环境说明
ubuntu18.04.1、openssl指令需要支持
openssl生成CA(Certificate Authority)
生成RSA Private Key
openssl genrsa -out ca.key
输出信息
$ openssl genrsa -out ca.key
Generating RSA private key, 2048 bit long modulus (2 primes)
........................................................................................+++++
.............................................................................................+++++
e is 65537 (0x010001)
备注:默认是2048 bit,也可以指定为4096,指令如下
openssl genrsa -out ca.key 4096生成CA证书
CA配置文件
新建ca.conf文件,然后添加以下内容
basicConstraints = CA:TRUE
keyUsage = cRLSign, keyCertSign
[req]
distinguished_name = req_distinguished_name
prompt = no
[req_distinguished_name]
C = CN
ST = GuangDong
L = ShenZhen
CN = My Test Root CAC:表示国家 ST是省份 L是区域 CN是Common Name,CN将会显示到证书路径
生成证书指令
openssl req -x509 -new -sha512 -nodes -key ca.key -days 3650 -out ca.crt -config ca.conf-x509 :输出证书而不是证书签名请求 (CSR)。
-sha512: 指定将用于对证书进行签名的哈希函数。此处可以使用其他值,例如 sha256 和 sha384。
-nodes :表示证书应未加密。
-key ca.key :指定我们用来签名的私钥。
-days 3650:指定证书的有效天数,3650=10年。
-out ca.crt :指定输出文件名。
-config ca.conf :指定了我们希望使用的配置文件。
执行之后,在当前目录下生成如下文件
$ ls
ca.crt ca.keyOpenssl创建主机证书(Host Certificate)
生成RSA Private Key
openssl genrsa -out server.key输出信息
$ openssl genrsa -out server.key
Generating RSA private key, 2048 bit long modulus (2 primes)
..........................................+++++
............................................................................+++++
e is 65537 (0x010001)备注:2048 bits是标准大小,也可以指定为4096 bits,指令如下
openssl genrsa -out server.key 4096生成CSR(Certificate Signing Request)
新建CSR配置文件
创建server.conf,添加以下内容
[req]
default_md = sha512
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
[req]
distinguished_name = req_distinguished_name
req_extensions = req_ext
prompt = no
[req_distinguished_name]
C = CN
ST = GuangDong
L = ShenZhen
O = My Company
OU = My Division
CN = mytesting.cn
[req_ext]
subjectAltName = @dns_dir_names
[dns_dir_names]
DNS.1 = mytesting.cn
DNS.2 = *.mytesting.cn创建CSR
openssl req -new -sha512 -nodes -key server.key -out server.csr -config server.conf生成csr和key
server.csr server.key
生成证书
新建配置文件
修改配置参数server_ext.conf,添加以下内容
basicConstraints = CA:FALSE
nsCertType = server
nsComment = "My webserver Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer:always
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @dns_dir_names
[dns_dir_names]
DNS.1 = mytesting.cn
DNS.2 = *.mytesting.cn签名CSR
openssl x509 -req -sha512 -days 3650 -in server.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out server.crt -extfile server_ext.conf生成文件server.crt,webserver需要server.crt和server.key
生成pem证书文件
openssl x509 -in server.crt -out server.pem -outform PEM文件名称server.pem,webserver使用需要用到server.key和server.pem
合并server.key和server.pem到一个文件
cat server.key >> server.pem 查看证书内容
openssl x509 -in server.pem -noout -text
$ openssl x509 -in server.pem -noout -text
Certificate:
Data:
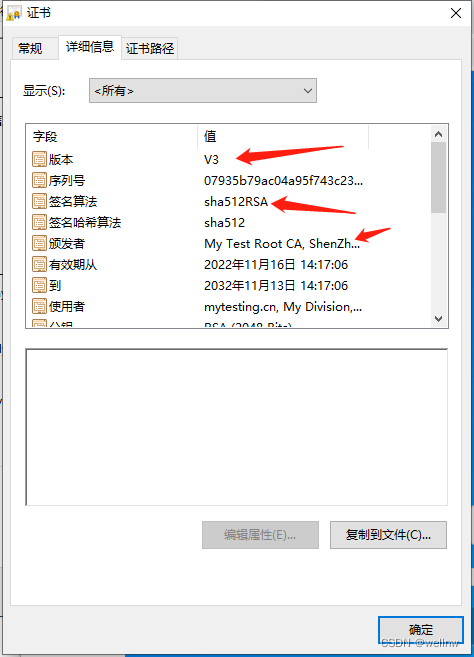
Version: 3 (0x2)
Serial Number:
07:93:5b:79:ac:04:a9:5f:74:3c:23:4c:fd:5c:28:8d:b3:2e:a7:12
Signature Algorithm: sha512WithRSAEncryption
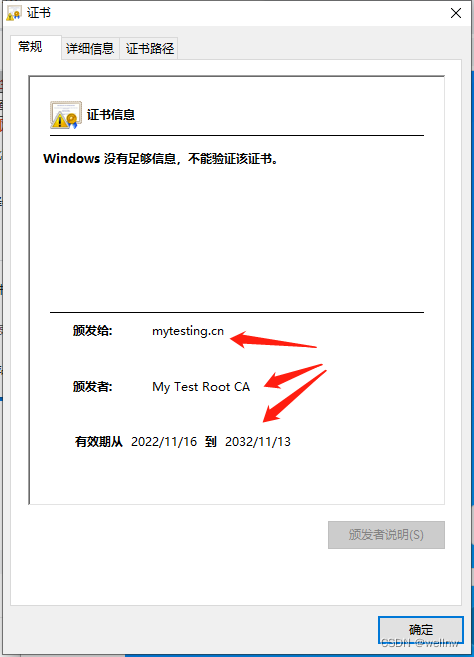
Issuer: C = CN, ST = GuangDong, L = ShenZhen, CN = My Test Root CA
Validity
Not Before: Nov 16 06:17:06 2022 GMT
Not After : Nov 13 06:17:06 2032 GMT
Subject: C = CN, ST = GuangDong, L = ShenZhen, O = My Company, OU = My Division, CN = mytesting.cn
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:ad:d3:c8:78:16:0a:f3:f2:de:50:33:94:5b:0b:
64:71:a1:76:e6:37:2c:09:6b:7e:35:8e:6d:10:1e:
3e:9c:75:c0:e6:0d:b1:4e:32:8d:21:80:b6:4c:f4:
45:07:5a:67:e4:fd:af:de:4d:1f:c5:92:f5:d3:52:
78:ef:2c:58:b6:42:0d:f6:aa:9a:b4:64:1a:33:e7:
76:93:4c:8d:ab:1e:b3:d4:35:12:45:5d:f7:53:c4:
a3:60:bf:78:5d:c9:15:f8:1c:22:af:c2:dc:3a:d5:
10:94:6e:3c:32:05:7b:8e:f3:d2:4a:7b:c2:8d:11:
dd:6b:35:38:cd:0e:26:ec:5b:8f:92:47:64:dd:68:
e7:6a:aa:12:bc:2b:97:f8:f5:a5:3e:e5:c9:9d:a5:
2a:ce:51:2f:74:28:ce:dd:44:33:d9:b2:17:f2:a0:
72:57:9f:70:ae:1f:96:4c:30:6c:2b:16:e2:20:de:
86:cf:b6:6a:13:40:fb:7d:07:04:80:a6:85:ae:72:
a2:c9:11:75:30:a7:f0:10:7b:82:63:aa:f9:44:e5:
5f:c3:6b:42:46:17:8d:d2:33:c1:be:d1:81:2c:13:
97:dd:3d:8f:98:3a:fe:b6:da:f3:21:8e:d0:a8:b5:
6e:93:87:9e:54:5f:51:78:03:e3:48:54:de:c2:21:
e5:d9
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Cert Type:
SSL Server
Netscape Comment:
My webserver Certificate
X509v3 Subject Key Identifier:
1C:D9:B5:4E:17:C7:3F:DC:B3:13:FA:D2:27:DB:3D:62:C9:68:5E:51
X509v3 Authority Key Identifier:
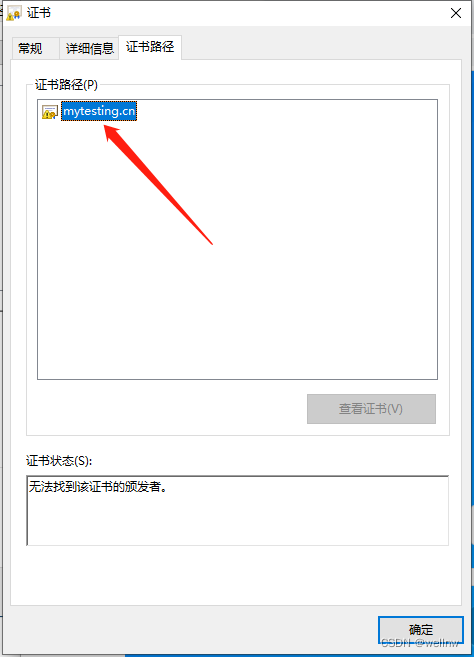
DirName:/C=CN/ST=GuangDong/L=ShenZhen/CN=My Test Root CA
serial:2E:17:36:B8:DE:A6:EA:76:90:DE:EE:09:37:7D:DA:AE:FE:1D:48:68
X509v3 Key Usage:
Digital Signature, Non Repudiation, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Subject Alternative Name:
DNS:mytesting.cn, DNS:*.mytesting.cn
Signature Algorithm: sha512WithRSAEncryption
b5:05:8c:83:8c:d8:58:13:9f:5f:4f:60:c9:94:34:4c:87:49:
8a:65:74:c4:18:ea:0b:3d:3b:61:3a:5f:ee:4b:1a:93:7d:07:
84:b7:08:5b:ee:22:7c:06:9c:ce:ec:d9:29:26:6d:fa:52:14:
b3:ad:b3:dd:46:ab:61:aa:66:6c:e6:17:42:d1:43:f3:ef:e4:
fb:1f:37:1e:cb:1e:f0:71:c1:28:97:22:45:c2:8b:d1:0d:7b:
72:45:27:06:93:68:33:e2:62:4e:39:e8:60:82:c2:f8:2b:30:
69:8e:31:d0:bd:43:20:51:07:e6:76:fd:5b:7a:56:38:56:de:
0a:7b:46:f3:84:e4:3b:10:c6:6a:8a:0b:28:ca:7d:a2:0f:7b:
03:0c:de:6b:e1:d5:c6:23:dc:f5:83:af:29:95:39:8a:ec:38:
61:09:0d:b6:95:6a:d3:49:17:a8:cc:96:d6:bf:9a:5d:f4:ed:
78:5f:c1:71:a6:a9:43:94:51:72:82:40:5f:d7:d4:1b:30:56:
97:a1:b3:80:2b:36:4f:3d:3b:5a:a0:1e:3c:02:ad:31:d8:42:
18:0a:84:04:31:05:91:0d:e8:70:ec:ce:43:d3:85:73:47:a7:
d5:39:48:5f:93:fc:03:56:e8:ce:67:2b:36:7f:bf:ac:61:d4:
f3:f6:d7:b8
lighttpd增加支持https修改
修改lighttpd.conf配置
在server.modules 中增加mod_openssl,同时增加以下配置
$SERVER["socket"] == "0.0.0.0:443" {
ssl.engine = "enable"
ssl.pemfile = "/var/lighttpd/server-crt.pem"
server.document-root = "/tmp/www/"
}
重启lighttpd服务器
lighttpd -f /var/lighttpd/lighttpd.conf &
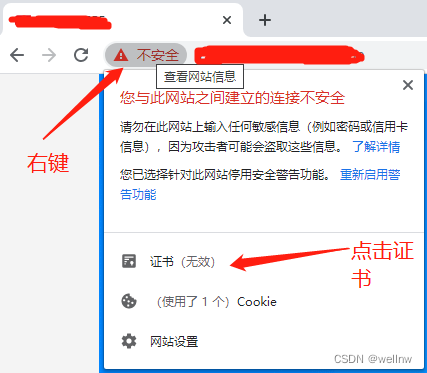
测试
使用google浏览器,访问webserver





![[附源码]计算机毕业设计JAVA房屋租赁管理系统](https://img-blog.csdnimg.cn/31dc35b8dea64614a8f2c16c4fe14b59.png)