关于Domain_audit
该工具是PowerView、Impacket、PowerUpSQL、BloodHound、Ldaprelayscan和Crackmapexec的包装器,用于自动执行枚举和在On-Prem Active Directory渗透测试期间执行的大量检查。
检查项目
Invoke-AD CheckAll将按顺序执行以下操作:
- 收集AD对象的基础数据,以
/data/格式放入.csv目录 - 使用bloodhound收集数据-收集方法所有,acl和会话在后台。
- 在
/data/中创建所有(已启用)用户、管理员帐户、计算机和组的列表 - 列出用户、组、计算机、OU、GPO、管理员、域控制器和域功能级别的数量。
- 检查管理员数量是否超过5%(域中管理员数量高)
- 枚举域信任和forst内的信任
- 检查是否安装了AzureAD或Azure SSO
- 在SQL检查的新窗口中执行runas
- 检查域中的SQL实例
- 检查当前用户是否有权访问SQL实例
- 检查当前用户是否为sysadmin
- 收集SQL实例的数据库信息
- 检查谁正在运行SQL实例
- 检查数据库链接是否为sysadmin
- 运行invoke-sqlaudit并保存所有数据
- 检查弱密码
- 检查执行xp_dirtree和执行xp_fileexist
- 检查域功能级别是否为2016
- 检查密码策略配置
- 检查cleartextpassword = 1
- 检查密码长度
- 检查密码复杂性
- 检查帐户锁定
- 检查Kerberos策略配置是否从默认值更改
- 检查名称中是否有带有LAPS的GPO
- 检查GPO应用于哪个OU
- 检查LAPS策略
- 检查admin account name
- 检查密码复杂性
- 检查密码长度
- 检查密码日期
- 检查pwexpirationprotection enabled
- 检查已启用
- 检查是否有安装了LAPS的系统
- 检查是否存在未安装LAPS的系统
- 如果找到LAPS GPO或找到LAPS计算机-检查当前用户是否可以读取LAPS密码
- 获取所有用户的描述-手动检查密码或感兴趣的信息
- 检查字符串pw、pass、ww或wachtwoord是否在描述中。
- 获取带有描述的所有组-手动检查密码或感兴趣的信息
- 获取所有带有说明的计算机-手动检查密码或感兴趣的信息
- 检查是否有具有Spn的管理员
- 检查是否存在具有Spn的用户
- 具有Spn的Kerberoast用户
- 检查具有受限委派的用户
- 检查具有无约束委派的用户
- 检查具有受限委派的计算机
- 检查除域控制器之外的具有不受约束委派的计算机
- 检查具有基于资源的受约束委派集的计算机
- 检查用户的PASSWD_NOT_REQ属性
- 检查用户密码是否为空
- 检查用户的DONT_REQ_PREAUTH属性
- AS-REP Roast用户
- 检查用户的DONT_EXPIRE_PASSWORD属性
- 检查是否有使用可逆加密的用户
- 检查是否有使用DES加密的用户
- 检查是否有使用旧密码的域管理员
- 检查KRBTGT是否有旧密码
- 检查AD中的EOL操作系统
- 查看EOS Windows 10版本
- 检查无登录或pwdlastset早于365天的非活动计算机对象
- 检查过去365天内未登录的非活动用户
- 检查是否所有特权用户都属于受保护用户组
- 检查是否所有特权用户都有“此帐户敏感且无法委派”标志
- 检查是否有下列特权组的成员:帐户操作员、备份操作员、打印操作员、DNS管理员、架构管理员
- 检查高特权组中是否有计算机对象
- 检查谁可以向域添加计算机对象
- 检查这是否是默认的身份验证用户组
- 检查ms-ds-machineaccountqouta是什么,如果它是null(好)或not-set(坏)或其他值。
- 检查ADIDNS
- 如果它包含已验证用户组的createchild
- 如果通配符记录存在
- 检查Pre-Windows2000 Compatible Access组的成员资格,以及经过身份验证的用户是否仍然是该组的成员
- 检查printspooler服务是否正在DC上运行
- 检查LDAP签名是否已启用,LDAPS是否已配置且LDAPS绑定是否已启用
- 检查域中是否存在默认Exchange组
- 检查是否存在Exchange服务器以及其是否处于活动状态
- 检查默认Exchange组中的成员身份
- 检查sysvol中的密码
- 检查netlogon中的密码(脚本,程序等)
- 检索所有计算机对象的IP地址并创建/24范围以供进一步枚举
- 扫描已知的Windows端口+ ssh和web的范围。为每个端口创建列表
- 检查可访问计算机上的SMB
- 检查SMBv1
- 检查签名要求
- 检查可读共享
- 检查可写共享
- 检查WebService客户端是否正在可访问的机器上运行
- 检查访问
- 通过SMB检查当前用户是否为本地管理员
- 检查当前用户是否可以通过WINRM访问
- 检查当前用户是否可以通过RDP访问
- 检查当前用户是否可以通过MSSQL进行访问并且是sysadmin(WIP)
功能特性
- 是否创建EOS Server版本查询?
- 将域管理员/企业管理员的查询/检查更新到所有特权组。
- 更新查询以从数据中筛选禁用用户。
- 检查旧的易受攻击的Exchange权限
- 将特权角色函数更改为循环并添加更多角色
- 删除可访问计算机的-Ping功能,并使用Invoke-Portscan对特定端口执行端口扫描
- 通过SMB、RDP、MSSQL等检查对发现的计算机的访问!
- 找到一种审计所有ACL的方法(Invoke-ACLScanner从非域加入的角度看不起作用,-ResolvGUIDS中断!)
- 添加ADCS检查,但首先需要在LAB环境中进行设置。
- 添加跳过dns更改的功能
- 为每个函数添加依赖性选项
安装和设置
- 安装python 3.10(例如从Windows商店)
git clone https://github.com/0xJs/domain_audit
cd .\domain_audit\import\
git clone https://github.com/SecureAuthCorp/impacket
cd impacket; python3 -m pip install .
cd ../;
git clone https://github.com/zyn3rgy/LdapRelayScan;
cd LdapRelayScan;
python3 -m pip install -r .\requirements.txt
cd ../../;
- 请确保脚本中的以下工具的路径viariables正确(如果您遵循了安装步骤,则应该正确)
$script:PowerView_Path = "$PSScriptRoot\import\PowerView.ps1"
$script:Powerupsql_Path = "$PSScriptRoot\import\PowerUpSQL.ps1"
$script:Impacket_Path = "$PSScriptRoot\import\impacket"
$script:BloodHound_Path = "$PSScriptRoot\import\Sharphound.ps1"
$script:GpRegisteryPolicy_Path = "$PSScriptRoot\import\GPRegistryPolicy\GPRegistryPolicy.psd1"
$script:CME_Path = "$PSScriptRoot\import\cme"
$script:LdapRelayScan_Path = "$PSScriptRoot\import\LdapRelayScan\LdapRelayScan.py"
- 访问Sysvol访问被拒绝的问题?
- 要解决此问题,请运行
gpedit.msc,转到Computer -> Administrative Templates -> Network -> Network Provider -> Hardened UNC Paths,启用策略并单击“显示”按钮。 - 在“值名称”中输入
*,在值中输入RequireMutualAuthentication=0,RequireIntegrity=0,RequirePrivacy=0。 - 在“值名称”中输入
*,在值中输入RequireMutualAuthentication=0,RequireIntegrity=0,RequirePrivacy=0。 - 在“值名称”中输入
*,在值中输入RequireMutualAuthentication=0,RequireIntegrity=0,RequirePrivacy=0。
- 要解决此问题,请运行
- 如果仍然出现问题,请添加以下内容:
reg add HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\NetworkProvider\HardenedPaths /v "\\*\SYSVOL" /d "RequireMutualAuthentication=0" /t REG_SZ /f
reg add HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\NetworkProvider\HardenedPaths /v "\\*\NETLOGON" /d "RequireMutualAuthentication=0" /t REG_SZ /f
运行使用
- 以管理员身份启动PowerShell
- 这是将DNS服务器更改为DC IP并将域添加到主机文件所必需的。否则,某些检查/执行将失败,例如Impacket。
运行所有检查
PS C:\Users\user\Desktop> . C:\Tools\domain_audit\domain_audit.ps1
PS C:\Users\user\Desktop> Invoke-ADCheckAll -Domain "amsterdam.bank.local" -User "john" -Password "Welcome2022!" -Server 10.0.0.3
- 页面底部的示例输出。
运行单独检查
- 有些检查需要主机文件中的DNS和域名。所以最好是设置它!
设置dns和主机文件
Invoke-ChangeDNS -Server 10.0.0.3 -Domain "amsterdam.bank.local"
运行检查
Invoke-ADEnum -Domain "amsterdam.bank.local" -User "john" -Password "Welcome2022!" -Server 10.0.0.3
Invoke-ADEnumTrust -Domain "amsterdam.bank.local" -User "john" -Password "Welcome2022!" -Server 10.0.0.3
Invoke-ADCheckSQL -Domain "amsterdam.bank.local" -User "john" -Password "Welcome2022!" -Server 10.0.0.3
输出
该工具将在当前目录或提供的位置创建一个包含域名和日期的目录。在这个目录中有三个目录:
Data,具有来自域对象的.csv文件、侦探数据和一些对象列表。Findings,检查的输出可能是有趣的内容或报告为发现。Checks,具有检查的输出,应手动评估以检查是否有要报告的内容。
示例输出Invoke-ADCheckAll
PS C:\Users\user\Desktop> . C:\Tools\domain_audit\domain_audit.ps1
PS C:\Users\user\Desktop> Invoke-ADCheckAll -Domain "amsterdam.bank.local" -User "john" -Password "Welcome2022!" -Server 10.0.0.3
[+] Running as administrator, changing DNS to 10.0.0.3 and adding 10.0.0.3 amsterdam.bank.local to host file
[+] AD Authentication for amsterdam.bank.local\john succeeded!
[+] Output will be written in C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22
---------- DATA EXPLAINED ----------
- All data is written to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\
- In this folder are three subfolders
- files in \findings\ are findings that should be reported
- files in \checks\ needs to be checked
- files in \data\ is raw data
---------- COLORS EXPLAINED ----------
White is informational text
Green means check has passed
Yellow means manually check the data
Dark Red means finding
---------- GATHERING DATA ----------
[+] Gathering data of all Users, Groups, Computerobject, GPO's, OU's, DC's and saving it to csv
[+] Gathering BloodHound data all, session and ACL in seperate PowerShell session in background
---------- BASIC ENUMERATION ----------
[W] Saving a list of all users to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\list_users.txt
[W] Saving a list of all enabled users to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\list_users_enabled.txt
[W] Saving a list of all administrators to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\list_administrators.txt
[W] Saving a list of all groups to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\list_groups.txt
[W] Saving a list of all computerobjects to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\list_computers.txt
---------- DOMAIN INFORMATION ----------
The domain functional level is: Windows 2016
In the domain amsterdam.bank.local there are:
- 27 users and 25 enabled users
- 51 groups
- 4 computers
- 4 OU's
- 2 GPO's
- 3 Administrators
- 1 Domain Controllers
---Checking if amount of admins is more then 5% of all users---
[-] There are 3 administrators, which is 11.11% of all users
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\large_amount_of_administrators.txt
---------- ENUMERATING DOMAIN TRUSTS ----------
[+] The domain amsterdam.bank.local trusts 1 domains which are:
bank.local
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\trusts.txt
[+] The trust for domain bank.local is WITHIN_FOREST, enumerating trusts
[+] The domain bank.local trusts 2 domains which are:
amsterdam.bank.local
secure.local
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\trusts.txt
---Checking if AzureAD connect is in use---
[+] AzureAD connect is not installed
---Checking if Azure SSO is in use---
[+] Azure SSO is not configured
---------- EXECUTING CHECKS ----------
[+] Executing in another window because runas is required
[+] Pleace manually supply the Password Welcome2022!
--- Running SQL checks in new window ---
Enter the password for amsterdam.bank.local\john:
Attempting to start powershell.exe -Exec bypass -NoExit Import-Module C:\Tools\domain_audit\domain_audit.ps1; Set-Variable Findings_Path -Value C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings; Set-Variable Data_Path -Value C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data; Set-Variable Checks_Path -Value C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\checks; Set-Variable OutputDirectoryCreated -Value True; Invoke-ADCheckSQL -Domain amsterdam.bank.local -Server 10.0.0.3 -User john -Password Welcome2022! -SkipPrompt as user "amsterdam.bank.local\john" ...
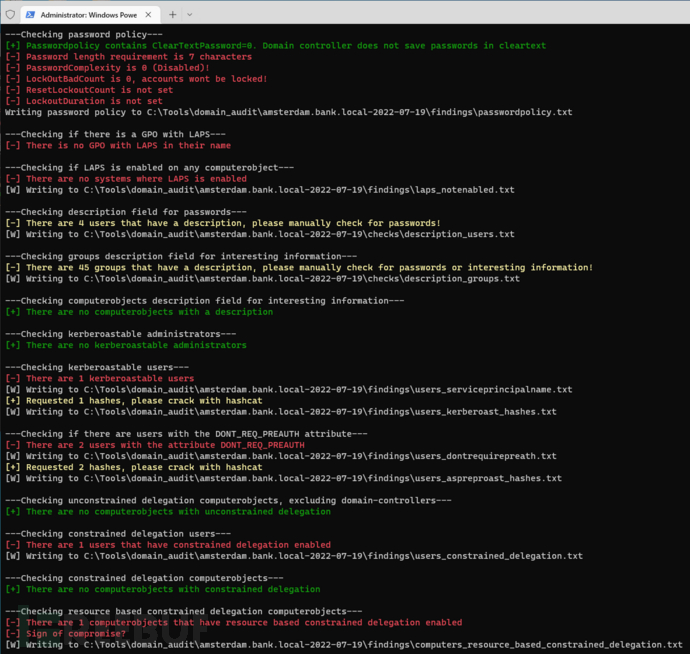
---Checking password policy---
[+] Passwordpolicy contains ClearTextPassword=0. Domain controller does not save passwords in cleartext
[-] Password length requirement is 7 characters
[-] PasswordComplexity is 0 (Disabled)!
[-] LockOutBadCount is 0, accounts wont be locked!
[-] ResetLockoutCount is not set
[-] LockoutDuration is not set
Writing password policy to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\passwordpolicy.txt
---Checking if there is a GPO with LAPS---
[-] There is no GPO with LAPS in their name
---Checking if LAPS is enabled on any computerobject---
[-] There are no systems where LAPS is enabled
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\laps_notenabled.txt
---Checking description field for passwords---
[-] There are 4 users that have a description, please manually check for passwords!
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\checks\description_users.txt
---Checking groups description field for interesting information---
[-] There are 45 groups that have a description, please manually check for passwords or interesting information!
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\checks\description_groups.txt
---Checking computerobjects description field for interesting information---
[+] There are no computerobjects with a description
---Checking kerberoastable administrators---
[-] There are 1 kerberoastable administrators
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\administrators_serviceprincipalname.txt
---Checking kerberoastable users---
[-] There are 2 kerberoastable users
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\users_serviceprincipalname.txt
[+] Requested 2 hashes, please crack with hashcat
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\users_kerberoast_hashes.txt
---Checking if there are users with the DONT_REQ_PREAUTH attribute---
[-] There are 2 users with the attribute DONT_REQ_PREAUTH
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\users_dontrequirepreath.txt
[+] Requested 2 hashes, please crack with hashcat
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\users_aspreproast_hashes.txt
---Checking constrained delegation users---
[-] There are 1 users that have constrained delegation enabled
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\users_constrained_delegation.txt
---Checking unconstrained delegation computerobjects, excluding domain-controllers---
[-] There are 1 users that have unconstrained delegation enabled
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\users_unconstrained_delegation.txt
---Checking constrained delegation computerobjects---
[+] There are no computerobjects with constrained delegation
---Checking unconstrained delegation computerobjects, excluding domain-controllers---
[-] There are 1 computerobjects that have unconstrained delegation enabled
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\computers_unconstrained_delegation.txt
---Checking resource based constrained delegation computerobjects---
[+] There are no computerobjects with resource based constrained delegation
---Checking if there are users with the PASSWD_NOTREQD attribute---
[-] There are 2 users with the attribute PASSWD_NOTREQD
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\users_passwdnotreqd.txt
---Checking for users with empty password---
[-] The password for user bank_dev is empty
[-] The password for user steve is empty
---Checking if there are users with the DONT_EXPIRE_PASSWORD attribute---
[-] There are 17 users with the attribute DONT_EXPIRE_PASSWORD
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\users_dontexpirepassword.txt
---Checking if there are users with the reversible encryption---
[+] There are no users with reversible encryption
---Checking if there are users with DES encryption---
[+] There are no users with DES encryption
---Checking if administrator accounts - that aren't disabled - have a password older then 365 days---
[+] There where no enabled administrators with a password older then 365 days
---Checking if KRBTGT account has a password older then 365 days---
[+] The password from the krbtgt is not older then 365 days
---Checking if there are EOL operating systems in the AD---
[+] There are no computerobjects in the AD that are EOL
---Checking if there are end of service Windows 10 operating systems in the AD---
[+] There are no Windows 10 computerobjects computerobjects in the AD that are End Of Service
---Checking if there are computerobjects that have no login or login/pwdlastset older then 365 days---
[+] There are no computerobjects in the AD that are inactive
---Checking if there are users that didn't login for 365 days---
[+] There are no users in the AD that are inactive (didn't login or changed their password in the last 365 days)
---Checking if members of privileged groups are part of the protected users group---
[-] There are 3 privileged users not part of the protected users group
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\administrators_notin_protectedusersgroup.txt
---Checking if members of privileged groups have the flag 'this account is sensitive and cannot be delegated'---
[-] There are 3 privileged users without the flag 'this account is sensitive and cannot be delegated' that aren't in the Protected Users group
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\administrators_delegation_flag.txt
---Checking if there are members in high privileged groups---
[+] There are no users in the Account Operators group
[+] There are no users in the Backup Operators group
[+] There are no users in the Print Operators group
[+] There are no users in the DNS Admins group
[+] There are no users in the Schema Admins group
---Checking if there are computerobjects part ofhigh privileged groups---
[+] There are no computerobjects part of a high privileged groups
---Checking who can add computerobjects to the domain---
[-] The authenticated users group(S-1-5-11) can add 10 computerobjects to the domain
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\authenticated_users_can_join_domain.txt
[W] Writing amount of computerobjects that can be joined to the domain by the object to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\checks\can_join_domain_amount.txt
---Checking if there are passwords in the SYSVOL share---
This might take a while
[+] Checking SYSVOL of DC02
[-] There might be 1 passwords in the SYSVOL of DC02. Please manually check
Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\checks\sysvol_passwords.txt
---Checking if there are passwords in the NETLOGON share---
This might take a while
[+] Checking NETLOGON of DC02
[-] There might be 1 passwords(string pass) in the NETLOGON of DC02. Please manually check
Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\checks\netlogon_passwords.txt
---Checking printspooler service on each DC---
[-] Printspooler enabled on DC02
Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\printspooler_domaincontrollers.txt
---Running LdapRelayScan---
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\domaincontrollers_ldaprelayscan.txt
---Checking for LDAP signing---
[+] One or more domain controller(s) does not require LDAP signing
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\domaincontrollers_no_ldap_signing.txt
---Checking for LDAPS binding---
[+] One or more domain controller(s) does not require LDAPS binding
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\domaincontrollers_no_ldaps_binding.txt
---Checking if exchange is used within the domain---
[+] No Exchange groups exist
---Checking which machines are reachable from current machine through ping---
[+] There are 3 computers which are reachable
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\computers_accessible.txt
---Running crackmapexec against each reachable host enumerating SMB data and shares---
[+] Crackmapexec will hang and needs a enter to continue
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\crackmapexec_reachablecomputers.txt
---Checking for hosts which have SMBV1 enabled---
[+] There are no reachable computers which have SMBV1 enabled (SMBv1:True)
---Checking for hosts without signing---
[+] There are 2 reachable computers which does not require signing (Signing:False)
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\computers_nosigning.txt
---Checking for shares with READ access---
[+] There are 4 shares the current user can READ
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\shares_read_access.txt
---Checking for shares with WRITE access---
[+] There are 1 shares the current user can WRITE to
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\shares_write_access.txt
---Running crackmapexec against each reachable host enumerating webclient service---
[+] Crackmapexec will hang and needs a enter to continue
[W] Writing all data to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\data\crackmapexec_webdav.txt
[+] There are 1 systems with the webclient service running
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\computers_webdav.txt
---------- EXECUTING SQL CHECKS ----------
---Checking MSSQL instances---
[+] Found 1 MSSQL instances
[+] Checking connection to each MSSQL instance
[-] The current user can access 1 MSSQL instances
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\SQLserver_user_has_access.txt
---Checking if the user is sysadmin on the accessible instances---
[+] The current user is not sysdmin to any SQL instances
---Checking database links for sysadmin security context---
[-] There are 1 links which run under the security context of a sysadmin user
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\SQLserver_sysadmin_on_links.txt
---Running Invoke-SQLAudit on the accessible instances---
This might take a while
VERBOSE: WEB01.amsterdam.bank.local : No named instance found.
VERBOSE: WEB01.amsterdam.bank.local : Connection Success.
VERBOSE: WEB01.amsterdam.bank.local : Checking for autoexec stored procedures...
[-] Invoke-SQLAudit found 7 issues
[W] Writing to C:\Users\user\Desktop\amsterdam.bank.local-2022-08-22\findings\SQLserver_sqlaudit.txt
许可证协议
本项目的开发与发布遵循GPL-3.0开源许可证协议。
项目地址
Domain_audit:【GitHub传送门】
CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享