文章目录
- TCP三次握手/TCP三次挥手
- TCP三次握手
- TCP四次挥手
- 完整报文
- 实例代码
- HttpSampleClient
- HttpSampleServer
- HttpsSampleClient
- HttpsSampleServer
- TcpSampleClient
- TcpSampleServer
- UdpSampleClient
- UdpSampleSever
- 资料
TCP三次握手/TCP三次挥手
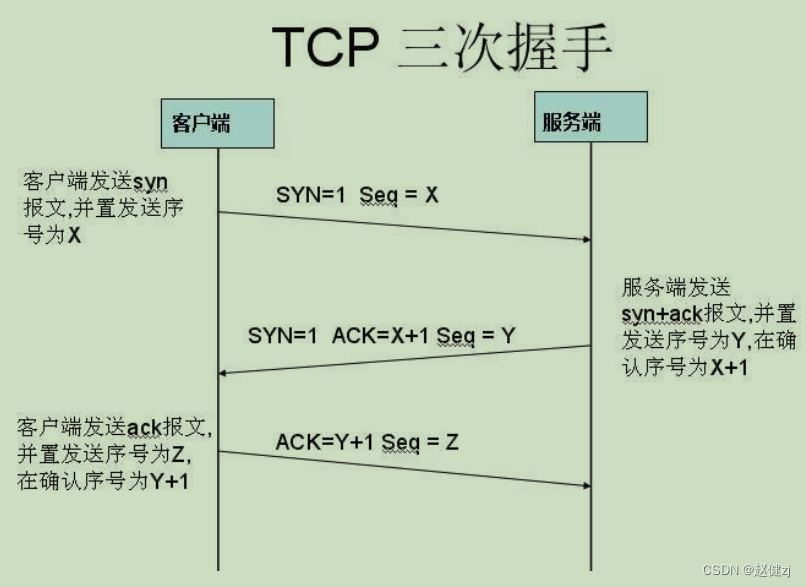
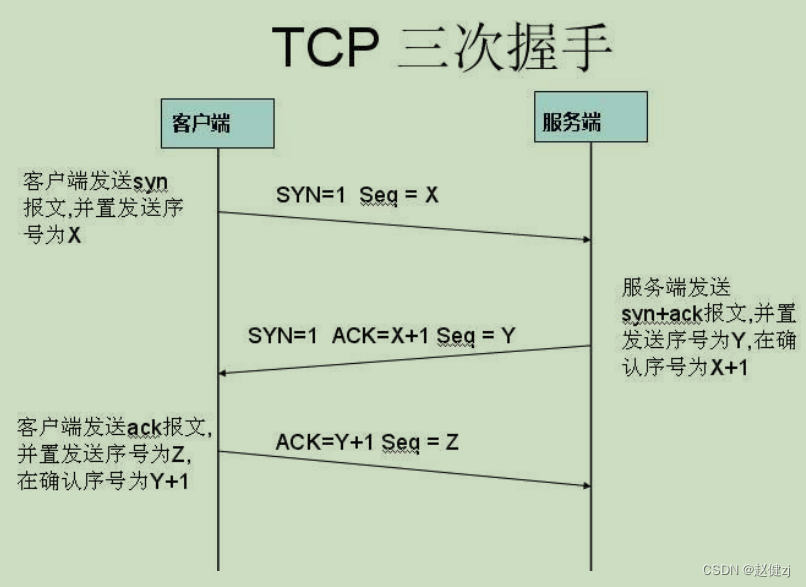
“三次握手”的目的是“为了防止已失效的连接请求报文段突然又传送到了服务端,因而产生 错误”。主要目的防止 server 端一直等待,浪费资源。换句话说,即是为了保证服务端能收 接受到客户端的信息并能做出正确的应答而进行前两次(第一次和第二次)握手,为了保证客 户端能够接收到服务端的信息并能做出正确的应答而进行后两次(第二次和第三次)握手。
“四次挥手”原因是因为 tcp 是全双工模式,接收到 FIN 时意味将没有数据再发来,但是还是 可以继续发送数据。
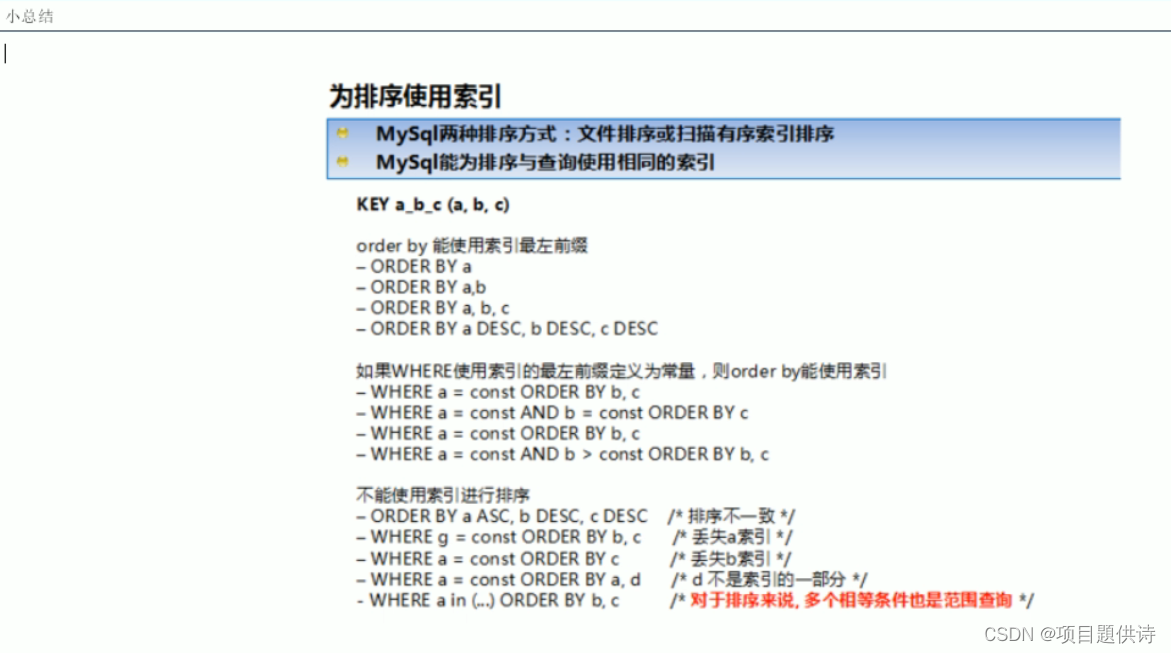
TCP三次握手
TCP四次挥手
完整报文
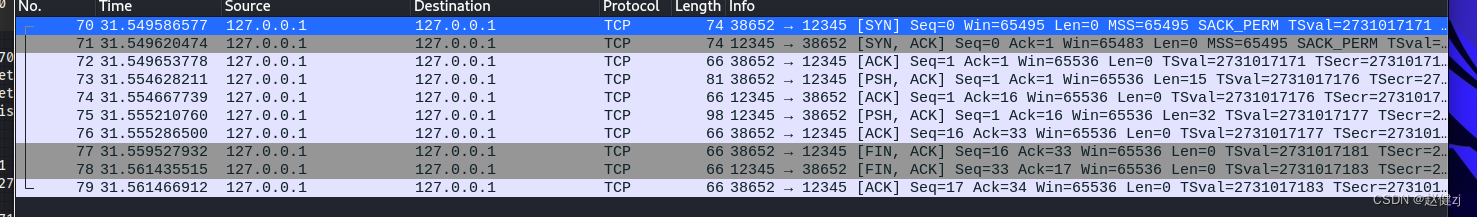
# 三次握手:SYN=1 Seq=0
No. Time Source Destination Protocol Length Info
50 7.055660280 127.0.0.1 127.0.0.1 TCP 74 44156 → 12345 [SYN] Seq=0 Win=65495 Len=0 MSS=65495 SACK_PERM TSval=2731439096 TSecr=0 WS=128
Frame 50: 74 bytes on wire (592 bits), 74 bytes captured (592 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.312489778 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.312489778 seconds
[Time delta from previous captured frame: 0.004110298 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 7.055660280 seconds]
Frame Number: 50
Frame Length: 74 bytes (592 bits)
Capture Length: 74 bytes (592 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: TCP SYN/FIN]
[Coloring Rule String: tcp.flags & 0x02 || tcp.flags.fin == 1]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 0, Len: 0
# 三次握手:SYN1 ACK=1 Seq=0
No. Time Source Destination Protocol Length Info
51 7.055692471 127.0.0.1 127.0.0.1 TCP 74 12345 → 44156 [SYN, ACK] Seq=0 Ack=1 Win=65483 Len=0 MSS=65495 SACK_PERM TSval=2731439096 TSecr=2731439096 WS=128
Frame 51: 74 bytes on wire (592 bits), 74 bytes captured (592 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.312521969 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.312521969 seconds
[Time delta from previous captured frame: 0.000032191 seconds]
[Time delta from previous displayed frame: 0.000032191 seconds]
[Time since reference or first frame: 7.055692471 seconds]
Frame Number: 51
Frame Length: 74 bytes (592 bits)
Capture Length: 74 bytes (592 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: TCP SYN/FIN]
[Coloring Rule String: tcp.flags & 0x02 || tcp.flags.fin == 1]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 12345, Dst Port: 44156, Seq: 0, Ack: 1, Len: 0
# 三次握手:Ack=1 Seq=1
No. Time Source Destination Protocol Length Info
52 7.055725041 127.0.0.1 127.0.0.1 TCP 66 44156 → 12345 [ACK] Seq=1 Ack=1 Win=65536 Len=0 TSval=2731439096 TSecr=2731439096
Frame 52: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.312554539 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.312554539 seconds
[Time delta from previous captured frame: 0.000032570 seconds]
[Time delta from previous displayed frame: 0.000032570 seconds]
[Time since reference or first frame: 7.055725041 seconds]
Frame Number: 52
Frame Length: 66 bytes (528 bits)
Capture Length: 66 bytes (528 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: TCP]
[Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 1, Ack: 1, Len: 0
# 客户端发送消息 Hello, server!.
No. Time Source Destination Protocol Length Info
53 7.057834891 127.0.0.1 127.0.0.1 TCP 81 44156 → 12345 [PSH, ACK] Seq=1 Ack=1 Win=65536 Len=15 TSval=2731439098 TSecr=2731439096
Frame 53: 81 bytes on wire (648 bits), 81 bytes captured (648 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.314664389 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.314664389 seconds
[Time delta from previous captured frame: 0.002109850 seconds]
[Time delta from previous displayed frame: 0.002109850 seconds]
[Time since reference or first frame: 7.057834891 seconds]
Frame Number: 53
Frame Length: 81 bytes (648 bits)
Capture Length: 81 bytes (648 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp:data]
[Coloring Rule Name: TCP]
[Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 1, Ack: 1, Len: 15
Data (15 bytes)
0000 48 65 6c 6c 6f 2c 20 73 65 72 76 65 72 21 0a Hello, server!.
# 服务端应答
No. Time Source Destination Protocol Length Info
54 7.057859991 127.0.0.1 127.0.0.1 TCP 66 12345 → 44156 [ACK] Seq=1 Ack=16 Win=65536 Len=0 TSval=2731439098 TSecr=2731439098
Frame 54: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.314689489 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.314689489 seconds
[Time delta from previous captured frame: 0.000025100 seconds]
[Time delta from previous displayed frame: 0.000025100 seconds]
[Time since reference or first frame: 7.057859991 seconds]
Frame Number: 54
Frame Length: 66 bytes (528 bits)
Capture Length: 66 bytes (528 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: TCP]
[Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 12345, Dst Port: 44156, Seq: 1, Ack: 16, Len: 0
# 服务端发送消息 Server received: Hello, server!.
No. Time Source Destination Protocol Length Info
55 7.059237157 127.0.0.1 127.0.0.1 TCP 98 12345 → 44156 [PSH, ACK] Seq=1 Ack=16 Win=65536 Len=32 TSval=2731439100 TSecr=2731439098
Frame 55: 98 bytes on wire (784 bits), 98 bytes captured (784 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.316066655 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.316066655 seconds
[Time delta from previous captured frame: 0.001377166 seconds]
[Time delta from previous displayed frame: 0.001377166 seconds]
[Time since reference or first frame: 7.059237157 seconds]
Frame Number: 55
Frame Length: 98 bytes (784 bits)
Capture Length: 98 bytes (784 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp:data]
[Coloring Rule Name: TCP]
[Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 12345, Dst Port: 44156, Seq: 1, Ack: 16, Len: 32
Data (32 bytes)
0000 53 65 72 76 65 72 20 72 65 63 65 69 76 65 64 3a Server received:
0010 20 48 65 6c 6c 6f 2c 20 73 65 72 76 65 72 21 0a Hello, server!.
# 客户端还给了一个回应
No. Time Source Destination Protocol Length Info
56 7.059273656 127.0.0.1 127.0.0.1 TCP 66 44156 → 12345 [ACK] Seq=16 Ack=33 Win=65536 Len=0 TSval=2731439100 TSecr=2731439100
Frame 56: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.316103154 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.316103154 seconds
[Time delta from previous captured frame: 0.000036499 seconds]
[Time delta from previous displayed frame: 0.000036499 seconds]
[Time since reference or first frame: 7.059273656 seconds]
Frame Number: 56
Frame Length: 66 bytes (528 bits)
Capture Length: 66 bytes (528 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: TCP]
[Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 16, Ack: 33, Len: 0
# 四次挥手 1 FIN=1 Ack=33 Seq=16
No. Time Source Destination Protocol Length Info
57 7.062253079 127.0.0.1 127.0.0.1 TCP 66 44156 → 12345 [FIN, ACK] Seq=16 Ack=33 Win=65536 Len=0 TSval=2731439103 TSecr=2731439100
Frame 57: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.319082577 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.319082577 seconds
[Time delta from previous captured frame: 0.002979423 seconds]
[Time delta from previous displayed frame: 0.002979423 seconds]
[Time since reference or first frame: 7.062253079 seconds]
Frame Number: 57
Frame Length: 66 bytes (528 bits)
Capture Length: 66 bytes (528 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: TCP SYN/FIN]
[Coloring Rule String: tcp.flags & 0x02 || tcp.flags.fin == 1]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 16, Ack: 33, Len: 0
# 四次挥手 2 ACK=17 Seq=33
No. Time Source Destination Protocol Length Info
58 7.110165407 127.0.0.1 127.0.0.1 TCP 66 12345 → 44156 [ACK] Seq=33 Ack=17 Win=65536 Len=0 TSval=2731439151 TSecr=2731439103
Frame 58: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.366994905 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.366994905 seconds
[Time delta from previous captured frame: 0.047912328 seconds]
[Time delta from previous displayed frame: 0.047912328 seconds]
[Time since reference or first frame: 7.110165407 seconds]
Frame Number: 58
Frame Length: 66 bytes (528 bits)
Capture Length: 66 bytes (528 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: TCP]
[Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 12345, Dst Port: 44156, Seq: 33, Ack: 17, Len: 0
# 四次挥手: 3 Fin=1 Ack=17 Seq=33
No. Time Source Destination Protocol Length Info
61 7.390471256 127.0.0.1 127.0.0.1 TCP 66 12345 → 44156 [FIN, ACK] Seq=33 Ack=17 Win=65536 Len=0 TSval=2731439431 TSecr=2731439103
Frame 61: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.647300754 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.647300754 seconds
[Time delta from previous captured frame: 0.000234452 seconds]
[Time delta from previous displayed frame: 0.280305849 seconds]
[Time since reference or first frame: 7.390471256 seconds]
Frame Number: 61
Frame Length: 66 bytes (528 bits)
Capture Length: 66 bytes (528 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: TCP SYN/FIN]
[Coloring Rule String: tcp.flags & 0x02 || tcp.flags.fin == 1]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 12345, Dst Port: 44156, Seq: 33, Ack: 17, Len: 0
# 四次挥手 4 Ack=34 Seq=17
No. Time Source Destination Protocol Length Info
62 7.390499061 127.0.0.1 127.0.0.1 TCP 66 44156 → 12345 [ACK] Seq=17 Ack=34 Win=65536 Len=0 TSval=2731439431 TSecr=2731439431
Frame 62: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0
Section number: 1
Interface id: 0 (lo)
Encapsulation type: Ethernet (1)
Arrival Time: Aug 29, 2023 08:26:32.647328559 EDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1693311992.647328559 seconds
[Time delta from previous captured frame: 0.000027805 seconds]
[Time delta from previous displayed frame: 0.000027805 seconds]
[Time since reference or first frame: 7.390499061 seconds]
Frame Number: 62
Frame Length: 66 bytes (528 bits)
Capture Length: 66 bytes (528 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: TCP]
[Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 17, Ack: 34, Len: 0
实例代码
HttpSampleClient
import java.io.BufferedReader;
import java.io.InputStreamReader;
import java.net.HttpURLConnection;
import java.net.URL;
public class HttpSampleClient {
public static void main(String[] args) {
try {
URL url = new URL("http://localhost:8080");
HttpURLConnection connection = (HttpURLConnection) url.openConnection();
connection.setRequestMethod("GET");
int responseCode = connection.getResponseCode();
System.out.println("Response Code:" + responseCode);
// read content
BufferedReader reader = new BufferedReader(new InputStreamReader(connection.getInputStream()));
String line;
StringBuilder response = new StringBuilder();
while ((line = reader.readLine()) != null) {
response.append(line);
}
reader.close();
System.out.println("Response Body: " + response);
connection.disconnect();
} catch (Exception e) {
e.printStackTrace();
}
}
}
HttpSampleServer
import com.sun.net.httpserver.HttpExchange;
import com.sun.net.httpserver.HttpHandler;
import com.sun.net.httpserver.HttpServer;
import java.io.IOException;
import java.io.OutputStream;
import java.net.InetSocketAddress;
public class HttpSampleServer {
public static void main(String[] args) {
try {
// create http server to bind 8080
HttpServer server = HttpServer.create(new InetSocketAddress("127.0.0.1", 8080), 0);
// bind path
server.createContext("/", new MyHandler());
server.start();
System.out.println("Http Sever started on port 8080");
} catch (Exception e) {
e.printStackTrace();
}
}
static class MyHandler implements HttpHandler {
// 设置响应头c
@Override
public void handle(HttpExchange exchange) throws IOException {
String response = "Hello from the local HTTP server!";
exchange.sendResponseHeaders(200, response.getBytes().length);
// 获取输出流并写入响应内容
OutputStream os = exchange.getResponseBody();
os.write(response.getBytes());
os.close();
}
}
}
HttpsSampleClient
import javax.net.ssl.*;
import java.io.BufferedReader;
import java.io.InputStreamReader;
import java.io.PrintWriter;
public class HttpsSampleClient {
public static void main(String[] args) {
try {
// Create and configure the SSL context
SSLContext sslContext = SSLContext.getInstance("TLS");
sslContext.init(null, new TrustManager[]{new X509TrustManager() {
public java.security.cert.X509Certificate[] getAcceptedIssuers() {
return null;
}
public void checkClientTrusted(java.security.cert.X509Certificate[] certs, String authType) {
}
public void checkServerTrusted(java.security.cert.X509Certificate[] certs, String authType) {
}
}}, new java.security.SecureRandom());
// Create an SSL socket
SSLSocketFactory sslSocketFactory = sslContext.getSocketFactory();
SSLSocket socket = (SSLSocket) sslSocketFactory.createSocket("localhost", 12345);
// Get input and output streams for secure communication
BufferedReader reader = new BufferedReader(new InputStreamReader(socket.getInputStream()));
PrintWriter writer = new PrintWriter(socket.getOutputStream(), true); // autoFlush
// Send a message to the server
String message = "Hello, server!";
writer.println(message);
// Read response from the server
String serverResponse = reader.readLine();
System.out.println("Server response: " + serverResponse);
// Close resources
reader.close();
writer.close();
socket.close();
} catch (Exception e) {
e.printStackTrace();
}
}
}
HttpsSampleServer
import javax.net.ssl.*;
import java.io.BufferedReader;
import java.io.FileInputStream;
import java.io.InputStreamReader;
import java.io.PrintWriter;
import java.security.KeyStore;
public class HttpsSampleServer {
public static void main(String[] args) {
String keystorePath = "./keystore.jks";
char[] keystorePassword = "flannery".toCharArray();
try {
// Load the keystore containing the server's SSL certificate
KeyStore keystore = KeyStore.getInstance("JKS");
keystore.load(new FileInputStream(keystorePath), keystorePassword);
// Create and configure the SSL context
KeyManagerFactory kmf = KeyManagerFactory.getInstance("SunX509");
kmf.init(keystore, keystorePassword);
SSLContext sslContext = SSLContext.getInstance("TLS");
sslContext.init(kmf.getKeyManagers(), null, null);
// Create an SSL server socket
SSLServerSocketFactory sslServerSocketFactory = sslContext.getServerSocketFactory();
SSLServerSocket serverSocket = (SSLServerSocket) sslServerSocketFactory.createServerSocket(12345);
System.out.println("Server listening on port 12345...");
// Wait for a client to connect
SSLSocket clientSocket = (SSLSocket) serverSocket.accept();
System.out.println("Client connected: " + clientSocket.getInetAddress().getHostAddress());
// Get input and output streams for secure communication
BufferedReader reader = new BufferedReader(new InputStreamReader(clientSocket.getInputStream()));
PrintWriter writer = new PrintWriter(clientSocket.getOutputStream(), true); // autoFlush
// Read data from client and respond
String clientMessage;
while ((clientMessage = reader.readLine()) != null) {
System.out.println("Received from client: " + clientMessage);
writer.println("Server received: " + clientMessage);
}
// Close resources
reader.close();
writer.close();
clientSocket.close();
serverSocket.close();
} catch (Exception e) {
e.printStackTrace();
}
}
}
TcpSampleClient
import java.io.*;
import java.net.Socket;
public class TcpSampleClient {
public static void main(String[] args) {
try {
// Create a socket to connect to the server
Socket socket = new Socket("localhost", 12345);
// Get input and output streams for the socket
InputStream inputStream = socket.getInputStream();
OutputStream outputStream = socket.getOutputStream();
// Create readers and writers for easier communication
BufferedReader reader = new BufferedReader(new InputStreamReader(inputStream));
PrintWriter writer = new PrintWriter(outputStream, true); // autoFlush
// Send a message to the server
String message = "Hello, server!";
writer.println(message);
// Read response from the server
String serverResponse = reader.readLine();
System.out.println("Server response: " + serverResponse);
// Close resources
reader.close();
writer.close();
socket.close();
} catch (IOException e) {
e.printStackTrace();
}
}
}
TcpSampleServer
import java.io.*;
import java.net.ServerSocket;
import java.net.Socket;
public class TcpSampleServer {
public static void main(String[] args) {
extracted();
}
private static void extracted() {
try {
// Create a server socket
ServerSocket serverSocket = new ServerSocket(12345);
System.out.println("Server listening on port 12345...");
// Wait for a client to connect
Socket clientSocket = serverSocket.accept();
System.out.println("Client connected: " + clientSocket.getInetAddress().getHostAddress());
// Get input and output streams for the socket
InputStream inputStream = clientSocket.getInputStream();
OutputStream outputStream = clientSocket.getOutputStream();
// Create readers and writers for easier communication
BufferedReader reader = new BufferedReader(new InputStreamReader(inputStream));
PrintWriter writer = new PrintWriter(outputStream, true); // autoFlush
// Read data from client and respond
String clientMessage;
while ((clientMessage = reader.readLine()) != null) {
System.out.println("Received from client: " + clientMessage);
writer.println("Server received: " + clientMessage);
}
// Close resources
//reader.close();
//writer.close();
//clientSocket.close();
//serverSocket.close();
} catch (IOException e) {
e.printStackTrace();
}
}
}
UdpSampleClient
import java.io.IOException;
import java.net.DatagramPacket;
import java.net.DatagramSocket;
import java.net.InetAddress;
public class UdpSampleClient {public static void main(String[] args) {
try {
DatagramSocket clientSocket = new DatagramSocket();
String message = "Hello, server!";
byte[] sendData = message.getBytes();
InetAddress serverAddress = InetAddress.getByName("localhost");
int serverPort = 12345;
DatagramPacket sendPacket = new DatagramPacket(sendData, sendData.length, serverAddress, serverPort);
clientSocket.send(sendPacket);
byte[] receiveData = new byte[1024];
DatagramPacket receivePacket = new DatagramPacket(receiveData, receiveData.length);
clientSocket.receive(receivePacket);
String serverResponse = new String(receivePacket.getData(), 0, receivePacket.getLength());
System.out.println("Server response: " + serverResponse);
clientSocket.close();
} catch (IOException e) {
e.printStackTrace();
}
}
}
UdpSampleSever
import java.io.IOException;
import java.net.DatagramPacket;
import java.net.DatagramSocket;
import java.net.InetAddress;
public class UdpSampleSever {
public static void main(String[] args) {
try {
DatagramSocket serverSocket = new DatagramSocket(12345);
System.out.println("Server listening on port 12345...");
byte[] receiveData = new byte[1024];
while (true) {
DatagramPacket receivePacket = new DatagramPacket(receiveData, receiveData.length);
serverSocket.receive(receivePacket);
String clientMessage = new String(receivePacket.getData(), 0, receivePacket.getLength());
System.out.println("Received from client: " + clientMessage);
InetAddress clientAddress = receivePacket.getAddress();
int clientPort = receivePacket.getPort();
String serverResponse = "Server received: " + clientMessage;
byte[] sendData = serverResponse.getBytes();
DatagramPacket sendPacket = new DatagramPacket(sendData, sendData.length, clientAddress, clientPort);
serverSocket.send(sendPacket);
}
} catch (IOException e) {
e.printStackTrace();
}
}
}
资料
超详细的wireshark抓包使用教程
jks证书文件的生成步骤
如何使用wireshark抓取HTTPS数据包?
wireshark抓包分析HTTPS
Burp Suite的基本介绍及使用
渗透测试工具Burp Suite详解
vmware ctrl键粘滞的问题
wireshark过滤规则
Burp Suite HTTPS详解