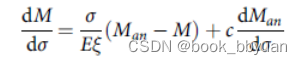文章目录
- 4. Network Layer
- 4.1 Router
- 4.1.1 Input port functions
- 4.1.2 Destination-based forwarding
- 4.1.3 Switching fabrics
- 4.1.4 Input port queueing
- 4.1.5 Output ports
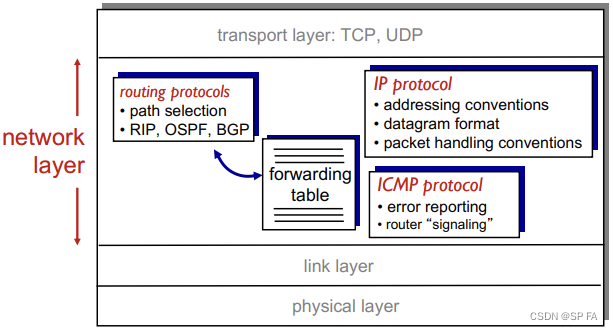
- 4.2 Internet Protocol
- 4.2.1 IP fragmentation, reassembly
- 4.3 IPv4 addressing
- 4.3.1 Subnets
- 4.3.2 Network Classes
- 4.3.3 CIDR
- 4.3.4 DHCP
- 4.3.5 Hierarchical addressing
- 4.4 NAT
- 4.5 IPv6
- 4.5.1 IPv6 datagram format:
- 4.5.22 Transition from IPv4 to IPv6
- 4.6 Generalized Forward and SDN
4. Network Layer
- Transport segment from sending to receiving host
- On sending side encapsulates segments into datagrams
- On receiving side, delivers segments to transport layer
- Network layer protocols in every host, router
- Router examines header fields in all IP datagrams passing through it.
Two key network-layer functions
- Forwarding: move packets from router’s input to appropriate router output.
- Routing: determine route taken by packets from source to destination (Routing algorithms)
data plane
- Local, per-router function
- Determines how datagram arriving on router input port is forwarded to router output port.
- Forwarding function
control plane
- Network-wide logic
- Determines how datagram is routed among routers along end-end path from source host to destination host
- Two control-plane approaches:
- traditional routing algorithms: implemented in routers.
- software-defined networking (SDN): implemented in (remote) servers.
Pre-router control plane
A distinct (typically remote) controller interacts with local control agents (CAs)
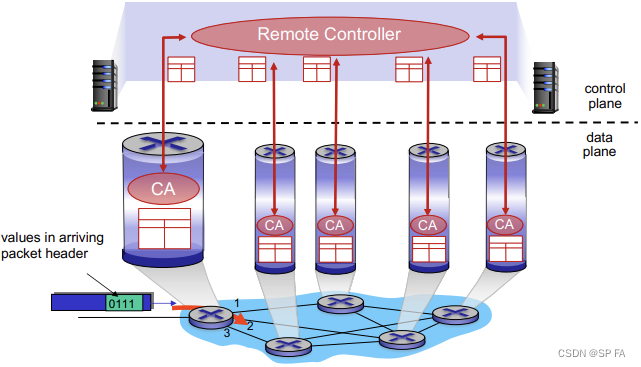
4.1 Router
High-level view of generic router architecture:
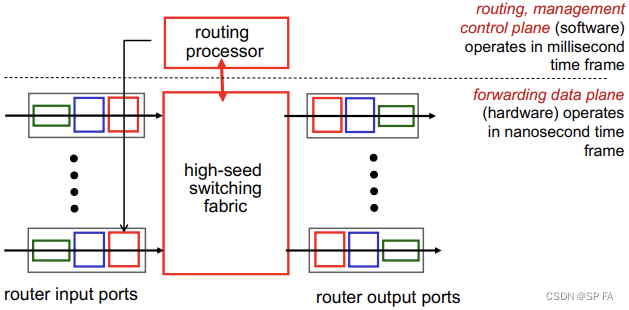
4.1.1 Input port functions
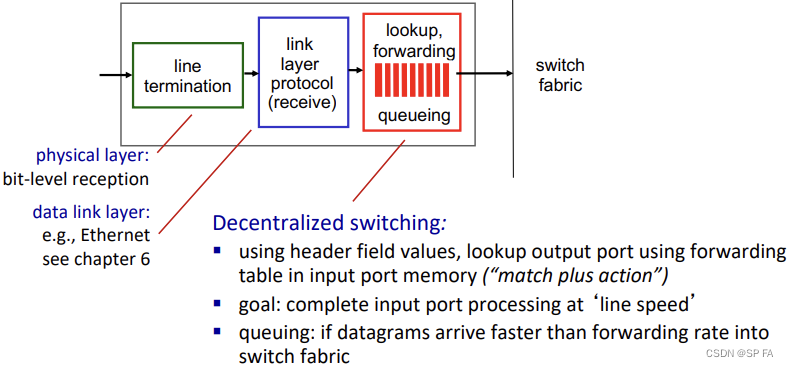
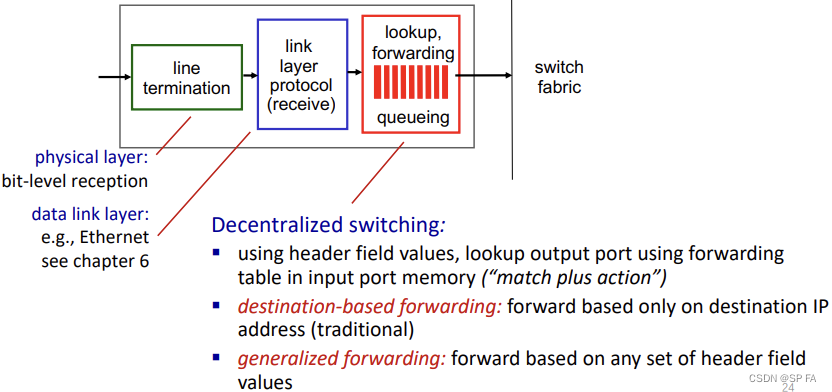
4.1.2 Destination-based forwarding
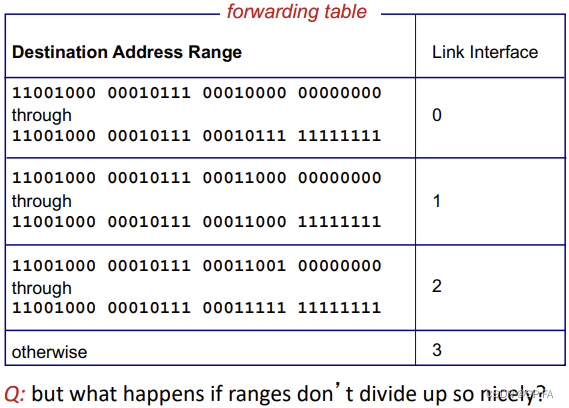
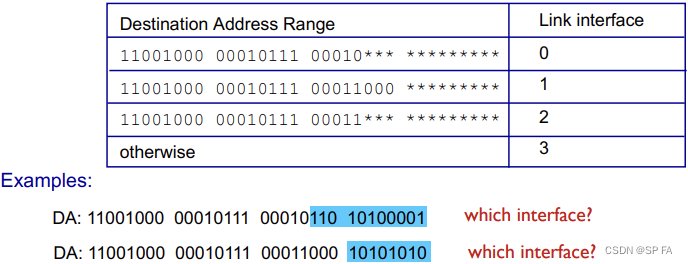
Longest prefix matching
- When looking forwarding table entry for given destination address, use longest address prefix that matches destination address.
- Longest prefix matching: often performed using ternary content addressable memories (TCAMs)
- Content addressable: present address to TCAM: retrieve address in one clock cycle, regardless of table size.
- Cisco Catalyst: can up 1M routing table entries in TCAM
4.1.3 Switching fabrics
- Transfer packet from input buffer to appropriate output buffer
- Switching rate: rate at which packets can be transfer from inputs to outputs
- Often measured as multiple of input/output line rate
- N inputs: switching rate N times line rate desirable
- Three types of switching fabrics
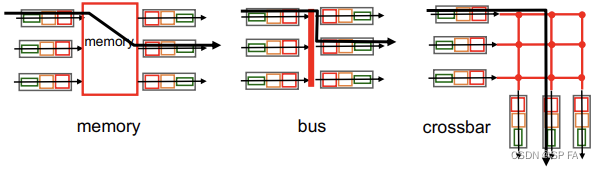
- Switching via memory (first generation routers)
- Traditional computers with switching under direct control of CPU
- Packet copied to system’s memory
- Speed limited by memory bandwidth (2 bus crossings per datagram)
- Switching via a bus
- Datagrams from input port memory to output memory via a shared bus
- Bus contention: switching speed limited by bus bandwidth
- Cisco 5600: 32 bus
- Switching via interconnection network
- Overcome bus bandwidth limitations
- Banyan networks, crossbar, other interconnection nets initially developed to connect processors in multiprocessor
- Advanced design: fragmenting datagram into fixed length cells, switch cells through the fabric
- Cisco 12000: switches 60 Gbps through the interconnection network.
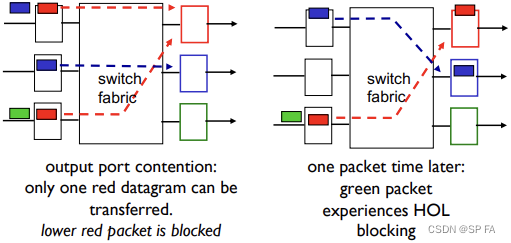
4.1.4 Input port queueing
- Fabric slower than input ports combined, so queueing may occur at input queues (queueing delay and loss due to input buffer overflow)
- Head-of-the-line (HOL) blocking: queued datagram at front of queue prevents others in queue from moving forward
4.1.5 Output ports
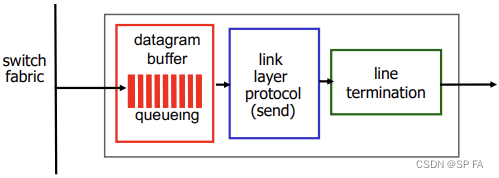
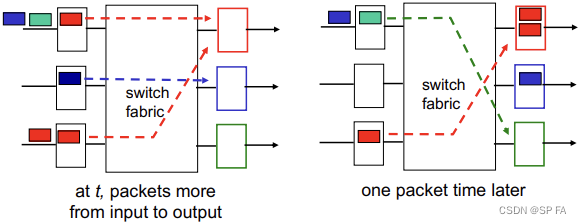
- RFC 3439 rule of thumb: average buffering equal to “typical” R T T RTT RTT (say 250 msec) times link capacity C C C
- Recent recommendation: with N N N flows, buffering equal to R T T ⋅ C N \frac{RTT\cdot C}{\sqrt N} NRTT⋅C
Scheduling mechanisms
- Scheduling: choose next packet to send on link
- FIFO scheduling: send in order of arrival to queue
- Discard policy: if packet arrives to full queue
- Tail drop: drop arriving packet
- Priority: drop/remove on priority basis
- Random: drop/remove randomly
- Discard policy: if packet arrives to full queue
- Priority
- send highest priority queued packet
- Multiple classes, with different priorities. Class may depend on marking or other header info (IP source / dest, port numbers)
- Round Robin (RR) scheduling
- Multiple classes
- Cyclically scan class queues, sending one complete packet from each class (if available)
- Weighted Fair Queueing (WFQ)
- Generalized Round Robin
- Each class gets weighted amount of service in each cycle
4.2 Internet Protocol
Host, router network layer functions:
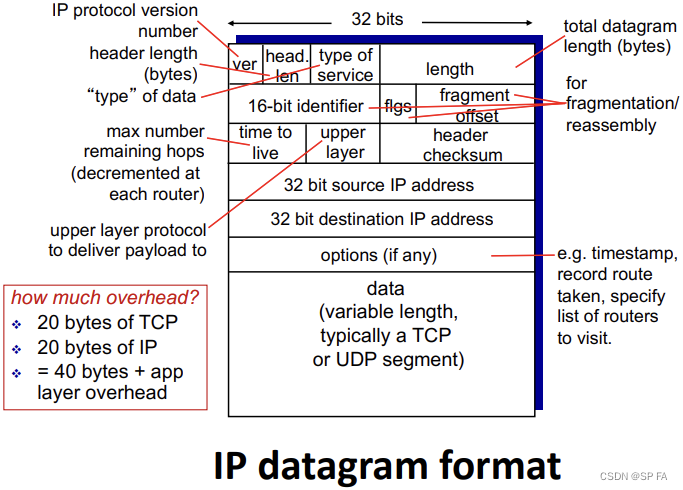
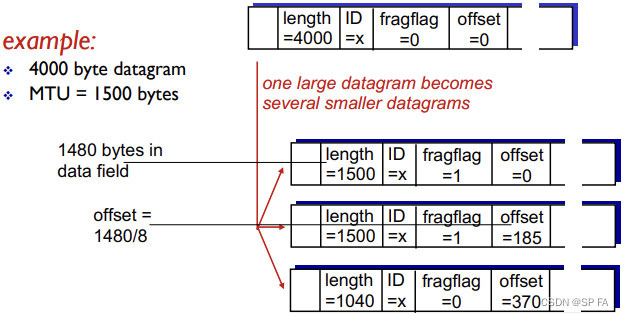
4.2.1 IP fragmentation, reassembly
Network links have MTU (max transfer size), largest possible link-level frame (Different link types, defferent MTUs)
Large IP datagram divided within net
- One datagram becomes several datagrams
- “Reassembled” only at final destination
- IP header bits used to identify, order related fragments.
4.3 IPv4 addressing
IP address: 32-bit identifier for host, router interface
Interface: connection between host/router and physical link
- Router’s typically have multiple interfaces
- Host typically has one or two interfaces
IP addresses associated with each interface
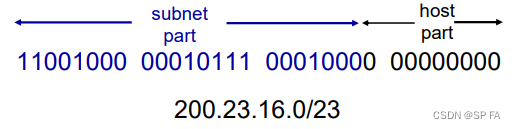
4.3.1 Subnets
IP address, two parts:
- Subnet part: high order bits
- Host part: low order bits
What’s a subnet?
Device interfaces with same subnet part of IP address. Can physically reach each other without intervening router
Recipe
To determine the subnets, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is called a subnet.
4.3.2 Network Classes
Classful addressing
- The network portion of an IP address were constrained to be 8, 16, or 24 bits in length.
- Subnets with 8-, 16-, and 24-bit subnet addresses were known as class A, B and C networks.
- It became problematic
- A class A (/8) subnet could accommodate only up to 2 8 − 2 = 254 2^8 − 2 = 254 28−2=254 hosts
- A class B (/16) subnet supporting 2 16 – 2 = 65534 2^{16} – 2 = 65534 216–2=65534 hosts, which is too large
4.3.3 CIDR
CIDR: Classless Inter Domain Routing
- Subnet portion of address of arbitrary length
- Address format: a.b.c.d/x, where x is # bits in subnet portion of address
4.3.4 DHCP
DHCP: Dynamic Host Configuration Protocol
Goal: allow host to dynamically obtain its IP address from network server when it joins network
- Can renew its lease on address in use
- Allows reuse of addresses (only hold address while connected/“on”)
- Support for mobile users who want to join network (more shortly)
DHCP overview:
- host broadcasts “DHCP discover” msg [optional]
- DHCP server responds with “DHCP offer” msg [optional]
- host requests IP address: “DHCP request” msg
- DHCP server sends address: “DHCP ack” msg
DHCP can return more than just allocated IP address on subnet:
- Address of first-hop router for client
- Name and IP address of DNS sever
- Network mask (indicating network versus host portion of address)
4.3.5 Hierarchical addressing
route aggregation
Hierarchical addressing allows efficient advertisement of routing information
The ability to use a single prefix to advertise multiple networks is often referred to as address aggregation or route aggregation.
more specific routes
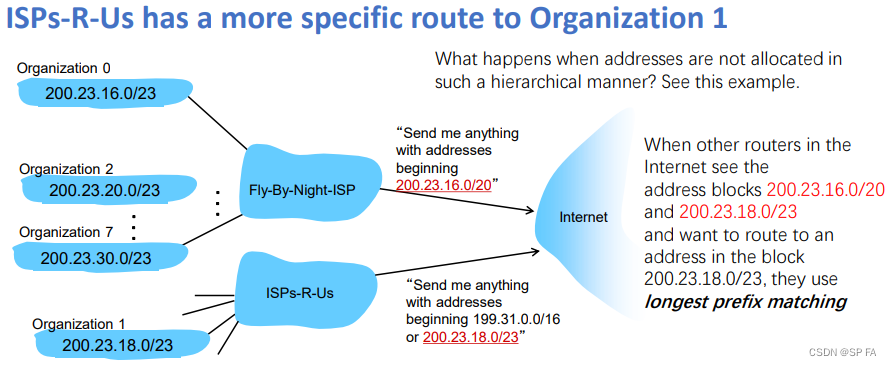
4.4 NAT
NAT: network address translation
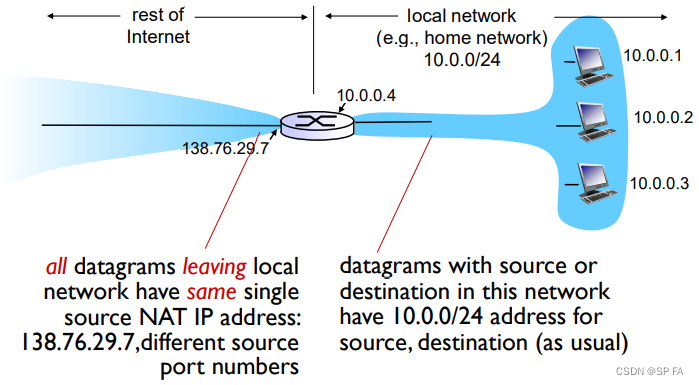
Motivation: local network uses just one IP address as far as outside world is concerned:
- Range of addresses not needed from ISP: just one IP address for all devices
- Can change addresses of devices in local network without notifying outside world
- Can change ISP without changing addresses of devices in local network
- Devices inside local net not explicitly addressable, visible by outside world (a security plus)
Implementation: NAT router must:
- Remember (in NAT translation table) every (source IP address, port #) to (NAT IP address, new port #) translation pair
- Outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #)
- Incoming datagrams: replace (NAT IP address, new port #) in dest fields of every incoming datagram with corresponding (source IP address, port #) stored in NAT table.
16-bit port-number field: 60,000 simultaneous connections with a single LAN-side address.
NAT is controversial:
- Routers should only process up to layer 3
- Address shortage should be solved by IPv6
- Violates end-to-end argument (NAT possibility must be taken into account by app designers, e.g., P2P applications)
- NAT traversal: what if client wants to connect to server behind NAT?
4.5 IPv6
Initial motivation: 32-bit address space soon to be completely allocated.
Additional motivation:
- Header format helps speed processing/forwarding
- Header changes to facilitate Q&S
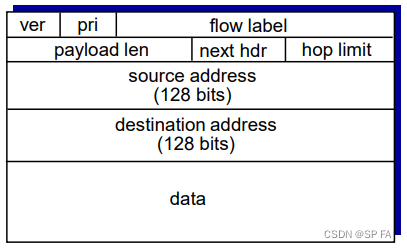
4.5.1 IPv6 datagram format:
Fixed-length 40 byte header. No fragmentation allowed.
- Priority (Traffic Class): identify priority among datagrams in flow.
- Flow Label: identify datagrams in same “flow”.
- Next header: identify upper layer protocol for data.
Other changes from IPv4
- Checksum: removed entirely to reduce processing time at each hop.
- Options: allowed, but outside of header, indicated by “Next Header” field.
- ICMPv6: new version of ICMP. Additional message types and Multicast group management functions.