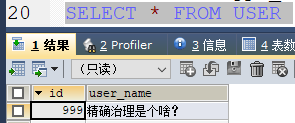
解题思路
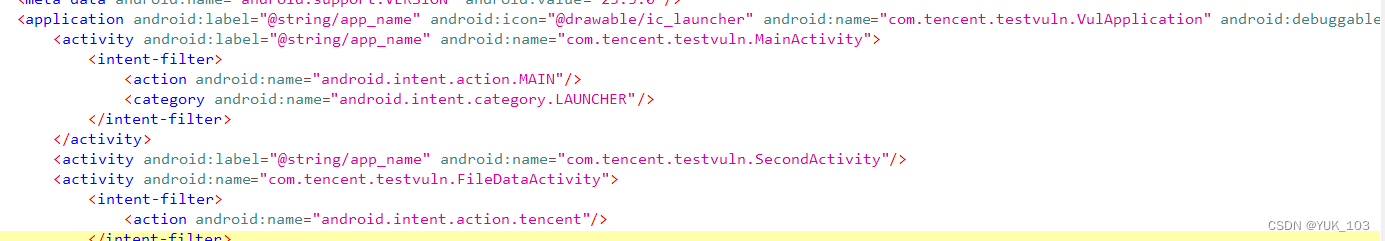
导入jadx查看manifest.xml
查看主函数并未发现有价值的东西,于是查看manifest.xml中主函数下一个<activity>
截取FileDataActivity代码
package com.tencent.testvuln;
import android.os.Bundle;
import android.widget.TextView;
import com.tencent.testvuln.c.Encryto;
public class FileDataActivity extends a {
private TextView c;
/* access modifiers changed from: protected */
@Override // com.tencent.testvuln.a
public void onCreate(Bundle bundle) {
super.onCreate(bundle);
setContentView(R.layout.activity_main3);
this.c = (TextView) findViewById(R.id.textView1);
this.c.setText(Encryto.decode(this, "9YuQ2dk8CSaCe7DTAmaqAA=="));
}
}
这里有一个Encryto.decode函数,查看声明
package com.tencent.testvuln.p003c;
/* renamed from: com.tencent.testvuln.c.Encryto */
public class Encryto {
public static native int checkSignature(Object obj);
public static native String decode(Object obj, String str);
public static native String doRawData(Object obj, String str);
public static native String encode(Object obj, String str);
public native String HelloLoad();
static {
System.loadLibrary("JNIEncrypt");
}
}
看到JNI就说明调用外部的库文件了,查看资源文件

放入IDA中分析,shift + F12查看字符串
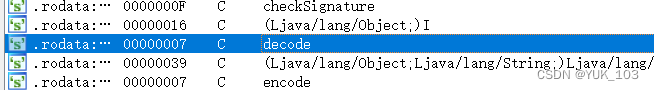
双击跳转,再次双击,跳转到汇编代码,按F5转换伪代码
int __cdecl decode(int a1, int a2, int a3, int a4)
{
char *v4; // esi
int result; // eax
char *v6; // esi
size_t v7; // eax
int v8; // [esp+0h] [ebp-2Ch]
int (__cdecl *v9)(int, char *, size_t); // [esp+0h] [ebp-2Ch]
char v10[20]; // [esp+4h] [ebp-28h] BYREF
unsigned int v11; // [esp+18h] [ebp-14h]
v11 = __readgsdword(0x14u);
if ( checkSignature(a1, a2, a3) == 1 )
{
strcpy(v10, "thisisatestkey==");
v4 = (char *)(*(int (__cdecl **)(int, int, _DWORD))(*(_DWORD *)a1 + 676))(a1, a4, 0);
v8 = AES_128_ECB_PKCS5Padding_Decrypt(v4, (int)v10);
(*(void (__cdecl **)(int, int, char *))(*(_DWORD *)a1 + 680))(a1, a4, v4);
result = (*(int (__cdecl **)(int, int))(*(_DWORD *)a1 + 668))(a1, v8);
}
else
{
v6 = UNSIGNATURE[0];
v9 = *(int (__cdecl **)(int, char *, size_t))(*(_DWORD *)a1 + 652);
v7 = strlen(UNSIGNATURE[0]);
result = v9(a1, v6, v7);
}
return result;
}
很简单,有AES关键字,猜测是AES128加密,mode为ECB,密文为之前看到的9YuQ2dk8CSaCe7DTAmaqAA==,密钥为thisisatestkey==
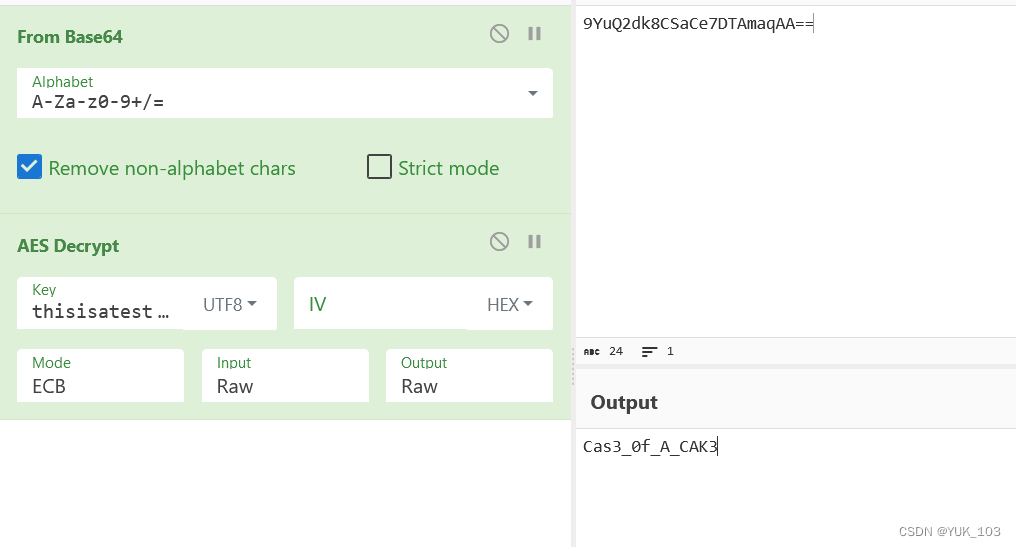
连蒙带猜提交成功。
2023.7.6 牙疼。。。。。