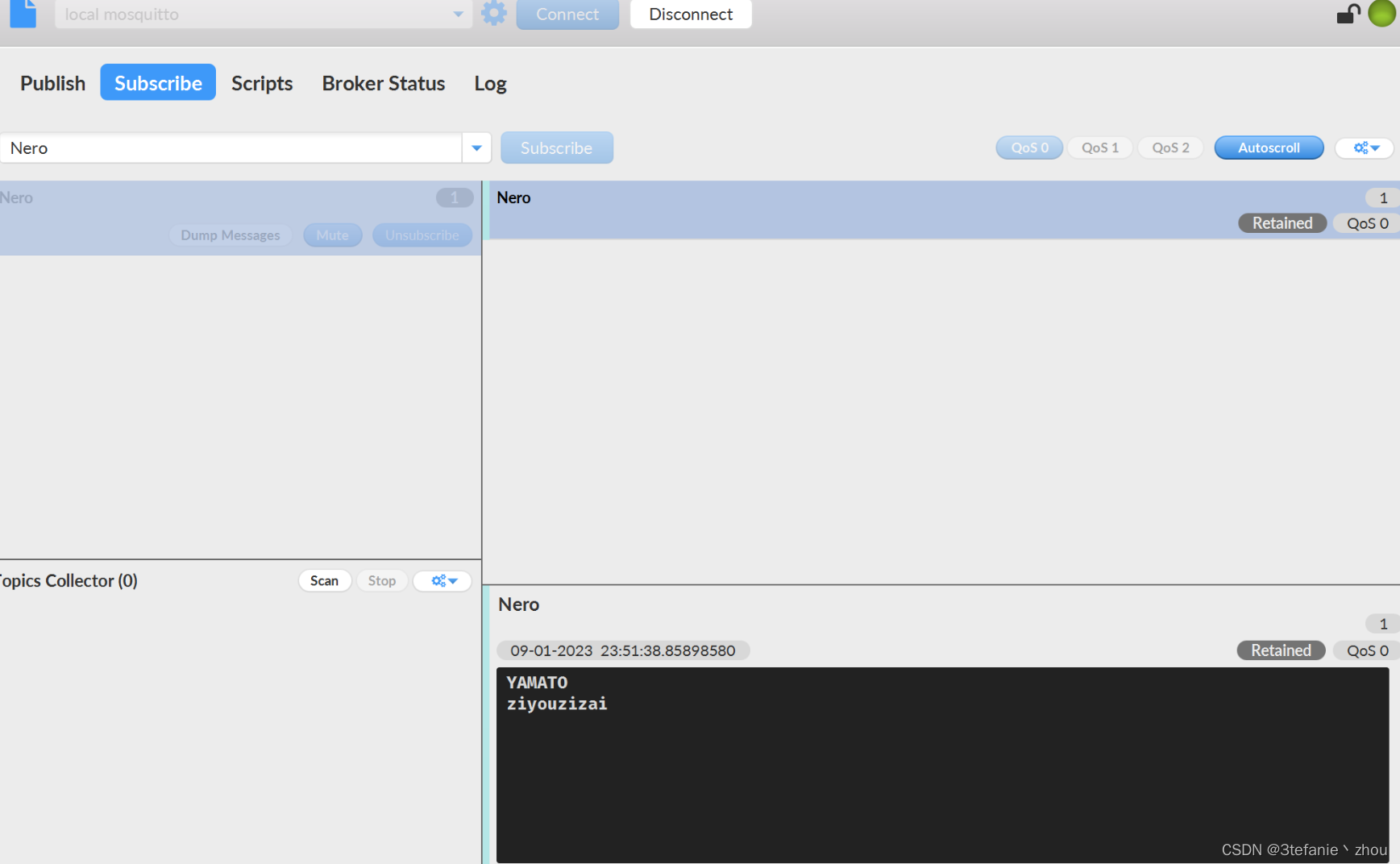
使用MQTT连接,根据题目提示订阅Nero,得到两串字符串
YAMATO
ziyouzizai
猜测是隐藏在Nero的子主题下面,但是不知道是哪个以及哪一级,所以使用多级通配符#去通配Nero下的子主题,订阅Nero/#发现flag,实际上订阅Nero/YAMATO即可得到flag
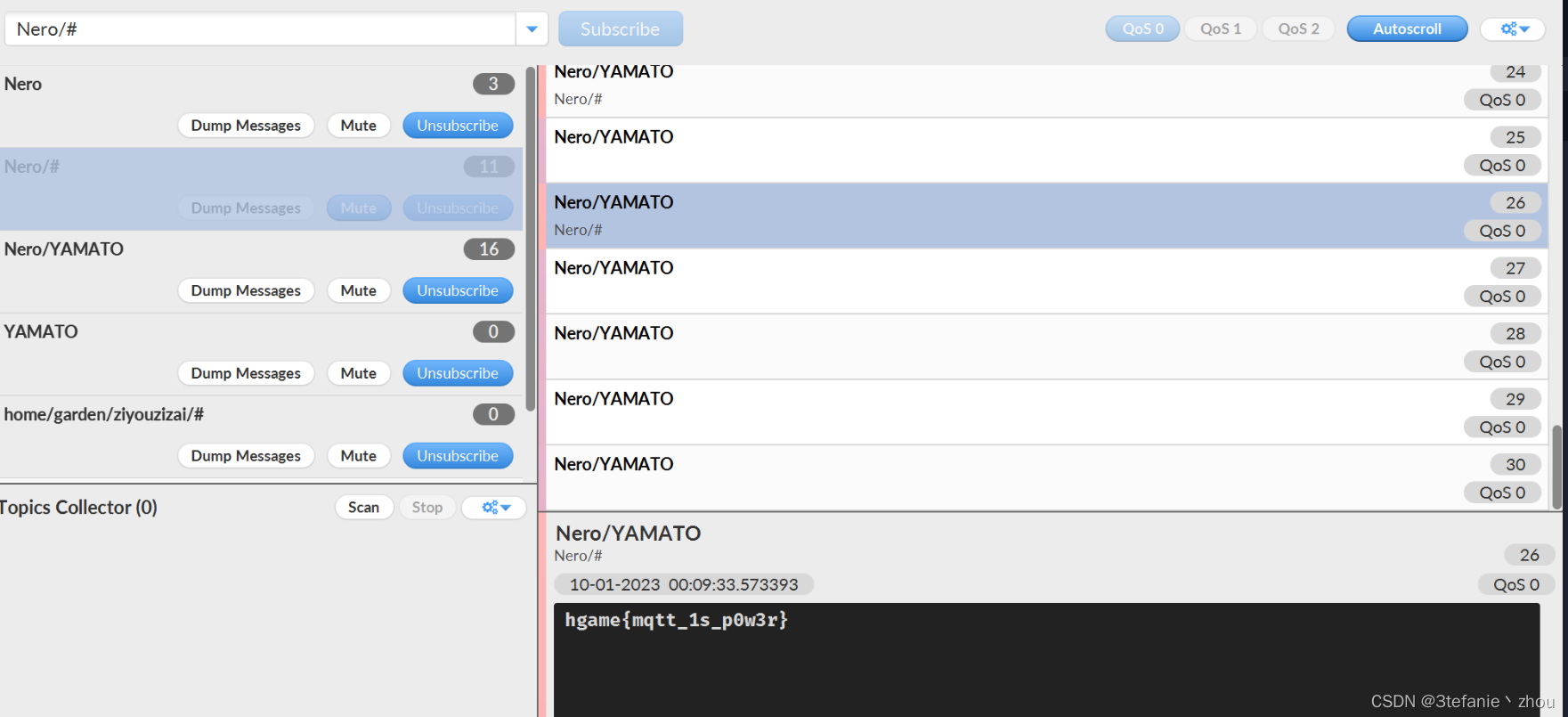
得到flag:
hgame{mqtt_1s_p0w3r}
【何谓遗憾,不可再得之物,不可再遇之人,便是遗憾】