一、弱口令检测---John the Ripper
1.了解 John the Ripper
John the Ripper 是一款开源的密码破解工具,可使用密码字典(包含各种密码组合的列表文件)来进行暴力破解。
- 一款密码分析工具,支持字典式的暴力破解
- 通过对shadow文件的口令分析,可以检测密码强度
- 官方网站:http://www.openwall.com/john/

2.破解详情
#解压工具包
cd /opt
tar zxf john-1.8.0.tar.gz
#安装软件编译工具
yum install -y gcc gcc-c++ make
#切换到src子目录
cd /opt/john-1.8.0/src
#进行编译安装
make clean linux-x86-64#准备待破解的密码文件
cp /etc/shadow /opt/shadow.txt
#执行暴力破解
cd /opt/john-1.8.0/run
./john /opt/shadow.txt
#查看已破解出的账户列表
./john --show /opt/shadow.txt
[root@localhost ~]# cd /opt #解压工具包
[root@localhost opt]# tar zxvf john-1.8.0.tar.gz
john-1.8.0/README
john-1.8.0/doc/CHANGES
john-1.8.0/doc/CONFIG
···
[root@localhost opt]# yum install -y gcc gcc-c++ make #安装软件编译工具
已加载插件:fastestmirror, langpacks
Loading mirror speeds from cached hostfile
file:///mnt/repodata/repomd.xml: [Errno 14] curl#37 - "Couldn't open file /mnt/repodata/repomd.xml"
正在尝试其它镜像。
软件包 gcc-4.8.5-44.el7.x86_64 已安装并且是最新版本
软件包 gcc-c++-4.8.5-44.el7.x86_64 已安装并且是最新版本
软件包 1:make-3.82-24.el7.x86_64 已安装并且是最新版本
无须任何处理
[root@localhost ~]# cd /opt/john-1.8.0/src/ #切换到src子目录
[root@localhost src]# make clean linux-x86-64 #进行编译安装
rm -f ../run/john ../run/unshadow ../run/unafs ../run/unique ../run/john.bin ../run/john.com ../run/unshadow.com ../run/unafs.com ../run/unique.com ../run/john.exe ../run/unshadow.exe ../run/unafs.exe ../run/unique.exe
rm -f ../run/john.exe john-macosx-* *.o *.bak core
rm -f detect bench generic.h arch.h tmp.s
cp /dev/null Makefile.dep
ln -sf x86-64.h arch.h
···
[root@localhost src]# cp /etc/shadow /opt/shadow.txt #准备待破解的密码文件
[root@localhost src]# cd /opt/john-1.8.0/run #执行暴力破解
[root@localhost run]# ./john /opt/shadow.txt
Loaded 3 password hashes with 3 different salts (crypt, generic crypt(3) [?/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
abc123 (lisi)
abc123 (root)
3g 0:00:00:22 100% 2/3 0.1358g/s 399.8p/s 408.5c/s 408.5C/s 123456..pepper
Use the "--show" option to display all of the cracked passwords reliably
Session completed
[root@localhost run]# ./john --show /opt/shadow.txt #查看已破解出的账户列表
root:abc123::0:99999:7:::
lisi:abc123:19834:0:99999:7:::
2 password hashes cracked, 0 left
[root@localhost run]#> john.pot #清空已破解出的账户列表,以便重新分析
./john --wordlist=./password.lst /opt/shadow.txt #使用指定的字典文件进行破解
[root@localhost run]# > john.pot #清空已破解出的账户列表
[root@localhost run]# ./john --wordlist=./password.lst /opt/shadow.txt #清空已破解出的账户列表
Loaded 3 password hashes with 3 different salts (crypt, generic crypt(3) [?/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
abc123 (lisi)
abc123 (root)
2g 0:00:00:00 100% 4.615g/s 147.6p/s 443.0c/s 443.0C/s 123456..pepper
Use the "--show" option to display all of the cracked passwords reliably
Session completed
[root@localhost run]#
二、网络端口扫描---NMAP
1.了解NMAP
NMAP 是一个强大的端口扫描类安全评测工具,支持 ping 扫描、多端口检测等多种技术。
- 一款强大的网络端口扫描、安全、检测工具
- 官方网站:http://nmap.org/
- CentOS 7.3光盘中安装包 nmap-6.40-7.el7.x86_64.rpm
2.常见的nmap命令选项和扫描类型
| -p | 指定扫描的端口 |
| -n | 禁用反向 DNS 解析(以加快扫描速度) |
| -sS | TCP的SYN扫描(半开扫描),只向目标发出SYN数据包,如果收到SYN/ACK响应包就认为目标端口正在监听,并立即断开连接;否则认为目标端口并未开放 |
| -sT | TCP连接扫描,这是完整的TCP扫描方式(默认扫描类型),用来建立一个TCP连接,如果成功则认为目标端口正在监听服务,否则认为目标端口并未开放 |
| -sF | TCP的FIN扫描,开放的端口会忽略这种数据包,关闭的端口会回应RST数据包。许多防火墙只对SYN数据包进行简单过滤,而忽略了其他形式的 TCP 攻击包。这种类型的扫描可间接检测防火墙的健壮性 |
| -sU | UDP 扫描,探测目标主机提供哪些 UDP 服务,UDP 扫描的速度会比较慢 |
| -sP | ICMP 扫描,类似于 ping 检测,快速判断目标主机是否存活,不做其他扫描 |
| -P0 | 跳过ping检测,这种方式认为所有的目标主机是存活的,当对方不响应ICMP请求时,使用这种方式可以避免因无法 ping 通而放弃扫描 |
3.NMAP
检查并安装 namp工具
[root@localhost ~]# rpm -qa|grep nmap #查看nmap
[root@localhost ~]# yum install -y nmap #安装nmap#分别查看本机开放的TCP端口、UDP端口
nmap -sT 127.0.0.1
nmap -sU 127.0.0.1
[root@localhost ~]# nmap -sT 127.0.0.1 #查看本机开放的TCP端口
Starting Nmap 6.40 ( http://nmap.org ) at 2024-04-22 20:53 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00038s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
111/tcp open rpcbind
631/tcp open ipp
Nmap done: 1 IP address (1 host up) scanned in 0.04 seconds
[root@localhost ~]# nmap -sU 127.0.0.1 #查看本机开放的UDP端口
Starting Nmap 6.40 ( http://nmap.org ) at 2024-04-22 20:53 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.0000010s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
111/udp open rpcbind
5353/udp open|filtered zeroconf
Nmap done: 1 IP address (1 host up) scanned in 2.69 seconds
#检测192.168.10.0/24网段有哪些主机提供HTTP服务
nmap -p 10 192.168.10.0/24
[root@localhost ~]# nmap -p 10 192.168.10.0/24 #检测192.168.10.0/24网段有哪些主机提供HTTP服务
Starting Nmap 6.40 ( http://nmap.org ) at 2024-04-22 20:56 CST
Nmap scan report for localhost (192.168.10.1)
Host is up (0.00040s latency).
PORT STATE SERVICE
10/tcp closed unknown
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for localhost (192.168.10.2)
Host is up (0.00031s latency).
PORT STATE SERVICE
10/tcp closed unknown
MAC Address: 00:50:56:E1:6D:15 (VMware)
Nmap scan report for localhost (192.168.10.254)
Host is up (-0.10s latency).
PORT STATE SERVICE
10/tcp filtered unknown
MAC Address: 00:50:56:F8:2A:39 (VMware)
Nmap scan report for localhost (192.168.10.120)
Host is up (0.000038s latency).
PORT STATE SERVICE
10/tcp closed unknown
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.51 seconds
#检测192.168.80.0/24网段有哪些存活主机
nmap -n -sP 192.168.80.0/24
[root@localhost ~]# nmap -n -sP 192.168.10.0/24
Starting Nmap 6.40 ( http://nmap.org ) at 2024-04-22 20:59 CST
Nmap scan report for 192.168.10.1
Host is up (0.00039s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.10.2
Host is up (0.00012s latency).
MAC Address: 00:50:56:E1:6D:15 (VMware)
Nmap scan report for 192.168.10.254
Host is up (-0.10s latency).
MAC Address: 00:50:56:F8:2A:39 (VMware)
Nmap scan report for 192.168.10.120
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.04 seconds
[root@localhost ~]#
补充知识:ss与netstat
| n | 以数值形式显示IP |
| l | 显示处于监听状态的网络连接及端口信息 |
| t | 查看TCP协议相关的信息 |
| p | 显示与网络连接相关联的进程号、进程名称信息(该选项需要root权限) |
| a | 显示主机中所有活动的网络连接信息(包括监听、非监听状态的服务端口) |
| u | 显示UDP协议相关的信息 |
| r | 显示路由表信息 |
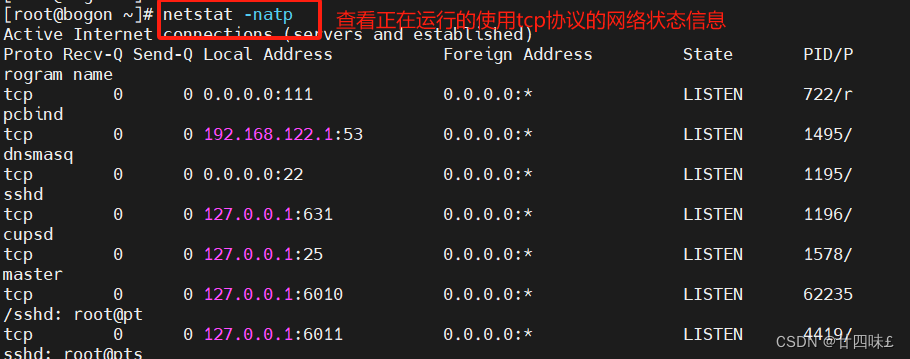
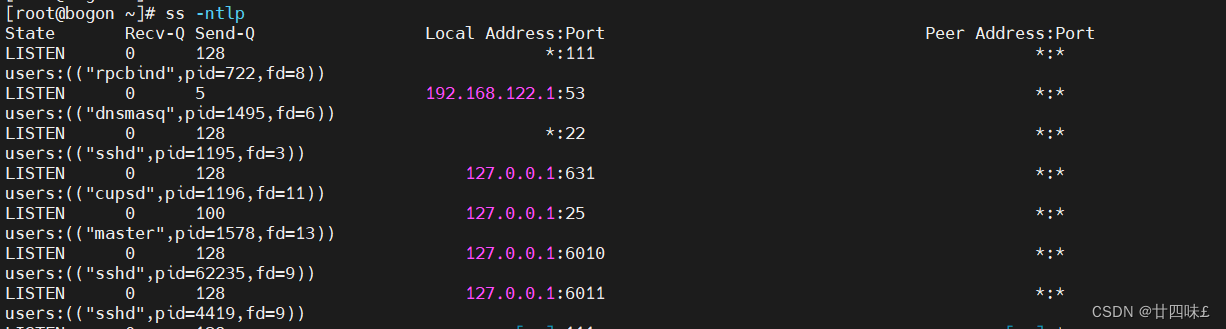
netstat -natp 查看正在运行的使用TCP协议的网络状态信息
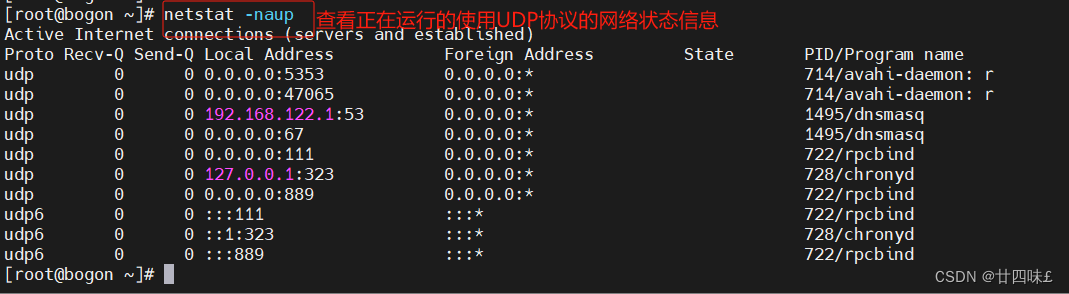
netstat -naup 查看正在运行的使用UDP协议的网络状态信息






![[RTOS 学习记录] 复杂工程项目的管理](https://img-blog.csdnimg.cn/img_convert/299e42a82bcfd1b79b68a9e95fba5a32.png#pic_center)
![[第一届 帕鲁杯 CTF挑战赛 2024] Crypto/PWN/Reverse](https://img-blog.csdnimg.cn/direct/cca0ad5a294b40378def6c701ceb43d8.png)