harbor https部署
- 准备
- docker-compose安装
- https 证书
- harbor安装
- 访问harbor
- 推镜像到harbor
准备
192.168.112.99,harbor,centos7
192.168.112.3,测试机,centos7
docker版本:docker-ce 20.10.16(部署参考:https://blog.csdn.net/weixin_41988331/article/details/88743963)
docker-compose版本:1.29.2(部署参考:同上,或者下载最新发行版,https://github.com/docker/compose/releases,阿里云)
harbor版本:harbor-offline-installer-v2.6.4.tgz(GitHub 地址 https://github.com/goharbor/harbor/releases,阿里云)
docker-compose安装
mv docker-compose-linux-x86_64 /usr/local/bin/docker-compose
chmod +x /usr/local/bin/docker-compose
docker-compose version
https 证书
mkdir certs
cd certs
#创建CA私钥
openssl genrsa -out ca.key 4096
#自签名机构生成CA证书
openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=CN/ST=Jangsu/L=Nanjing/O=example/OU=Personal/CN=xxx.com" \
-key ca.key \
-out ca.crt
#参数说明:
## C,Country,代表国家
## ST,STate,代表省份
## L,Location,代表城市
## O,Organization,代表组织,公司
## OU,Organization Unit,代表部门
## CN,Common Name,代表服务器域名
## emailAddress,代表联系人邮箱地址。
#客户端私钥证书生成
openssl genrsa -out xxx.com.key 4096
openssl req -sha512 -new \
-subj "/C=CN/ST=Jangsu/L=Nanjing/O=example/OU=Personal/CN=xxx.com" \
-key xxx.com.key \
-out xxx.com.csr
#生成多个域名请求
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1=xxx.com
DNS.2=harbor.xxx.com
DNS.3=192.168.112.99
EOF
#使用自签名CA签发证书
openssl x509 -req -sha512 -days 3650 \
-extfile v3.ext \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in xxx.com.csr \
-out xxx.com.crt

harbor安装
这里采用离线方式: 下载包,https://github.com/goharbor/harbor/releases
tar -xf harbor-offline-installer-v2.6.4.tgz -C /usr/local/harbor/
mv certs /usr/local/harbor/
cd /usr/local/harbor/
cp harbor.yml harbor.yml.tmpl
修改harbor.yml
hostname: harbor.xxx.com
certificate: /usr/local/harbor/certs/server.crt
private_key: /usr/local/harbor/certs/server.key
data_volume: /data
建立Harbor数据目录,并使用数据盘挂载到/data目录
mkdir /data
./install.sh --help
Note: Please set hostname and other necessary attributes in harbor.yml first. DO NOT use localhost or 127.0.0.1 for hostname, because Harbor needs to be accessed by external clients.
Please set --with-notary if needs enable Notary in Harbor, and set ui_url_protocol/ssl_cert/ssl_cert_key in harbor.yml bacause notary must run under https.
Please set --with-trivy if needs enable Trivy in Harbor
Please set --with-chartmuseum if needs enable Chartmuseum in Harbor
#--with-trivy 开启trivy扫描
./install.sh --with-trivy --with-chartmuseum
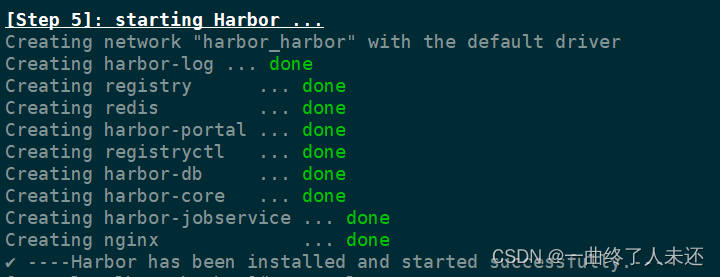
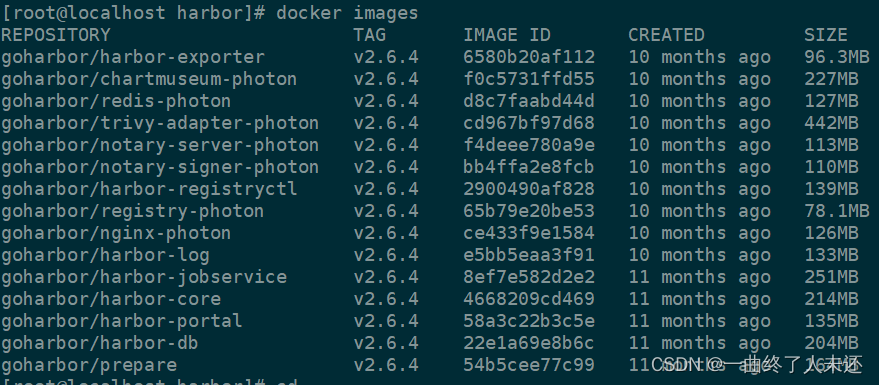
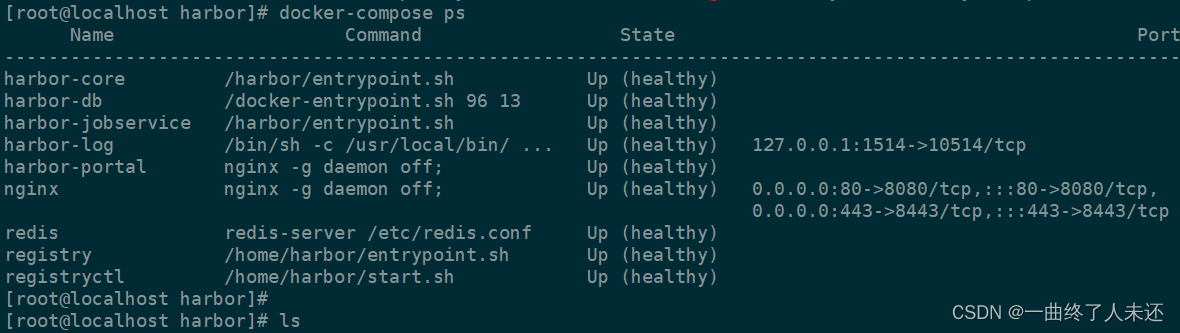
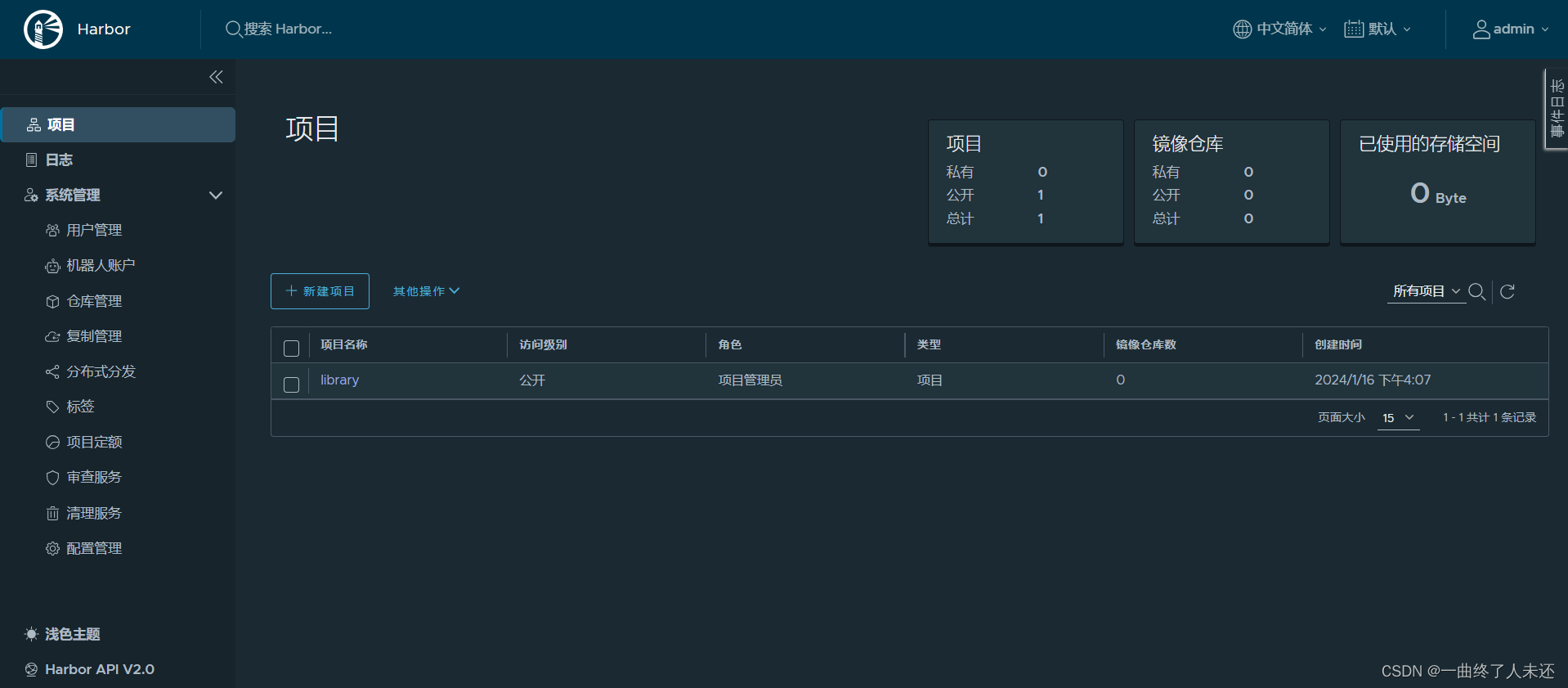
访问harbor
hosts绑定
192.168.112.99 harbor.xxx.com
登录账号密码:admin Harbor12345

推镜像到harbor
192.168.112.3# mkdir /etc/docker/certs.d/xxx.com -p
192.168.112.99# scp /usr/local/harbor/certs/xxx.com.crt 192.168.112.3:/etc/docker/certs.d/xxx.com
192.168.112.3# vim /etc/hosts
192.168.112.99 harbor.xxx.com
192.168.112.3# cat daemon.json
{"insecure-registries":["harbor.xxx.com"]}
192.168.112.3# systemctl restart docker
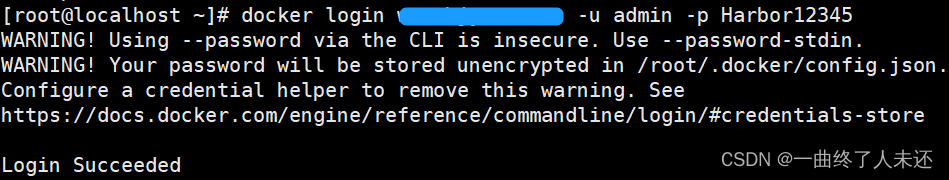
192.168.112.3# docker login harbor.xxx.com -u admin -p Harbor12345
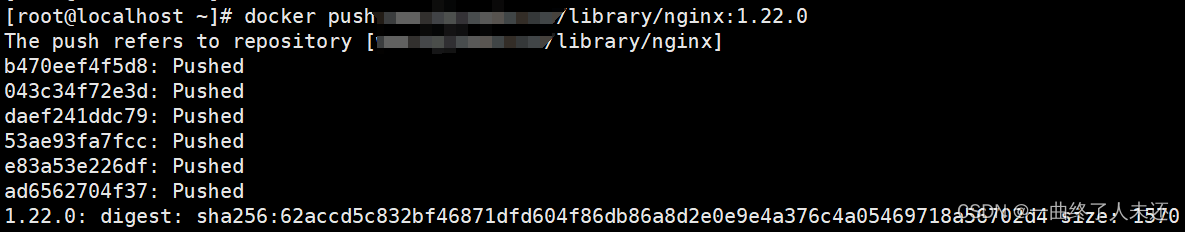
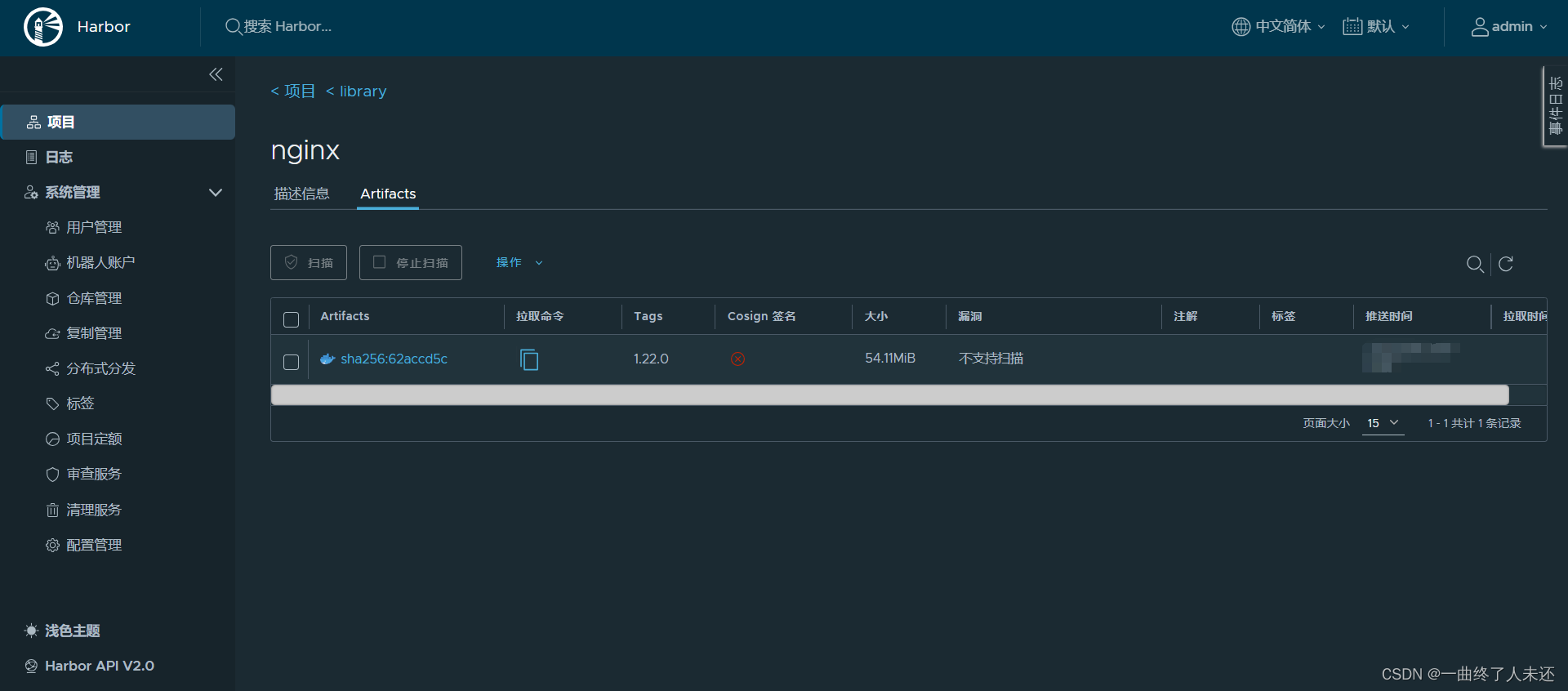
参考链接:https://www.cnblogs.com/punchlinux/p/16499966.html







![[ PyQt入门教程 ] Qt Designer工具的使用](https://img-blog.csdnimg.cn/img_convert/9a82a8677f6a23bd3867d084dcb81c12.png)