rsarsa
题目描述
Math is cool! Use the RSA algorithm to decode the secret message, c, p, q, and e are parameters for the RSA algorithm.
p = 9648423029010515676590551740010426534945737639235739800643989352039852507298491399561035009163427050370107570733633350911691280297777160200625281665378483
q = 11874843837980297032092405848653656852760910154543380907650040190704283358909208578251063047732443992230647903887510065547947313543299303261986053486569407
e = 65537
c = 83208298995174604174773590298203639360540024871256126892889661345742403314929861939100492666605647316646576486526217457006376842280869728581726746401583705899941768214138742259689334840735633553053887641847651173776251820293087212885670180367406807406765923638973161375817392737747832762751690104423869019034
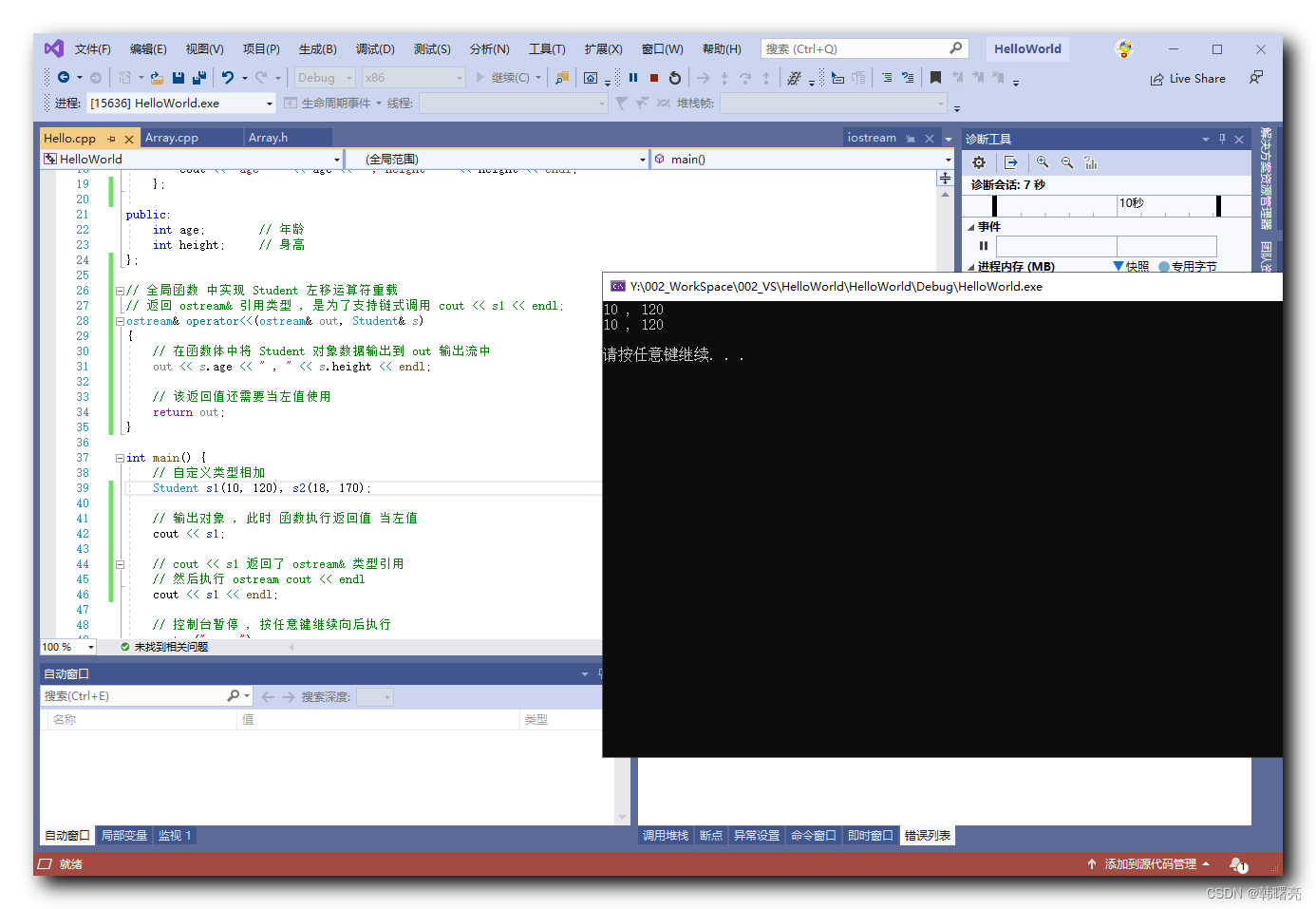
Use RSA to find the secret message使用脚本
import gmpy2
e = 65537
p = 9648423029010515676590551740010426534945737639235739800643989352039852507298491399561035009163427050370107570733633350911691280297777160200625281665378483
q = 11874843837980297032092405848653656852760910154543380907650040190704283358909208578251063047732443992230647903887510065547947313543299303261986053486569407
n = p * q
# 密文
C = 83208298995174604174773590298203639360540024871256126892889661345742403314929861939100492666605647316646576486526217457006376842280869728581726746401583705899941768214138742259689334840735633553053887641847651173776251820293087212885670180367406807406765923638973161375817392737747832762751690104423869019034
d = gmpy2.invert(e, (p - 1) * (q - 1))
print(d)
# 求明文
M = pow(C, d, n) # 快速求幂取模运算 pow(a,b,c)为a的b次方再对c取余
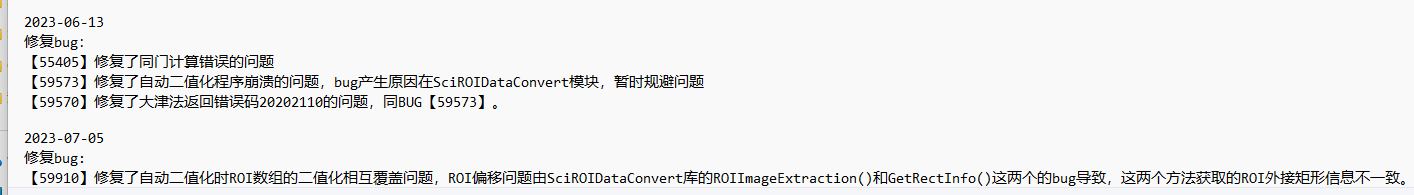
print(M)12行是d的值,第三行是flag 即m

windows系统密码
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
ctf:1002:06af9108f2e1fecf144e2e8adef09efd:a7fcb22a88038f35a8f39d503e7f0062:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SUPPORT_388945a0:1001:aad3b435b51404eeaad3b435b51404ee:bef14eee40dffbc345eeb3f58e290d56:::别人说这个都是32位的比较符合md5加密
使用md5在线解密破解,md5解密加密
信息化时代的步伐
我都惊呆了

606046152623600817831216121621196386数字跟中文互相转换,用中文电码
中文电码查询 Chinese Commercial Code - 标准电报码免费在线查询|姓名电码|美国签证电码
凯撒?替换?呵呵!
MTHJ{CUBCGXGUGXWREXIPOYAOEYFIGXWRXCHTKHFCOHCFDUCGTXZOHIXOEOWMEHZO} 其实格式很明显了,因为就是有{}
第一个m变成f移动七位,t变成l移动8位。是依次增加的,其实写个脚本也是可以实现的
看到有个在线解密,就是可以给他按怎样的方式解密,有参考的加密方式,挺方便的
解出来的第一个就是了,去掉空格,外包flag
quipqiup - cryptoquip and cryptogram solver
萌萌哒的八戒

搜了搜,有猪圈密码
对照

传统知识+古典密码
小明某一天收到一封密信,信中写了几个不同的年份
辛卯,癸巳,丙戌,辛未,庚辰,癸酉,己卯,癸巳。
信的背面还写有“+甲子”,请解出这段密文。
key值:CTF{XXX}
这就是六十甲子解密,查找对应的数字,然后+甲子就是加60
辛卯28,癸巳30,丙戌23,辛未08,庚辰17,癸酉10,己卯16,癸巳30
加上60,对应ascii码:XZSDMFLZ

栅栏密码解密

然后使用凯撒
 flag{SHUANGYU}
flag{SHUANGYU}

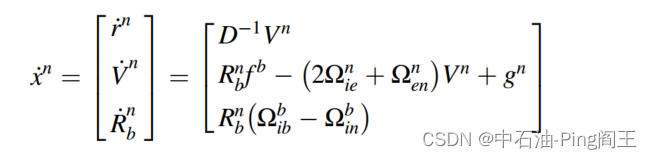


![socket.error: [Errno 10049]错误](https://img-blog.csdnimg.cn/eba3ada035f14233b92c5b963b452be3.png)