WMI是Windows操作系统管理数据和操作的基础设施,系统管理员可以使用VB Script、PowerShell及Windows API(C++、C#等)管理本地或远程计算机。
使用WMI框架应用程序可以直接访问EC RAM、 I/O端口、Memory地址、寄存器、Setup NV设定值,以及其他的系统设备资源。
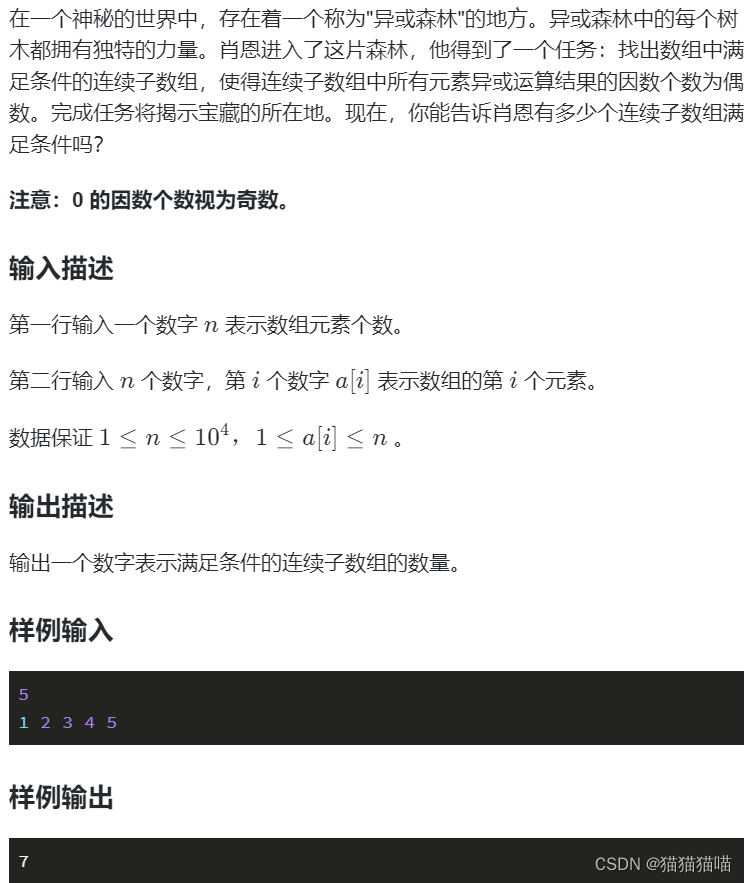
一、Asl code设计
OemWMIDemo.asl
Scope(\_SB)
{
Device(AMW1)//WMI
{
// pnp0c14 is Plug and Play ID assigned to WMI mapper
Name(_HID, "PNP0C14")
Name(_UID, "WMIDEMO")
// Description of data and events supported
Name(_WDG, Buffer() {
//
// Event
// GUID 93B56635-6D54-42D7-BB7D-DF77D452CCE4
// BIOS can generator WMI event by Notify (<<WMI device name>>, 0xAC)
//
0x35, 0x66, 0xB5, 0x93, 0x54, 0x6D, 0xD7, 0x42, 0xBB, 0x7D, 0xDF, 0x77, 0xD4, 0x52, 0xCC, 0xE4, // GUID
0xAC, 0, // Event Notification ID
1, // Instance Count
0x08, // Flags (WMIACPI_REGFLAG_EVENT)
//
// Method
// GUID ABBC0FB8-8EA1-11D1-A000-C90629100000
//
0xB8, 0x0F, 0xBC, 0xAB, 0xA1, 0x8E, 0xD1, 0x11, 0xA0, 0x00, 0xC9, 0x06, 0x29, 0x10, 0, 0,
0x44, 0x45, // Object Id (DE)
1, // Instance Count
0x02, // Flags (WMIACPI_REGFLAG_METHOD)
//
// This GUID for returning the MOF data
// 05901221-D566-11D1-B2F0-00A0C9062910
0x21, 0x12, 0x90, 0x05, 0x66, 0xd5, 0xd1, 0x11, 0xb2, 0xf0, 0x00, 0xa0, 0xc9, 0x06, 0x29, 0x10,
66, 68, // Object ID (BD)
1, // Instance Count
0x00, // Flags(none)
})
Name(FEAC, Buffer(0x04)
{
0x00, 0x00, 0x00, 0x00
})
Method (EVAC, 0)
{
Return (FEAC)
} // End of Method EVAC
//
// EcRAM Method data block
// Arg0 has the instance being queried
// Arg1 has the method id
// Arg2 has the data passed
Method(WMDE, 3)
{
//MethodId 1
if(LEqual(Arg1, 1))
{
Store(Arg2, FEAC)
Notify(AMW1, 0xAC)
Return(0)
}
}
// More info about an event
// Arg0 is the event id that was fired
Method(_WED, 1, NotSerialized)
{
If(LEqual(Arg0, 0xAC))
{
Return(EVAC())
}
}
// -------- Compiled version of "Associated MOF File" below --------
// Memo: generated by mofcomp.exe
Name(WQBD, Buffer()
{
})
}
}//end scope _SB
其中Mof GUID(0x21, 0x12, 0x90, 0x05, 0x66, 0xd5, 0xd1, 0x11, 0xb2, 0xf0, 0x00, 0xa0, 0xc9, 0x06, 0x29, 0x10)为固定值。
二、Mof code设计
OemWMIDemo.mof
[WMI, Dynamic, provider("WMIProv"),
locale("MS\\0x409"),
GUID("{ABBC0FB8-8EA1-11D1-A000-C90629100000}"),
Description("Call BIOS Function through WMI")
]
class WmiDemo
{
[key, read]
string InstanceName;
[read]
Boolean Active;
[WmiMethodId(1),
Implemented,
read, write,
Description("My method 1")
] void MyMethod1([inout, Description("My method 1")] uint32 Data);
};
[WMI, Dynamic, provider("WMIProv"),
locale("MS\\0x409"),
GUID("{93B56635-6D54-42D7-BB7D-DF77D452CCE4}"),
Description("Event generated when machine is hit")
]
class DemoWmiEvent : WMIEvent
{
[key, read]
string InstanceName;
[read]
Boolean Active;
[WmiDataId(1),
read, write,
Description("Force with which the machine was hit")
] uint32 Force;
};
三、编译Mof文件
工具:
mofcomp.exe为系统自带
wmimofck.exe可以从Windows WDK拷贝
将mof文件编译成bmf二进制文件
D:\WMI_Demo>mofcomp.exe -B:OemWMIDemo.bmf OemWMIDemo.mof
分析 MOF 文件: OemWMIDemo.mof
已成功分析 MOF 文件
将二进制 MOF 数据存储在 OemWMIDemo.bmf 中
Binary mof file OemWMIDemo.bmf expanded to 3126 bytes
使用wmimofck.exe可生成VBS脚本
D:\WMI_Demo>wmimofck.exe -tOemWMIDemo.vbs OemWMIDemo.bmf
Microsoft (R) WDM Extensions To WMI MOF Checking Utility Version 1.50.0000
Copyright (c) Microsoft Corp. 1997-2000. All rights reserved.
Binary mof file OemWMIDemo.bmf expanded to 3126 bytes
使用wmimofck.exe将bmf二进制文件转成文本
D:\WMI_Demo>wmimofck.exe -x"WIMDemo.txt" OemWMIDemo.bmf
Microsoft (R) WDM Extensions To WMI MOF Checking Utility Version 1.50.0000
Copyright (c) Microsoft Corp. 1997-2000. All rights reserved.
将文本中的内容填入asl文件中Name(WQBD, Buffer() { })的Buffer里。
四、测试
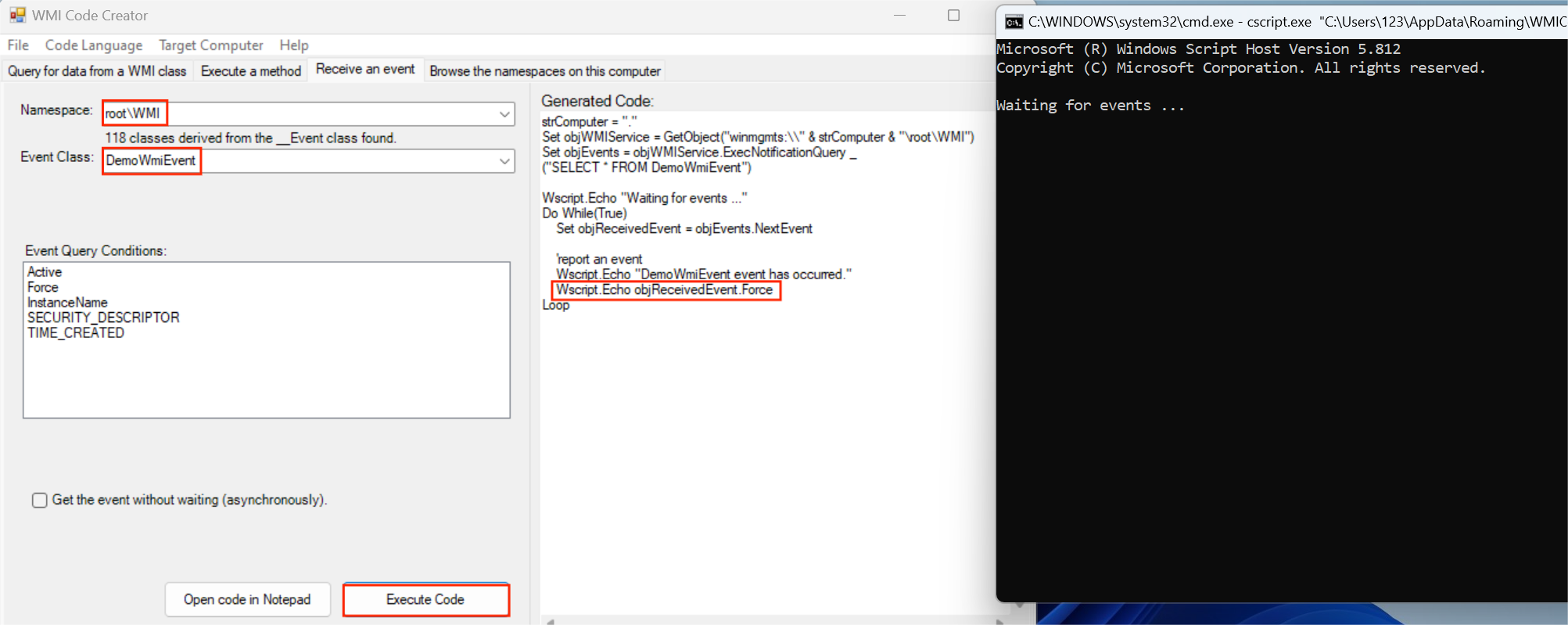
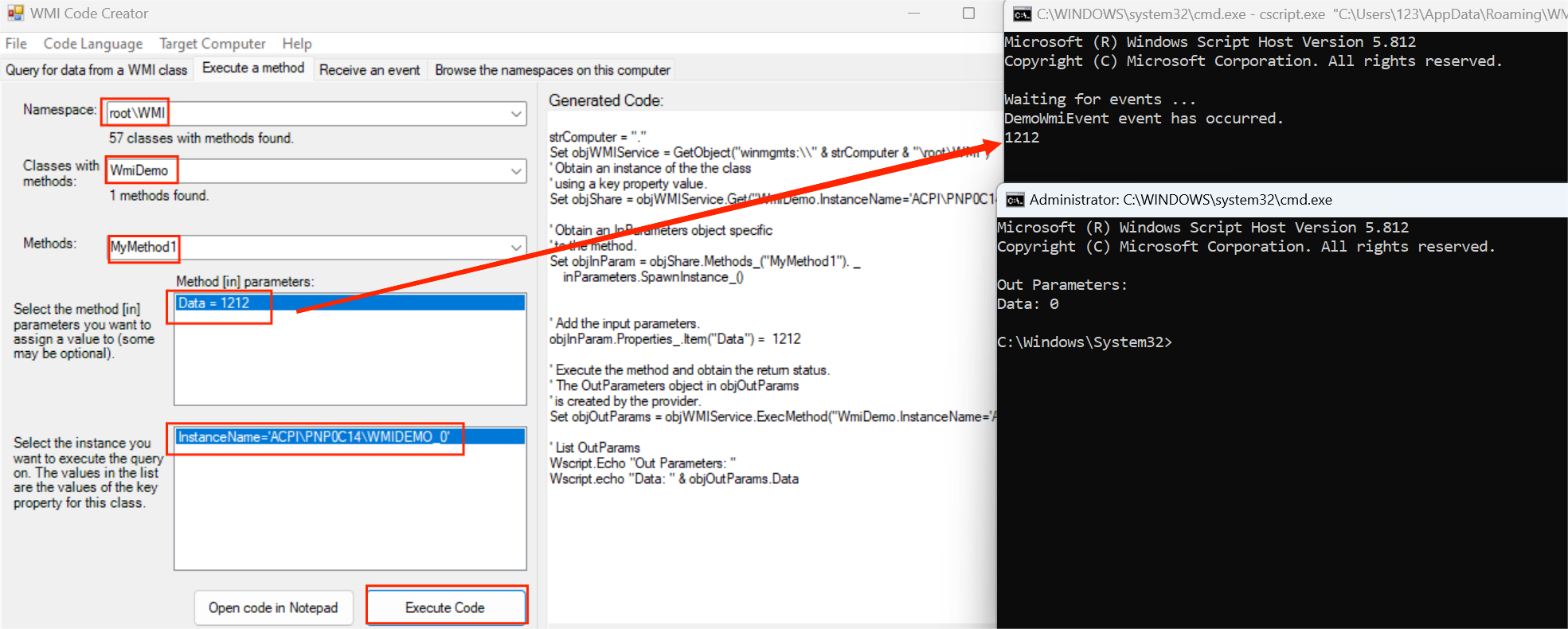
使用WMICodeCreator.exe工具进行测试。可支持生成VBScript, C#, and VB .NET代码。
管理员身份打开WMICodeCreator.exe。
-
首先设置event,并执行
在VBS脚本中,添加Wscript.Echo objReceivedEvent.Force语句可输出Event的返回值
-
设置Method,并执行
注意instance要出来,并且选中,如果没出来可能是GUID没填对,没选中的话执行会报错。
参考
创建一个WMI ACPI device
基于Windows Management Instrumentation(WMI)的BIOS接口设计