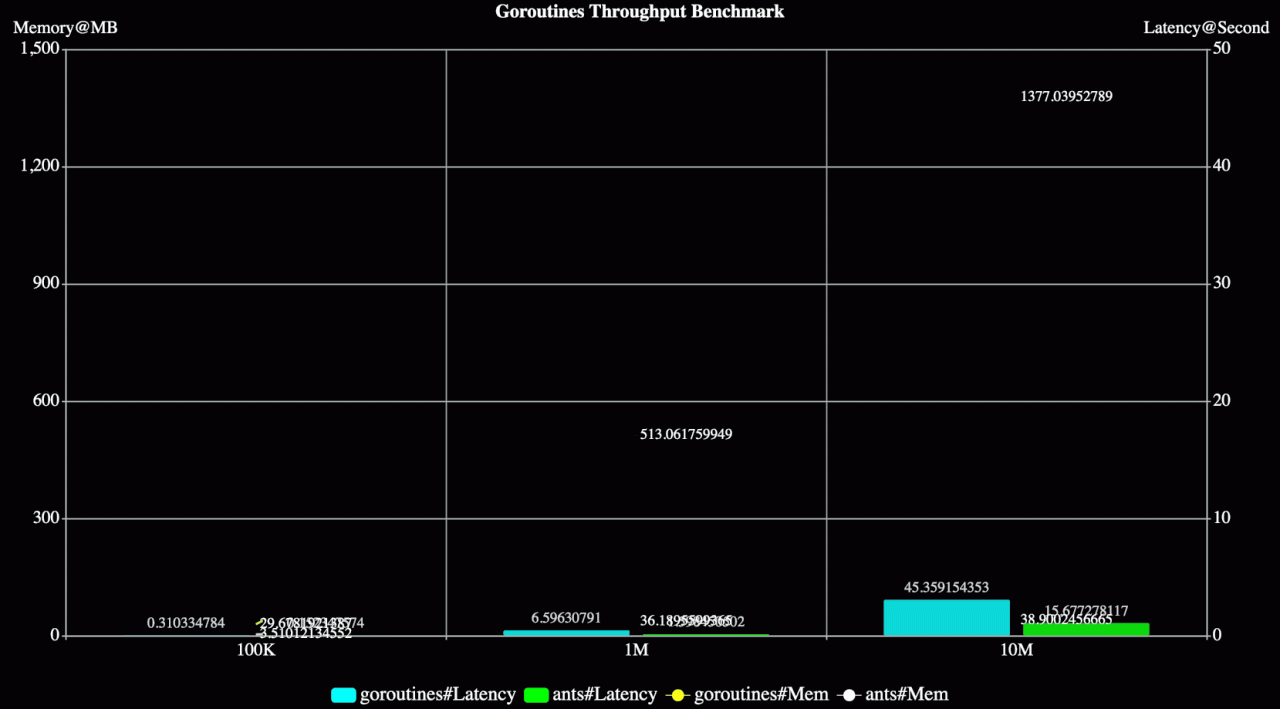
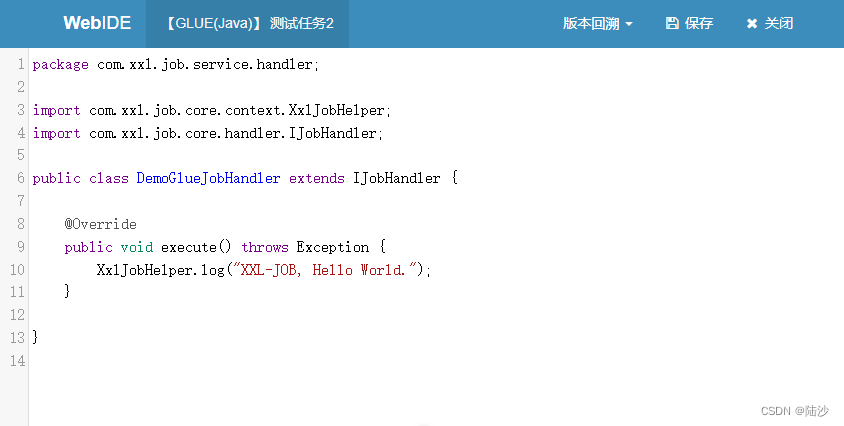
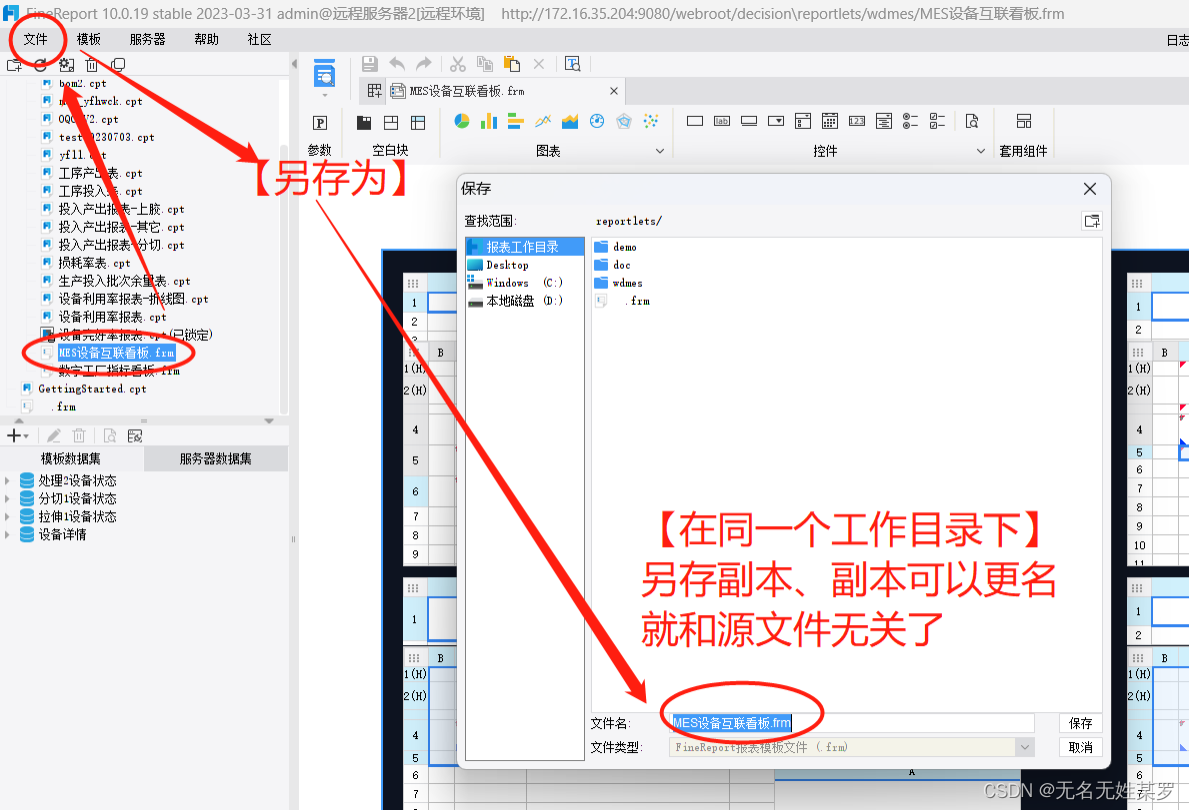
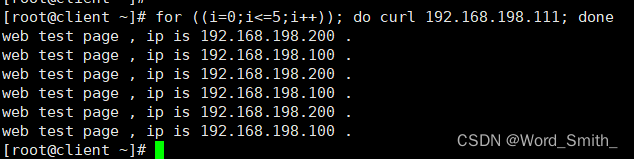
你是否希望使用 SSL/TLS 证书来保护你的 Elasticsearch 部署? 在本文中,我们将指导你完成为 Elasticsearch 创建 PEM 和 P12 证书的过程。 这些证书在建立安全连接和确保 Elasticsearch 集群的完整性方面发挥着至关重要的作用。
友情提示:你可以选择其中一种方法来在你的环境中创建和使用证书。
方法一:创建 P12 证书
如果你还没有安装好自己的 Elasticsearch 的话,请参考之前的文章 “如何在 Linux,MacOS 及 Windows 上进行安装 Elasticsearch”。在安装完 Elasticsearch 后,我们进行如下的步骤:
创建 CA 证书
./bin/elasticsearch-certutil ca$ pwd
/Users/liuxg/elastic/elasticsearch-8.9.0
$ ./bin/elasticsearch-certutil ca
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.
The 'ca' mode generates a new 'certificate authority'
This will create a new X.509 certificate and private key that can be used
to sign certificate when running in 'cert' mode.
Use the 'ca-dn' option if you wish to configure the 'distinguished name'
of the certificate authority
By default the 'ca' mode produces a single PKCS#12 output file which holds:
* The CA certificate
* The CA's private key
If you elect to generate PEM format certificates (the -pem option), then the output will
be a zip file containing individual files for the CA certificate and private key
Please enter the desired output file [elastic-stack-ca.p12]:
Enter password for elastic-stack-ca.p12 :
$ ls
LICENSE.txt bin elastic-stack-ca.p12 logs
NOTICE.txt config jdk.app modules
README.asciidoc data lib plugins从上面的的输出中,我们可以看到多了一个叫做 elastic-stack-ca.p12 的文件。生成的过程中,我们可以使用自己喜欢的 password 来加密这个证书。
默认情况下,“ca” 模式生成一个 PKCS#12 输出文件,其中包含:
- CA 证书
- CA 的私钥
我们可以通过如下的命令来进行检查:
$ keytool -keystore elastic-stack-ca.p12 -list
Enter keystore password:
Keystore type: PKCS12
Keystore provider: SUN
Your keystore contains 1 entry
ca, Aug 8, 2023, PrivateKeyEntry,
Certificate fingerprint (SHA-256): 8C:32:23:AB:22:8A:51:96:D8:6D:8C:A1:32:E8:E5:DC:A1:97:A4:59:F3:55:18:EC:A1:E0:EB:96:74:61:D5:81当然,我们也可以使用如下的工具来查看:
openssl pkcs12 -info -nodes -in elastic-stack-ca.p12$ openssl pkcs12 -info -nodes -in elastic-stack-ca.p12
Enter Import Password:
MAC: sha256, Iteration 10000
MAC length: 32, salt length: 20
PKCS7 Data
Shrouded Keybag: PBES2, PBKDF2, AES-256-CBC, Iteration 10000, PRF hmacWithSHA256
Bag Attributes
friendlyName: ca
localKeyID: 54 69 6D 65 20 31 36 39 31 34 36 36 33 36 31 33 35 34
Key Attributes: <No Attributes>
-----BEGIN PRIVATE KEY-----
MIIEvwIBADANBgkqhkiG9w0BAQEFAASCBKkwggSlAgEAAoIBAQDYmz7UmFR83SNN
9SoCPoV9PU5DbTYPDVCFWXNoshsntgkrrhtOqP5a7vAXGT3uVvvN6kEQSVz5jtV5
nZtuTI/xbMDyM76JwZwfD8ncwiuNnfeqGGkHAFMDDSuj2b+dgmiUgadcX1LM1mtj
D8r7ayWJLzVoqZGW5OohUtSE5nbirRHWYg0z7pAFE9eVKXGonJwdr2ps5KIaQeAw
4XwRxsOrfNnI6qOia9LPSuoYhiHHvFGQLg/SApDga3DWWcCvC1Y7G6ThkSmBHJN5
343j9WTyG1zfeKbxX5Y6Kc95CIe5ddafP9YziNBLYfOW3vyRtykw8KCYy6Tv+X6B
7TGcEcgfAgMBAAECggEAB1/U4vmcrSbKNBxyP0lQBu3pyc0TpHq+w9hCLM2DgMKa
mIYahkvY/QRaRpVxalMQl5FJTcik0n1uZYmPTreeK7xluHLSiQlL/pkgm9Q9SPQy
Oyd0y+w5Ta1KtkIl9LLWSws7xQVQLr3nqHCGzjB23EjJkYEHl9+LQqWTRQ/Wx4WU
2q9+SY5Er5nc3XPlzZYif2j61Yl1w97sjFibgVola6Ad0dJ4ALF8EGy9WChQ66NJ
ajoRaN2LMImQZHF2Zt1tM/MwI3czC+3O7tPZOlNZ0UKGeYEUQ/snsvjNhKq4MrwC
tOdFF+opQ2lP6jOrA/b83V9tHQehhj80MxWbGrk2QQKBgQDs33DrNGw4ZspDRi70
5HGoofebZ6uUzffAMRgRp0HTJYnVABLw7FmAwT0LUJdfj0MN8K1FUdKMMxCVRg90
cMDO061gzzfOIpDcAhbzilNXC1DXsE710rk8QMZ7iFY0E9D5CfsOBAljDdKgRzzT
+2hOJ/efbA0s99UKPeDyZ64d2QKBgQDqGN0x2VpXIOLn0srAJx+mwPyrHhBgrGfR
DWwsyMfnJBv5dKOJOhPLRdyPX0k7HLrFyj6Pmki0B/TF8kq0qW3Epy3pWti/VgDJ
YrhZkqjUjhVb4C7/BNTs3kCqyaiucXvaofvymAoTqEpglZ/oYHkqwit6jz18teD7
2ep+IlzCtwKBgQC/MPMRxfR76evkNSf9ns5m0KTtGNaTe1Q4GuhUh25IIYqJFFA1
inALzu2YzmoARcBX5iXVR9/sLeN6uVwMHl5iEtVkyJ1AkwHdswoXdVUjcwzDq5lw
LbA6BAaw+zCpRD1uZjHv9C4nd6bEm/trFwfv3a6vTSWtYDTi2WNSBYGysQKBgQDT
fXMYvgzn+kYEumOCBdaKiH+8+IRDUn7YVxALxbkUEYNUcxPrvhRz6MHCpYs7ZFE4
r+alRfW48BcrXiIv5YHN0FuiHvkCo2hCiHWUNvNgVJznTDopGuxissgpg9ZpAw2q
D/3WxZUU/U10xLia782H27P8HbynFooT/mPjYJf9MQKBgQCqm5fYBhZxTQ5FAZe4
gTdiShx81Nr8cUbTBpVGfK/ADCc+G+67fAK7EYgg2LxcKpHkuy/NNUkcnFYKjvAX
FhLkSA8N/fXsLYi3JgbvFoaKAsb003TcV7/rPM+0Oqcrxy4feJM/2QeYIqpPVtlV
kjUYJSAaHIGiK6OlbBuBWIRzzA==
-----END PRIVATE KEY-----
PKCS7 Encrypted data: PBES2, PBKDF2, AES-256-CBC, Iteration 10000, PRF hmacWithSHA256
Certificate bag
Bag Attributes
friendlyName: ca
localKeyID: 54 69 6D 65 20 31 36 39 31 34 36 36 33 36 31 33 35 34
subject=CN = Elastic Certificate Tool Autogenerated CA
issuer=CN = Elastic Certificate Tool Autogenerated CA
-----BEGIN CERTIFICATE-----
MIIDSjCCAjKgAwIBAgIVALXN3Mz3+RI7lj3cGczFF2T3X3l3MA0GCSqGSIb3DQEB
CwUAMDQxMjAwBgNVBAMTKUVsYXN0aWMgQ2VydGlmaWNhdGUgVG9vbCBBdXRvZ2Vu
ZXJhdGVkIENBMB4XDTIzMDgwODAzNDUyOVoXDTI2MDgwNzAzNDUyOVowNDEyMDAG
A1UEAxMpRWxhc3RpYyBDZXJ0aWZpY2F0ZSBUb29sIEF1dG9nZW5lcmF0ZWQgQ0Ew
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDYmz7UmFR83SNN9SoCPoV9
PU5DbTYPDVCFWXNoshsntgkrrhtOqP5a7vAXGT3uVvvN6kEQSVz5jtV5nZtuTI/x
bMDyM76JwZwfD8ncwiuNnfeqGGkHAFMDDSuj2b+dgmiUgadcX1LM1mtjD8r7ayWJ
LzVoqZGW5OohUtSE5nbirRHWYg0z7pAFE9eVKXGonJwdr2ps5KIaQeAw4XwRxsOr
fNnI6qOia9LPSuoYhiHHvFGQLg/SApDga3DWWcCvC1Y7G6ThkSmBHJN5343j9WTy
G1zfeKbxX5Y6Kc95CIe5ddafP9YziNBLYfOW3vyRtykw8KCYy6Tv+X6B7TGcEcgf
AgMBAAGjUzBRMB0GA1UdDgQWBBRbBxCWijjKV9vJ0sHNxTyXASgguDAfBgNVHSME
GDAWgBRbBxCWijjKV9vJ0sHNxTyXASgguDAPBgNVHRMBAf8EBTADAQH/MA0GCSqG
SIb3DQEBCwUAA4IBAQDLSMpvzOOIjgon3Z+16q9wO9RgwK5AogJjtiYdPcUWSQVU
JWOdJSDEJCGD+N2pse1F46/nfWY1sJRS1/iM5CxKIiYna4HULOzCYhxsk4WK5kZx
wZ5TNx9WW/+rBYiltjwR48DpVQbEAUCtR47LxW/KSqqr2THRXG2Ni/6jFns498nV
IrGOUVLPW7bEpMTWUMmnCxIjgpqY7wO+7ePgu1/zSLghxMQlTgMw4sSskiGDeboz
SKxh27ttk9sStyvDhEUW+eir+peUdY/xoezVViAM7T5UtlT1iQzhZ1JCWbJtQhfV
8Y8wBF2UUo+ZF4SkQ2Pkwodhz4BbHCw9dH1Q+AnW
-----END CERTIFICATE-----我们可以通过如下的命令来查看该证书的有效期:
openssl pkcs12 -in elastic-stack-ca.p12 -nodes -nokeys -clcerts | openssl x509 -enddate -noout$ openssl pkcs12 -in elastic-stack-ca.p12 -nodes -nokeys -clcerts | openssl x509 -enddate -noout
Enter Import Password:
notAfter=Aug 7 03:45:29 2026 GMT创建证书
我们使用如下的命令:
./bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12$ ./bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.
The 'cert' mode generates X.509 certificate and private keys.
* By default, this generates a single certificate and key for use
on a single instance.
* The '-multiple' option will prompt you to enter details for multiple
instances and will generate a certificate and key for each one
* The '-in' option allows for the certificate generation to be automated by describing
the details of each instance in a YAML file
* An instance is any piece of the Elastic Stack that requires an SSL certificate.
Depending on your configuration, Elasticsearch, Logstash, Kibana, and Beats
may all require a certificate and private key.
* The minimum required value for each instance is a name. This can simply be the
hostname, which will be used as the Common Name of the certificate. A full
distinguished name may also be used.
* A filename value may be required for each instance. This is necessary when the
name would result in an invalid file or directory name. The name provided here
is used as the directory name (within the zip) and the prefix for the key and
certificate files. The filename is required if you are prompted and the name
is not displayed in the prompt.
* IP addresses and DNS names are optional. Multiple values can be specified as a
comma separated string. If no IP addresses or DNS names are provided, you may
disable hostname verification in your SSL configuration.
* All certificates generated by this tool will be signed by a certificate authority (CA)
unless the --self-signed command line option is specified.
The tool can automatically generate a new CA for you, or you can provide your own with
the --ca or --ca-cert command line options.
By default the 'cert' mode produces a single PKCS#12 output file which holds:
* The instance certificate
* The private key for the instance certificate
* The CA certificate
If you specify any of the following options:
* -pem (PEM formatted output)
* -multiple (generate multiple certificates)
* -in (generate certificates from an input file)
then the output will be be a zip file containing individual certificate/key files
Enter password for CA (elastic-stack-ca.p12) :
Please enter the desired output file [elastic-certificates.p12]:
Enter password for elastic-certificates.p12 :
Certificates written to /Users/liuxg/elastic/elasticsearch-8.9.0/elastic-certificates.p12
This file should be properly secured as it contains the private key for
your instance.
This file is a self contained file and can be copied and used 'as is'
For each Elastic product that you wish to configure, you should copy
this '.p12' file to the relevant configuration directory
and then follow the SSL configuration instructions in the product guide.
For client applications, you may only need to copy the CA certificate and
configure the client to trust this certificate.
$ ls
LICENSE.txt data logs
NOTICE.txt elastic-certificates.p12 modules
README.asciidoc elastic-stack-ca.p12 plugins
bin jdk.app
config lib在运行上面的命令时,我们需要输入在上一步定义的 password。在输出中,我们可以看到一个新生成的 elastic-certificates.p12 文件。默认情况下,“cert” 模式生成一个 PKCS#12 输出文件,其中包含:
- 实例证书
- 实例证书的私钥
- CA 证书
我们可以通过如下的工具来进行检查:
$ keytool -keystore elastic-certificates.p12 -list
Enter keystore password:
Keystore type: PKCS12
Keystore provider: SUN
Your keystore contains 2 entries
ca, Aug 8, 2023, trustedCertEntry,
Certificate fingerprint (SHA-256): 8C:32:23:AB:22:8A:51:96:D8:6D:8C:A1:32:E8:E5:DC:A1:97:A4:59:F3:55:18:EC:A1:E0:EB:96:74:61:D5:81
instance, Aug 8, 2023, PrivateKeyEntry,
Certificate fingerprint (SHA-256): 98:45:D7:F2:B2:AC:0B:A0:2C:EF:14:FB:70:54:1B:00:24:02:CB:D5:48:57:2C:8A:47:92:F9:F3:0A:0E:1D:78当然,我们也可以使用如下的工具来查看:
openssl pkcs12 -info -nodes -in elastic-stack-ca.p12$ openssl pkcs12 -info -nodes -in elastic-stack-ca.p12
Enter Import Password:
MAC: sha256, Iteration 10000
MAC length: 32, salt length: 20
PKCS7 Data
Shrouded Keybag: PBES2, PBKDF2, AES-256-CBC, Iteration 10000, PRF hmacWithSHA256
Bag Attributes
friendlyName: ca
localKeyID: 54 69 6D 65 20 31 36 39 31 34 36 36 33 36 31 33 35 34
Key Attributes: <No Attributes>
-----BEGIN PRIVATE KEY-----
MIIEvwIBADANBgkqhkiG9w0BAQEFAASCBKkwggSlAgEAAoIBAQDYmz7UmFR83SNN
9SoCPoV9PU5DbTYPDVCFWXNoshsntgkrrhtOqP5a7vAXGT3uVvvN6kEQSVz5jtV5
nZtuTI/xbMDyM76JwZwfD8ncwiuNnfeqGGkHAFMDDSuj2b+dgmiUgadcX1LM1mtj
D8r7ayWJLzVoqZGW5OohUtSE5nbirRHWYg0z7pAFE9eVKXGonJwdr2ps5KIaQeAw
4XwRxsOrfNnI6qOia9LPSuoYhiHHvFGQLg/SApDga3DWWcCvC1Y7G6ThkSmBHJN5
343j9WTyG1zfeKbxX5Y6Kc95CIe5ddafP9YziNBLYfOW3vyRtykw8KCYy6Tv+X6B
7TGcEcgfAgMBAAECggEAB1/U4vmcrSbKNBxyP0lQBu3pyc0TpHq+w9hCLM2DgMKa
mIYahkvY/QRaRpVxalMQl5FJTcik0n1uZYmPTreeK7xluHLSiQlL/pkgm9Q9SPQy
Oyd0y+w5Ta1KtkIl9LLWSws7xQVQLr3nqHCGzjB23EjJkYEHl9+LQqWTRQ/Wx4WU
2q9+SY5Er5nc3XPlzZYif2j61Yl1w97sjFibgVola6Ad0dJ4ALF8EGy9WChQ66NJ
ajoRaN2LMImQZHF2Zt1tM/MwI3czC+3O7tPZOlNZ0UKGeYEUQ/snsvjNhKq4MrwC
tOdFF+opQ2lP6jOrA/b83V9tHQehhj80MxWbGrk2QQKBgQDs33DrNGw4ZspDRi70
5HGoofebZ6uUzffAMRgRp0HTJYnVABLw7FmAwT0LUJdfj0MN8K1FUdKMMxCVRg90
cMDO061gzzfOIpDcAhbzilNXC1DXsE710rk8QMZ7iFY0E9D5CfsOBAljDdKgRzzT
+2hOJ/efbA0s99UKPeDyZ64d2QKBgQDqGN0x2VpXIOLn0srAJx+mwPyrHhBgrGfR
DWwsyMfnJBv5dKOJOhPLRdyPX0k7HLrFyj6Pmki0B/TF8kq0qW3Epy3pWti/VgDJ
YrhZkqjUjhVb4C7/BNTs3kCqyaiucXvaofvymAoTqEpglZ/oYHkqwit6jz18teD7
2ep+IlzCtwKBgQC/MPMRxfR76evkNSf9ns5m0KTtGNaTe1Q4GuhUh25IIYqJFFA1
inALzu2YzmoARcBX5iXVR9/sLeN6uVwMHl5iEtVkyJ1AkwHdswoXdVUjcwzDq5lw
LbA6BAaw+zCpRD1uZjHv9C4nd6bEm/trFwfv3a6vTSWtYDTi2WNSBYGysQKBgQDT
fXMYvgzn+kYEumOCBdaKiH+8+IRDUn7YVxALxbkUEYNUcxPrvhRz6MHCpYs7ZFE4
r+alRfW48BcrXiIv5YHN0FuiHvkCo2hCiHWUNvNgVJznTDopGuxissgpg9ZpAw2q
D/3WxZUU/U10xLia782H27P8HbynFooT/mPjYJf9MQKBgQCqm5fYBhZxTQ5FAZe4
gTdiShx81Nr8cUbTBpVGfK/ADCc+G+67fAK7EYgg2LxcKpHkuy/NNUkcnFYKjvAX
FhLkSA8N/fXsLYi3JgbvFoaKAsb003TcV7/rPM+0Oqcrxy4feJM/2QeYIqpPVtlV
kjUYJSAaHIGiK6OlbBuBWIRzzA==
-----END PRIVATE KEY-----
PKCS7 Encrypted data: PBES2, PBKDF2, AES-256-CBC, Iteration 10000, PRF hmacWithSHA256
Certificate bag
Bag Attributes
friendlyName: ca
localKeyID: 54 69 6D 65 20 31 36 39 31 34 36 36 33 36 31 33 35 34
subject=CN = Elastic Certificate Tool Autogenerated CA
issuer=CN = Elastic Certificate Tool Autogenerated CA
-----BEGIN CERTIFICATE-----
MIIDSjCCAjKgAwIBAgIVALXN3Mz3+RI7lj3cGczFF2T3X3l3MA0GCSqGSIb3DQEB
CwUAMDQxMjAwBgNVBAMTKUVsYXN0aWMgQ2VydGlmaWNhdGUgVG9vbCBBdXRvZ2Vu
ZXJhdGVkIENBMB4XDTIzMDgwODAzNDUyOVoXDTI2MDgwNzAzNDUyOVowNDEyMDAG
A1UEAxMpRWxhc3RpYyBDZXJ0aWZpY2F0ZSBUb29sIEF1dG9nZW5lcmF0ZWQgQ0Ew
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDYmz7UmFR83SNN9SoCPoV9
PU5DbTYPDVCFWXNoshsntgkrrhtOqP5a7vAXGT3uVvvN6kEQSVz5jtV5nZtuTI/x
bMDyM76JwZwfD8ncwiuNnfeqGGkHAFMDDSuj2b+dgmiUgadcX1LM1mtjD8r7ayWJ
LzVoqZGW5OohUtSE5nbirRHWYg0z7pAFE9eVKXGonJwdr2ps5KIaQeAw4XwRxsOr
fNnI6qOia9LPSuoYhiHHvFGQLg/SApDga3DWWcCvC1Y7G6ThkSmBHJN5343j9WTy
G1zfeKbxX5Y6Kc95CIe5ddafP9YziNBLYfOW3vyRtykw8KCYy6Tv+X6B7TGcEcgf
AgMBAAGjUzBRMB0GA1UdDgQWBBRbBxCWijjKV9vJ0sHNxTyXASgguDAfBgNVHSME
GDAWgBRbBxCWijjKV9vJ0sHNxTyXASgguDAPBgNVHRMBAf8EBTADAQH/MA0GCSqG
SIb3DQEBCwUAA4IBAQDLSMpvzOOIjgon3Z+16q9wO9RgwK5AogJjtiYdPcUWSQVU
JWOdJSDEJCGD+N2pse1F46/nfWY1sJRS1/iM5CxKIiYna4HULOzCYhxsk4WK5kZx
wZ5TNx9WW/+rBYiltjwR48DpVQbEAUCtR47LxW/KSqqr2THRXG2Ni/6jFns498nV
IrGOUVLPW7bEpMTWUMmnCxIjgpqY7wO+7ePgu1/zSLghxMQlTgMw4sSskiGDeboz
SKxh27ttk9sStyvDhEUW+eir+peUdY/xoezVViAM7T5UtlT1iQzhZ1JCWbJtQhfV
8Y8wBF2UUo+ZF4SkQ2Pkwodhz4BbHCw9dH1Q+AnW
-----END CERTIFICATE-----openssl pkcs12 -in elastic-certificates.p12 -nodes -nokeys -clcerts | openssl x509 -enddate -noout$ openssl pkcs12 -in elastic-certificates.p12 -nodes -nokeys -clcerts | openssl x509 -enddate -noout
Enter Import Password:
notAfter=Aug 7 03:52:51 2026 GMT我们可以使用如上的证书来配置 Elasticsearch:
#elasticsearch.yml example
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.client_authentication: required
xpack.security.transport.ssl.keystore.path: elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: elastic-certificates.p12
xpack.security.transport.http.enabled: true
xpack.security.transport.http.verification_mode: certificate
xpack.security.transport.http.client_authentication: required
xpack.security.transport.http.keystore.path: elastic-certificates.p12
xpack.security.transport.http.truststore.path: elastic-certificates.p12更多参考 “Elasticsearch:使用不同的 CA 更新安全证书 (一)(二)”
方法二:创建 pem 和 key 证书
生成 CA 证书
我们使用如下的命令来进行:
./bin/elasticsearch-certutil ca --pem$ pwd
/Users/liuxg/elastic/elasticsearch-8.9.0
$ ./bin/elasticsearch-certutil ca --pem
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.
The 'ca' mode generates a new 'certificate authority'
This will create a new X.509 certificate and private key that can be used
to sign certificate when running in 'cert' mode.
Use the 'ca-dn' option if you wish to configure the 'distinguished name'
of the certificate authority
By default the 'ca' mode produces a single PKCS#12 output file which holds:
* The CA certificate
* The CA's private key
If you elect to generate PEM format certificates (the -pem option), then the output will
be a zip file containing individual files for the CA certificate and private key
Please enter the desired output file [elastic-stack-ca.zip]:
$ ls
LICENSE.txt bin elastic-stack-ca.zip logs
NOTICE.txt config jdk.app modules
README.asciidoc data lib plugins从上面的输出中,我们可以看到一个叫做 elastic-stack-ca.zip 的文件被生成了。我们可以通过如下的命令来进行解压缩:
unzip elastic-stack-ca.zip $ unzip elastic-stack-ca.zip
Archive: elastic-stack-ca.zip
creating: ca/
inflating: ca/ca.crt
inflating: ca/ca.key
$ tree ./ca -L 2
./ca
├── ca.crt
└── ca.key
生成证书
我们使用如下的命令来进行操作:
./bin/elasticsearch-certutil cert -ca-cert ca/ca.crt -ca-key ca/ca.key --pem$ pwd
/Users/liuxg/elastic/elasticsearch-8.9.0
$ ls
LICENSE.txt ca jdk.app plugins
NOTICE.txt config lib
README.asciidoc data logs
bin elastic-stack-ca.zip modules
$ ./bin/elasticsearch-certutil cert -ca-cert ca/ca.crt -ca-key ca/ca.key --pem
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.
The 'cert' mode generates X.509 certificate and private keys.
* By default, this generates a single certificate and key for use
on a single instance.
* The '-multiple' option will prompt you to enter details for multiple
instances and will generate a certificate and key for each one
* The '-in' option allows for the certificate generation to be automated by describing
the details of each instance in a YAML file
* An instance is any piece of the Elastic Stack that requires an SSL certificate.
Depending on your configuration, Elasticsearch, Logstash, Kibana, and Beats
may all require a certificate and private key.
* The minimum required value for each instance is a name. This can simply be the
hostname, which will be used as the Common Name of the certificate. A full
distinguished name may also be used.
* A filename value may be required for each instance. This is necessary when the
name would result in an invalid file or directory name. The name provided here
is used as the directory name (within the zip) and the prefix for the key and
certificate files. The filename is required if you are prompted and the name
is not displayed in the prompt.
* IP addresses and DNS names are optional. Multiple values can be specified as a
comma separated string. If no IP addresses or DNS names are provided, you may
disable hostname verification in your SSL configuration.
* All certificates generated by this tool will be signed by a certificate authority (CA)
unless the --self-signed command line option is specified.
The tool can automatically generate a new CA for you, or you can provide your own with
the --ca or --ca-cert command line options.
By default the 'cert' mode produces a single PKCS#12 output file which holds:
* The instance certificate
* The private key for the instance certificate
* The CA certificate
If you specify any of the following options:
* -pem (PEM formatted output)
* -multiple (generate multiple certificates)
* -in (generate certificates from an input file)
then the output will be be a zip file containing individual certificate/key files
Please enter the desired output file [certificate-bundle.zip]:
Certificates written to /Users/liuxg/elastic/elasticsearch-8.9.0/certificate-bundle.zip
This file should be properly secured as it contains the private key for
your instance.
After unzipping the file, there will be a directory for each instance.
Each instance has a certificate and private key.
For each Elastic product that you wish to configure, you should copy
the certificate, key, and CA certificate to the relevant configuration directory
and then follow the SSL configuration instructions in the product guide.
For client applications, you may only need to copy the CA certificate and
configure the client to trust this certificate.
$ ls
LICENSE.txt ca elastic-stack-ca.zip modules
NOTICE.txt certificate-bundle.zip jdk.app plugins
README.asciidoc config lib
bin data logs我们发现一个新生成的 elastic-stack-ca.zip 文件。我们可以通过解压缩的方法来查看里面的文件:
unzip certificate-bundle.zip $ unzip certificate-bundle.zip
Archive: certificate-bundle.zip
creating: instance/
inflating: instance/instance.crt
inflating: instance/instance.key 我们可以通过如下的命令来进行查看:
openssl x509 -in ca/ca.crt -text -noout$ openssl x509 -in ca/ca.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
a0:08:2b:4a:2e:42:27:1a:e9:b3:09:54:a4:f1:71:ed:6f:61:a6:45
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = Elastic Certificate Tool Autogenerated CA
Validity
Not Before: Aug 8 04:28:33 2023 GMT
Not After : Aug 7 04:28:33 2026 GMT
Subject: CN = Elastic Certificate Tool Autogenerated CA
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:85:3c:66:37:4c:66:03:93:27:58:34:c9:c9:38:
5c:12:e0:1a:85:b4:89:23:5f:ed:ad:2e:df:8d:0b:
0a:0c:39:df:04:e2:43:34:03:92:c7:d0:4a:55:84:
78:1f:d7:0d:48:38:17:e9:a7:3b:93:11:2a:a4:f3:
b5:67:bf:d3:89:99:ff:67:1c:40:3c:bf:bf:d5:9a:
4d:3f:88:b4:76:5c:4f:c6:7e:a7:2b:92:53:f5:d8:
60:1d:39:03:e1:4f:b4:a3:06:ef:60:dd:db:be:c3:
25:4b:34:d1:42:a2:0c:c9:59:af:9c:90:6c:1f:8c:
3b:8f:cc:55:6f:f2:83:83:d7:7a:89:fd:3b:c1:a7:
91:53:b1:60:0f:2c:84:14:16:9d:7c:33:38:55:f0:
85:ec:e7:cf:64:c2:2a:00:f4:9d:04:8e:af:e2:54:
f1:6d:3a:81:3b:0c:ad:cd:21:6d:fe:02:4b:66:c7:
d0:17:1f:4a:f7:ad:30:49:ab:5e:aa:df:0b:8d:2e:
01:2d:c5:e6:30:95:60:0a:2b:06:59:21:7b:b9:6d:
60:93:9c:1b:ba:49:09:73:26:49:9d:61:97:c9:f4:
26:53:53:95:31:de:d4:c3:d3:cd:63:01:df:63:05:
fa:63:cf:6e:ed:e2:63:62:85:93:ea:7a:53:a7:b5:
4d:8f
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
16:E4:55:54:1F:49:64:FB:8D:39:4C:9A:A1:67:9C:44:D0:49:47:10
X509v3 Authority Key Identifier:
16:E4:55:54:1F:49:64:FB:8D:39:4C:9A:A1:67:9C:44:D0:49:47:10
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
12:a5:62:41:8d:e3:8f:5e:e4:ff:ec:6a:24:ba:f0:7b:b7:9c:
00:28:81:45:d0:83:6b:dd:48:02:f6:21:c9:3c:45:da:ec:d3:
24:a6:37:eb:bf:57:65:bb:50:05:aa:2d:8c:e4:da:15:01:9d:
72:7b:4a:d6:79:42:30:dd:2f:da:a8:3a:9a:48:e5:4c:73:ef:
ca:70:4f:b4:55:7e:a7:6e:43:3b:6a:e0:94:87:ec:a6:83:75:
6c:c9:6a:a9:23:52:66:e8:59:c1:3b:0d:cf:2c:e0:33:01:e5:
8a:81:a9:d7:3e:aa:68:c8:47:e2:c6:35:5d:49:b7:f8:3f:b4:
5c:2d:d3:da:cd:67:f2:fc:4d:a5:45:0b:e8:c9:10:89:18:94:
36:af:2e:c3:f2:1b:a6:80:06:55:32:ed:f2:83:a2:26:3a:58:
7d:cd:51:fd:4f:e8:02:2f:66:63:6e:9d:36:c8:3f:32:8e:0d:
67:cb:5f:7c:4c:62:73:a3:9b:ce:5e:ba:fb:92:81:64:b2:56:
72:0d:69:3e:03:0c:7a:61:10:2c:2d:f5:d2:54:5f:de:42:b4:
0c:4c:cb:65:99:e4:8a:fd:57:b0:ad:f8:23:00:35:fb:54:84:
6d:32:b2:34:53:7a:99:40:b3:56:75:02:08:04:27:07:5e:4e:
78:65:33:77openssl x509 -in instance/instance.crt -text -noout$ openssl x509 -in instance/instance.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
ab:59:38:42:bc:5f:2d:0f:2b:22:e3:44:14:78:ed:5f:5e:73:fe:43
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = Elastic Certificate Tool Autogenerated CA
Validity
Not Before: Aug 8 04:32:58 2023 GMT
Not After : Aug 7 04:32:58 2026 GMT
Subject: CN = instance
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:a2:e6:6e:74:ce:52:8a:d8:3b:6b:3f:23:cb:a6:
e9:5e:83:55:6c:e1:77:53:0e:e1:9e:fd:18:cc:43:
57:a5:09:9c:e6:06:ab:89:cd:83:f6:4a:71:ab:1c:
f5:ed:74:26:15:67:52:27:d5:5c:b3:f3:c5:ba:ee:
41:cb:45:10:a9:84:b7:87:88:de:6f:ec:db:62:36:
b8:6e:84:ca:9d:99:da:8f:73:3f:d6:54:5e:88:7f:
1a:96:91:e6:e3:e6:17:c6:a8:df:d9:fa:b7:ad:de:
b1:d7:c6:dd:05:46:5f:2e:e1:c4:4f:f0:7d:95:7e:
d4:83:b6:b8:5a:7d:4e:51:b8:54:9b:76:09:6f:b6:
14:57:86:c3:77:0f:26:19:f9:d9:12:68:b8:4c:d5:
07:5c:2a:c5:7e:a2:53:b0:8b:bd:9c:d4:13:56:13:
ae:53:99:16:81:64:0c:9a:df:d1:9d:ff:f7:21:74:
01:08:bf:22:91:09:bd:b9:f3:12:dc:51:4b:29:54:
b6:09:d4:47:f0:b5:22:48:b9:d6:22:ac:2e:9a:43:
45:35:e4:8e:a0:c3:0a:88:97:a9:36:96:9d:a3:08:
df:fa:4c:51:05:2f:ef:80:51:56:02:0f:ee:5a:47:
53:75:20:23:7a:c5:a8:4d:65:67:e9:46:f6:a0:24:
0b:e7
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
AF:83:15:0D:DF:5E:7F:55:84:07:7E:C4:F9:F4:5C:69:65:98:10:1B
X509v3 Authority Key Identifier:
16:E4:55:54:1F:49:64:FB:8D:39:4C:9A:A1:67:9C:44:D0:49:47:10
X509v3 Basic Constraints:
CA:FALSE
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
20:8d:c2:d1:21:8e:82:9a:9c:7a:82:6c:d3:4e:c4:6b:cd:e5:
99:ab:27:ee:0a:05:47:c1:d3:3e:b5:2a:29:07:a8:0c:79:f4:
b5:1f:23:f9:c9:3f:26:ba:c2:2b:2a:9f:2d:d8:78:dc:77:8c:
6a:4c:17:39:84:35:bc:d8:0c:e0:5d:14:59:ae:7f:a4:f6:4d:
b9:ab:da:57:c7:ee:9c:48:ac:82:72:53:6b:1a:be:3f:1d:96:
f0:de:70:df:5d:7f:5f:aa:a2:ed:27:94:2d:80:be:6a:b1:a0:
b1:1a:56:25:67:b4:f6:d9:bb:80:fe:03:c8:07:76:9e:60:2e:
60:3a:2f:f1:c9:83:83:4f:b2:ee:fe:ef:64:93:ac:5a:20:0d:
18:cc:bc:3d:9c:9b:89:89:de:22:5b:1b:45:d1:66:c0:22:85:
01:3b:98:b3:9b:f4:41:d9:45:56:a6:ea:bc:99:5f:71:e0:57:
a8:39:10:c9:41:ed:cf:68:49:82:8d:b9:fb:56:8e:19:be:05:
de:7e:bd:ed:88:6e:a7:0f:9c:b4:28:e8:bd:b5:12:d6:52:7f:
1e:89:24:73:0d:39:61:32:66:e4:f6:99:78:86:e5:26:a5:c9:
36:e3:66:a6:4f:97:76:c3:3d:cf:6d:17:47:d3:75:65:d4:a0:
7a:88:16:aa我们可以通过上面的证书来配置 Elasticsearch:
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.client_authentication: required
xpack.security.transport.ssl.keystore.path: instance.key
xpack.security.transport.ssl.truststore.path: instance.crt
xpack.security.transport.http.enabled: true
xpack.security.transport.http.verification_mode: certificate
xpack.security.transport.http.client_authentication: required
xpack.security.transport.http.keystore.path: instance.key
xpack.security.transport.http.truststore.path: instance.crt更多阅读的文章:
-
Elasticsearch:为日志分析设置安全的 Elasticsearch 管道
-
Elasticsearch:如何使用自定义的证书安装 Elastic Stack 8.x
-
Security:如何安装 Elastic SIEM 和 EDR
-
Elasticsearch:如何在不更新证书的情况下为集群之间建立互信